Improving Transmission in Integrated Unmanned Aerial Vehicle–Intelligent Connected Vehicle Networks with Selfish Nodes Using Opportunistic Approaches
Abstract
1. Introduction
1.1. Background and Motivations
1.2. Related Works
- First, the authors in [20,21,22,23] have explored the application of opportunistic transmission in VDTNs. However, these studies primarily focused on leveraging the mobility of ICVs or temporary caching at roadside RSUs to facilitate data distribution. While these studies effectively improve the transmission performance of vehicular communications, they ignore the potential benefits of integrating UAVs into VDTNs. Therefore, additional research is essential to investigate the integration of UAVs in opportunistic transmission strategies and to assess their effects on delivery ratios and latency.
- Second, although the authors in [24,25,26,27,28] have investigated the deployment of relaying UAVs in vehicular networks, these works have primarily focused on end-to-end delay-sensitive transmissions and optimized network resources (such as spectrum, power, and trajectory) to enhance network performance. However, they did not address the transmission problem in scenarios where direct communication links are not available within vehicular networks.
- Finally, most of the aforementioned studies assumed that all communication nodes in vehicular networks are cooperative. The existence of selfish nodes that can negatively affect transmission performance was not taken into account. It is noted that, in vehicular networks characterized by social attributes, selfish nodes may exhibit non-cooperative behavior by refusing to forward data or by consuming excessive resources, resulting in lower overall efficiency.
1.3. Contributions
- First, this paper investigates the application of opportunistic transmission in integrated UAV–ICV networks, where the “store-carry-forward” mechanisms are adopted. Then, considering the selfish behavior of communication nodes due to factors such as energy, cache, and other practical constraints, this paper defines the types of node cooperation and analyzes the probability of encounters between nodes.
- Second, an opportunistic transmission scheme for integrated UAV–ICV networks, enabled by node cooperation, is proposed. By evaluating the forwarding capabilities of each relay node, this paper initially floods the information to be transmitted. On this basis, this paper uses UAVs to assist with delivery.
- Finally, to demonstrate the advantages of the designed scheme, this paper compares it with the state-of-the-art schemes [21,22,23] via simulations. Real map data are used for the simulations. The simulation results indicate that the designed scheme outperforms the state-of-the-art schemes in terms of the delivery ratio and average delivery delay. Furthermore, the effect of the proportion of selfish nodes and the cooperation threshold on the performance of integrated UAV–ICV networks is fully discussed.
1.4. Organization
2. System Model
2.1. Opportunistic Transmission Model with Selfish Nodes
2.2. Encounter Probability Analysis Model
3. Opportunistic Transmission Scheme for Integrated UAV–ICV Networks Enabled by Node Cooperation
3.1. Information Flooding
- Case 1: When the next-hop node is a type II communication node, the transfer probability of the communication node is compared with the cooperation threshold of the type II communication node. If , the message copy is transmitted. If , the message copy is not transmitted.
- Case 2: When the next-hop node is a type III communication node, the message copy type is first evaluated, with defined as the message type. If , it indicates that the message copy is related to the relay node, and the message copy is transmitted. If , it indicates that the message is not related to the relay node, and the cooperation threshold must be compared. If , the message copy is transmitted. If , the message copy is not transmitted.
