The rapid advancement of smart cities relies on innovative energy systems that ensure sustainability, resilience and efficiency. Networked Microgrids (NMGs) are the cornerstone in this domain due to their interconnected microgrid clusters that are reliable, efficient and provide operational flexibility [
1]. NMGs utilize Distributed Energy Resources (DERs) such as solar panels, wind turbines, generators, etc., to generate localized energy solutions that align with smart city objectives of reducing carbon footprints and optimizing resource utilization in a highly dynamic urban environment.
Motivation
In smart city energy systems, NMGs often operate in decentralized or hybrid configurations, where individual DERs, such as a solar panel on a resident’s house, contribute power to the local grid, enhancing energy resilience and sustainability. For example, in Copenhagen, Denmark, community-owned solar panels and wind turbines integrate with municipal grids in a hybrid setup, enabling localized power generation that supports the city’s carbon neutrality by 2025 goal (see Copenhagen’s Smart City Energy Plan:
https://urbandevelopmentcph.kk.dk, accessed on 23 October 2025). In such systems, the trustworthiness of each DER is critical to ensure stable operation, as a single faulty or malicious unit (e.g., a compromised solar inverter) can disrupt power supply or compromise grid security. Even in centralized grid configurations, where a state utility may control power input, assessing individual DER trustworthiness ensures reliable contributions, facilitating efficient energy management and fault prevention across the NMG. This motivates the need for a trust evaluation framework capable of processing unstructured DER data, such as SCADA logs, to derive actionable trust metrics for smart city applications.
