Validation of Authentication Measures Implementation in Iot Mobile Applications
Abstract
:1. Introduction
2. Iot Authentication Mechanisms: State of the Art
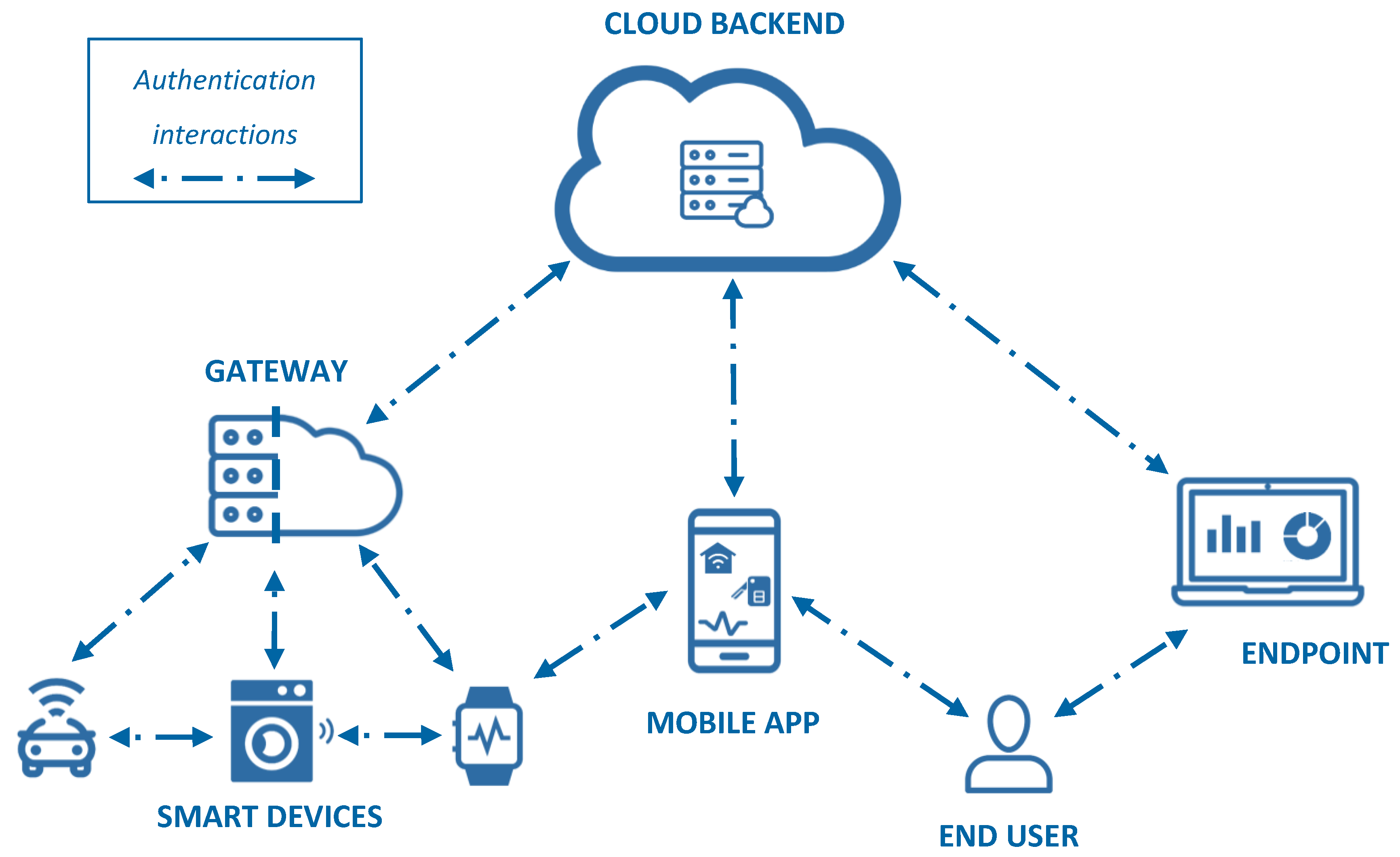
2.1. Iot Authentication Reference Model
2.2. Iot Authentication Challenges
- Amount and heterogeneity of devices: the incredibly high (and increasing) number of IoT devices as well as their heterogeneous nature (e.g. different applications, functions, manufacturers) pose a challenge when it comes to identity provisioning/management, as well as authentication processes.
