A Methodological Approach to Evaluate Security Requirements Engineering Methodologies: Application to the IREHDO2 Project Context
Abstract
:1. Introduction
- The description of a whole methodology for evaluating SRE based on a set of generic evaluation criteria that shall be refined for each organizations.
- The application of this methodology to the IREHDO2 project context.
- An evaluation of three SRE methodologies based on the feedback from security experts.
2. Related Works
- Issue A: Evaluation criteria coverage. SRE methodologies aim at covering the whole SRE process (i.e., elicitation, evaluation and documentation) [22]. From our study, we noted that the majority of the evaluation studies except [29] lack a full emphasis on the whole SRE process [35]. While some works [21,22,31] concentrate on evaluating the extent of support to security requirements elicitation at earlier stages; some others [27] focus on evaluating the extent of support to documentation in terms of reusable patterns or modelling initiatives.
- Issue B: Evaluation criteria affirmation. The evaluation criteria must result from a systematic process or standard method, such as [36], to facilitate reusability. However, in the majority of works, the proposed evaluation criteria were ad hoc and lack affirmation on why the criteria were good enough to be considered for the evaluation [28,31,32]. In this aspect only [29] can be noted as an exceptional case as the evaluation is based on the international standard [30].
- Issue C: Lack of stakeholders’ involvement. This issue concerns the involvement of stakeholders’ views while formulating the evaluation criteria. As highlighted in [37], the requirements process is a human endeavour, and so the requirements method or tool must be able to support the need for stakeholders to communicate their ideas and obtain feedback. In our context, stakeholders refer to the SRE methodology users (e.g., requirements engineers). However, from our observation we found that none of these comparative studies involved SRE experts while formulating the evaluation criteria for an SRE methodology. Moreover, almost all of the works acknowledge (either implicitly/explicitly) the significance of involving stakeholders’ perspectives in the SRE process. For instance, [22] includes a criterion that concerns the integration of stakeholders’ views to support multilateral security requirements analysis.
