Abstract
Unmanned aerial vehicles (UAVs) are vulnerable to global positioning system (GPS) spoofing attacks, which can mislead their navigation systems and result in unpredictable catastrophic consequences. To address this issue, we propose a detection method based on stacked ensemble learning that combines convolutional neural network (CNN) and extreme gradient boosting (XGBoost) to detect spoofing signals in the GPS data received by UAVs. First, we applied the synthetic minority oversampling (SMOTE) technique to the dataset to address the issue of class imbalance. Then, we used a CNN model to extract high-level features, combined with the original features as input for the stacked model. The stacked model employs XGBoost as the base learner, which is optimized through five-fold cross-validation, and utilizes logistic regression for the final prediction. Furthermore, we incorporated magnetic field data to enhance the system’s robustness, thereby further improving the accuracy and reliability of GPS spoofing attack detection. Experimental results indicate that the proposed model achieved a high accuracy of 99.79% in detecting GPS spoofing attacks, demonstrating its potential effectiveness in enhancing UAV security.
1. Introduction
As unmanned aerial vehicle (UAV) technology advances rapidly, its applications have continuously expanded to encompass numerous industries, including logistics delivery, agricultural monitoring, disaster relief, and military reconnaissance. The high-precision autonomous operation capabilities of UAVs reduce human intervention while significantly lowering inherent risks in logistics and military operations. This not only eliminates threats to operator safety but also reduces the likelihood of human error. However, despite their excellent performance in executing complex tasks, UAVs remain susceptible to cybersecurity attacks, particularly GPS spoofing attacks. By transmitting forged global positioning system (GPS) signals, attackers can interfere with a UAV’s positioning system, causing it to misjudge its current location, thereby deviating from its intended trajectory and potentially leading to a crash. Such attacks not only threaten the normal UAV operation but may also result in severe economic losses and safety hazards. Therefore, developing effective GPS spoofing detection methods is of critical importance for ensuring the safe operation of UAVs.
GPS spoofing attacks occur when attackers use fake or manipulated GPS signals to replace genuine ones, causing UAVs to deviate from their intended destinations. This type of attack can lead to UAVs being captured or controlled by unauthorized parties. Through GPS spoofing attacks, attackers can manipulate UAVs to deviate from their intended flight paths without detection. A scenario of a UAV GPS spoofing attack is illustrated in Figure 1. Assume a UAV is following a predetermined route toward its target location but at some point is deceived by GPS signals sent by an attacker. As a result, the flight control system generates a false position that deviates from the UAV’s actual location and further computes subsequent false positions, ultimately guiding the UAV to a destination set by the attacker. Due to the GPS spoofing attack, the UAV deviates from its planned route and proceeds along an altered flight path toward a false destination. However, from the perspective of the ground control station (GCS), operators can only observe the UAV flying along a false flight path toward the intended destination [1].
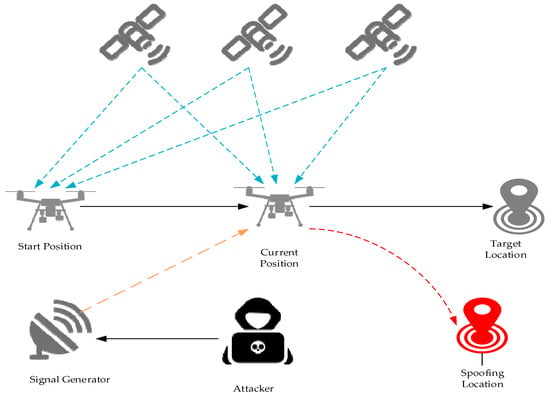
Figure 1.
GPS spoofing attack.
With the rise in UAV spoofing attacks, developing simple and effective solutions for GPS spoofing challenges is crucial. Particularly for civilian UAVs, the GPS signals they use are unencrypted, making them easily accessible and exploitable by anyone. This characteristic exposes civilian UAVs to greater security risks and technical challenges when confronting GPS spoofing attacks, posing unprecedented threats. Therefore, effectively ensuring the security of UAV GPS signals has become a critical problem urgently requiring resolution in the field of UAV security.
In recent years, to tackle the problem of UAV GPS signals being easily subjected to spoofing attacks, numerous researchers have adopted techniques such as energy detection [2], path detection [3], and receiver fingerprinting [4]. Energy detection performs poorly when processing weak and noisy signals and can easily misidentify normal GPS signals as spoofed signals. Multipath detection is limited in effectively handling subtle GPS spoofing and typically requires additional hardware support and precise clock synchronization. The fingerprinting method relies on large datasets for model training, necessitates extensive receiver hardware support, and is also susceptible to environmental changes, which can affect its accuracy.
As technology advances, emerging complex spoofing techniques can circumvent traditional detection methods, necessitating more precise tools and time synchronization to counter such attacks. Due to the weak nature of GPS signals, they can easily confuse existing detection systems, leading to errors in distinguishing between genuine and spoofed signals. Given the critical role of UAVs in security assurance, logistics delivery, and other fields, protecting them from GPS spoofing attacks is of paramount importance. To address these challenges, it is especially urgent to develop reliable detection methods to ensure the safety of UAVs during critical missions. Currently, numerous studies have employed machine learning techniques to classify and detect spoofing attacks on UAVs, achieving significant results that demonstrate advantages in enhancing detection accuracy and defensive capabilities. In this study, we leverage deep learning models and ensemble classifiers, utilizing a dataset of 17 GPS signal features from real-world experiments for model training and testing, thereby enhancing detection accuracy and reliability.
