A Novel Security Architecture for WSN-Based Applications in Smart Grid
Abstract
:1. Introduction
1.1. Background
1.2. Problem Statement
1.3. Contribution
- A novel clustering algorithm is proposed to elect the CHs. Given the sensitivity of their role, many metrics are considered in the election process, particularly the trust metric of the sensor nodes and the number of trust neighbors. To balance the load on the CHs, the size of the cluster is also considered.
- Then, a distributed PKI is designed where the CHs play the role of the certification authority in their clusters. In each cluster, a registration authority (RA) is responsible for checking the authenticity of the sensor nodes before being certified.
- Afterward, the performance of the clustering algorithm and the robustness of the architecture is evaluated using simulation.
2. Security in WSN-Based SG
2.1. Attacks
- DoS
- Sinkhole Attack
- Sybil Attack
- Traffic analysis Attack
2.2. Related Work
3. Clustering Protocols in WSNs
3.1. Classification of Clustering Protocols in WSNs
- Probabilistic/non-probabilistic clustering: each sensor node is assigned with a probability used as the main parameter to select the cluster head nodes [13,19]. In non- probabilistic clustering, many of the basic and specific factors such as the location of the nodes, the number of neighbors, and security factors [20] are considered in the election process of CHs [13].
- Clustering in a homogeneous/heterogeneous network: In a homogeneous network, the nodes in the same level are fully equivalent to each other. The sensor nodes are equivalent in initial energy, sensing limits, and communication limits. Therefore, in the same conditions, the sensor nodes have a similar response and every node can be a CH. In homogeneous networks, clustering algorithms are divided into two types: energy-based and hybrid parameters-based [14]. In a heterogeneous network, the sensor nodes differ in their efficiency, resources, energy, and power. Hence, the sensor nodes are classified into two classes: super-node and normal node. A super-node is a sensor node that has advanced hardware and high processing capability. The normal node has a lower capability. The CHs are selected from super-nodes. Heterogeneous networks are also divided into two types based on the parameters of CHs selection: energy-based and hybrid parameters-based [14].
- Energy-based clustering: To select the optimal cluster head in a heterogeneous network, in this type of algorithm, the sensor node with the highest energy level has the priority to be CH [14].
- Hybrid parameters-based clustering: the clustering algorithms select CHs based on different parameters, such as the size of the cluster, the neighbors’ information, the distance between the nodes and the base station, etc. [14].
3.2. Related Work
- Cluster Size: the formed clusters may have an equal or unequal size that relies on the number of nodes in the cluster. In equal size clustering, all clusters have a fixed and predefined size, however, in unequal-size clustering, the clusters have variable sizes [27].
- Heterogeneity of the energy level: the heterogeneity level of WSNs is linked to the energy levels of the nodes. A two-level WSNs contains two energy levels for nodes named advance and normal node. The advance has more energy compared to a normal node [28].
- Heterogeneity: the WSNs are classified as homogeneous or heterogeneous based on the capabilities of the sensor nodes such as power, processing, and storage [29].
- CH selection: the CH can be selected using different parameters: Energy-based or hybrid-based. The selection may also be probabilistic or non-probabilistic.
- Routing approach: two approaches of routing are possible: classical routing and optimized routing. In classical routing, the selection of the base nodes is based on a timer function, which leads to irregular traffic flow in various base nodes. Optimized routing approaches are based on optimization algorithms, such as Fuzzy logic (FL), Genetic Algorithm (GA), and PSO [28].
- Clustering control: the control of the clustering in WSNs can be centralized or distributed. In the centralized approach, the sink node controls the clustering and needs global information (e.g., energy level) of the network. Moreover, it is responsible for the selection of the CHs. In a distributed approach, the sensor nodes cooperate to create the clusters [28].
- Inter-Clustering Routing: The sensor nodes and particularly the CH can communicate with the sink node in a single-hop or a multi-hop. In single-hop, the sensor nodes communicate directly with the sink node. However, in multi-hop, the sensor nodes communicate with the sink node via a mediator node in multi-hop routing [28].
- Intra-Clustering Routing: Member nodes can communicate with the CH in a single-hop or a multi-hop. In single-hop, the member nodes communicate directly with the CH, but in multi-hop, the member nodes communicate with it via a mediator node [28].
