1. Introduction
Quadrotors have been a topic of particular interest in recent years. They have been widely used in military, industry, and disaster rescuing, owing to their low cost, small size, and autonomous navigation capabilities. Compared with a single quadrotor, a swarm with distributed multi-agent systems can provide better robustness. To establish a well-performed swarm, the distributed consensus is a basic but crucial problem.
Distributed consensus has been widely discussed for a long time. Many works have been conducted on both the consensus itself and the application of distributed consensus. Ref. [
1] provides a new algorithm that deals with link failures and channel noise. Ref. [
2] discusses the topic of filtering in sensor networks. Ref. [
3] provides a new time-discrete algorithm for wireless sensor networks. Refs. [
4,
5] investigate the consensus problem for second-order multi-agent systems. In addition, Ref. [
6] proposes a relative position measurement method to reach consensus. Ref. [
7] discusses the convergent speed of consensus.
However, many of these Algorithms mentioned above are based on the assumption that all agents are legitimate ones, but they are vulnerable when there are malfunctional agents occur in the system discussed in Refs. [
8,
9,
10], which leads to the problem of resilient consensus. Resilient consensus refers to consensus in a case, where agents become malfunctional due to either physical faulty or communication failure. As malfunction can be found in many multi-agent systems such as autonomous vehicles, delivery drones, or partners in security and defense as described in Refs. [
11,
12,
13], the resilient consensus has become a very important problem worthy of investigation.
To deal with resilient consensus, many theories and control protocols have been proposed. Ref. [
14] provides a consensus protocol that enables a system of n asynchronous processes, some of them malfunctional, to reach an agreement. This article has improved the t-resilient protocol to t < n/3. Refs. [
9,
15] conclude a basic result that well-behaving agents can always agree upon a parameter if and only if the number of malfunctional agents is less than 1/2 of the network connectivity. Grounded on the previous knowledge, Ref. [
16] proposes a distributed function calculation iterative method to overcome the weakness brought by malfunctional agents. Ref. [
15] focus on local strategies that provide resilience to faults and compromised nodes. Ref. [
17] proposes DP-MSR Algorithm to reach resilient consensus. Refs. [
18,
19] consider trust evaluation applications in consensus protocols. Ref. [
20] has further successfully proved that their protocol is useful even if t = n/2 and it emphasized the interagent trust. However, much of the research is based on the hypothesis that the malfunctional agents will directly broadcast their abnormal behavior to others without detection or observation from others and these consensus protocols are simplified and not suitable for quadrotor systems.
For real quadrotors discussed in this paper, such a hypothesis is not suitable and we need to formulate a method to detect such abnormal behavior of malfunctional quadrotors. Ref. [
21] chooses to utilize visual techniques to detect faulty robots but with a strictly demanding requirement that robots should be within close range, typically 50 cm. To overcome this limitation, Ref. [
22] focuses on the expected behavior of other agents offline to predict other’s possible failure. However, if the other robot faces a sudden fault after broadcasting a health status, it will not be able to react in time. To reach in-time reactions, Ref. [
23] analyzes the coordination data and the signal strength of neighboring agents to detect failure. However, the noise was not taken into consideration. Refs. [
24,
25] eliminate noise and detect failure using the PCA-EWMA method, but may lose features in data or lead to misleading indications by increasing false alarms and missed detections, and yet they might not perform well in time response situations. Therefore, Therefore, this article mainly deals with the sudden and severe situations that one quadrotor may encounter such as collisions with obstacles in
Section 5.2, which could possibly lead to sensor failure or even system failure. In addition, the possible malicious attacks [
20] may also be taken into our consideration. Under these situations, we need a novel method that based on trust evaluations between quadrotors in order to improve the robustness of the whole swarm system.
Therefore, motivated by existing research [
20], our work extends the trust value evaluation method to an online adaptive controller which is designed for multiple quadrotors systems. Specifically, each quadrotor in the swarm will monitor its nearby quadrotors. Based on the collected information, a trust value is assigned to each connected nearby quadrotor depending on whether the latter is within or out of the established tolerance, and therefore, the trust matrix is formed as trust evaluations for the whole swarm system. On this basis, an adaptive controller will adjust the weight according to the trust matrix. Finally, simulations are performed to verify the feasibility and expandability of our proposed method.