Moreover, DERs remain vulnerable to tampering whether through physical interference, software exploits or data manipulation even when operated by private power companies or integrated into virtual power plants (VPPs). For instance, in the U.S., the National Renewable Energy Laboratory (NREL) has demonstrated that compromised rooftop solar inverters in residential microgrids can inject false telemetry data or destabilize frequency regulation [
2]. Thus, individual DER trust assessment serves as an essential layer of defense, enabling internal validation within private utilities, resilience in VPPs and overall grid integrity in smart city deployments [
3]. This motivates the need for a trust evaluation framework capable of processing unstructured DER data, such as SCADA logs, to derive actionable trust metrics for smart city applications.
Several trust frameworks tailored for smart grids and microgrids are available in the existing literature; however, most of them rely on structured telemetry data or predefined metrics [
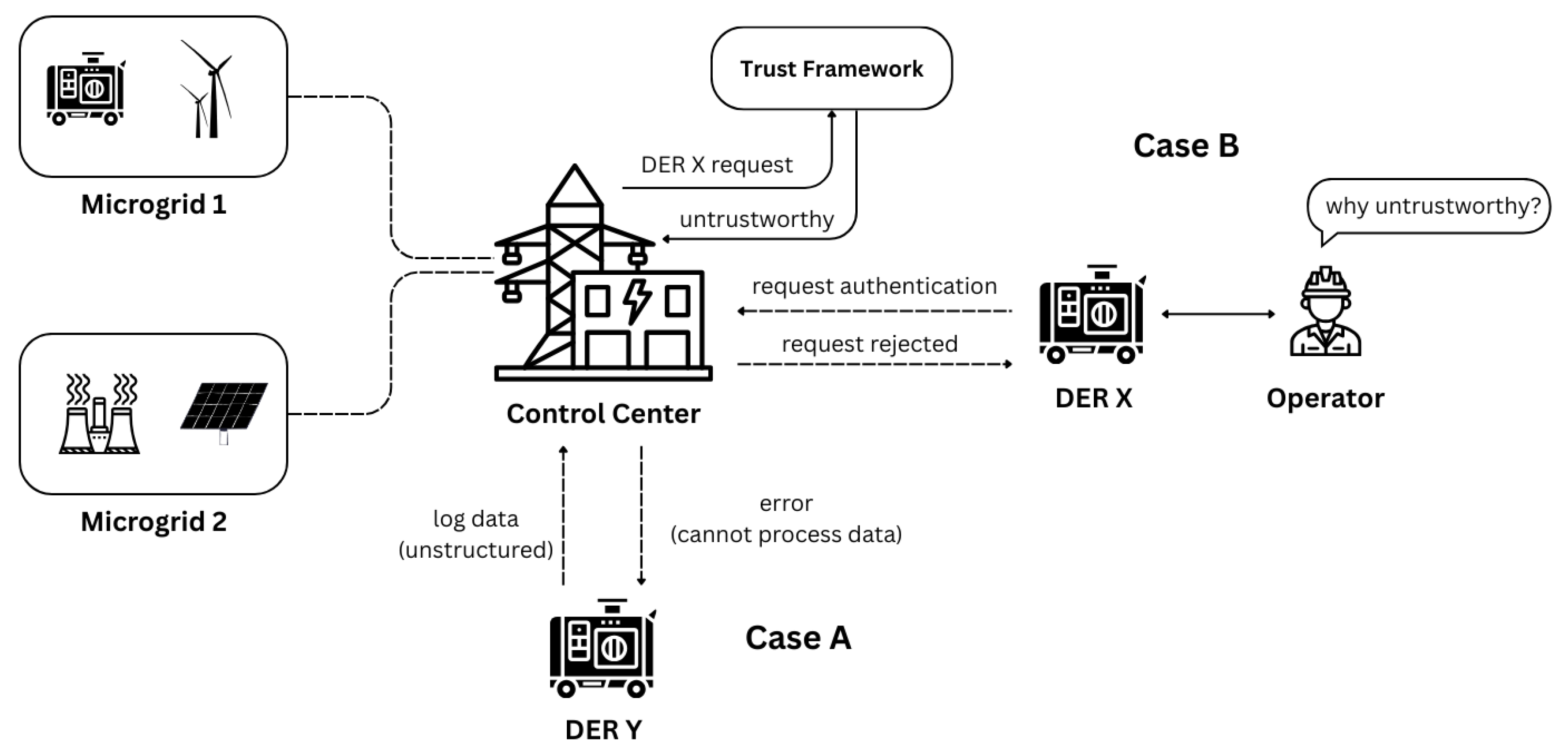
4]. In real-world smart city deployment, DERs often generate unstructured data, including log files, technical reports, status messages and other textual information. This unstructured data contains rich contextual information about DER behavior that mostly remains unexplored due to the limitations of conventional data processing techniques, as illustrated in Case A in
Figure 1. Furthermore, most of the existing trust frameworks lack either explainability or adaptability to dynamically changing trust contexts or are very sensitive to noise in the training data, as shown in Case B in
Figure 1. Consequently, there exists a pressing need for a trust evaluation system that can effectively interpret unstructured data and derive actionable insights from it to support smart city energy infrastructure.
Recent advances in Language Models (LMs) and Neural Networks have demonstrated remarkable success in analyzing unstructured data using techniques like Natural Language Processing (NLP), classification and information extraction [
5]. These techniques provide unique opportunities to reimagine trust assessment methodologies especially in systems like NMGs where non-tabular data is common.