To address the critical challenges faced by UAVs, this paper proposes a novel GPS spoofing detection method based on a CNN-XGBoost model, integrating data augmentation, deep feature extraction, and ensemble-based classification techniques. By employing the extreme gradient boosting (SMOTE) algorithm, the method effectively addresses data imbalance, while convolutional neural network (CNN) extracts key features from complex GPS signals, which are subsequently classified using an extreme gradient boosting (XGBoost) model to achieve superior detection accuracy. To enhance model robustness and generalization in challenging scenarios, dropout and early stopping mechanisms are incorporated to mitigate overfitting. Notably, this study is the first to implement a stacked ensemble architecture combining CNN and XGBoost for UAV GPS spoofing detection. Furthermore, integrating magnetic field data enhances the accuracy and robustness of spoofing detection, providing a comprehensive solution in this field. The contributions of this study are as follows:
- This paper introduces magnetic field data, which are combined with other sensor data (such as accelerometers and gyroscopes) to detect and counter GPS spoofing attacks. By integrating multi-source sensor information, the system’s anti-interference capability and robustness are significantly improved.
- This paper proposes a stacked ensemble model that combines deep learning and machine learning to detect UAV GPS spoofing signals, with an accuracy of 99.79%.
- An advanced data augmentation strategy using SMOTE was introduced to effectively balance the class distribution in the GPS spoofing attack dataset, which significantly enhanced the model’s classification performance and recognition ability. This data augmentation technique not only optimized the overall performance of the classifier but also improved the model’s generalization ability, resulting in greater robustness and accuracy in handling data imbalance issues.
The structure of this paper is as follows: Section 2 reviews related works, highlighting recent advancements in GPS spoofing detection for UAVs. Section 3 outlines the proposed CNN-XGBoost model’s architecture, covering its design and functionality. Section 4 explains the experimental design, covering data preparation, feature selection, evaluation metrics, and result analysis. Section 5 examines the model’s strengths and weaknesses, and potential areas for future research. Section 6 summarizes the main findings and their significance.
2. Related Works
This section introduces the necessary background knowledge and reviews previously proposed solutions for countering GPS spoofing.
2.1. Geomagnetic Field and Magnetometer
The Earth’s magnetic field is created by the movement of metals like iron and nickel in its interior. This magnetic field can be regarded as a giant magnet that encompasses the entire Earth. The Earth’s magnetic field strength at the surface typically ranges from 25 to 65 microteslas, varying by geographical location. These variations are relatively stable globally and are not affected by weather conditions or physical obstructions.
Magnetometers are sensors that measure the strength and direction of magnetic fields. They are composed of three mutually perpendicular magnetoresistive sensors, positioned along the X, Y, and Z axes, which can measure changes in the ambient magnetic field and convert them into electrical signals. Magnetometers are widely used in navigation and positioning systems of devices, including mobile devices, UAVs, and automotive navigation systems. In addition to measuring the Earth’s magnetic field, magnetometers can detect interfering magnetic fields originating from within or outside the device, thereby aiding in precise positioning.
GPS relies on satellite signals to determine the location of a device, but these signals are susceptible to spoofing attacks. Attackers aim to mislead the device by sending fake GPS signals, causing it to miscalculate its actual position. Such attacks represent a significant threat to systems dependent on GPS navigation, including drones and self-driving cars. In [5], GPS spoofing signals in drones are detected using geomagnetic anomalies arising from variations [6,7] in the Earth’s subsurface metal composition and nearby metal structures. A straight flight route was designed, and the study analyzed the different geomagnetic field strengths corresponding to various geographical locations. The experimental results show a strong correlation between the drone’s position and the magnetic field strength. Since the horizontal position of the drone is calculated based on the GPS signal, magnetic field strength offers a viable method for detecting GPS spoofing attacks. Therefore, the geomagnetic field serves as an effective auxiliary tool for detecting GPS spoofing attacks [8,9].
2.2. Relevant Detection Schemes
To provide a comprehensive overview of the latest advancements in UAV GPS spoofing detection, this paper summarizes various innovative methods, highlighting the explorations and achievements of different research teams in this field.
In deep learning-based GPS spoofing detection schemes, numerous studies have proposed various methods, each possessing unique advantages and limitations. The work in [10] proposes a detection method using long short-term memory (LSTM) networks trained on speed, acceleration, and latitude–longitude data to detect spoofing attacks via position prediction errors. Although this method achieves a detection rate of 78% under stable UAV flight conditions, its performance is relatively limited in complex dynamic environments. The work in [11] employs a cellular network-assisted multilayer perceptron (MLP) model to verify the authenticity of GPS signals using path loss data, achieving a detection rate of 93%. However, its reliance on cellular network infrastructure limits its application in areas without network coverage. The work in [12] utilizes deep learning techniques based on direction-of-arrival (DOA) estimation, distinguishing spoofing signals through a CNN classifier, achieving a detection accuracy of 95%. Despite its excellent performance, it requires substantial hardware in terms of multi-element antenna arrays. The work in [13] combines an MLP model with generative adversarial networks (GANs) for data augmentation, enhancing detection performance. However, the computational complexity of GANs may increase the difficulty of practical deployment. The work in [14] proposes the deep learning-based satellite image matching (DeepSIM) method based on satellite image matching. Although this method achieves a ground detection rate of 94.8%, its reliance on cameras and satellite images limits its application in complex environments.
In machine learning-based approaches, the work in [15] introduces the metric-optimized dynamic selector (MOD) and the weighted metric-optimized dynamic selector (WMOD). Their integrated feature selection method optimizes the model’s accuracy, achieving up to 99.6%; however, their complexity may lead to high computational overhead. The work in [16] employs tree models to analyze UAV flight data, demonstrating excellent performance during stable flight but showing reduced sensitivity to dynamic changes. The work in [17] employs a linear regression (LR) model to predict UAVs’ flight trajectories and detect spoofing attacks by comparing discrepancies between predicted latitude and longitude values and GPS data. Although this method demonstrates potential effectiveness, its detection rate was not explicitly evaluated in experiments.
