A Capacity-Constrained Weighted Clustering Algorithm for UAV Self-Organizing Networks Under Interference
Abstract
1. Introduction
- (1)
- A capacity-constrained weighted clustering algorithm is proposed, which includes initial node partitioning, CH and BCH selection, and dynamic cluster maintenance. This method aims to improve the stability and robustness of UAV self-organizing networks in the interference environment.
- (2)
- A capacity-constrained partitioning algorithm based on K-means++ is designed, which considers both similarity-based partitioning and capacity balance, enabling the effective establishment of initial node partitions and addressing the problem of partition imbalance.
- (3)
- A weighted summation-based CH and BCH selection algorithm is proposed, which comprehensively considers factors such as connectivity, remaining energy, mobility similarity, average distance, and external interference to optimize the selection process.
- (4)
- The algorithm is validated through simulation experiments, with the results showing that the proposed clustering algorithm effectively performs network clustering in interference environments. A comprehensive evaluation is conducted by comparing it with baseline clustering schemes.
2. Related Works
3. Clustering Model for UAV Systems
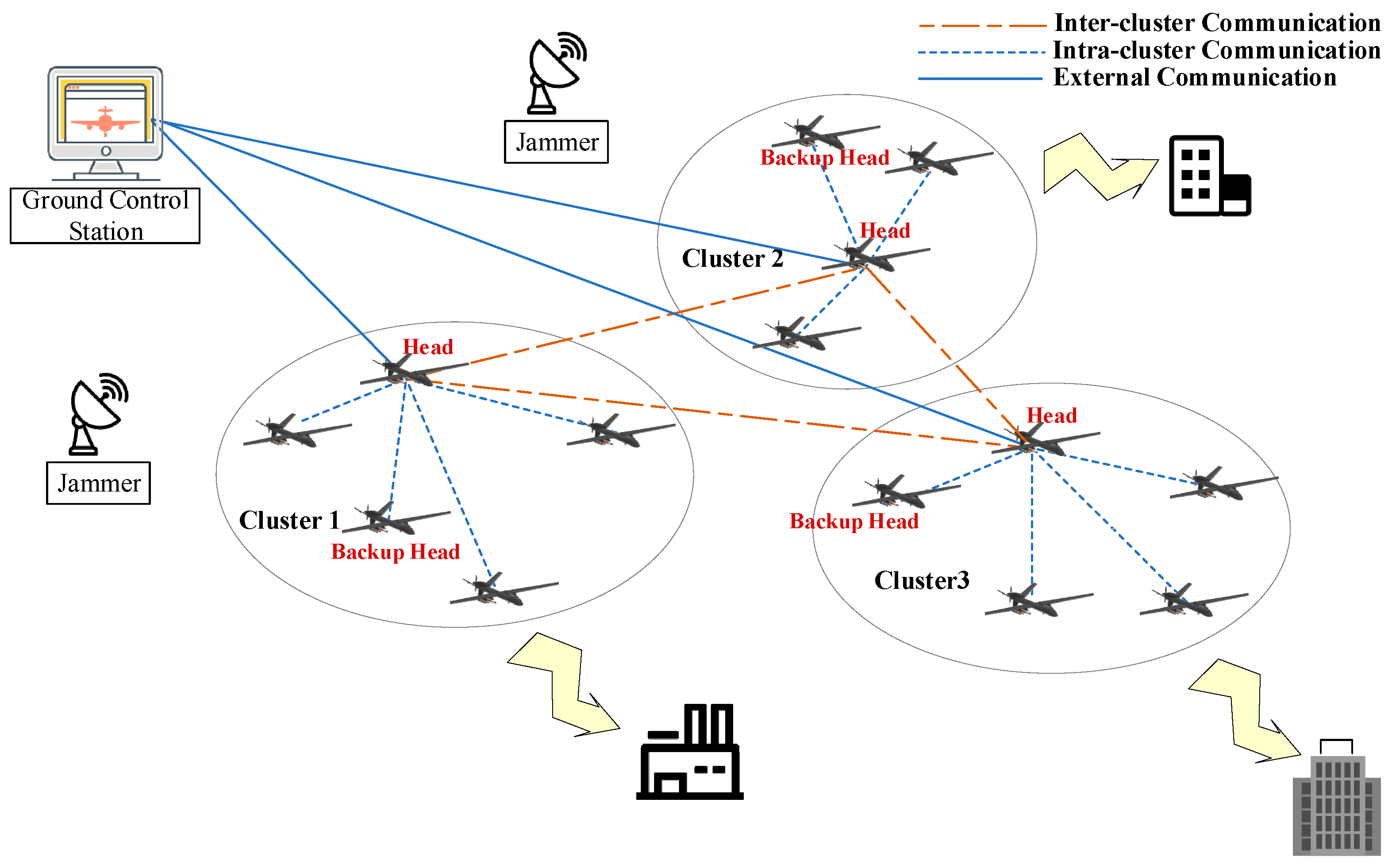
3.1. Network Topology Model
3.2. Network Clustering Process
3.2.1. Information Exchange Process Between Nodes
- Partition message: Sent by the ground control station to notify UAV nodes of the initial partitioning results and task information.
- Hello message: Used for node sharing of basic information to perform initial partitioning, cluster head selection, and backup cluster head selection.
- C_Clustering message: Sent by the cluster head node to inform other nodes within the partition to join its cluster.
- C_Reply message: Used by cluster members to reply to the cluster head, informing it of new nodes joining the cluster.
- C_Update message: Sent by the cluster head to notify all nodes within the cluster of the updated cluster member information.
