Investigation of Data Quality Assurance across IoT Protocol Stack for V2I Interactions
Abstract
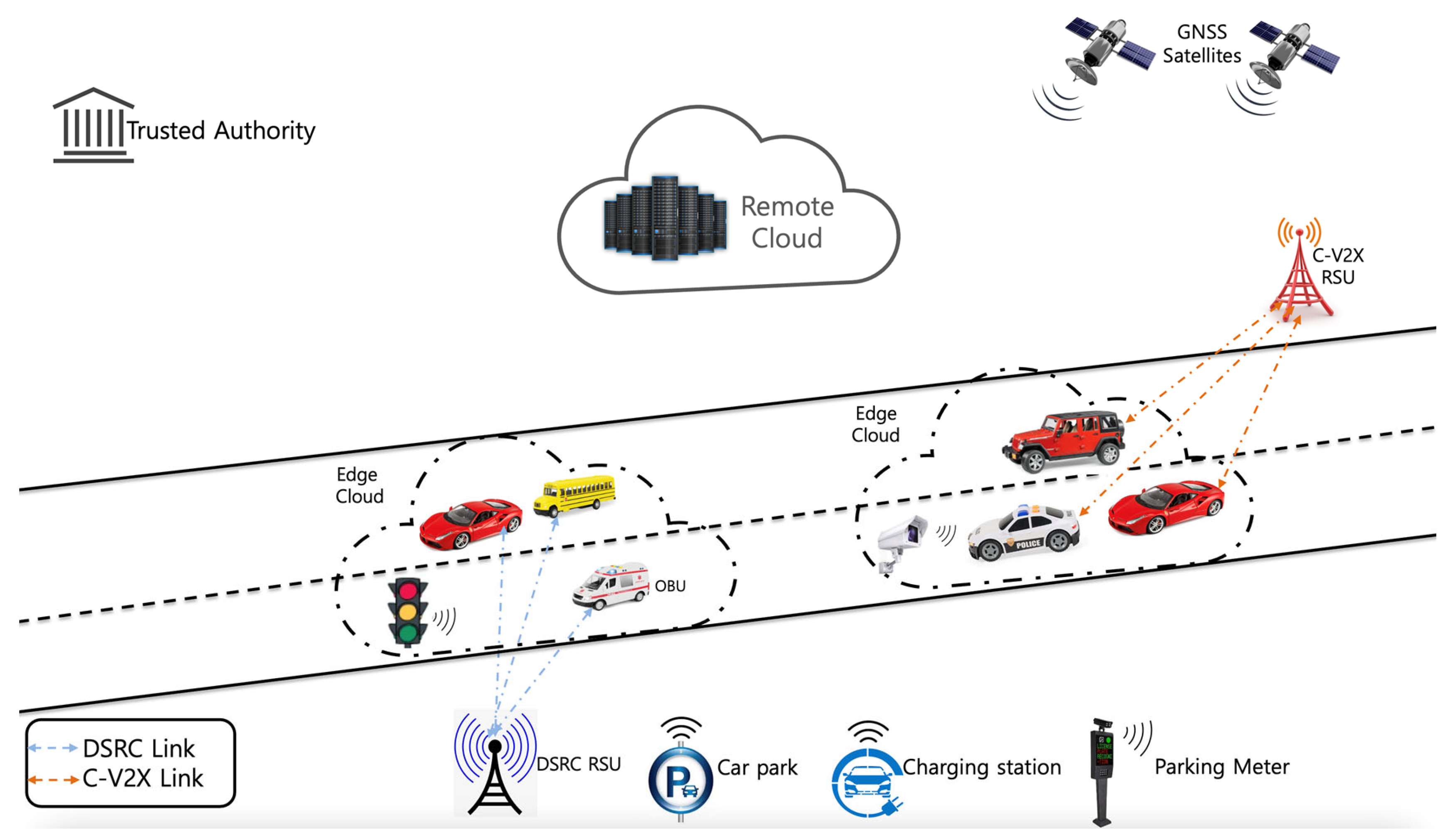
:1. Introduction
- Presents an unconventional viewpoint on the IoT protocol stack, underscoring the drawbacks of depending solely on a single protocol/layered approach for ensuring reliable data transmission within IoT applications.
- Provides a support framework with a focus on DQ for identifying and selecting suitable IoT protocol stack for a specific use case requiring efficient data transmission within the V2I ecosystem and IoT applications in general.
- Presents a structured way of organising and customising the IoT protocol stack, making it easier to pinpoint areas for adaptation and optimisation.
2. Data Quality and Related Dimensions
2.1. Accuracy
2.2. Availability
2.3. Completeness
2.4. Confidentiality
2.5. Consistency
2.6. Data Integrity
2.7. Reliability
2.8. Timeliness
2.9. Traceability
2.10. Validity
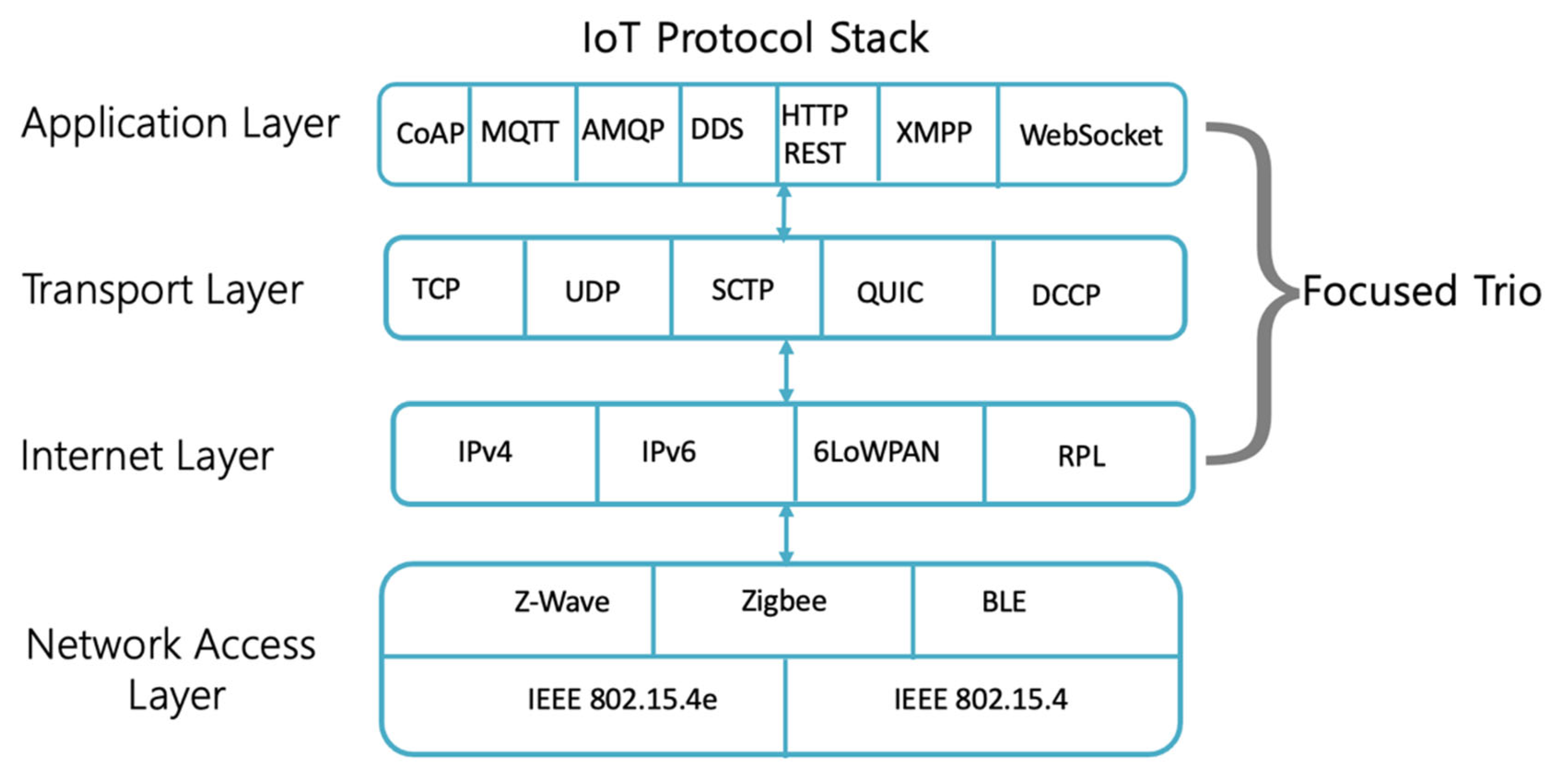
3. Overview of Network Protocols
3.1. Application Layer
3.1.1. Constrained Application Protocol
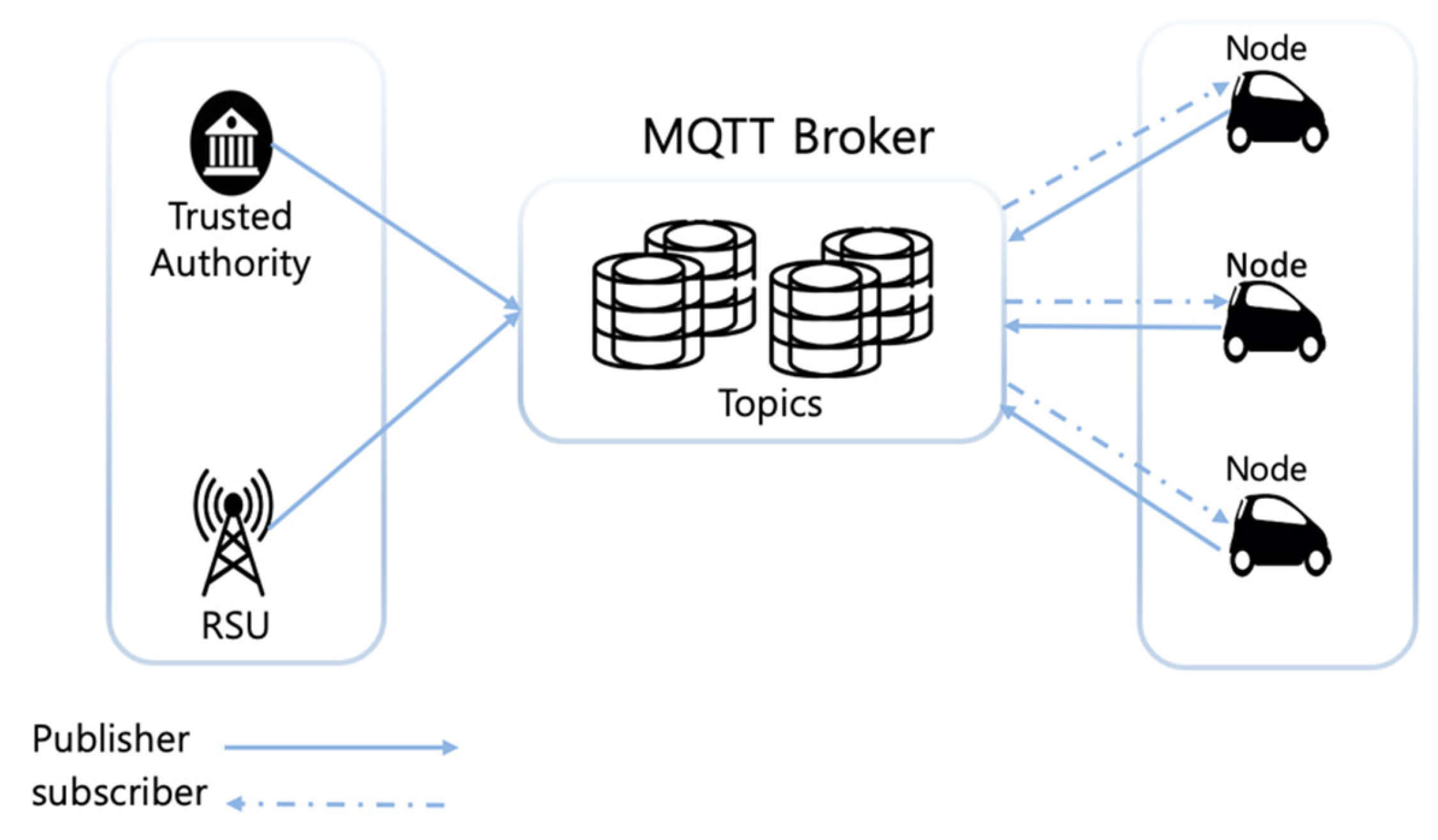
3.1.2. The Message Queuing Telemetry Transport
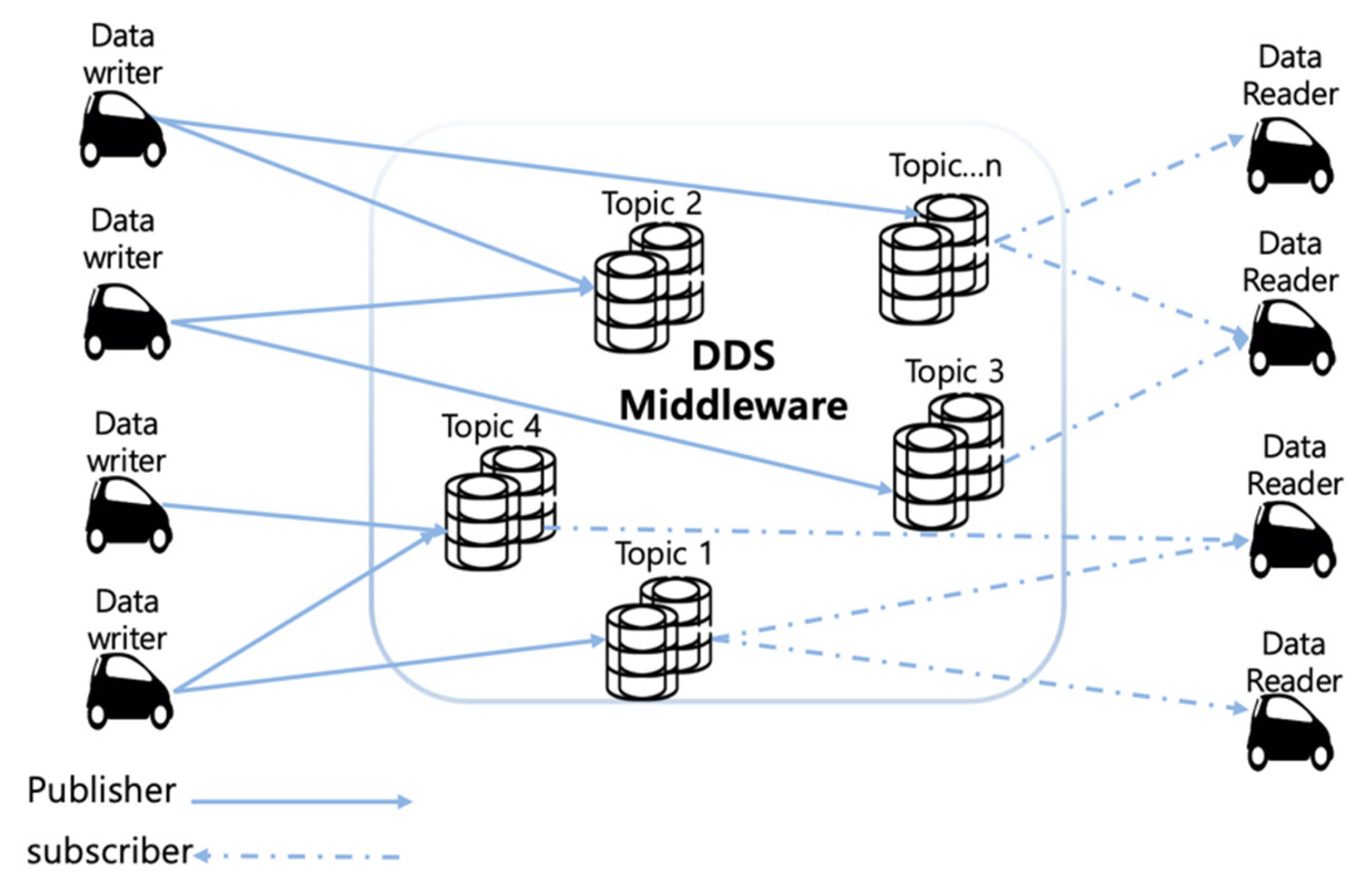
3.1.3. Data Distribution Service
3.1.4. Extensible Messaging and Presence Protocol
3.1.5. Advanced Message Queuing Protocol
3.1.6. HTTP REST
3.1.7. WebSocket
3.2. Transport Layer
3.2.1. Datagram Congestion Control Protocol
3.2.2. Steam Control Transmission Protocol
3.2.3. Quick UDP Internet Connection
3.3. Internet Layer
3.3.1. Low-Power Wireless Personal Area Networks
3.3.2. Routing Protocol for Low-Power and Lossy Networks
4. Survey of Network Protocols
5. Methodology
6. Findings and Discussion
6.1. Mapping
6.2. Data Quality Acting as a Complement of Quality of Service
6.3. Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| 3G | Third Generation |
| 4G | Fourth Generation |
| 6LowPAN | Pv6 over Low-Power Wireless Personal Area Networks |
| ACK | Acknowledgement |
| AMQP | Advanced Message Queuing Protocol |
| C-ITS | Cooperative Intelligent Transportation System |
| C-V2X | Cellular Vehicle-to-Everything |
| CoAP | Constrained Application Protocol |
| DCCP | Datagram Congestion Control Protocol |
| DDS | Data Distribution Service |
| DNS | Domain Name Server |
| DQ | Data Quality |
| DSRC | Dedicated Short-range Communication |
| FTP | File Transfer Protocol |
| GNSS | Global Navigation Satellite System. |
| HTTP | Hypertext transfer protocol |
| IETF | Internet Engineering Task Force |
| IoT | Internet of things |
| IP | Internet Protocol |
| IPv4 | Internet Protocol version 4 |
| IPv6 | Internet Protocol version 6 |
| LLNs | Low-Power and Lossy Networks |
| M2M | Machine-to-Machine |
| MANET | Mobile Ad Hoc Network |
| ModQUIC | Modified Quick UDP Internet Connections |
| MQTT | Message Queuing Telemetry Transport |
| MQTT-SN | Message Queuing Telemetry Transport-Sensor Network |
| PDR | Packet Delivery Ratio |
| PSNR | Peak Signal-to-Noise Ratio |
| QoS | Quality of services |
| QUIC | Quick UDP Internet Connections |
| REST | Representational State Transfer |
| REST | Representational State Transfer |
| RPL | Routing Protocol for Low-Power and Lossy Networks |
| RTT | Round Trip Time |
| SCTP | Stream Control Transmission Protocol |
| SMTP | Simple Mail Transfer Protocol |
| STD | Spatial-Temporal Data |
| TCP | Transmission Control Protocol |
| TCP/IP | Transmission Control Protocol/Internet Protocol |
| TFRC | TCP-Friendly Rate Control |
| UDP | User Datagram Protocol |
| V2I | Vehicle-to-Infrastructure |