The main contributions of this work are of three aspects: (1) Based on the proposed trust value evaluation method, legitimate quadrotors are able to identify the malfunctional quadrotor. (2) Based on the proposed trust value evaluation method and the adaptive consensus protocol, legitimate quadrotors are able to converge to the correct position and maintain velocity consensus in the presence of malfunctional quadrotors. (3) Based on the proposed trust value evaluation method, the swarm system can outperform the single-quadrotor detecting method in terms of robustness and accuracy.
This article is addressed as the following: in
Section 1, we introduce the background of consensus and related works; in
Section 1, we introduce the model and consensus protocol we use; in
Section 3, we analyze the properties of our adaptive consensus protocols; in
Section 4, we briefly illustrate a simple 2-D plane simulation utilizing the method we proposed in
Section 2; in
Section 5, we discuss multiple quadrotors system in realistic situations.
Section 6 concludes the paper.
2. Problem Description
We consider the problem of trust evaluations for the swarm system consensus protocol, where malfunctional quadrotors exist. We firstly establish a general mathmatic frame [
18,
19,
20] to describe the problem. The quadrotors in the system communicate with each other over a network, which in this case, is represented by an undirected graph
, where
indicates the set of node indices for agents and
indicates the set of undirected edges in this graph. We use
to denote the edge connecting quadrotors
i and
j. Since it’s an undirected graph, once quadrotor
i views quadrotor
j as its neighbor,
j also recognizes
i as its neighbor. Therefore, we donate the neighbors of
i as a set
. With the graph
, we introduce the trust matrix
and we associate time-varying trust values
, which captures the value of trust
i to
j, in another word, to which extent, quadrotor
i views quadrotor
j as a legitimate quadrotor. Additionally, the matrix
need not be symmetric. We next define
as a time-varying weight matrix and use
to donate the
entry of the weight matrix, which can be later derived from the trust matrix
. Note that
must have nonnegative entries, and will have positive entry
only if quadrotor
i and
j are connected and
i views
j as a trusted neighbor. We consider the case where a subset of nodes with indices denoted by the set
,
∈
V, is either
malicious or
malfunctional and, thus, does not reliably follow the order in the consensus protocol. The set
is assumed to be unknown, with cardinality |
|. At the same time, a quadrotor that is not malicious or malfunctional is termed
legitimate, and the set of legitimate quadrotors is denoted
,
, with cardinality |
|.
In what follows, we use to denote the zero matrix, where the dimension of is to be understood from the context. A nonnegative matrix is row-stochastic if the sum of its entries in every row is equal to 1, and it is row-substochastic if the sum of its entries in every row is equal to or less than 1. We use to denote the vector with all entries equal to 1. Given a vector , we use or (when has a subscript) to denote its ith entry. A similar notation is used for the entries of a matrix.
2.1. Model
We are concerned with the problem of consensus in a two-dimensional XY-plane, where each legitimate quadrotor updates its value by the following general and widely-used equations for all time
t:
where
represents the position of quadrotors at time
t,
indicates the velocity of quadrotors at time
t and
stands for the acceleration of quadrotors at time
t, which is the control input in the simulation and swarm system discussed later as well. All three symbols mentioned above are n-dimensional vectors, in which n represents the number of quadrotors discussed in this article. Remark that for the 2D-plane distributed system that will be discussed later in this article, we assume that each quadrotor will maintain its own attitude. Therefore, we only need to separate the vector into two directions
X and
Y.
Besides, for the
mentioned above. We choose the following equations [
26] as the consensus protocol:
where
comes from
,
. We donate the
as the original weight matrix that contains the initial weights of every quadrotor to their neighbors.
,
and
are user-defined parameters, which illustrate the control gain. Unlike Refs. [
18,
20], the consensus protocol we choose here is a more typical and more general second-order consensus protocol and suitable for swarm systems discussed in this paper.
Definition 1 (Malfunctional quadrotors:). Quadrotor i is said to be malfunctional if it does not follow the consensus protocol rule in to update its value after some time t. To be more specific, we refer Malfunctional quadrotors to those which may deviate from the original calculated route whether resulting from communication failure, collision or hardware fault.
