Mutual Identity Authentication Based on Dynamic Identity and Hybrid Encryption for UAV–GCS Communications
Abstract
1. Introduction
2. Scheme Overview
2.1. Communication Nodes
2.2. Attack Model
3. Process of DIHE
3.1. Notations
3.2. Authentication Workflow
- Stage 1: UAV initiates an authentication request.
- (1)
- Step 1: Generate a Temporary Key Parameter.
- (2)
- Step 2: Send Authentication Message.
- Stage 2: GCS authentication and reply.
- (1)
- Step 1: Identity Authentication and Key Negotiation.
- (2)
- Step 2: Identity Updating.
- (3)
- Step 3: GCS Reply Authentication.
- Stage 3: UAV authentication and reply.
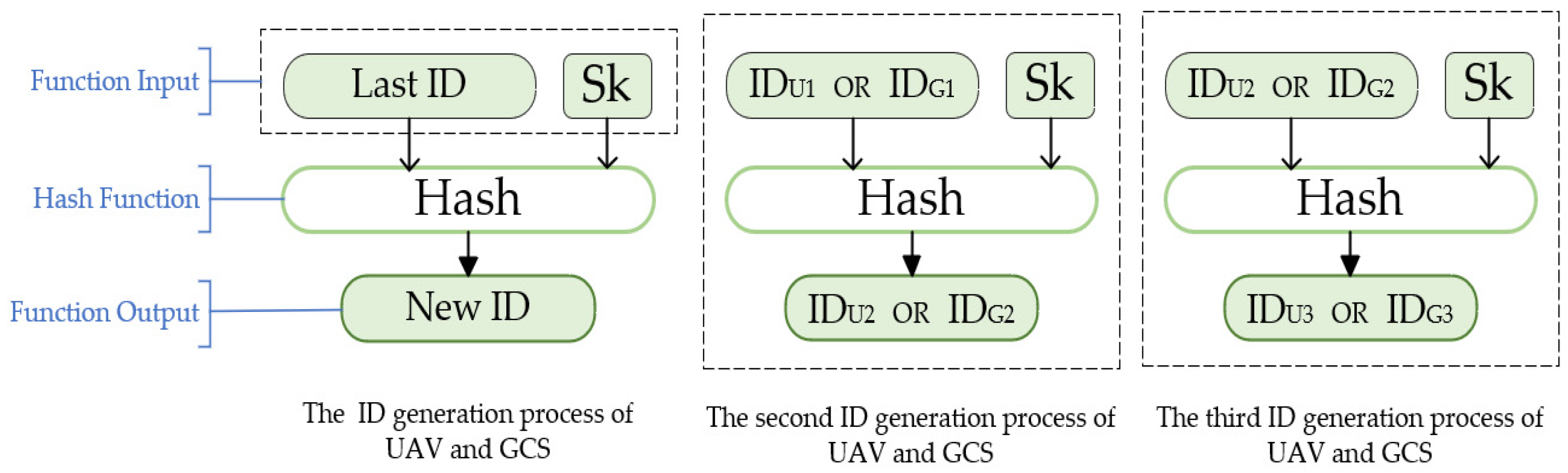
3.3. Dynamic Identity Updating
4. Security Analysis
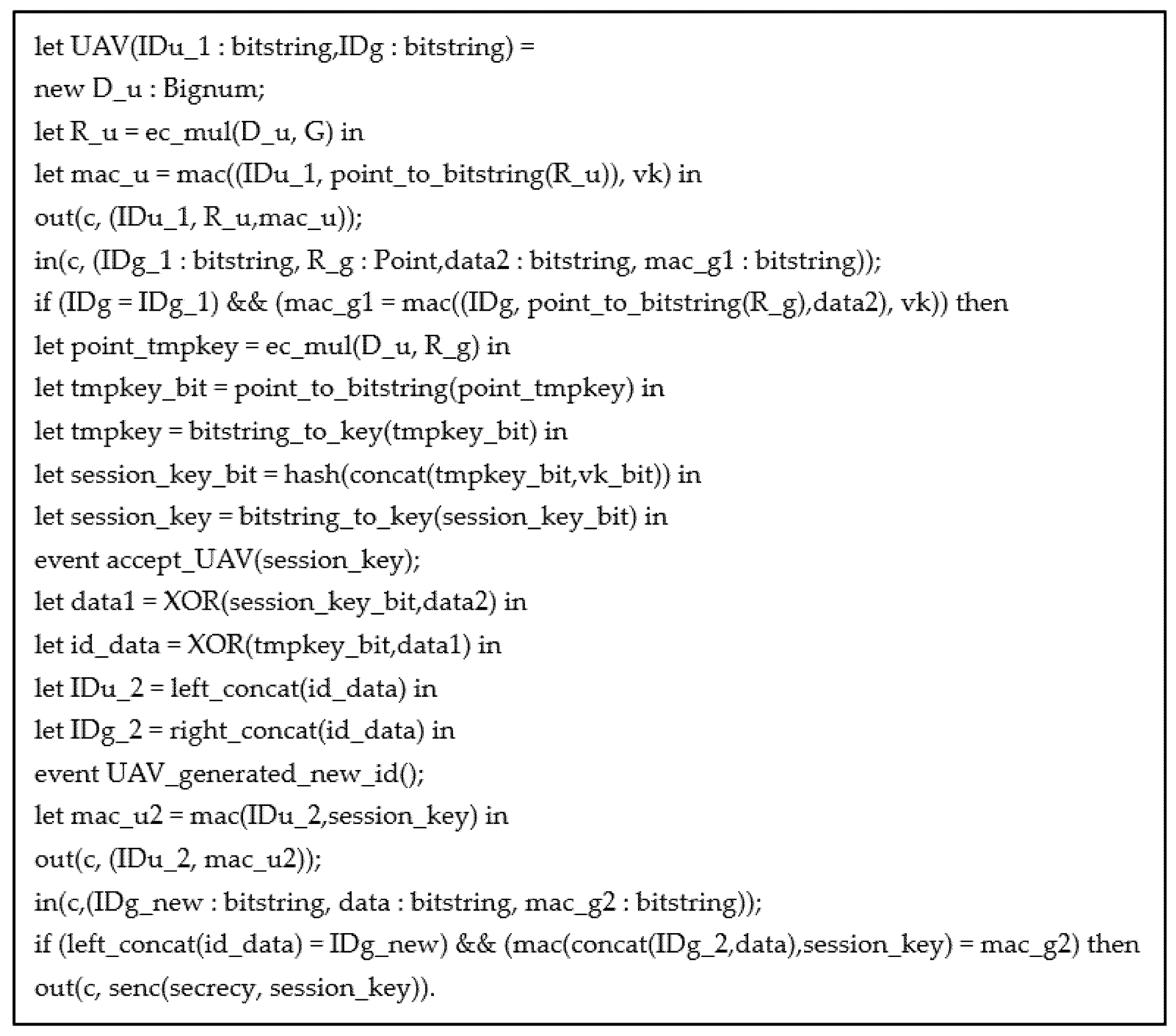
4.1. ProVerif Code Process
4.2. ProVerif Verification Procedures
4.3. Security Analysis Results
4.4. Safety Function Comparison
5. Results Analysis
5.1. Calculate Cost
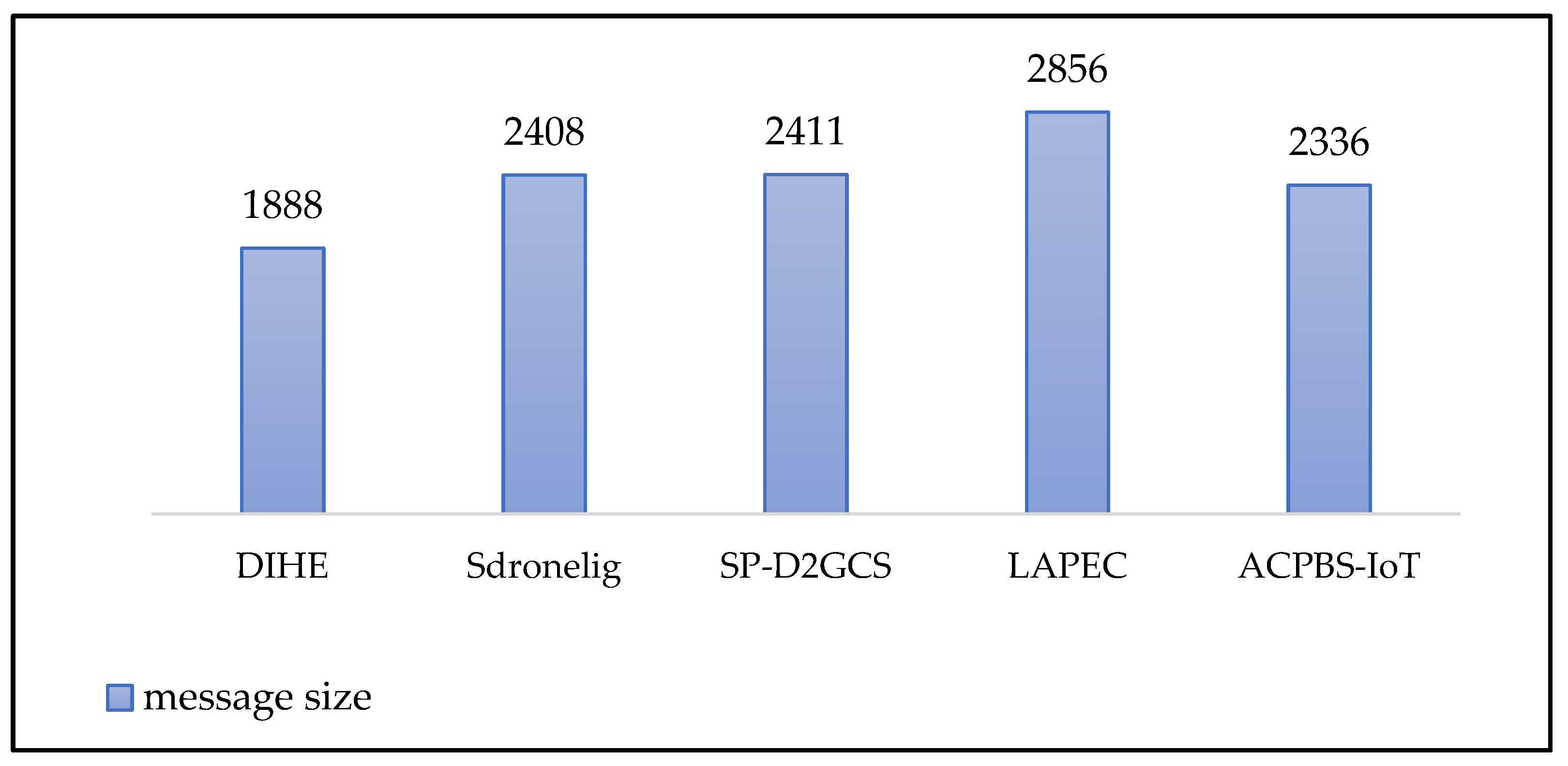
5.2. Communication Overhead
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Chang, A.; Liang, Y.; Jiang, M.; Li, X.; Chen, Z.; Liu, R. Application of UAV Intelligent Management and Control Platform on Overhead Transmission Lines Inspection. In Forthcoming Networks and Sustainability in the Iot Era; Proceedings of the FoNeS-IoT 2021, Lecture Notes on Data Engineering and Communications Technologies, Nicosia, Turkey, 27–28 December 2021; Volume 2; AlTurjman, F., Rasheed, J., Eds.; Springer: Cham, Switzerland, 2022; Volume 130, pp. 251–260. [Google Scholar]