| V2V | Vehicles-to-Vehicles |
| V2X | Vehicle-to-Everything |
| VANET | Vehicular Ad Hoc Network |
| XMPP | Extensible Messaging and Presence Protocol |
References
- Ashton, K. That ‘internet of things’ thing. RFID J. 2009, 22, 97–114. [Google Scholar]
- Li, S.; Xu, L.D.; Zhao, S. The internet of things: A survey. Inf. Syst. Front. 2015, 17, 243–259. [Google Scholar] [CrossRef]
- Sunyaev, A. The internet of things. In Internet Computing; Springer: Cham, Switzerland, 2020; pp. 301–337. [Google Scholar]
- Sagiroglu, S.; Sinanc, D. Big data: A review. In Proceedings of the 2013 International Conference on Collaboration Technologies and Systems (CTS), San Diego, CA, USA, 20–24 May 2013; pp. 42–47. [Google Scholar]
- Liu, C.; Nitschke, P.; Williams, S.P.; Zowghi, D. Data quality and the Internet of Things. Computing 2020, 102, 573–599. [Google Scholar] [CrossRef]
- Karkouch, A.; Mousannif, H.; Al Moatassime, H.; Noel, T. Data quality in internet of things: A state-of-the-art survey. J. Netw. Comput. Appl. 2016, 73, 57–81. [Google Scholar] [CrossRef]
- Chauhan, S.; Agarwal, N.; Kar, A.K. Addressing big data challenges in smart cities: A systematic literature review. Info 2016, 18, 73–90. [Google Scholar] [CrossRef]
- Tanenbaum, A.S. Network protocols. ACM Comput. Surv. 1981, 13, 453–489. [Google Scholar] [CrossRef]
- Shang, W.; Yu, Y.; Droms, R.; Zhang, L. Challenges in IoT Networking via TCP/IP Architecture. NDN Project. 2016. Available online: https://named-data.net/wp-content/uploads/2016/02/ndn-0038-1-challenges-iot.pdf (accessed on 14 April 2023).
- Forouzan, B.A. TCP/IP Protocol Suite; McGraw-Hill Higher Education: Chicago, IL, USA, 2002. [Google Scholar]
- Shojafar, M.; Cordeschi, N.; Baccarelli, E. Energy-efficient adaptive resource management for real-time vehicular cloud services. IEEE Trans. Cloud Comput. 2016, 7, 196–209. [Google Scholar] [CrossRef]
- Sharma, C.; Gondhi, N.K. Communication protocol stack for constrained IoT systems. In Proceedings of the 2018 3rd International Conference on Internet of Things: Smart Innovation and Usages (IoT-SIU), Bhimtal, India, 23–24 February 2018; pp. 1–6. [Google Scholar]
- Chand, H.V.; Karthikeyan, J. Survey on the role of IoT in intelligent transportation system. Indones. J. Electr. Eng. Comput. Sci. 2018, 11, 936–941. [Google Scholar] [CrossRef]
- Arena, F.; Pau, G. An overview of vehicular communications. Future Internet 2019, 11, 27. [Google Scholar] [CrossRef]
- Peng, H.; Liang, L.; Shen, X.; Li, G.Y. Vehicular communications: A network layer perspective. IEEE Trans. Veh. Technol. 2018, 68, 1064–1078. [Google Scholar] [CrossRef]
- Malik, R.Q.; Ramli, K.N.; Kareem, Z.H.; Habelalmatee, M.I.; Abbas, H. A Review on Vehicle-to-Infrastructure Communication System: Requirement and Applications. In Proceedings of the 2020 3rd International Conference on Engineering Technology and Its Applications (IICETA), Najaf, Iraq, 6–7 September 2020; pp. 159–163. [Google Scholar]
- Ndashimye, E.; Ray, S.K.; Sarkar, N.I.; Gutiérrez, J.A. Vehicle-to-infrastructure communication over multi-tier heterogeneous networks: A survey. Comput. Netw. 2017, 112, 144–166. [Google Scholar] [CrossRef]
- Li, Y. An overview of the DSRC/WAVE technology. In Quality, Reliability, Security and Robustness in Heterogeneous Networks, Proceedings of the 7th International Conference on Heterogeneous Networking for Quality, Reliability, Security and Robustness, QShine 2010, and Dedicated Short Range Communications Workshop, DSRC 2010, Houston, TX, USA, 17–19 November 2010; Revised Selected Papers 7; Springer: Berlin/Heidelberg, Germany, 2012; pp. 544–558. [Google Scholar]
