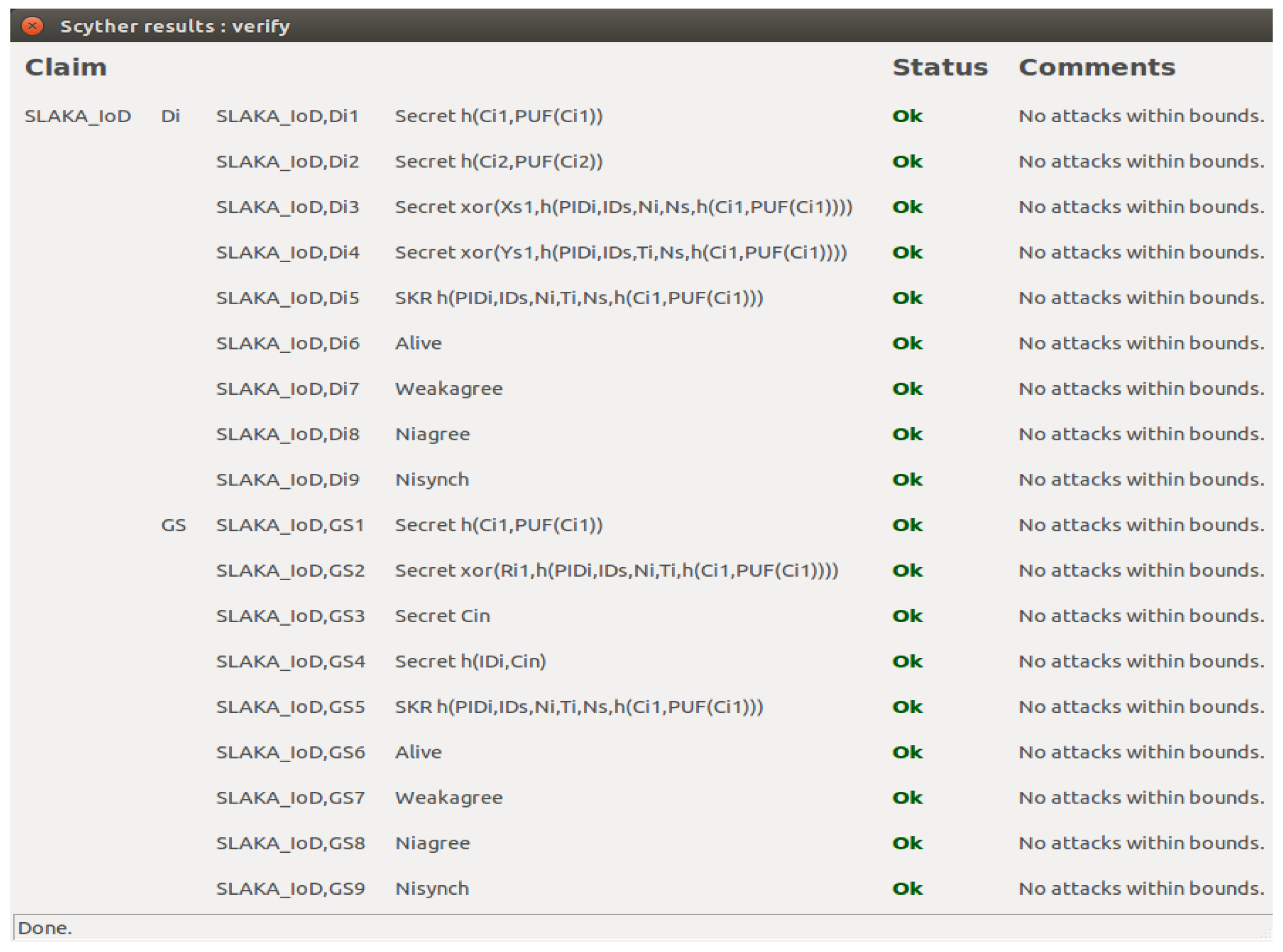
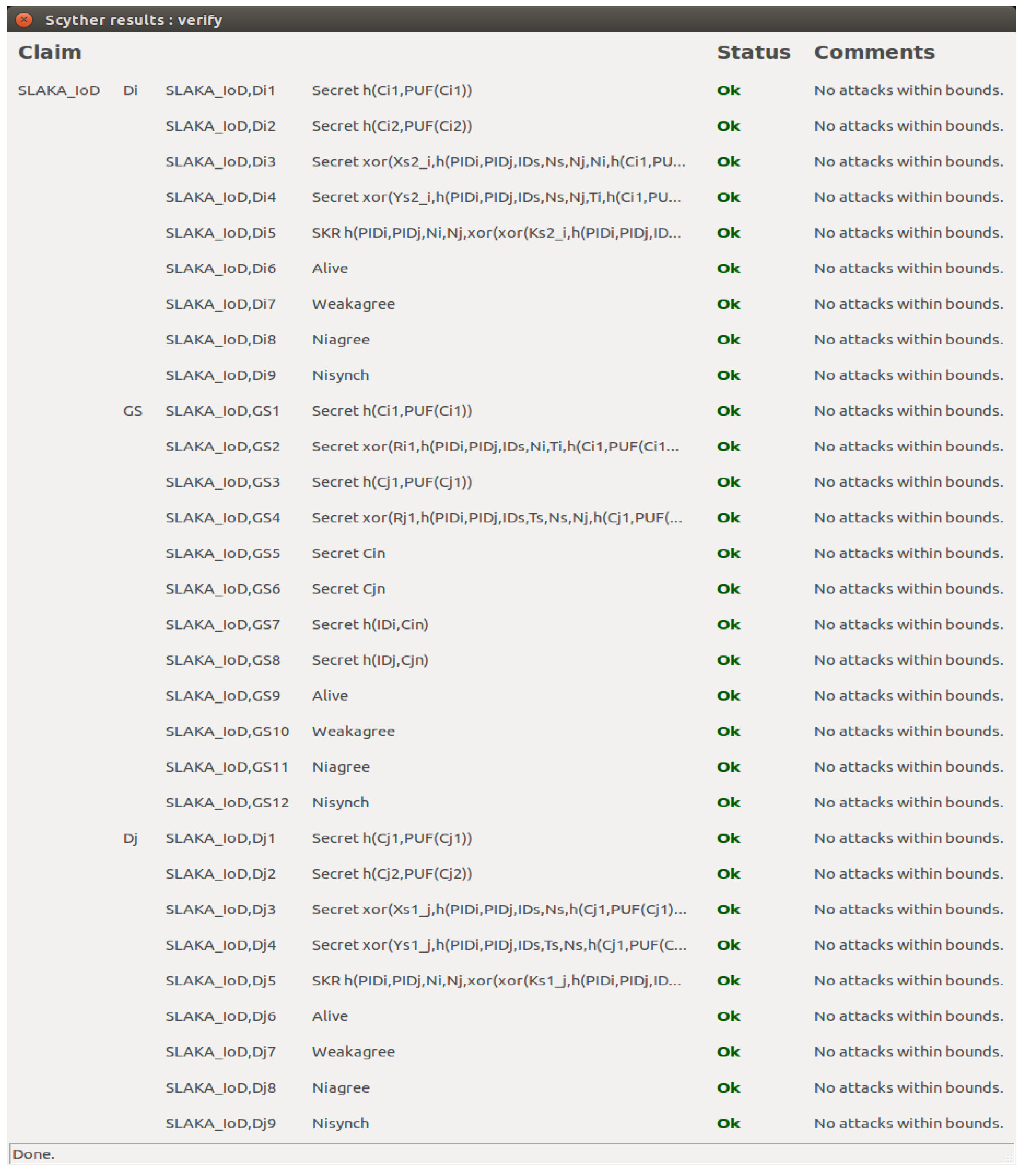
In this section, we first perform informal security analysis of SLAKA-IoD. Then, we provide a formal security analysis of SLAKS-IoD based on the strand space model. Third, we also provide security verification through the Scyther tool (v1.1.3) to prove the security of SLAKA-IoD. Finally, we compare the security features of SLAKA-IoD with other related schemes.