- Resource and capability constraints: most authentication mechanisms rely on the possession and validation of credentials, which can be seen as a hindering factor for constrained devices.
- Changes in location and time: smart devices are not static either in terms of location (changes in physical location and consequently in network) or in terms of time (multiple events happening simultaneously). This volatility needs to be taken into account when it comes to providing suitable and resilient authentication processes.
2.3. Iot Authentication Protocols, Frameworks, and Standards
2.3.1. Application Layer
- Security Assertion Mark-up Language (SAML): SAML is an open security standard developed by OASIS that allows the exchange of authentication and authorization information among different parties or entities [16]. It is an XML-based framework that supports Single Sign On (SSO) and identity federation mainly in accessing web resources. It defines the role of a trusted identity provider that stands between the user who wants access to some resources and the service provider in charge of their access control. SAML is well targeted for IoT deployments, as the standard defines possible communication flows among parties, profiles, and bindings with other communication protocols (HTTP, SOAP). In addition, SAML is compatible with multiple authentication mechanisms and architectures (e.g. Kerberos, (un)protected usernames and passwords over HTTP, X.509 Public Key Infrastructure, Pretty Good Privacy (PGP), Smart Cards…), showing a huge degree of interoperability, which is certainly a desired characteristic for IoT deployments. Regarding resource and capability constraints, most authentication mechanisms rely on the possession and validation of credentials, which can be seen as a hindering factor for constrained devices.
- OAuth 2.0 and OpenID Connect (OIDC): OAuth 2.0 is an open standard developed by the IETF Auth WG. It consists of an authorization framework that aimed to provide secure delegated access to resources or services by a third party on behalf of the owner [17]. By means of introducing an authorization layer, the resource owner does not have to share its credentials with any third-party application. Although originally thought for HTTP resource access, the standard provides several extensions to allow interoperability, such as SAML2, JSON (JavaScript Object Notation), Web Token (JWT), or even for the use of OAuth with native apps or resource-constrained devices. It is worth noting that OAuth is an authorization protocol, and not an authentication one. To solve this issue, OpenID Connect [18] is an identity layer built on top of OAuth 2.0 to fill the authentication gap. This allows third-party apps (clients) to authenticate/verify the identity of the users. In terms of security, it is compliant with ISO/IEC 29115 Entity Authentication Assurance [19], and therefore offers four different levels of authentication assurance, allowing for example the use of encryption, which is quite pertinent also for IoT environments.
- Fast IDentity Online (FIDO): In terms of multi-factor authentication (MFA) in the context of IoT, FIDO aims at addressing the lack of interoperability between authentication devices and the inconvenience of remembering multiple passwords [20]. It combines PKI mechanisms with a second factor that protects access to the private key, thus strengthening the security of authentication. Moreover, FIDO defines how its schema can be used in conjunction with other authentication protocols (such as the ones mentioned above) as well as in the context of the IoT, focusing on smartphones as users’ primary interaction devices to communicate to the rest of the IoT ecosystem.
- Constrained Application Protocol (CoAP) on top of Datagram Transport Layer Security (DTLS): When devices communicate with each other, standardized as well as proprietary mechanisms exist to establish keys for communication and authenticate in a secure manner. IETF standards in this respect include the Datagram Transport Layer Security (DTLS) [21], which uses Transport Layer Security protocol (TLS) over User Datagram Protocol (UDP), and not over Transmission Control Protocol (TCP) as most implementations. In the case of IoT resource-constrained devices, DTLS can be extended with different security mechanisms when Constrained Application Protocol (CoAP) [22] is used at the application layer, e.g. security modes such as NoSec (no security at all), PreSharedKey (symmetric authentication), RawPublicKey (asymmetric authentication), and Certificate.
