Threat Modeling and Attacks on Digital Twins of Vehicles: A Systematic Literature Review
Abstract
Highlights
- This paper conducts an in-depth review of 23 studies on threat modeling and security testing in automotive digital twins using the PRISMA framework.
- It identifies deficiencies and proposes improved methodologies to enhance current security and safety validation practices for interconnected automotive systems.
- This paper highlights the need for more advanced threat modeling and emphasizes the importance of improving cybersecurity to prevent potential attacks on connected vehicles.
- It suggests future research and practical strategies for secure digital twin system design in the automotive sector, supporting the development of resilient smart urban environments through a robust interconnected vehicle security framework.
Abstract
1. Introduction
- Clarification of Digital Twin Definitions: The review consolidates different interpretations of digital twins present in existing research, classifying them into physics-based, data-driven, and hybrid models. This differentiation lays the groundwork for the analysis and findings of the review [2,3].
- Overview of Digital Twin Implementations: The review highlights the extensive use of digital twins across various sectors, particularly in automotive applications, stressing the significance of threat modeling within this context and identifying existing platforms that support automotive digital twins [4].
- Identification of Passive Security Testing Techniques: A considerable portion of the review is focused on passive testing techniques within digital twins, offering a thorough examination of security challenges that are unique to passive testing in vehicular systems [5].
- Mitigation Recommendations: Drawing from the findings, the review proposes actions to tackle the identified security issues, such as adopting proactive defense strategies, ensuring data privacy, and following best practices for secure deployment [8].
Methodology of Review
- Databases: The search was carried out in three major academic databases: IEEE Xplore, ACM Digital Library, and ScienceDirect. These databases were selected for their wide coverage of peer-reviewed literature in cybersecurity, digital twin, and automotive systems.
- Keywords: Search queries used Boolean combinations of relevant terms, such as “digital twin”, “cybersecurity”, “smart city”, “vehicular systems”, “automotive”, and “threat modeling”. The complete Boolean query used across databases was as follows:
This formulation is also illustrated in Section 6(“Threat modeling” OR “Security analysis” OR “Vulnerability assessment”) AND (“Digital Twin”) AND (“Vehicle” OR “Automotive”) AND (“Attack” OR “Cyberattack” OR “Cybersecurity” OR “Security threat”) - Timeframe: Publications from January 2015 to February 2024 were considered, with a particular emphasis on works from the last five years (2019–2024) to capture recent developments.
- Inclusion Criteria: Only peer-reviewed journal articles, conference proceedings, authoritative standards (e.g., ISO, NIST) and relevant white papers were included. Exclusion criteria included duplicate entries, non-English papers, non-peer-reviewed publications, and inaccessible full texts.
- Gray Literature: Although gray literature sources (e.g., industrial tools, expert opinions) were briefly reviewed for contextual understanding, they were excluded from the final analysis due to a lack of methodological rigor and relevance to the research questions.
- Classification Process: Selected papers were categorized according to their domain (vehicular, smart city, industrial), architectural layers (physical, communication, application, security) and cybersecurity focus (threat modeling, simulation, validation). An inductive thematic coding approach was applied to extract recurring themes and identify knowledge gaps.
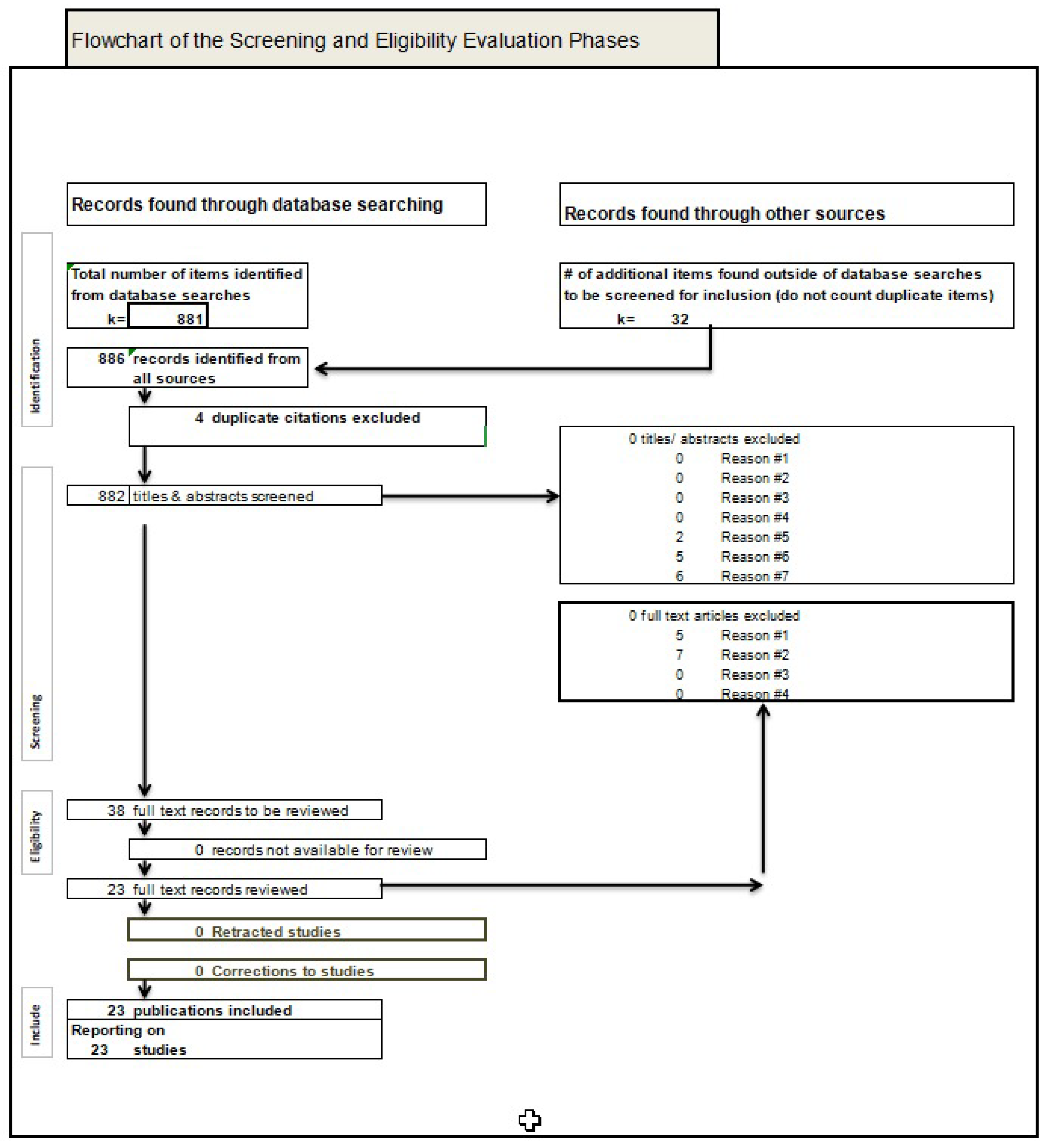
- Selection Summary: An initial pool of 854 publications was reduced to 20 high-quality articles after applying inclusion/exclusion criteria, keyword filtering, abstract screening, snowballing and full-text analysis. Details are presented in Section 6.2.4.