- Network partitioning stage
- 2.
- Node neighbor discovery stage
- 3.
- CH and BCH node selection Stage
- 4.
- Cluster Head Invitation Phase
- 5.
- Cluster Member Joining and Confirmation Phase
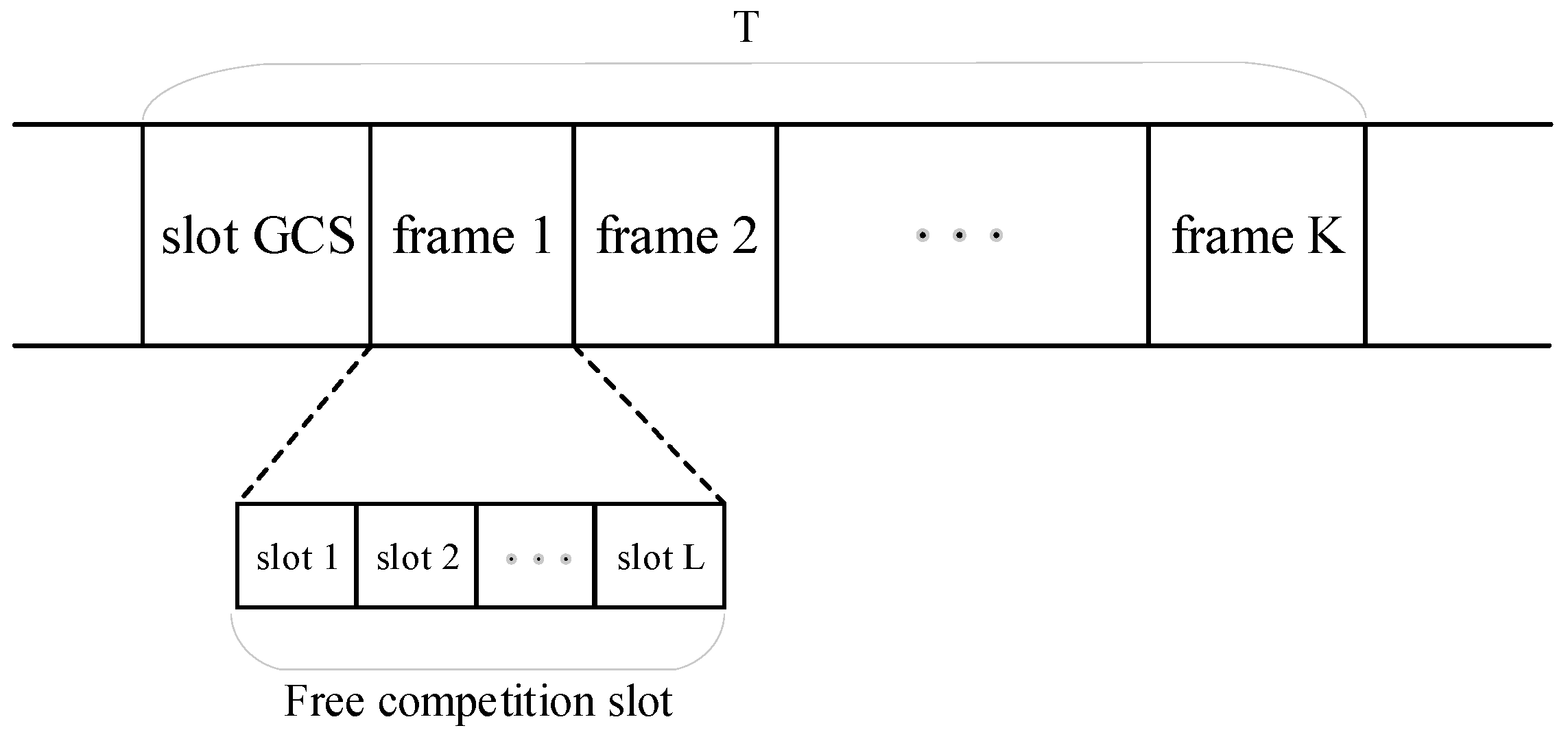
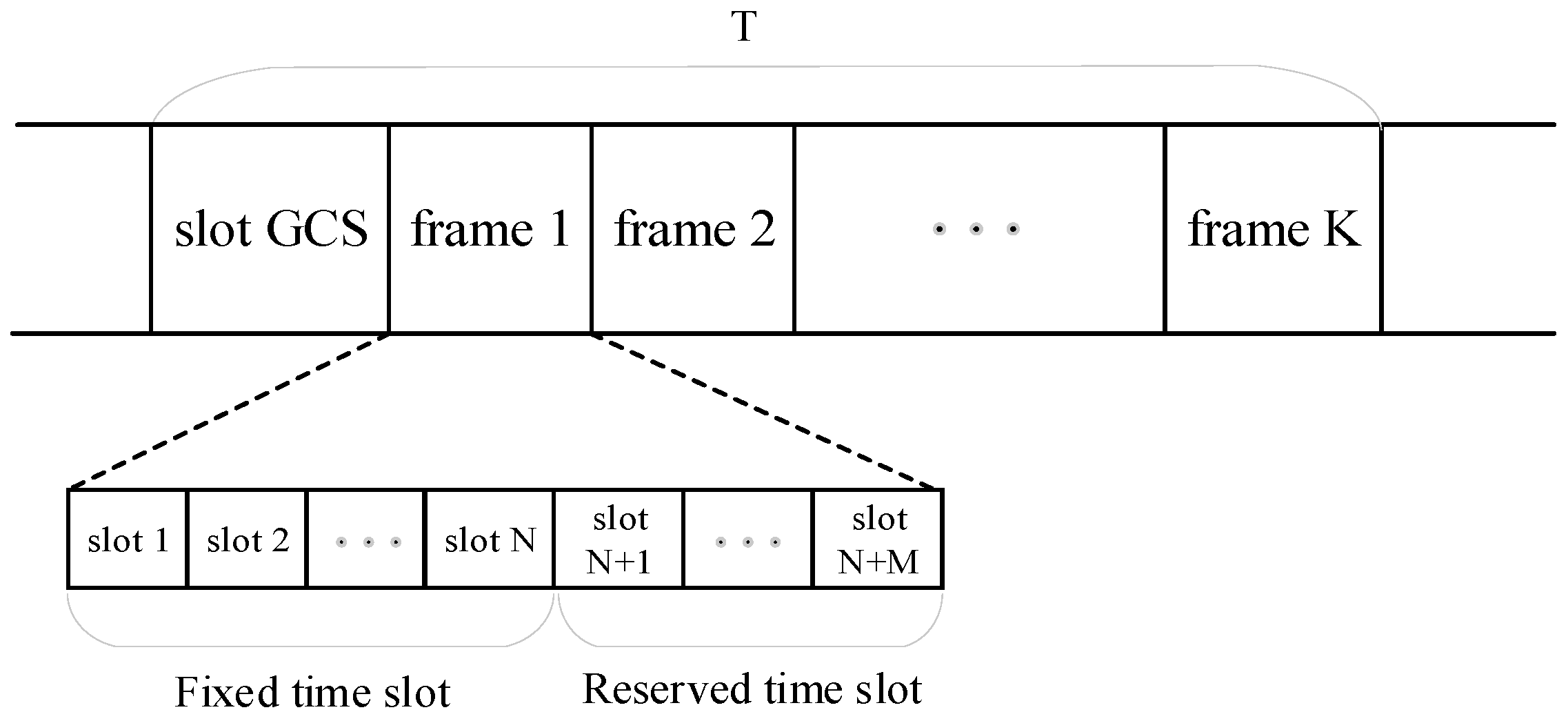
3.2.2. Time Slot Allocation of Nodes
- Time slot allocation in the network partitioning phase
- 2.
- Time slot allocation in the neighbor discovery phase
- 3.
- Time slot allocation in the clustering phase
4. Design of a Capacity-Constrained Weighted Clustering Algorithm
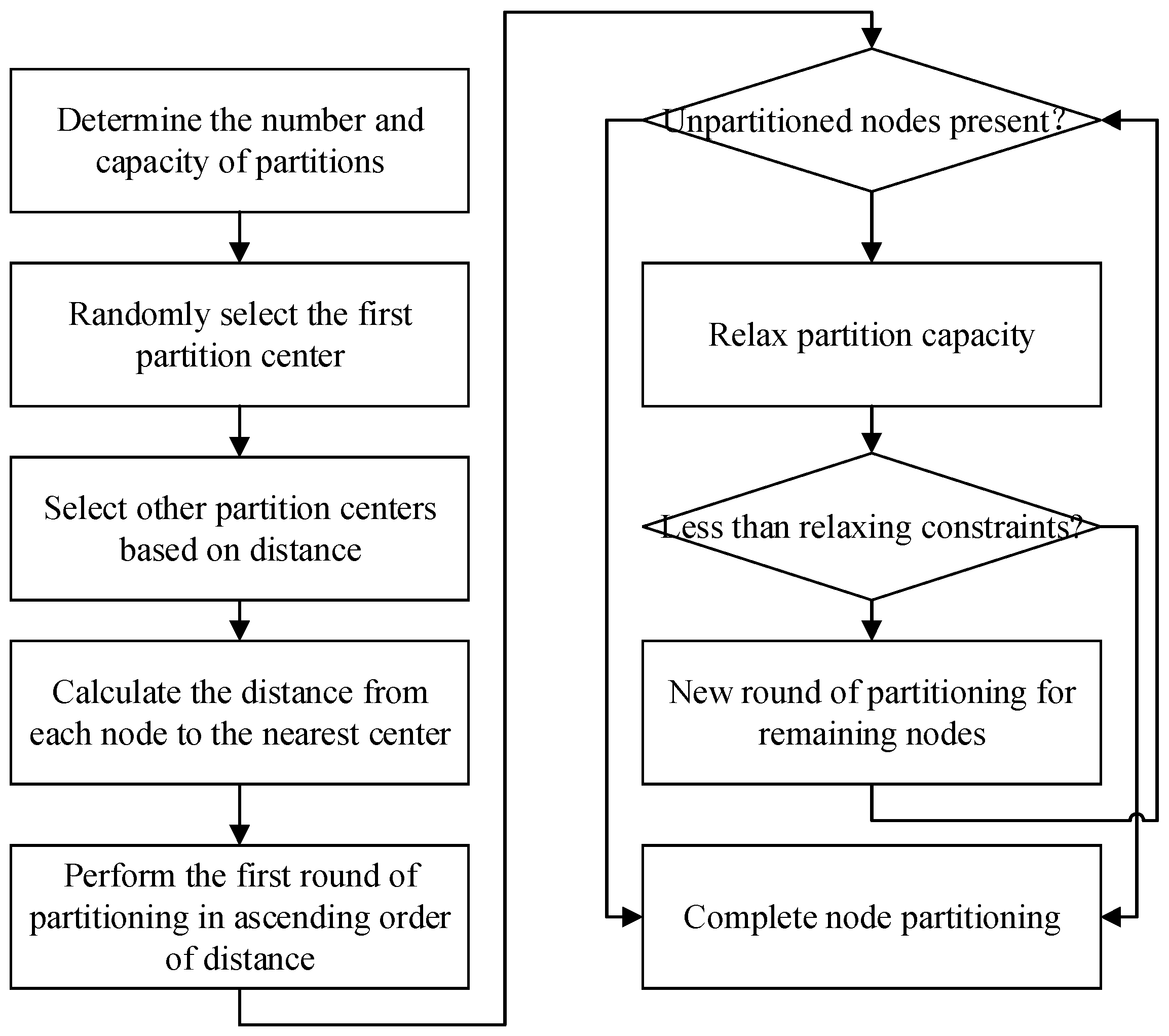
4.1. Network Partition
| Algorithm 1. Capacity-constrained partitioning algorithm based on K-means++ | |
| Input: Total number of nodes numNodes, number of partitions numClusters, maximum number of nodes per partition maxNodes, relaxation of constraints relaxation, maximum constraint relaxation maxRelaxation | |
| Output: Partition set P = {, ,…, } | |
| //K-means++ initialization | |
| 1 | Randomly select a node as the first partition center |
| 2 | for k = 2 to numClusters do |
| 3 | Select the next partition center based on distance |
| 4 | end for |
| //Preliminary Node Allocation | |
| 5 | Calculate the distance from each node to the nearest cluster center |
| 6 | Sort nodes by distance from smallest to largest in sortedNodeIndices[] |
| 7 | for = 1 to numNodes do |
| 8 | |
| 9 | Get the target partition |
| 10 | if number of nodes in partition <maxNodes do |
| 11 | Allocate node to the partition |
| 12 | end if |
| 13 | end for |
| // Dynamic relaxation of allocation | |
| 14 | if unallocated nodes exist and relaxation ≤ maxRelaxation do |
| 15 | Allow the number of nodes per partition to be maxNodesPerCluster + relaxation |
| 16 | Attempt to reassign unallocated nodes again |
| 17 | if there are still unallocated nodes do |
| 18 | relaxation = relaxation + 1 |
| 19 | end if |
| 20 | end if |
| 21 | return Partition set P = {, ,…, } |
4.2. CH and BCH Node Selection
- Connectivity Factor
- 2.
