Identify a Spoofing Attack on an In-Vehicle CAN Bus Based on the Deep Features of an ECU Fingerprint Signal
Abstract
:1. Introduction
- 1)
- The RNN-LSTM is proposed to extract the deep features and authenticate CAN data frame IDs based on the inherent characteristics of the electronic device. Experimental results show that our method improves the accuracy of ECU identification.
- 2)
- A simulation model of the ECU’s communication physical layer is proposed to produce simulating data.
- 3)
- The acceleration of the classifier with FPGA is proposed by parallel processing to satisfy real-time detection.
2. Related Works and Motivation
3. Backgrounds
4. System Model
4.1. CAN Communication Physical Layer Model
4.2. Spoofing Attack Model on CAN Bus
4.3. Recurrent Neural Network with Long Short-Term Memory
4.4. Real-Time RNN-LSTM Acceleration Based on FPGA
- 1)
- To optimize the computation procedure, we firstly deal with a higher computation of LSTM gates based on FPGA. For the flatted multiplications on the matrix of each LSTM gate, our accelerator can achieve the computation, where , , , and . The non-linear activation function sigmoid and tanh includes the exponentiation and division, which are very expensive in FPGA. So, we approximated them with segmented linear functions hard_sigmoid and hard_tanh, which are calculated as follows:
- 2)
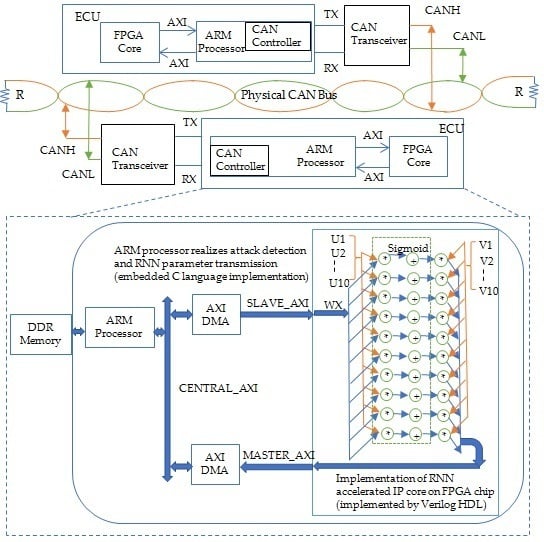
- To reduce the communication consumption, we must consider the storage position in FPGA for the weights and biases of the RNN model, which are usually near 10M. We have adopted a compromise between in-vehicle CAN communication and limited memory space in the ECU platform, where the network parameters, the matrix, or the vector are saved in external DRAM and can be read into FPGA through AXI4 stream interface. An overview of our RNN-SLTM acceleration implementation on the ZYNQ-7010 embedded platform is presented in Figure 7.