2. In-Vehicle Digital Systems: A Testing Challenge
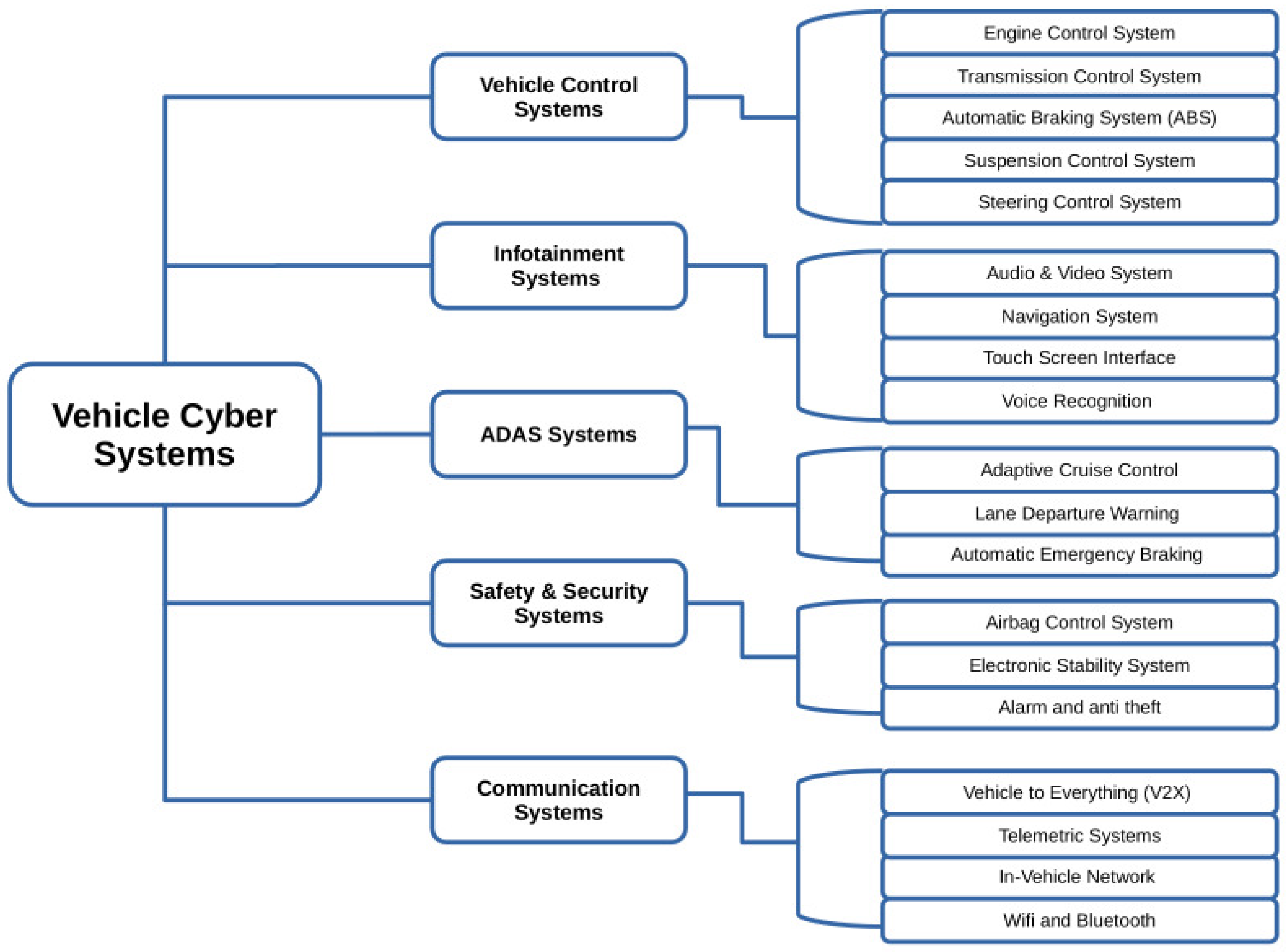
2.1. Defining Vehicular Cyber Systems
2.2. Cybersecurity Testing
- Penetration Testing: This simulates a cyber-attack on the car to find any potential holes and gauge how well the system can fend off threats.
- Fuzz Testing: Sending random data to a vehicle’s systems is known as “fuzz testing”, which aims to find any potential flaws and gauge how the system handles unexpected inputs.
- Code Review: Reviewing the vehicle’s source code to look for any security flaws such as buffer overflows or SQL injection vulnerabilities is known as a “code review”.
- Vulnerability Scanning: Vulnerability scanning entails looking for known weaknesses in vehicle systems using automated technologies.
- Wireless Security Testing: Testing the security of the vehicle’s wireless network, which includes Wi-Fi, Bluetooth, and cellular connections, is known as wireless network security testing.
- Physical Security Testing: Testing the vehicle’s physical security, including its locks, alarms, and anti-theft equipment, is known as physical security testing.
- User interface testing: This examines the safety of the information system and other components of the user interface in the car to find any potential security holes or vulnerabilities.
- Threat modeling: This is the process to identify possible threats and vulnerabilities that the vehicle may encounter and to assess how they may affect vehicle security.
- Hardware-in-the-Loop Testing: This is worth mentioning because it is a similar step of digital twin testing. ECU’s that manage different vehicular operations, including cybersecurity-related systems, are tested using a technique called hardware in the loop (HIL). HIL testing is crucial for ensuring that vehicle’s cybersecurity systems work properly and can detect and respond to cyberattacks in the context of automotive cybersecurity. HIL testing involves coupling the ECU to a simulation environment that resembles the actual driving environment in which the car will function [9]. The ECU can interact with the simulated vehicle environment in the same way as in the actual world thanks to a variety of inputs that can be included in this simulation environment, including sensors, actuators, and communication networks [9]. HIL testing is particularly crucial in the domain of automotive cybersecurity for testing the cybersecurity systems created to recognize and react to cyberattacks. Firewalls, intrusion detection systems, and other security measures might be a part of these systems. HIL testing can assist in locating any flaws or vulnerabilities in the cybersecurity systems and ensuring that they are operating properly by simulating actual cyber-attacks on the vehicle’s systems.
2.3. Role of Standards: UNECE R155 and Digital Twin Security Protocols
- Simulating CSMS audit trails to meet Article 6.2 of R155 [14].
- Validating secure software update mechanisms and over-the-air (OTA) protocols, as required by Annex 5. of Article 6.
- Testing and monitoring detection mechanisms across all R155-defined threat categories, including emerging threats.
- Enabling continuous vulnerability assessment and incident response, in alignment with Article 7.
- Modeling supply chain risks and third-party components, fulfilling the expectations of Annex 8 of Article 7.
| UNECE R155 Ref. [14] | Requirement | DT Application | Example | RQ Alignment |
|---|---|---|---|---|
| Article 6.2 | CSMS Audits | Simulate ECU integrity checks | Tampering detection | RQ3: Attack simulation |
| Annex 5 | Secure Updates | Validate OTA protocols | Secure software updates | RQ3: Attack simulation |
| Article 7 | Continuous Monitoring | Real-time threat detection and vulnerability management | CAN-Bus spoofing detection | RQ1: Threat identification |
| Annex 8 | Supply Chain Risk Assessment | Model third-party and V2X vulnerabilities | STRIDE analysis for supplier components | RQ2: Threat modeling |
3. Digital Twin: A New Era of Automotive Security Testing
3.1. Definition of Digital Twin
- Simulation-Based Digital Twins: These digital twins simulate a physical system or process’s behavior, functionality, and interactions using physics-based models. They can be used to forecast how a physical system or process will operate under various circumstances [23].
- Data-driven Digital Twin: To predict the behavior and effectiveness of a physical system or process, digital twin evaluate and interpret real-time data from sensors and other data sources using data analytics and machine learning methods. They can be applied to process optimization, quality assurance, and predictive maintenance.
- Hybrid Digital Twin: Hybrid digital twins combine the advantages of simulation-based and data-driven digital twins to precisely and fully capture a physical system or process [24]. In addition to simulating complex, multi-domain systems and processes, they can be used to merge various types of data and models.
- Analytical-Digital Twin: These types of digital twins assess and improve the functionality and behaviors of a physical system or process using mathematical models and algorithms. In complex systems, they can be applied for decision-making, control, and optimization [25].
- Control-Based Digital Twin: The behavior and efficiency of a physical system or process are regulated and optimized by these digital twins via real-time feedback control and monitoring [26]. They can be applied to the closed-loop optimization and control of dynamic systems.
3.2. Digital Twin: A Transformation of Automotive Systems
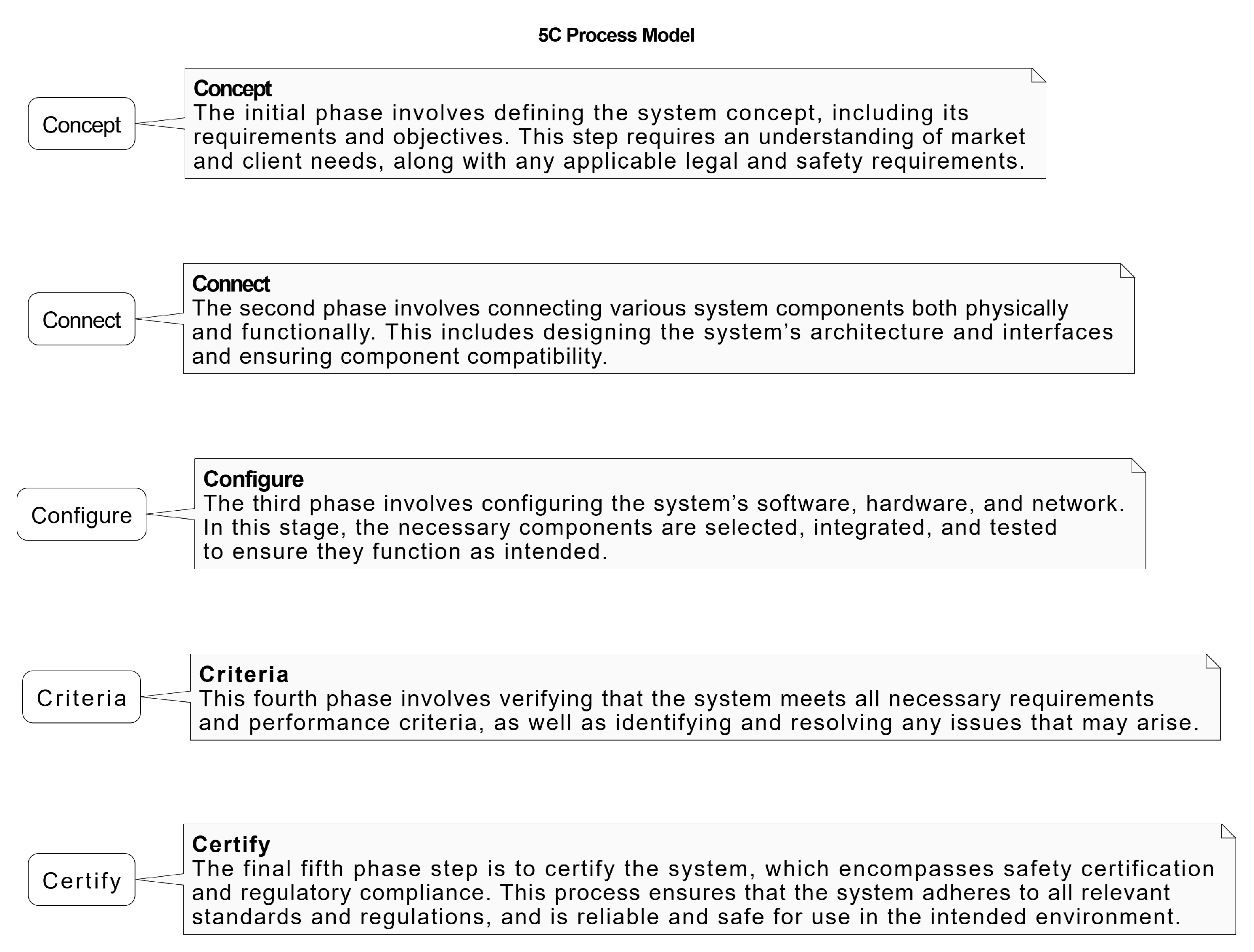
- Concept: In the context of digital twin in automotive security testing, the idea phase comprises establishing the goals and parameters of the digital twin model, identifying possible security threats and vulnerabilities, and formulating a plan to mitigate them [4,31]. One could think of this phase as threat modeling.