Additionally, there are some specialized detection schemes for GPS spoofing. The work in [18] detects GPS spoofing through geomagnetic anomalies, which is suitable for real-time detection in airborne systems but may be limited by magnetic interference. The work in [19] detects spoofing by analyzing the correlation between video streams and GPS signals, which is effective under specific conditions but requires further evaluation for general applicability. The work in [20] utilizes distributed radar systems for tracking, where data fusion provides high-precision location information; however, it requires substantial radar network infrastructure. The work in [21] employs ultra-wideband ranging to identify spoofing attacks by comparing distances between nodes, though additional hardware support is necessary. The work in [22] introduces a cooperative GPS spoofing detection scheme for flying ad hoc networks, showing excellent performance in multi-node scenarios but with limited applicability in single-node environments.
In the field of malicious drone defense, various mechanisms relevant to GPS spoofing detection have been proposed. The work in [23] presents a learning-based defense mechanism that employs machine learning algorithms to analyze drone flight trajectories and communication patterns, enabling the effective identification of anomalous behaviors and corresponding countermeasures, particularly for detecting complex GPS spoofing in dynamic environments. The work in [24] adopts a game theory model to analyze attack and defense strategies in drone communications. By simulating interactions between attackers and defenders, this model proposes solutions to optimize transmission security, providing theoretical support for attack modeling. Additionally, data transmission security is critical in drone systems. The work in [25] designs a multi-layered data security framework, integrating encryption, access control, and authentication technologies to ensure data integrity and prevent tampering in drone communications, offering valuable insights for GPS spoofing detection methods. Finally, the work in [26] proposes a resource and trajectory optimization approach. By optimizing flight trajectories and communication resources, this approach significantly improves resistance to communication interference and data tampering attacks. It also provides an effective method for detecting GPS spoofing through trajectory anomaly detection, substantially improving detection accuracy and robustness.
In contrast, this paper proposes a stacked ensemble model combining CNN and XGBoost, addressing data imbalance with SMOTE and integrating deep learning’s feature extraction with machine learning’s classification strengths, achieving high detection accuracy in complex environments. This method not only fully utilizes multi-dimensional sensor data, enhancing the model’s robustness, but also introduces early stopping and a learning rate scheduler to prevent overfitting, further improving the model’s generalization ability. Compared with other methods, our method offers advantages in hardware requirements and data applicability, and can provide a stable and efficient GPS spoofing detection solution without the need for external infrastructure support.
3. CNN-XGBoost Stacked Ensemble Model
3.1. CNN
A CNN is a type of artificial neural network specifically designed to process data organized in a grid-like topology. It comprises multiple layers that extract hierarchical features from input data to make predictions. The core components of a CNN include convolutional, pooling, and fully connected layers. The convolutional layer extracts local features through sliding filters (e.g., 32 filters with a kernel size of 3 and stride of 1) and generates a feature map, while the pooling layer (e.g., a max pooling layer with a pooling size of 2) reduces computational complexity by compressing the data, thereby enhancing the model’s robustness. To mitigate overfitting, a dropout layer may be introduced. After multiple convolution and pooling operations, the CNN integrates local features through a fully connected layer (e.g., a fully connected layer containing 64 ReLU-activated neurons) to produce the final prediction. To further improve model performance, the deep features extracted by the CNN can be concatenated with the original features and used as input to a gradient boosting model, such as an XGBoost model with a learning rate of 0.1. This approach enables comprehensive feature utilization and enhances prediction accuracy by combining the feature extraction capabilities of deep learning with the classification advantages of XGBoost.
In this study, we employed the parametric rectified linear unit (PreLU) activation function to process the results of convolution operations. The PReLU activation function is an activation function used in artificial neural networks. It extends the traditional rectified linear unit (ReLU) function by adding a learnable parameter, allowing the function to have a non-zero slope in the negative region. This improvement enables PReLU to better handle the negative portions of the input data. The PReLU function is defined as follows:
where is the input value and is a learnable parameter during training, usually a constant less than 1. The parameter gives it greater flexibility in handling negative inputs. Unlike the traditional ReLU, which outputs 0 when the input is negative, PReLU behaves the same as the standard ReLU when x ≥ 0, directly outputting the input value, but when x < 0, the output of PReLU is . This design allows PReLU to adjust when facing negative inputs, making it more effective than the standard ReLU.
The structure of the CNN is shown in Figure 2. The pooling layers in CNN effectively reduce the spatial dimensions of feature maps by performing downsampling operations. The primary function of pooling layers is to make the representation of feature maps more concise and easier to process. Pooling operations bring two major advantages.
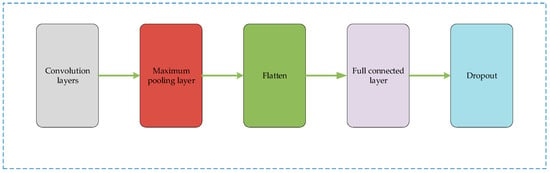
Figure 2.
CNN architecture diagram.
First, they reduce the number of parameters and the computational complexity, enhancing the model’s efficiency; second, by introducing translation invariance, they help alleviate the overfitting problem, meaning that minor changes in the input data do not significantly affect the output. Common pooling methods include max pooling and average pooling. This paper uses max pooling, which reduces data dimensions while enhancing the model’s robustness and stability.
3.2. XGBoost
XGBoost is an optimized implementation of gradient boosting decision trees (GBDT). Unlike traditional GBDT, XGBoost adds a regularization term to the loss function. Moreover, since some loss functions are hard to differentiate, XGBoost approximates them using the second-order Taylor expansion. XGBoost incrementally builds a series of weak learners (usually decision trees), combining each tree’s prediction results with the residuals from previous trees to gradually improve the model’s overall predictive accuracy.