3.3. Discussion
4. Methodology
4.1. Overview
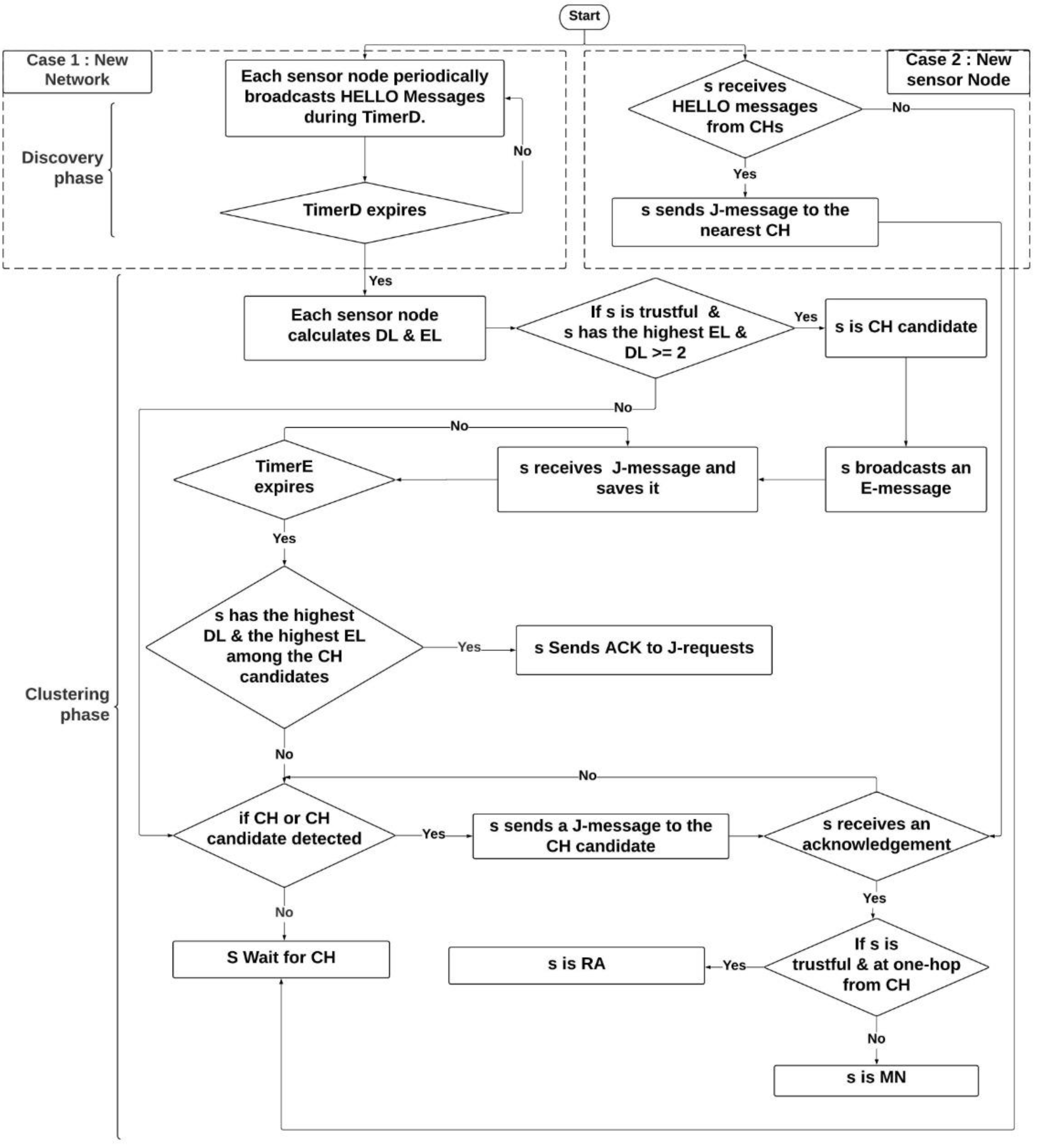
4.2. Clustering Algorithm
4.3. The Characteristics of the Proposed PKI
- CA: it is the CH of the cluster. Its role is to manage short-term certificates for RAs and MNs.
- RA: it is a truthful node at 1 hop of the CA. Its role is to check certification requests received from MNs before forwarding them to the CA. The certification request is valid only if the requester node has a valid long-term certificate.
- MN: It is a regular node with no particular role in the cluster.