- Configure: During the setup stage, the digital twin model is altered to replicate various security situations and possible cyberattacks. To do this, it may be necessary to modify the digital twin model’s properties to account for different system configurations and security settings [3].
- Validation: The accuracy and effectiveness of the digital twin in detecting and blocking security threats are tested. This may involve simulating different security situations and comparing the results with empirical data to ensure that the model accurately depicts the behavior of the real system [34,35].
- Physical Layer: The vehicle’s physical components, including the engine, gearbox, brakes, and other mechanical components, are a part of the physical layer. The installation of sensors and other monitoring devices on the physical system would be required for this layer in order to gather real-time data [37] about the vehicle in the context of a vehicular digital twin for security testing and attack simulation [38,39].
- Communication Layer: The communication layer comprises the interfaces and protocols that allow different components of the automotive system to communicate with one another [40]. In order to facilitate real-time monitoring and testing for attack simulation and security testing, this layer would use the twin model in conjunction with the physical layer [41].
- Application Layer: This layer consists of the software applications and services that run on top of the communication layer. To verify the security of the vehicle system, this layer would involve creating a digital twin model and a variety of attack scenarios [42].
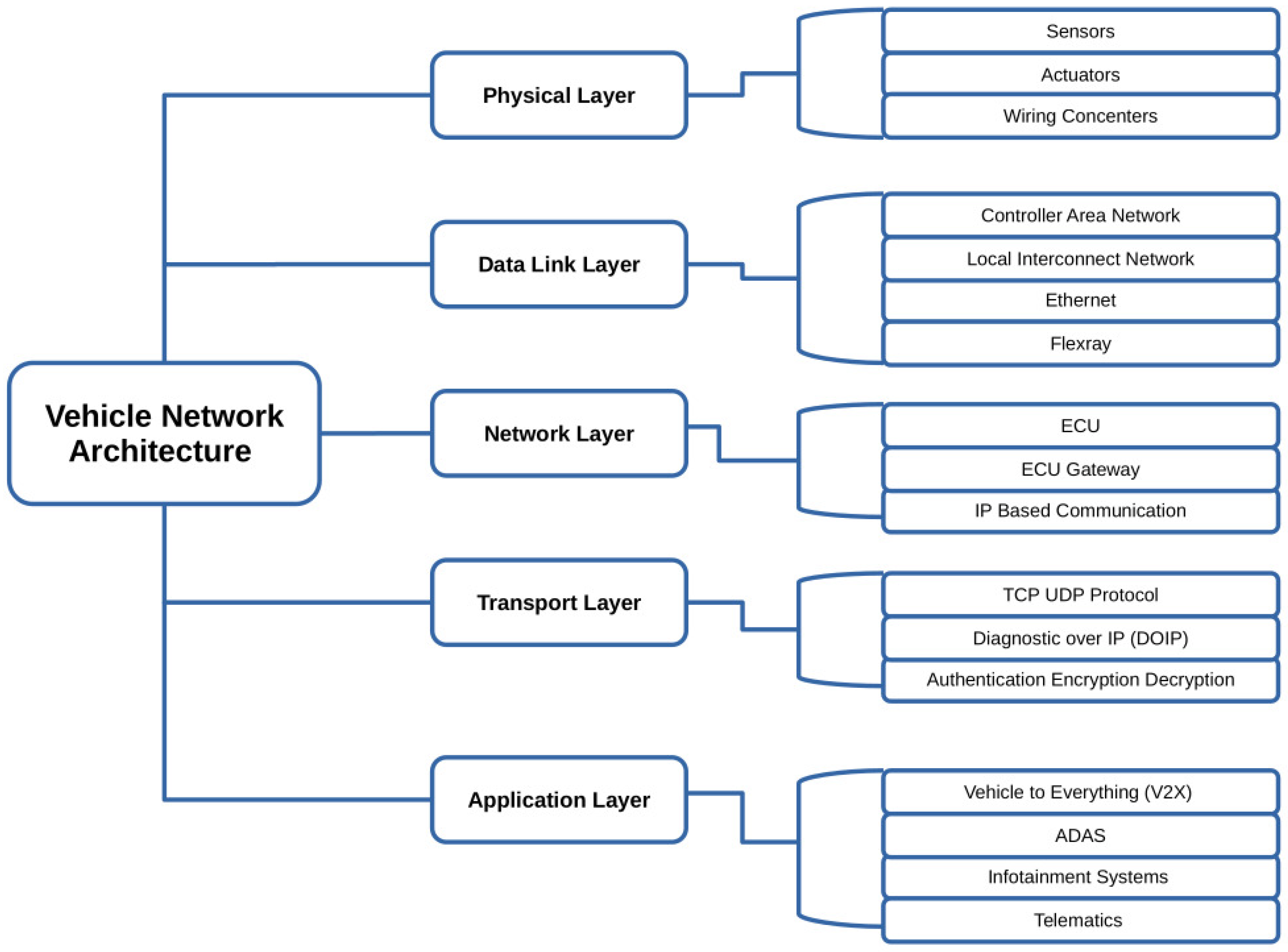
Linking 5C Taxonomy and Layered Architecture to DT Security Testing
4. Definitions of Terminologies
5. Related Systematic Reviews
6. Systematic Literature Review Methodology
6.1. Defining the Scope: Research Questions and Objectives
6.1.1. RQ1: How to Identify and Assess Threats to Automotive Digital Twin?
6.1.2. RQ2: What Are the Current Methodologies Used for Threat Modeling in the Context of Digital Twins of Vehicles?
6.1.3. RQ3: What Are the Most Effective Methods for Validating Threat Models and Assessing Attacks on Digital Twins of Vehicles?
6.2. Review Protocol
6.2.1. Digital Databases
6.2.2. Search Stings
6.2.3. Criteria for Selection
- Inclusion Criteria:
- Include papers that show work on security aspects in automotives.
- The digital twin, namely in the automotive sector, should be the main topic of the paper.
- Articles that are focused on firmware and methodologies.
- Exclusion Criteria:
- Papers that are not fully accessible.
- Non-published, non-peer reviewed.
- Papers that do not have proper methods or are not verified with valid scientific methodology.
6.2.4. Gray Literature
7. Findings
7.1. Results After Query Execution
7.2. Research Question 1: How to Identify and Assess Threats to Automotive Digital Twin?
- Cyber Systems;
- Electrical and Electronic Systems;
- Autonomous Systems.
7.2.1. Cyber Systems: Vulnerabilities and Attack Vectors
7.2.2. Electrical and Electronic Systems
7.2.3. Autonomous Systems
7.2.4. Summary
7.3. Research Question 2: What Are the Current Methodologies Used for Threat Modeling in the Context of Digital Twins of Vehicles?
- Data analysis approach
- System analysis approach
- Threat identification approach
7.3.1. Data Analysis Approach
- Hackers and attackers;
- Extensions and add-ons;
- Authorized users;
- Vendors and suppliers;
- End users;
- Network and connections;
- SDLC (Software design life cycle).
7.3.2. System Analysis Approach
7.3.3. Threat Identification Approach
7.3.4. Summary
7.4. Research Question 3: What Are the Most Effective Methods for Validating Threat Models and Assessing Attacks on Digital Twins of Vehicles?