- Remaining energy factor
- 3.
- Mobility similarity factor
- 4.
- External interference factor
- 5.
- Average distance factor
| Algorithm 2. Anti-interference weighted selection algorithm for CHs and BCHs | |
| Input: Partition set P = {, ,…, }, node information nodes, number of partitions numClusters | |
| Output: = {, , …, }, = {, , …, } | |
| //Calculate node weights | |
| 1 | for = 1 to numClusters do |
| 2 | do |
| 3 | Calculate the cluster head selection factors by nodes |
| 4 | |
| 5 | end for |
| 6 | end for |
| //Select CHs and BCHs based on weights | |
| 7 | for = 1 to numClusters do |
| 8 | Nodes within the partition are sorted in descending order of weight |
| 9 | = number of the node with the minimum weight |
| 10 | = number of the node with the second smallest weight |
| 11 | if there are nodes with the same weight do |
| 12 | Compare connectivity and select those with high connectivity |
| 13 | end if |
| 14 | end for |
| 15 | return = {, , …, }, = {, , …, } |
4.3. Dynamic Maintenance of the Clustered Network
- Joining the cluster member node
- 2.
- Offline of the cluster member node
- 3.
- Offline of the cluster head node
5. Simulation and Results
5.1. Simulation Parameter Settings
- External interference factor (): The interference is a critical determinant of communication stability, especially in complex emergency rescue environments, where it can cause signal attenuation, data loss, and connection interruptions. To ensure that the system can effectively cope with interference and maintain communication stability, the weight of the external interference factor is set to 0.30, prioritizing nodes with strong anti-jamming capabilities during CH and BCH selection.
- Connectivity Factor (): The number of neighboring nodes directly affects network stability and scalability, since intra-cluster communication relies on the cluster head. So the cluster head should prioritize selecting UAVs that are connected to more neighbor nodes to ensure efficient communication. Based on this, the weight of the connectivity factor is set to 0.25 to ensure the selection of nodes with a larger number of neighboring nodes as the cluster head.