5. Results
5.1. Simulation Setup
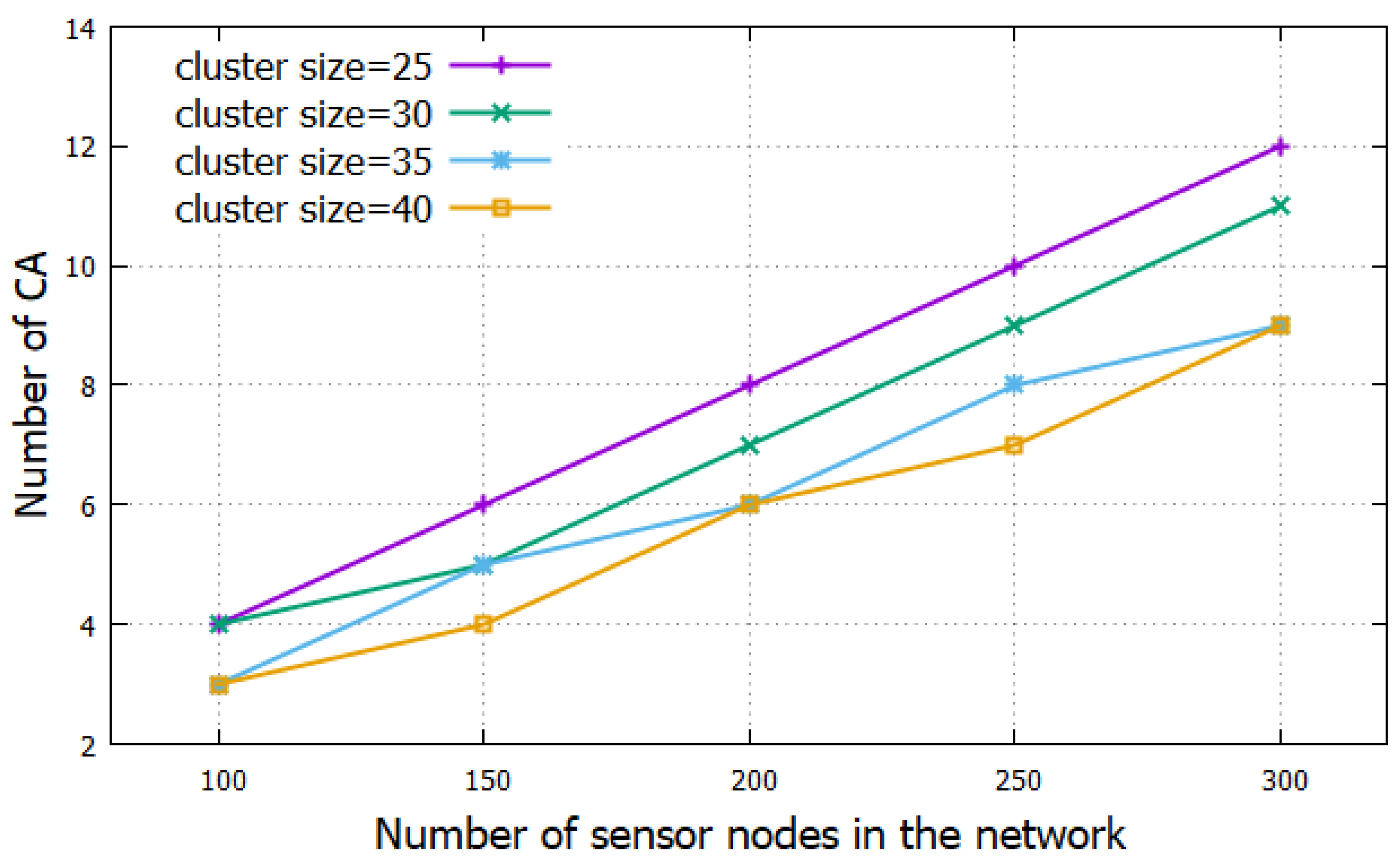
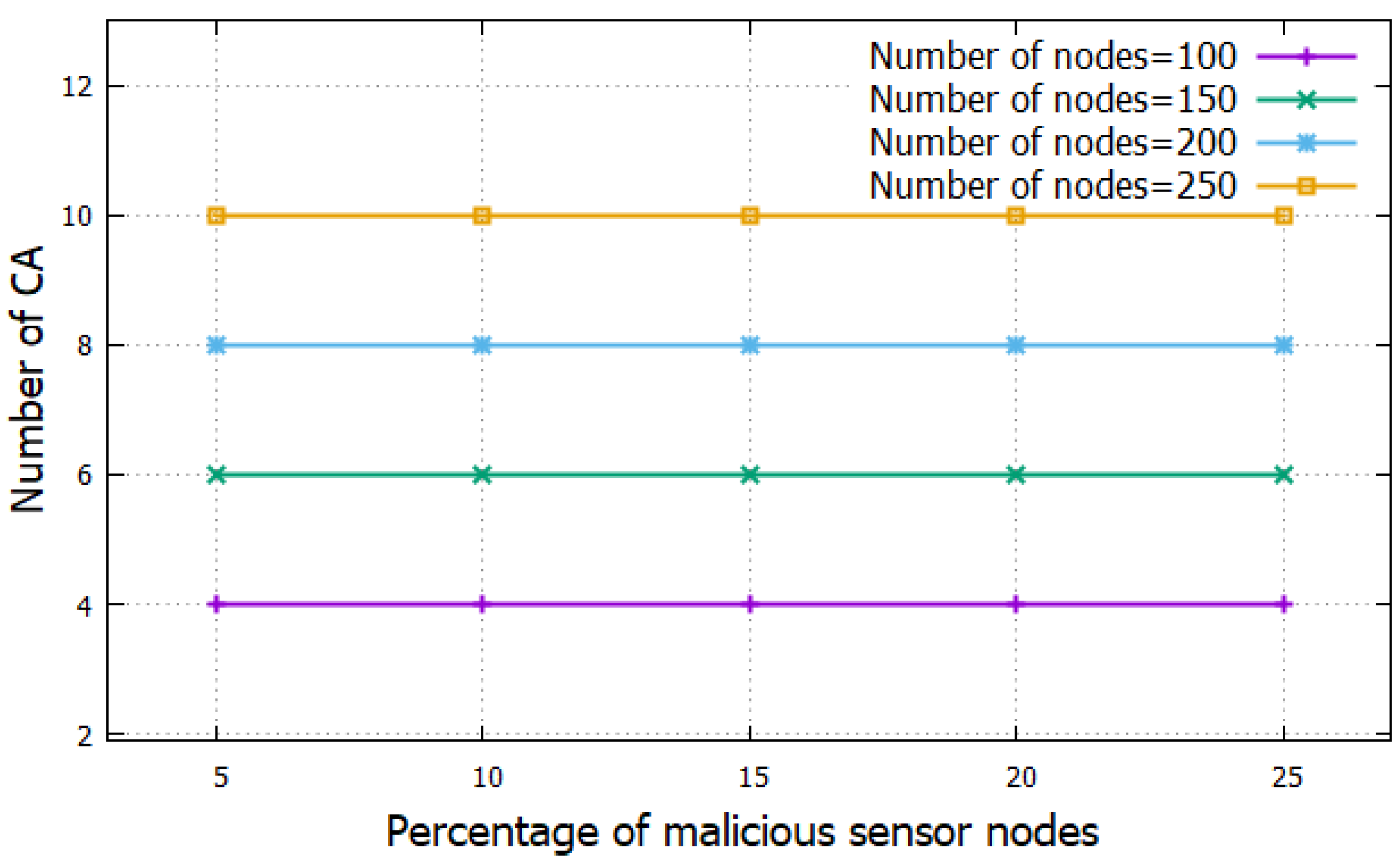
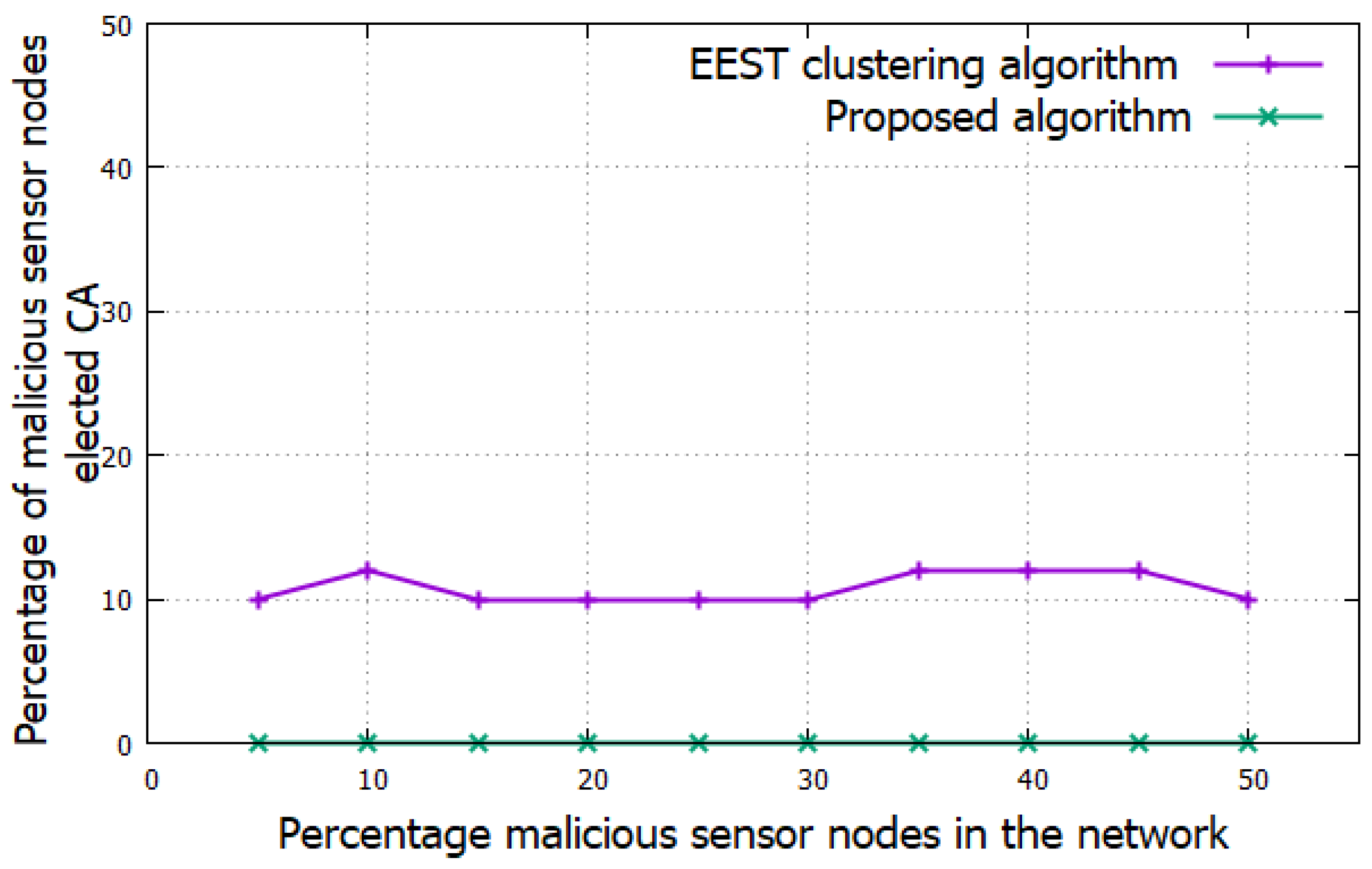
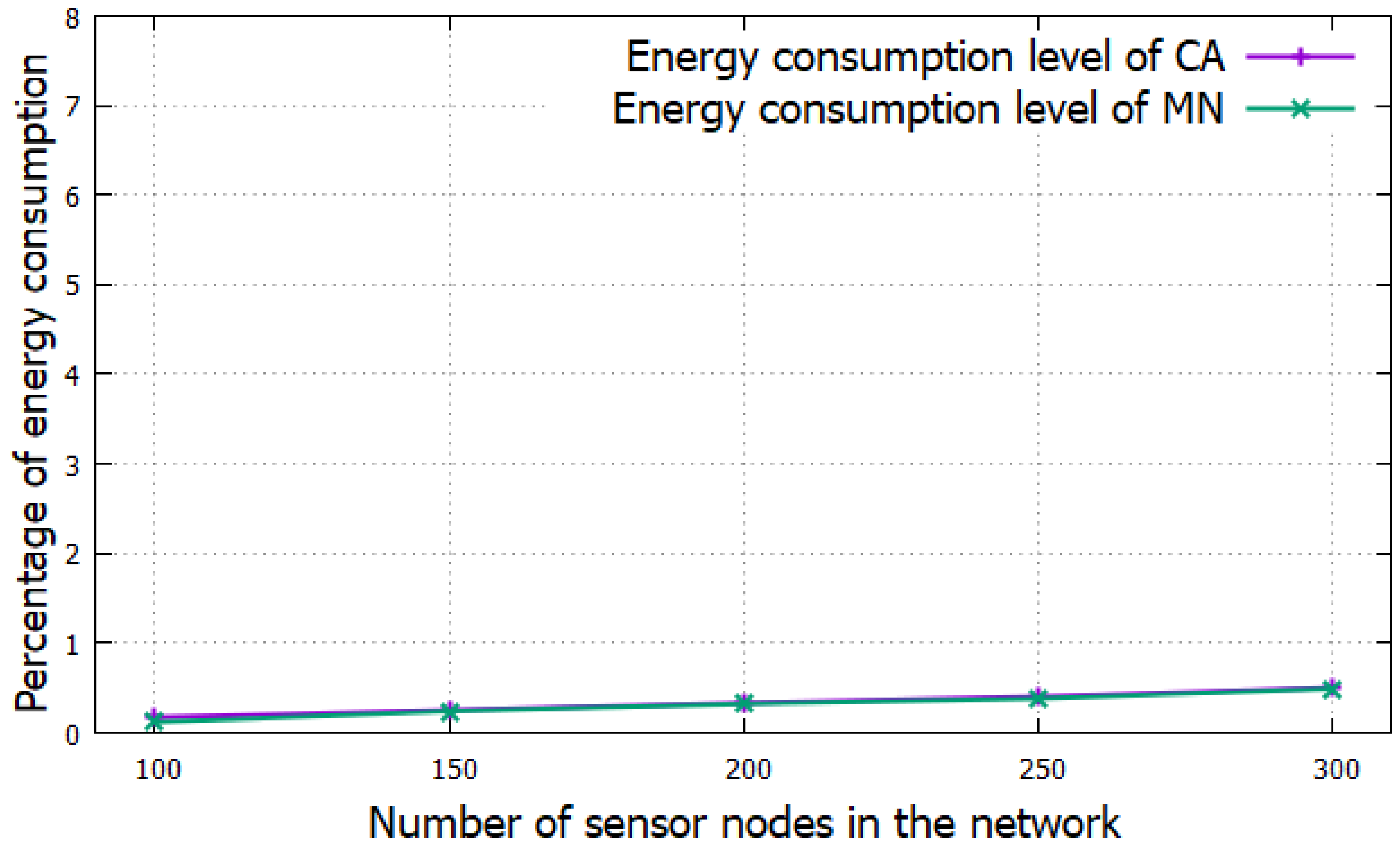
5.2. Simulation Results
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Rekik, S.; Baccour, N.; Jamiel, M.; Drira, K. Wireless sensor network based smart grid communications: Challenges, protocol optimizations, and validation platforms. Wirel. Pers. Commun. 2017, 95, 4025–4047. [Google Scholar] [CrossRef] [Green Version]
- Tuna, G.; Örenbaş, H.; Daş, R.; Kogias, D.; Baykara, M.; Gülez, K. Information security threats and an easy-to-implement attack detection framework for wireless sensor network-based smart grid applications. In Proceedings of the 5th International Conference on Materials and Applications for Sensors and Transducers, Mykonos, Greece, 27–30 September 2015. [Google Scholar]
- Mehmood, G.; Khan, M.S.; Waheed, A.; Zareei, M.; Fayaz, M.; Sadad, T.; Kama, N.; Azmi, A. An Efficient and Secure Session Key Management Scheme in Wireless Sensor Network. Complexity 2021, 2021, 6577492. [Google Scholar] [CrossRef]
- Amutha, J.; Sharma, S.; Sharma, S.K. Strategies based on various aspects of clustering in wireless sensor networks using classical, optimization and machine learning techniques: Review, taxonomy, research findings, challenges and future directions. Comput. Sci. Rev. 2021, 40, 100376. [Google Scholar] [CrossRef]
- Chhaya, L.; Sharma, P.; Bhagwatikar, G.; Kumar, A. Wireless sensor network based smart grid communications: Cyberattacks, intrusion detection system and topology control. Electronics 2017, 6, 5. [Google Scholar] [CrossRef]
