Internet of Drones: Improving Multipath TCP over WiFi with Federated Multi-Armed Bandits for Limitless Connectivity
Abstract
1. Introduction
- Provide a minimum of 20 Gbit/s throughputs;
- Be backward compatible with IEEE 802.11ad; and
- Broaden the collection of conceivable use cases and situations by offering innovative PHY and MAC layer solutions.
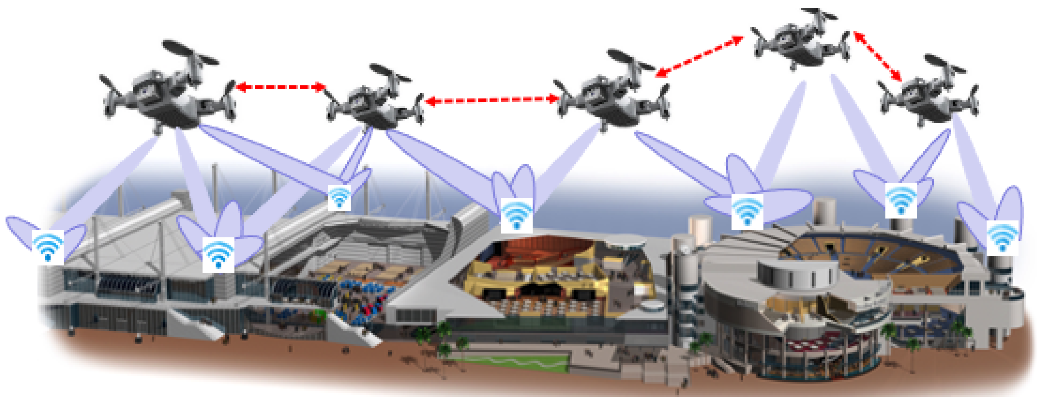
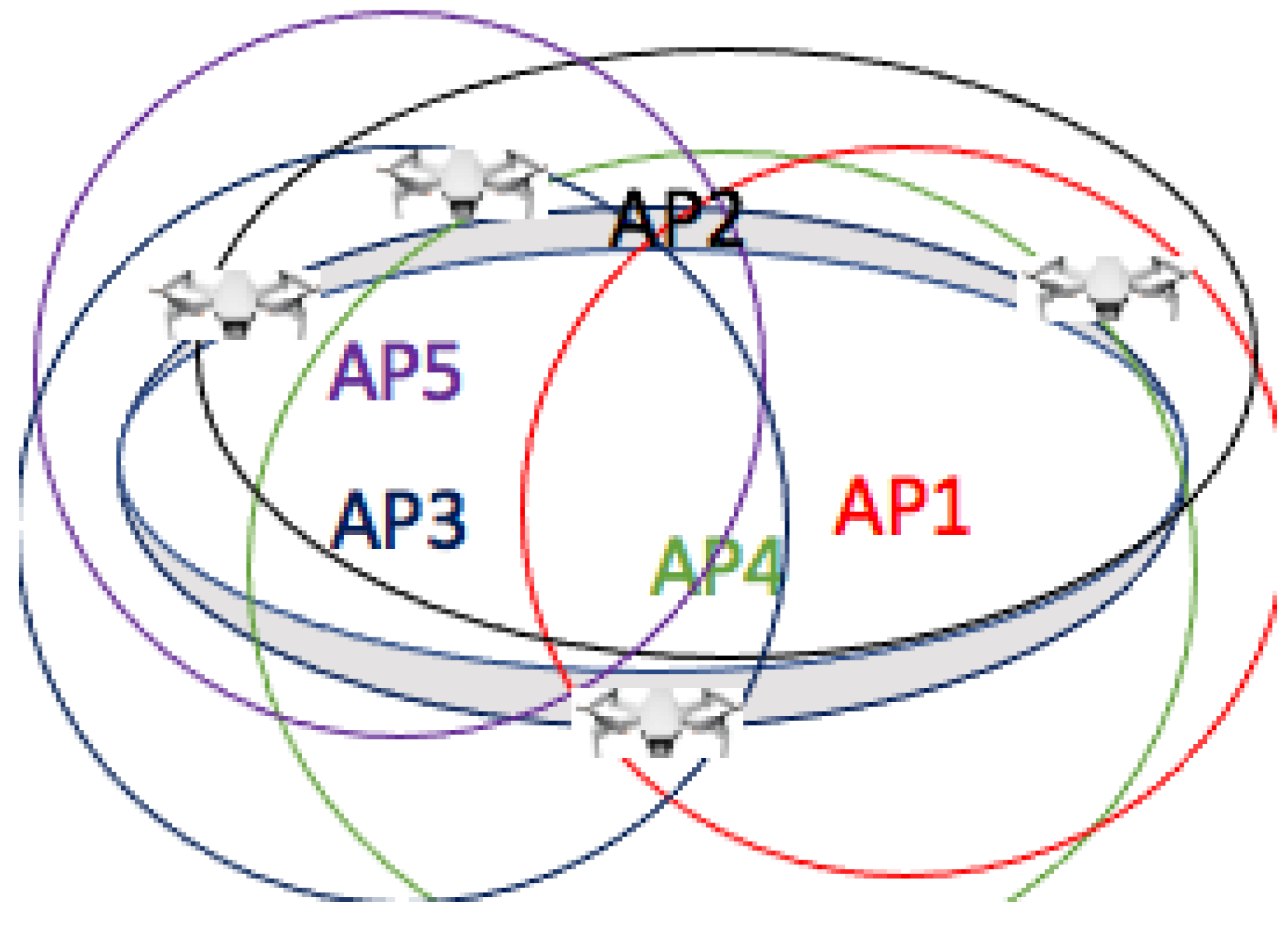
1.1. Motivating Example
1.2. Challenges and Contributions
1.2.1. Multipath TCP over IEEE 802.11ay
- ∘
- Uncertain mmWave links and delays. Future applications such as trajectory control and haptic communications require extremely low delay control information and high-speed video delivery guarantees. However, as a result of queueing, beamforming, channel bonding, MIMO, mobility-induced handoffs, other connections sharing the link, retransmissions, etc., the time taken to travel a packet from end-to-end is inherently stochastic and time-varying. Therefore, packets can easily arrive at the devices reordered, in which case they need to be buffered until they can be delivered in the correct order to the TRA-Layer [11], creating head-of-line blocking (HoL). The resulting buffering delay can be substantial, to the point where it essentially undermines the speed/latency gain from the use of several 802.11ay links.
- ∘
- Unknown delays in learning PHY/MAC dynamics from the TRA layer. When a connection is first established, the end hosts are unaware of the link’s properties (e.g., queuing/retransmissions) and PHY/MAC techniques (e.g., MIMO/bonding, backoffs, etc.). Typically, information is limited to obtained during the first connection handshake and perhaps stored past historical data. As the connection proceeds, feedback is received from packet transmissions, but this feedback is delayed (round trip time (RTT) can correspond to the transmission of hundreds of packets over high-speed 802.11ay). Small packets (with short control information from the server) thus have limited information to link characteristics, and bulk connections (8K video streaming uplink to the server) need to learn the link characteristics on the fly (e.g., simultaneous tracking, estimation, and optimization) as packets are being transmitted.