Let ∈ denote the vector of values ∈ R for all the quadrotors at time t.
Without loss of generality, we assume that the quadrotor indices are ordered in such a way that the vector
can be separated into two components: the first part of representing the legitimate quadrotors’ values
, the second part of the component representing the malfunctional quadrotors’ values
. In this way, the consensus dynamics become the following forms:
In addition,
and
are defined as follows:
where
is the matrix multiplying the state component corresponding to the legitimate quadrotors’ values, and
is the matrix multiplying the state component corresponding to the malfunctional quadrotors’ values.
is defined as the identity matrix. The symbol ⊗ represents the Kronecker multiplication.
and
are the specific area of the Laplacian matrix of graph G. The matrices
and
dictate the dynamics of the malfunctional quadrotors’ values, which will not be necessary to give specific formulas.
Definition 2 (Trust evaluation :). For every and , the parameter represents to which extent the quadrotor i views quadrotor j as a trustworthy neighbor at a certain time t.
We assume the availability of such observations (t) throughout this article. In the next section, we will discuss how to determine through quadrotors’ communication systems.
In this article, we assume that indicates quadrotor j is temporarily regarded as a trusted(legitimate) neighbor by quadrotor i at time t and vice versa. Note that = 0 means at time t, quadrotor j’s role is ambiguous to quadrotor i, which will not play a role in the iteration Equations (3) and (6).
Our ultimate goal is to reach convergence under the influence of malfunctions and design available observations of trust. Toward this target, our first priority is to decide which information should be sent through networks. By and , we need the location of quadrotor i and the location of at time t to determine the velocity and the expected location at time . In addition, for the determination of , we need the predicted speed of quadrotor i and the location of at the time t.
2.2. Noise
When it comes to the real system, whether we use drones or vehicles, there must be unmodeled factors such as friction, magnetic field, and data lagging, which may lead to the deviation between the actual movement and the computational one. Therefore, we set up noise equations that simulate the real environment as follows:
where
indicates the instability of location caused by noise.
is an arbitrary variable that has uniform distribution with a certain interval that the user can set up. In addition,
is also a user-decided parameter that reduces or enlarges the influence of noise depending on the requirement of the real system. For simplicity, we assume that for both directions of every quadrotor, the parameter is the same
. In addition, the second term is the basic wind disturbances, where
C is the air drag coefficient,
is the density of air and
S is the windward area. Noise is important in this article as it gives a hint on how to determine the trust matrix. In addition, we include the term in the later simulations to serve as disturbances that the swarm system could possibly encounter in reality.
When taking noise into consideration, the iteration Formulas
and
evolve into the following modified equations:
where
stands for the actuals position of quadrotors at time
t.
2.3. The Trust Matrix and the Weight Matrix
In this subsection, firstly, we will discuss the methods to determine the trust matrix, which is obtained from the communication of quadrotors. After that, we directly derive the weight matrix.
Let
be the difference between the distance of quadrotor
i and
j and that after iteration (1) and (6) has been conducted, which can be written as:
See that the computed
and the actual movement
, are directly obtained by computing the following equations:
So we consider the trust matrix entry
of
as follows:
where
is a trust value changing constant and, the equation represents the overall trust of
i to
j considering the information gathered from
to
. In addition,
indicates the tolerance of error that will affect trust values. The equation provides some tolerance for a quadrotor to judge its neighbor. It will not simply classify a neighboring quadrotor as a legitimate or a malfunctional one based on one prediction as the trust value must go below zero to change its neighbor’s status from legitimate to malfunctional. It views the overall performance of its neighbors so as to resist certain extent of false prediction that the disturbances may generate in the process.
We now define a time-dependent trusted neighborhood for each quadrotor
i as
. This is the set of neighbors that legitimate quadrotor
i identifies as its legitimate neighbors at time
. Denote
for all
where,
>0 can be thought of as a parameter limiting the maximum influence that the neighbors of quadrotor
i are allowed to have on quadrotor
i’s update values (i.e., a value of
approaching infinity would preclude neighbors from influencing quadrotor
i’s updated values). Using these quantities, we define the weight matrix
by choosing its entries
as follows: for every
, we have
In this case, we do not consider the difference of weight between cooperative ones for simplicity, which might be improved in the future.