5.1. Informal Security Analysis
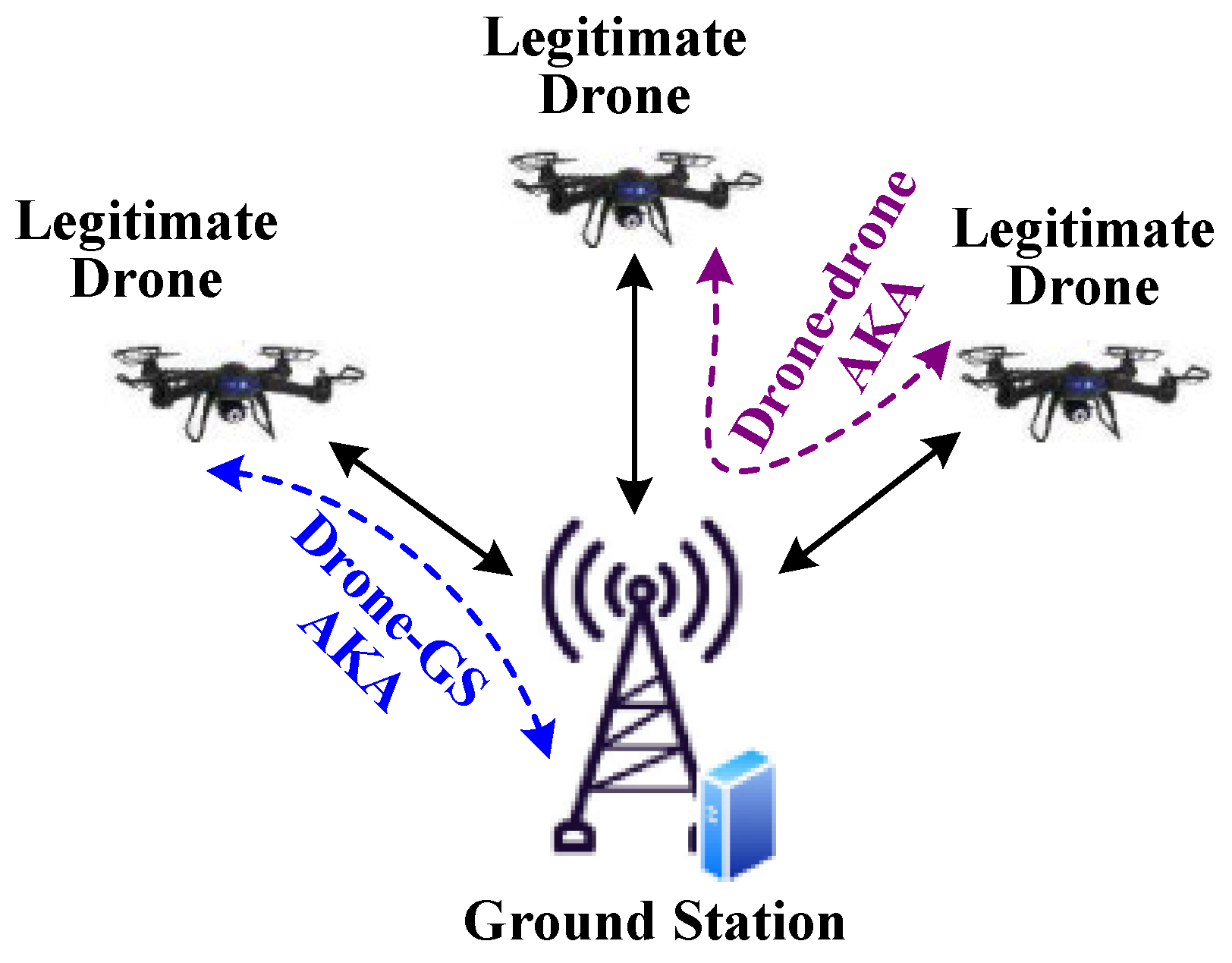
This section evaluates the security of SLAKA-IoD based on informal security analysis. We prove that SLAKA-IoD can resist various potential security attacks and provide mutual authentication, session key agreement, anonymity and untraceability.
- (1)
Impersonation Attack
In the drone-GS authentication and key agreement phase of SLAKA-IoD, if wants to impersonate , then it needs to construct . However, it is impossible to calculate and because does not know . Similarly, if wants to impersonate the , then it needs to construct , but it cannot calculate , and because does not know .