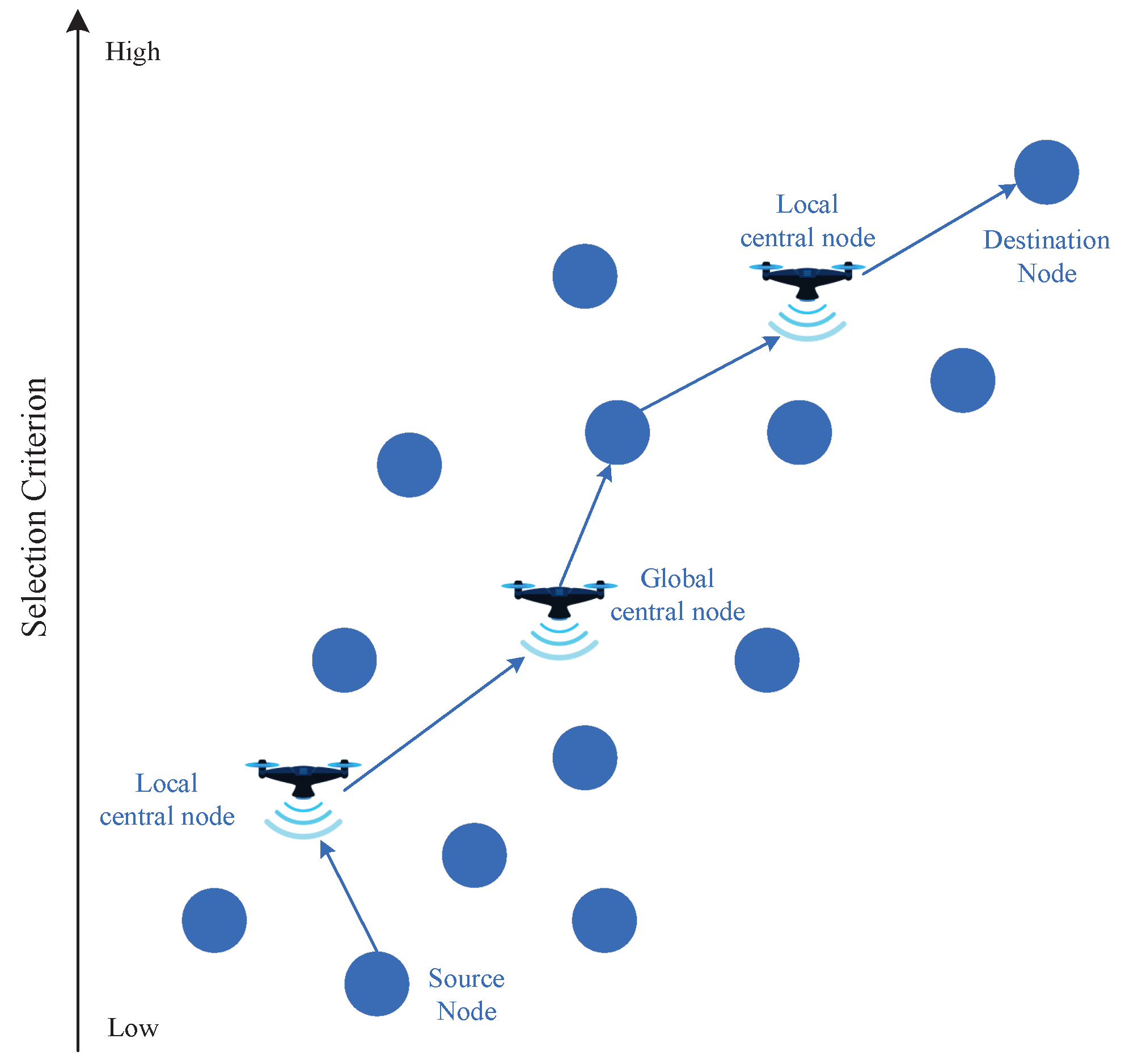
3.2. UAV-Assisted Information Transmission
4. Performance Evaluation
4.1. Simulation Parameters
4.2. Simulation Results
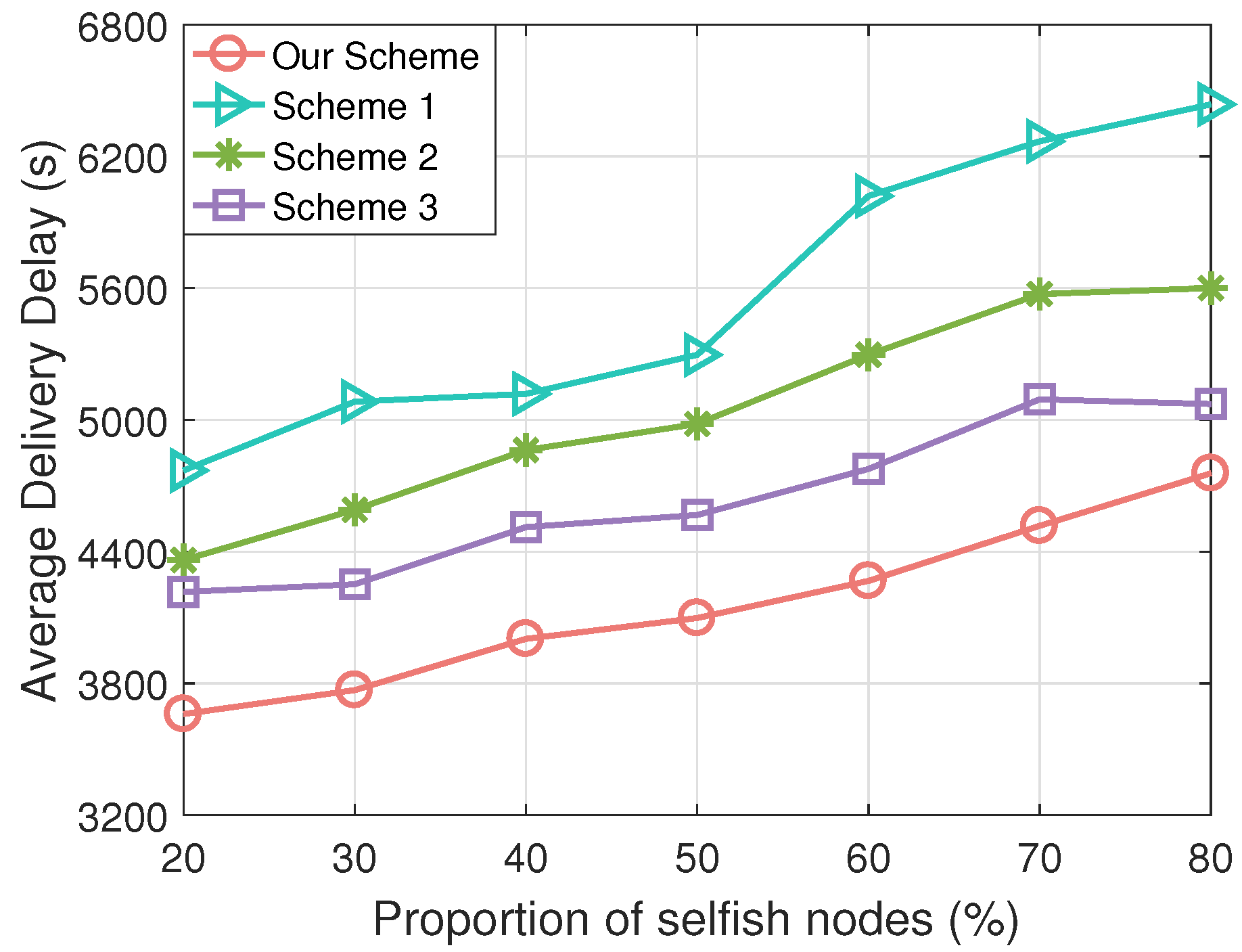