3. Analysis
Proposition 1. There exists a finite time instant such that for all almost surely when and β are chosen properly.
Proof. Let
, then by Chernoff-Hoeffding Inequality [
27] TH1.1, we have the following:
where
,
. By the linearity of the expectation, we have
. In addition,
can be illustrated by the following equations:
for every
and every
,
.
for every
and every
,
.
The two equations above indicate to which extent the M reaches to as time t increases. In other words, when we choose proper and , that M in (14) reaches for every , and reaches for every , occurs at a finite time almost surely by Borel–Cantelli Lemma. Thus, there exists a (random) finite time such that for all almost surely. □
In addition, we will give out an explicit example in the next section to prove there is such proper and .
Next, we will state the convergence of legitimate agents’ values. In particular, we use the decomposition of the legitimate quadrotor states [see(4)] to formulate the following propositions.
Lemma 1 ([
26,
28]).
Let , be the max eigenvalue of graph , then under the following conditions:The matrix in (6) is a stochastic matrix.
Proposition 2 (Convergence of legitimate quadrotors’ values).
Let be the vector of the initial value of legitimate agents. We have the following equations: Proof. By Proposition 1, there exists a finite time instant
such that
for all
almost surely. Thus, by Lemma 1 there exists a finite time instant
such that
directly from the definition in (6). In addition, by Perron–Frobenius theorem, we have
where
v is a a stochastic column vector.
Therefore, we have the following equations:
where
is a specific finite vector. Thus, Proposition 2 has been proved. □
Proposition 3 (Convergence of malfunctional quadrotors’ values).
Consider defined byThen, the entries of this vector are all the same almost surely.
Proof. By Proposition 1 and Lemma 1, this imply and for all almost surely.
Therefore, we have the following equations:
for some finite
, indicating that all the coordinates of the vector
are identical almost surely. □
By the result of Propositions 2 and 3, we directly get the following result.
Proposition 4. There exists, almost surely, a random variable that the consensus algorithm converges almost surely, Proof. The result is directly obtained from Propositions 2 and 3 and the statement that . □
4. MATLAB Simulation
In this section, we evaluate the performance of convergence of legitimate quadrotors through MATLAB. For simplicity, we set the graph as a fully connected graph, and consider a system with 30 quadrotors among which there are 15 malfunctional ones. The initial location X, Y of each quadrotor is randomly chosen and the malfunctional quadrotors are also randomly chosen in order to guarantee generality. In addition, we consider the two most common cases in that the malfunctional quadrotors cannot move or in a circular movement.
4.1. Static Situation
In the first case, we discuss the situation where malfunctional quadrotors are set as static ones, which means they will remain in their initial locations and hover during the whole simulation as if they fail to take off. We set , the X and Y noise , tolerance () = 0.05, and we set the least trusted limitation . Besides, we set to fulfill the requirement of convergence theory.