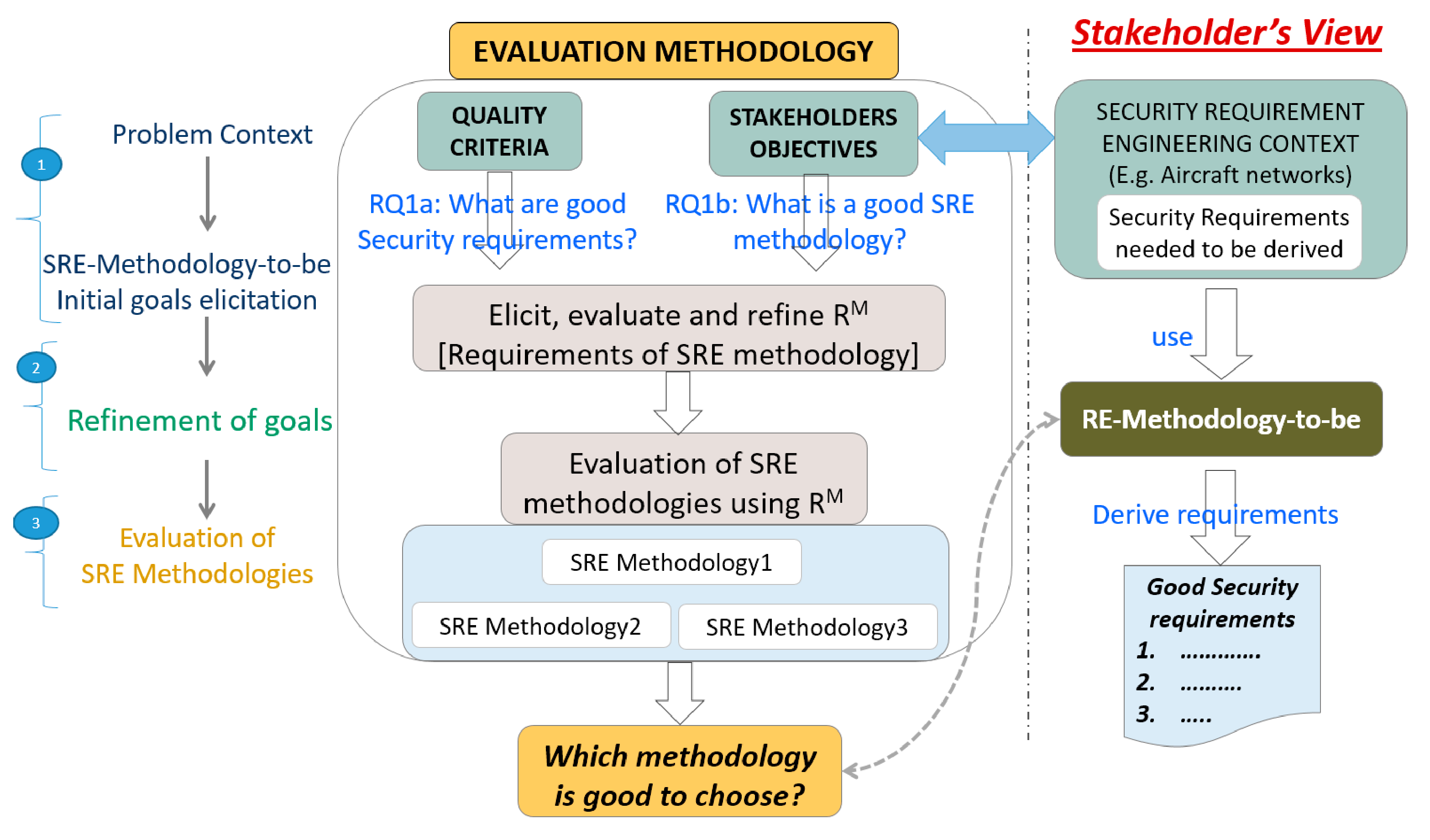
3. Our SRE Evaluation Methodology
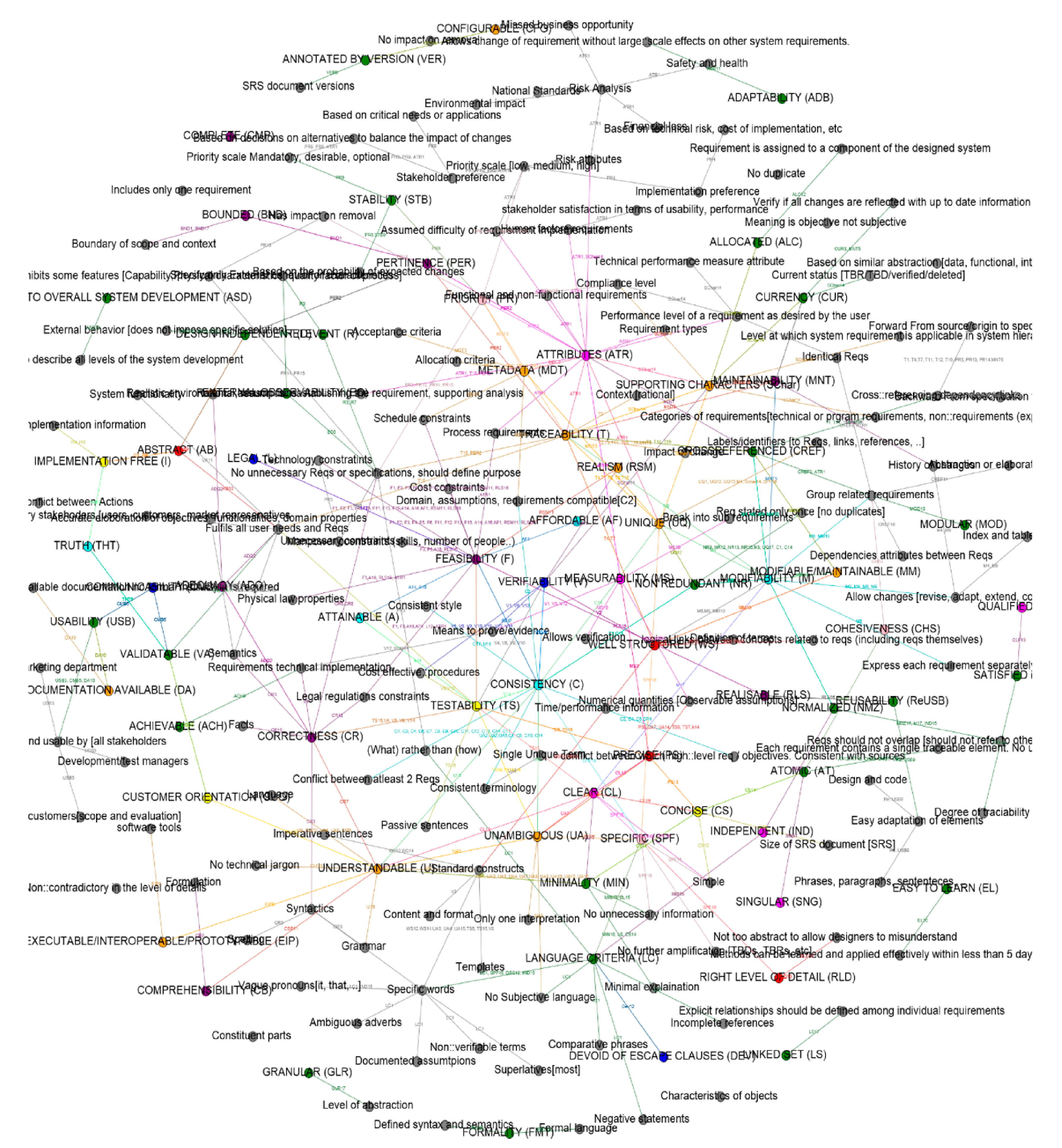
4. How to Qualify Good Security Requirements?
5. What Is a Good SRE Methodology?
5.1. Step1: Problem Context and Initial Requirement Analysis
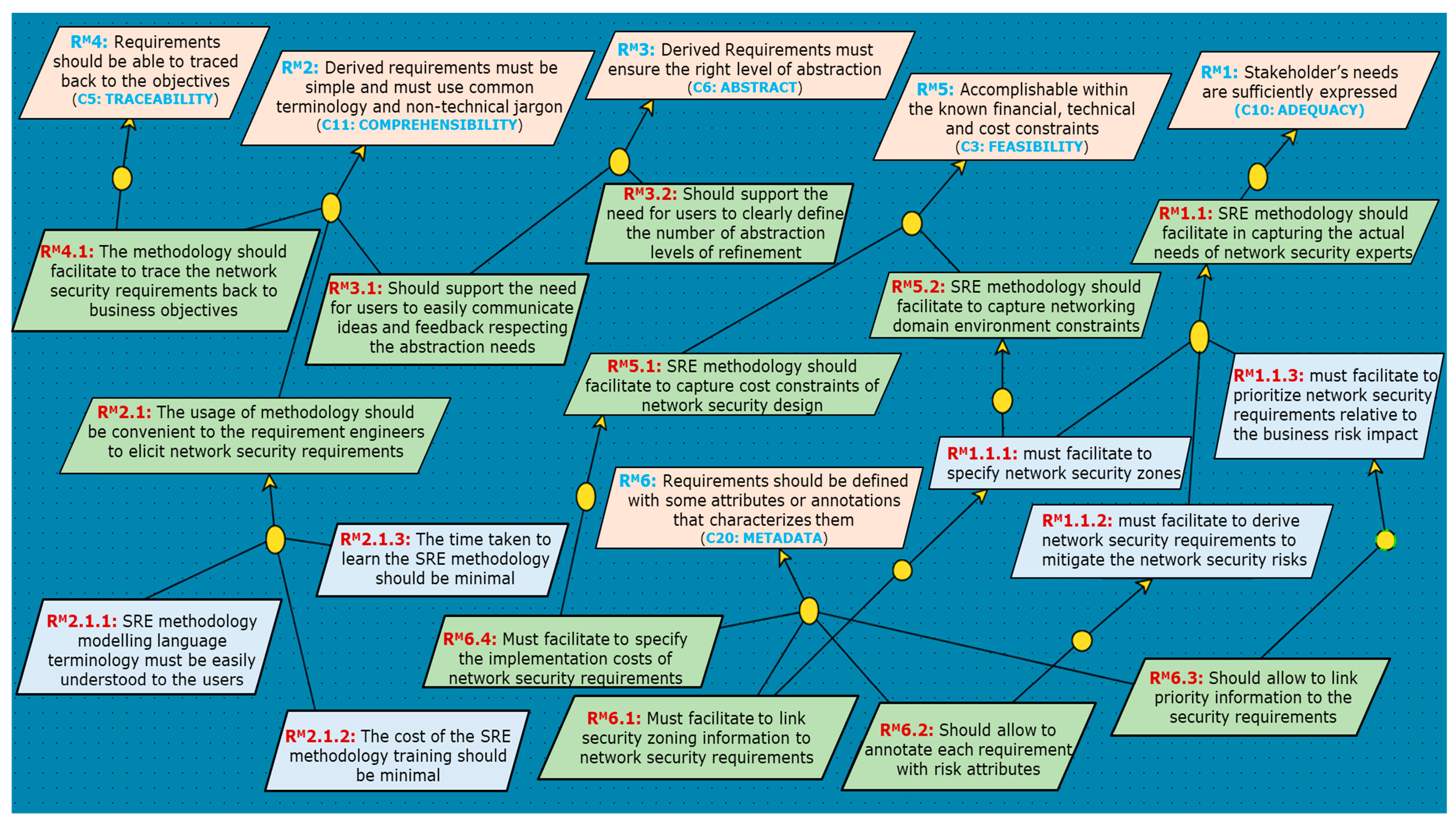
5.2. Step2: Refinement (RM) Requirement Analysis
Adequacy (C10) and Metadata (C20)
Comprehensibility (C11)
Abstract (C6)
Traceability (C3) and Feasibility (C5)
Evaluation Methods and Metrics
6. Evaluation of Existing SRE Approaches
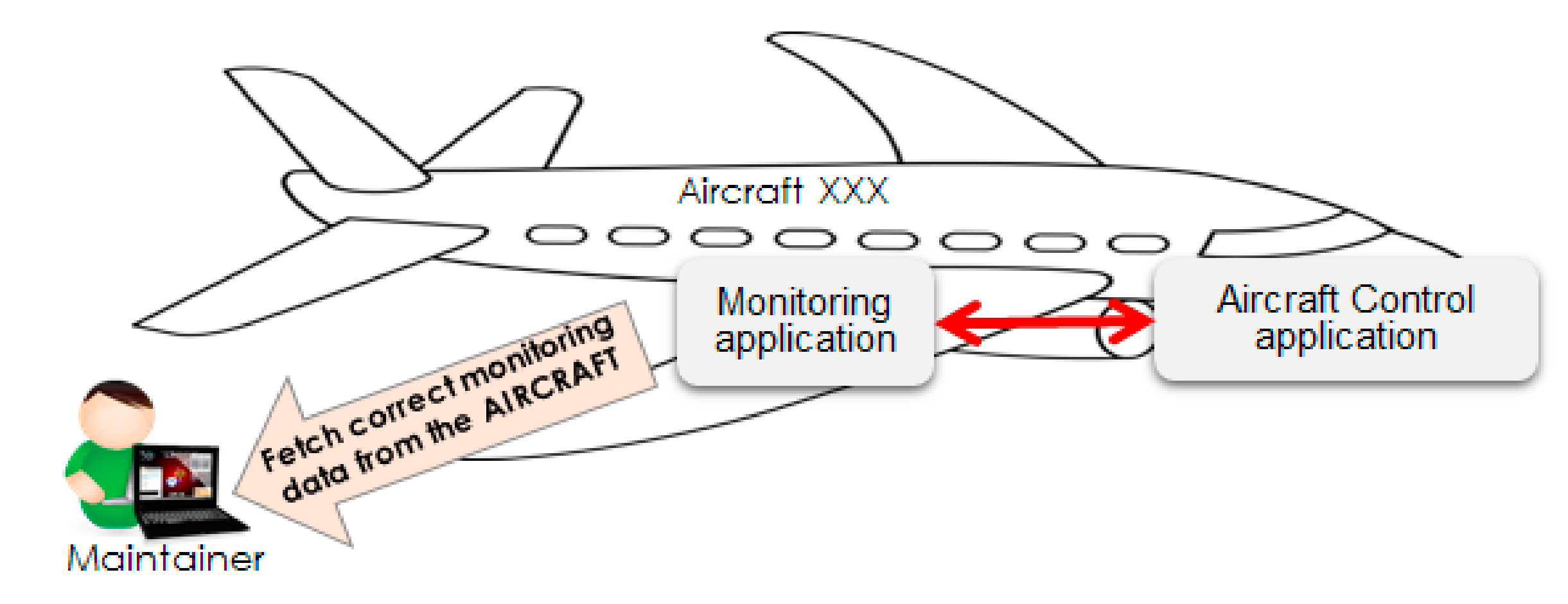
6.1. Evaluation Iteration 1—Use Case Scenario 1
6.1.1. Scenario Implementation Using Secure KAOS
6.1.2. Scenario Implementation Using STS
6.1.3. Scenario Implementation Using SEPP
6.1.4. Evaluation at Iteration 1—Results and Discussion
6.2. Evaluation Iteration 2—Use Case Scenario 2
6.3. Evaluation Iteration 2—STS Modelling and Feedback Discussion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| CSPF | concertized security problem frames |
| KAOS | Keep All Objectives Satisfied |
| RE | Requirement Engineering |
| SABSA | Sherwood Applied Business Security Architecture |
| SEPP | Security Engineering Process using Patterns |
| SPF | security problem frames |
| SRE | Security Requirement Engineering |
| STS | Secure socio-Technical Systems |
References
- SANS. Securing Against the Most Common Vectors of Cyber Attacks 2017. Available online: https://www.sans.org/white-papers/37995/ (accessed on 12 July 2021).
- ISO/IEC 27033 IT Network Security Standard. Available online: http://www.iso27001security.com/html/27033.html (accessed on 11 July 2021).
- SANS. Infrastructure Security Architecture for Effective Security Monitoring 2015. Available online: https://www.sans.org/white-papers/36512/ (accessed on 12 July 2021).
- Stawowski, M. Network Security Architecture. ISSA J. 2009, 7, 34–38. Available online: https://www.bluetoad.com/publication/?m=1336&i=16198&p=34&ver=html5 (accessed on 12 July 2021).
- Laborde, R.; Kamel, M.; Barrère, F.; Benzekri, A. Implementation of a Formal Security Policy Refinement Process in WBEM Architecture. J. Netw. Syst. Manag. 2007, 15, 241–266. [Google Scholar] [CrossRef]
- Laborde, R.; Barrère, F.; Benzekri, A. Toward authorization as a service: A study of the XACML standard. In Proceedings of the 16th Communications & Networking Symposium, Society for Computer Simulation International, San Diego, CA, USA, 7–10 April 2013; p. 9. [Google Scholar]
- Laborde, R.; Oglaza, A.; Wazan, A.S.; Barrère, F.; Benzekri, A. A situation-driven framework for dynamic security management. Ann. Telecommun. 2019, 74, 185–196. [Google Scholar] [CrossRef] [Green Version]
- Barrere, F.; Benzekri, A.; Grasset, F.; Laborde, R. A multi-domain security policy distribution architecture for dynamic IP based VPN management. In Proceedings of the Policies for Distributed Systems and Networks, Monterey, CA, USA, 5–7 June 2002. [Google Scholar]
- Sherwood, N.A. SABSA (Sherwood Applied Business Security Architecture)—A Business-Driven Approach; CRC Press: Boca Raton, FL, USA, 2005. [Google Scholar]
- Hoo, K.S.; Sudbury, A.; Jaquith, A. Tangible ROI through Secure Software Engineering. Security Business Q. 2001, 1. [Google Scholar]
- Iqbal, J.; Ahmad, R.B.; Khan, M.; Alyahya, S.; Nasir, M.H.N.; Akhunzada, A.; Shoaib, M. Requirements engineering issues causing software development outsourcing failure. PLoS ONE 2020, 15, e0229785. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Bulusu, S.T.; Laborde, R.; Wazan, A.S.; Barrère, F.; Benzekri, A. Towards the weaving of the characteristics of good security requirements. In Proceedings of the International Conference on Risks and Security of Internet and Systems, Paris, France, 4–6 November 2020; Springer: Berlin/Heidelberg, Germany, 2016; pp. 60–74. [Google Scholar]
- Bulusu, S.T.; Laborde, R.; Wazan, A.S.; Barrère, F.; Benzekri, A. Which Security Requirements Engineering Methodology Should I Choose?: Towards a Requirements Engineering-based Evaluation Approach. In Proceedings of the 12th International Conference on Availability, Reliability and Security, Reggio Calabria, Italy, 29 August–1 September 2017; ACM: New York, NY, USA, 2017; p. 29. [Google Scholar]