7.4.1. Penetration Testing
7.4.2. Attack Simulation
7.4.3. Summary
7.5. Publication Trends
8. Discussion
9. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- El-Rewini, Z.; Sadatsharan, K.; Selvaraj, D.F.; Plathottam, S.J.; Ranganathan, P. Cybersecurity challenges in vehicular communications. Veh. Commun. 2020, 23, 100214. [Google Scholar] [CrossRef]
- Grieves, M.; Vickers, J. Digital Twin: Mitigating Unpredictable, Undesirable Emergent Behavior in Complex Systems; Springer: Cham, Switzerland, 2017; pp. 85–113. [Google Scholar]
- da Silva, A.C.F.; Wagner, S.; Lazebnik, E.; Traitel, E. Using a cyber digital twin for continuous automotive security requirements verification. arXiv 2021, arXiv:2102.00790. [Google Scholar] [CrossRef]
- Tao, F.; Qi, Q.; Wang, L.; Nee, A. Digital twins and cyber–physical systems toward smart manufacturing and industry 4.0: Correlation and comparison. Engineering 2019, 5, 653–661. [Google Scholar] [CrossRef]
- Hu, W.; Zhang, T.; Deng, X.; Liu, Z.; Tan, J. Digital twin: A state-of-the-art review of its enabling technologies, applications and challenges. J. Intell. Manuf. Spec. Equip. 2021, 2, 1–34. [Google Scholar] [CrossRef]
- Engströma, V.; Lagerströma, R. Two decades of cyberattack simulations: A systematic literature review. Comput. Secur. 2022, 116, 102681. [Google Scholar] [CrossRef]
- Faleiro, R.; Pan, L.; Pokhrel, S.R.; Doss, R. Digital twin for cybersecurity: Towards enhancing cyber resilience. In Proceedings of the Broadband Communications, Networks, and Systems: 12th EAI International Conference, BROADNETS 2021, Virtual Event, 28–29 October 2021; Proceedings 12. Springer: Berlin/Heidelberg, Germany, 2022; pp. 57–76. [Google Scholar]
- Kapoor, P.; Vora, A.; Kang, K.D. Detecting and mitigating spoofing attack against an automotive radar. In Proceedings of the 2018 IEEE 88th Vehicular Technology Conference (VTC-Fall), Chicago, IL, USA, 27–30 August 2018; pp. 1–6. [Google Scholar]
- Oruganti, P.S.; Appel, M.; Ahmed, Q. Hardware-in-loop based automotive embedded systems cybersecurity evaluation testbed. In Proceedings of the ACM Workshop on Automotive Cybersecurity, Dallas, TX, USA, 27 March 2019; pp. 41–44. [Google Scholar]
- Berkovich, S.; Avdoshin, S. Enhancing the Security of Digital Twins in Cyber-Physical Systems. Int. J. Netw. Secur. 2020, 22, 41–50. [Google Scholar]
- Chhetri, S.; Zheng, Z.; Leshem, G.; Al Faruque, M. Security of IoT Cyber-Physical Systems: Digital Twin-based Approach. In Proceedings of the IEEE International Conference on Hardware/Software Codesign and System Synthesis, Seoul, Republic of Korea, 1–6 October 2017; pp. 1–10. [Google Scholar]
- Alcaraz, C.; Zeadally, S. Cybersecurity and Privacy in Smart Cities. In Smart Cities: Cybersecurity and Privacy; Domingo-Ferrer, J., Sánchez, D., Eds.; Routledge: Abingdon, UK, 2018. [Google Scholar]
- Lu, Y.; Liu, C.; Wang, K.; Huang, H.; Xu, X. Digital Twin-Based Cyber-Physical Production System: A 5C Architecture Perspective. IEEE Access 2020, 8, 2168–2175. [Google Scholar]
- UNECE. UNECE Regulation No.155: Cyber Security and Cyber Security Management System; United Nations Economic Commission for Europe: Geneva, Switzerland, 2021; Available online: https://unece.org/transport/documents/2021/03/standards/un-regulation-no-155-cyber-security-and-cyber-security (accessed on 17 June 2025).
- Segovia, M.; Garcia-Alfaro, J. Design, modeling and implementation of digital twins. Sensors 2022, 22, 5396. [Google Scholar] [CrossRef]
- Ferreira, A.; Pacheco, F.; Goncalves, J. Digital Twins in Smart Cities for Cybersecurity Monitoring. IEEE Access 2021, 9, 17576–17588. [Google Scholar]
- Chen, J.; Li, Z.; Zhang, Y.; Zheng, L. Digital Twin in Industrial Cybersecurity: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2021, 23, 2061–2085. [Google Scholar]
- Boyes, H.; Watson, T. Digital twins: An analysis framework and open issues. Comput. Ind. 2022, 143, 103763. [Google Scholar] [CrossRef]
- Unity Technologies. Digital Twin Definition. Available online: https://unity.com/solutions/digital-twin-definition (accessed on 27 March 2025).
- Sharifi, A.; Yamagata, Y.; Kono, T.; Yokohari, M. (Eds.) Security and Privacy Applications for Smart City Development; CRC Press: Boca Raton, FL, USA, 2021. [Google Scholar]
- Fuller, A.; Fan, Z.; Day, C.; Barlow, C. Digital twin: Enabling technologies, challenges and open research. IEEE Access 2020, 8, 108952–108971. [Google Scholar] [CrossRef]
- Liu, Z.; Qin, Y.; Yang, Y.; Feng, Y. Cybersecurity and the Digital Twin: Recent Advancements and Future Trends. J. Netw. Comput. Appl. 2020, 160, 102642. [Google Scholar]
- Jones, C.; Silva, J.; Sundaram, R. Exploring the Security Implications of Digital Twin in Critical Infrastructures. J. Inf. Secur. Appl. 2018, 40, 58–64. [Google Scholar]
- Ma, Z.; Zhang, H.; Wang, P. Digital Twin-Driven Cyber-Physical Production System: Framework and Implementation. J. Manuf. Syst. 2019, 58, 36–45. [Google Scholar]
- Smith, A.; Brown, C.; Johnson, D. Blockchain for Digital Twin Security in Industrial IoT: A Survey. IEEE Internet Things J. 2020, 7, 13212–13225. [Google Scholar]
- Park, J.; Kim, H.; Lee, D. Digital Twin for Cybersecurity in Autonomous Vehicles: A Survey. In Proceedings of the 2021 IEEE International Conference on Autonomous Systems (ICAS), Montréal, QC, Canada, 11–13 August 2021; pp. 98–105. [Google Scholar]
- Homaei, M.; Mogollon Gutierrez, O.; Sancho Nunez, J.C.; Avila Vegas, M.; Caro Lindo, A. A Review of Digital Twins and Their Application in Cybersecurity Based on Artificial Intelligence. arXiv 2023, arXiv:2311.01154. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Guo, S.; Dai, M.; Luan, T.H.; Liu, Y. A Survey on Digital Twins: Architecture, Enabling Technologies, Security and Privacy, and Future Prospects. arXiv 2023, arXiv:2301.13350. [Google Scholar] [CrossRef]
- Liu, S.; Leng, J.; Zhang, H. Digital Twin for Cyber-Physical System in Industry 4.0: A Comprehensive Review. In Proceedings of the 2019 IEEE International Conference on Systems, Man and Cybernetics (SMC), Bari, Italy, 6–9 October 2019; pp. 1897–1902. [Google Scholar]
- Buchholz, M.; Suri, N.; Hensley, B. Cyber Resilience and Autonomous Digital Twins. In Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2023. [Google Scholar] [CrossRef]
- Yoon, J.; Kim, Y.; Seo, J. Secure Communication in Digital Twin Systems with Blockchain Integration. Sensors 2020, 20, 6458. [Google Scholar]
- Marksteiner, S.; Bronfman, S.; Wolf, M.; Lazebnik, E. Using Cyber Digital Twins for Automated Automotive Cybersecurity Testing. In Proceedings of the 2021 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Vienna, Austria, 7–11 September 2021; pp. 123–128. [Google Scholar]
- Elayan, H.; Shrestha, R.; Tang, J. Digital Twin in Smart Cities: Cybersecurity and Privacy Challenges. In Proceedings of the 2020 IEEE International Smart Cities Conference (ISC2), Virtually, 28 September–1 October 2020; pp. 1–7. [Google Scholar]
- de Hoz Diego, J.D.; Temperekidis, A.; Katsaros, P.; Konstantinou, C. An iot digital twin for cyber-security defence based on runtime verification. In Proceedings of the Leveraging Applications of Formal Methods, Verification and Validation. Verification Principles: 11th International Symposium, ISoLA 2022, Rhodes, Greece, 22–30 October 2022; Proceedings, Part I. Springer: Berlin/Heidelberg, Germany, 2022; pp. 556–574. [Google Scholar]
- Tan, L.; Li, W.; Wang, X.; Huang, X. Security in Cyber-Physical Systems: The Role of Digital Twins. IEEE Internet Things J. 2020, 7, 4438–4446. [Google Scholar]
- Bonney, M.; de Angelis, M.; Dal Borgo, M.; Andrade, L.; Beregi, S.; Jamia, N.; Wagg, D. Development of a digital twin operational platform using Python Flask. Data-Centric Eng. 2022, 3, e1. [Google Scholar] [CrossRef]