2.3.2. Communication Layer
- Bluetooth Low Energy (BLE): Bluetooth Low Energy [25] (BLE) is a version of Bluetooth technology that focuses on low-energy consumption, tackling problems from old Bluetooth versions such as fast battery draining and the frequent loss of connection, requiring frequent pairing and re-pairing. Such features closely relate to the needs of IoT, which further supports why BLE is widely used in such environments. Bluetooth Core Specification provides a number of features that cover security aspects such as encryption, trust, data integrity, and the privacy of the user’s data [26]. In terms of authentication, the pairing process allows BLE devices to exchange device information for the establishment of a secure link. The following options exist in the different versions of BLE:
- ○
- Legacy Pairing (BLE 4.0/1): The devices exchange a Temporary Key (TK) and use it to create a Short-Term Key (STK), which is used to encrypt the connection. The security of the entire process depends on the pairing method used to exchange the TK:
- ▪
- Just Works is an implementation where the TK is set to ‘0000’, making it easy for an adversary to brute force the STK and eavesdrop on the connection. Moreover, there is no way of verifying the devices in the connection, and thus offers no man-in-the-middle (MITM) protection.
- ▪
- Passkey is a similar concept, except that the TK is a six-digit number that is passed between the devices by the user. This method provides relatively good protection from passive eavesdropping, except if the adversary is present during the pairing process and is able to eavesdrop the exchanged values.
- ▪
- Out-of-Band (OOB) pairing involves exchanging the TK using a different wireless technology such as NFC. This allows for the exchange of a very large TK, up to 128 bits, greatly enhancing the security of the connection
- ○
- Secure Connections (BLE 4.2/3): This new model introduces the numeric comparison method to the three methods mentioned above. Instead of using a TK and STK, LE Secure Connections use a single Long-Term Key (LTK) to encrypt the connection. The LTK is generated and exchanged using Elliptic Curve Diffie–Hellman (ECDH) public key cryptography. This approach offers significantly stronger security when compared to the original BLE key exchange protocol.
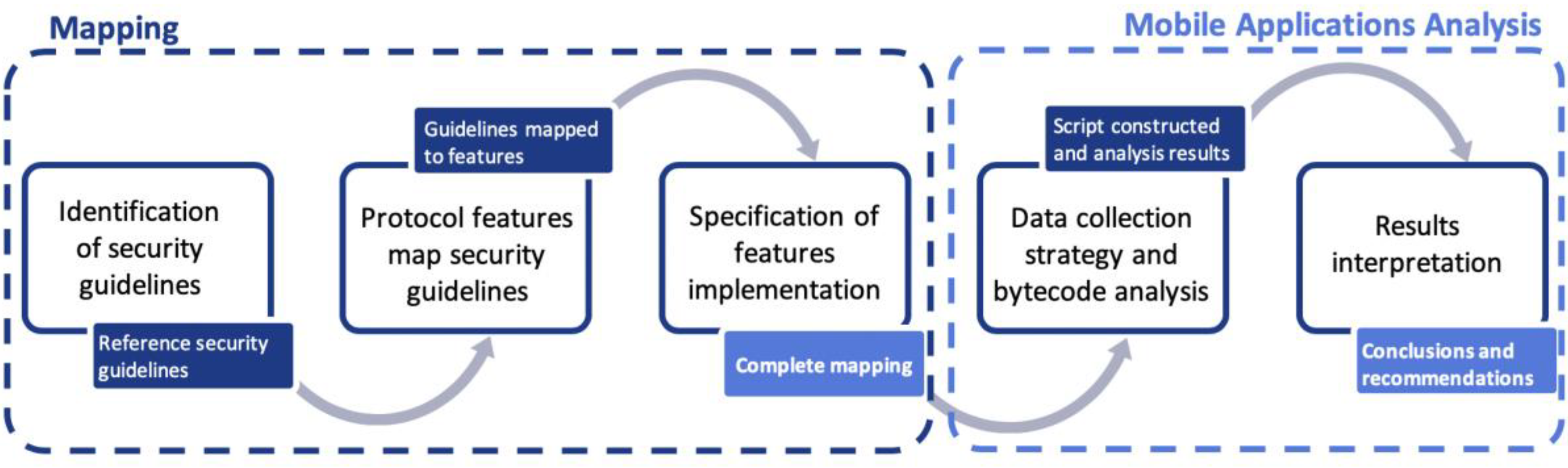
3. Methodology for Evaluating the Secure Implementation of Authentication Protocols
3.1. Step 1: Identification of Security Guidelines