Main advantages of XGBoost:
- Highly efficient and scalable: XGBoost processes large-scale datasets quickly and effectively, with low demands on memory and other hardware resources.
- Implements boosted tree models internally and can automatically handle missing values.
- Simple and easy to use: compared to other machine learning libraries, users can readily employ XGBoost and achieve excellent results.
The principle of GBDT is illustrated in Figure 3. GBDT enhances the model’s predictive performance by progressively building a series of decision trees. First, GBDT starts with the first tree (Tree 1), using its output as the initial predicted value . Then, the second tree (Tree 2) does not directly predict the target value , but fits the residual of the first tree, that is, , obtaining output . Subsequently, each new tree sequentially learns the residuals (errors) from the previous trees, such as , until the last tree (Tree m). The final prediction is the sum of all tree outputs, expressed as . By gradually reducing the prediction error, the GBDT model can approximate the true target values, thereby significantly improving overall predictive accuracy.
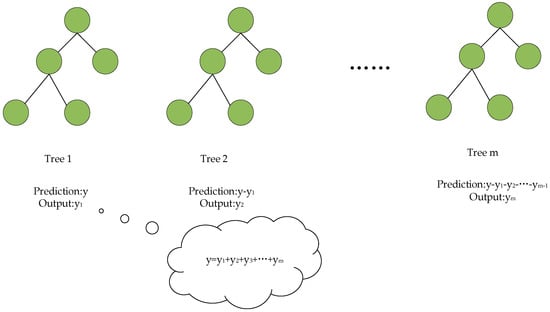
Figure 3.
GBDT architecture diagram.
XGBoost, as illustrated in Figure 4, enhances predictive performance by constructing a sequence of multiple decision trees. First, the process begins with the first tree (Tree 1), generating the initial prediction . Next, the second tree (Tree 2) is trained to fit the residuals of the previous tree (which is the difference between the current prediction and the actual value), producing . This process continues iteratively, with each subsequent tree further reducing the residual errors based on the previous tree, until the final tree (Tree K) is constructed. The final prediction is the sum of the predictions from all trees, expressed as . This cumulative approach allows the model to gradually reduce errors, significantly improving predictive accuracy. Compared to traditional gradient boosting methods, XGBoost introduces regularization to control model complexity and prevent overfitting, while employing efficient parallel computing and tree structure optimization algorithms to improve training speed and performance.
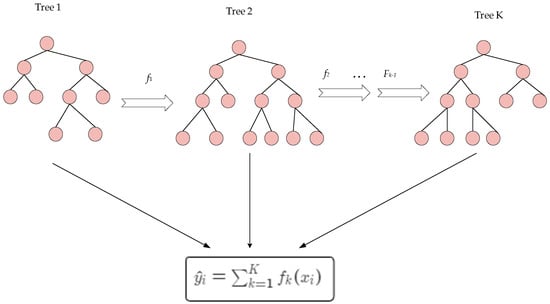
Figure 4.
XGBoost architecture diagram.
3.3. CNN-XGBoost Model Architecture
CNN-XGBoost is a hybrid model that combines CNN and the XGBoost algorithm. It leverages the feature extraction capabilities of CNN and the powerful classification abilities of XGBoost to enhance data modeling and prediction performance. The model structure is shown in Figure 5.
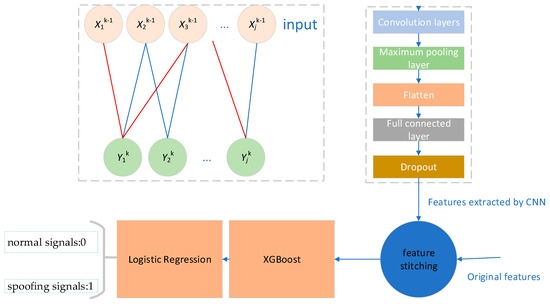
Figure 5.
CNN-XGBoost model architecture diagram.
CNN-XGBoost enhances the model’s predictive performance by combining the feature extraction capabilities of CNN with the powerful classification abilities of XGBoost. Specifically, the model first uses CNN to extract features from the data, then combines these extracted features with the original features as input to XGBoost, and finally makes the prediction through a stacking classifier.
Advantages of the CNN-XGBoost Model:
- Strong feature extraction capability: CNN can automatically learn high-level and abstract features from data, excelling at capturing complex patterns and feature structures.
- Outstanding classification performance: As an improved decision tree algorithm, XGBoost possesses strong nonlinear modeling capabilities and good robustness, effectively handling various complex classification tasks.
- Handling data imbalance issues: SMOTE technology can be used to balance the dataset, making the model more adaptable to imbalanced data distributions and improving the classifier’s overall performance.
- Enhancing generalization ability: By integrating predictions from multiple models (e.g., stacking models), it enhances the model’s predictive power and robustness, effectively improving its generalization performance on unseen data.
- Preventing overfitting: Employs regularization methods (such as Dropout) and optimization strategies (such as early stopping and reduced learning rate on plateau) to prevent overfitting during training, ensuring the model’s stability and generalization ability.
4. Simulation Experiments
This paper validates the proposed UAV GPS spoofing detection method through detailed experiments and evaluation. Firstly, the experimental setup is introduced, including data selection and the configuration of experimental parameters. Subsequently, the experimental results are analyzed and discussed. The results indicate that the proposed method has significant advantages in detecting UAV GPS spoofing attacks.
4.1. Experimental Setup
4.1.1. Data Selection
In this study, the dataset [27] was constructed using flight logs from drones functioning under normal and GPS spoofing attack scenarios. The data include normal signals encoded as “0” and spoofing signals encoded as “1”. The GPS spoofing attack was simulated using a HackRF software-defined radio (SDR) device. This device employs the GPS-SDR-SIM tool (Global Positioning System Software-Defined Radio Simulator) to generate high-fidelity GPS signals, which are delayed and then forwarded to the human–machine interface. This process deceives the GPS receiver, leading to a miscalculation of the drone’s operational parameters, thereby inducing a GPS spoofing attack. The dataset was collected using a Holybro S500 drone featuring a Pixhawk GPS receiver and a Pixhawk 4 flight controller (PX4 firmware version v1.11.3).