- Zhang, P.; Cui, M.; Li, X. Digital Twins for Cybersecurity in Smart Manufacturing: A Framework. IEEE Access 2020, 8, 57902–57911. [Google Scholar]
- Damjanovic-Behrendt, V.; Hofmann, C. A privacy-aware digital twin for smart grid operations. Energy Procedia 2017, 114, 389–394. [Google Scholar]
- Damjanovic-Behrendt, V. A digital twin-based privacy enhancement mechanism for the automotive industry. In Proceedings of the 2018 International Conference on Intelligent Systems (IS), Funchal, Portugal, 25–27 September 2018; pp. 272–279. [Google Scholar]
- Uslar, M.; Rosinger, C.; Schlegel, S. Security by design for the smart grid: Combining SGAM and NISTIR 7628. IEEE Trans. Smart Grid 2021, 10, 123–130. [Google Scholar]
- Lee, J.; Bagheri, B.; Kao, H. Security of Digital Twins for Cyber-Physical Systems in Smart Manufacturing. Comput. Ind. 2020, 109, 76–83. [Google Scholar]
- Jiang, Y.; Wang, S.; Feng, X. Digital Twins for Cybersecurity in Healthcare Systems: A Survey. IEEE Access 2020, 8, 69013–69022. [Google Scholar]
- He, Y.; Sun, J.; Liu, Z. Digital Twin and Its Cybersecurity Challenges. IEEE Trans. Ind. Inform. 2021, 17, 1420–1430. [Google Scholar]
- Henry, P.; Radcliffe, M.; Freeman, S. Cybersecurity for Digital Twins in Smart Grids: A Comprehensive Review. IEEE Access 2019, 7, 35958–35977. [Google Scholar]
- Wolf, M. Threat Modeling Tool extension for Penetration Tester (TMTe4PT). Master Thesis, Deggendorf Institute of Technology, Deggendorf, Germany, 2019. [Google Scholar]
- Fernandez de Arroyabe, I.; Watson, T.; Angelopoulou, O. Cybersecurity in the Automotive Industry: A Systematic Literature Review (SLR). J. Comput. Inf. Syst. 2023, 63, 716–734. [Google Scholar] [CrossRef]
- de Oliveira, L.P.; Wehrmeister, M.A.; de Oliveira, A. Systematic literature review on automotive diagnostics. In Proceedings of the 2017 VII Brazilian Symposium on Computing Systems Engineering (SBESC), Curitiba, PR, Brazil, 6–10 November 2017; pp. 1–8. [Google Scholar]
- Kim, K.; Kim, J.S.; Jeong, S.; Park, J.H.; Kim, H.K. Cybersecurity for autonomous vehicles: Review of attacks and defense. Comput. Secur. 2021, 103, 102150. [Google Scholar] [CrossRef]
- Bhatti, G.; Mohan, H.; Singh, R.R. Towards the future of smart electric vehicles: Digital twin technology. Renew. Sustain. Energy Rev. 2021, 141, 110801. [Google Scholar] [CrossRef]
- Jones, D.; Snider, C.; Nassehi, A.; Yon, J.; Hicks, B. Characterising the Digital Twin: A systematic literature review. Cirp J. Manuf. Sci. Technol. 2020, 29, 36–52. [Google Scholar] [CrossRef]
- El-Sayed, M.; Sankar, S.; Prasad, M.; Badr, Y. Edge of Things: The Big Picture on the Integration of Edge, IoT and the Digital Twin. J. Parallel Distrib. Comput. 2021, 144, 171–185. [Google Scholar]
- Schwarz, C.; Wang, Z. The role of digital twins in connected and automated vehicles. IEEE Intell. Transp. Syst. Mag. 2022, 14, 41–51. [Google Scholar] [CrossRef]
- Semeraro, C.; Lezoche, M.; Panetto, H.; Dassisti, M. Digital twin paradigm: A systematic literature review. Comput. Ind. 2021, 130, 103469. [Google Scholar] [CrossRef]
- Kitchenham, B.A.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering; Technical Report EBSE, 2007-001; Software Engineering Group, School of Computer Science and Mathematics, Keele University: Keele, Staffordshire, UK; Department of Computer Science, University of Durham: Durham, UK, 2007. [Google Scholar]
- Altair. One Total Twin. Available online: https://altair.com/one-total-twin/ (accessed on 17 June 2025).
- Autodesk. Digital Twin: Unlock the Value of the Physical and Digital Worlds. Available online: https://www.autodesk.eu/campaigns/digital-twin (accessed on 17 June 2025).
- Amazon Web Services, Inc. AWS IoT TwinMaker. Available online: https://aws.amazon.com/iot-twinmaker/ (accessed on 17 June 2025).
- Ahmad, F.; Adnane, A.; Franqueira, V.N. A systematic approach for cyber security in vehicular networks. J. Comput. Commun. 2016, 4, 38–62. [Google Scholar] [CrossRef]
- Bozdal, M.; Randa, M.; Samie, M.; Jennions, I. Hardware trojan enabled denial of service attack on can bus. Procedia Manuf. 2018, 16, 47–52. [Google Scholar] [CrossRef]
- Singh, A.; Singh, M. An empirical study on automotive cyber attacks. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018; pp. 47–50. [Google Scholar]
- He, C.; Luan, T.H.; Lu, R.; Su, Z.; Dong, M. Security and Privacy in Vehicular Digital Twin Networks: Challenges and Solutions. IEEE Wirel. Commun. 2022, 30, 154–160. [Google Scholar] [CrossRef]
- Salfer, M.; Eckert, C. Attack surface and vulnerability assessment of automotive electronic control units. In Proceedings of the 2015 12th International Joint Conference on e-Business and Telecommunications (ICETE), Colmar, France, 20–22 July 2015; Volume 4, pp. 317–326. [Google Scholar]
- Bozdal, M.; Samie, M.; Jennions, I. A survey on can bus protocol: Attacks, challenges, and potential solutions. In Proceedings of the 2018 International Conference on Computing, Electronics & Communications Engineering (iCCECE), Southend, UK, 16–17 August 2018; pp. 201–205. [Google Scholar]
- Kang, T.U.; Song, H.M.; Jeong, S.; Kim, H.K. Automated reverse engineering and attack for CAN using OBD-II. In Proceedings of the 2018 IEEE 88th Vehicular Technology Conference (VTC-Fall), Chicago, IL, USA, 27–30 August 2018; pp. 1–7. [Google Scholar]
- Komissarov, R.; Wool, A. Spoofing attacks against vehicular FMCW radar. In Proceedings of the 5th Workshop on Attacks and Solutions in Hardware Security, Virtual, 19 November 2021; pp. 91–97. [Google Scholar]
- Kamal, M.; Barua, A.; Vitale, C.; Laoudias, C.; Ellinas, G. GPS location spoofing attack detection for enhancing the security of autonomous vehicles. In Proceedings of the 2021 IEEE 94th Vehicular Technology Conference (VTC2021-Fall), Virtually, 27–30 September 2021; pp. 1–7. [Google Scholar]
- Franke, U.; Cohen, M.; Sigholm, J. What can we learn from enterprise architecture models? An experiment comparing models and documents for capability development. Softw. Syst. Model. 2018, 17, 695–711. [Google Scholar] [CrossRef]
- Macher, G.; Sporer, H.; Berlach, R.; Armengaud, E.; Kreiner, C. Sahara: A security-aware hazard and risk analysis method. In Proceedings of the 2015 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 9–13 March 2015; pp. 621–624. [Google Scholar]
- Cui, J.; Sabaliauskaite, G. Us 2: An unified safety and security analysis method for autonomous vehicles. In Proceedings of the Advances in Information and Communication Networks: Proceedings of the 2018 Future of Information and Communication Conference (FICC), Singapore, 5–6 April 2018; Springer: Berlin/Heidelberg, Germany, 2018; Volume 1, pp. 600–611. [Google Scholar]
- Martin, J.; Carter, A. Nhtsa cybersecurity research. In Proceedings of the 25th International Technical Conference on the Enhanced Safety of Vehicles (ESV). National Highway Traffic Safety Administration, Detroit, MI, USA, 5–8 June 2017. [Google Scholar]
- Knight, A. The Hitchhiker’s Guide To Hacking Connected Cars: Methodology and Jump Kit Readiness. Available online: https://alissaknight.medium.com/the-hitchhikers-guide-to-hacking-connected-cars-methodology-and-jump-kit-readiness-3efcab428210 (accessed on 4 November 2017).
- Ruddle, A.R.; Weyl, B.; Idrees, S.; Roudier, Y.; Friedewald, M.; Leimbach, T.; Fuchs, A.; Gürgens, S.; Henninger, O.; Rieke, R.; et al. Security Requirements for Automotive On-Board Networks Based on Dark-Side Scenarios. Deliverable D2.3: EVITA—E-Safety Vehicle Intrusion Protected Applications; Technical Report, Project No. 224275, Seventh Framework Programme (FP7); Fraunhofer Institute for Secure Information Technology SIT: Darmstadt, Germany, 2009; Available online: https://www.evita-project.org/Publications/EVITA_D2.3.pdf (accessed on 17 June 2025).