We demonstrate the following 2D-time results and properties:
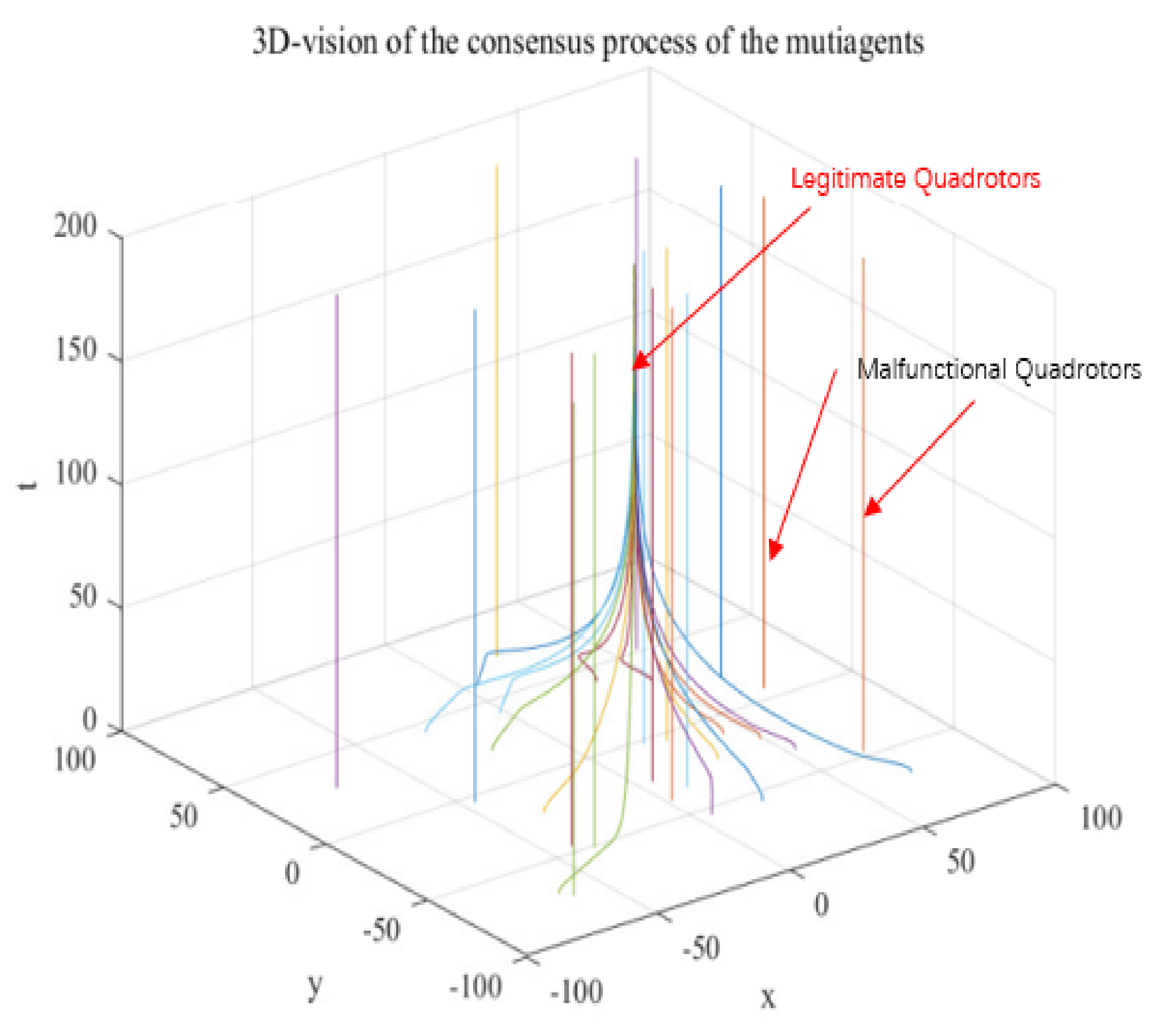
Figure 1 demonstrates the
movement with the time of all the quadrotors in the swarm system. As mentioned in the previous conditions, the malfunctional agents won’t move so it remains in their initial positions. The legitimate ones successfully reach their consensus.