- Wu, Y.; Chen, L.; Kong, L.; Zhang, J.; Wang, M. Research on Application Mode of Large Fixed-Wing UAV System on Overhead Transmission Line. In Proceedings of the 2017 IEEE International Conference On Unmanned Systems (ICUS), Beijing, China, 27–29 October 2017; Xu, X., Ed.; IEEE: New York, NY, USA, 2017; pp. 88–91. [Google Scholar]
- Herschel, R.; Wallrath, P.; Hofstaetter, M.; Taupe, P.; Krueger, E.; Philippi, M.; Kunze, J.; Rotter, J.M.; Heusinger, V.; Ari, M.; et al. UAV-Borne Remote Sensing for AI-Assisted Support of Search and Rescue Missions. In Proceedings of the Electro-Optical Remote Sensing XVI, Berlin, Germany, 5–8 September 2022; Kamerman, G.W., Steinvall, O., Eds.; Spie-Int Soc Optical Engineering: Bellingham, WC, USA, 2022; Volume 12272, p. 1227203. [Google Scholar]
- Zhang, D.; Yang, P.P.-J.; Tsou, J.-Y. Advancing Social Equity in Urban UAV Logistics: Insights from the Academic Literature and Social Media. Drones 2024, 8, 688. [Google Scholar] [CrossRef]
- Yaacoub, J.-P.; Noura, H.; Salman, O.; Chehab, A. Security Analysis of Drones Systems: Attacks, Limitations, and Recommendations. Internet Things 2020, 11, 100218. [Google Scholar] [CrossRef] [PubMed]
- Tedeschi, P.; Al Nuaimi, F.A.; Awad, A.I.; Natalizio, E. Privacy-Aware Remote Identification for Unmanned Aerial Vehicles: Current Solutions, Potential Threats, and Future Directions. IEEE Trans. Ind. Inform. 2024, 20, 1069–1080. [Google Scholar] [CrossRef]
- Ullah, Z.; Al-Turjman, F.; Mostarda, L. Cognition in UAV-Aided 5G and Beyond Communications: A Survey. IEEE Trans. Cogn. Commun. Netw. 2020, 6, 872–891. [Google Scholar] [CrossRef]
- Liu, Y.; Dai, H.-N.; Wang, Q.; Shukla, M.K.; Imran, M. Unmanned Aerial Vehicle for Internet of Everything: Opportunities and Challenges. Comput. Commun. 2020, 155, 66–83. [Google Scholar] [CrossRef]