- Bulusu, S.T.; Laborde, R.; Wazan, A.S.; Barrère, F.; Benzekri, A. Applying a Requirement Engineering Based Approach to Evaluate the Security Requirements Engineering Methodologies. In Proceedings of the ACM SAC RE 2018, Pau, France, 9–13 April 2018. [Google Scholar]
- Bulusu, S.T.; Laborde, R.; Wazan, A.S.; Barrère, F.; Benzekri, A. A Requirements Engineering-Based Approach for Evaluating Security Requirements Engineering Methodologies. In Information Technology-New Generations; Springer: Berlin/Heidelberg, Germany, 2018; pp. 517–525. [Google Scholar]
- Dalpiaz, F.; Paja, E.; Giorgini, P. Security Requirements Engineering: Designing Secure Socio-Technical Systems; MIT Press: Cambridge, MA, USA, 2016. [Google Scholar]
- Van Lamsweerde, A. Requirements Engineering: From System Goals to UML Models to Software Specifications; Wiley: Hoboken, NJ, USA, 2009. [Google Scholar]
- Hatebur, D.; Heisel, M.; Schmidt, H. A pattern system for security requirements engineering. In Proceedings of the 2011 Sixth International Conference on the Availability, Reliability and Security (ARES), Vienna, Austria, 22–26 August 2011; IEEE: Piscataway, NJ, USA, 2007; pp. 356–365. [Google Scholar]
- Karpati, P.; Sindre, G.; Opdahl, A.L. Characterising and analysing security requirements modelling initiatives. In Proceedings of the 2011 Sixth International Conference on Availability, Reliability and Security (ARES), Vienna, Austria, 10–13 April 2007; IEEE: Piscataway, NJ, USA, 2011; pp. 710–715. [Google Scholar]
- Khwaja, A.A.; Urban, J.E. A synthesis of evaluation criteria for software specifications and specification techniques. Int. J. Softw. Eng. Knowl. Eng. 2002, 12, 581–599. [Google Scholar] [CrossRef]
- Mayer, N. Model-Based Management of Information System Security Risk; University of Namur: Namur, Belgium, 2009. [Google Scholar]
- Fabian, B.; Gürses, S.; Heisel, M.; Santen, T.; Schmidt, H. A comparison of security requirements engineering methods. Requir. Eng. 2010, 15, 7–40. [Google Scholar] [CrossRef]
- Rannenberg, K.; Pfitzmann, A.; Müller, G. IT security and multilateral security. Multilater. Secur. Commun. Technol. Infrastruct. Econ. 1999, 3, 21–29. [Google Scholar]
- Muñante, D.; Chiprianov, V.; Gallon, L.; Aniorté, P. A review of security requirements engineering methods with respect to risk analysis and model-driven engineering. In Proceedings of the International Conference on Availability, Reliability, and Security, Fribourg, Switzerland, 8–12 September 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 79–93. [Google Scholar]
- van Lamsweerde, A. Elaborating security requirements by construction of intentional anti-models. In Proceedings of the ICSE 2004: 26th International Conference on Software Engineering, Washington, DC, USA, 23–28 May 2004; pp. 148–157. [Google Scholar]
- Elahi, G.; Yu, E. A goal oriented approach for modeling and analyzing security trade-offs. In Proceedings of the International Conference on Conceptual Modeling, Auckland, New Zealand, 5–9 November 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 375–390. [Google Scholar]
- Souag, A.; Mazo, R.; Salinesi, C.; Comyn-Wattiau, I. Reusable knowledge in security requirements engineering: A systematic mapping study. Requir. Eng. 2015, 21, 1–33. [Google Scholar] [CrossRef]
- Uzunov, A.V.; Fernandez, E.B.; Falkner, K. Engineering Security into Distributed Systems: A Survey of Methodologies. J. Ucs 2012, 18, 2920–3006. [Google Scholar]
- Mellado, D.; Blanco, C.; Sánchez, L.E.; Fernández-Medina, E. A systematic review of security requirements engineering. Comput. Stand. Interfaces 2010, 32, 153–165. [Google Scholar] [CrossRef]
- IEEE 830 IEEE 830-1998—IEEE Recommended Practice for Software Requirements Specifications. Available online: https://standards.ieee.org/findstds/standard/830-1998.html (accessed on 27 May 2016).
- Mead, N.R. How to Compare the Security Quality Requirements Engineering (SQUARE) Method with Other Methods. DTIC Document. 2007. Available online: https://resources.sei.cmu.edu/library/asset-view.cfm?assetid=8257 (accessed on 12 July 2021).
- Nhlabatsi, A.; Nuseibeh, B.; Yu, Y. Security requirements engineering for evolving software systems: A survey. In Security-Aware Systems Applications and Software Development Methods; IGI Global: Hershey, PA, USA, 2012; pp. 108–128. [Google Scholar]