5. Experimental Results
5.1. Simulation Results
5.2. Identifying the Spoofing Attack
5.3. Attack Accelerated Detection Based on FPGA
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Tuohy, S.; Glavin, M.; Hughes, C.; Jones, E.; Trivedi, M.; Kilmartin, L. Intra-vehicle networks: A review. IEEE Trans. Intell. Transp. Syst. 2015, 16, 534–545. [Google Scholar] [CrossRef]
- Miller, C.; Valasek, C. Remote exploitation of an unaltered passenger vehicle. Black Hat USA 2015, 2015, 91. [Google Scholar]
- Groza, B.; Murvay, P.-S.; Murvay, S. Security solutions for the controller area network: Bringing authentication to in-vehicle networks. IEEE Veh. Technol. Mag. 2018, 13, 40–47. [Google Scholar] [CrossRef]
- Avatefipour, O.; Hafeez, A.; Tayyab, M.; Malik, H. Linking received packet to the transmitter through physical-fingerprinting of controller area network. In Proceedings of the 2017 IEEE Workshop on Information Forensics and Security (WIFS), Rennes, France, 4–7 December 2017; pp. 1–6. [Google Scholar]
- Choi, W.; Jo, H.J.; Woo, S.; Chun, J.Y.; Park, J.; Lee, D.H. Identifying ECUs using inimitable characteristics of signals in controller area networks. IEEE Trans. Veh. Technol. 2018, 67, 4757–4770. [Google Scholar] [CrossRef]
- Murvay, P.-S.; Groza, B. Source identification using signal characteristics in controller area networks. IEEE Signal Process. Lett. 2014, 21, 395–399. [Google Scholar] [CrossRef]
- Choi, W.; Joo, K.; Jo, H.J.; Park, M.C.; Lee, D.H. VoltageIDS: Low-level communication characteristics for automotive intrusion detection system. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2114–2129. [Google Scholar] [CrossRef]
- Woo, S.; Jo, H.J.; Lee, D.H. A practical wireless attack on the connected car and security protocol for in-vehicle CAN. IEEE Trans. Intell. Transp. Syst. 2015, 16, 993–1006. [Google Scholar] [CrossRef]
- Woo, S.; Jo, H.J.; Kim, I.S.; Lee, N.H. A practical security architecture for in-vehicle CAN-FD. IEEE Trans. Intell. Transp. Syst. 2016, 17, 2248–2261. [Google Scholar] [CrossRef]
- Zago, G.M.; de Freitas, E.P. A quantitative performance study on CAN and CAN FD vehicular networks. IEEE Trans. Ind. Electron. 2018, 65, 4413–4422. [Google Scholar] [CrossRef]
- Theissler, A. Anomaly detection in recordings from in-vehicle networks. In Proceedings of the First International Workshop, BigDap 2014, Madrid, Spain, 11–12 September 2014; p. 23. [Google Scholar]
- Kang, M.-J.; Kang, J.-W. Intrusion detection system using deep neural network for in-vehicle network security. PLoS ONE 2016, 11, e0155781. [Google Scholar] [CrossRef] [PubMed]
- Taylor, A.; Leblanc, S.; Japkowicz, N. Anomaly detection in automobile control network data with long short-term memory networks. In Proceedings of the 2016 IEEE International Conference on Data Science and Advanced Analytics (DSAA), Montreal, QC, Canada, 17–19 October 2016. [Google Scholar]
- Cho, K.-T.; Shin, K.G. Fingerprinting electronic control units for vehicle intrusion detection. In Proceedings of the 25th USENIX Security Symposium, Austin, TX, USA, 10–12 August 2016. [Google Scholar]
- Cho, K.-T.; Shin, K.G. Error handling of in-vehicle networks makes them vulnerable. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016. [Google Scholar]
- Iehira, K.; Inoue, H.; Ishida, K. Spoofing attack using bus-off attacks against a specific ECU of the CAN bus. In Proceedings of the 15th EEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 12–15 January 2018. [Google Scholar]
- Song, M.; Kim, H.R.; Kim, H.K. Intrusion detection system based on the analysis of time intervals of CAN messages for in-vehicle network. In Proceedings of the 2016 International Conference on Information Networking (ICOIN), Kota Kinabalu, Malaysia, 13–15 January 2016. [Google Scholar]