- Rivest, R.L.; Shamir, A.; Adleman, L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems. Commun. Acm 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic Curve Cryptosystems. Math. Comp. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Miller, V.S. Use of Elliptic Curves in Cryptography. In Advances in Cryptology—CRYPTO ’85 Proceedings; Williams, H.C., Ed.; Springer: Berlin/Heidelberg, Germany, 1986; pp. 417–426. [Google Scholar]
- Gagnd, M. Applications of Bilinear Maps in Cryptography; University of Waterloo: Waterloo, ON, Canada, 2002. [Google Scholar]
- Fernandez, M.J.; Sanchez-Cuevas, P.J.; Heredia, G.; Ollero, A. Securing UAV Communications Using ROS with Custom ECIES-Based Method. In Proceedings of the 2019 International Workshop on Research, Education and Development of Unmanned Aerial Systems (RED UAS 2019), Cranfield, UK, 25–27 November 2019; IEEE: New York, NY, USA, 2019; pp. 237–246. [Google Scholar]
- Chen, L.; Qian, S.; Lim, M.; Wang, S. An Enhanced Direct Anonymous Attestation Scheme with Mutual Authentication for Network-Connected UAV Communication Systems. China Commun. 2018, 15, 61–76. [Google Scholar] [CrossRef]
- Tian, Y.; Yuan, J.; Song, H. Efficient Privacy-Preserving Authentication Framework for Edge-Assisted Internet of Drones. J. Inf. Secur. Appl. 2019, 48, 102354. [Google Scholar] [CrossRef]
- Rahman, K.; Khan, M.A.; Afghah, F.; Barb, G.; Innab, N.; Cheema, T.A. An Efficient Authentication and Access Control Protocol for Securing UAV Networks Against Anomaly-Based Intrusion. IEEE Access 2024, 12, 62750–62764. [Google Scholar] [CrossRef]