- Average distance factor (): Distance is an important factor influencing communication efficiency and energy consumption. Cluster heads tend to select nodes that are closer to others to reduce communication delay, improve signal quality, and lower energy consumption. Therefore, the weight of distance is set to 0.20 to ensure that cluster head selection optimizes communication quality and energy efficiency to the greatest extent.
- Remaining energy factor (): Remaining energy determines node longevity and overall network lifespan. To extend the network’s operational time and ensure system stability, the weight of the energy factor is set to 0.15, allowing the node’s energy state to be fully considered during cluster head selection.
- Mobility similarity factor (): Mobility affects cluster-head stability, since rapid speed differences can lead to frequent role changes. Considering that the speed difference between nodes is relatively small in this task scenario, the influence of mobility on cluster head selection is relatively small. So the weight of the mobility similarity factor is set to 0.10 to appropriately reflect the dynamic characteristics of the nodes during selection.
5.2. Clustering Network and Dynamic Maintenance Function Simulation
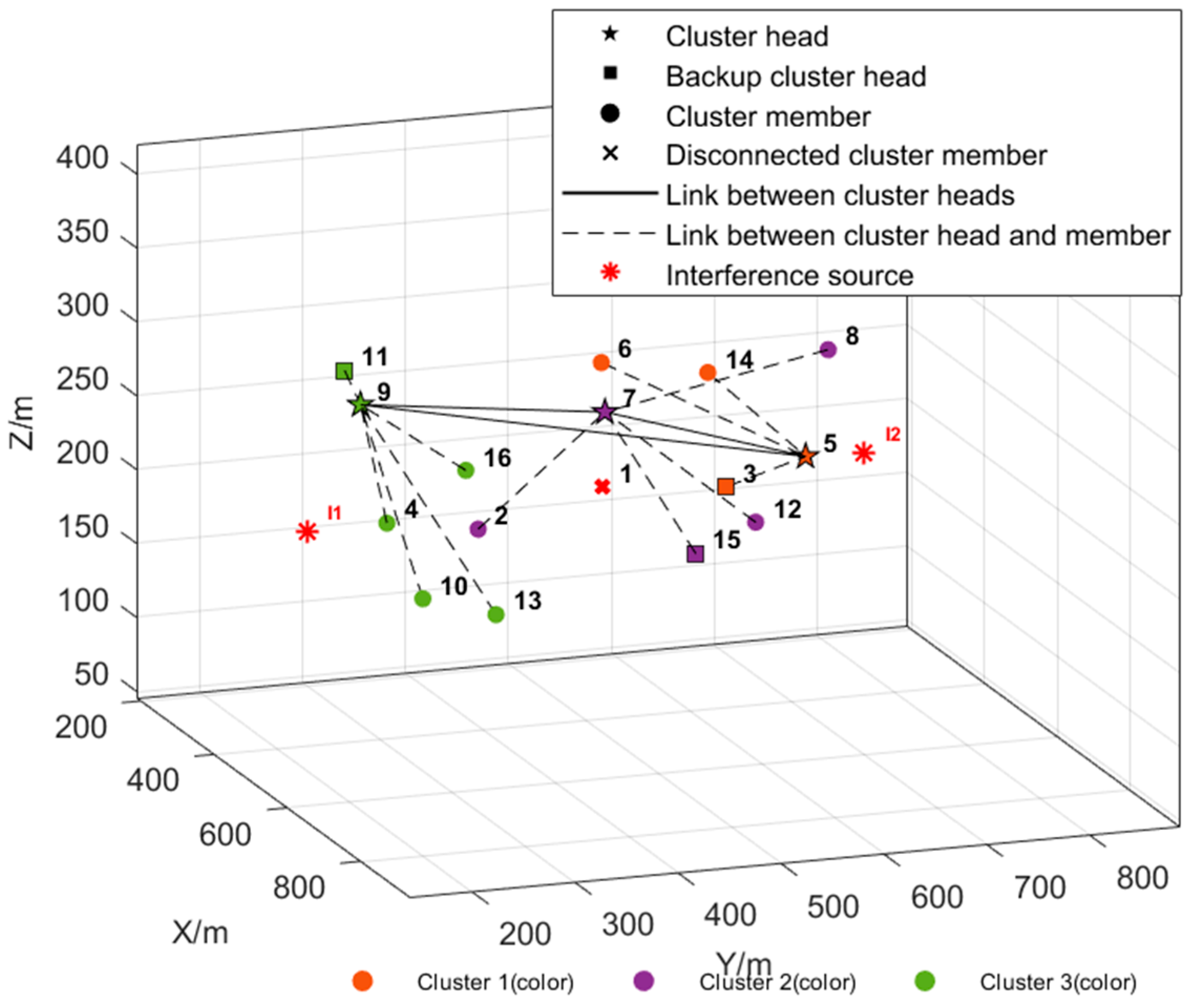
5.2.1. Simulation of Clustering Network Function
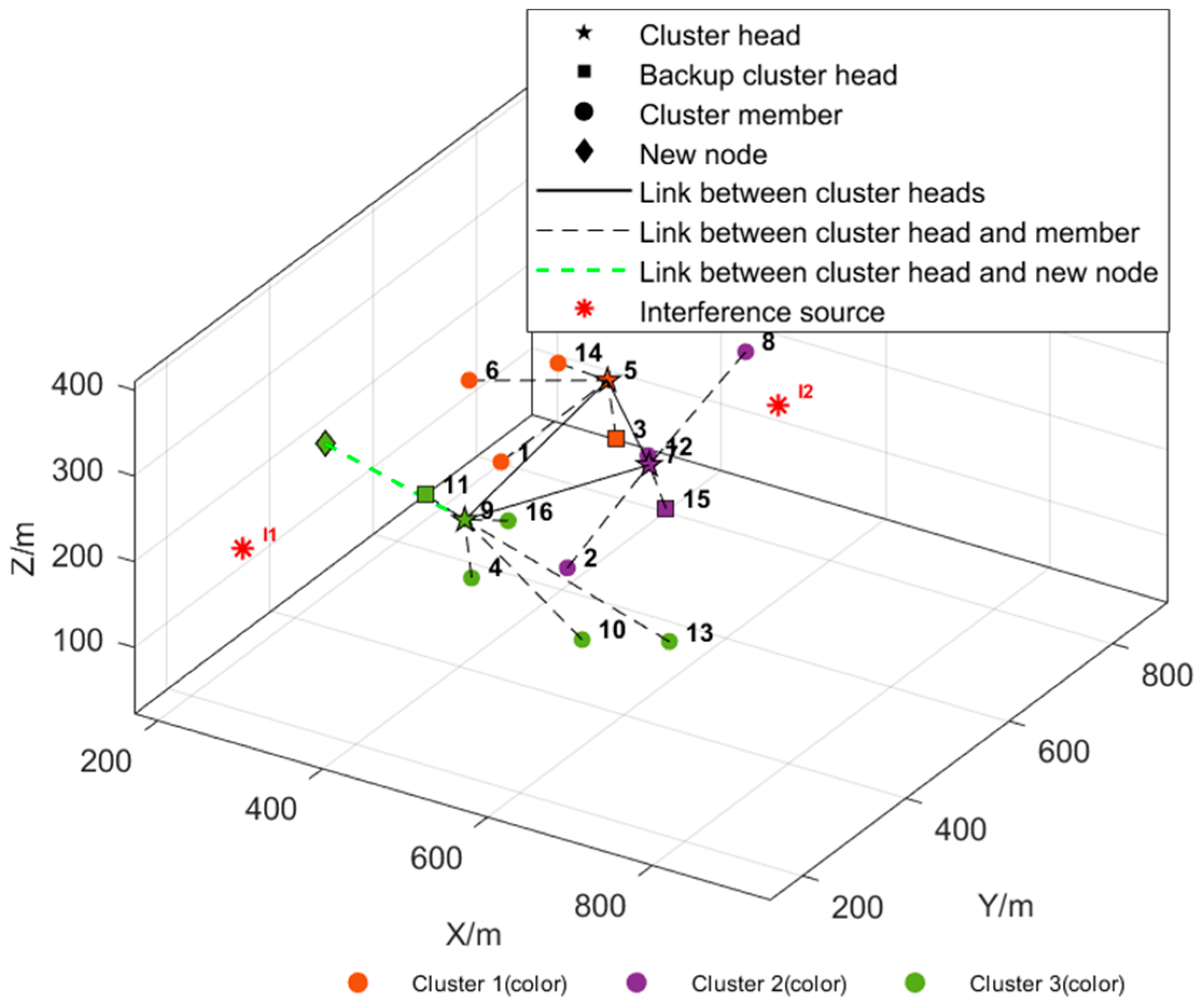
5.2.2. Simulation of Dynamic Maintenance Function Under Interference
- 4.
- Cluster member disconnected
- 5.
- Cluster head disconnected
- 6.
- New Node Joining
5.3. Analysis of Indicator Simulation Results
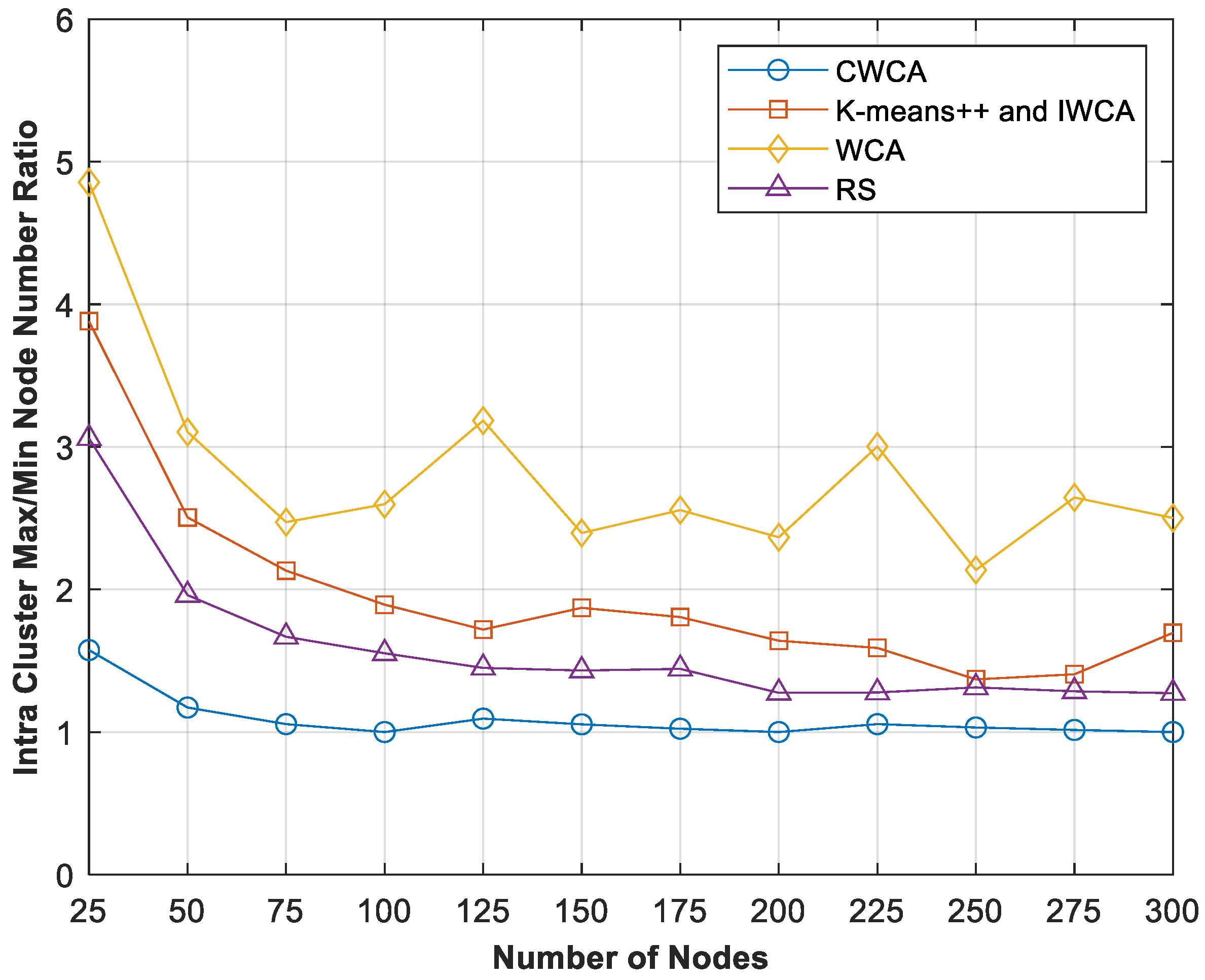
5.3.1. Balance of Intra-Cluster Node Distribution
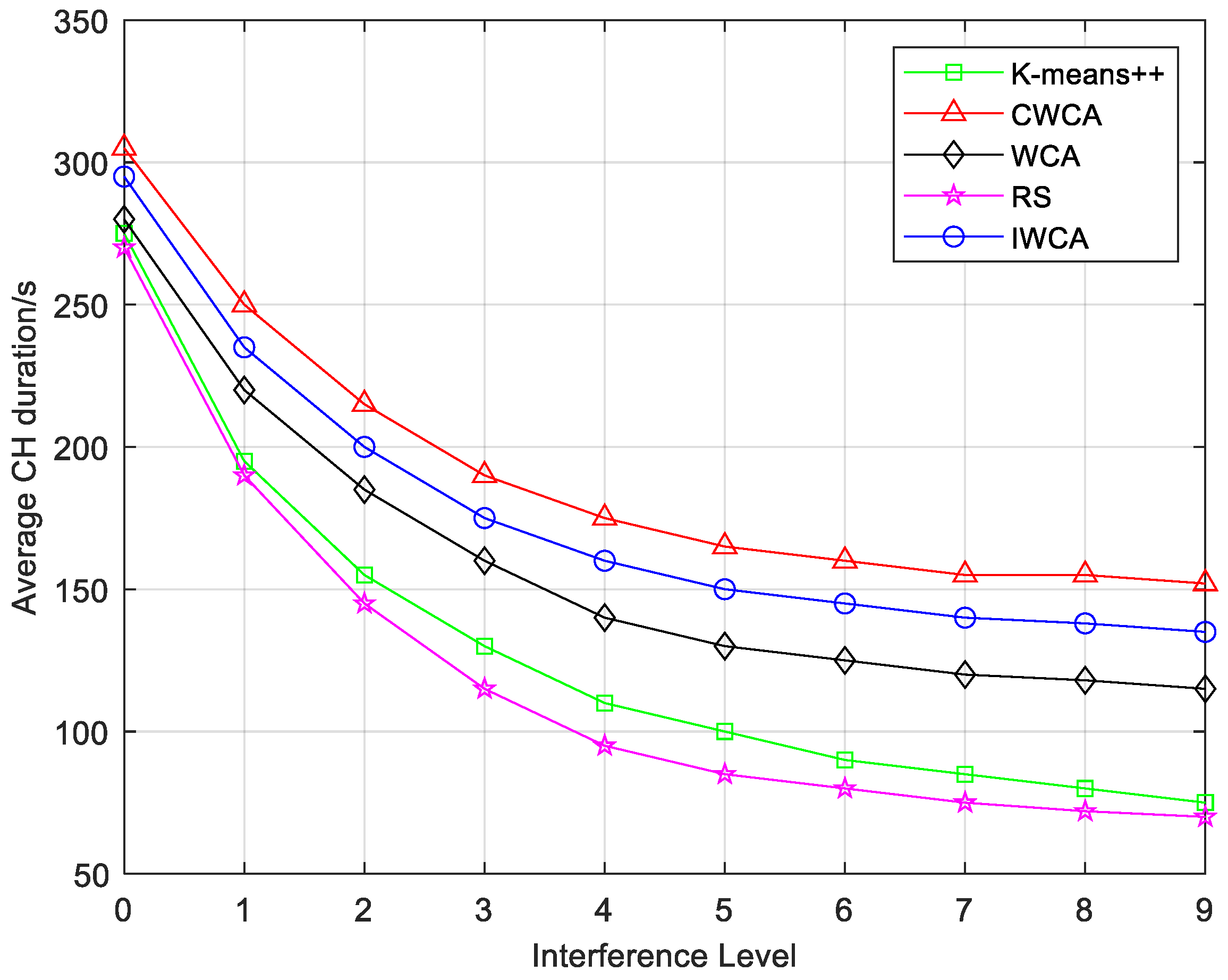
5.3.2. Average Cluster Head Duration Under Interference
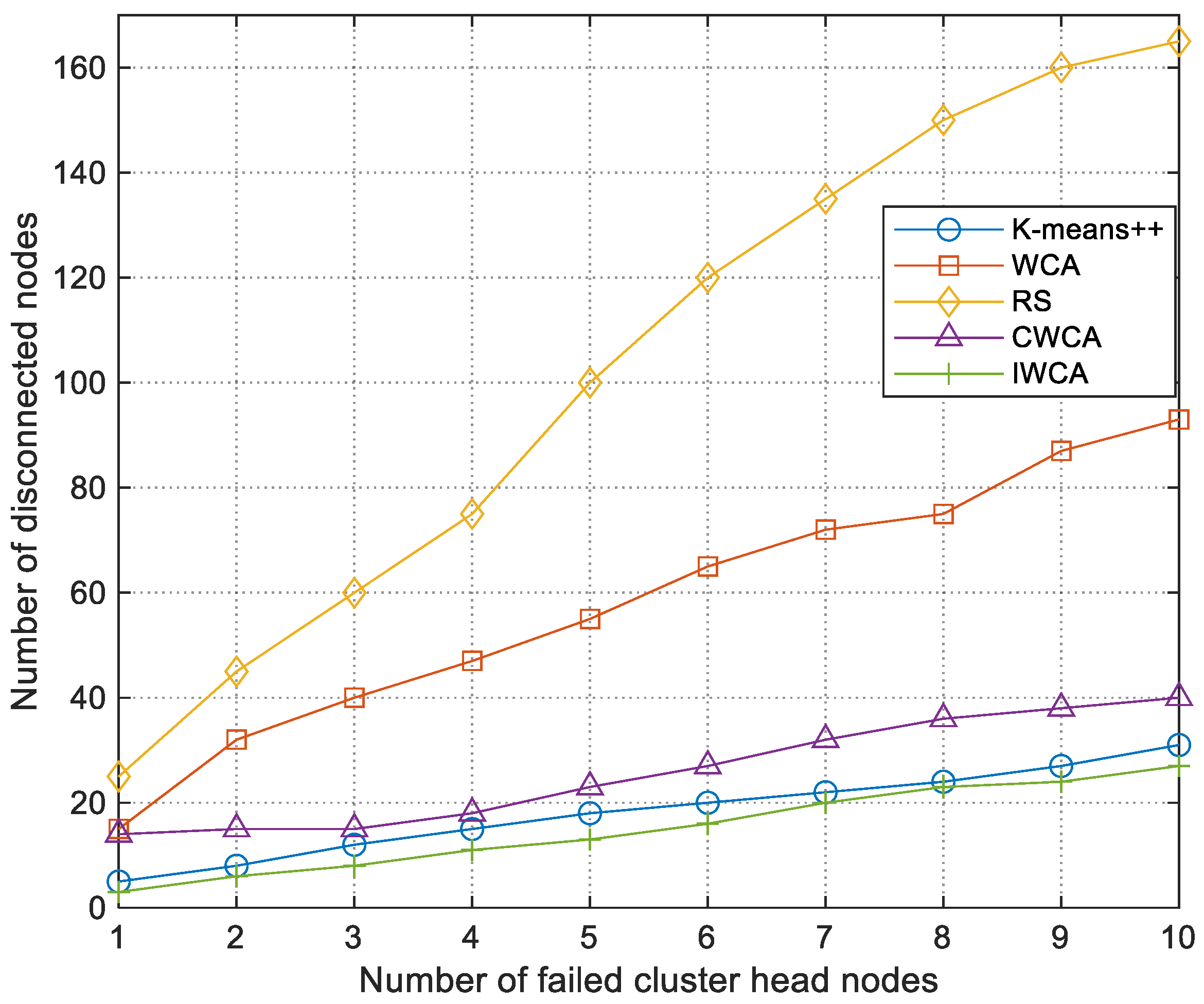
5.3.3. Reconstruction Performance of Cluster Head Failure Under Interference
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Mohsan, S.A.H.; Othman, N.Q.H.; Li, Y.; Alsharif, M.H.; Khan, M.A. Unmanned Aerial Vehicles (UAVs): Practical Aspects, Applications, Open Challenges, Security Issues, and Future Trends. Intel. Serv. Robot. 2023, 16, 109–137. [Google Scholar] [CrossRef] [PubMed]
- Bekmezci, İ.; Sahingoz, O.K.; Temel, Ş. Flying Ad-Hoc Networks (FANETs): A Survey. Ad Hoc Netw. 2013, 11, 1254–1270. [Google Scholar] [CrossRef]
- Qamar, R.A.; Sarfraz, M.; Ghauri, S.A.; Mahmood, A. TRMaxAlloc: Maximum Task Allocation Using Reassignment Algorithm in Multi-UAV System. Comput. Commun. 2023, 206, 110–123. [Google Scholar] [CrossRef]