After obtaining the dataset required for the simulation experiments, we selected appropriate features for GPS spoofing attack detection. Our main goal is to accurately detect UAV GPS spoofing attacks, and the selection of features should be based on the specific impacts of these attacks on the UAV. The feature selection process should follow two key principles: applicability and effectiveness. The features we finally selected are shown in Table 1, and the dataset has 17 feature dimensions.

Table 1.
Feature names and meanings.
4.1.2. Data Preprocessing
To eliminate the impact caused by differences in feature scales and to prevent features with different scales from slowing down the convergence speed during model training, we standardized the data. The standardization steps are as follows.
Calculating the mean and standard deviation of the features: For each feature, calculate its mean and standard deviation. The calculations are as follows:
where is the number of samples, and a feature column in dataset X has a mean and a standard deviation , which are calculated as follows.
Zero-centering of feature values: For each feature in the dataset, subtract the mean of that feature from all its data points to make the new mean of the feature zero.
Standard deviation normalization: Subtract the mean from each feature value and divide by its standard deviation, scaling the feature to have a standard deviation of 1. The calculation formula is
where represents the value of the j-th sample for the i-th feature, denotes the mean value, and represents the standard deviation
The dataset was split into a 70% training set and a 30% test set to train the model and assess its generalization performance.
4.1.3. Data Augmentation
Due to the imbalance in the amount of normal data and spoofed data, data augmentation is needed to address the data imbalance issue. There are various technical methods to handle data imbalance, such as random oversampling, SMOTE [28], Borderline-SMOTE [29], ADASYN (adaptive synthetic sampling) [30], SVM-SMOTE (support vector machines SMOTE) [31], and GANs (generative adversarial networks). In this study, we use the SMOTE method for the data augmentation of the UAV dataset.
SMOTE is a commonly used data augmentation method specifically designed to address class imbalance problems. Unlike simply replicating minority class samples, SMOTE generates synthetic samples in the feature space to increase minority class samples. This method effectively prevents the model from overfitting minority class data and enhances the classifier’s ability to recognize the minority class. Its core idea is to balance class distribution by generating synthetic samples between minority class instances. SMOTE selects a minority class sample and generates new samples through linear interpolation with its k-nearest minority neighbors in the feature space, increasing diversity in the minority class and improving the model’s classification performance. This method provides an effective means to solve class imbalance problems. Advantages of the SMOTE algorithm are as follows:
Increases the diversity of minority class samples, which helps improve the model’s generalization ability.
By increasing the number of minority class samples, it enhances the classifier’s ability to recognize the minority class and reduces the negative impact of class imbalance on model performance. The formula for computing synthetic samples in SMOTE is
Let denote the newly generated synthetic sample, where represents the current minority class sample. The sample is randomly selected from the nearest neighbors of . The variable λ is a random number between 0 and 1, usually drawn from a uniform distribution.
4.2. Evaluation Criteria
To evaluate the proposed method’s detection performance, the experiments used accuracy (Acc), precision (Prec), and recall (Rec) as metrics for GPS spoofing detection. The confusion matrix is shown in Table 2.

Table 2.
Confusion matrix.
In GPS spoofing detection, true positive (TP) denotes the instances where both the actual and predicted labels are positive, indicating the correct identification of a positive condition. False negative (FN) refers to the cases where the true label is positive but the prediction is negative, resulting in a failure to detect the positive condition. False positive (FP) occurs when the true label is negative, but the model incorrectly predicts a positive outcome, thus generating an erroneous positive result. Finally, true negative (TN) signifies the cases where both the true and predicted labels are negative, reflecting correct identification of the absence of the condition. Accuracy measures the proportion of correct predictions, calculated as the sum of TP and TN divided by the total number of detections. Precision indicates the proportion of actual spoofing attacks among all cases predicted as spoofing attacks and inversely correlates with the false positive rate. Higher precision reflects a lower false positive rate. Recall measures the proportion of actual GPS spoofing attacks detected, indicating the model’s coverage in identifying spoofing.
4.3. Five-Fold Cross-Validation
In order to minimize random factors and incidental variations in the experiment, we employed a five-fold cross-validation method to train and evaluate the performance of the spoofing detection model.
As shown in Figure 6, we performed stratified sampling on the data-augmented GPS signal dataset, dividing it into five non-overlapping subsets. In each iteration, one subset was used as the test set, while the others served as the training set. This process was repeated five times, with each subset serving as the test set once. The model was trained and evaluated in each iteration, yielding five evaluation results (E1, E2, E3, E4, E5). Finally, we obtained the overall performance evaluation of the model by calculating the average of these five results (E = (E1 + E2 + E3 + E4 + E5)/5). This approach allows for a more robust evaluation of the model’s performance, reducing the bias that may result from a single data split.
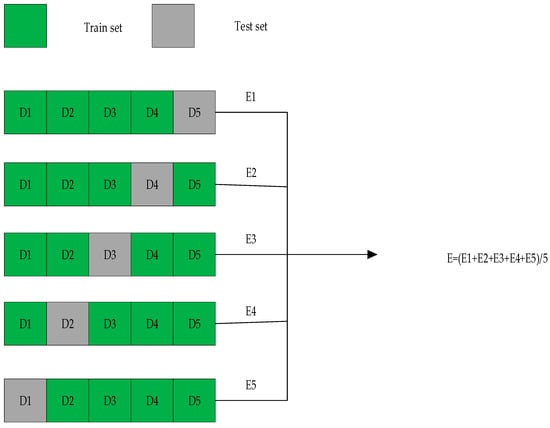
Figure 6.