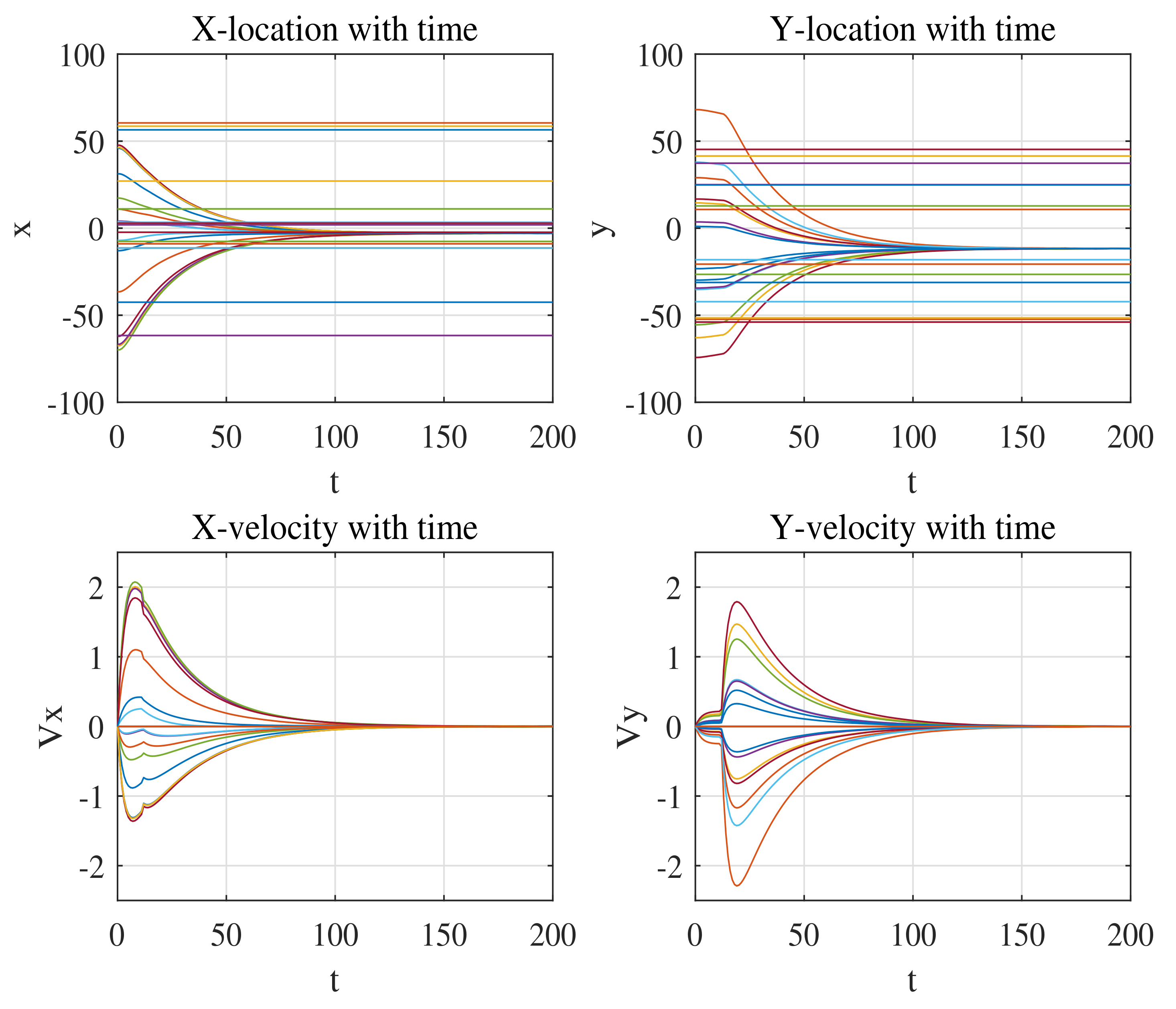
Figure 2 demonstrates the velocity and location of agents with time. As can be seen, the
X and
Y position converges and their velocities reach zero in the end, which fulfills the consensus requirement.
4.2. Movement Situation
In the second case, we discuss the situation where malfunctional quadrotors are set as moving ones, they will start a circular movement with radius and the center is located at . We set , the noise , tolerance () = 0.05. In addition, we design . .