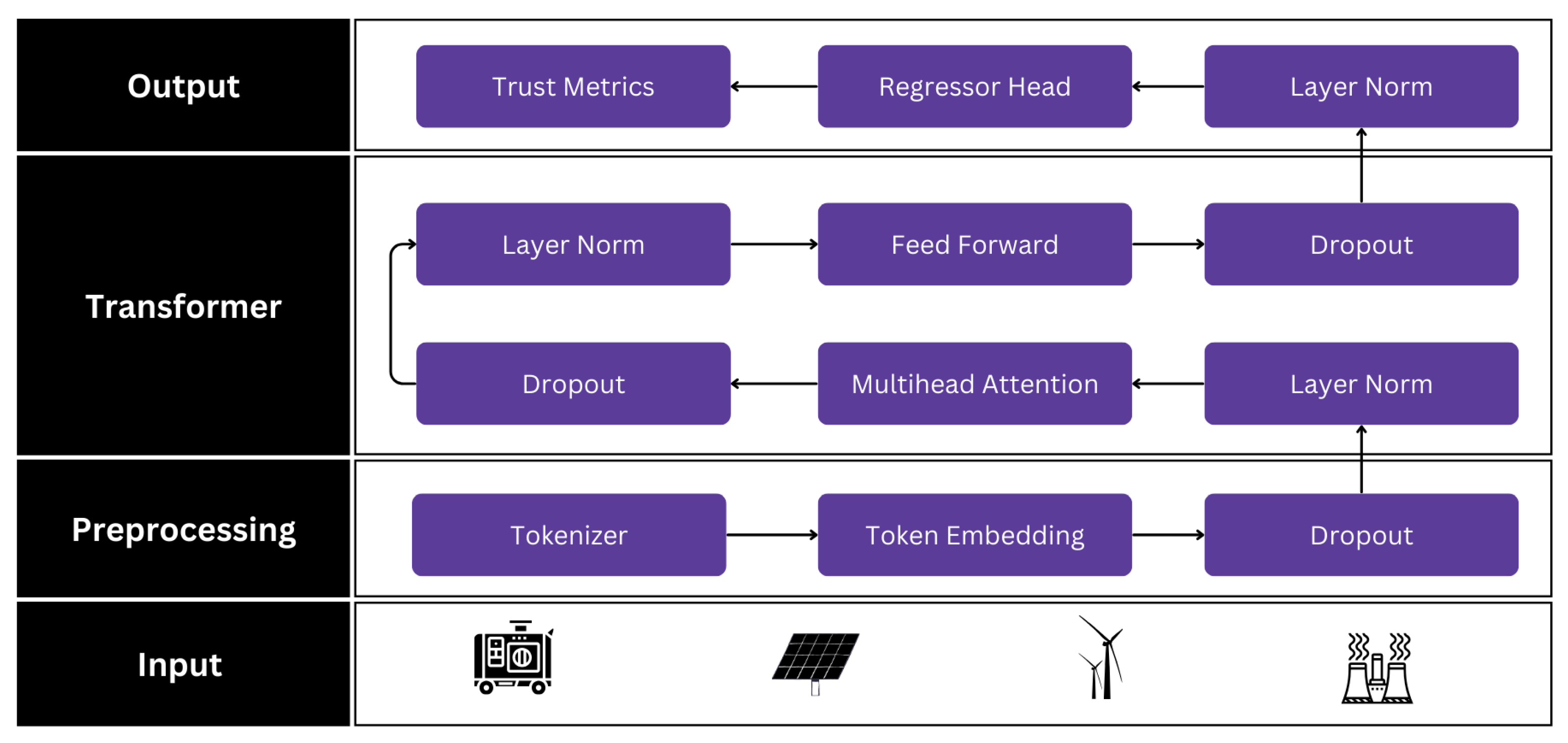
In this research, we propose a novel framework specifically designed for NMGs. The framework comprises two key components:
An SLM module capable of processing unstructured DER data to extract meaningful trust indicators including availability, reliability, productivity, stability and reputation.
A Neural Network-based trust framework that uses these trust indicators to calculate overall trust for the DER and also enhances the interpretability of the model.