Five-fold cross-validation architecture.
4.4. Experimental Results and Analysis
To evaluate the performance of various models in UAV GPS spoofing detection, we conducted comparative experiments by applying multiple classification algorithms on the same dataset. The evaluated models included decision tree (DT), GBDT, linear SVM (SVM-linear), radial basis function SVM (SVM-rbf), k-nearest neighbors (KNN), MLP, XGBoost, and the CNN-XGBoost model proposed in this paper. We used standard classification metrics—accuracy, precision, and recall—to evaluate each model’s performance. The results are shown in Table 3, illustrating the performance of different models on these three metrics. Notably, the CNN-XGBoost model achieved the best performance in the UAV GPS spoofing detection task. Specifically, the CNN-XGBoost model achieved an accuracy of 99.38%, a precision of 99.33%, and a recall of 98.67%, which indicates that the model possesses exceptionally high effectiveness and reliability in recognizing and detecting malicious GPS signals.

Table 3.
Experimental results of classification models.
By comparison, traditional machine learning models such as DT and GBDT also demonstrated high performance, achieving accuracies of 97.51% and 97.24%, precisions of 95.39% and 97.31%, and recalls of 96.67% and 96.84%, respectively. However, these traditional models are still inferior in overall performance to the CNN-XGBoost model. SVM-linear and SVM-rbf exhibited relatively weaker performance in this task, with accuracies of 74.90% and 80.42%, respectively. Furthermore, the performance of the MLP and KNN models was not as advantageous as that of the CNN-XGBoost model. Specifically, the accuracy of the CNN-XGBoost-LR model exceeded those of the SVM-linear, SVM-rbf, and KNN models by 24.48%, 18.96%, and 19.92%, respectively. This advantage is mainly attributed to the CNN’s ability to extract deep features from the data, while XGBoost excels at handling feature importance ranking and aggregation. By integrating the strengths of these two models, the CNN-XGBoost model effectively reduces both the miss rate and the false positive rate, thereby enhancing the overall efficiency of GPS spoofing detection. Compared to other models, the CNN-XGBoost model exhibits superior performance in accuracy, stability, and detection effectiveness, demonstrating its strong applicability and robustness in complex scenarios.
The experimental evaluation of advanced methods for UAV GPS spoofing detection highlights the superior performance of the proposed CNN-XGBoost model. Table 4 provides an overview of the accuracy metrics achieved by cutting-edge approaches, including TimeGAN-LSTM, LSTM-KF, PCA-CNN-LSTM, and CNN-XGBoost, showcasing the advantages of the proposed solution in detection accuracy.

Table 4.
Accuracy comparison of advanced methods.
The TimeGAN-LSTM model [32], combining a Time-series Generative Adversarial Network (TimeGAN) for synthetic data creation with LSTM networks for sequential data processing, achieved an accuracy of 98.08%, demonstrating its proficiency in managing imbalanced datasets and time-series data. The LSTM-KF model [33], which integrates Kalman Filters (KF) for probabilistic estimation with LSTM networks, slightly outperformed it with an accuracy of 98.30%, offering enhanced reliability for real-time UAV operations. The PCA-CNN-LSTM model [34], which applies Principal Component Analysis (PCA) for dimensionality reduction and uses CNN and LSTM for feature extraction and sequence modeling, achieved a commendable accuracy of 99.49%, emphasizing the value of hybrid architectures and feature refinement.
By comparison, the proposed CNN-XGBoost model demonstrated exceptional performance, achieving an accuracy of 99.79%, outperforming all other evaluated models. This improvement is driven by its novel design, which combines CNN for in-depth feature extraction with XGBoost for efficient classification. The use of an ensemble approach enhances detection precision while addressing overfitting through regularization techniques and effectively resolving data imbalance with SMOTE augmentation. Moreover, the inclusion of multi-source sensor data, such as magnetic field information, further strengthens the model’s robustness and accuracy. This comparative analysis reaffirms the superiority of the CNN-XGBoost model in UAV GPS spoofing detection, establishing it as a highly effective and reliable approach for addressing this critical security challenge.
5. Discussion
The proposed CNN-XGBoost model exhibited robust performance in detecting GPS spoofing attacks on UAVs. However, recognizing its limitations is essential for offering a balanced perspective and informing future research priorities. This study is constrained by its reliance on a single dataset for experimental validation, which might limit the model’s applicability in real-world scenarios. Such reliance may fail to represent the diversity of GPS spoofing attacks across various environments. While SMOTE effectively addresses the class imbalance problem, its dependence on synthetic data could result in deviations from the true data distribution. Furthermore, the model’s reliance on GPS and geomagnetic data could constrain its effectiveness under significant signal interference.
Future research should incorporate datasets from diverse sources, including publicly available and real-world collections, to enhance the model’s applicability and robustness. It should also explore the combination of SMOTE with GANs and introduce authentic spoofing signals to significantly enhance the model’s robustness and versatility. Additionally, integrating data sources such as inertial measurement units (IMUs), visual odometers, and radar systems could further enhance the model’s adaptability to challenging environments.
6. Conclusions
In UAV GPS spoofing detection, the stacked ensemble method combining CNN and XGBoost models has demonstrated significant potential. This method fully leverages the powerful feature extraction capabilities of CNN and the efficient classification performance of XGBoost, exhibiting excellent performance in terms of detection accuracy, recall, and other metrics. By employing the SMOTE technique for data augmentation to balance the class distribution between spoofed and normal data, the overall performance of the model was improved.