- Zhang, Y.; Gao, X.; Ye, N.; Niyato, D.; Han, Z.; Yang, K. Joint UAV Deployment, Power Allocation, and Coalition Formation for Physical Layer Security in Heterogeneous Networks. IEEE Trans. Veh. Technol. 2025, 74, 10994–11009. [Google Scholar] [CrossRef]
- Shah, Z.; Javed, U.; Naeem, M.; Zeadally, S.; Ejaz, W. Mobile Edge Computing (MEC)-Enabled UAV Placement and Computation Efficiency Maximization in Disaster Scenario. IEEE Trans. Veh. Technol. 2023, 72, 13406–13416. [Google Scholar] [CrossRef]
- Xu, J.; Ota, K.; Dong, M. Big Data on the Fly: UAV-Mounted Mobile Edge Computing for Disaster Management. IEEE Trans. Netw. Sci. Eng. 2020, 7, 2620–2630. [Google Scholar] [CrossRef]
- Sanz-Martos, S.; López-Franco, M.D.; Álvarez-García, C.; Granero-Moya, N.; López-Hens, J.M.; Cámara-Anguita, S.; Pancorbo-Hidalgo, P.L.; Comino-Sanz, I.M. Drone Applications for Emergency and Urgent Care: A Systematic Review. Prehospital Disaster Med. 2022, 37, 502–508. [Google Scholar] [CrossRef] [PubMed]
- Wang, Y.; Chen, W.; Luan, T.H.; Su, Z.; Xu, Q.; Li, R.; Chen, N. Task Offloading for Post-Disaster Rescue in Unmanned Aerial Vehicles Networks. IEEE/ACM Trans. Netw. 2022, 30, 1525–1539. [Google Scholar] [CrossRef]
- Oubbati, O.S.; Atiquzzaman, M.; Lorenz, P.; Tareque, H.; Hossain, S. Routing in Flying Ad Hoc Networks: Survey, Constraints, and Future Challenge Perspectives. IEEE Access 2019, 7, 81057–81105. [Google Scholar] [CrossRef]
- Mowla, N.I.; Tran, N.H.; Doh, I.; Chae, K. AFRL: Adaptive Federated Reinforcement Learning for Intelligent Jamming Defense in FANET. J. Commun. Netw. 2020, 22, 244–258. [Google Scholar] [CrossRef]
- Yasser, M.; Shalash, O.; Ismail, O. Optimized Decentralized Swarm Communication Algorithms for Efficient Task Allocation and Power Consumption in Swarm Robotics. Robotics 2024, 13, 66. [Google Scholar] [CrossRef]
- Li, Y.; Gao, X.; Shi, M.; Kang, J.; Niyato, D.; Yang, K. Dynamic Weighted Energy Minimization for Aerial Edge Computing Networks. IEEE Internet Things J. 2025, 12, 683–697. [Google Scholar] [CrossRef]
- Yang, K.; Wang, Y.; Gao, X.; Shi, C.; Huang, Y.; Yuan, H.; Shi, M. Communications in Space–Air–Ground Integrated Networks: An Overview. Space Sci. Technol. 2025, 5, 0199. [Google Scholar] [CrossRef]
- Chen, X.; Tang, J.; Lao, S. Review of Unmanned Aerial Vehicle Swarm Communication Architectures and Routing Protocols. Appl. Sci. 2020, 10, 3661. [Google Scholar] [CrossRef]