- ∘
- Low delay forward error correction (FEC). The most efficient way to use coded packets or packet replication (e.g., cloning) over modern WiFi is currently unclear, and the design of low-delay cloning/coding for multipath links remains poorly understood in the literature.
1.2.2. Modeling Challenges
1.2.3. Contributions
- Intelligent multipath scheduler. We investigate developing learning-based (intelligent) multipath scheduling algorithms that distribute information and coded packets to links with the least amount of delay at the receiver.
- Collaborative beamforming and scheduling design. Considering the challenges in designing intelligent FEC-aware scheduling and low latency error-correcting codes at the PHY/MAC layer, the influence of the data size on the ideal multipath scheduler, and the necessity for collaborative bonding, beamforming, and scheduling, we employ multi-armed bandit with federated learning (FL) over the links, to explore and exploit optimal characteristics for the proposed integrated cross-layer design.
- Multipath network support from the TRA layer. In addition to the above innovations, we develop a coupled low-delay multipath scheduling protocol (LD-MPSP) for 802.11ay networks. We design tuneable packet cloning to adapt to the size of the flows and resolve the impeding challenges over erroneous 802.11ay links.
1.3. Literature
1.4. Organization
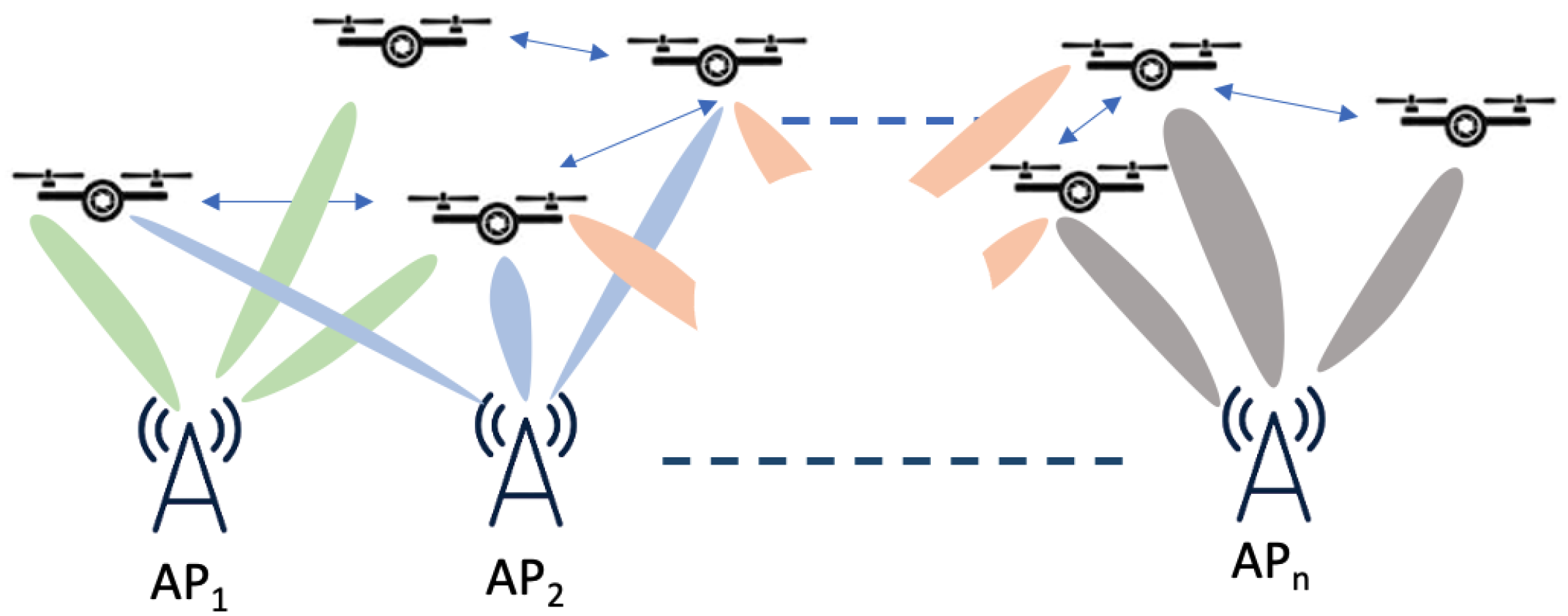
2. Network Scenarios and Problems
2.1. Background of 802.11ay
2.2. Observations
2.3. Packet Scheduling over 802.11ay from TRA Layer
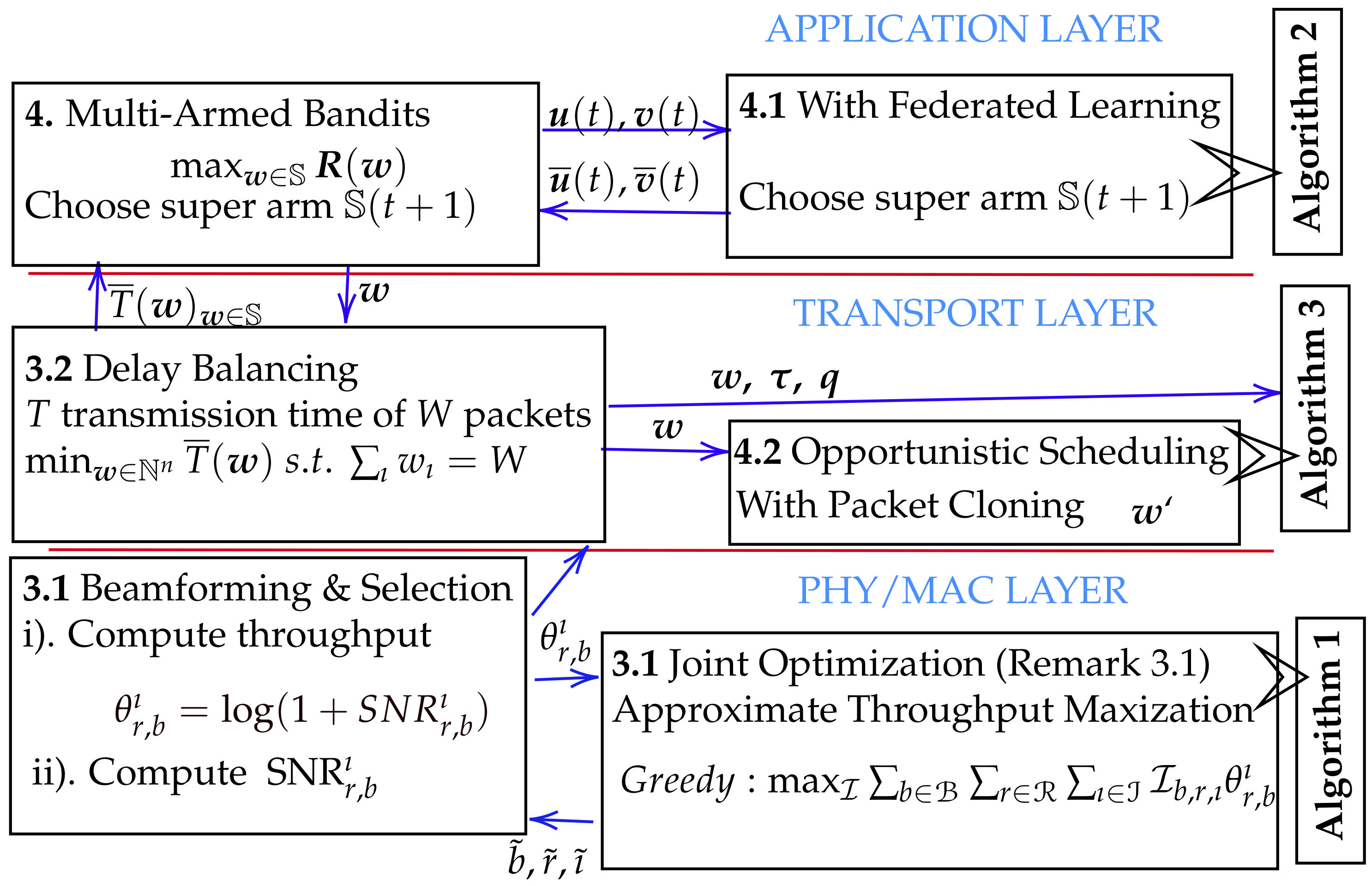
3. Analytic Modeling
3.1. Modeling Beamforming and Selection Mechanism
| Algorithm 1 Beamforming and RF chain allocation |
|
3.2. Understanding Delay Balancing
3.3. How the MPTCP Scheduler May Solve (11)