- Wang, X.; Mao, S.; Gong, M.X. An overview of 3GPP cellular vehicle-to-everything standards. GetMobile: Mob. Comput. Commun. 2017, 21, 19–25. [Google Scholar] [CrossRef]
- Ansari, K. Joint use of DSRC and C-V2X for V2X communications in the 5.9 GHz ITS band. IET Intell. Transp. Syst. 2021, 15, 213–224. [Google Scholar] [CrossRef]
- Wagh, T.; Bagrecha, R.; Salunke, S.; Shedge, S.; Lomte, V. A survey on vehicle to vehicle communication. In Computational Methods and Data Engineering: Proceedings of ICMDE 2020; Springer: Singapore, 2020; Volume 2, pp. 163–175. [Google Scholar]
- Ganeshkumar, N.; Kumar, S. Obu (on-board unit) wireless devices in vanet (s) for effective communication—A review. In Computational Methods and Data Engineering: Proceedings of ICMDE; Springer: Singapore, 2020; Volume 2, pp. 191–202. [Google Scholar]
- Wang, R.Y.; Strong, D.M. Beyond accuracy: What data quality means to data consumers. J. Manag. Inf. Syst. 1996, 12, 5–33. [Google Scholar] [CrossRef]
- Shih, C.S.; Chou, J.J.; Reijers, N.; Kuo, T.W. Designing CPS/IoT applications for smart buildings and cities. IET Cyber-Phys. Syst. Theory Appl. 2016, 1, 3–12. [Google Scholar] [CrossRef]
- Perez-Castillo, R.; Carretero, A.G.; Rodriguez, M.; Caballero, I.; Piattini, M.; Mate, A.; Kim, S.; Lee, D. Data quality best practices in IoT environments. In Proceedings of the 2018 11th International Conference on the Quality of Information and Communications Technology (QUATIC), Coimbra, Portugal, 4–7 September 2018; pp. 272–275. [Google Scholar]
- Alwan, A.A.; Ciupala, M.A.; Brimicombe, A.J.; Ghorashi, S.A.; Baravalle, A.; Falcarin, P. Data quality challenges in large-scale cyber-physical systems: A systematic review. Inf. Syst. 2022, 105, 101951. [Google Scholar] [CrossRef]
- Kapil, G.; Agrawal, A.; Khan, R.A. A study of big data characteristics. In Proceedings of the 2016 International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 21–22 October 2016; pp. 1–4. [Google Scholar]
- Sun, Z.; Strang, K.; Li, R. Big data with ten big characteristics. In Proceedings of the 2nd International Conference on Big Data Research, Weihai, China, 27–29 October 2018; pp. 56–61. [Google Scholar]
- Rehrl, K.; Gröchenig, S. Evaluating localization accuracy of automated driving systems. Sensors 2021, 21, 5855. [Google Scholar] [CrossRef] [PubMed]
- Szántó, M.; Hidalgo, C.; González, L.; Pérez, J.; Asua, E.; Vajta, L. Trajectory Planning of Automated Vehicles Using Real-Time Map Updates. IEEE Access 2023, 11, 67468–67481. [Google Scholar] [CrossRef]
- Bhatti, F.; Shah, M.A.; Maple, C.; Islam, S.U. A novel internet of things-enabled accident detection and reporting system for smart city environments. Sensors 2019, 19, 2071. [Google Scholar] [CrossRef]
- Issa, S.; Adekunle, O.; Hamdi, F.; Cherfi, S.S.S.; Dumontier, M.; Zaveri, A. Knowledge graph completeness: A systematic literature review. IEEE Access 2021, 9, 31322–31339. [Google Scholar] [CrossRef]
- Kaneyasu, H.; Nobayashi, D.; Tsukamoto, K.; Ikenaga, T.; Lee, M. Data completeness-aware transmission control for large spatio-temporal data retention. In Proceedings of the 2022 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 7–9 January 2022; pp. 1–5. [Google Scholar]
- Bhalaji, D.N. Reliable data transmission with heightened confidentiality and integrity in IOT empowered mobile networks. J. IoT Soc. Mob. Anal. Cloud 2020, 2, 106–117. [Google Scholar]