- Alzahrani, B.; Oubbati, O.S.; Barnawi, A.; Atiquzzaman, M.; Alghazzawi, D. UAV Assistance Paradigm: State-of-the-Art in Applications and Challenges. J. Netw. Comput. Appl. 2020, 166, 102706. [Google Scholar] [CrossRef]
- Zhang, Y.; Gao, X.; Shi, M.; Yuan, H.; Kang, J.; Niyato, D.; Yang, K. Robust Secure UAV Communications with the Aid of Jamming Beamforming. IEEE Trans. Commun. 2025. [Google Scholar] [CrossRef]
- Gheisari, M.; Abbasi, A.A.; Sayari, Z.; Rizvi, Q.; Asheralieva, A.; Banu, S.; Awaysheh, F.M.; Shah, S.B.H.; Raza, K.A. A Survey on Clustering Algorithms in Wireless Sensor Networks: Challenges, Research, and Trends. In Proceedings of the 2020 International Computer Symposium (ICS), Tainan, Taiwan, 17–19 December 2020; pp. 294–299. [Google Scholar]
- Geng, R.; Ji, R.; Zi, S. Research on Task Allocation of UAV Cluster Based on Particle Swarm Quantization Algorithm. Math. Biosci. Eng. 2022, 20, 18–33. [Google Scholar] [CrossRef]
- Aadil, F.; Ahsan, W.; Rehman, Z.U.; Shah, P.A.; Rho, S.; Mehmood, I. Clustering Algorithm for Internet of Vehicles (IoV) Based on Dragonfly Optimizer (CAVDO). J. Supercomput. 2018, 74, 4542–4567. [Google Scholar] [CrossRef]
- Liu, Y.; Li, Y.; Cheng, W.; Wang, W.; Yang, J. UAV-Assisted Cluster-Based Task Allocation for Mobile Crowdsensing in a Space–Air–Ground–Sea Integrated Network. Sensors 2023, 24, 208. [Google Scholar] [CrossRef]
- Yu, J.Y.; Chong, P.H.J. A Survey of Clustering Schemes for Mobile Ad Hoc Networks. IEEE Commun. Surv. Tutor. 2005, 7, 32–48. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S.; Badotra, S.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S.; Alassery, F. Energy-Efficient Clustering Scheme for Flying Ad-Hoc Networks Using an Optimized LEACH Protocol. Energies 2021, 14, 6016. [Google Scholar] [CrossRef]
- Lin, C.R.; Gerla, M. Adaptive Clustering for Mobile Wireless Networks. IEEE J. Sel. Areas Commun. 1997, 15, 1265–1275. [Google Scholar] [CrossRef]
- Amis, A.D.; Prakash, R. Load-Balancing Clusters in Wireless Ad Hoc Networks. In Proceedings of the Proceedings 3rd IEEE Symposium on Application-Specific Systems and Software Engineering Technology, Richardson, TX, USA, 24–25 March 2000; pp. 25–32. [Google Scholar]
- Gerla, M.; Tzu-Chieh Tsai, J. Multicluster, Mobile, Multimedia Radio Network. Wirel. Netw. 1995, 1, 255–265. [Google Scholar] [CrossRef]