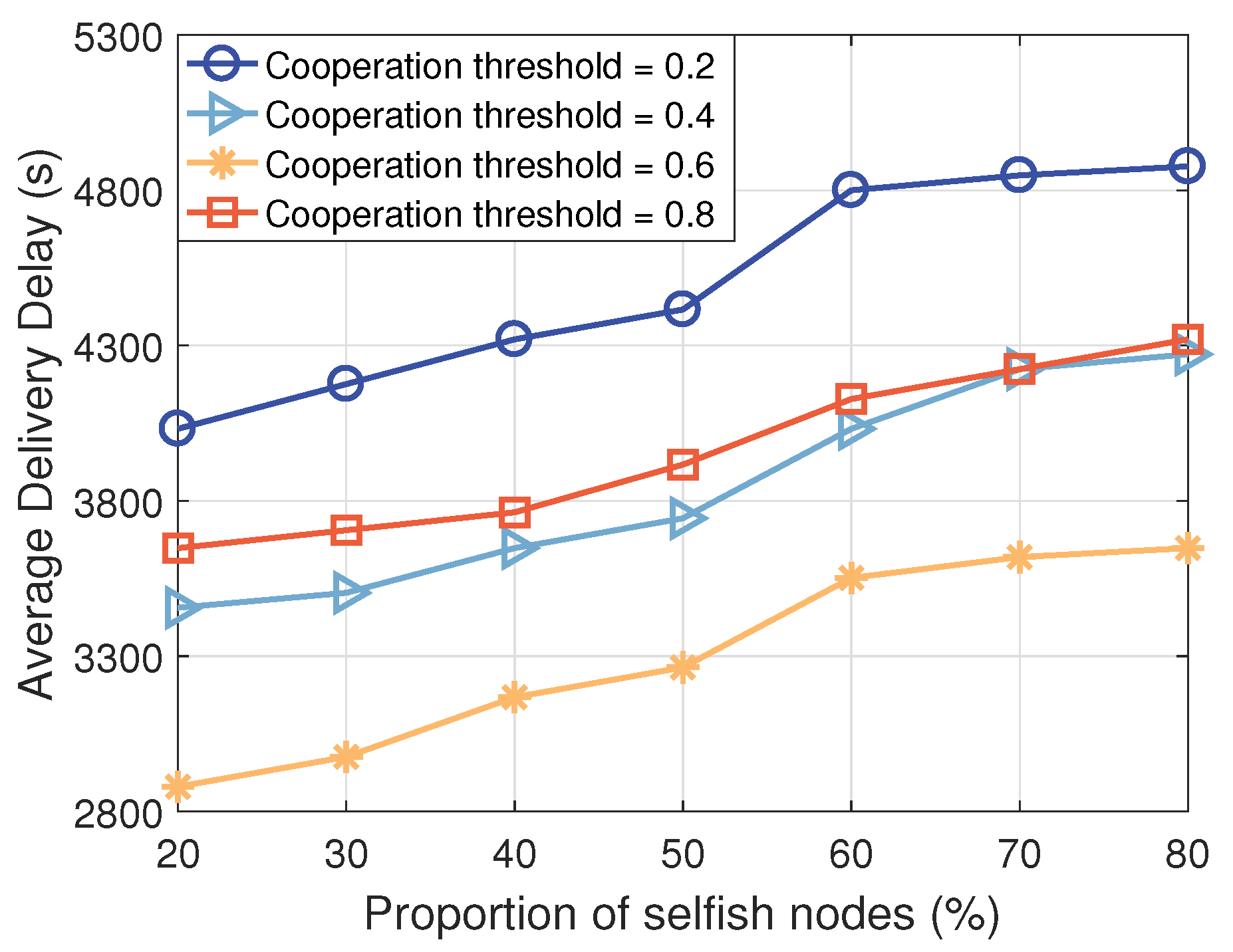
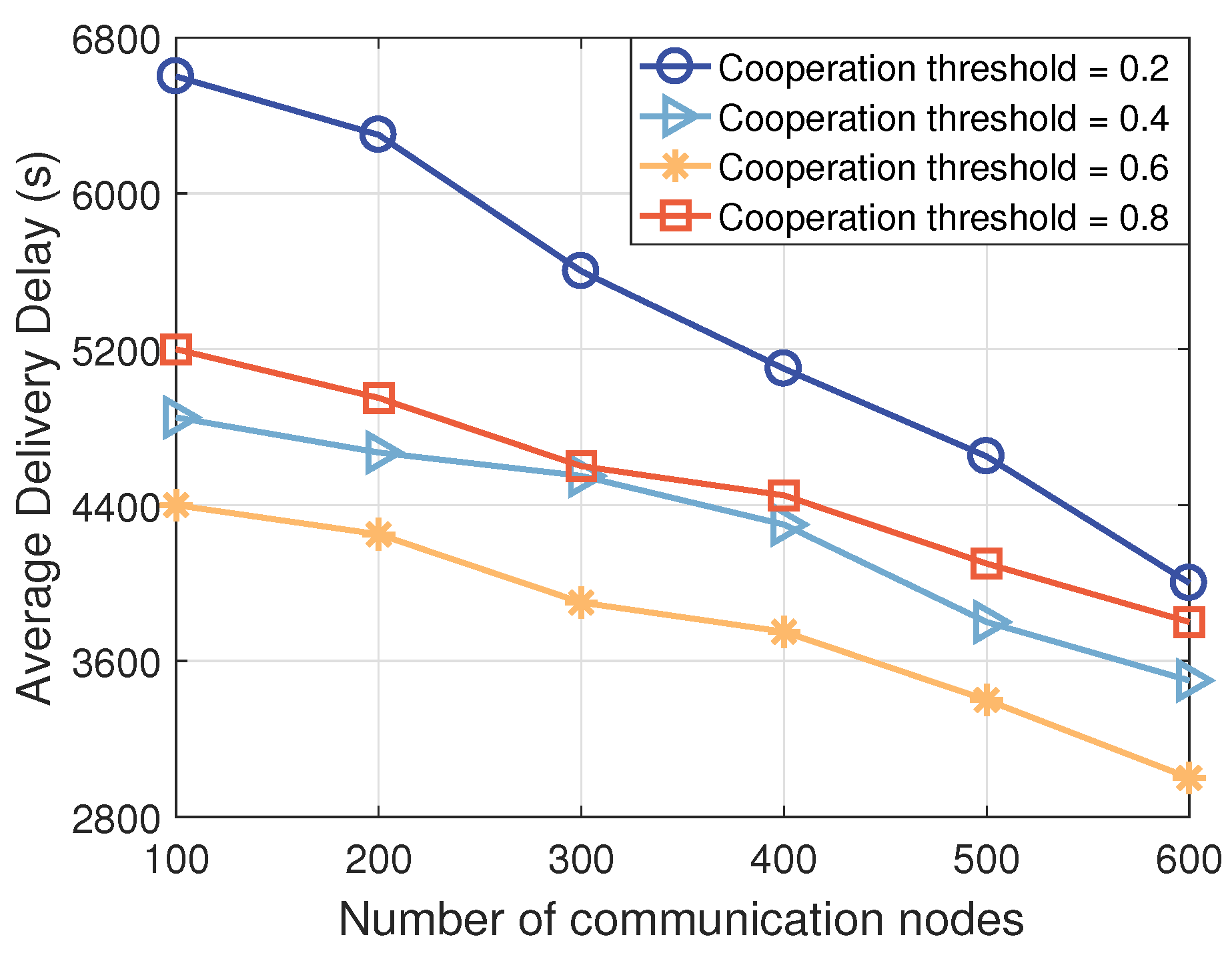
- Delivery Ratio: This metric is the most important for evaluating the opportunistic transmission scheme in integrated UAV–ICV networks. A higher delivery ratio indicates greater accuracy in information delivery by the scheme.
- Average Delivery Delay: This metric can assess the transmission ability of the opportunistic transmission scheme in integrated UAV–ICV networks. Smaller delays indicate higher ability and efficiency of the scheme.