- Liu, Y. Wireless Sensor Network Applications in Smart Grid: Recent Trends and Challenges. Int. J. Distrib. Sens. Netw. 2012, 8, 1–8. [Google Scholar] [CrossRef]
- Alfandi, O.; Bochem, A.; Kellner, A.; Hogrefe, D. Simple secure PKI-based scheme for wireless sensor networks. In Proceedings of the 2011 Seventh International Conference on Intelligent Sensors, Sensor Networks and Information Processing, Adelaide, Australia, 6–9 December 2011; pp. 359–364. [Google Scholar] [CrossRef]
- Nandhini, M.; Praveenkumar, B. An Implementation of Public Key Infrastructure Using Wireless Communication Networks. Int. J. Grid Distrib. Comput. 2015, 8, 35–42. [Google Scholar]
- Mahmoud, M.M.E.A.; Mišić, J.; Shen, X. A scalable public key infrastructure for smart grid communications. In Proceedings of the 2013 IEEE Global Communications Conference (GLOBECOM), Atlanta, GA, USA, 9–13 December 2013; pp. 784–789. [Google Scholar] [CrossRef]
- He, D.; Chan, S.; Zhang, Y.; Guizani, M.; Chen, C.; Bu, J. An enhanced public key infrastructure to secure smart grid wireless communication networks. IEEE Netw. 2014, 28, 10–16. [Google Scholar] [CrossRef]
- Shahzad, F.; Pasha, M.; Ahmad, A. A Survey of Active Attacks on Wireless Sensor Networks and their Countermeasures. IJCSIS 2017, 14, 54–65. [Google Scholar]
- Kivande, M.V.; Wade, A.M. Adaptive and Channel Aware Forwarding Attack Detection for Mobile Sensor in WSN with Security of Data. Int. J. Eng. Sci. 2017, 7, 13256. [Google Scholar]