4. Multi-Armed Bandit (MAB) for Optimal MPTCP Scheduling
| Algorithm 2 MS-UCB multipath scheduling algorithm |
|
4.1. With Federated Learning
4.2. With Packet Cloning
5. Multi-Connectivity over IEEE 802.11ay Links
- ∘
- For each Ack on link ı, , and
- ∘
- For each packet loss on link ı,
| Algorithm 3 LD-MPSP Algorithm |
|
5.1. Fluid Approximation
5.2. Equilibrium Conditions
5.3. Utility Maximization
5.4. Computational Complexity of LDMPSP
6. Results and Discussion
6.1. Simulation Setup
- In NS-3, we have created an MPTCP module [11] that adheres to RFC-6824 and closely resembles the MPTCP Linux kernel architecture. See [11], where we can obtain a quick overview of our module. Several path management approaches (e.g., FullMesh and NdiffPorts), MPTCP congestion control and scheduling protocols (e.g., LIA, OLIA, BALIA, DALIA) are supported by the module.
- IEEE 802.11ad/ay NS-3 implementation is another main foundation of our performance evaluation setup [33]. We utilize the IEEE 802.11ay MAC layer design with a very accurately abstracted PHY layer. In addition, we implement a realistic mmWave channel model based on channel profiles obtained by the ray-tracing software at 60 GHz. Our NS-3 MPTCP module is coupled tightly with the 802.11ad/ay implementation.
- We adopt a MATLAB-based code/beam generator for creating codebook instances that describe the beam patterns of an IEEE 802.11ad/ay enabled device’s phased antenna array(s) (https://github.com/wigig-tools/codebook-generator, accessed on 22 November 2022);
- We implement a MATLAB-based mmWave channel modeling as a ray-tracing software for channel realization building upon quasi-deterministic channel realization software publicly available in GihHub (https://github.com/wigig-tools/qd-realization, accessed on 22 November 2022);
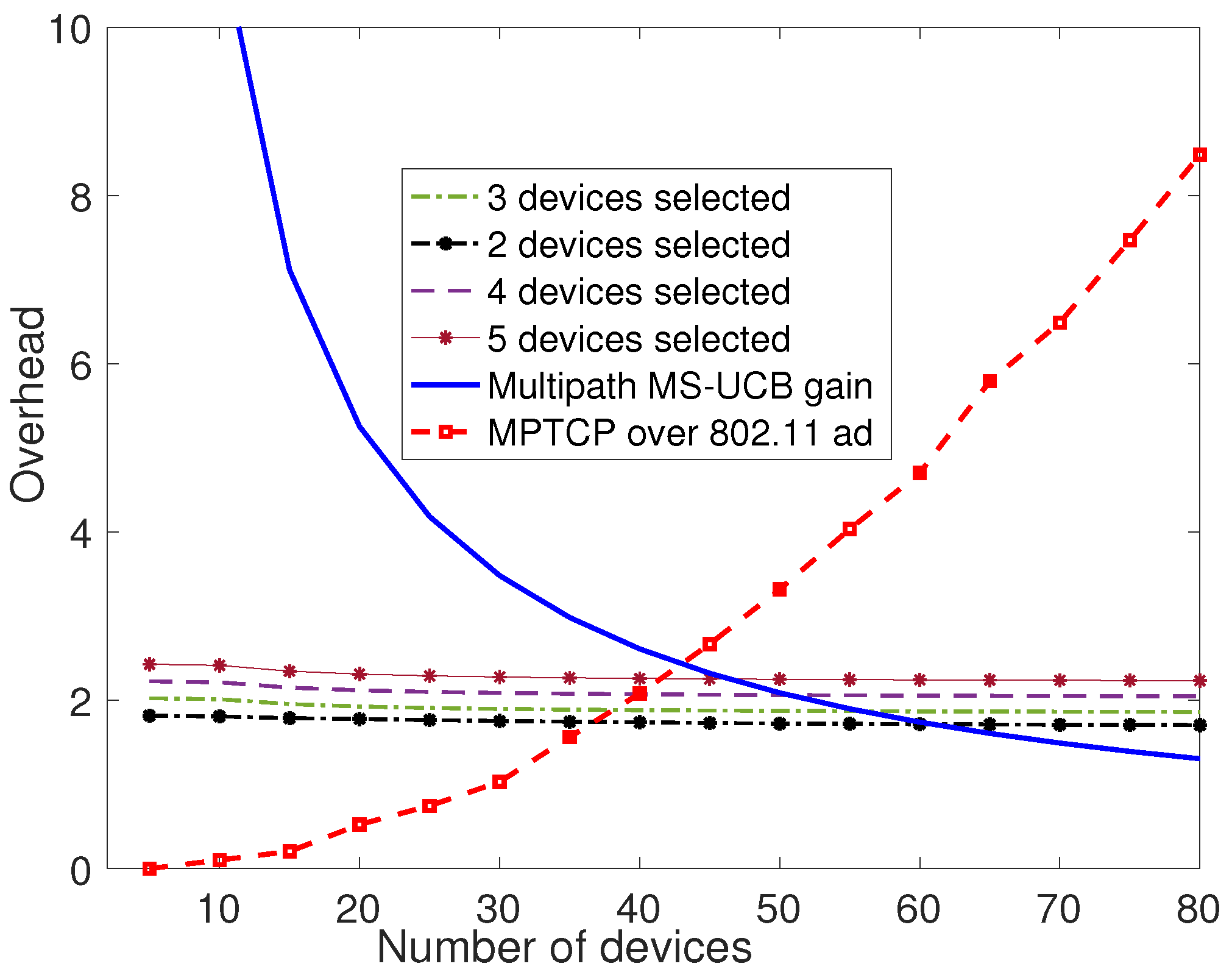