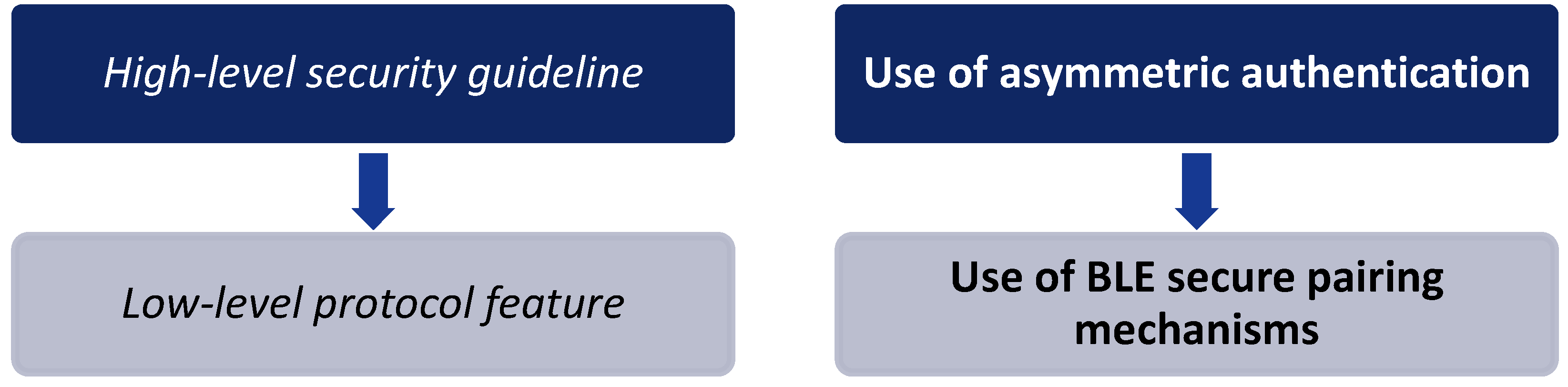
3.2. Step 2: Protocol Features Mapping Against Security Guidelines
3.3. Step 3: Specification of Features Implementation in API Calls
3.4. Step 4: Data Collection Strategy and Bytecode Analysis
3.5. Step 5: Results Interpretation
4. Experimental Validation
4.1. Oauth 2.0 in Combination with Oidc Analysis Findings and Conclusions
4.1.1. Steps 1 to 3: Complete Mapping
- The ENISA Smartphone Secure Development Guideline that refers to securing the tokens in transit is selected for the analysis.
- The OAuth and OIDC features that address this guideline are explored. The first one refers to the use of Proof Key for Code Exchange (PKCE) to protect against the interception of authentication communications, and the second one refers to use of HTTPS in order to protect tokens from disclosure in storage and transport [17].
- The implementation of the aforementioned two features in Android has to be specified. Regarding the PKCE feature, two query parameters are used to perform the protection, ‘code_challenge’ and ‘code_verifier’, so these will be the two searches in the application bytecode. Regarding the use of HTTPS in all the requests, Android provides several methods to set the parameters in the HTTP request, but the common elements are the "Authorization" request header field and "Bearer" request field value to select the Bearer authentication scheme to transmit the access tokenFirst item.
4.1.2. Step 4: Data Collection Strategy and Bytecode Analysis
- Strategy: Taking as input the bytecode search elements from the mapping shown in Table 2, the strategy of searches is built. The main objective is to validate the implementation of the OAuth protocol (and consequent use of tokens) and the OIDC on top of it. Moreover, a secondary objective refers to evaluating whether the application code considers the security options that the OAuth + OIDC framework provides.
- When it comes to the strategy, all the searches are independent from one another, as each of them represents a sole authentication measure and can exist without the others in the code. Nevertheless, several of the searches need to be considered sequentially in order to examine whether sets of bytecode elements have been implemented. Following the previous example of feature 8, we need to identify whether tokens are being exchanged securely. We first look for the ‘Authorization’ request header field, and within the same class that this string is found, we look for instances of ‘Bearer’.