In the design of the method in this paper, besides data normalization and SMOTE augmentation, magnetic field data were also incorporated and combined with sensor data such as accelerometers and gyroscopes, thereby further enriching the input feature space and providing additional dimensional information for spoofing detection. In the feature extraction phase, CNN automatically extracts deep features from complex patterns, followed by efficient classification of these features by XGBoost. Finally, logistic regression is employed as a meta-classifier to fuse the outputs of multiple classifiers, thereby enhancing the model’s generalization ability and robustness. Experimental results indicate that this stacked ensemble method achieves significantly higher detection accuracy than individual models when handling high-dimensional complex data. Integrating magnetic field data improved detection performance, highlighting the value of multi-source data fusion in complex detection tasks. Compared to other methods in the literature, the approach proposed in this study not only exhibits superior detection performance but also demonstrates broad application prospects in UAV GPS spoofing detection. Future research directions may include incorporating more types of base classifiers, multi-task learning, or deep ensemble learning techniques to further optimize model performance, while also exploring its generalizability and stability across different types of UAV datasets.
Author Contributions
Conceptualization, X.Z.; Methodology, X.Z.; Software, Z.M.; Validation, X.Z.; Formal Analysis, Z.M.; Investigation, T.M.; Resources, T.M.; Data Curation, X.Z.; Writing—Original Draft Preparation, X.Z.; Writing—Review and Editing, T.M.; Visualization, X.Z.; Supervision, T.M.; Project Administration, T.M.; Funding Acquisition, T.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China (60472127) for the study on quantitative evaluation models and simulation research of civil aviation flight safety, the Key R&D Project of Sichuan Provincial Science and Technology Department (2022YFJ0213) for the development and application of an auxiliary decision-making system for general aviation safety operations, and the Civil Aviation Administration of China (ASSA2022/17) for the technical research and evaluation of equivalent safety management mechanisms for general aviation operating units in compliance with regulations.
Data Availability Statement
The data are available at [27].
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Wei, X.; Sun, C.; Lyu, M.; Song, Q.; Li, Y. ConstDet: Control Semantics-Based Detection for GPS Spoofing Attacks on UAVs. Remote Sens. 2022, 14, 5587. [Google Scholar] [CrossRef]
- Zhang, B.; Teunissen, P.J.G.; Yuan, Y.; Zhang, H.; Li, M. Joint Estimation of Vertical Total Electron Content (VTEC) and Satellite Differential Code Biases (SDCBs) Using Low-Cost Receivers. J. Geod. 2018, 92, 401–413. [Google Scholar] [CrossRef]
- Nasser, A.; Hassan, H.A.H.; Chaaya, J.A.; Mansour, A.; Yao, K.-C. Spectrum Sensing for Cognitive Radio: Recent Advances and Future Challenges. Sensors 2021, 21, 2408. [Google Scholar] [CrossRef] [PubMed]
- Mohanti, S.; Soltani, N.; Sankhe, K.; Jaisinghani, D.; Chowdhury, K. AirID: Injecting a Custom RF Fingerprint for Enhanced UAV Identification Using Deep Learning. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020. [Google Scholar]
- Whelan, J.; Sangarapillai, T.; Minawi, O.; Almehmadi, A.; El-Khatib, K. Novelty-Based Intrusion Detection of Sensor Attacks on Unmanned Aerial Vehicles. In Proceedings of the MSWiM’20: 23rd International ACM Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Alicante, Spain, 16–20 November 2020. [Google Scholar]
- Heirtzler, J.R.; Dickson, G.O.; Herron, E.M.; Pitman, W.C.; Le Pichon, X. Marine Magnetic Anomalies, Geomagnetic Field Reversals, and Motions of the Ocean Floor and Continents. J. Geophys. Res. 1968, 73, 2119–2136. [Google Scholar] [CrossRef]
- Canciani, A.; Raquet, J. Absolute Positioning Using the Earth’s Magnetic Anomaly Field: Magnetic Anomaly Navigation. J. Inst. Navig. 2016, 63, 111–126. [Google Scholar] [CrossRef]
- Pasku, V.; De Angelis, A.; De Angelis, G.; Arumugam, D.D.; Dionigi, M.; Carbone, P.; Moschitta, A.; Ricketts, D.S. Magnetic Field-Based Positioning Systems. IEEE Commun. Surv. Tutor. 2017, 19, 2003–2017. [Google Scholar] [CrossRef]
- Brzozowski, B.; Kazmierczak, K. Magnetic Field Mapping as a Support for UAV Indoor Navigation System. In Proceedings of the 2017 IEEE International Workshop on Metrology for AeroSpace (MetroAeroSpace), Padua, Italy, 21–23 June 2017; pp. 583–588. [Google Scholar]
- Wang, S.; Wang, J.; Su, C.; Ma, X. Intelligent Detection Algorithm Against UAVs’ GPS Spoofing Attack. In Proceedings of the 2020 IEEE 26th International Conference on Parallel and Distributed Systems (ICPADS), Hong Kong, 2–4 December 2020; pp. 382–389. [Google Scholar] [CrossRef]