- Liu, M.; Wang, Y.; Li, H.; Jing, Y.; Zhang, G.; He, W. Analyzing V2I Channel and Spatial Consistency through Simulation. In Proceedings of the 2021 7th International Conference on Computer and Communications (ICCC), Chengdu, China, 10–13 December 2021; pp. 453–458. [Google Scholar]
- Zadorozhny, V.; Krishnamurthy, P.; Abdelhakim, M.; Pelechrinis, K.; Xu, J. Data credence in iot: Vision and challenges. In Open Journal of Internet of Things (OJIOT), v. 3, N. 1, 114-126, 2017. Special Issue: Proceedings of the International Workshop on Very Large Internet of Things (VLIoT 2017) in Conjunction with the VLDB 2017 Conference; Research online Publishing: Lübeck, Germany, 2017; Volume 3, pp. 114–126. [Google Scholar]
- Gopinath, S.; Vinoth Kumar, K.; Jaya Sankar, T. Secure location aware routing protocol with authentication for data integrity. Cluster Comput. 2019, 22 (Suppl. 6), 13609–13618. [Google Scholar] [CrossRef]
- Kafi, M.A.; Othman, J.B.; Badache, N. A survey on reliability protocols in wireless sensor networks. ACM Comput. Surv. 2017, 50, 1–47. [Google Scholar] [CrossRef]
- Franco, A.; Landfeldt, B.; Körner, U.; Nyberg, C. Statistical guarantee of timeliness in networks of IoT devices. Telecommun. Syst. 2022, 80, 487–496. [Google Scholar] [CrossRef]
- Lomotey, R.K.; Pry, J.C.; Chai, C. Traceability and visual analytics for the Internet-of-Things (IoT) architecture. World Wide Web 2018, 21, 7–32. [Google Scholar] [CrossRef]
- Corallo, A.; Paiano, R.; Guido, A.L.; Pandurino, A.; Latino, M.E.; Menegoli, M. Intelligent monitoring Internet of Things based system for agri-food value chain traceability and transparency: A framework proposed. In Proceedings of the 2018 IEEE Workshop on Environmental, Energy, and Structural Monitoring Systems (EESMS), Salerno, Italy, 21–22 June 2018; pp. 1–6. [Google Scholar]
- Zheng, D.; Jing, C.; Guo, R.; Gao, S.; Wang, L. A traceable blockchain-based access authentication system with privacy preservation in VANETs. IEEE Access 2019, 7, 117716–117726. [Google Scholar] [CrossRef]
- Qi, J.; Gao, T. A privacy-preserving authentication and pseudonym revocation scheme for VANETs. IEEE Access 2020, 8, 177693–177707. [Google Scholar] [CrossRef]
- Pandey, R.D.; Snigdh, I. Validity as a Measure of Data Quality in Internet of Things Systems. Wirel. Pers. Commun. 2022, 126, 933–948. [Google Scholar] [CrossRef]
- Hussain, R.; Bouk, S.H.; Javaid, N.; Khan, A.M.; Lee, J. Realization of VANET-based cloud services through named data networking. IEEE Commun. Mag. 2018, 56, 168–175. [Google Scholar] [CrossRef]
- Al-Omaisi, H.; Sundararajan, E.A.; Alsaqour, R.; Abdullah, N.F.; Abdelhaq, M. A survey of data dissemination schemes in vehicular named data networking. Veh. Commun. 2021, 30, 100353. [Google Scholar] [CrossRef]
- Priyadarshi, D.; Behura, A. Analysis of different iot protocols for heterogeneous devices and cloud platform. In Proceedings of the 2018 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 3–5 April 2018; pp. 0868–0872. [Google Scholar]
- Alani, M.M. Tcp/ip model. In Guide to OSI and TCP/IP Models; Springer: Cham, Switzerland, 2014; pp. 19–50. [Google Scholar]
- Kumar, S. A Review on Client-Server based applications and research opportunity. Int. J. Recent Sci. Res. 2019, 10, 33857–33862. [Google Scholar]
- Dizdarević, J.; Carpio, F.; Jukan, A.; Masip-Bruin, X. A survey of communication protocols for internet of things and related challenges of fog and cloud computing integration. ACM Comput. Surv. 2019, 51, 1–29. [Google Scholar] [CrossRef]
- Shelby, Z.; Hartke, K.; Bormann, C. The constrained application protocol (CoAP) (No. rfc7252). 2014. Available online: https://www.rfc-editor.org/rfc/rfc7252 (accessed on 29 April 2023).