- Analysis: An initial sample of 325 IoT Android mobile applications from Google Play Store was gathered. While we do not claim to extrapolate and generalize findings based on this dataset, we still consider it representative in order to highlight indicative results. The results of the analysis are summarized in Table 3.
4.1.3. Step 5: Results Interpretation
- Tendency of a mobile application developer to delegate authentication and authorization processes to well-established authentication and authorization services.
- Diversity of OAuth 2.0 framework implementations due to the lack of a reference API for developers, thus increasing fragmentation.
4.2. BLE Analysis Findings and Conclusions
4.2.1. Steps 1 to 3: Complete Mapping
- We first select the ENISA Smartphone Secure Development Guideline to be tackled, namely the one that encourages developers to use asymmetric cryptography when possible.
- Based on the previous selection, features covering the specific guideline are sought. By examining the security specifications of BLE [26], we identify that the secure pairing implemented for BLE versions 4.2 and 4.3 uses asymmetric cryptography.
- Finally, the implementation of this feature, i.e. secure pairing, in Android has to be pinpointed. In the case of Java for Android, a dedicated native ECDH Key Pair Generator exists, which is included in the package java.security.*, and corresponds to the parameter ‘sect163k1’.
4.2.2. Step 4: Data Collection Strategy and Bytecode Analysis
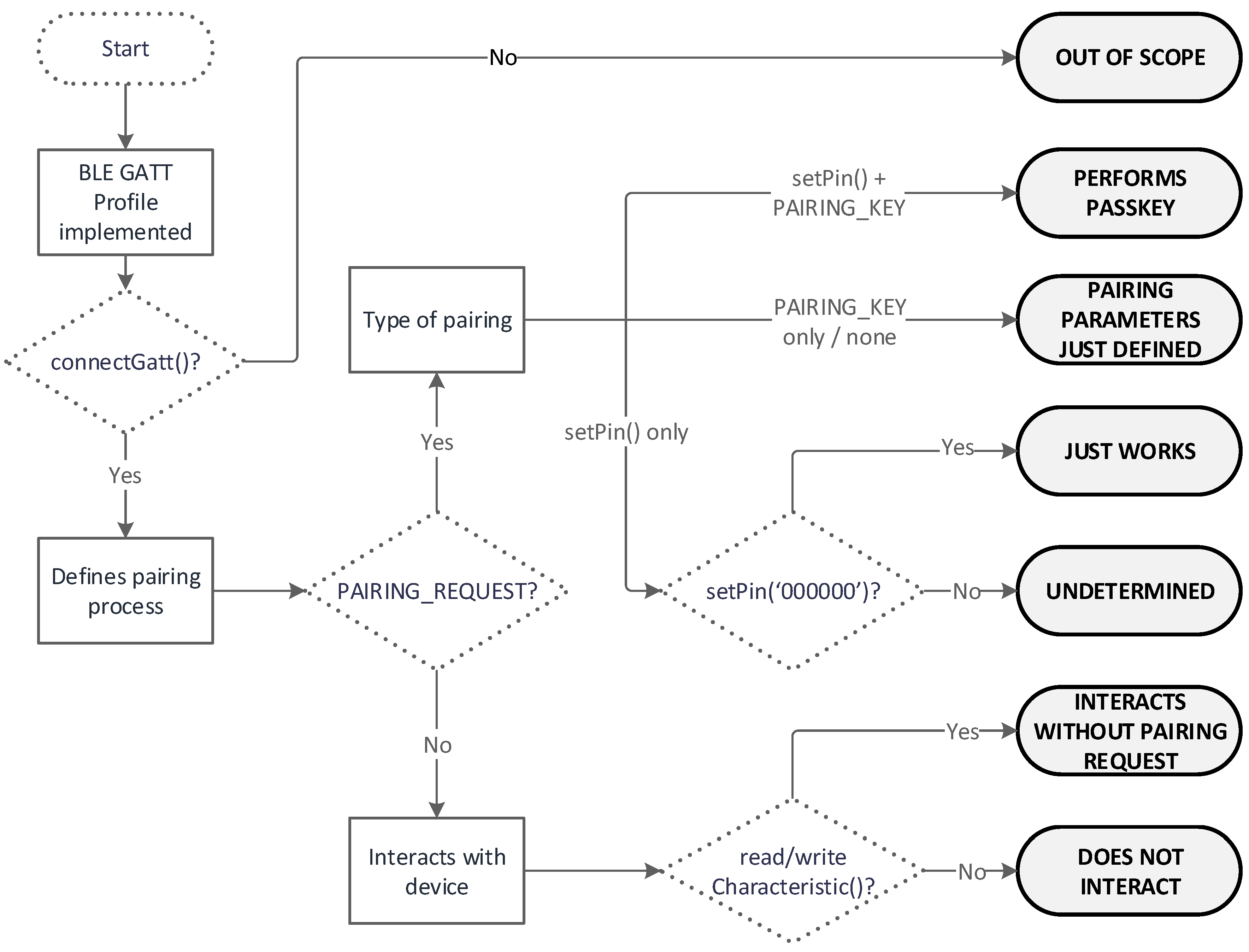
- Strategy: It is worth mentioning beforehand the existence of a BLE reference API Guide for Android developers [28], which has been the basis for the searches in the code. In this case, all the target findings refer to the pairing process. Therefore, the first element to search is ‘connectGatt()’ API call, which belongs to the GATT Profile [29], and is a general specification in all current BLE application profiles. Thus, we discard all the applications that use another type of Bluetooth technology, and only work on the ones implementing BLE.
- Analysis: For this analysis, a sample of 1022 IoT Android mobile applications from Google Play Store was gathered. These applications underwent the process defined in the decision tree shown in Figure 5, and were classified into the different output categories to determine their BLE pairing implementations. While we acknowledge the limited size of the dataset, these indicative findings can serve as input for further and more thorough investigation given adequate resources and time.