In the drone–drone authentication and key agreement phase of SLAKA-IoD, if wants to impersonate , then it needs to construct , but it cannot calculate and because does not know . If wants to impersonate , then it needs to construct , but it cannot calculate , and because does not know . Similarly, if wants to impersonate , then it needs to construct or , but it cannot calculate , , , , , , and because does not know and .
Consequently, SLAKA-IoD can resist impersonation attacks.
- (2)
Replay Attack
In the drone-GS authentication and key agreement phase of SLAKA-IoD, is protected with and includes , where is unknown to and is the current timestamp of . Hence, cannot be replayed. is protected with and includes , where is extended from and is the random number of . Thus, cannot be replayed.
In the drone–drone authentication and key agreement phase of SLAKA-IoD, is protected with and includes . Similarly, is protected with and includes , where is unknown to and is the current timestamp of the. Hence, and cannot be replayed. is protected with and includes , where is the random number of the . Similarly, is protected with and includes . Hence, and cannot be replayed.
Therefore, SLAKA-IoD can resist replay attacks.
- (3)
Denial of Service (DoS) Attack
If wants to perform DoS attacks on the SLAKA-IoD protocol, then it must be able to replay some messages of the protocol, or forge some legitimate messages of the protocol. As just described, , , , , and cannot be replayed. In addition, these messages are protected with or , which are unknown to . As a result, cannot forge them. Hence, SLAKA-IoD can resist DoS attacks.
- (4)
MITM Attack
If wants to perform MITM attacks on the SLAKA-IoD protocol, then it must intercept and tamper with the messages in the protocol. According to the above description, , , , , and are protected with or , which are unknown to . As a result, can intercept these messages, but it cannot tamper with them. Hence, SLAKA-IoD can prevent MITM attacks.
- (5)
Drone Physical Capture Attack
Assume that has physically captured or . Then, by performing power analysis attacks on them, can obtain the stored information of or , including , , , , , , , and . Although can obtain this information, it cannot try to probe or alter the integrated circuits of captured drones to retrieve the output responses of their PUFs, because this attempt will irreversibly modify the slight physical variations in the integrated circuits and in turn destroy these PUFs. That is to say, cannot obtain , , and based on , , , and , respectively, resulting in not being able to obtain , , and to compute any session key in SLAKA-IoD. Thus, SLAKA-IoD can prevent drone physical capture attacks.
- (6)
Desynchronization Attack
For the drone-GS authentication and key agreement phase of SLAKA-IoD, stores old values before receiving the second message of the phase, and updates , and after receiving the second message of the phase. In addition, not only stores old values , but also new values . Thus, whether or not blocks the second message of the phase to perform desynchronization attacks, there is always a set of pseudo-identity and key material values used for this phase between and .
For the drone–drone authentication and key agreement phase of SLAKA-IoD, stores old values before receiving the fourth message of the phase, and updates , and after receiving the fourth message of the phase. In addition, not only stores old values, and , but also new values, and . not only stores old values, , but also new values, , which will be used to update , and . Thus, whether or not blocks the third or fourth message of the phase to perform desynchronization attacks, there is always a set of pseudo-identity and key material values used for this phase among , and the .
Hence, SLAKA-IoD can prevent desynchronization attacks.
- (7)
Session Key Disclosure Attack
In the drone-GS authentication and key agreement phase of SLAKA-IoD, . However, cannot compute the session key, , because it does not know and .
In the drone–drone authentication and key agreement phase of SLAKA-IoD, . However, cannot compute the session key, , because it does not know , and .
Thus, SLAKA-IoD is resilient to session key disclosure attacks.
- (8)
ESL Attack
Based on the CK threat model, can compromise the session state and secret credentials apart from all the activities permitted under the DY threat model. In the drone-GS authentication and key agreement phase of SLAKA-IoD, even if can obtain the long-term secret , it cannot compute the session key, , because it does not know , which is computed by running the PUF of .
In the drone–drone authentication and key agreement phase of SLAKA-IoD, even if can obtain the short-term secret , it cannot compute the session key, , because it does not know and , which are computed by running PUFs of and , respectively.
Consequently, SLAKA-IoD is resilient to ESL attacks.