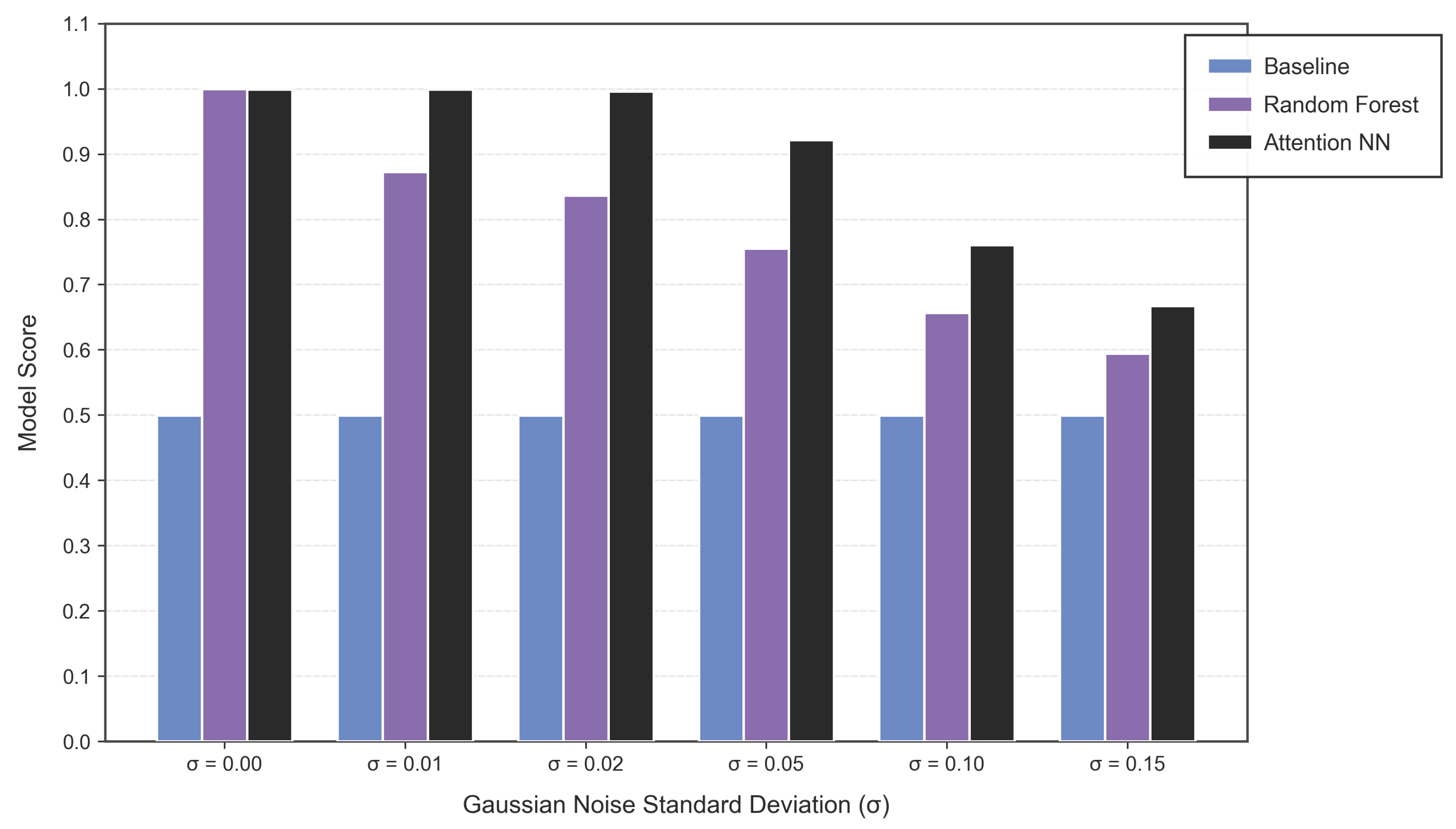
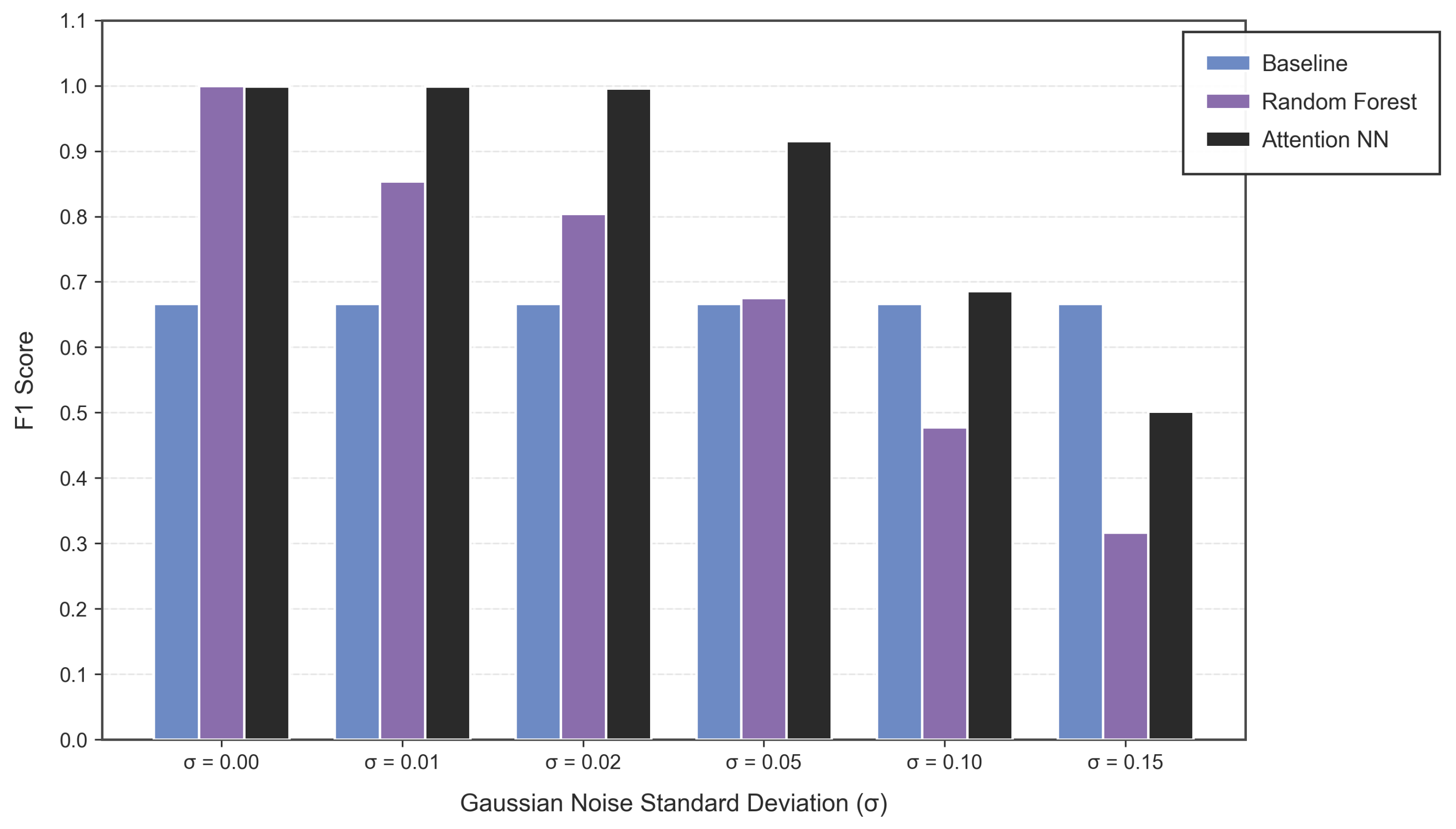
This two-stage architecture bridges the gap between raw DER-generated data and informed decision making at the control center. The SLM ensures contextual extraction while the neural network provides adaptability, interpretability and accuracy in trust assessment. In order to access the effectiveness of the proposed framework, we conducted a series of experiments. The results indicated that our framework achieves a high precision and consistency in trust evaluation, outperforming traditional methods in performance and efficiency. Furthermore, by transforming unstructured data into meaningful metrics, the framework significantly improves interpretability and automation in an NMG environment. The major contributions of this research are listed below:
Design a framework that leverages an SLM for parsing unstructured DER data into key trust attributes like availability, reliability, productivity, stability and reputation.
Develop a neural network-based trust framework that uses extracted indicators to compute precise and adaptive trust scores.
Integrate both intrinsic and extrinsic explainability methods to provide transparency in the model’s decision making process that increases user confidence in AI-driven trust delivery.
The rest of this paper is organized as follows:
Section 2 presents related work in the domain of contextual information extraction and trust assessment.
Section 3 describes the design and architecture of the proposed framework.
Section 4 presents the results and discussion on the experiments conducted to assess the suitability of the proposed framework. Finally,
Section 5 concludes the paper and outlines future research directions.