- Niazi, M.; Saeed, A.M.; Alshayeb, M.; Mahmood, S.; Zafar, S. A maturity model for secure requirements engineering. Comput. Secur. 2020, 95, 101852. [Google Scholar] [CrossRef]
- Sommerville, I.; Sawyer, P. Requirements Engineering: A Good Practice Guide; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 1997. [Google Scholar]
- ISO29148:2011 ISO/IEC/IEEE 29148:2011 Systems and Software Engineering—Life Cycle Processes—Requirements Engineering. Available online: https://www.iso.org/standard/45171.html (accessed on 12 July 2021).
- ISO, I. ISO/IEC 15408-1:2009 Information technology—Security techniques—Evaluation criteria for IT security—Part 1: Introduction and general model. Int. Organ. Stand. 2009. Available online: https://standards.iso.org/ittf/PubliclyAvailableStandards/c050341_ISO_IEC_15408-1_2009.zip (accessed on 12 July 2021).
- Kotonya, G.; Sommerville, I. Requirements engineering with viewpoints. Softw. Eng. J. 1996, 11, 5–18. [Google Scholar] [CrossRef] [Green Version]
- Firesmith, D. Common Requirements Problems, Their Negative Consequences, and the Industry Best Practices to Help Solve Them. J. Object Technol. 2007, 6, 17–33. [Google Scholar] [CrossRef]
- Firesmith, D. Specifying good requirements. J. Object Technol. 2003, 2, 77–87. [Google Scholar] [CrossRef] [Green Version]
- Christian, T. Security Requirements Reusability and the SQUARE Methodology; Carnegie-Mellon Univ Pittsburgh Pa Software Engineering Inst: Fairfax County, VA, USA, 2010. [Google Scholar]
- Van Lamsweerde, A.; Brohez, S.; De Landtsheer, R.; Janssens, D. From system goals to intruder anti-goals: Attack generation and resolution for security requirements engineering. Proc. RHAS 2003, 3, 49–56. [Google Scholar]
- Anderson, R.J. Security Engineering: A Guide to Building Dependable Distributed Systems; John Wiley & Sons: Hoboken, NJ, USA, 2010; ISBN 978-1-118-00836-2. [Google Scholar]
- Mar, B.W. Requirements for development of software requirements. In Proceedings of the INCOSE International Symposium; Wiley Online Library: Hoboken, NJ, USA, 1994; Volume 4, pp. 34–39. [Google Scholar]
- Wiegers, K.E. Writing quality requirements. Softw. Dev. 1999, 7, 44–48. [Google Scholar]
- Wieringa, R.J. Requirements Engineering: Frameworks for Understanding; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 1996. [Google Scholar]
- Boehm, B.W. Verifying and validating software requirements and design specifications. IEEE Softw. 1984, 1, 75. [Google Scholar] [CrossRef]
- Pfleeger, S.L.; Atlee, J.M. Software Engineering: Theory and Practice; Pearson Education India, 1998; Available online: https://www.pearson.com/us/higher-education/program/Pfleeger-Software-Engineering-Theory-and-Practice-4th-Edition/PGM58925.html (accessed on 11 July 2021).
- Davis, A.; Overmyer, S.; Jordan, K.; Caruso, J.; Dandashi, F.; Dinh, A.; Kincaid, G.; Ledeboer, G.; Reynolds, P.; Sitaram, P. Identifying and measuring quality in a software requirements specification. In Proceedings of the 1st International Software Metrics Symposium, Baltimore, MD, USA, 21–22 May 1993; IEEE: Piscataway, NJ, USA, 1993; pp. 141–152. [Google Scholar]
- Young, R.R. The Requirements Engineering Handbook; Artech House: Norwood, MA, USA, 2004. [Google Scholar]
- Hull, E.; Jackson, K.; Dick, J. Requirements Engineering; Springer Science & Business Media: Berlin, Germany, 2010; ISBN 978-1-84996-405-0. [Google Scholar]
- Kar, P.; Bailey, M. Requirements Management Working Group: Characteristics of Good Requirements. In Proceedings of the INCOSE International Symposium, Boston, MA, USA, 7–11 July 1996; Wiley Online Library: Hoboken, NJ, USA, 1996; Volume 6, pp. 1225–1233. [Google Scholar]
- Zielczynski, P. Requirements Management Using IBM Rational RequisitePro; IBM Press/Pearson plc: Indianapolis, IN, USA, 2008. [Google Scholar]
- Mannion, M.; Keepence, B. SMART requirements. ACM Sigsoft Softw. Eng. Notes 1995, 20, 42–47. [Google Scholar] [CrossRef]
- IEEE 1233—Guide for Developing System Requirements Specifications. 1998. Available online: https://ieeexplore.ieee.org/document/741940 (accessed on 12 July 2021).