- Chen, C.-L.; Deng, Y.-Y.; Weng, W.; Chen, C.-H.; Chiu, Y.-J.; Wu, C.-M. A Traceable and Privacy-Preserving Authentication for UAV Communication Control System. Electronics 2020, 9, 62. [Google Scholar] [CrossRef]
- Xia, T.; Wang, M.; He, J.; Lin, S.; Shi, Y.; Guo, L. Research on Identity Authentication Scheme for UAV Communication Network. Electronics 2023, 12, 2917. [Google Scholar] [CrossRef]
- Ko, Y.; Kim, J.; Duguma, D.G.; Astillo, P.V.; You, I.; Pau, G. Drone Secure Communication Protocol for Future Sensitive Applications in Military Zone. Sensors 2021, 21, 2057. [Google Scholar] [CrossRef] [PubMed]
- Zhang, S.; Liu, Y.; Han, Z.; Yang, Z. A Lightweight Authentication Protocol for UAVs Based on ECC Scheme. Drones 2023, 7, 315. [Google Scholar] [CrossRef]
- Bera, B.; Das, A.K.; Garg, S.; Piran, M.J.; Hossain, M.S. Access Control Protocol for Battlefield Surveillance in Drone-Assisted IoT Environment. IEEE Internet Things J. 2022, 9, 2708–2721. [Google Scholar] [CrossRef]
- Iqbal, U.; Intikhab, S. Re-Keying Mechanism for TinySec Using ECC and Hash Chains. In Proceedings of the 2017 4th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 6–7 January 2017; IEEE: New York, NY, USA, 2017. [Google Scholar]
- Han, M.; Jiang, W. A Secure Communication Method Based on Message Hash Chain. Appl. Sci. 2022, 12, 4505. [Google Scholar] [CrossRef]
- Huang, Q.; Huang, H.; Wang, W.; Li, Q.; Wu, Y. An Authentication Scheme Based on Novel Construction of Hash Chains for Smart Mobile Devices. Wirel. Commun. Mob. Comput. 2020, 2020, 8888679. [Google Scholar] [CrossRef]