- Van Herrewege, A.; Singelee, D.; Verbauwhede, I. CANAuth-A simple, backward compatible broadcast authentication protocol for CAN bus. In Proceedings of the ECRYPT Workshop on Lightweight Cryptography, Louvain-la-Neuve, Belgium, 28–29 November 2011. [Google Scholar]
- Kurachi, R.; Matsubara, Y.; Takada, H.; Adachi, N.; Miyashita, Y.; Horihata, S. CaCAN-centralized authentication system in CAN (Controller Area Network). In Proceedings of the 12th International Conference on Embedded Security in Cars (ESCAR 2014), Hamburg, Germany, 18–19 November 2014. [Google Scholar]
- Gerdes, R.M.; Mina, M.; Russell, S.F.; Daniels, T.E. Physical-layer identification of wired ethernet devices. IEEE Trans. Inf. Forensics Secur. 2012, 7, 1339–1353. [Google Scholar] [CrossRef]
- Farsi, M.; Ratcliff, K.; Barbosa, M. An overview of controller area network. Comput. Control Eng. J. 1999, 10, 113–120. [Google Scholar] [CrossRef]
- IEEE. 524-2016—IEEE Guide for the Installation of Overhead Transmission Line Conductors; IEEE: Piscataway, NJ, USA, 2017; pp. 1–162. [Google Scholar]
- Zdenek, K.; Jiri, S. Simulation of CAN bus physical layer using SPICE. In Proceedings of the 2013 International Conference on Applied Electronics, Pilsen, Czech Republic, 10–12 September 2013. [Google Scholar]
- Shao, H.; Luo, F.; Xu, J. Simulation of CAN physical layer based on SystemVision. In Proceedings of the 12th International Conference on Natural Computation, Fuzzy Systems and Knowledge Discovery (ICNC-FSKD), Changsha, China, 13–15 August 2016. [Google Scholar]
- Poudel, B.; Giri, N.K.; Munir, A. Design and comparative evaluation of GPGPU-and FPGA-based MPSoC ECU architectures for secure, dependable, and real-time automotive CPS. In Proceedings of the 28th International Conference on Application-specific Systems, Architectures and Processors (ASAP), Seattle, WA, USA, 10–12 July 2017. [Google Scholar]
- Chang, A.X.M.; Culurciello, E. Hardware accelerators for recurrent neural networks on FPGA. In Proceedings of the 2017 IEEE International Symposium on Circuits and Systems (ISCAS), Baltimore, MD, USA, 28–31 May 2017. [Google Scholar]










| Machine Learning Model | Features | Average Accuracy (%) |
|---|---|---|
| BDT | Time (6 features), frequency (5 features) | 92.00 |
| NN | Time (6 features), frequency (5 features) | 95.20 |
| SVM (Linear kernel) | Time (6 features), frequency (5 features) | 96.00 |
| SVM (RBF kernel) | Time (6 features), frequency (5 features) | 96.00 |
| RNN-LSTM | deep features | 98.76 |
| [5] | Our Model | |
|---|---|---|
| Average mis-identification rate (%) | 0.36 | 0.16 |
| Resource | Utilization | Available | Utilization (%) |
|---|---|---|---|
| LUT | 8777 | 17,600 | 49.87 |
| LUTRAM | 601 | 6000 | 10.02 |
| FF | 9601 | 35,200 | 25.74 |
| BRAM | 9 | 60 | 15.00 |
| DSP | 25 | 80 | 31.25 |
| BUFG | 1 | 32 | 3.13 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, Y.; Duan, Z.; Tehranipoor, M. Identify a Spoofing Attack on an In-Vehicle CAN Bus Based on the Deep Features of an ECU Fingerprint Signal. Smart Cities 2020, 3, 17-30. https://doi.org/10.3390/smartcities3010002
Yang Y, Duan Z, Tehranipoor M. Identify a Spoofing Attack on an In-Vehicle CAN Bus Based on the Deep Features of an ECU Fingerprint Signal. Smart Cities. 2020; 3(1):17-30. https://doi.org/10.3390/smartcities3010002
Chicago/Turabian StyleYang, Yun, Zongtao Duan, and Mark Tehranipoor. 2020. "Identify a Spoofing Attack on an In-Vehicle CAN Bus Based on the Deep Features of an ECU Fingerprint Signal" Smart Cities 3, no. 1: 17-30. https://doi.org/10.3390/smartcities3010002
APA StyleYang, Y., Duan, Z., & Tehranipoor, M. (2020). Identify a Spoofing Attack on an In-Vehicle CAN Bus Based on the Deep Features of an ECU Fingerprint Signal. Smart Cities, 3(1), 17-30. https://doi.org/10.3390/smartcities3010002