6.2. Evaluating Multipath Scheduling with Beamforming and Selection
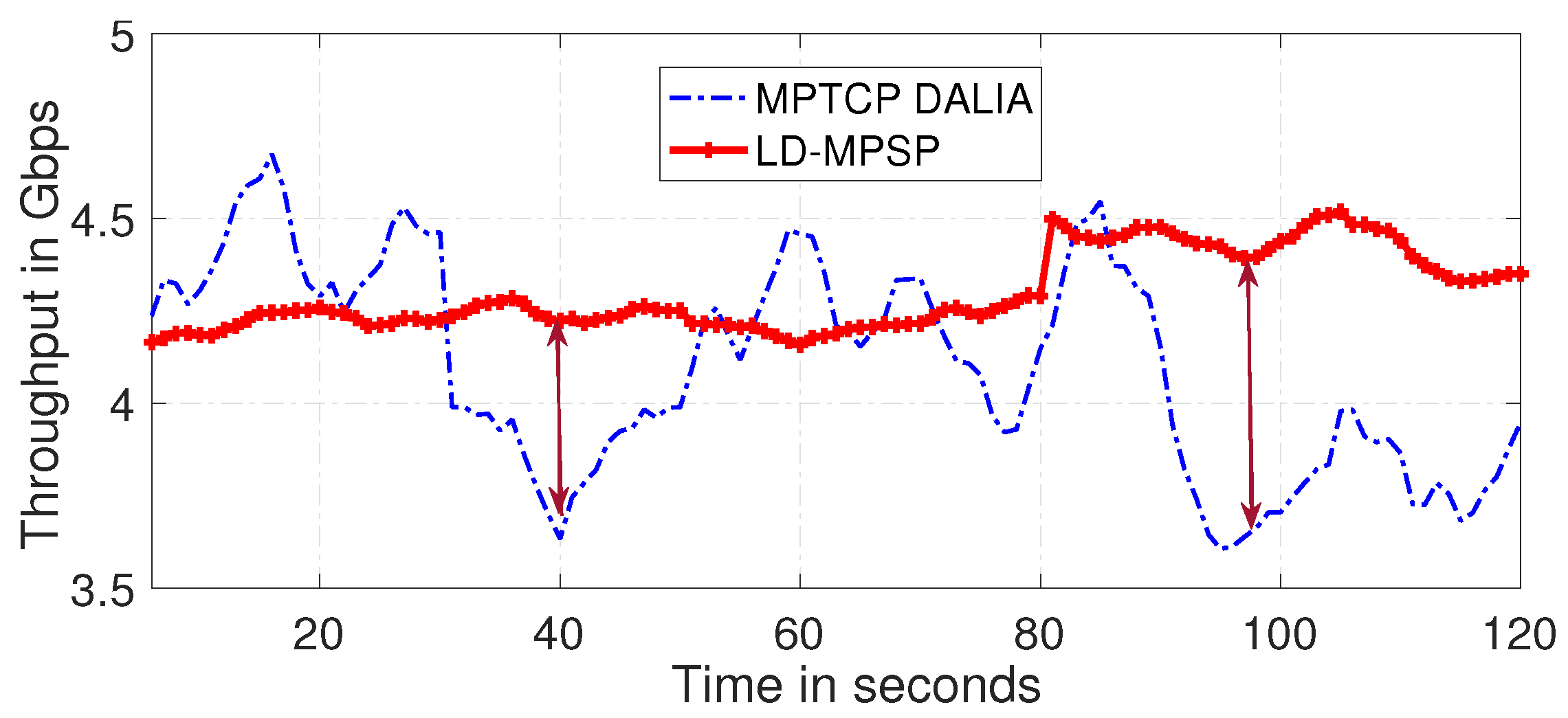
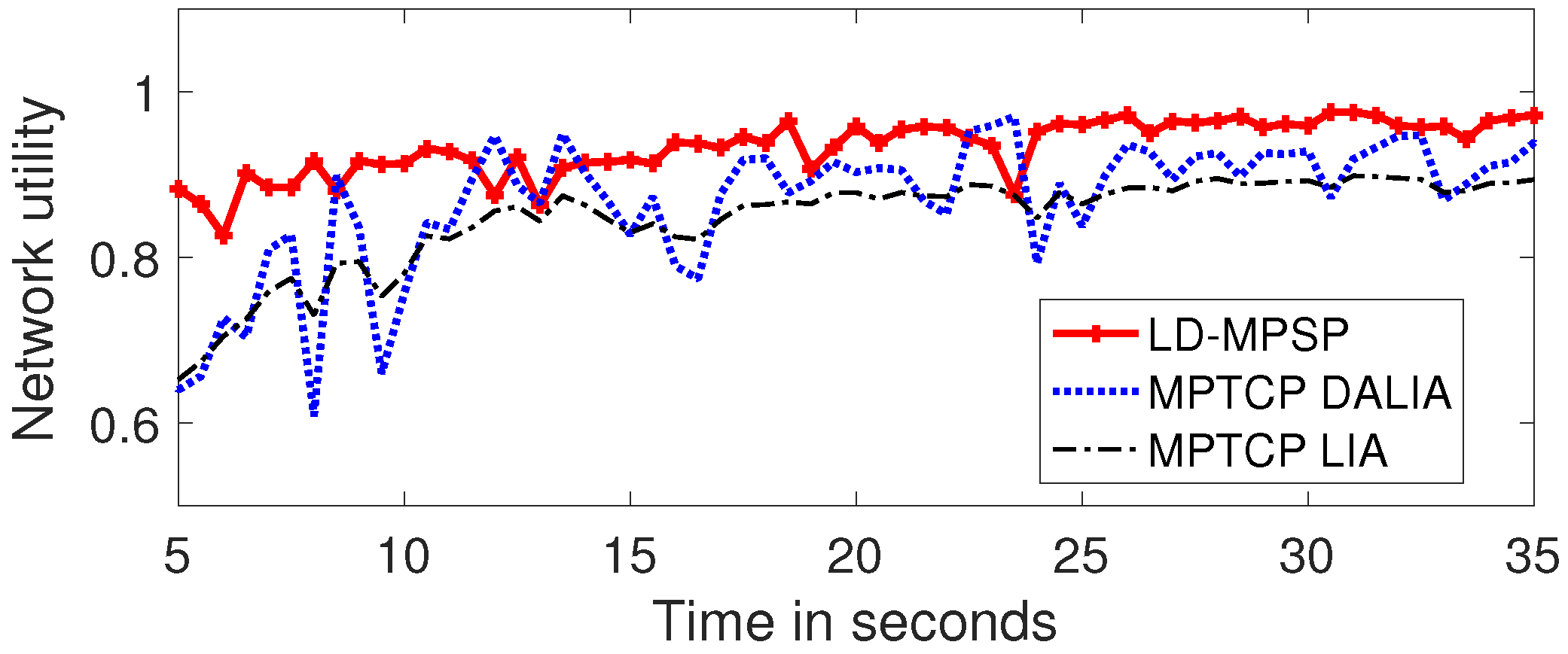
6.3. Observing Application Performance from the TRA Layer
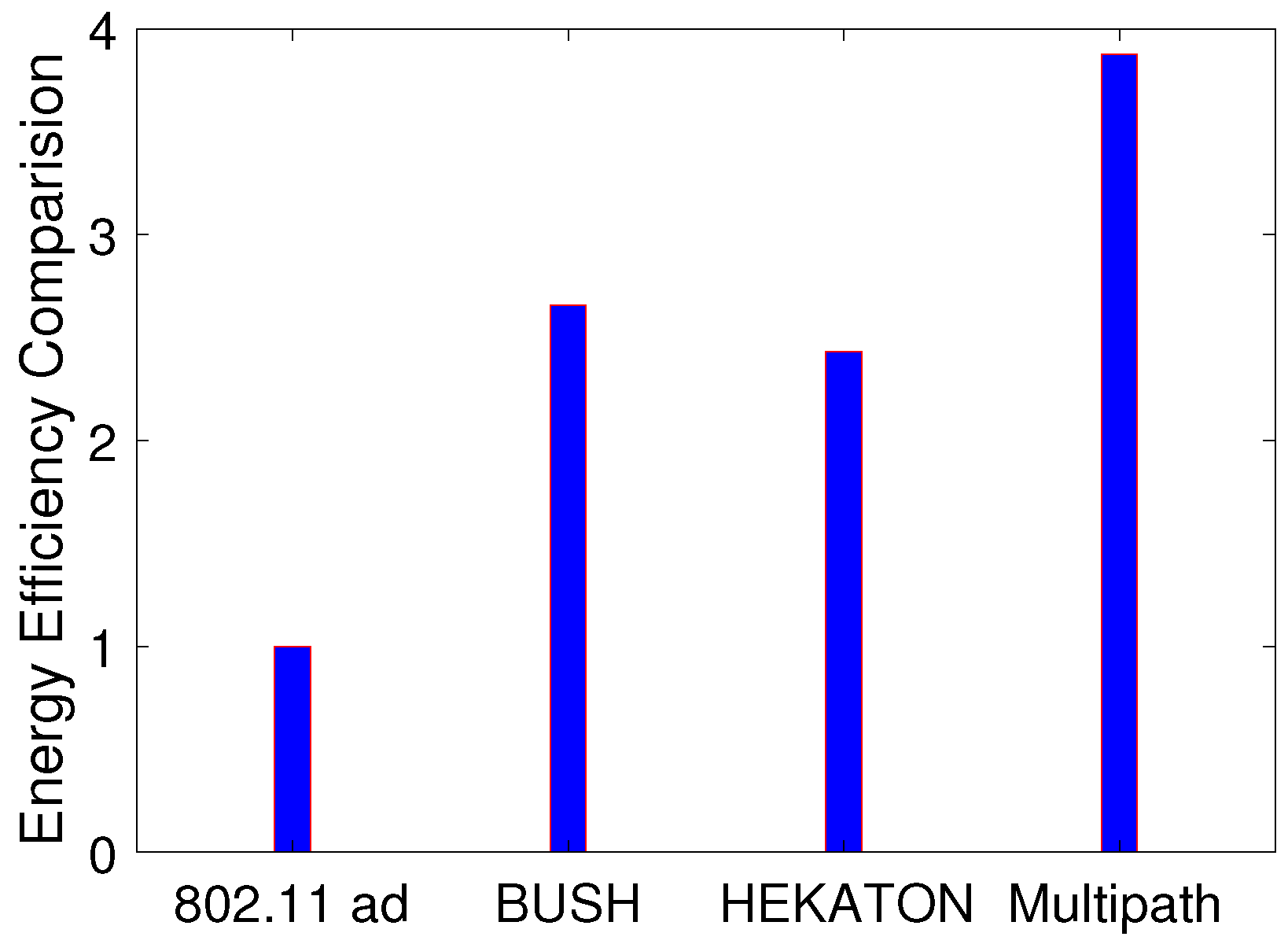
6.4. Comparing Energy Efficiency
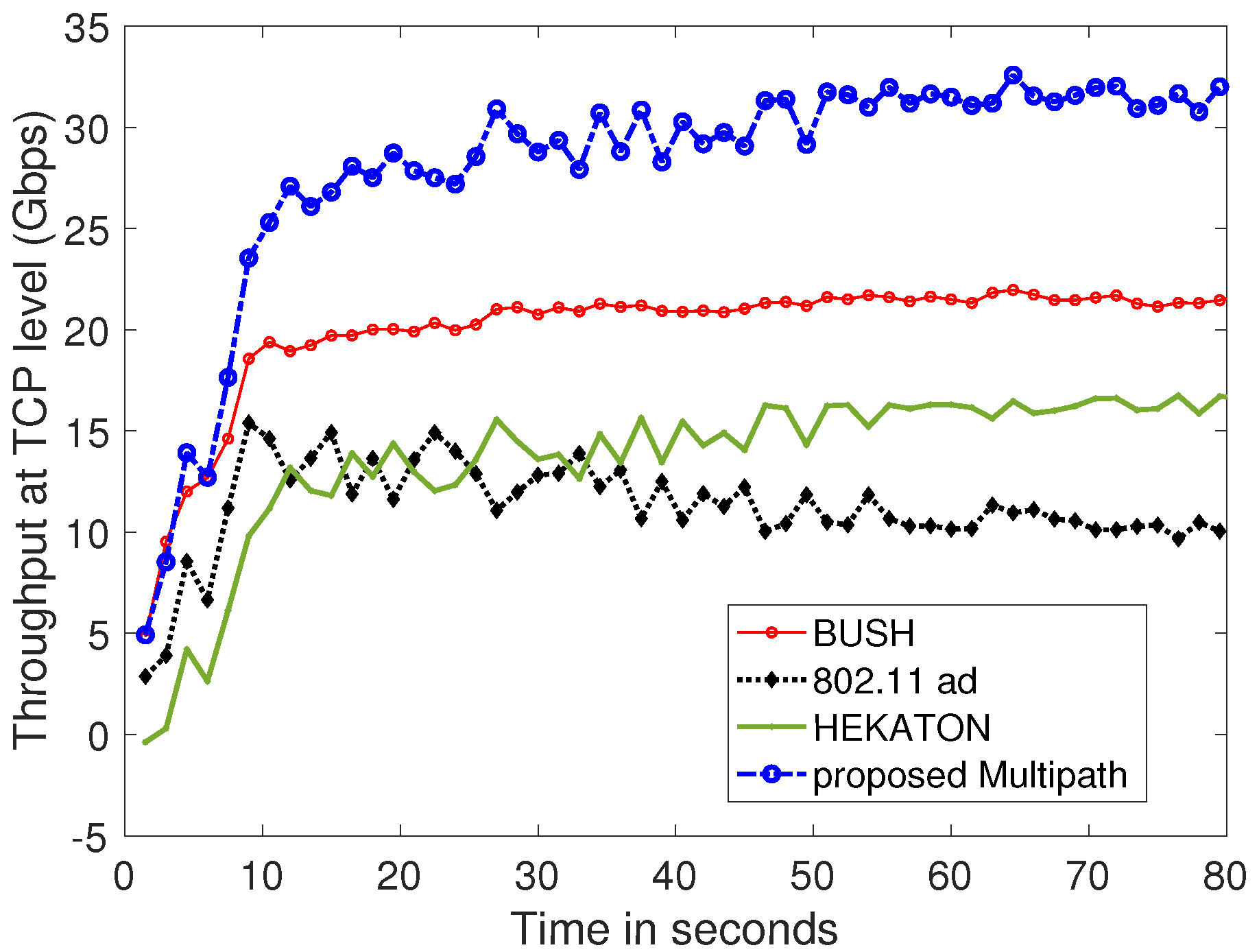
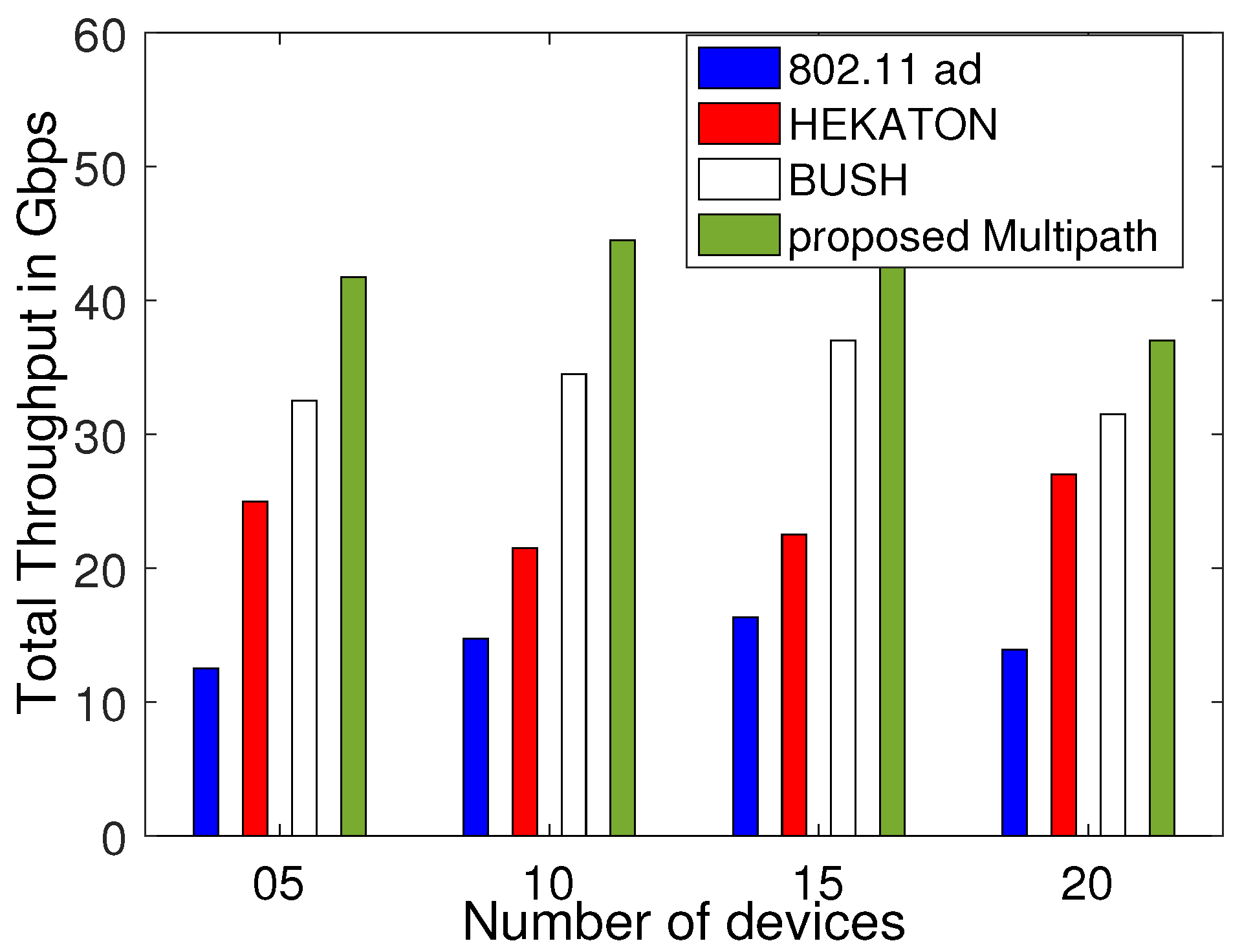
6.5. Evaluating Aggregate Throughput
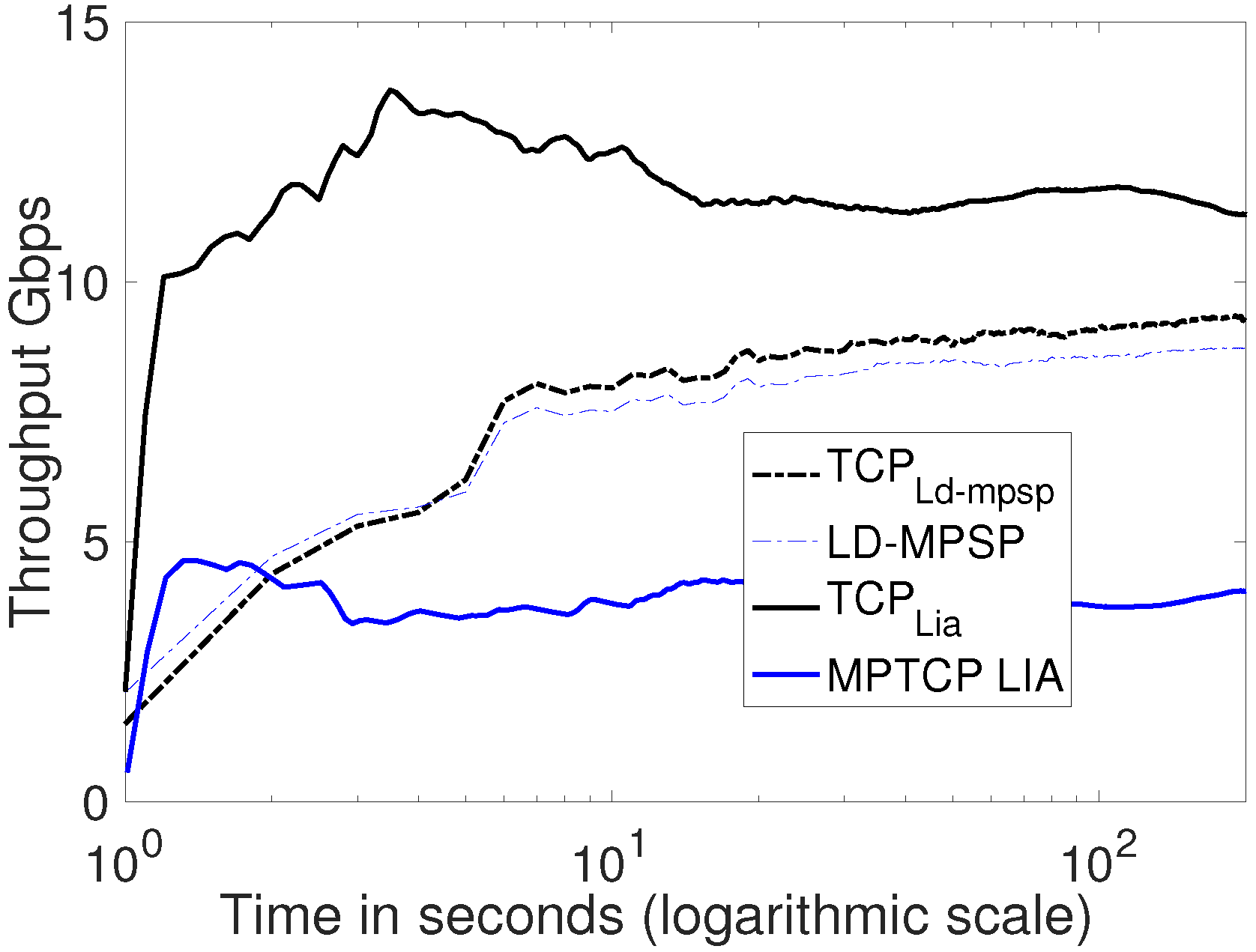
6.6. Comparing the Proposed Framework with Celebrated Multipath TCP
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- IEEE Draft Standard for Information Technology-Telecommunications and Information Exchange Between Systems—Local and Metropolitan Area Networks-Specific Requirements Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications-Amendment 2: Enhanced Throughput for Operation in License-Exempt Bands Above 45 GHz; IEEE: Piscataway, NJ, USA, 2020.
