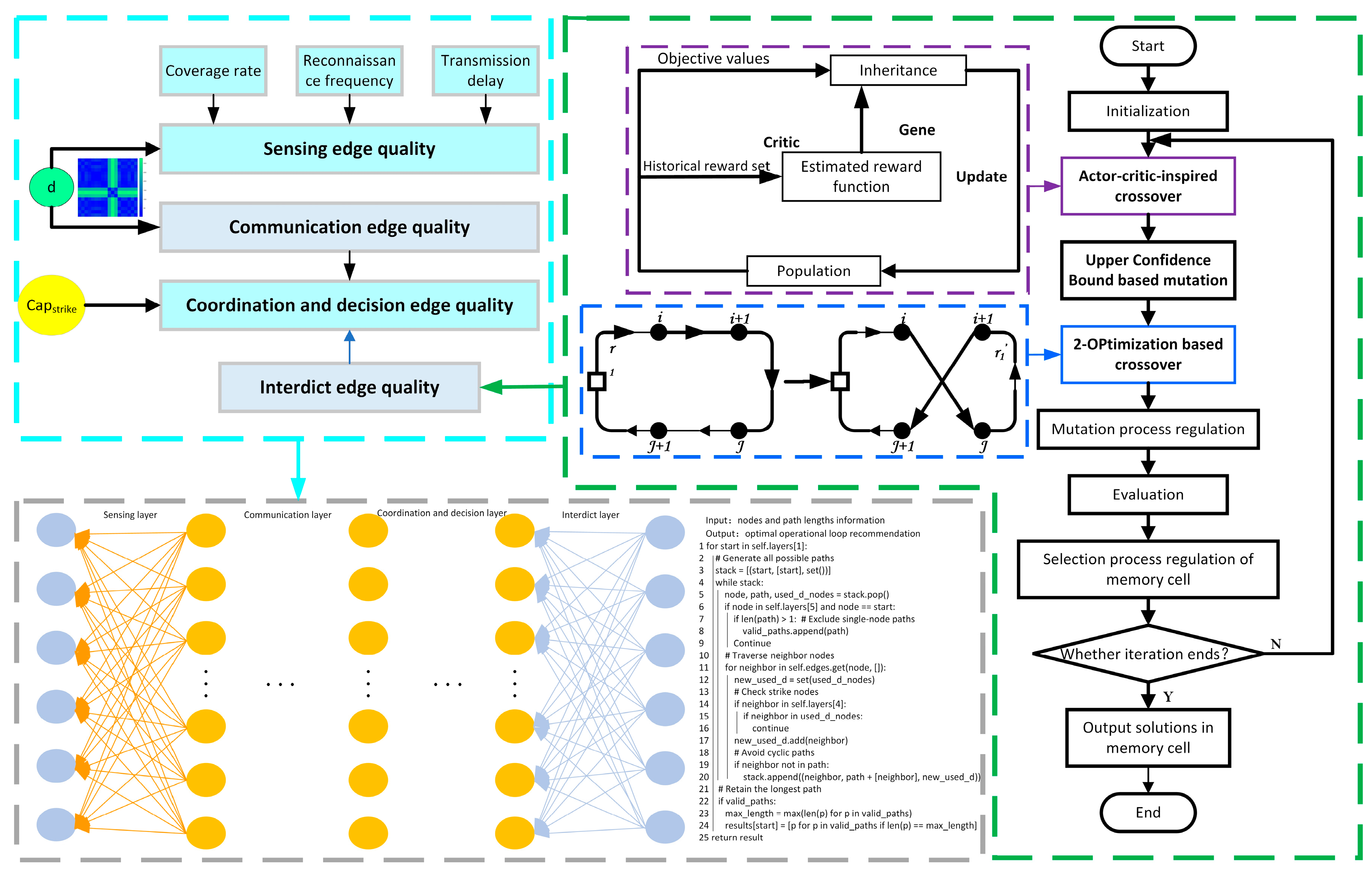
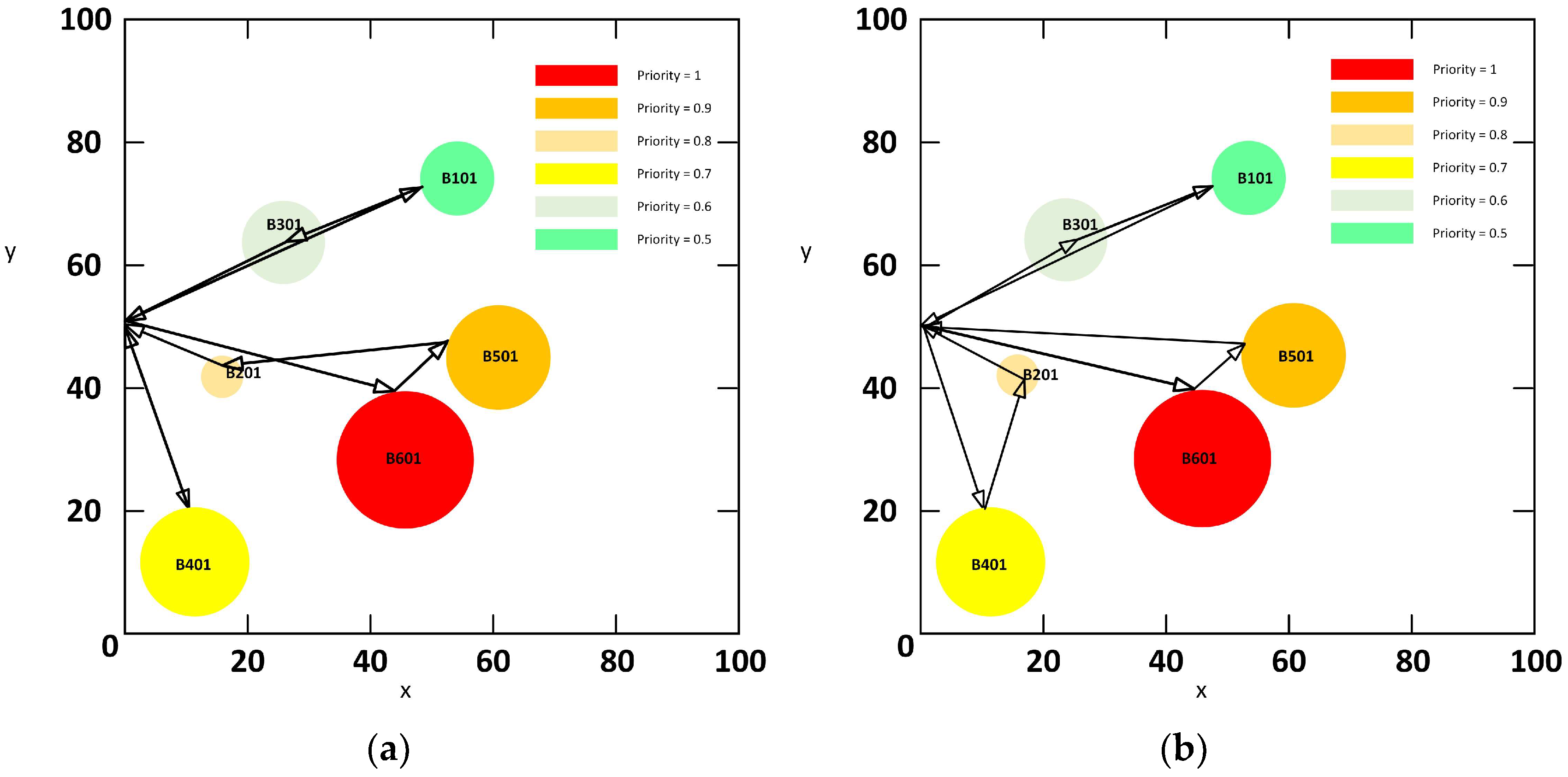
To enable a single operational cycle recommendation to accomplish protection tasks for multiple target nodes based on UAV capabilities, this paper will formulate the problem from two perspectives: heterogeneous complex network modeling and path planning.
2.1. Heterogeneous Networked System Modeling
Multi-UAV collaborative protection constitutes a complex safeguarding framework comprising multiple functional networks, including surveillance networks, communication networks, command-and-control networks, and protection networks. These networks involve numerous equipment nodes and interconnecting edges. The development of a capability model for protection-oriented networks aims to enable the rapid computational assessment of protection capabilities in operational environments.
The core of system modeling lies in establishing and integrating the logical relationships and constraint rules among system components to construct a computable and evaluable protection system model. Building upon prior work on multifunctional fusion networks [
25], multilayer networks, and operational network modeling [
26], this study employs a heterogeneous network representation to characterize the diverse equipment types and edge relationships within protection networks, incorporating their unique features.