- Riaz, M.N. Clustering algorithms of wireless sensor networks: A survey. Int. J. Wirel. Microw. Technol. 2018, 8, 40–53. [Google Scholar]
- Rostami, A.S.; Badkoobe, M.; Mohanna, F.; Keshavarz, H.; Hosseinabadi, A.A.R.; Sangaiah, A.K. Survey on clustering in heterogeneous and homogeneous wireless sensor networks. J. Supercomput. 2018, 74, 277–323. [Google Scholar] [CrossRef]
- Fanian, F.; Rafsanjani, M.K. Cluster-based routing protocols in wireless sensor networks: A survey based on methodology. J. Netw. Comput. Appl. 2019, 142, 111–142. [Google Scholar] [CrossRef]
- Arjunan, S.; Sujatha, P. A survey on unequal clustering protocols in Wireless Sensor Networks. J. King Saud Univ.-Comput. Inf. Sci. 2019, 31, 304–317. [Google Scholar] [CrossRef]
- Zeb, A.; Islam, A.K.M.M.; Zareei, M.; Al Mamoon, I.; Mansoor, N.; Baharun, S.; Katayama, Y.; Komaki, S. Clustering Analysis in Wireless Sensor Networks: The Ambit of Performance Metrics and Schemes Taxonomy. Int. J. Distrib. Sens. Netw. 2016, 12, 1–12. [Google Scholar] [CrossRef] [Green Version]
- El Khediri, S. Wireless sensor networks: A survey, categorization, main issues, and future orientations for clustering protocols. Computing 2022, 104, 1–63. [Google Scholar] [CrossRef]
- Zahedi, A. An efficient clustering method using weighting coefficients in homogeneous wireless sensor networks. Alex. Eng. J. 2018, 57, 695–710. [Google Scholar] [CrossRef]
- Koucheryavy, A.; Salim, A. Cluster head selection for homogeneous Wireless Sensor Networks. In Proceedings of the 2009 11th International Conference on Advanced Communication Technology, Gangwon, Korea, 15–18 February 2009. [Google Scholar]