- Huang, K.; Huang, L.; Quan, Y.; Du, H.; Luo, C.; Lu, L.; Hou, R. Mutli-Link Channel Access Schemes for IEEE 802.11be Extremely High Throughput. IEEE Commun. Stand. Mag. 2022, 6, 46–51. [Google Scholar] [CrossRef]
- Sahoo, A.; Gao, W.; Ropitault, T.; Golmie, N. Admission Control and Scheduling of Isochronous Traffic With Guard Time in IEEE 802.11ad MAC. IEEE Trans. Mob. Comput. 2022, 1–10. [Google Scholar] [CrossRef]
- Ghasempour, Y.; da Silva, C.R.C.M.; Cordeiro, C.; Knightly, E.W. IEEE 802.11ay: Next-Generation 60 GHz Communication for 100 Gb/s WiFi. IEEE Commun. Mag. 2017, 55, 186–192. [Google Scholar] [CrossRef]
- Wischik, D.; Raiciu, C.; Greenhalgh, A.; Handley, M. Design, Implementation and Evaluation of Congestion Control for Multipath TCP. In Proceedings of the USENIX NSDI Conference, Boston, MA, USA, 30 March–1 April 2011; Volume 11, p. 8. [Google Scholar]
- Wu, H.; Caso, G.; Ferlin, S.; Alay, O.; Brunstrom, A. Multipath Scheduling for 5G Networks: Evaluation and Outlook. IEEE Commun. Mag. 2021, 59, 44–50. [Google Scholar] [CrossRef]
- Peng, Q.; Walid, A.; Hwang, J.; Low, S.H. Multipath TCP: Analysis, Design, and Implementation. IEEE/ACM Trans. Netw. 2016, 24, 596–609. [Google Scholar] [CrossRef]
- Michel, F.; Cohen, A.; Malak, D.; Coninck, Q.D.; Médard, M.; Bonaventure, O. FlEC: Enhancing QUIC With Application-Tailored Reliability Mechanisms. IEEE/ACM Trans. Netw. 2022, 1–14. [Google Scholar] [CrossRef]
- Wei, W.; Xue, K.; Han, J.; Wei, D.S.; Hong, P. Shared bottleneck-based congestion control and packet scheduling for multipath TCP. IEEE/ACM Trans. Netw. 2020, 28, 653–666. [Google Scholar] [CrossRef]
- 3GPP. 3GPP TS 23.501, V16.6.0 (ETSI); System Architecture for the 5G System; 3GPP: Paris, France, 2020. [Google Scholar]
- Pokhrel, S.R.; Mandjes, M. Improving Multipath TCP Performance over WiFi and Cellular Networks: An Analytical Approach. IEEE Trans. Mob. Comput. 2019, 18, 2562–2576. [Google Scholar] [CrossRef]
- Van De Meent, R.; Mandjes, M.; Pras, A. Gaussian traffic everywhere? In Proceedings of the 2006 IEEE International Conference on Communications, Istanbul, Turkey, 11–15 June 2006; Volume 2, pp. 573–578. [Google Scholar]
- Hohn, N.; Veitch, D.; Abry, P. Cluster processes: A natural language for network traffic. IEEE Trans. Signal Process. 2003, 51, 2229–2244. [Google Scholar] [CrossRef]
- Heemskerk, M.; Mandjes, M.; Mathijsen, B. Staffing for many-server systems facing non-standard arrival processes. Eur. J. Oper. Res. 2022, 296, 900–913. [Google Scholar] [CrossRef]
- Mandjes, M.; Van De Meent, R. Resource dimensioning through buffer sampling. IEEE/ACM Trans. Netw. 2009, 17, 1631–1644. [Google Scholar] [CrossRef]
- Asanjarani, A.; Nazarathy, Y.; Taylor, P. A survey of parameter and state estimation in queues. Queueing Syst. 2021, 97, 39–80. [Google Scholar] [CrossRef]
- Mandjes, M.; Ravner, L. Hypothesis testing for a Lévy-driven storage system by Poisson sampling. Stoch. Process. Their Appl. 2021, 133, 41–73. [Google Scholar] [CrossRef]
- Krishnasamy, S.; Sen, R.; Johari, R.; Shakkottai, S. Learning unknown service rates in queues: A multiarmed bandit approach. Oper. Res. 2021, 69, 315–330. [Google Scholar] [CrossRef]
- Pokhrel, S.R.; Choi, J. Low-Delay Scheduling for Internet of Vehicles: Load-Balanced Multipath Communication With FEC. IEEE Trans. Commun. 2019, 67, 8489–8501. [Google Scholar] [CrossRef]
- Xie, X.; Chai, E.; Zhang, X.; Sundaresan, K.; Khojastepour, A.; Rangarajan, S. Hekaton: Efficient and practical large-scale MIMO. In Proceedings of the 21st Annual International Conference on Mobile Computing and Networking, Paris, France, 7–11 September 2015; pp. 304–316. [Google Scholar]
- Chen, Z.; Zhang, X.; Wang, S.; Xu, Y.; Xiong, J.; Wang, X. Enabling Practical Large-Scale MIMO in WLANs With Hybrid Beamforming. IEEE/ACM Trans. Netw. 2021, 29, 1605–1619. [Google Scholar] [CrossRef]
- Amakawa, S.; Aslam, Z.; Buckwater, J.; Caputo, S.; Chaoub, A.; Chen, Y.; Corre, Y.; Fujishima, M.; Ganghua, Y.; Gao, S.; et al. White Paper on RF Enabling 6G—Opportunities and Challenges from Technology to Spectrum; 6G Flagship: Oulu, Finland, 2021. [Google Scholar]
- Raiciu, C.; Handley, M.; Wischik, D. Coupled Congestion Control for Multipath Transport Protocols; IETF RFC 6356; Internet Engineering Task Force: Fremont, CA, USA, 2011. [Google Scholar]
- Lee, C.; Jung, J.; Chung, J.M. DEFT: Multipath TCP for High Speed Low Latency Communications in 5G Networks. IEEE Trans. Mob. Comput. 2020, 20, 3311–3323. [Google Scholar] [CrossRef]