As defined in [
3], a heterogeneous network comprises multiple node types or relationship types and can be represented as a directed graph
. For operational relevance,
denotes equipment nodes, with key attributes including the kind, attribute, communication channel capacity, operational radius, capability metrics, and geographic coordinates. These node characteristics are formally expressed via Equation (1):
In the formula,
represents the agent group, where the same indicates different equipment belonging to the same team—this paper only considers system interaction scenarios between two distinct agent groups;
represents the attributes of the corresponding equipment, i.e., the basic core functions of the UAV, namely detection, energy management, and protection, where the same UAV can integrate multiple core functionalities;
Parameter characterizes the nodal degree constraint of a UAV, defining the maximum allowable inter-agent communication edges for maintaining stable network connectivity;
indicates the operational radius of the node, where the UAV can complete protective operations within the coverage ranges of designated objectives;
represents the protection capabilities of the UAV. This paper primarily considers the core capabilities relevant to the defense loop: sensing capabilities, communication capabilities, coordination and decision capabilities, and protection capabilities, which are expressed as .
represents the spatial location of the UAV, which is a crucial factor in mission protection and determines both inter-UAV coordination and collaborative effectiveness.
denotes the connecting edge relationship between nodes.
Sensing edge (): Our UAV systems acquire dangerous object signatures through active sensing (radar wave emission) or passive detection (infrared signal reception).
Communication edge (): Detection-capable UAVs transmit environmental signatures to decision-making units, where data processing converts raw signals into operational data.
Coordination and decision edge (): Our control systems analyze and evaluate decision support information, formulate protection plans, and disseminate operational commands to task execution UAVs.
Task execution edge (): Upon receiving execution directives, our protection-capable UAVs perform assigned tasks using platform-specific operational methods in accordance with mission requirements.
2.2. Description of the Path Planning Problem
A set of protective equipment (red team) remains on standby at designated positions, prepared to execute safeguarding tasks. During each operational cycle, the equipment departs from and returns to these predefined locations. To verify task completion, every incoming target node’s effective interception zone must be traversed by at least one protective unit. Based on the real-time positional data of adversarial target nodes—collected via reconnaissance systems—along with their priority levels, optimal interception paths are planned for the protective equipment.
The task allocation problem primarily aims to minimize the total path length, thereby reducing energy consumption. However, if this were the sole objective, the optimized solution would assign all interception tasks to a single unit, resulting in prolonged operational durations and missed optimal interception windows for high-priority targets. To enhance mission timeliness, a secondary objective is introduced: distributing tasks across multiple units while minimizing the longest individual path length.
Furthermore, the varying priority levels of adversarial target nodes influence interception sequences and response dynamics. For instance, prioritizing the interception of a ground command center may degrade the responsiveness of secondary targets, thereby increasing the mission success rates. Higher-priority targets are therefore assigned elevated interception precedence.
These three objectives—(1) total path minimization, (2) workload balancing, and (3) priority-based scheduling—interact and constrain one another, necessitating concurrent optimization. Thus, the formulated task allocation scenario constitutes a multi-objective optimization problem (MOP).
The mathematical model is represented as follows.
A group of UAV protection systems performs coordinated multi-node safeguarding operations. Departing from initial positions , the systems follow predetermined paths to visit a set of target nodes distributed in non-cooperative zones before returning to their origin. During path planning, the current positions of target nodes , obtained through reconnaissance systems, are denoted by coordinates , with effective protection ranges represented by . The initial position is located at .
In order to describe the defense relationship between the interdictor units and the designated objective node, the assignment parameter
is introduced;
if the interdictor unit
is assigned to the target node
, and
otherwise. Define
as the set of designated objective nodes that the task execution unit is assigned to interdict, and the set of all destinations of protective unit
is denoted as
. For
,
denotes the transition of protective asset
from location
to location
. The task sequence of protective asset
is denoted as
. Based on the above definition, the task allocation problem can be formulated as
Of these, constraints (5) and (6) ensure that each target node is interdicted by only one UAV; constraint (7) maintains flow conservation with both incoming and outgoing flows; constraints (8) and (9) guarantee that each target node is assigned to a UAV for servicing with no omissions. Due to the payload and range limitations of the UAV protective assets, constraints (10)–(12) limit the maximum number of nodes and operational range per UAV; constraint (11) restricts mission participation to designated protective UAVs.