- Rehman, E.; Sher, M.; Naqvi, S.H.A.; Khan, K.B.; Ullah, K. Energy Efficient Secure Trust Based Clustering Algorithm for Mobile Wireless Sensor Network. J. Comput. Netw. Commun. 2017, 2017, 1630673. [Google Scholar] [CrossRef]
- Singh, S.P.; Sharma, S.C. Proceeding of the International Conference on Computer Networks, Big Data and IoT (ICCBI—2018), Madurai, India, 19–20 December 2018; Springer International Publishing: Cham, Switzerland, 2020; pp. 1775–1780. [Google Scholar]
- Xie, B.; Wang, C. An improved distributed energy efficient clustering algorithm for heterogeneous WSNs. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017. [Google Scholar]
- Pathak, G.R.; Patil, S.H.; Tryambake, J.S. Efficient and trust based black hole attack detection and prevention in WSN. Int. J. Comput. Sci. Bus. Inform. 2014, 14, 93–103. [Google Scholar]
- Wang, J.; Cao, Y.; Li, B.; Kim, H.-J.; Lee, S. Particle swarm optimization based clustering algorithm with mobile sink for WSNs. Futur. Gener. Comput. Syst. 2017, 76, 452–457. [Google Scholar] [CrossRef]
- Otoum, S.; Kantarci, B.; Mouftah, H.T. Hierarchical trust-based black-hole detection in WSN-based smart grid monitoring. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017. [Google Scholar] [CrossRef]
- Belabed, F.; Bouallegue, R. An optimized weight-based clustering algorithm in wireless sensor networks. In Proceedings of the 2016 International Wireless Communications and Mobile Computing Conference (IWCMC), Paphos, Cyprus, 5–9 September 2016; pp. 757–762. [Google Scholar] [CrossRef]