4.2.1. Performance Comparison Under Different Proportions of Selfish Nodes
4.2.2. Impact of Different Node Cooperation Thresholds on Transmission Performance
4.2.3. Impact of Different Number of Nodes on Transmission Performance
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Lin, H.; Qian, J.; Di, B. Learning for Adaptive Multi-Copy Relaying in Vehicular Delay Tolerant Network. IEEE Trans. Intell. Transp. Syst. 2024, 25, 3054–3063. [Google Scholar] [CrossRef]
- Nakayima, O.; Soliman, M.I.; Ueda, K.; Mohamed, S.A.E. Combining Software-Defined and Delay-Tolerant Networking Concepts With Deep Reinforcement Learning Technology to Enhance Vehicular Networks. IEEE Open J. Veh. Technol. 2024, 5, 721–736. [Google Scholar] [CrossRef]
- Zou, Y.; Wei, Z.; Cui, Y.; Liu, X.; Feng, Z. UD-MAC: Delay Tolerant Multiple Access Control Protocol for Unmanned Aerial Vehicle Networks. IEEE Sens. J. 2023, 23, 23653–23663. [Google Scholar] [CrossRef]
- Wang, D.; Wang, Z.; Yu, K.; Wei, Z.; Zhao, H.; Al-Dhahir, N.; Guizani, M.; Leung, V.C.M. “Active aerial reconfigurable intelligent surface assisted secure communications: Integrating sensing and positioning. IEEE J. Sel. Areas Commun. 2024, 42, 2769–2785. [Google Scholar] [CrossRef]
- Du, H.; Wen, Q.; Zhang, S.; Gao, M. An Improved Conditional Privacy Protection Scheme Based on Ring Signcryption for VANETs. IEEE Internet Things J. 2023, 10, 17881–17892. [Google Scholar] [CrossRef]
- Tornell, S.M.; Calafate, C.T.; Cano, J.-C.; Manzoni, P. DTN Protocols for Vehicular Networks: An Application Oriented Overview. IEEE Commun. Surv. Tutor. 2015, 17, 868–887. [Google Scholar] [CrossRef]
- Asuquo, P.; Cruickshank, H.; Ogah, C.P.A.; Lei, A.; Sun, Z. A Distributed Trust Management Scheme for Data Forwarding in Satellite DTN Emergency Communications. IEEE J. Sel. Areas Commun. 2018, 36, 246–256. [Google Scholar] [CrossRef]
- Fan, Z.; Gong, S.; Long, Y.; Li, L.; Gu, B.; Luong, N.C. Delay-Tolerant Multi-Agent DRL for Trajectory Planning and Transmission Control in UAV-Assisted Wireless Networks. In Proceedings of the 2024 IEEE 99th Vehicular Technology Conference (VTC2024-Spring), Singapore, 24–27 June 2024; pp. 1–5. [Google Scholar]
- Abdelkader, T.; Naik, K.; Nayak, A.; Goel, N.; Srivastava, V. A performance comparison of delay-tolerant network routing protocols. IEEE Netw. 2016, 30, 46–53. [Google Scholar] [CrossRef]
- Tan, H.; Zheng, W.; Vijayakumar, P. Secure and Efficient Authenticated Key Management Scheme for UAV-Assisted Infrastructure-Less IoVs. IEEE Trans. Intell. Transp. Syst. 2023, 24, 6389–6400. [Google Scholar] [CrossRef]
- Liao, Z.; Ma, Y.; Huang, J.; Wang, J. Energy-Aware 3D-Deployment of UAV for IoV With Highway Interchange. IEEE Trans. Commun. 2023, 71, 1536–1548. [Google Scholar] [CrossRef]
- He, Y.; Huang, F.; Wang, D.; Zhang, R.; Gu, X.; Pan, J. NOMA-Enhanced Cooperative Relaying Systems in Drone-Enabled IoV: Capacity Analysis and Height Optimization. IEEE Trans. Veh. Technol. 2024; early access. [Google Scholar] [CrossRef]