- Hakeem, S.A.A.; El-Kader, S.M.A.; Kim, H. A Key Management Protocol Based on the Hash Chain Key Generation for Securing LoRaWAN Networks. Sensors 2021, 21, 5838. [Google Scholar] [CrossRef]
- Alkatheiri, M.S.; Saleem, S.; Alqarni, M.A.; Aseeri, A.O.; Chauhdary, S.H.; Zhuang, Y. A Lightweight Authentication Scheme for a Network of Unmanned Aerial Vehicles (UAVs) by Using Physical Unclonable Functions. Electronics 2022, 11, 2921. [Google Scholar] [CrossRef]
- Chandran, I.; Vipin, K. A PUF Secured Lightweight Mutual Authentication Protocol for Multi-UAV Networks. Comput. Netw. 2024, 253, 110717. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Irshad, A.; Alzahrani, B.A.; Alhindi, A.; Shariq, M.; Das, A.K. TS-PAID: A Two-Stage PUF-Based Lightweight Authentication Protocol for Internet of Drones. IEEE Access 2025, 13, 1458–1469. [Google Scholar] [CrossRef]
- Lei, Y.; Zeng, L.; Li, Y.-X.; Wang, M.-X.; Qin, H. A Lightweight Authentication Protocol for UAV Networks Based on Security and Computational Resource Optimization. IEEE Access 2021, 9, 53769–53785. [Google Scholar] [CrossRef]
- Wang, W.; Han, Z.; Gadekallu, T.R.; Raza, S.; Tanveer, J.; Su, C. Lightweight Blockchain-Enhanced Mutual Authentication Protocol for UAVs. IEEE Internet Things J. 2024, 11, 9547–9557. [Google Scholar] [CrossRef]
- Zhang, L.; Xu, J.; Obaidat, M.S.; Li, X.; Vijayakumar, P. A PUF-Based Lightweight Authentication and Key Agreement Protocol for Smart UAV Networks. IET Commun. 2022, 16, 1142–1159. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C. On the Security of Public Key Protocols. Inf. Theory IEEE Trans. 1981, 29, 198–208. [Google Scholar] [CrossRef]