- Sabor, N.; Sasaki, S.; Abo-Zahhad, M.; Ahmed, S. A comprehensive survey on hierarchical-based routing protocols for mobile wireless sensor networks: Review, taxonomy, and future directions. Wirel. Commun. Mob. Comput. 2017, 2017, 2818542. [Google Scholar] [CrossRef]
- Velmurugan, S.; Logashanmugham, E. Secure Mobile Beacon Based Obstacle Awareness in WSN. Inst. Integr. Omics Appl. Biotechnol. 2017, 8, 1–7. [Google Scholar]
- Varga, A. Using the OMNeT++ discrete event simulation system in education. IEEE Trans. Educ. 1999, 42, 11. [Google Scholar] [CrossRef]
- Castalia. Available online: http://cpham.perso.univ-pau.fr/ENSEIGNEMENT/PAU-UPPA/INGRES-M1/Castalia%20-%20User%20Manual.pdf (accessed on 25 October 2021).



| Authors | Routing Approach (Classical, Optimized) | Control Manner (Centralized C, Distributed D) | Clustering Properties | Heterogeneity | CH Selection | Energy Level Heterogeneity | |||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Clusters Size (Variable V/Fixed F) | Inter-Cluster Routing | Intra-Cluster Routing | Homogeneous/Heterogeneous Network | Probabilistic | Non- Probabilistic | ||||||
| Hybrid Based | Energy-Based | Hybrid Based | Energy-Based | ||||||||
| Zahedi et al. [19] | Classical | D | V | Single-Hop | Single-Hop | Homogeneous | - | √ | - | - | One Level |
| Singh et al. [22] | Optimized | C | V | Multi-Hop | Single-Hop | Homogeneous | √ | - | - | - | One Level |
| B. Xie and C. Wang [23] | Classical | D | V | Single-Hop | Single-Hop | Heterogeneous | - | √ | - | - | Multi-level |
| Pathak et al. [24] | Classical | D | V | Multi-Hop | Single-Hop | Heterogeneous | √ | - | - | - | Multi-level |