- NetworkX developers NetworkX 2.1 Python Package. Available online: https://networkx.github.io/documentation/stable/# (accessed on 21 June 2016).
- Gephi.org Gephi 0.9.2—The Open Graph Viz Platform. Available online: https://gephi.org/ (accessed on 21 June 2016).
- Ahmad, S. Measuring the Effectiveness of Negotiation in Software Requirements Engineering; University of Western Australia: Crawley, WA, Australia, 2012. [Google Scholar]
- David Lynas SABSA Foundation Courses Training—David Lynas Consulting Limited. Available online: https://www.sabsacourses.com/course-schedule/ (accessed on 7 September 2018).
- Stevens, S.S. On the Theory of Scales of Measurement. Science 1946, 103, 677–680. [Google Scholar] [CrossRef] [PubMed]
- Respect-IT KAOS Tool—Objectiver: HomePage. Available online: http://www.objectiver.com/index.php?id=25 (accessed on 11 July 2021).
- Kletz, T.A. HAZOP and HAZAN: Identifying and Assessing Process Industry Hazards; IChemE: Boca Raton, FL, USA, 1999. [Google Scholar]
- Laborde, R.; Bulusu, S.T.; Wazan, A.S.; Barrère, F.; Benzekri, A. Logic-based methodology to help security architects in eliciting high-level network security requirements. In Proceedings of the 34th ACM/SIGAPP Symposium on Applied Computing, Limassol, Cyprus, 8–12 April 2019; pp. 1610–1619. [Google Scholar]


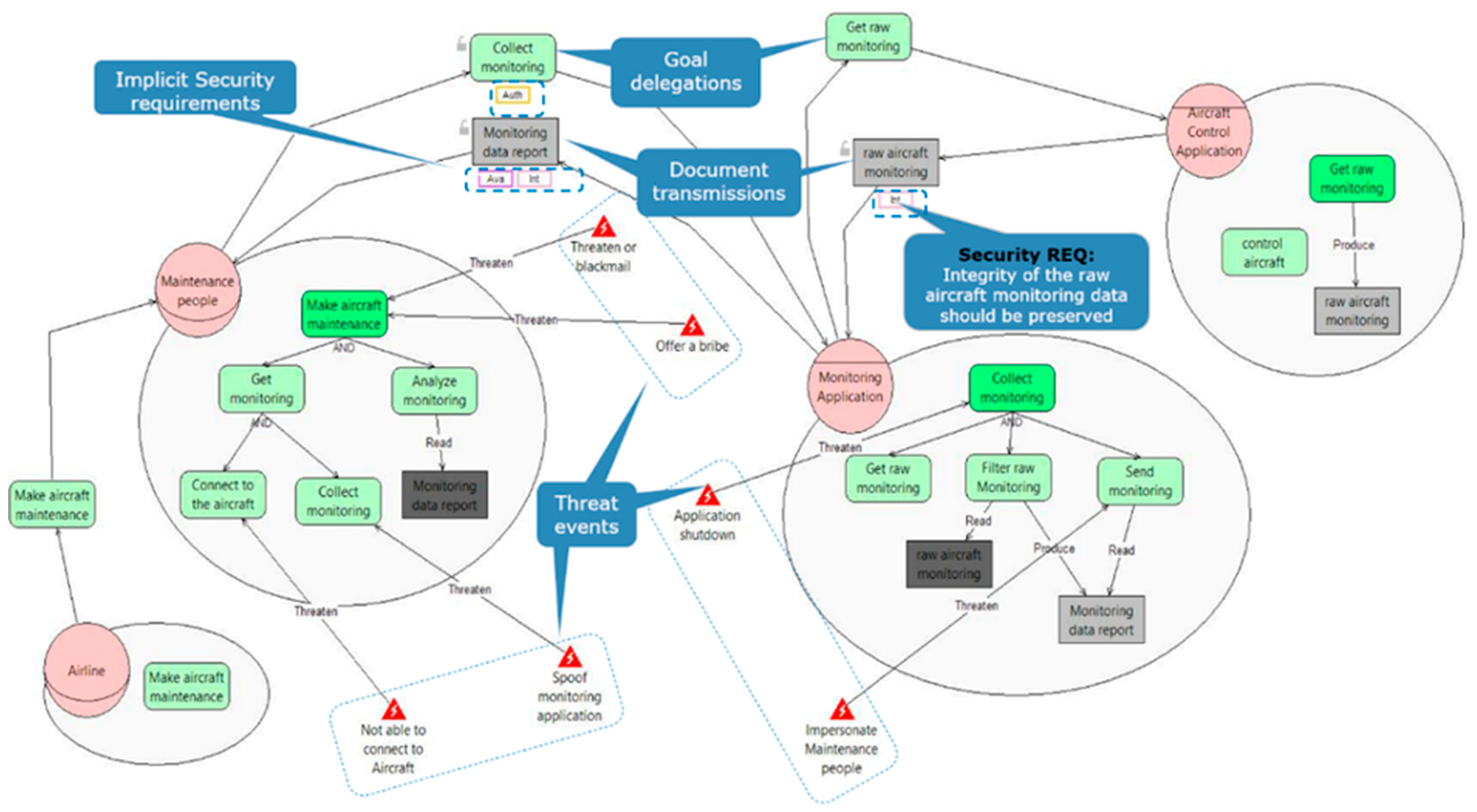
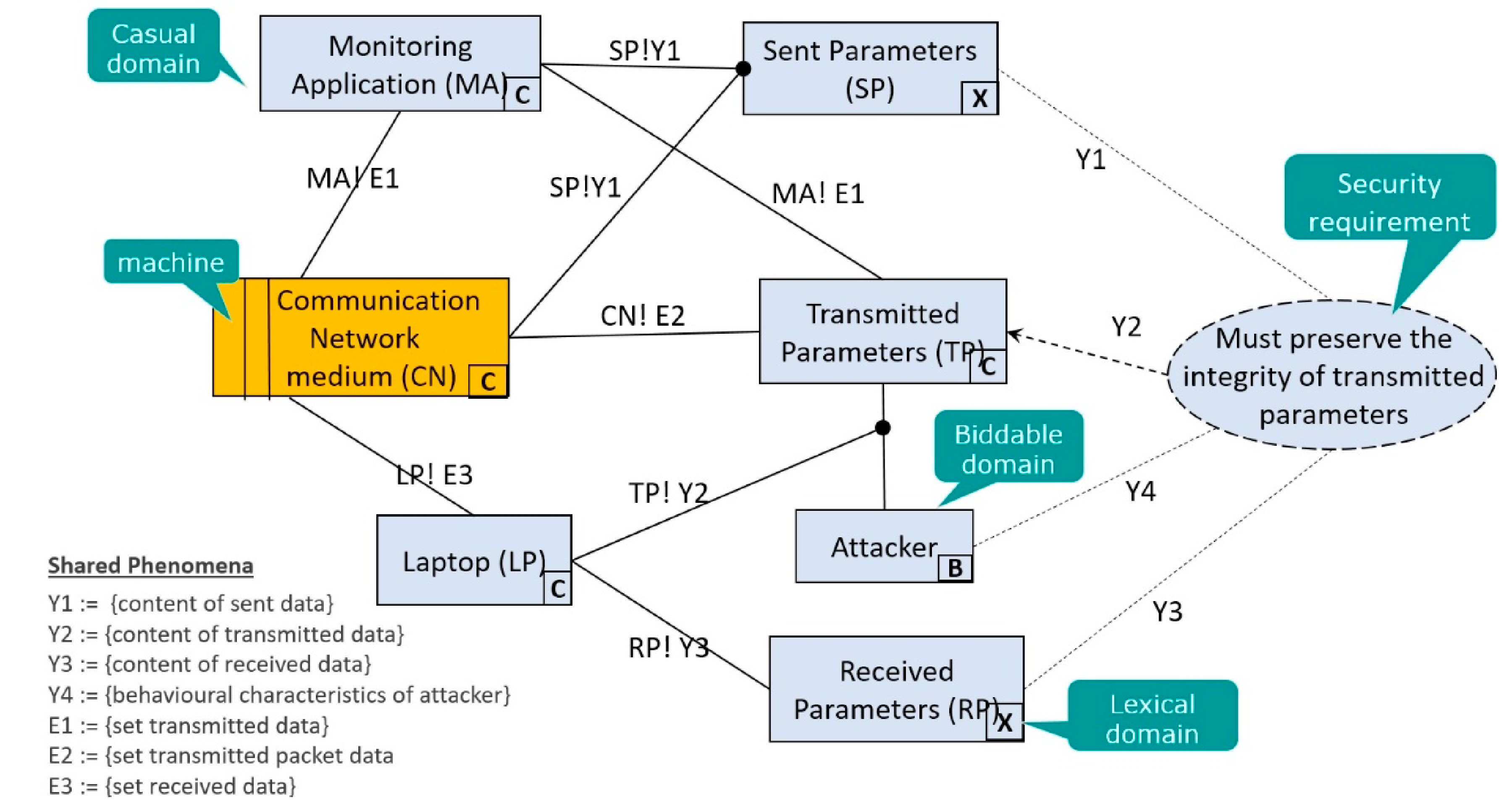
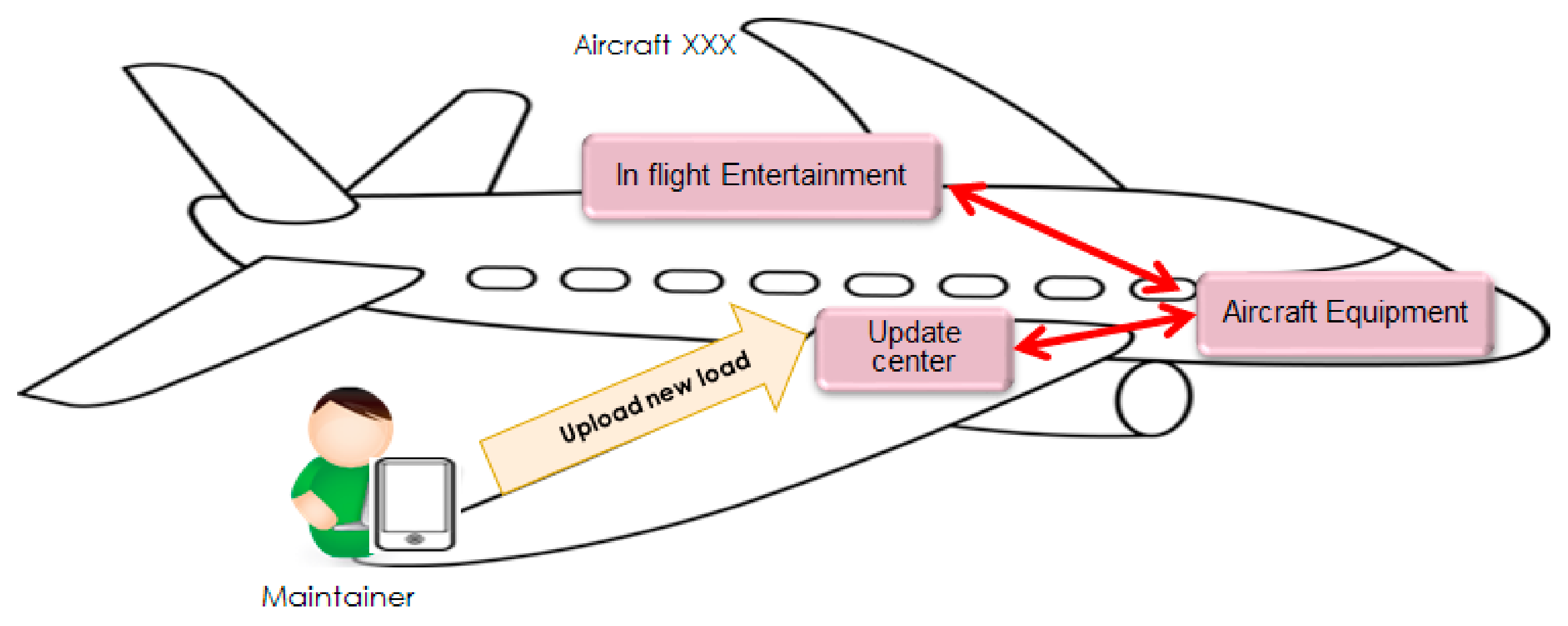

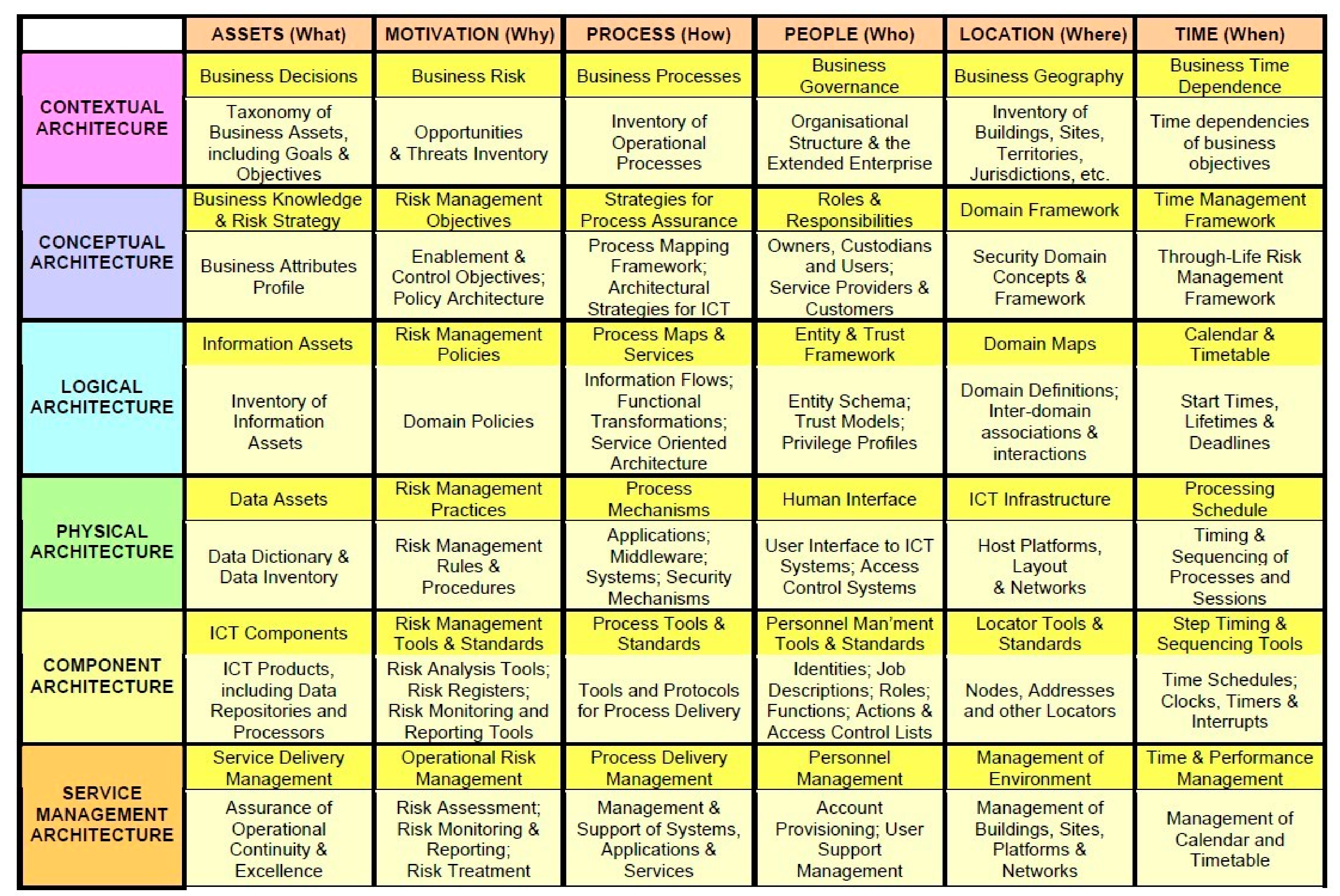
| Source Identifier | Source Name | Number of Criteria Proposed in the Source |
|---|---|---|
| 1 | ISO 29148:2011 [35] | 13 |
| 2 | Van Lamsweerde 2009 [17] | 11 |
| 3 | Firesmith 2003 [39] | 15 |
| 4 | Wiegers 1999 [44] | 10 |
| 5 | Wieringa 1996 [45] | 7 |
| 6 | Boehm 1984 [46] | 5 |
| 7 | Pfleeger and Atlee 1998 [47] | 8 |
| 8 | IEEE 830 1998 [30] | 9 |
| 9 | Davis et al. 1993 [48] | 20 |
| 10 | Mar 1994 [43] | 13 |
| 11 | Sommerville and Sawyer 1997 [34] | 7 |
| 12 | Young 2004 [49] | 15 |
| 13 | Hull et al. 2010 [50] | 15 |
| 14 | Kar and Bailey 1996 [51] | 10 |
| 15 | Zielczynski 2008 [52] | 13 |
| 16 | Mannion and Keepence 1995 [53] | 5 |
| 17 | IEEE 12333:1998 [54] | 9 |
| Total | 185 | |
| No | Abstract Criterion Definition | Characteristics of Good Security Requirements | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| S1 | S2 | S3 | S4 | S5 | S6 | S7 | S8 | S9 | S10 | S11 | S12 | S13 | S14 | S15 | S16 | S17 | ||||
| ISO29148 | Lamsweerde | Firesmith | KE Wiegers | Wieringa | Boehm | Pfleeger and Atlee | IEEE830 | Davis | Brain Mar | Sommerville | R R Young | Hull et al. | Karl et bailey | Peter | Mannion | IEEE 12333 | Credibility | Applicability | ||
| C1 | Should include all the needs of all the stakeholders | Complete | Complete | Complete | Complete | Complete | Complete | Complete | Complete | Complete | Complete | Complete | Complete | Complete | Complete | Complete | -- | Complete | High | All |
| C2 | Compatible, non-contradictory requirements | Consistent | Consistent | Consistent | Consistent | Consistent | Consistent | Consistent | Consistent | Consistent | Consistent | Consistent | Consistent | Consistent | Consistent | Consistent | -- | Consistent | High | All |
| C3 | Accomplishable within given financial, time, legal, technological constraints | Feasible/Affordable | Feasible | Feasible | Feasible | Feasible | Feasible | Feasible | -- | Achievable | Feasible | Realism | feasible | feasible/legal | Attainable | feasible/realistic/possible | Attainable/realisable | -- | High | All |
| C4 | Requirements must be well documented | -- | Good structuring | -- | -- | -- | -- | -- | -- | organized | -- | -- | -- | -- | -- | -- | -- | configurable | low | All |