- Chatterjee, M.; Das, S.K.; Turgut, D. WCA: A Weighted Clustering Algorithm for Mobile Ad Hoc Networks. Clust. Comput. 2002, 5, 193–204. [Google Scholar] [CrossRef]
- Aadil, F.; Bajwa, K.B.; Khan, S.; Chaudary, N.M.; Akram, A. CACONET: Ant Colony Optimization (ACO) Based Clustering Algorithm for VANET. PLoS ONE 2016, 11, e0154080. [Google Scholar] [CrossRef] [PubMed]
- Arafat, M.Y.; Moh, S. Bio-Inspired Approaches for Energy-Efficient Localization and Clustering in UAV Networks for Monitoring Wildfires in Remote Areas. IEEE Access 2021, 9, 18649–18669. [Google Scholar] [CrossRef]
- Ali, Z.A.; Han, Z.; Masood, R.J. Collective Motion and Self-Organization of a Swarm of UAVs: A Cluster-Based Architecture. Sensors 2021, 21, 3820. [Google Scholar] [CrossRef]
- Sun, G.; Qin, D.; Lan, T.; Ma, L. Research on Clustering Routing Protocol Based on Improved PSO in FANET. IEEE Sens. J. 2021, 21, 27168–27185. [Google Scholar] [CrossRef]
- Kaur, P.; Singh, A. Nature-Inspired Optimization Techniques in VANETs and FANETs: A Survey. In Proceedings of the Advanced Computational and Communication Paradigms, Sikkim, India, 8–10 September 2017; Bhattacharyya, S., Chaki, N., Konar, D., Chakraborty, U.K., Singh, C.T., Eds.; Springer: Singapore, 2018; pp. 651–663. [Google Scholar]
- Wang, X.; Liu, Z.; Jian, C.; Shi, S.; Gu, J.; Shi, F. A Dynamic Scale UAV Weighted Clustering Algorithm. In Proceedings of the 2021 IEEE International Conference on Unmanned Systems (ICUS), Beijing, China, 15–17 October 2021; pp. 209–213. [Google Scholar]
- Sun, Y.; Mi, Z.; Wang, H.; Lu, F.; Zhao, N. Adaptive Enhanced Weighted Clustering Algorithm for UAV Swarm. In Proceedings of the 2020 IEEE 20th International Conference on Communication Technology (ICCT), Nanning, China, 28–31 October 2020; pp. 709–714. [Google Scholar]
- Yang, X.; Yu, T.; Chen, Z.; Yang, J.; Hu, J.; Wu, Y. An Improved Weighted and Location-Based Clustering Scheme for Flying Ad Hoc Networks. Sensors 2022, 22, 3236. [Google Scholar] [CrossRef]
- Khayat, G.; Mavromoustakis, C.X.; Pitsillides, A.; Batalla, J.M.; Markakis, E.K.; Mastorakis, G. On the Weighted Cluster S-UAV Scheme Using Latency-Oriented Trust. IEEE Access 2023, 11, 56310–56323. [Google Scholar] [CrossRef]
- Zhang, Y.; Hu, Z.; Wang, Z.; Wen, X.; Lu, Z. Survivability Analysis of Unmanned Aerial Vehicle Network Based on Dynamic Weighted Clustering Algorithm with Dual Cluster Heads. Electronics 2023, 12, 1743. [Google Scholar] [CrossRef]