- Blanchet, B. An Efficient Cryptographic Protocol Verifier Based on Prolog Rules. In Proceedings of the IEEE Computer Security Foundations Workshop, Cape Breton, NS, Canada, 11–13 June 2001. [Google Scholar]



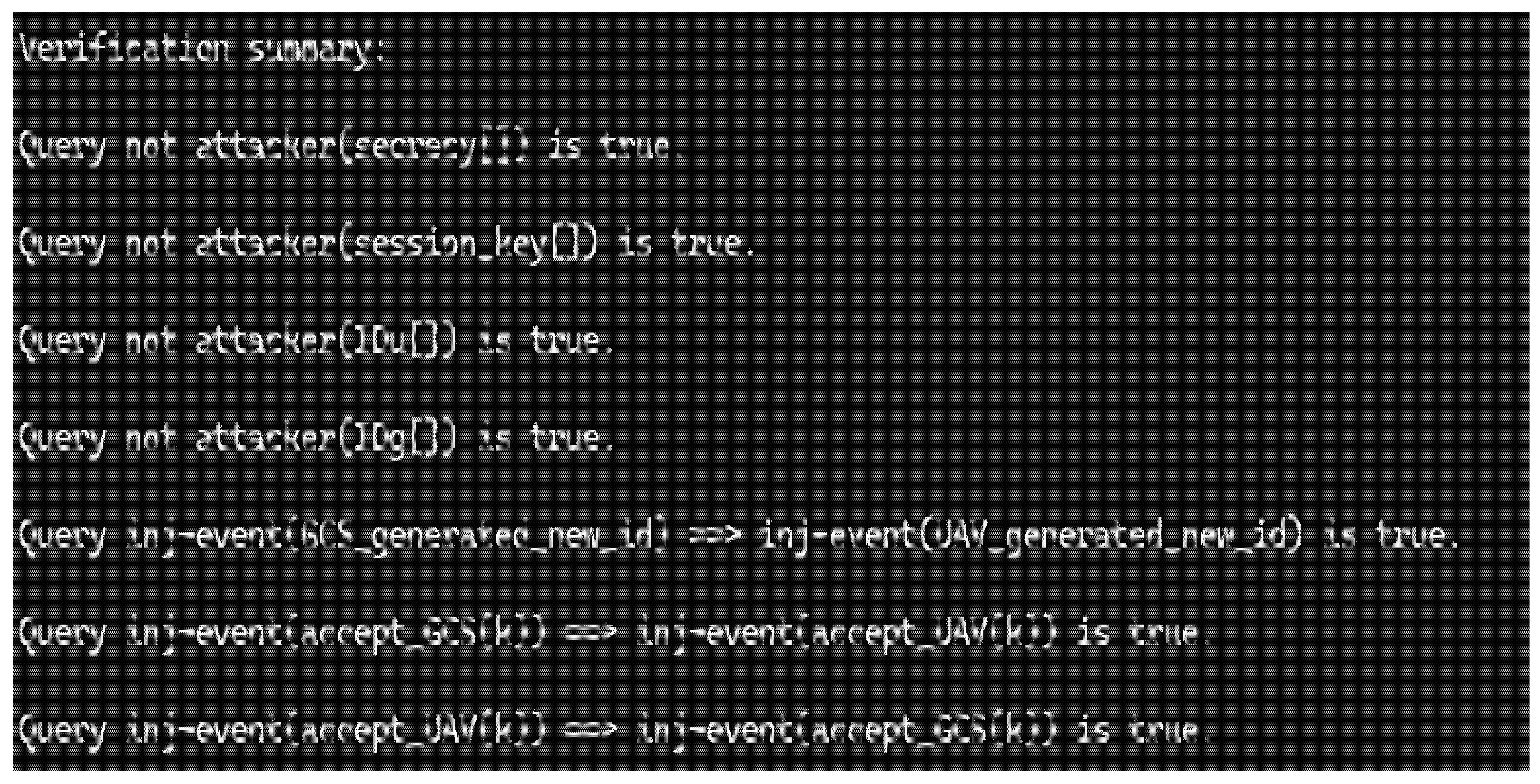
| Symbols | Meaning |
|---|---|
| UAV and GCS identities (i indicates the ID used for the i message) | |
| Shared initial key | |
| Base point of elliptic curve | |
| The scalar multiplication symbol of an elliptic curve. | |
| Temporary private keys for UAV and GCS | |
| Temporary public keys for UAV and GCS | |
| Message authentication code | |
| Hash-based message authentication code | |
| Hash function | |
| XOR operation | |
| Temporary key | |
| Final key | |
| Identity data | |
| Result of the XOR operation between and | |
| Result of the XOR operation between and | |
| Message identification |
| Security Event Definitions |
|---|
| event accept_GCS(key) |
| event accept_UAV(key) |
| event GCS_generated_new_id() |
| event UAV_generated_new_id() |
| Query Statements |
|---|
| query attacker(secrecy) |
| query attacker(session_key) |
| query attacker(IDu) |
| query attacker(IDg) |
| query inj-event(GCS_generated_new_id) ==> inj-event(UAV_generated_new_id) query Sk:key; inj-event(accept_GCS(Sk)) ==> inj-event(accept_UAV(Sk)) query Sk:key; inj-event(accept_UAV(Sk)) ==> inj-event(accept_GCS(Sk)) |
| Security Functions | DIHE | Sdronelig [18] | SP-D2GCS [19] | LAPEC [20] | ACPBS-IoT [21] |
|---|---|---|---|---|---|
| Mutual Authentication | YES | YES | YES | YES | YES |
| Anti-Man-in-the-Middle Attack | YES | YES | YES | YES | YES |
| Dynamic Identity | YES | NO | YES | NO | YES |
| Resist Replay Attacks | YES | YES | YES | YES | YES |