- Chun, S.M.; Park, J.T. Mobile CoAP for IoT mobility management. In Proceedings of the 2015 12th Annual IEEE Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2015; pp. 283–289. [Google Scholar]
- Mishra, B.; Kertesz, A. The use of MQTT in M2M and IoT systems: A survey. IEEE Access 2020, 8, 201071–201086. [Google Scholar] [CrossRef]
- Hussein, M.; Galal, A.I.; Abd-Elrahman, E.; Zorkany, M. Internet of things (IoT) platform for multi-topic messaging. Energies 2020, 13, 3346. [Google Scholar] [CrossRef]
- Kaushik, S.; Poonia, R.C.; Khatri, S.K. Comparative study of various protocols of DDS. J. Stat. Manag. Syst. 2017, 20, 647–658. [Google Scholar] [CrossRef]
- Bendel, S.; Springer, T.; Schuster, D.; Schill, A.; Ackermann, R.; Ameling, M. A service infrastructure for the Internet of Things based on XMPP. In Proceedings of the 2013 IEEE International Conference on Pervasive Computing and Communications Workshops (PERCOM Workshops), San Diego, CA, USA, 18–22 March 2013; pp. 385–388. [Google Scholar]
- Wang, H.; Xiong, D.; Wang, P.; Liu, Y. A lightweight XMPP publish/subscribe scheme for resource-constrained IoT devices. IEEE Access 2017, 5, 16393–16405. [Google Scholar] [CrossRef]
- Hayes, M.; Omar, T. End to end vanet/iot communications a 5g smart cities case study approach. In Proceedings of the 2019 IEEE International Symposium on Technologies for Homeland Security (HST), Woburn, MA, USA, 5–6 November 2019; pp. 1–5. [Google Scholar]
- Kramer, J. Advanced message queuing protocol (AMQP). Linux J. 2009, 2009, 3. [Google Scholar]
- Bhimani, P.; Panchal, G. Message delivery guarantee and status update of clients based on IOT-AMQP. In Intelligent Communication and Computational Technologies: Proceedings of Internet of Things for Technological Development; IoT4TD 2017; Springer: Singapore, 2018; pp. 15–22. [Google Scholar]
- Tilkov, S. A brief introduction to REST. InfoQ, December 2007, 10. Available online: https://www.espinosa-oviedo.com/web-programming/files/readings/A-Brief-Introduction-to-REST.pdf (accessed on 31 April 2023).
- Hireche, S.; Dennai, A.; Kadri, B. Toward a Novel RESTFUL Big Data-Based Urban Traffic Incident Data Web Service for Connected Vehicles. Comput. J. 2023. [Google Scholar] [CrossRef]
- Bayılmış, C.; Ebleme, M.A.; Çavuşoğlu, Ü.; Küçük, K.; Sevin, A. A survey on communication protocols and performance evaluations for Internet of Things. Digit. Commun. Netw. 2022, 8, 1094–1104. [Google Scholar] [CrossRef]
- Soewito, B.; Gunawan, F.E.; Kusuma, I.G.P. Websocket to support real time smart home applications. Procedia Comput. Sci. 2019, 157, 560–566. [Google Scholar] [CrossRef]
- Mitrović, N.; Ðorđević, M.; Veljković, S.; Danković, D. Implementation of WebSockets in ESP32 based IoT Systems. In Proceedings of the 2021 15th International Conference on Advanced Technologies, Systems and Services in Telecommunications (TELSIKS), Nis, Serbia, 20–22 October 2021; pp. 261–264. [Google Scholar]
- Rahman, M.R.; Akhter, S. Real time bi-directional traffic management support system with gps and websocket. In Proceedings of the 2015 IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing, Liverpool, UK, 26–28 October 2015; pp. 959–964. [Google Scholar]
- Ong, L.; Yoakum, J. An Introduction to the Stream Control Transmission Protocol (SCTP) (No. rfc3286). 2002. Available online: https://www.rfc-editor.org/rfc/rfc3286.html (accessed on 31 April 2023).
- Kohler, E.; Handley, M.; Floyd, S. Datagram Congestion Control Protocol (DCCP) (No. rfc4340). 2006. Available online: https://www.rfc-editor.org/rfc/rfc4340.html (accessed on 31 April 2023).
- Iyengar, J.; Thomson, M. QUIC: A UDP-based multiplexed and secure transport. In RFC 9000; IETF 2021; Available online: https://datatracker.ietf.org/doc/html/rfc9000 (accessed on 31 April 2023).
- Abdelsalam, A.; Luglio, M.; Roseti, C.; Zampognaro, F. TCP wave: A new reliable transport approach for future internet. Comput. Netw. 2017, 112, 122–143. [Google Scholar] [CrossRef]
- Al-Saadi, R.; Armitage, G.; But, J.; Branch, P. A survey of delay-based and hybrid TCP congestion control algorithms. IEEE Commun. Surv. Tutor. 2019, 21, 3609–3638. [Google Scholar] [CrossRef]
- Stewart, R.; Metz, C. SCTP: New transport protocol for TCP/IP. IEEE Internet Comput. 2001, 5, 64–69. [Google Scholar] [CrossRef]
- Eklund, J. Latency Reduction for Soft Real-Time Traffic Using SCTP Multihoming. Ph.D. Thesis, Karlstad University Press, Karlstad, Sweden, 2016. [Google Scholar]
- Langley, A.; Riddoch, A.; Wilk, A.; Vicente, A.; Krasic, C.; Zhang, D.; Yang, F.; Kouranov, F.; Swett, I.; Iyengar, J.; et al. The quic transport protocol: Design and internet-scale deployment. In Proceedings of the Conference of the ACM Special Interest Group on Data Communication, Los Angeles, CA, USA, 21–25 August 2017; pp. 183–196. [Google Scholar]
- Megyesi, P.; Krämer, Z.; Molnár, S. How quick is QUIC? In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- Babatunde, O.; Al-Debagy, O. A comparative review of internet protocol version 4 (ipv4) and internet protocol version 6 (ipv6). arXiv 2014, arXiv:1407.2717. [Google Scholar]
- Olsson, J. 6LoWPAN demystified. Tex. Instrum. 2014, 13, 1–13. [Google Scholar]
- Tömösközi, M.; Reisslein, M.; Fitzek, F.H. Packet header compression: A principle-based survey of standards and recent research studies. IEEE Commun. Surv. Tutor. 2022, 24, 698–740. [Google Scholar] [CrossRef]
- Winter, T.; Thubert, P.; Brandt, A.; Hui, J.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, J.P.; Alexander, R. RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks (No. rfc6550). 2012. Available online: https://www.rfc-editor.org/rfc/rfc6550.html (accessed on 5 May 2023).