4.2.3. Step 5: Results Interpretation
- A limited number of applications were implementing pairing (authentication) mechanisms in a secure, complete, and verifiable way.
- There existed devices using BLE that allowed communication with smartphones without a previous secure pairing process.
5. Discussion
Funding
Acknowledgments
Conflicts of Interest
References
- Wolf, M.; Serpanos, D. Safety and Security of Cyber-Physical and Internet of Things Systems. Proc. IEEE 2017, 105, 983–984. [Google Scholar] [CrossRef]
- European Union Agency for Network and Information Security (ENISA). Baseline Security Recommendations for Internet of Things in the Context of Critical Information Infrastructures; European Union Agency for Network and Information Security (ENISA): Athens, Greece, 2017. [Google Scholar]
- Applied Cybersecurity Divsion (ACD)—NIST ITL. IoT Cybersecurity Considerations. Available online: https://www.nist.gov/itl/applied-cybersecurity/iot-cybersecurity-considerations (accessed on 1 June 2018).
- Sa Silva, J.; Zhang, P.; Pering, T.; Boavida, F.; Hara, T.; Liebau, N.C. People-Centric Internet of Things. IEEE Commun. Mag. 2017, 55, 18–19. [Google Scholar] [CrossRef]
- Dye, S.M.; Scarfone, K. A standard for developing secure mobile applications. Comput. Stand. Interfaces 2014, 36, 524–530. [Google Scholar] [CrossRef]
- Open Web Application Security Project (OWASP). IoT Attack Surface Areas. Available online: https://www.owasp.org/index.php/IoT_Attack_Surface_Areas (accessed on 1 June 2018).
- European Union Agency for Network and Information Security (ENISA). Smartphone Secure Development Guidelines; European Union Agency for Network and Information Security (ENISA): Athens, Greece, 2017. [Google Scholar]
- Open Web Application Security Project (OWASP). OWASP Mobile Security Project. Available online: https://www.owasp.org/index.php/OWASP_Mobile_Security_Project#tab=Secure_M-Development (accessed on 1 June 2018).
- Open Web Application Security Project (OWASP). IoT Framework Assessment. Available online: https://www.owasp.org/index.php/IoT_Framework_Assessment (accessed on 1 June 2018).