- Ruijters, E.; Stoelinga, M. Fault tree analysis: A survey of the state-of-the-art in modeling, analysis and tools. Comput. Sci. Rev. 2015, 15, 29–62. [Google Scholar] [CrossRef]
- Izosimov, V.; Asvestopoulos, A.; Blomkvist, O.; Törngren, M. Security-aware development of cyber-physical systems illustrated with automotive case study. In Proceedings of the 2016 Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 14–18 March 2016; pp. 818–821. [Google Scholar]
- Hillenbrand, P.; Tenbohlen, S.; Keller, C.; Spanos, K. Understanding conducted emissions from an automotive inverter using a common-mode model. In Proceedings of the 2015 IEEE International Symposium on Electromagnetic Compatibility (EMC), Dresden, Germany, 16–22 August 2015; pp. 685–690. [Google Scholar]
- Wang, Y.; Yu, B.; Yu, H.; Xiao, L.; Ji, H.; Zhao, Y. Automotive cybersecurity vulnerability assessment using the common vulnerability scoring system and bayesian network model. IEEE Syst. J. 2022, 17, 2880–2891. [Google Scholar] [CrossRef]
- Schmittner, C.; Ma, Z.; Schoitsch, E.; Gruber, T. A case study of fmvea and chassis as safety and security co-analysis method for automotive cyber-physical systems. In Proceedings of the 1st ACM Workshop on Cyber-Physical System Security, Singapore, 14–17 April 2015; ACM: New York, NY, USA, 2015; pp. 69–80. [Google Scholar]
- Park, S.; Park, H. Pier: Cyber-resilient Risk Assessment Model for Connected and Autonomous Vehicles. Wirel. Netw. 2024, 30, 4591–4605. [Google Scholar] [CrossRef]
- Monteuuis, J.P.; Boudguiga, A.; Zhang, J.; Labiod, H.; Servel, A.; Urien, P. Sara: Security automotive risk analysis method. In Proceedings of the 4th ACM Workshop on Cyber-Physical System Security, Incheon, Republic of Korea, 4 June 2018; pp. 3–14. [Google Scholar]
- Zhang, Y.; Chu, L.; Ou, Y.; Guo, C.; Liu, Y.; Tang, X. A cyberphysical system-based velocity-profile prediction method and case study of application in plug-in hybrid electric vehicle. IEEE Trans. Cybern. 2019, 51, 40–51. [Google Scholar] [CrossRef]
- Fang, W.; Zhang, W.; Chen, W.; Pan, T.; Ni, Y.; Yang, Y. Trust-based attack and defense in wireless sensor networks: A survey. Wirel. Commun. Mob. Comput. 2020, 2020, 1–20. [Google Scholar] [CrossRef]
- Dietz, M.; Vielberth, M.; Pernul, G. Integrating digital twin security simulations in the security operations center. In Proceedings of the 15th International Conference on Availability, Reliability and Security, Virtually, 25–28 August 2020; pp. 1–9. [Google Scholar]
- Toyama, T.; Yoshida, T.; Oguma, H.; Matsumoto, T. Pasta: Portable automotive security testbed with adaptability. In Proceedings of the Black Hat Europe, London, UK, 3–6 December 2018. [Google Scholar]
- Shevchenko, N.; Chick, T.A.; O’Riordan, P.; Scanlon, T.P.; Woody, C. Threat Modeling: A Summary of Available Methods; Technical Report; Carnegie Mellon University Software Engineering Institute: Pittsburgh, PA, USA, 2018. [Google Scholar]
- Fraile, M.; Ford, M.; Gadyatskaya, O.; Kumar, R.; Stoelinga, M.; Trujillo-Rasua, R. Using attack-defense trees to analyze threats and countermeasures in an ATM: A case study. In Proceedings of the Practice of Enterprise Modeling: 9th IFIP WG 8.1. Working Conference, PoEM 2016, Skövde, Sweden, 8–10 November 2016; Proceedings. Springer: Berlin/Heidelberg, Germany, 2016; Volume 9, pp. 326–334. [Google Scholar]
- Do, Q.; Mirakhorli, M. Cyber Resilience of Digital Twin Systems in Critical Infrastructures. IEEE Trans. Dependable Secur. Comput. 2019, 17, 123–132. [Google Scholar]
- Smith, C. The Car Hacker’s Handbook: A Guide for the Penetration Tester; No Starch Press: San Francisco, CA, USA, 2016. [Google Scholar]
- Ebert, C.; Ray, R. Penetration Testing for Automotive Cybersecurity. ATZelectronics Worldw. 2021, 16, 16–22. [Google Scholar] [CrossRef]
- Dürrwang, J.; Braun, J.; Rumez, M.; Kriesten, R.; Pretschner, A. Enhancement of automotive penetration testing with threat analyses results. SAE Int. J. Transp. Cybersecur. Priv. 2018, 1, 91–112. [Google Scholar] [CrossRef]
- Garikapati, D.; Shetiya, S.S. Autonomous Vehicles: Evolution of Artificial Intelligence and the Current Industry Landscape. Big Data Cogn. Comput. 2024, 8, 42. [Google Scholar] [CrossRef]
- Wang, Z.; Gupta, R.; Han, K.; Wang, H.; Ganlath, A.; Ammar, N.; Tiwari, P. Mobility digital twin: Concept, architecture, case study, and future challenges. IEEE Internet Things J. 2022, 9, 17452–17467. [Google Scholar] [CrossRef]
- Pascale, F.; Adinolfi, E.A.; Coppola, S.; Santonicola, E. Cybersecurity in automotive: An intrusion detection system in connected vehicles. Electronics 2021, 10, 1765. [Google Scholar] [CrossRef]
- Dietz, M.; Putz, B.; Pernul, G. A distributed ledger approach to digital twin secure data sharing. In Proceedings of the IFIP Annual Conference on Data and Applications Security and Privacy, Charleston, SC, USA, 15–17 July 2019; Springer International Publishing: Cham, Switzerland, 2019; Volume 11559, pp. 281–300. [Google Scholar]
- Eckhart, M.; Ekelhart, A. Towards security-aware virtual environments for digital twins. In Proceedings of the 4th ACM Workshop on Cyber-Physical System Security, Incheon, Republic of Korea, 4 June 2018; pp. 61–72. [Google Scholar]
- Katsikeas, S.; Johnsson, P.; Hacks, S.; Lagerström, R. VehicleLang: A probabilistic modeling and simulation language for modern vehicle IT infrastructures. Comput. Secur. 2022, 117, 102705. [Google Scholar] [CrossRef]
- Laaki, H.; Miche, Y.; Tammi, K. Prototyping a digital twin for real-time remote control over mobile networks. IEEE Access 2020, 8, 5823–5832. [Google Scholar]
- Oka, D.K. Trends of Automotive Threats and Attacks. Technical Report. In Proceedings of the GlobalPlatform Cybersecurity Vehicle Forum, Tokyo, Japan, 22 May 2025. [Google Scholar]
- Harbor, B. Digital Twins in Automotive Cybersecurity: A Smarter Way for TARA, 2025. Published on Block Harbor Insights. Available online: https://www.blockharbor.io/blog/digital-twins-in-automotive-cybersecurity-a-smarter-way-for-tara (accessed on 16 June 2025).