- Wang, W.; Xu, X.; Bilal, M.; Khan, M.; Xing, Y. UAV-Assisted Content Caching for Human-Centric Consumer Applications in IoV. IEEE Trans. Consum. Electron. 2024, 70, 927–938. [Google Scholar] [CrossRef]
- He, Y.; Wang, D.; Huang, F.; Zhang, R.; Min, L. Aerial-Ground Integrated Vehicular Networks: A UAV-Vehicle Collaboration Perspective. IEEE Trans. Intell. Transp. Syst. 2024, 25, 5154–5169. [Google Scholar] [CrossRef]
- Wang, Y.; Tang, Z.; Huang, A.; Zhang, H.; Chang, L.; Pan, J. Placement of UAV-Mounted Edge Servers for Internet of Vehicles. IEEE Trans. Veh. Technol. 2024, 73, 10587–10601. [Google Scholar] [CrossRef]
- Sun, L.; Wan, L.; Wang, J.; Lin, L.; Gen, M. Joint Resource Scheduling for UAV-Enabled Mobile Edge Computing System in Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2023, 24, 15624–15632. [Google Scholar] [CrossRef]
- Du, Z.; Wu, C.; Yoshinaga, T.; Chen, X.; Wang, X.; Yau, K.L.A.; Ji, Y. A Routing Protocol for UAV-Assisted Vehicular Delay Tolerant Networks. IEEE Open J. Comput. Soc. 2021, 2, 85–98. [Google Scholar] [CrossRef]
- Gu, S.; Sun, X.; Yang, Z.; Huang, T.; Xiang, W.; Yu, K. Energy-Aware Coded Caching Strategy Design With Resource Optimization for Satellite-UAV-Vehicle-Integrated Networks. IEEE Internet Things J. 2022, 9, 5799–5811. [Google Scholar] [CrossRef]
- Hazarika, B.; Singh, K. AFL-DMAAC: Integrated Resource Management and Cooperative Caching for URLLC-IoV Networks. IEEE Trans. Intell. Veh. 2024, 9, 5101–5117. [Google Scholar] [CrossRef]
- Han, C.; Yao, H.; Mai, T.; Zhang, N.; Guizani, M. QMIX Aided Routing in Social-Based Delay-Tolerant Networks. IEEE Trans. Veh. Technol. 2022, 71, 1952–1963. [Google Scholar] [CrossRef]
- Taileb, S.; Loucif, S.; Khaoua, M.O. On the Performance of Epidemic DTN Routing on Low-Power and Lossy Networks. In Proceedings of the 2023 2nd International Conference on Electronics, Energy and Measurement (IC2EM), Medea, Algeria, 28–29 November 2023; pp. 1–5. [Google Scholar]
- Jia, B.; Li, W.; Zhou, T. A Novel P2P Service Discovery Algorithm Based on Markov in Internet of Things. In Proceedings of the 2017 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC), Guangzhou, China, 21–24 July 2017; pp. 26–31. [Google Scholar]
- Gupta, A.; Agrawal, A.; Nagrath, P. Variant of BUBBLE Rap forwarding Algorithm for delay tolerant networks. In Proceedings of the 2016 International Conference on Computational Techniques in Information and Communication Technologies (ICCTICT), New Delhi, India, 11–13 March 2016; pp. 63–68. [Google Scholar]
- Su, Y.; Liwang, M.; Chen, Z.; Du, X. Toward Optimal Deployment of UAV Relays in UAV-Assisted Internet of Vehicles. IEEE Trans. Veh. Technol. 2023, 72, 13392–13405. [Google Scholar] [CrossRef]
- Liu, Y.; Lin, P.; Zhang, M.; Zhang, Z.; Yu, F.R. Mobile-Aware Service Offloading for UAV-Assisted IoV: A Multiagent Tiny Distributed Learning Approach. IEEE Internet Things J. 2024, 11, 21191–21201. [Google Scholar] [CrossRef]