- Ye, Y.; Zhang, X.; Xie, L.; Qin, K. A Dynamic TDMA Scheduling Strategy for MANETs Based on Service Priority. Sensors 2020, 20, 7218. [Google Scholar] [CrossRef]
- Arthur, D.; Vassilvitskii, S. K-Means++: The Advantages of Careful Seeding; Society for Industrial and Applied Mathematics: New Orleans, LA, USA, 2007; pp. 1027–1035. [Google Scholar]
- Gupta, P.; Kumar, P.R. The Capacity of Wireless Networks. IEEE Trans. Inf. Theory 2000, 46, 388–404. [Google Scholar] [CrossRef]
- Zeng, Y.; Zhang, R. Energy-Efficient UAV Communication with Trajectory Optimization. IEEE Trans. Wirel. Commun. 2017, 16, 3747–3760. [Google Scholar] [CrossRef]
- Zhou, Y.; Tang, D.; Zhou, H.; Xiang, X. Moving Target Geolocation and Trajectory Prediction Using a Fixed-Wing UAV in Cluttered Environments. Remote Sens. 2025, 17, 969. [Google Scholar] [CrossRef]


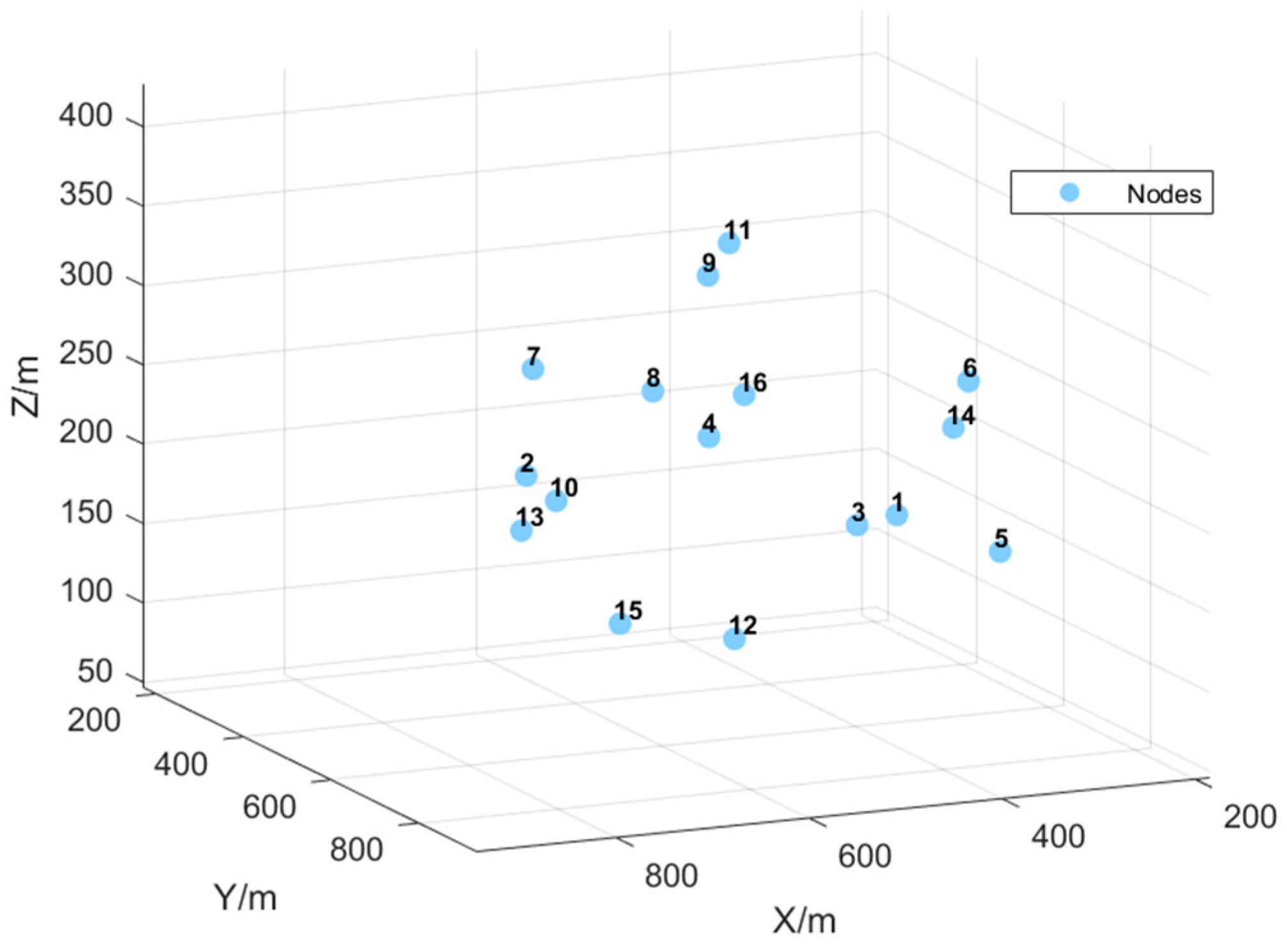
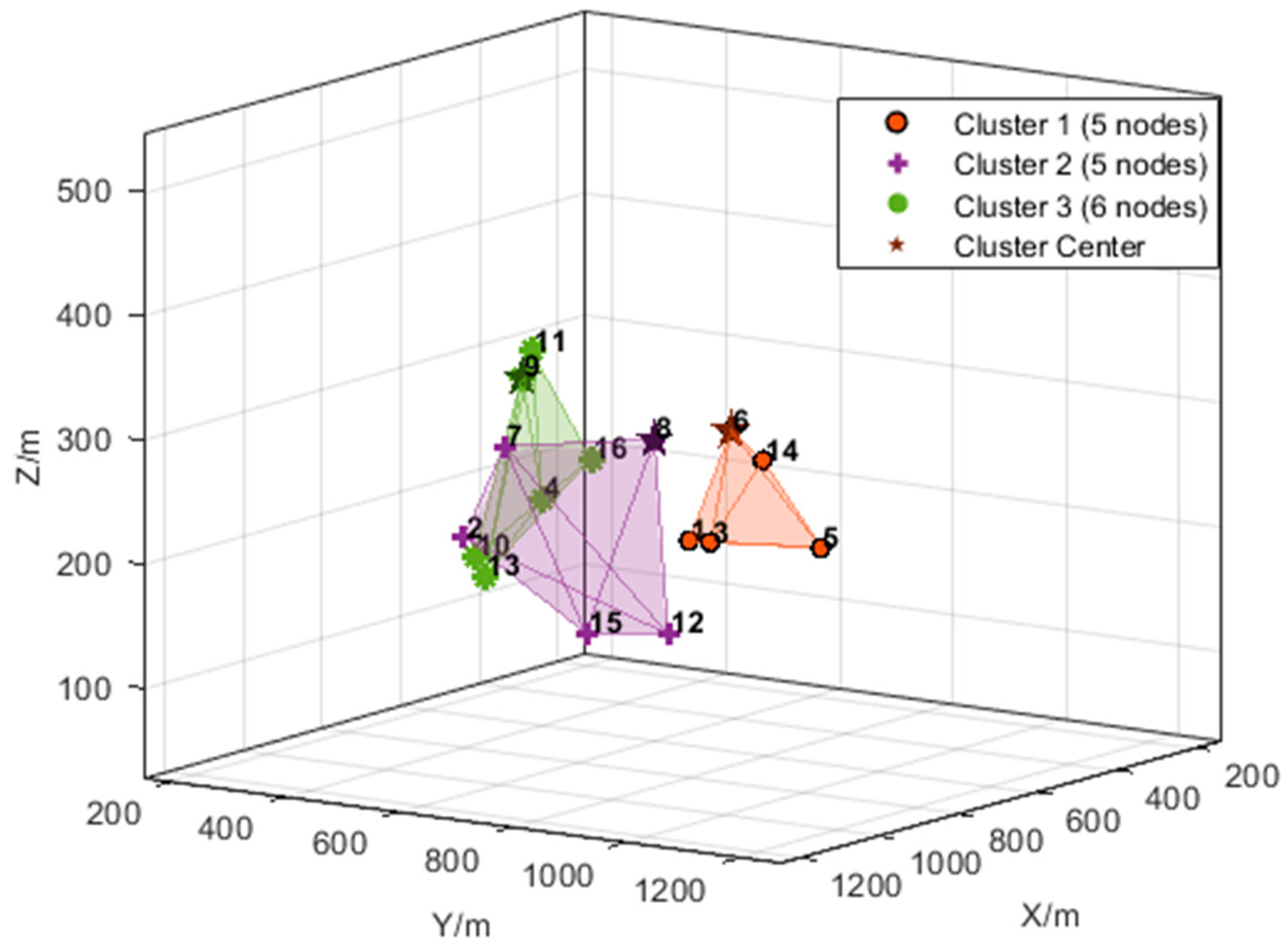
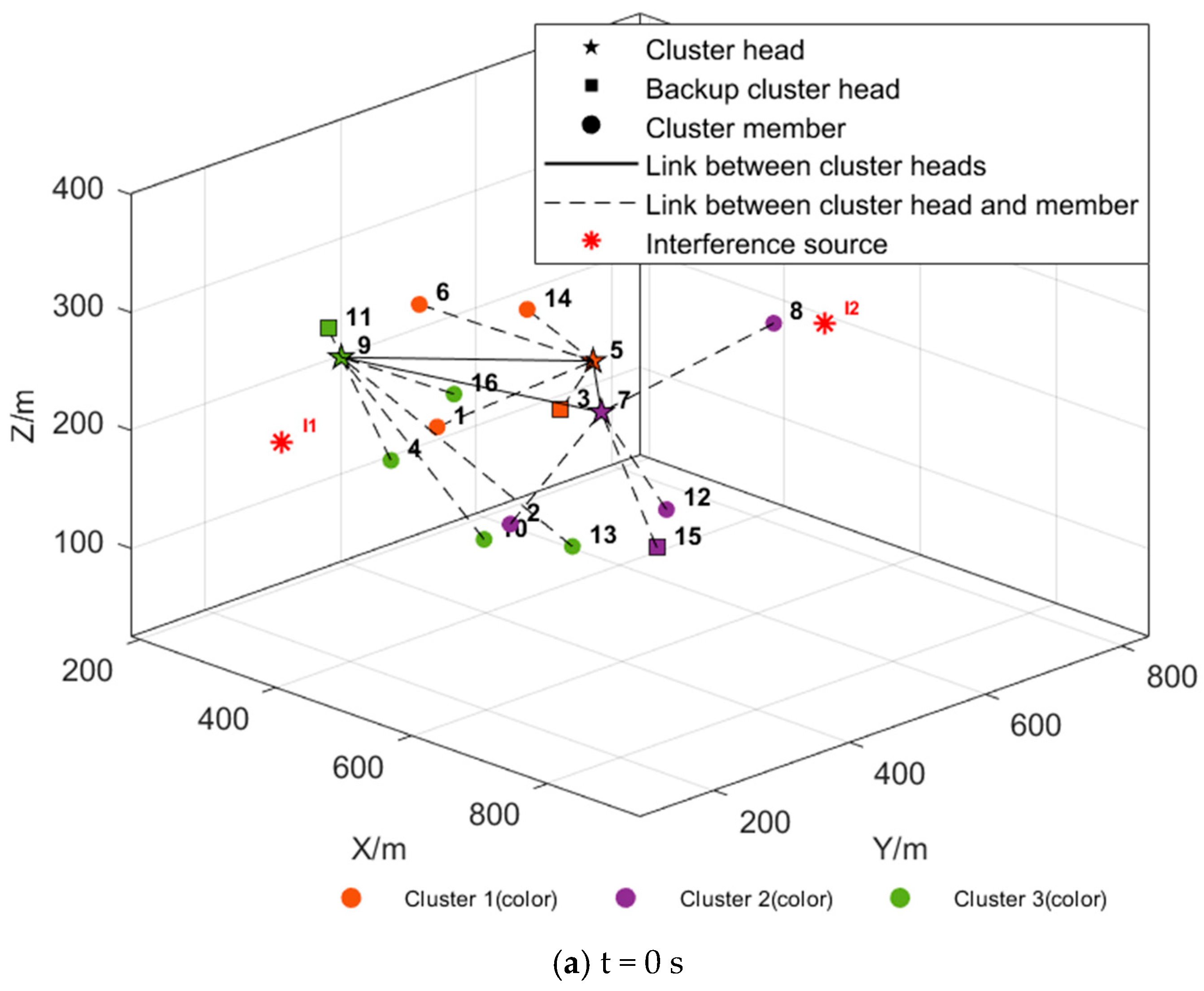
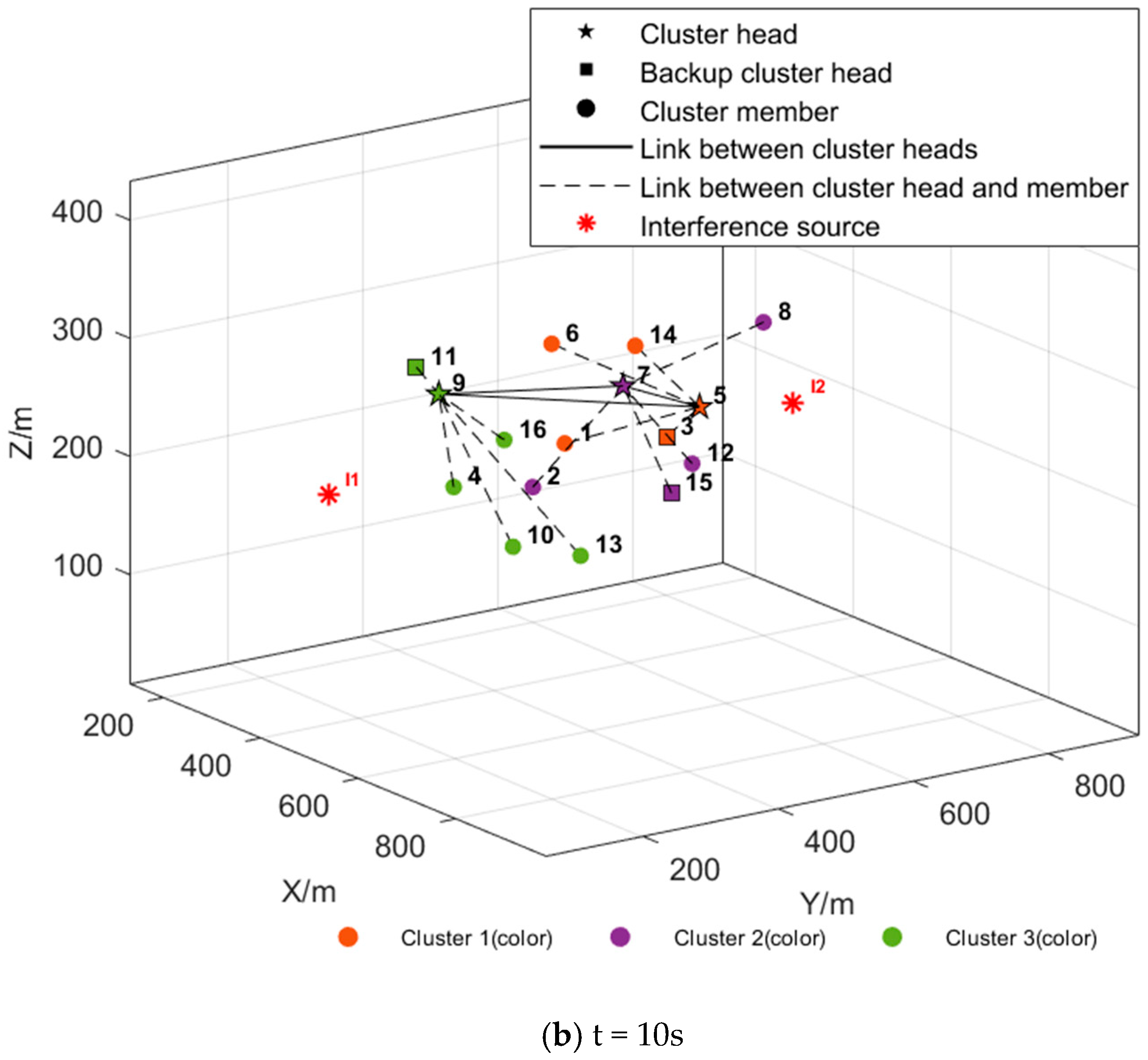



| Parameter Type | Setting |
|---|---|
| Simulation area | 1000 × 1000 × 1000 m |
| Number of nodes | 16~300 |
| Speed | 20~30 m/s |
| Acceleration | 5~10 m/s2 |
| Initial energy | 100 J |
| Intra-cluster maximum communication distance | 300 m |
| Inter-cluster maximum communication distance | 600 m |
| w | |
| Weighting coefficient |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, S.; Gong, P.; Wang, W.; Liu, J.; Feng, Z.; Gao, X. A Capacity-Constrained Weighted Clustering Algorithm for UAV Self-Organizing Networks Under Interference. Drones 2025, 9, 527. https://doi.org/10.3390/drones9080527
Li S, Gong P, Wang W, Liu J, Feng Z, Gao X. A Capacity-Constrained Weighted Clustering Algorithm for UAV Self-Organizing Networks Under Interference. Drones. 2025; 9(8):527. https://doi.org/10.3390/drones9080527
Chicago/Turabian StyleLi, Siqi, Peng Gong, Weidong Wang, Jinyue Liu, Zhixuan Feng, and Xiang Gao. 2025. "A Capacity-Constrained Weighted Clustering Algorithm for UAV Self-Organizing Networks Under Interference" Drones 9, no. 8: 527. https://doi.org/10.3390/drones9080527
APA StyleLi, S., Gong, P., Wang, W., Liu, J., Feng, Z., & Gao, X. (2025). A Capacity-Constrained Weighted Clustering Algorithm for UAV Self-Organizing Networks Under Interference. Drones, 9(8), 527. https://doi.org/10.3390/drones9080527