- Das, P.; Al Asif, M.R.; Jahan, S.; Ahmed, K.; Bui, F.M.; Khondoker, R. STRIDE-Based Cybersecurity Threat Modeling, Risk Assessment and Treatment of an In-Vehicle Infotainment System. Vehicles 2024, 6, 1140–1163. [Google Scholar] [CrossRef]
- AbdulGhaffar, A.; Matrawy, A. LLMs’ Suitability for Network Security: A Case Study of STRIDE Threat Modeling. arXiv 2025, arXiv:2505.04101. [Google Scholar] [CrossRef]
- Kang, Y.; Wen, J.; Kang, J.; Zhang, T.; Du, H.; Niyato, D.; Yu, R.; Xie, S. Hybrid-Generative Diffusion Models for Attack-Oriented Twin Migration in Vehicular Metaverses. arXiv 2024, arXiv:2407.11036. [Google Scholar] [CrossRef]
- Voas, J.; Mell, P.; Laplante, P.; Piroumian, V. Security and Trust Considerations for Digital Twin Technology; Technical Report NIST IR 8356; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2025. [Google Scholar] [CrossRef]
- Farsi, M.; Daneshkhah, A.; Hosseinian-Far, A.; Jahankhani, H. (Eds.) Digital Twin Technologies and Smart Cities; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar]
- Sivarethinamohan, R.; Reddy, R.S. Digital Twin for Smart City Resilience and Solutions. In Digital Twin and Blockchain for Smart Cities; Wiley: Hoboken, NJ, USA, 2024. [Google Scholar] [CrossRef]
- Korman, M.; Välja, M.; Björkman, G.; Ekstedt, M.; Vernotte, A.; Lagerström, R. Analyzing the effectiveness of attack countermeasures in a SCADA system. In Proceedings of the 2nd Workshop on Cyber-Physical Security and Resilience in Smart Grids, SPSR-SG@CPSWeek, Pittsburgh, PA, USA, 21 April 2017; pp. 73–78. [Google Scholar]
- Ross, J.W. Enterprise architecture: Driving business benefits from it. Ssrn Electron. J. 2006, 1–15. [Google Scholar] [CrossRef]
- Iacob, M.E.; Meertens, L.; Jonkers, H.; Quartel, D. From enterprise architecture to business models and back. Softw. Syst. Model. 2014, 13, 1059–1083. [Google Scholar] [CrossRef]
- Dodge, M.; Kitchin, R. The challenges of cybersecurity for smart cities. In Creating Smart Cities; Coletta, C., Evans, L., Heaphy, L., Kitchin, R., Eds.; Routledge: London, UK, 2018. [Google Scholar] [CrossRef]
- Al-Issa, Y.; Soltanisehat, L.; Bertino, E. Cybersecurity in Digital Twin for Industrial IoT: Challenges and Solutions. IEEE Trans. Ind. Electron. 2018, 65, 1533–1544. [Google Scholar]
- Yu, S.; Zhou, Y.; Xu, J. Cybersecurity Framework for Digital Twins in Industrial IoT Environments. Future Gener. Comput. Syst. 2019, 94, 451–466. [Google Scholar]
- Hearn, M.; Rix, S. Cybersecurity considerations for digital twin implementations. IIC J. Innov. 2019, 10, 107–113. [Google Scholar]
- Wei, X.; Zhang, W.; Lu, R. Digital Twin for Smart Grid Security: Architecture and Applications. J. Grid Comput. 2018, 16, 479–497. [Google Scholar]
- Zhang, J.; Yang, G.; Jiang, L. A Digital Twin-Based Approach for Improving the Cybersecurity of Industrial Control Systems. In Proceedings of the 2019 IEEE International Conference on Cyber-Physical Systems (ICCPS), Montreal, QC, Canada, 16–18 April 2019; pp. 347–350. [Google Scholar]
- Coletta, C.; Evans, L.; Heaphy, L.; Kitchin, R. (Eds.) Creating Smart Cities; Routledge: London, UK, 2019. [Google Scholar]
- Groshev, O.; Shishkov, B.; Qiao, Y. Towards Secure Digital Twins for IoT-Enabled Smart Manufacturing. Int. J. Secur. Netw. 2019, 14, 191–201. [Google Scholar]
- Kaur, M.; Mishra, V.; Maheshwari, P. The convergence of digital twin, IoT, and machine learning: Transforming data into action. In Digital Twin Technologies and Smart Cities; Springer International Publishing: Cham, Switzerland, 2020; pp. 3–17. [Google Scholar]
- Raza, M.; Saeed, M.J.; Riaz, M.B.; Sattar, M.A. Federated Learning for Privacy-Preserving Intrusion Detection in Software-Defined Networks. IEEE Access 2024, 12, 69551–69567. [Google Scholar] [CrossRef]
- Smart Nation and Digital Government Office. Singapore’s Smart City Initiatives: A Sustainable Future. Smart Nation Singapore. 2025. Available online: https://www.smartnation.gov.sg/initiatives/smart-city-solutions/ (accessed on 16 March 2025).
- Li, Y.; Peng, P.; Xu, Y.; Huang, H. Blockchain-Enabled Digital Twins: Secure and Efficient Cyber-Physical Systems. IEEE Access 2021, 9, 3488–3501. [Google Scholar]
- Gheisari, M.; Ali, S. Blockchain for Digital Twin Management and Security in Internet of Things. In Proceedings of the 2020 IEEE International Conference on Blockchain, Rhodes Island, Greece, 2–6 November 2020; pp. 43–50. [Google Scholar]
- European Commission. Rolling Plan for ICT Standardisation 2025. Available online: https://interoperable-europe.ec.europa.eu/collection/rolling-plan-ict-standardisation/rolling-plan-2025 (accessed on 27 April 2024).
- Eckhart, M.; Ekelhart, A. A specification-based state replication approach for digital twins. In Proceedings of the 2018 Workshop on Cyber-Physical Systems Security and Privacy, Toronto, ON, Canada, 15–19 October 2019; pp. 36–47. [Google Scholar]
- El-Hajj, M. Systematic literature review: Digital twins’ role in enhancing security for Industry 4.0 applications. Secur. Priv. 2024, 7, e396. [Google Scholar] [CrossRef]
- Ozkan-Okay, M.; Akin, E.; Aslan, Ö.; Kosunalp, S.; Iliev, T.; Stoyanov, I.; Beloev, I. A comprehensive survey: Evaluating the efficiency of artificial intelligence and machine learning techniques on cybersecurity solutions. IEEE Access 2024, 12, 12229–12256. [Google Scholar] [CrossRef]
- Karafili, E.; Bales, K.; Lupu, E. A Formal Approach for Digital Twins of Critical Infrastructures. Int. J. Crit. Infrastruct. Prot. 2018, 22, 32–43. [Google Scholar]


| Digital Twin Type | Security Testing Characteristics |
|---|---|
| Physics-Based | Detection of Known Attacks: High. Accurately replicates ECU behavior under defined conditions. Detection of Novel Attacks: Low. Lacks adaptability to emerging threats. Computational Cost: High. Requires detailed system modeling. Adaptability: Low. Rigid and difficult to generalize. Transparency: High. Model logic is interpretable. Data Requirements: Moderate. Primarily specification-based. |
| Data-Driven | Detection of Known Attacks: Moderate. Matches statistical patterns in past data. Detection of Novel Attacks: High. Uses anomaly detection via ML. Computational Cost: Moderate. Depends on data size and model complexity. Adaptability: High. Easily retrains on new patterns. Transparency: Low. Often opaque (black-box behavior). Data Requirements: High. Requires large, labeled datasets. |
| Hybrid | Detection of Known Attacks: High. Leverages physics-based accuracy. Detection of Novel Attacks: High. Adds ML adaptability. Computational Cost: High. Combines two modeling paradigms. Adaptability: Moderate. Better than physics only, less than ML. Transparency: Moderate. Mix of logic-based and data-driven behavior. Data Requirements: High. Uses both structured and real-world data. |
| 5C Stage | Layer | Security Testing Function | Example | RQ Alignment |
|---|---|---|---|---|
| Connection | Connectivity | Threat detection via IDS | CAN-Bus spoofing detection | RQ1: Threat identification |
| Conversion | DT Data | Data integrity testing | ECU data validation | RQ1: Threat identification |
| Cyber | DT Virtual | Threat modeling with STRIDE/PASTA | Data poisoning mitigation | RQ2: Threat modeling |
| Cognition | Service | Attack simulation with VehicleLang | Zero-day attack validation | RQ3: Validation/attack simulation |
| Configuration | All Layers | Lifecycle security testing | Firmware update security | RQ3: Validation/attack simulation |
| Terminology | Explanation |
|---|---|
| Automotive Systems | A system that incorporates all of a vehicle’s parts, both physically and through the software programs that operate on them. |
| Digital Twin | A digital replica of a physical system in the actual world, used to simulate real-time functioning. |
| Attack Simulation | The process of simulating different cyberattacks to test a system’s security. |
| Security Testing | The procedure of testing a system to find and address any security risks and vulnerabilities. |
| Physical Layer | The section of a car’s system that houses its mechanical parts, such as the engine, transmission, and brakes. |
| Communication Layer | The layer of a vehicle system that contains the interfaces and communication protocols that permit communication between various components. |
| Application Layer | The portion of a vehicular system that houses the programs and services that operate on top of the communication layer. |
| Data Layer | The portion of a vehicle system that contains the data that the system has collected and processed. |
| Security Layer | The portion of a vehicle’s system that contains security measures and procedures used to guard against cyberattacks. |
| Cyberattack | An attempt to exploit a vulnerability in a system to steal, destroy, or gain unauthorized access. |
| Black-Box Modeling | A modeling strategy where the system is modeled based on its inputs and outputs without knowledge of its internal workings. |
| White-Box Modeling | A modeling strategy where the inner workings of a system can be directly modeled because they are known. |
| Hybrid Modeling | A modeling strategy that combines principles of black box and white box modeling. |
| Attack Surface | The collection of vulnerabilities and entry points that an attacker can exploit to compromise a system. |
| Threat Modeling | The process of identifying and evaluating potential threats and system weaknesses. |
| Selected Database | Web Address |
|---|---|
| IEEE | https://ieeexplore.ieee.org/ |
| Science Direct | https://www.sciencedirect.com/ |
| ACM | https://dl.acm.org/ |
| Database | First Results | IC/EC | Titles & Keywords | Snowballing | Abstract Reading | Full-Text Selection |