| C5 | Requirements should be able to refer back to its objective. Dependency or reference links between requirements should be explicity defined. | Traceable | Traceable | Cohesiveness | Traceable | Maintainable/ traceable | Traceable | Traceable | Traceable | Traceable /cross-referenced | Traceable | Traceable | Traceable/Allocated | Satisfied/Qualified/ Modular | -- | -- | Traceable | Traceable/Linked set | High | All |
| C6 | Requirements should state what is needed but not how they are met | Implementation Free | -- | External Observability | -- | Truth/Implementaion independence/Validity | -- | -- | -- | Design independent | Minimality/Right level of detail | -- | Design Independent | Abstract | Implementation Free | independent /Implementation Free | specific/appropriate level of detail | Abstract/Normalized/granular | Medium | All |
| C7 | Documented requirements must be easily adaptable to new changes | -- | Modifiable | -- | Modifiable | Maintainable/Modifiable | -- | -- | Modifiable | Modifiable | Maintainable/Modifiable | Adaptability | -- | -- | -- | -- | -- | Modifiable | Medium | All |
| C8 | No redundant requirements | -- | -- | -- | -- | -- | -- | -- | -- | Non-redundant | -- | -- | Non-redundant | Non-redundant | -- | Non-redundant | -- | -- | low | All |
| C9 | Every requirement is uniquely identified (i.e., number, name tag) | identification | -- | Identification | -- | -- | -- | -- | -- | -- | -- | -- | Unique | Unique | Identification | -- | -- | Unique set | low | All |
| C10 | Stakeholders needs are sufficienly expressed | -- | Adequacy | Validatability | -- | -- | -- | -- | -- | -- | -- | Validity | -- | -- | -- | -- | -- | -- | Medium | Each |
| C11 | Requirements defined are simple, using common terminology and non-technical jargon. | -- | Comprehensibility | Customer/User Orientation/Usability | -- | Understandable | -- | -- | -- | Understandable/ Concise | Simple | Comprehensibility | Concise/simple | Clear/precise | Understandable/minimal/ Concise | Concise/simple/precise | -- | -- | Medium | Each |
| C12 | Requirement statement must lead only one possible interpretation in common | Unambiguous | Unambiguous | Lack of Ambiguity | Unambiguous | Unambiguous Communicability | -- | Unambiguous | Unambiguous | Unambiguous | Unambiguous | -- | Unambiguous | -- | Unambiguous | Unambiguous | -- | Unambiguous | High | Each |
| C13 | Requirements defined allows evaluation - quantifiable values | -- | Measurable | -- | -- | -- | -- | -- | -- | Precise | -- | -- | -- | -- | -- | -- | Measurable | low | Each | |
| C14 | Every requirement has a purpose | Necessary/Bounded | Pertinence | Mandatory/Relevance | Necessary | -- | -- | Relevant | -- | -- | Necessary | -- | Necessary | -- | Necessary | Necessary | -- | Bounded | Medium | Each |
| C15 | Requirement should accurately represent the facts and needs. Syntactically and semantically | -- | -- | Correctness/Currency | Correct | -- | -- | Correct | Correct | Correct | Correct | -- | Correct | -- | -- | Understandable/Correct | -- | -- | Medium | Each |
| C16 | Non conjunctive requirements | Singular | -- | -- | -- | -- | -- | -- | -- | -- | -- | Atomic | -- | Atomic | -- | -- | low | Each | ||
| C17 | Should define some means to prove the compliance or satisfaction of requirement with stakeholder needs, standards and constraints. | Verifiable | -- | Verifiability | Verifiable | Verifiable | Testable | Testable | Verifiable | Verifiable | Verifiable/Testable | Verifiability | Verifiable | Verifiable | Verifiable | Verifiable/Testable | -- | Validatable | high | Each |
| C18 | Formulation of Requirement statements must follow specific criteria | Requirement language criteria/Requirements construct | -- | -- | -- | -- | -- | -- | -- | -- | Formality | -- | Devoid of escape clauses/Standard Construct | -- | Standard construct | -- | -- | -- | low | Each |