- Wan, L.; Sun, L.; Liu, K.; Wang, X.; Lin, Q.; Zhu, T. Autonomous Vehicle Source Enumeration Exploiting Non-Cooperative UAV in Software Defined Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2021, 22, 3603–3615. [Google Scholar] [CrossRef]
- Qin, P.; Fu, Y.; Ding, R.; He, H. Competition-Awareness Partial Task Offloading and UAV Deployment for Multitier Parallel Computational Internet of Vehicles. IEEE Syst. J. 2024, 18, 1753–1764. [Google Scholar] [CrossRef]
- Sami, H.; Saado, R.; Saoudi, A.E.; Mourad, A.; Otrok, H.; Bentahar, J. Opportunistic UAV Deployment for Intelligent On-Demand IoV Service Management. IEEE Trans. Netw. Serv. Manag. 2023, 20, 3428–3442. [Google Scholar] [CrossRef]
- Zhu, Y.; Xu, B.; Shi, X.; Wang, Y. A Survey of Social-Based Routing in Delay Tolerant Networks: Positive and Negative Social Effects. IEEE Commun. Surv. Tutor. 2013, 15, 387–401. [Google Scholar] [CrossRef]
- Liang, L.; Kim, J.; Jha, S.C.; Sivanesan, K.; Li, G.Y. Spectrum and power allocation for vehicular communications with delayed CSI feedback. IEEE Wirel. Commun. Lett. 2017, 6, 458–461. [Google Scholar] [CrossRef]





| Category | Parameter | Value |
|---|---|---|
| Scenario | Simulation Time | 24 h |
| Simulation Range | ||
| Simulation City | Xi’an | |
| Node | Transmission Mode | Wi-Fi |
| Transmission Range of ICVs | 200 m | |
| Transmission Range of UAVs | 1500 m | |
| Movement Speed | km/h | |
| UAV/ICV Cache Size | 50/150 MB | |
| Message | Message Size | MB |
| Message TTL | 5 h | |
| Generation Frequency | min | |
| Communication | Transmission Mechanism | OFDMA |
| Channel Bandwidth | 180 KHz | |
| Transmission Power | 30 dBm | |
| Path Loss Model (ICV-UAV) | ||
| Path Loss Model (ICV-ICV) | LoS in WINNER + B1 [30] | |
| Noise Power |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ye, M.; Zhou, Z.; Zhu, L.; Huang, F.; Li, T.; Wang, D.; Jin, Y.; He, Y. Improving Transmission in Integrated Unmanned Aerial Vehicle–Intelligent Connected Vehicle Networks with Selfish Nodes Using Opportunistic Approaches. Drones 2025, 9, 12. https://doi.org/10.3390/drones9010012
Ye M, Zhou Z, Zhu L, Huang F, Li T, Wang D, Jin Y, He Y. Improving Transmission in Integrated Unmanned Aerial Vehicle–Intelligent Connected Vehicle Networks with Selfish Nodes Using Opportunistic Approaches. Drones. 2025; 9(1):12. https://doi.org/10.3390/drones9010012
Chicago/Turabian StyleYe, Meixin, Zhenfeng Zhou, Lijun Zhu, Fanghui Huang, Tao Li, Dawei Wang, Yi Jin, and Yixin He. 2025. "Improving Transmission in Integrated Unmanned Aerial Vehicle–Intelligent Connected Vehicle Networks with Selfish Nodes Using Opportunistic Approaches" Drones 9, no. 1: 12. https://doi.org/10.3390/drones9010012
APA StyleYe, M., Zhou, Z., Zhu, L., Huang, F., Li, T., Wang, D., Jin, Y., & He, Y. (2025). Improving Transmission in Integrated Unmanned Aerial Vehicle–Intelligent Connected Vehicle Networks with Selfish Nodes Using Opportunistic Approaches. Drones, 9(1), 12. https://doi.org/10.3390/drones9010012