- McMahan, B.; Moore, E.; Ramage, D.; Hampson, S.; Arcas, B.A.y. Communication-efficient learning of deep networks from decentralized data. In Proceedings of the 20 th International Conference on Artificial Intelligence and Statistics, PMLR, Fort Lauderdale, FL, USA, 20–22 April 2017; pp. 1273–1282. [Google Scholar]
- Bellavista, P.; Giannelli, C.; Mamei, M.; Mendula, M.; Picone, M. Application-driven Network-aware Digital Twin Management in Industrial Edge Environments. IEEE Trans. Ind. Inform. 2021, 17, 7791–7801. [Google Scholar] [CrossRef]
- Gai, Y.; Krishnamachari, B.; Jain, R. Combinatorial network optimization with unknown variables: Multi-armed bandits with linear rewards and individual observations. IEEE/ACM Trans. Netw. 2012, 20, 1466–1478. [Google Scholar] [CrossRef]
- Xia, W.; Quek, T.Q.; Guo, K.; Wen, W.; Yang, H.H.; Zhu, H. Multi-Armed Bandit-Based Client Scheduling for Federated Learning. IEEE Trans. Wirel. Commun. 2020, 19, 7108–7123. [Google Scholar] [CrossRef]
- Zhu, Z.; Zhu, J.; Liu, J.; Liu, Y. Federated Bandit: A Gossiping Approach. Proc. ACM Meas. Anal. Comput. Syst. 2021, 5, 3–4. [Google Scholar] [CrossRef]
- Khalili, R.; Gast, N.; Popovic, M.; Le Boudec, J.Y. MPTCP is Not Pareto-optimal: Performance Issues and a Possible Solution. IEEE/ACM Trans. Netw. 2013, 21, 1651–1665. [Google Scholar] [CrossRef]
- Auer, P.; Cesa-Bianchi, N.; Fischer, P. Finite-time analysis of the multiarmed bandit problem. Mach. Learn. 2002, 47, 235–256. [Google Scholar] [CrossRef]
- Pokhrel, S.R.; Williamson, C. A Rent-Seeking Framework for Multipath TCP. ACM SIGMETRICS Perform. Eval. Rev. 2021, 48, 63–70. [Google Scholar] [CrossRef]
- Assasa, H.; Grosheva, N.; Ropitault, T.; Blandino, S.; Golmie, N.; Widmer, J. Implementation and evaluation of a WLAN IEEE 802.11 ay model in network simulator ns-3. In Proceedings of the WNS3 2021: 2021 Workshop on ns-3, Virtual, 23–24 June 2021; pp. 9–16. [Google Scholar]
- Pokhrel, S.R.; Walid, A. Learning to Harness Bandwidth with Multipath Congestion Control and Scheduling. IEEE Trans. Mob. Comput. 2021, 1. [Google Scholar] [CrossRef]
- Pokhrel, S.R.; Choi, J. Federated Learning With Blockchain for Autonomous Vehicles: Analysis and Design Challenges. IEEE Trans. Commun. 2020, 68, 4734–4746. [Google Scholar] [CrossRef]
- Pokhrel, S.R.; Choi, J. Improving TCP Performance Over WiFi for Internet of Vehicles: A Federated Learning Approach. IEEE Trans. Veh. Technol. 2020, 69, 6798–6802. [Google Scholar] [CrossRef]
- Pokhrel, S.R.; Choi, J.; Walid, A. Fair and Efficient Distributed Edge Learning With Hybrid Multipath TCP. IEEE/ACM Trans. Netw. 2022, 1–13. [Google Scholar] [CrossRef]

| MCS | EDMG SC | EDMG OFDM |
|---|---|---|
| Maximum TCP Throughput | 28.96 Gbps | 30.95 Gbps |
| Mobility TCP Throughput | 9.6 Gbps | 9.25 Gbps |
| Mobility MPTCP Throughput | 16.36 Gbps | 16.15 Gbps |
| Maximum MPTCP Throughput | 41.32 Gbps | 42.13 Gbps |
| Parameters | Value | Parameters | Value |
|---|---|---|---|
| TRA Protocol | TCP/MPTCP | TCP Header | |
| Aggregation | MSDU/MPDU | A-MSDU bytes | 7935 |
| IP Header | A-MPDU bytes | ||
| Payload size | Propagation delay | ||
| Block Ack Size | No. of Transmits | 27 sectors | |
| Sector Azimuth | :: | Congestion window | |
| Sector Elevation | :R0: | Transmit Power | 12 dBm |
| MPTCP | OLIA/BALIA | file size | small/bulk |
| MCS | EDMG SC | EDMG OFDM |
|---|---|---|
| Maximum TCP Throughput | 28.96 Gbps | 30.95 Gbps |
| Mobility TCP Throughput | 9.6 Gbps | 9.25 Gbps |
| Mobility MPTCP Throughput | 16.36 Gbps | 16.15 Gbps |
| Maximum MPTCP Throughput | 41.32 Gbps | 42.13 Gbps |
| Mobility LD-MPSP Throughput | 37.16 Gbps | 36.95 Gbps |
| Maximum LD-MPSP Throughput | 56.20 Gbps | 61.01 Gbps |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pokhrel, S.R.; Mandjes, M. Internet of Drones: Improving Multipath TCP over WiFi with Federated Multi-Armed Bandits for Limitless Connectivity. Drones 2023, 7, 30. https://doi.org/10.3390/drones7010030
Pokhrel SR, Mandjes M. Internet of Drones: Improving Multipath TCP over WiFi with Federated Multi-Armed Bandits for Limitless Connectivity. Drones. 2023; 7(1):30. https://doi.org/10.3390/drones7010030
Chicago/Turabian StylePokhrel, Shiva Raj, and Michel Mandjes. 2023. "Internet of Drones: Improving Multipath TCP over WiFi with Federated Multi-Armed Bandits for Limitless Connectivity" Drones 7, no. 1: 30. https://doi.org/10.3390/drones7010030
APA StylePokhrel, S. R., & Mandjes, M. (2023). Internet of Drones: Improving Multipath TCP over WiFi with Federated Multi-Armed Bandits for Limitless Connectivity. Drones, 7(1), 30. https://doi.org/10.3390/drones7010030