- Almusaylim, Z.A.; Alhumam, A.; Jhanjhi, N.Z. Proposing a secure RPL based internet of things routing protocol: A review. Ad Hoc Netw. 2020, 101, 102096. [Google Scholar] [CrossRef]
- Al-Masri, E.; Kalyanam, K.R.; Batts, J.; Kim, J.; Singh, S.; Vo, T.; Yan, C. Investigating messaging protocols for the Internet of Things (IoT). IEEE Access 2020, 8, 94880–94911. [Google Scholar] [CrossRef]
- Mijovic, S.; Shehu, E.; Buratti, C. Comparing application layer protocols for the Internet of Things via experimentation. In Proceedings of the 2016 IEEE 2nd International Forum on Research and Technologies for Society and Industry Leveraging a Better Tomorrow (RTSI), Bologna, Italy, 7–9 September 2016; pp. 1–5. [Google Scholar]
- Tandale, U.; Momin, B.; Seetharam, D.P. An empirical study of application layer protocols for IoT. In Proceedings of the 2017 International Conference on Energy, Communication, Data Analytics and Soft Computing (ICECDS), Chennai, India, 1–2 August 2017; pp. 2447–2451. [Google Scholar]
- Bansal, M. Performance Comparison of MQTT and CoAP Protocols in Different Simulation Environments. Inven. Commun. Comput. Technol. 2021, 2017, 549–560. [Google Scholar]
- Safaei, B.; Monazzah, A.M.H.; Bafroei, M.B.; Ejlali, A. Reliability side-effects in Internet of Things application layer protocols. In Proceedings of the 2017 2nd International Conference on System Reliability and Safety (ICSRS), Milan, Italy, 20–22 December 2017; pp. 207–212. [Google Scholar]
- Babovic, Z.B.; Protic, J.; Milutinovic, V. Web performance evaluation for internet of things applications. IEEE Access 2016, 4, 6974–6992. [Google Scholar] [CrossRef]
- Kayal, P.; Perros, H. A comparison of IoT application layer protocols through a smart parking implementation. In Proceedings of the 2017 20th Conference on Innovations in Clouds, Internet and Networks (ICIN), Paris, France, 7–9 March 2017; pp. 331–336. [Google Scholar]
- Ghotbou, A.; Khansari, M. Comparing application layer protocols for video transmission in IoT low power lossy networks: An analytic comparison. Wirel. Netw. 2021, 27, 269–283. [Google Scholar] [CrossRef]
- Chaudhary, A.; Peddoju, S.K.; Kadarla, K. Study of internet-of-things messaging protocols used for exchanging data with external sources. In Proceedings of the 2017 IEEE 14th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Orlando, FL, USA, 22–25 October 2017; pp. 666–671. [Google Scholar]
- Gupta, P. A Survey of Application Layer Protocols for Internet of Things. In Proceedings of the 2021 International Conference on Communication information and Computing Technology (ICCICT), Mumbai, India, 25–27 June 2021; pp. 1–6. [Google Scholar]
- Al-Qassab, R.A.; Aal-Nouman, M.I. Performance Evaluation of CoAP and MQTT_SN Protocols. In Proceedings of the International Conference on Emerging Technology Trends in Internet of Things and Computing, Erbil, Iraq, 6–8 June 2021; Springer International Publishing: Cham, Switzerland, 2021; pp. 223–236. [Google Scholar]
- Polese, M.; Chiariotti, F.; Bonetto, E.; Rigotto, F.; Zanella, A.; Zorzi, M. A survey on recent advances in transport layer protocols. IEEE Commun. Surv. Tutor. 2019, 21, 3584–3608. [Google Scholar] [CrossRef]
- AL-Dhief, F.T.; Sabri, N.; Latiff, N.A.; Malik, N.N.N.A.; Abbas, M.; Albader, A.; Mohammed, M.A.; AL-Haddad, R.N.; Salman, Y.D.; Khanapi, M.; et al. Performance comparison between TCP and UDP protocols in different simulation scenarios. Int. J. Eng. Technol. 2018, 7, 172–176. [Google Scholar]
- Wheeb, A.H. Performance evaluation of UDP, DCCP, SCTP and TFRC for different traffic flow in wired networks. Int. J. Electr. Comput. Eng. 2017, 7, 3552. [Google Scholar] [CrossRef]
- Sahraoui, Y.; Ghanam, A.; Zaidi, S.; Bitam, S.; Mellouk, A. Performance evaluation of TCP and UDP-based video streaming in vehicular ad-hoc networks. In Proceedings of the 2018 International Conference on Smart Communications in Network Technologies (SaCoNeT), El Oued, Algeria, 27–31 October 2018; pp. 67–72. [Google Scholar]
- Park, J.S.; Koh, S.J. Performance Comparison of SCTP and TCP over Linux Platform. J. Korean Inst. Commun. Inf. Sci. 2008, 33, 699–706. [Google Scholar]
- Kharat, P.; Kulkarni, M. Modified QUIC protocol for improved network performance and comparison with QUIC and TCP. Int. J. Internet Protoc. Technol. 2019, 12, 35–43. [Google Scholar] [CrossRef]
- Patel, U.; Chhatbar, J.; Shah, V. Comparitive study on ipv4 and ipv6 internet protocol. Int. J. Adv. Eng. Res. Dev. 2014, 1, 58–62. [Google Scholar]