- (9)
Anonymity and Untraceability
For the drone-GS authentication and key agreement phase of SLAKA-IoD, is used instead of , and is different in each round of the phase. In addition, is secret, which prevents from associating and .
For the drone–drone authentication and key agreement phase of SLAKA-IoD, and are used instead of and , respectively, and are are different in each round of the phase, respectively. In addition, and are secret, which prevents from associating with , and associating with .
Note that can obtain both and by physically capturing for the drone–drone authentication and key agreement phase of SLAKA-IoD. However, it is no longer meaningful for to track its physically captured . Therefore, SLAKA-IoD provides anonymity and untraceability.
- (10)
Mutual Authentication
In the drone-GS authentication and key agreement phase of SLAKA-IoD, after receiving , the computes and checks whether is equal to . If the condition is valid, successfully authenticates because only and know . Similarly, upon receiving , computes and , and then checks whether is equal to . If the condition is valid, successfully authenticates the because only and know .
In the drone–drone authentication and key agreement phase of SLAKA-IoD, after receiving , the computes and checks whether is equal to . If the condition is valid, successfully authenticates because only and know . Similarly, upon receiving , computes and checks whether is equal to . If the condition is valid, successfully authenticates both and . This is because only and know , and is included in . After obtaining , the computes and checks whether is equal to . If the condition is valid, the successfully authenticates because only and the know . Further, upon receiving , computes and checks whether is equal to , computes , and checks whether is equal to . If these conditions are valid, successfully authenticates both and the . This is because only and the know , and only and can compute .
Hence, SLAKA-IoD provides mutual authentication.
- (11)
Forward and Backward Secrecy
For the drone-GS authentication and key agreement phase of SLAKA-IoD, even if can obtain the current session key, , it cannot compromise the session key of any past session or any future session. This is because is different in each round of the phase and cannot be obtained by , where is used to compute .
For the drone–drone authentication and key agreement phase of SLAKA-IoD, even if can obtain the current session key, , it cannot compromise the session key of any past session or any future session. This is because , and are different in each round of the phase and cannot be obtained by , where , and are used to compute .
Hence, SLAKA-IoD provides forward and backward secrecy.
- (12)
PUF Challenge–Response Pair Protection
In the above SLAKA-IoD, and instead of and are securely transmitted to the and are stored in the . Similarly, and instead of and are securely transmitted to the and are stored in the . As a result, it is difficult for to obtain , , and . Even if can obtain and , it cannot guess and in reverse based on them, as they are generated by hashing and , respectively. Similarly, even if can obtain and , it cannot guess and in reverse based on them, as they are generated by hashing and , respectively.
Additionally, and are stored in instead of the . Similarly, and are stored in instead of . Therefore, in order to obtain the PUF challenge–response pairs of , it is also necessary for to capture to obtain and . Similarly, in order to obtain the PUF challenge–response pairs of , it is also necessary for to capture to obtain and .
Hence, SLAKA-IoD provides PUF challenge–response pair protection.
5.2. Formal Security Analysis Based on the Strand Space Model
Because the strand space model [
43,
44] is a well-studied formal analysis method for security protocols, we use the strand space model to analyze the security of our proposed SLAKA-IoD protocol as follows.
Definition 1. An infiltrated strand space, , is a space for the drone-GS authentication and key agreement phase of SLAKA-IoD if it is the union of three kinds of strands: (1) Initiator strands, with trace: . The principal associated with this strand is (2) Responder strands, with trace: . The principal associated with this strand is . (3) Penetrator strands, [43,44]. Theorem 1. Suppose (1) is a space for the drone-GS authentication and key agreement phase of SLAKA-IoD, and is a bundle containing an initiator strand, ; (2) ; (3) and are uniquely originating in . Then, contains a unique responder strand, .
Proof of Theorem 1. According to assumption (2), . Since , . By assumption (3), is uniquely originating in by assumption (3), so must uniquely originate on a responder strand . By assumptions (2) and (3), and is uniquely originating in , so must uniquely originate on according to assumption (1), where . According to and Definition 1, and . Hence, . □
According to Theorem 1,
successfully authenticates
, and can establish an injection agreement [
43,
44] with them.