|---|---|---|---|---|---|---|
| IEEE Xplore | 100 | 29 | 26 | 32 | 2 | 12 |
| Science Direct | 657 | 55 | 23 | 39 | 27 | 2 |
| ACM | 97 | 22 | 10 | 6 | 4 | 4 |
| Total | 854 | 116 | 59 | 77 | 33 | 18 |
| Areas | Relevant Systems |
|---|---|
| Design and Optimization | Cyber Systems Powertrain Suspension and Steering Electrical and Electronics Autonomous Driving |
| Maintenance | Cybersecurity maintenance Predictive maintenance |
| Vehicular Twin Systems | Sub-Systems | Attacks Possible |
|---|---|---|
| Cyber Systems | Vehicular Network Infotainment systems Telematics systems | Malware and Viruses, Dos Attacks Man-in-Middle attacks. Remote Exploits. |
| Electrical and Electronic Systems | Electronic Control Units (ECU’S) Sensors OBD systems | Software attacks Hardware attacks (EMI Attacks). Diagnostic access attacks. |
| Autonomous Systems | Lidar Radar Camera GPS | Spoofing attacks Sensor attacks |
| Authors | Research Objective | Methodology | Outcome |
|---|---|---|---|
| Kyounggon Kim et al. [48] | Systematic investigation of autonomous vehicle attacks and defenses | Classification of attacks into three categories and defenses into three categories, focusing on AI/ML-based solutions | Identified vulnerabilities and proposed defense strategies for smart city integration |
| Viktor Engström et al. [6] | Unified baseline for cyberattack simulations in computer security | Systematic review of 11 key papers from 1999–2019 | Highlighted commonalities and gaps in attack simulation research |
| Farhan Ahmad et al. [58] | Security and privacy of vehicular ad hoc networks (VANETs) | Asset-based approach with taxonomy of vulnerabilities, threats, and attacks | Proposes classification and mitigation strategies |
| Mehmet Bozdal et al. [59] | Demonstration of disruption via hardware Trojan on CAN bus | Simulates HT attack without physical access using untraceable faults | Highlights vulnerabilities in CAN communication |
| Aman Singh et al. [60] | Analyze cybersecurity vulnerabilities in automotive electronics | Focus on networked embedded systems and algorithms | Identified potential threats and proposed mitigation strategies |
| Chao He et al. [61] | Address security and privacy challenges in vehicular digital twin (VDT) networks | Analysis of VDT architecture and countermeasures for security | Identified open research challenges and proposed countermeasures |
| Mariana Segovia et al. [15] | Methodology for design and integration of digital twins (DTs) | Detailed phases from architecture planning to real-time data exchange | Outlined experimental platforms and standards for DTs |
| Pradeep Sharma Oruganti et al. [9] | Develop a testbed for automotive embedded systems’ cybersecurity evaluation | Hardware-in-loop platform with network and mobility simulators | Demonstrates a GPS spoofing attack |
| Leonardo Presoto de Oliveira et al. [47] | Review of tools and methods in automotive diagnostics | Systematic literature review and surveys for extracting OBD data | Identified gaps in human–machine interface approaches |
| Chao He et al. [43] | Investigate security and privacy issues in vehicular digital twin networks | Proposes inter- and intra-twin communication models | Suggests countermeasures and discusses privacy-sensitive information |
| Approach | Description | Applicability/Use |
|---|---|---|
| STRIDE | Checklist-based model focusing on spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege. | Widely adopted in software-driven systems (e.g., ECUs); suitable for early design threat enumeration. |
| Attack Trees | Hierarchical representation of attack goals and sub-goals using tree structures. | Effective for structured multi-step attacks; referenced in ISO 21434-based modeling. |
| DFD + Threat Models | Combines data flow diagrams with methods like STRIDE to trace threats through system boundaries. | Applied during system architecture planning for identifying data-related threats and flows. |
| STPA-Sec | System-Theoretic Process Analysis adapted for security to identify unsafe control actions. | Used in cyber-physical systems; strong for hazard modeling in safety-critical environments. |
| Bayesian Networks | Probabilistic modeling of threat propagation and dependency using graph-based logic. | Supports scenario simulation and intrusion prediction; rarely adopted in industry. |
| HEAVENS | A structured automotive-focused framework integrating threat assessment with risk quantification. | Aligned with ISO 21434; focuses on lifecycle security for connected vehicles. |
| Approach | Description | Methods |
|---|---|---|
| Data Analysis | Monitoring the system’s data flow to find potential security threats and flaws involving data assets and flows. | SAHARA [41] USSS [69] NHTSA [43] EVITA [44] HEAVENS [46] |
| System Analysis | Examining the system’s components and design to find any potential security holes and threats. | FTA [47] ETA [48] CMA [50] CVSS [52] FMVEA [53] VERA [54] |
| Threat Identification | Analyzing system interactions and components to find potential security threats and vulnerabilities. | SARA [55] SAM [56] BDG [57] PASTA [58] VAST [59] BNM [60] ATM [61] |
| Approach | Computational Complexity | Industry Adoption | Attack Scenario Applicability | RQ Alignment |
|---|---|---|---|---|
| STRIDE | Low; simple rule-based | Moderate; used in software-focused automotive systems | Known attacks (e.g., ECU injection) | RQ1: Threat identification; RQ2: Structured modeling |
| PASTA | High; multi-stage process | High; adopted by BMW, aligns with UNECE R155 | Structured attacks (e.g., CAN-Bus spoofing) | RQ2: Threat modeling; RQ3: Validation |
| MITRE ATT&CK | High; extensive database | Emerging in automotive; used in cybersecurity firms | Dynamic attacks (e.g., zero-day) | RQ1: Threat identification; RQ3: Attack simulation |
| Tool/Method | Implementation and Limitations |
|---|---|
| VehicleLang | Implementation: - Domain-specific modeling language - Generates attack graphs from known threats - Validated via expert input and Feigenbaum testing [95] Limitations: - Cannot simulate hardware-level behavior - Limited to known attack patterns - Not suitable for zero-day vulnerabilities |
| IDS (CAN-Bus + Bayesian) | Implementation: - Filters CAN-Bus messages - Detects anomalies using Bayesian models - Evaluated in experimental setups [92] Limitations: - High false-positive rate in real use - Resource limits on ECUs - Incompatibility due to proprietary protocols |
| Year | Number of Publications |
|---|---|
| 2012 | 1 |
| 2013 | 2 |
| 2014 | 4 |
| 2015 | 6 |
| 2016 | 9 |
| 2017 | 16 |
| 2018 | 40 |
| 2019 | 112 |
| 2020 | 267 |
| 2021 | 312 |
| Domain | Environment | Security Focus | Key Challenges |
|---|---|---|---|
| Industrial DT | Closed, structured | Asset control, predictive failure | Low adaptability, proprietary systems, limited external interfaces |
| Vehicular DT | Semi-open, mobile | ECU threats, OTA updates | Real-time safety constraints, mobile networks, physical-cyber convergence |
| Smart City DT | Open, public | Network-layer threats, privacy, trust | Scale, heterogeneous data, shared infrastructure, multi-party governance |
| Domain | Key Challenge | Threat Example | Cybersecurity Focus | RQ Alignment |
|---|---|---|---|---|
| Smart Cities [114] | Heterogeneous IoT integration [115] | Sensor spoofing | Scalable threat detection | RQ1: Threat identification; RQ2: Dynamic modeling |
| IIoT | Isolated system integrity | Malware injection | Process continuity | RQ2: Structured modeling |
| Autonomous Vehicles | Real-time safety critical attacks | CAN-Bus spoofing | ECU protection | RQ1: Threat identification; RQ3: Validation |
| Smart Grids | Power system stability | Grid cyberattacks | Resilience measures | RQ3: Attack simulation |
| Concept | Description | Citation/Example | RQ Alignment |
|---|---|---|---|
| DT-Based Trust Chains | Secure IoT data exchanges | El-Hajj (2024) [123]; Singapore pilot | RQ1: Threat identification |
| Autonomous Cyber-Defensive DTs | Adaptive attack mitigation | Ozkan-Okay et al. (2024) [124]; traffic system | RQ3: Attack simulation |
| Integrated Policy Frameworks | Standardized security protocols | 2024 EU initiative [121] | RQ2: Threat modeling |
| Priority Area | Description | AI/ML Solution | RQ Alignment |
|---|---|---|---|
| CAN-Bus Injection | Safety-critical vehicle control breach | Federated learning | RQ1: Threat identification; RQ2: Modeling |
| GPS Spoofing | Disruption of autonomous navigation | Reinforcement learning | RQ3: Attack simulation |
| OTA Firmware Tampering | Exploitation of software updates | Explainable AI for modeling | RQ2: Threat modeling; RQ3: Validation |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shah, U.M.; Minhas, D.M.; Kifayat, K.; Shah, K.A.; Frey, G. Threat Modeling and Attacks on Digital Twins of Vehicles: A Systematic Literature Review. Smart Cities 2025, 8, 142. https://doi.org/10.3390/smartcities8050142
Shah UM, Minhas DM, Kifayat K, Shah KA, Frey G. Threat Modeling and Attacks on Digital Twins of Vehicles: A Systematic Literature Review. Smart Cities. 2025; 8(5):142. https://doi.org/10.3390/smartcities8050142
Chicago/Turabian StyleShah, Uzair Muzamil, Daud Mustafa Minhas, Kashif Kifayat, Khizar Ali Shah, and Georg Frey. 2025. "Threat Modeling and Attacks on Digital Twins of Vehicles: A Systematic Literature Review" Smart Cities 8, no. 5: 142. https://doi.org/10.3390/smartcities8050142
APA StyleShah, U. M., Minhas, D. M., Kifayat, K., Shah, K. A., & Frey, G. (2025). Threat Modeling and Attacks on Digital Twins of Vehicles: A Systematic Literature Review. Smart Cities, 8(5), 142. https://doi.org/10.3390/smartcities8050142