| C19 | Requirements must be reusable by numerous stakeholders | -- | -- | -- | -- | -- | -- | -- | -- | reusable | -- | -- | -- | -- | -- | -- | -- | -- | low | Each |
| C20 | Individual requirements should be defined with some attributes or annotations that characterizes them (e.g., assumptions, rationale, risk realted information) | Attributes | -- | Metadata | Prioritized | -- | -- | -- | Ranked for importance/degree of stability | Ranked for importance/Ranked for stability | -- | -- | -- | -- | Suporting characteristics | -- | -- | -- | Medium | Each |
| No | Abstract Definitions | Criterion Names in Use | Questionnaire |
|---|---|---|---|
| C3 | Accomplishable within given financial, time, legal, technical constraints | Feasible, Affordable, Legal, Achievable | ► Is it possible to capture the constraints of security requirements? such as technical? Legal? Time? Financial? [35] ► Does the SRE methodology require training? is it within the project budget? [39] ► Is it possible to learn the SRE methodology notation within the project timelines? [31] |
| C5 | Requirement should be able to refer back to its objective. Dependency or reference links between requirements should be explicitly defined. | Traceable, Cohesiveness, Allocated, Satisfied/Qualified | ► Is it possible to trace the security requirements back to the business needs and vice-versa? [35] ► Is it possible to trace the group of similar requirements e.g., related to a particular abstraction level? [39] |
| C6 | Requirements should state what is needed but not how it is met | Abstract, Design independent, External observability, Implementation free, Right level of detail, Minimality | ► Is it possible to express security requirements without constraining the design solutions? [35] ► Is it possible to respect the abstraction needs of the stakeholders? [43] |
| C10 | Stakeholders needs are sufficiently expressed | Adequacy, Validability | ► Is it possible to capture the individual needs of all the stakeholders involved in the SRE process? [39] ► Is it possible to express the domain environment assumptions and domain constraints for implementing the security requirements? [17] |
| C11 | Requirements are simple using common terminology and non-technical jargon. | Clear, Concise, Comprehensibility, Customer/User Orientation, Communicability | ► Is the SRE modelling notation comprehensible to all the stakeholders involved in the SRE process? [39] ► Is the formulation of security requirements comprehensible to the stakeholders? [17] ► Does it facilitate easy communication of the ideas among the stakeholders involved at different abstraction levels of the SRE process? [45] |
| C20 | Individual requirements should be defined with some attributes or annotations that characterizes them | Attributes, Metadata, Prioritized, Ranked for importance, Degree of stability | ► Is it possible to express implementation costs of the security requirements? [35] ► Is it possible to express the risk attributes pertinent to the security requirements? [35] ► Is it possible to express the priority of the security requirements based on risk impact? [35] |
| RM2.1.1: The SRE-Methodology-to-be modelling language terminology must be easily understood to the user |
| RM2.1.2: The cost of the SRE-Methodology-to-be training must be minimal |
| RM2.1.3: The time taken to learn the SRE-Methodology-to-be must be minimal |
| RM3.1: The SRE-Methodology-to-be must support the need for users to easily communicate ideas and feedback respecting the abstraction needs |
| RM3.2: The SRE-Methodology-to-be must support the need for users to clearly define the number of abstraction levels of refinement |