- Sandur, A.; Giri, A. Performance Analysis of the merged 6L0WPAN-CoAP and RPL-CoAP with different combination of MAC and RDC layer protocols. In Proceedings of the 2022 IEEE 2nd Mysore Sub Section International Conference (MysuruCon), Mysuru, India, 16–17 October 2022; pp. 1–6. [Google Scholar]
- Mahmud, A.; Hossain, F.; Juhin, F.; Choity, T.A. Merging the communication protocols 6LoWPAN-CoAP and RPL-CoAP: Simulation and performance analysis using Cooja simulator. In Proceedings of the 2019 1st International Conference on Advances in Science, Engineering and Robotics Technology (ICASERT), Dhaka, Bangladesh, 3–5 May 2019; pp. 1–6. [Google Scholar]
- Sobin, C.C. A survey on architecture, protocols and challenges in IoT. Wirel. Pers. Commun. 2020, 112, 1383–1429. [Google Scholar] [CrossRef]
- Pohl, M.; Kubela, J.; Bosse, S.; Turowski, K. Performance evaluation of application layer protocols for the internet-of-things. In Proceedings of the 2018 Sixth International Conference on Enterprise Systems (ES), Limassol, Cyprus, 1–2 October 2018; pp. 180–187. [Google Scholar]
- Bilal, M.; Munir, E.U.; Ullah, A. BEMD: Beacon-oriented Emergency Message Dissemination scheme for highways. Ad Hoc Netw. 2023, 142, 103095. [Google Scholar] [CrossRef]
- Callebaut, G.; Leenders, G.; Van Mulders, J.; Ottoy, G.; De Strycker, L.; Van der Perre, L. The art of designing remote iot devices—Technologies and strategies for a long battery life. Sensors 2021, 21, 913. [Google Scholar] [CrossRef]
- Resner, D.; de Araujo, G.M.; Fröhlich, A.A. Design and implementation of a cross-layer IoT protocol. Sci. Comput. Program. 2018, 165, 24–37. [Google Scholar] [CrossRef]
- Singh, M.; Baranwal, G. Quality of service (qos) in internet of things. In Proceedings of the 2018 3rd International Conference on Internet of Things: Smart Innovation and Usages (IoT-SIU), Bhimtal, India, 23–24 February 2018; pp. 1–6. [Google Scholar]
- Beshley, M.; Kryvinska, N.; Seliuchenko, M.; Beshley, H.; Shakshuki, E.M.; Yasar, A.U.H. End-to-End QoS “smart queue” management algorithms and traffic prioritization mechanisms for narrow-band internet of things services in 4G/5G networks. Sensors 2020, 20, 2324. [Google Scholar] [CrossRef]
- Jung, C. Prioritized Data Transmission Mechanism for IoT. KSII Trans. Internet Inf. Syst. 2020, 14, 1–21. [Google Scholar]
- Tandon, A.; Srivastava, P. Location based secure energy efficient cross layer routing protocols for IOT enabling technologies. Int. J. Innov. Technol. Explor. Eng. (IJITEE) 2019, 8, 368–374. [Google Scholar]
- Jiang, S. On reliable data transfer in underwater acoustic networks: A survey from networking perspective. IEEE Commun. Surv. Tutor. 2018, 20, 1036–1055. [Google Scholar] [CrossRef]
- Kamble, S.J.; Kounte, M.R. A Survey on Emergency Vehicle Preemption Methods Based on Routing and Scheduling. Int. J. Comput. Netw. Appl. 2022, 9, 60–71. [Google Scholar] [CrossRef]
- Dey, N.; Neha, N.; Hariprasad, M.; Sandhya, S.; Moharir, M.; Akram, M. A Detail Survey on QUIC and its Impact on Network Data Transmission. In Proceedings of the 2022 6th International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 28–30 April 2022; pp. 378–385. [Google Scholar]
- Eklund, J.; Grinnemo, K.J.; Brunstrom, A. Using multiple paths in SCTP to reduce latency for signaling traffic. Compute. Commun. 2018, 129, 184–196. [Google Scholar] [CrossRef]
- Guo, Q.; Li, L.; Ban, X.J. Urban traffic signal control with connected and automated vehicles: A survey. Transp. Res. Part C Emerg. Technol. 2019, 101, 313–334. [Google Scholar] [CrossRef]
- Lee, W.H.; Chiu, C.Y. Design and implementation of a smart traffic signal control system for smart city applications. Sensors 2020, 20, 508. [Google Scholar] [CrossRef]

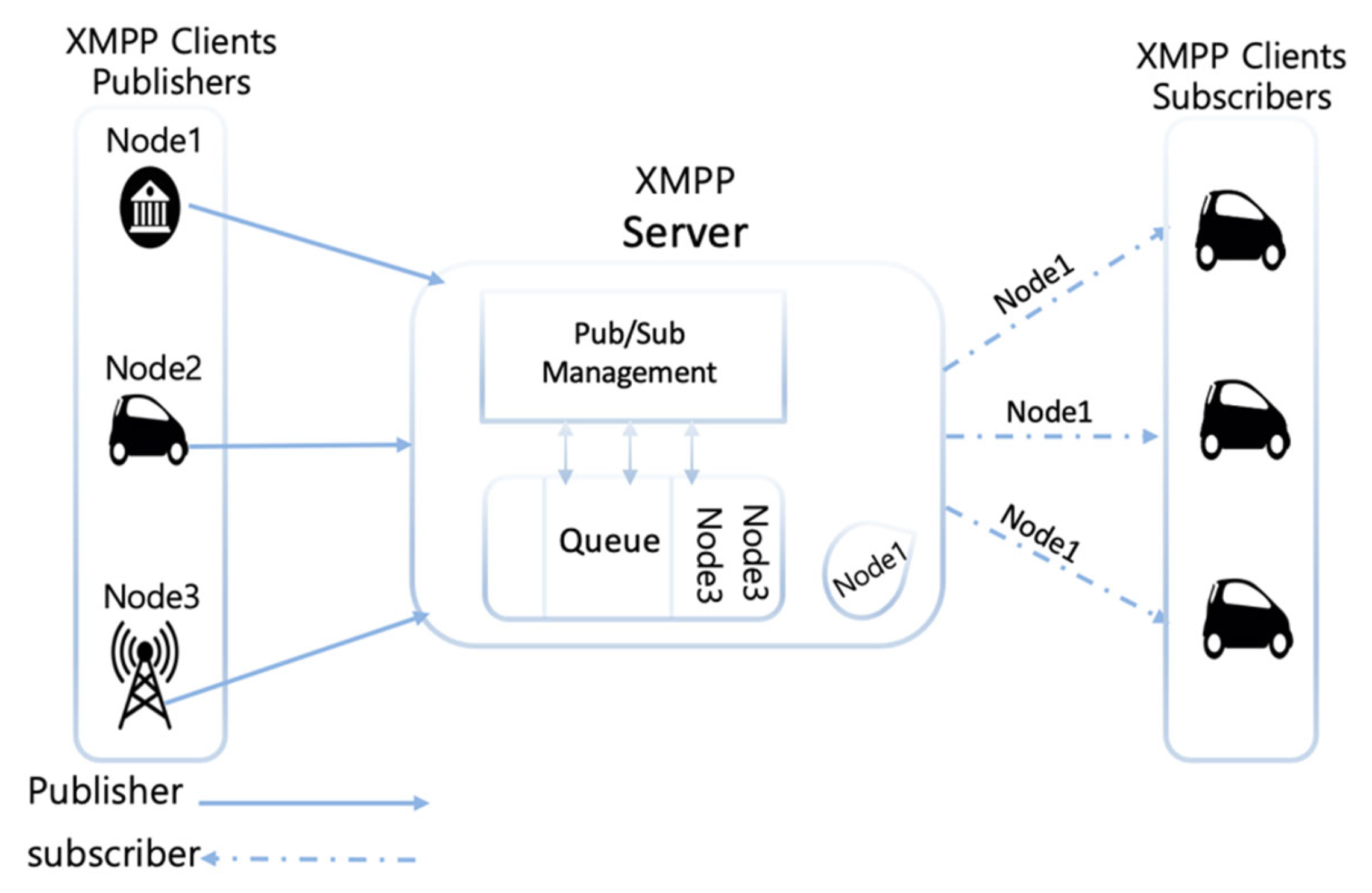
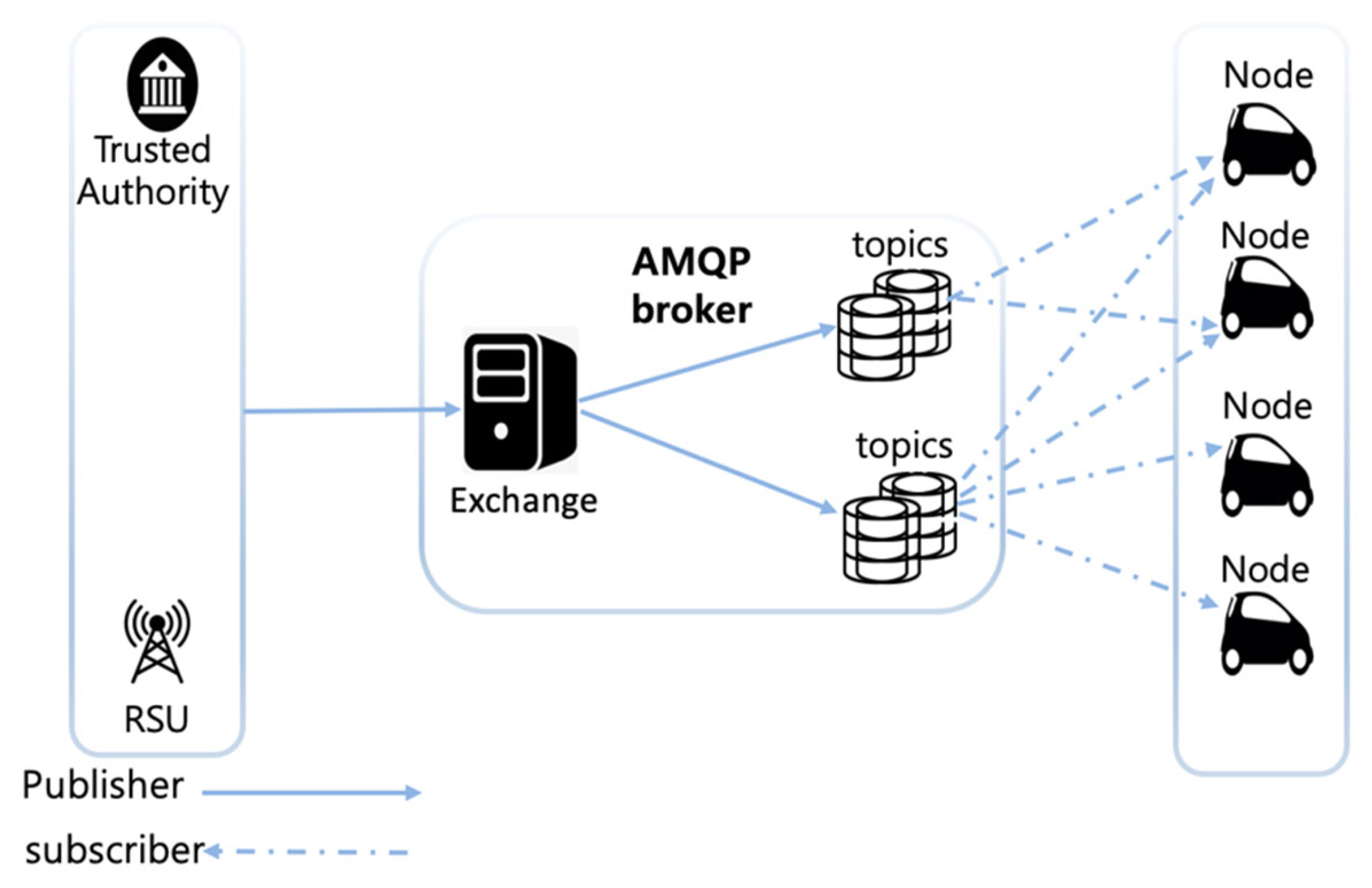

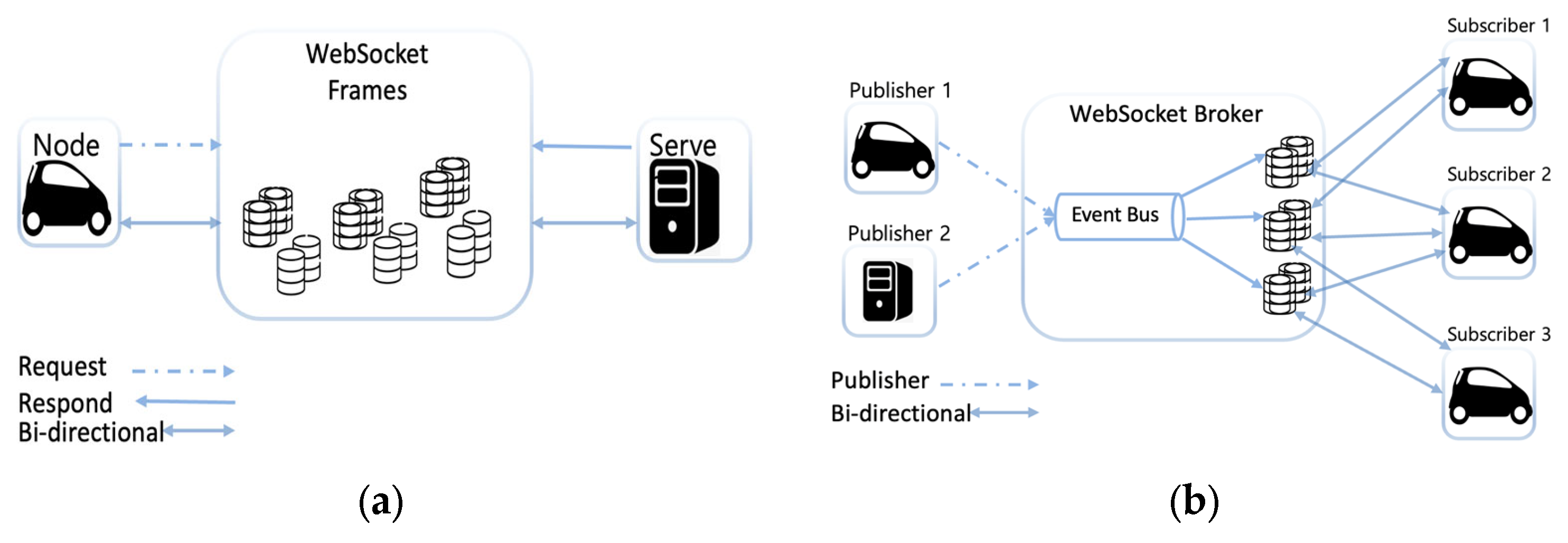
| CoAP | MQTT | HTTP REST | AMQP | XMPP | WebSocket | DDS | |
|---|---|---|---|---|---|---|---|
| Transport | UDP | TCP | TCP | TCP | TCP | TCP | TCP/UDP |
| Security | DTLS | SSL | TLS | TLS | TLS | SSL/TLS | SSL/TLS |
| Model | Req-Rep | Pub-Sub | Req-Rep | Pub-Sub | Pub-Sub Req-Rep | Pub-Sub | Pub-Sub |
| QoS | Yes | Yes | No | Yes | No | No | Yes |
| Architecture Style | Client-Server | Broker | Client-Server | Broker | Client-Server | Client-Server | Distributed |
| Interoperability | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Scalability | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Dynamic Discovery | Yes | No | No | No | NA | No | Yes |