Theorem 2. Suppose: (1) is a space for the drone-GS authentication and key agreement phase of SLAKA-IoD, and is a bundle containing a responder strand ; (2) ; (3)
is uniquely originating in , and is a fresh timestamp to prevent replay. Then, contains a unique initiator strand .
Proof of Theorem 2. According to assumptions (2) and (3), and is uniquely originating in , so must uniquely originate on an initiator strand . Since , must originate on a responder strand according to assumption (1), where , and . As a result, , i.e., is replayed, which contradicts with assumption (3). Hence, , so , and . That is to say, . □
According to Theorem 2,
successfully authenticates
, and can establish an injection agreement [
43,
44] with them.
From Theorems 1 and 2, mutual authentication between
and
is established. Additionally, injection agreement between
and
is established, so replay and MitM attacks between
and
are overcome according to the definition of the injection agreement [
43,
44].
Definition 2. An infiltrated strand space is a space for the drone–drone authentication and key agreement phase of SLAKA-IoD if it is the union of four kinds of strands: (1) Initiator strands with trace: . The principal associated with this strand is ; (2) Responder strands with trace:. The principal associated with this strand is ; (3) Server strands with trace: The principal associated with this strand is ; (4) Penetrator strands
[43,44]. Theorem 3. Suppose: (1) is a space for the drone–drone authentication and key agreement phase of SLAKA-IoD, and is a bundle containing an initiator strand ; (2) ; (3)
, and are uniquely originating in . Then, contains a unique responder strand and a unique server strand .
Proof of Theorem 3. According to assumptions (2) and (3), and is uniquely originating in . Since , must uniquely originate on a server strand . By assumption (3), is uniquely originating in . Since , must uniquely originate on according to assumption (1), where . According to and Definition 2, and . Hence, . By assumptions (2) and (3), and is uniquely originating in , so must uniquely originate on a responder strand , where . Since and is uniquely originating in , must uniquely originate on , where , and . According to Definition 2, and . Hence, . □
According to Theorem 3,
successfully authenticates
and
, and can establish an injection agreement [
43,
44] with each of them. Note that
,
,
and
are not known to
because they are only used between
and
.
Theorem 4. Suppose: (1) is a space for the drone–drone authentication and key agreement phase of SLAKA-IoD, and is a bundle containing a responder strand ; (2); (3)
and are uniquely originating in , and is a fresh timestamp to prevent replay. Then, contains a unique initiator strand and a unique server strand .
Proof of Theorem 4. According to assumptions (2) and (3), and is uniquely originating in . Since , must uniquely originate on a server strand . Since , must originate on a responder strand , where , and . As a result, , i.e., is replayed, which contradicts with assumption (3). Hence, , so and . That is to say, . By assumptions (2) and (3), and is uniquely originating in , so must uniquely originate on an initiator strand , where . Since , must originate on a server strand , where ,, , and . As a result, , i.e., is replayed, which contradicts with assumption (3). Hence, , so , , , and . That is to say, . □
According to Theorem 4,
successfully authenticates
and
, and can establish an injection agreement [
43,
44] with each of them. Note that
,
,
and
are not known to
because they are only used between
and
.
Theorem 5. Suppose: (1) is a space for the drone–drone authentication and key agreement phase of SLAKA-IoD, and is a bundle containing a server strand, ; (2)
; (3)
, and
are uniquely originating in , and is a fresh timestamp to prevent replay. Then, contains a unique initiator strand and a responder strand .
Proof of Theorem 5. By assumptions (2) and (3), and is uniquely originating in , so must uniquely originate on an initiator strand . Since , must originate on a server strand , where ,, , and . As a result, , i.e., is replayed, which contradicts with assumption (3). Hence, , so , , , and . That is to say, . By assumptions (2) and (3), and is uniquely originating in , so must uniquely originate on a responder strand . Since and is uniquely originating in , must uniquely originate on , where and . According to Definition 2, and . Hence, . □
According to Theorem 5,
successfully authenticates
and
, and can establish an injection agreement [
43,
44] with each of them.
From Theorems 3–5, mutual authentication among
,
and
is established. Additionally, injection agreement among
,
and
is established. Hence, according to the definition of the injection agreement [
43,
44], replay and MitM attacks among
,
and
are overcome.