- Dang, Y.; Benzaid, C.; Yang, B.; Taleb, T. Deep Learning for GPS Spoofing Detection in Cellular Enabled Unmanned Aerial Vehicle Systems. arXiv 2022, arXiv:2201.00568. [Google Scholar] [CrossRef]
- Jayaweera, M. A Novel Deep Learning GPS Anti-Spoofing System with DOA Time-Series Estimation. In Proceedings of the 2021 IEEE Global Communications Conference (GLOBECOM), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar]
- Kim, K.; Nalluri, S.; Kashinath, A.; Wang, Y.; Li, B. Security Analysis against Spoofing Attacks for Distributed UAVs. In Proceedings of the Workshop on Decentralized IoT Systems and Security, San Diego, CA, USA, 23–26 February 2020. [Google Scholar]
- Xue, N.; Niu, L.; Hong, X.; Li, Z.; Poepper, C. DeepSIM: GPS Spoofing Detection on UAVs Using Satellite Imagery Matching. In Proceedings of the Annual Computer Security Applications Conference 2020, Online, 7–11 December 2020. [Google Scholar]
- Talaei Khoei, T.; Ismail, S.; Kaabouch, N. Dynamic Selection Techniques for Detecting GPS Spoofing Attacks on UAVs. Sensors 2022, 22, 622. [Google Scholar] [CrossRef] [PubMed]
- Aissou, G.; Slimane, H.O.; Benouadah, S.; Kaabouch, N. Tree-Based Supervised Machine Learning Models For Detecting GPS Spoofing Attacks on UAS. In Proceedings of the 2021 IEEE 12th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 1–4 December 2021; pp. 0649–0653. [Google Scholar]
- Meng, L.; Yang, L.; Ren, S.; Tang, G.; Zhang, L.; Yang, F.; Yang, W. An Approach of Linear Regression-Based UAV GPS Spoofing Detection. Wirel. Commun. Mob. Comput. 2021, 2021, 5517500. [Google Scholar] [CrossRef]
- Wei, X.; Li, X.; Sun, C.; Zhang, H.; Ma, J. Mag Det: UAV GPS Spoofing Detection Based on the Geomagnetic Field. Chin. J. Comput. 2024, 47, 877–891. [Google Scholar]
- Davidovich, B.; Nassi, B.; Elovici, Y. Towards the Detection of GPS Spoofing Attacks Against Drones by Analyzing Camera’s Video Stream. Sensors 2022, 22, 2608. [Google Scholar] [CrossRef] [PubMed]
- Pardhasaradhi, B.; Cenkeramaddi, L.R. GPS Spoofing Detection and Mitigation for Drones Using Distributed Radar Tracking and Fusion. IEEE Sens. J. 2022, 22, 11122–11134. [Google Scholar] [CrossRef]
- Mykytyn, P.; Brzozowski, M.; Dyka, Z.; Langendoerfer, P. GPS-Spoofing Attack Detection Mechanism for UAV Swarms. arXiv 2023, arXiv:2301.12766. [Google Scholar] [CrossRef]
- Bada, M.; Boubiche, D.E.; Lagraa, N.; Kerrache, C.A.; Imran, M.; Shoaib, M. A Policy-Based Solution for the Detection of Colluding GPS-Spoofing Attacks in FANETs. Transp. Res. Part A Policy Pract. 2021, 149, 300–318. [Google Scholar] [CrossRef]
- Min, M.; Xiao, L.; Xu, D.; Huang, L.; Peng, M. Learning-Based Defense against Malicious Unmanned Aerial Vehicles. In Proceedings of the 2018 IEEE 87th Vehicular Technology Conference (VTC Spring), Porto, Portugal, 3–6 June 2018. [Google Scholar]
- Xiao, L.; Xie, C.; Min, M.; Zhuang, W. User-Centric View of Unmanned Aerial Vehicle Transmission Against Smart Attacks. IEEE Trans. Veh. Technol. 2017, 67, 3420–3430. [Google Scholar] [CrossRef]
- Yang, D.; Zhao, Y.; Yi, Z.; Yang, D.; He, S. A Design Scheme of Data Security for Unmanned Aerial Vehicles. In Proceedings of the Advanced Hybrid Information Processing, Changsha, China, 29–30 September 2022. [Google Scholar] [CrossRef]
- Lu, W.; Ding, Y.; Gao, Y.; Hu, S.; Gong, Y. Resource and Trajectory Optimization for Secure Communications in Dual-UAV-MEC Systems. IEEE Trans. Ind. Inform. 2021, 18, 2704–2713. [Google Scholar] [CrossRef]
- IEEE DataPort. UAV Attack Dataset. Available online: https://ieee-dataport.org/open-access/uav-attack-dataset (accessed on 13 December 2024).
- Napierala, K.; Stefanowski, J. Types of Minority Class Examples and Their Influence on Learning Classifiers from Imbalanced Data. J. Intell. Inf. Syst. 2015, 46, 563–597. [Google Scholar] [CrossRef]
- Kovács, G. An Empirical Comparison and Evaluation of Minority Oversampling Techniques on a Large Number of Imbalanced Datasets. Appl. Soft Comput. 2019, 83, 105662. [Google Scholar] [CrossRef]
- He, H.; Bai, Y.; Garcia, E.A.; Li, S. ADASYN: Adaptive Synthetic Sampling Approach for Imbalanced Learning. In Proceedings of the 2008 IEEE International Joint Conference on Neural Networks (IEEE World Congress on Computational Intelligence), Hong Kong, China, 1–8 June 2008. [Google Scholar] [CrossRef]
- Kang, Q.; Shi, L.; Zhou, M.; Wang, X.; Wu, Q.; Wei, Z. A Distance-Based Weighted Undersampling Scheme for Support Vector Machines and Its Application to Imbalanced Classification. IEEE Trans. Neural Netw. Learn. Syst. 2018, 29, 4152–4165. [Google Scholar] [CrossRef] [PubMed]
- Wang, L.; Sun, Y.; Yu, M.; Li, T.; Dong, M. UAV GPS spoofing detection model based on TimeGAN-LSTM. J. Electron. Meas. Instrum. 2023, 37, 122–135. [Google Scholar] [CrossRef]
- Sun, Y.; Cao, C.; Lai, J.; Yu, T. AntiGPS spoofing method for UAV based on LSTM-KF model. Chin. J. Netw. Inf. Secur. 2022, 6, 80–88. [Google Scholar]
- Sun, Y.; Yu, M.; Wang, L.; Li, T.; Dong, M. A Deep-Learning-Based GPS Signal Spoofing Detection Method for Small UAVs. Drones 2023, 7, 370. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).