| Wang, Jin et al. [25] | Optimized | C | V | Multi-Hop | Multi-Hop | Homogeneous | - | - | - | √ | One Level |
| Otoum et al. [26] | Classical | C | V | Single-Hop | Single-Hop | Homogeneous | - | - | - | √ | One Level |
| Belabed, Fatma, and Ridha Bouallegue [27] | Classical | C | F | Single-Hop | Single-Hop | Homogeneous | - | - | √ | - | One Level |
| Rehman, Eid et al. [21] | Classical | D | V | Single-Hop | Single-Hop | Heterogeneous | - | - | √ | - | Two-level |
| Proposed Algorithm | Classical | D | F | Single-Hop | Single-Hop | Homogeneous | - | - | √ | - | One-level |
| Parameters | Values |
|---|---|
| The number of sensor nodes | 200 |
| Network size | 100 × 100 m |
| Max number of nodes in a cluster | 25 |
| Percentage of malicious sensor nodes | (5, 25) |
| Simulation duration | 2000 s |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aljadani, N.; Gazdar, T. A Novel Security Architecture for WSN-Based Applications in Smart Grid. Smart Cities 2022, 5, 633-649. https://doi.org/10.3390/smartcities5020033
Aljadani N, Gazdar T. A Novel Security Architecture for WSN-Based Applications in Smart Grid. Smart Cities. 2022; 5(2):633-649. https://doi.org/10.3390/smartcities5020033
Chicago/Turabian StyleAljadani, Nouf, and Tahani Gazdar. 2022. "A Novel Security Architecture for WSN-Based Applications in Smart Grid" Smart Cities 5, no. 2: 633-649. https://doi.org/10.3390/smartcities5020033
APA StyleAljadani, N., & Gazdar, T. (2022). A Novel Security Architecture for WSN-Based Applications in Smart Grid. Smart Cities, 5(2), 633-649. https://doi.org/10.3390/smartcities5020033