- Internet Engineering Task Force (IETF). Design Considerations for Security Protocols in Constrained Environments. Available online: https://tools.ietf.org/id/draft-seitz-ace-design-considerations-00.txt (accessed on 1 June 2018).
- Internet Engineering Task Force (IETF). Group Authentication. Available online: https://tools.ietf.org/id/draft-zhu-ace-groupauth-00.txt (accessed on 1 June 2018).
- Internet Engineering Task Force (IETF). Authentication and Authorization for Constrained Environments (ace). Available online: https://datatracker.ietf.org/wg/ace/about/ (accessed on 1 June 2018).
- Internet Engineering Task Force (IETF). Constrained RESTful Environments (core). Available online: https://datatracker.ietf.org/wg/core/documents/ (accessed on 1 June 2018).
- oneM2M Partners. oneM2M—Standards for M2M and the Internet of Things. Available online: http://www.onem2m.org/ (accessed on 1 June 2018).
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. Authentication Protocols for Internet of Things: A Comprehensive Survey. Secur. Commun. Netw. 2017, 2017, 1–41. [Google Scholar] [CrossRef] [Green Version]
- OASIS. Security Assertion Markup Language (SAML) Specifications. Available online: http://saml.xml.org/saml-specifications (accessed on 1 June 2018).
- Internet Engineering Task Force (IETF). The OAuth 2.0 Authorization Framework. Available online: https://tools.ietf.org/html/rfc6749 (accessed on 1 June 2018).
- OpenID. OpenID Specifications. Available online: http://openid.net/developers/specs/ (accessed on 1 June 2018).
- International Organization for Standardization (ISO); International Electrotechnical Commission (IEC). International Standard 29115: Information Technology—Security Techniques—Entity Authentication Assurance Framework; International Organization for Standardization: Geneva, Germany, 2013. [Google Scholar]
- Shikiar, A.; Lindemann, L. The Future of Authentication for the Internet of Things. 2017. Available online: https://www.slideshare.net/FIDOAlliance/the-future-of-authentication-for-iot (accessed on 1 June 2018).
- Internet Engineering Task Force (IETF). Datagram Transport Layer Security Version 1.2. Available online: https://tools.ietf.org/html/rfc6347 (accessed on 1 June 2018).
- Constrained Application Protocol (CoAP). CoAP—RFC 7252 Constrained Application Protocol. Available online: http://coap.technology/ (accessed on 1 June 2018).
- Zigbee Alliance. Zigbee. Available online: http://www.zigbee.org/ (accessed on 1 June 2018).
- Parekh, J. WiFi’s Evolving Role in IoT. Available online: https://www.networkworld.com/article/3196191/lan-wan/wifi-s-evolving-role-in-iot.html (accessed on 1 June 2018).
- Gomez, C.; Oller, J.; Paradells, J. Overview and Evaluation of Bluetooth Low Energy: An Emerging Low-Power Wireless Technology. Available online: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC3478807/ (accessed on 1 June 2018).
- Bluetooth SIG Proprietary. Security Overview. In Specification of the Bluetooth System; Bluetooth SIG, Inc.: Kirkland, WA, USA, 2014; Volume 1, Part A, Section 5. [Google Scholar]
- Frew, J. (MakeUseOf). The Best Languages for Mobile App Development in 2016. Available online: https://www.makeuseof.com/tag/best-languages-mobile-app-development-2016 (accessed on 1 June 2018).
- Android Developers. Bluetooth Low Energy Overview—Documentation. Available online: https://developer.android.com/guide/topics/connectivity/bluetooth-le (accessed on 1 June 2018).
- Bluetooth SIG. GATT Overview. Available online: https://www.bluetooth.com/specifications/gatt/generic-attributes-overview (accessed on 1 June 2018).