| Authors | Year | Network Protocol Analysed | Experiment Setup and Testbed Environment | Performance Metrics | Best-Performing Protocol | |
|---|---|---|---|---|---|---|
| APPLICATION LAYER | Mijovic et al. [82] | 2016 | CoAP, MQTT, and WebSocket | STM32F411RE, ESP8266, Wi-Fi, and ARM-Mbed | Protocol efficiency and RTT | CoAP |
| Babovic et al. [85] | 2016 | AMQP, DDS, MQTT, and XMPP | Wi-Fi, Adobe Flash, HTML5, and Microsoft Silver | Latency and Throughput Server Utilisation | MQTT | |
| Tandale et al. [83] | 2017 | CoAP, MQTT, and HTTP REST | 4G and Broadband Raspberry Pi Aiocoap, Django & Mosquitto. | Bandwidth Consumption and Upload and Download time | CoAP | |
| Kayal and Perros [87] | 2017 | CoAP, MQTT, XMPP, and WebSocket | Eclipse Mosquitto, Hivemq, Openfire Server, Paho Python Client, and Smack Client | Average response Time Server Utilisation | CoAP | |
| Chaudhary et al. [89] | 2017 | CoAP, MQTT, and AMQP | Raspberry Pi, Wi-Fi, and Wireless RabbitMQ, Mosquitto broker, Libcoap server, Wireshark. Python and C | Packet Overhead, Message throughput, and Bandwidth Utilization | MQTT and CoAP | |
| Sharma and Gondhi [12] | 2018 | AMQP, CoAP, MQTT, and XMPP | Secondary data | Reliability Real-Time communication | CoAP | |
| Ghotbou and Khansari [88] | 2021 | AMQP, CoAP, DDS, MQTT, MQTT-SN, XMPP, WebSocket, HTTP/1.1/2.0, and RTP | Secondary Data | Video Streaming | CoAP | |
| Bansal and Priya [84] | 2021 | MQTT and CoAP | Cooja simulator, NS-3, and OMNeT++ | IoHT environment | ||
| Al-Qassab, and Aal-Nouman [91] | 2022 | CoAP and MQTT-SN | Wireless Sensor Networks, Contiki-O, and Cooja | Power consumption | CoAP | |
| TRANSPORT LAYER | Park and Koh [96] | 2008 | SCTP and TCP | Linus | Throughput, Multi-homing. | TCP |
| Wheeb [94] | 2017 | UDP, DCCP, SCTP, and TFRC | Wired Network and NS 2 | Throughput, End-to-End Video Streaming | SCTP DCCP UDP | |
| Sahraoui et al. [95] | 2018 | TCP and UDP | VANET, NS 2, and SUMO | Throughput, Packet Delivery Ratio, End-to-End Delay, and PSNR. | UDP | |
| AL-Dhief et al. [93] | 2018 | TCP and UDP | NS-2 | Bandwidth, End-to-End Delay, Throughput, Packet Delivery Ratio, Packet Size, and Packet Loss Ratio. | TCP | |
| Kharat, and Kulkarni [97] | 2019 | QUIC, Mod QUIC, and TCP | Wi-Fi and Client-server model | Throughput, delay, and loss rates. | ModQUIC | |
| INTERNET LAYER | Patel et al. [98] | 2014 | IPv4 and Ipv6 | Secondary data | Address space, Throughput, Security, and Jitter value | Ipv6 |
| Mahmud et al. [100] | 2019 | 6LoWPAN-CoAP and RPL-CoAP | Cooja and Ubuntu OS | Received packets, simulation time, and communication range. | RPL-CoAP | |
| Sandur and Giri [99] | 2022 | 6LoWPAN-CoAP and RPL-CoAP | Ubuntu OS and Cooja | Average Latency and Packet Delivery Ratio | RPL-CoAP |
| Application Layer | Transport Layer | Internet Layer | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| DQ Dimensions | AMQP | CoAP | DDS | MQTT | XMPP | HTTP REST | WebSocket | TCP | UDP | QUICK | DCCP | SCTP | Ipv6 | RPL | 6LoWPAN |
| Availability | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | |||||
| Data Accuracy | √ | √ | √ | √ | √ | ||||||||||
| Completeness | √ | √ | √ | √ | √ | √ | |||||||||
| Confidentiality | √ | √ | √ | √ | |||||||||||
| Consistency | √ | √ | √ | √ | √ | √ | √ | √ | |||||||
| Data Integrity | √ | √ | √ | √ | √ | √ | √ | √ | √ | ||||||
| Reliability | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | ||||
| Timeliness | √ | √ | √ | √ | √ | √ | √ | ||||||||
| Traceability | |||||||||||||||
| Validity | |||||||||||||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Suleman, D.; Shibl, R.; Ansari, K. Investigation of Data Quality Assurance across IoT Protocol Stack for V2I Interactions. Smart Cities 2023, 6, 2680-2705. https://doi.org/10.3390/smartcities6050121
Suleman D, Shibl R, Ansari K. Investigation of Data Quality Assurance across IoT Protocol Stack for V2I Interactions. Smart Cities. 2023; 6(5):2680-2705. https://doi.org/10.3390/smartcities6050121
Chicago/Turabian StyleSuleman, Danladi, Rania Shibl, and Keyvan Ansari. 2023. "Investigation of Data Quality Assurance across IoT Protocol Stack for V2I Interactions" Smart Cities 6, no. 5: 2680-2705. https://doi.org/10.3390/smartcities6050121
APA StyleSuleman, D., Shibl, R., & Ansari, K. (2023). Investigation of Data Quality Assurance across IoT Protocol Stack for V2I Interactions. Smart Cities, 6(5), 2680-2705. https://doi.org/10.3390/smartcities6050121