| RM4.1: The SRE-Methodology-to-be must facilitate the tracing of the network security requirements back to business objectives |
| RM6.1: The SRE-Methodology-to-be must facilitate the specification of network security zone requirements |
| RM6.2: The SRE-Methodology-to-be must allow annotating each requirement with risk attributes |
| RM6.3: The SRE-Methodology-to-be must allow annotating each requirement with priority information |
| RM6.4: The SRE-Methodology-to-be must facilitate the specification of the implementation costs of network security requirements |
| RM6.2: The SRE-Methodology-to-Be Must Allow Annotating Each Requirement with Risk Attributes | Performance Measure |
|---|---|
| The annotation feature is extensible. Requirements can be linked with risk attributes, i.e., asset criticality, risk event, risk likelihood, control strength) | high |
| At least two risk attributes, i.e., risk events and risk likelihood | medium |
| At least one risk attribute, i.e., risk events | low |
| Requirement cannot be annotated with any kind risk information | nil |
| Quality Criteria (Root Goal Nodes) | Elicited Evaluation Criteria List (RM) | STS | Secure KAOS | SEPP |
|---|---|---|---|---|
| Comprehensibility (C11) | RM2.1.1: The SRE methodology modelling language terminology must be easily understood to the user | high | medium | low |
| RM2.1.2: The cost of the SRE methodology training should be minimal | high | medium | low | |
| RM2.1.3: The time taken to learn the SRE methodology should be minimal | high | medium | low | |
| Abstract (C6) | RM3.1: Should support the need for users to easily communicate ideas and feedback respecting the abstraction needs | nil | nil | nil |
| RM3.2: Should support the need for users to clearly define the number of abstraction levels of refinement | nil | nil | nil | |
| Traceability (C4) | RM4.1: The methodology should facilitate to trace the (network) security requirements back to business objectives | medium | high | low |
| Feasibility (C5) Adequacy (C10) Metadata (C20) | RM6.1: Must facilitate to specify and link network security zone information | nil | nil | nil |
| Metadata (C20) | RM6.2: Should annotate each requirement with risk attributes | low | medium | nil |
| Adequacy (C11) Metadata (C20) | RM6.3: Should annotate each requirement with priority information | nil | high | nil |
| Feasibility (C5) Metadata (C20) | RM6.4: Must facilitate to specify the implementation costs of network security requirements | nil | nil | nil |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Laborde, R.; Bulusu, S.T.; Wazan, A.S.; Oglaza, A.; Benzekri, A. A Methodological Approach to Evaluate Security Requirements Engineering Methodologies: Application to the IREHDO2 Project Context. J. Cybersecur. Priv. 2021, 1, 422-452. https://doi.org/10.3390/jcp1030022
Laborde R, Bulusu ST, Wazan AS, Oglaza A, Benzekri A. A Methodological Approach to Evaluate Security Requirements Engineering Methodologies: Application to the IREHDO2 Project Context. Journal of Cybersecurity and Privacy. 2021; 1(3):422-452. https://doi.org/10.3390/jcp1030022
Chicago/Turabian StyleLaborde, Romain, Sravani Teja Bulusu, Ahmad Samer Wazan, Arnaud Oglaza, and Abdelmalek Benzekri. 2021. "A Methodological Approach to Evaluate Security Requirements Engineering Methodologies: Application to the IREHDO2 Project Context" Journal of Cybersecurity and Privacy 1, no. 3: 422-452. https://doi.org/10.3390/jcp1030022
APA StyleLaborde, R., Bulusu, S. T., Wazan, A. S., Oglaza, A., & Benzekri, A. (2021). A Methodological Approach to Evaluate Security Requirements Engineering Methodologies: Application to the IREHDO2 Project Context. Journal of Cybersecurity and Privacy, 1(3), 422-452. https://doi.org/10.3390/jcp1030022