| Smartphone Secure Development Guidelines | Protocol Features | Bytecode Search |
|---|---|---|
| Summary | Summary | Element to find |
| First Section, guideline 2 | Protocol method/parameter 1 | methodX(), PARAM_1 |
| Third Section, guideline 5 | Protocol method/parameter 2 | methodY(), PARAM_2 |
| ENISA Smartphone Secure Development Guidelines | OAuth + OIDC Features | Bytecode Search |
|---|---|---|
| Summary | Summary | Element to find |
| - Instead of passwords, consider using longer-term authorization tokens that can be securely stored on the device (as per the OAuth model) | 1. Use of OAuth 2.0 model, which uses tokens as the basis for authentication and authorization | StringBuilder oauth JSON (token) |
| - Use the latest versions of the authorization standards (such as OAuth 2.0) | ||
| - Use authentication that ties back to the end user identity (rather than only to the device identity). | 2. OpenID Connect on top of OAuth | scope=openid id_token |
| - Authentication should not be used as a replacement of authorization security controls | ||
| - Do not rely on client-side security controls. Both authentication and authorization controls should be implemented on the server side. | 3. Use Authorization Code Grant | getQueryParameter (“code”) |
| - Tokens can be issued by the backend service after verifying the user credentials initially. | ||
| - Use unpredictable session identifiers with high entropy | 4. Protect against CSRF | getQueryParameter (“state”) |
| - Require authentication credentials or tokens to be passed with any subsequent request | 5. Use of refresh tokens | refresh_token |
| - Provide the ability to the mobile user to change passwords or other authentication tokens | ||
| - Do not reveal registered usernames and remove any fingerprint of their existence from verbose error messages | 6. Use of OAuth standard error messages | invalid_request, invalid_token, inssuficient_scope |
| - Tokens revocable by server | ||
| - Secure the tokens in transit | 7. Proof Key for Code Exchange | code_challenge=abc code_verifier=1242 |
| 8. Use of HTTP over TLS (HTTPS) in token transmissions | https://urlencoded post.setHeader (“Authorization” + “Bearer”) | |
| - Tokens are time bounded | 9. Token frequently expires frequently | JSON (expires_in) |
| Bytecode Element | Occurrences |
|---|---|
| Summary | Summary |
| Oauth | 144 |
| getQueryParameter + code | 192 |
| getQueryParameter + state | 165 |
| openid | 170 |
| code_challenge | 5 |
| code_verifier | 6 |
| code_challenge + code_verifier | 1 |
| Authorization + Bearer | 94 |
| JSON + token | 85 |
| JSON + expires_in | 70 |
| ENISA Smartphone Secure Development Guidelines | BLE Features | Bytecode Search |
|---|---|---|
| Summary | Summary | Element to find |
| - Using asymmetric cryptography for authentication and authorization purposes | 1. Use of BLE secure pairing mechanisms | sect163k1 |
| - Ensure that a strong password policy is being followed | 2. Enforce restrictions when setting the pin | setPin() + !setPin(0,0,0,0,0,0) |
| - Use unpredictable session identifiers with high entropy | ||
| - Require authentication credentials or tokens to be passed with any subsequent request | 3. Make pairing setup expire frequently | cancelBondProcess() |
| - Use authentication that ties back to the end user identity (rather than only to the device identity) | 4. Use of the Passkey method | extra.PAIRING_KEY + extra_PAIRING_VARIANT = PASSKEY |
| - Do not store any passwords or secrets in the application binary |
| TOTAL APPLICATIONS: 1022 | ||||
|---|---|---|---|---|
| Using Gatt: 534 | Not Using Gatt: 488 | |||
| Pairing | 58 | Not Pairing Requests | 476 | |
| Only defining pairing parameters | 53 | Communicating without requesting pairing | 475 | |
| Just Works | 2 | Just connecting | 1 | |
| Implements Passkey method | 3 | |||
© 2019 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fernández Bascuñana, G. Validation of Authentication Measures Implementation in Iot Mobile Applications. Smart Cities 2019, 2, 163-178. https://doi.org/10.3390/smartcities2020012
Fernández Bascuñana G. Validation of Authentication Measures Implementation in Iot Mobile Applications. Smart Cities. 2019; 2(2):163-178. https://doi.org/10.3390/smartcities2020012
Chicago/Turabian StyleFernández Bascuñana, Gema. 2019. "Validation of Authentication Measures Implementation in Iot Mobile Applications" Smart Cities 2, no. 2: 163-178. https://doi.org/10.3390/smartcities2020012