| Data Integrity Protection | YES | YES | YES | YES | YES |
| Forward Safety | YES | YES | YES | YES | YES |
| Light Initialization | YES | NO | NO | YES | NO |
| Calculation Type | Description | Time (ms) |
|---|---|---|
| Elliptic curve point multiplication | 2.431 | |
| Elliptic curve point addition operation | 0.883 | |
| Hash operation (SHA-256) | 0.482 | |
| Hash operation (Blake2b) | 0.420 | |
| XOR operation | 0.275 | |
| Symmetric encryption and decryption | 0.727 | |
| Digital signature generation operation | 1.396 | |
| Signature verification operation | 1.036 | |
| Digital certificate verification | 2.618 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lin, L.; Shangguan, R.; Ge, H.; Liu, Y.; Zhou, Y.; Zhou, Y. Mutual Identity Authentication Based on Dynamic Identity and Hybrid Encryption for UAV–GCS Communications. Drones 2025, 9, 422. https://doi.org/10.3390/drones9060422
Lin L, Shangguan R, Ge H, Liu Y, Zhou Y, Zhou Y. Mutual Identity Authentication Based on Dynamic Identity and Hybrid Encryption for UAV–GCS Communications. Drones. 2025; 9(6):422. https://doi.org/10.3390/drones9060422
Chicago/Turabian StyleLin, Lin, Runzong Shangguan, Hongjuan Ge, Yinchuan Liu, Yuefei Zhou, and Yanbo Zhou. 2025. "Mutual Identity Authentication Based on Dynamic Identity and Hybrid Encryption for UAV–GCS Communications" Drones 9, no. 6: 422. https://doi.org/10.3390/drones9060422
APA StyleLin, L., Shangguan, R., Ge, H., Liu, Y., Zhou, Y., & Zhou, Y. (2025). Mutual Identity Authentication Based on Dynamic Identity and Hybrid Encryption for UAV–GCS Communications. Drones, 9(6), 422. https://doi.org/10.3390/drones9060422