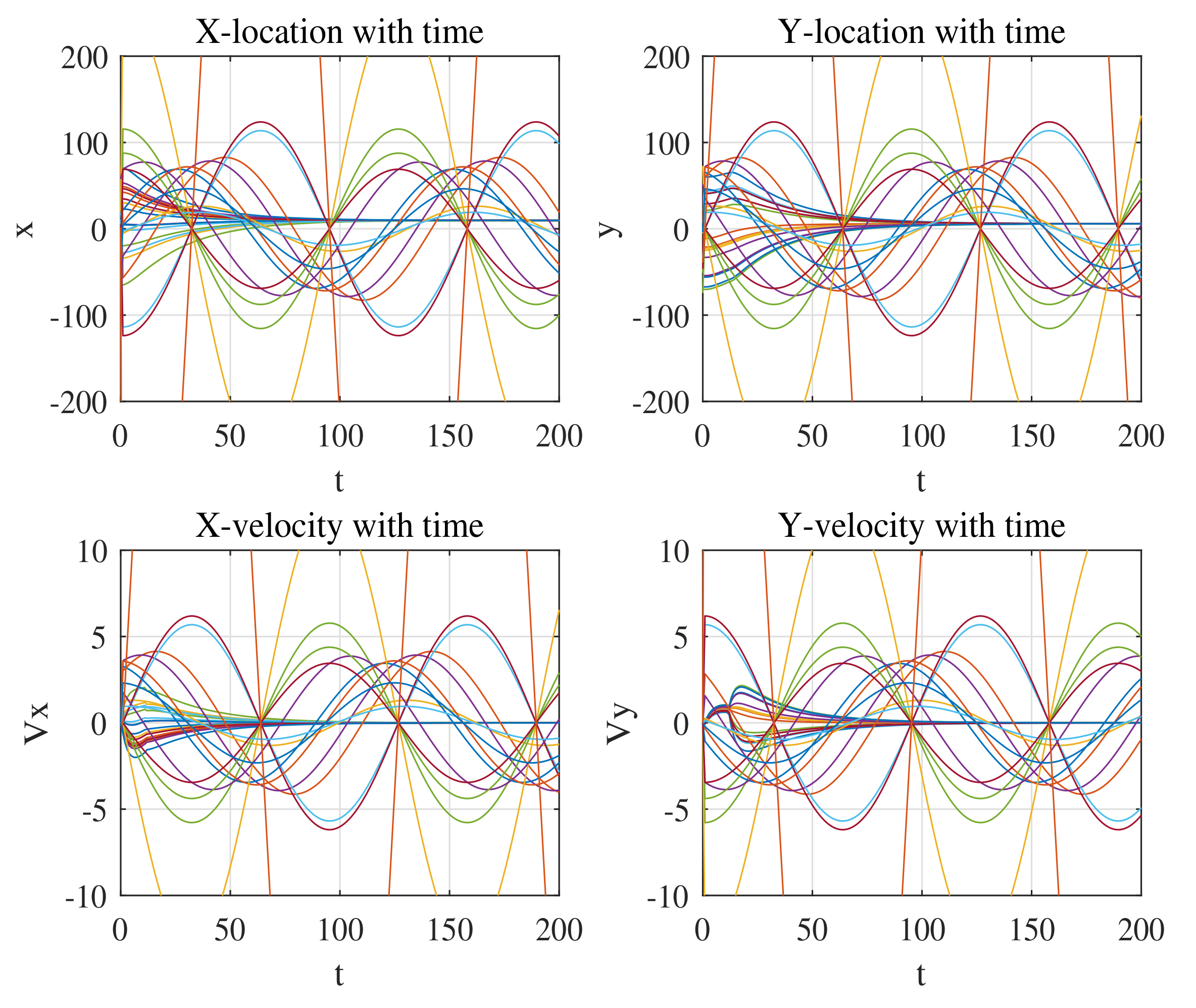
Figure 3 and
Figure 4 demonstrate the situation that the malfunctional quadrotors rotate around the origin with the radius of their original distance with it. It’s clearly showed on the graph that the actual trajectory of each quadrotor and their correspondent speeds and positions. Judging from the graphs, we conclude that even if the malfunctional ones are moving in circles, it will not affect the consensus of the legitimate ones, and they will converge to their center, which proves the robustness of our method.
5. Gazebo Simulation
In this section, we apply our theory to the quadrotor swarm in Gazebo. We consider the four-quadrotor-situation where one of them is out of control. In the first case, the malfunctional quadrotor will hover at the original place after taking off, and in the second case will hit the obstacles. We firstly provide a pseudocode of our proposed scheme (Algorithm 1).
| Algorithm 1 online adapative controller weight |
-
Input:
Initial location of each quadrotor -
Output:
Next-step Trust and Weight - 1:
functionTrustevaluation() - 2:
while not reach consensus do - 3:
if Quadrotor j fall within the tolerance of predicted location then - 4:
else - 5:
end if - 6:
if - 7:
then - 8:
end if - 9:
end while - 10:
end function
|
Each quadrotor will examine its relationship with its neighbours utilizing the above algorithm at each step, which means that they will online adapt the weight asigned to each other in the proposed protocol. As result, they will be able to distinguish the malfunctional quadrotors and eliminate their impacts on the whole robotic system.
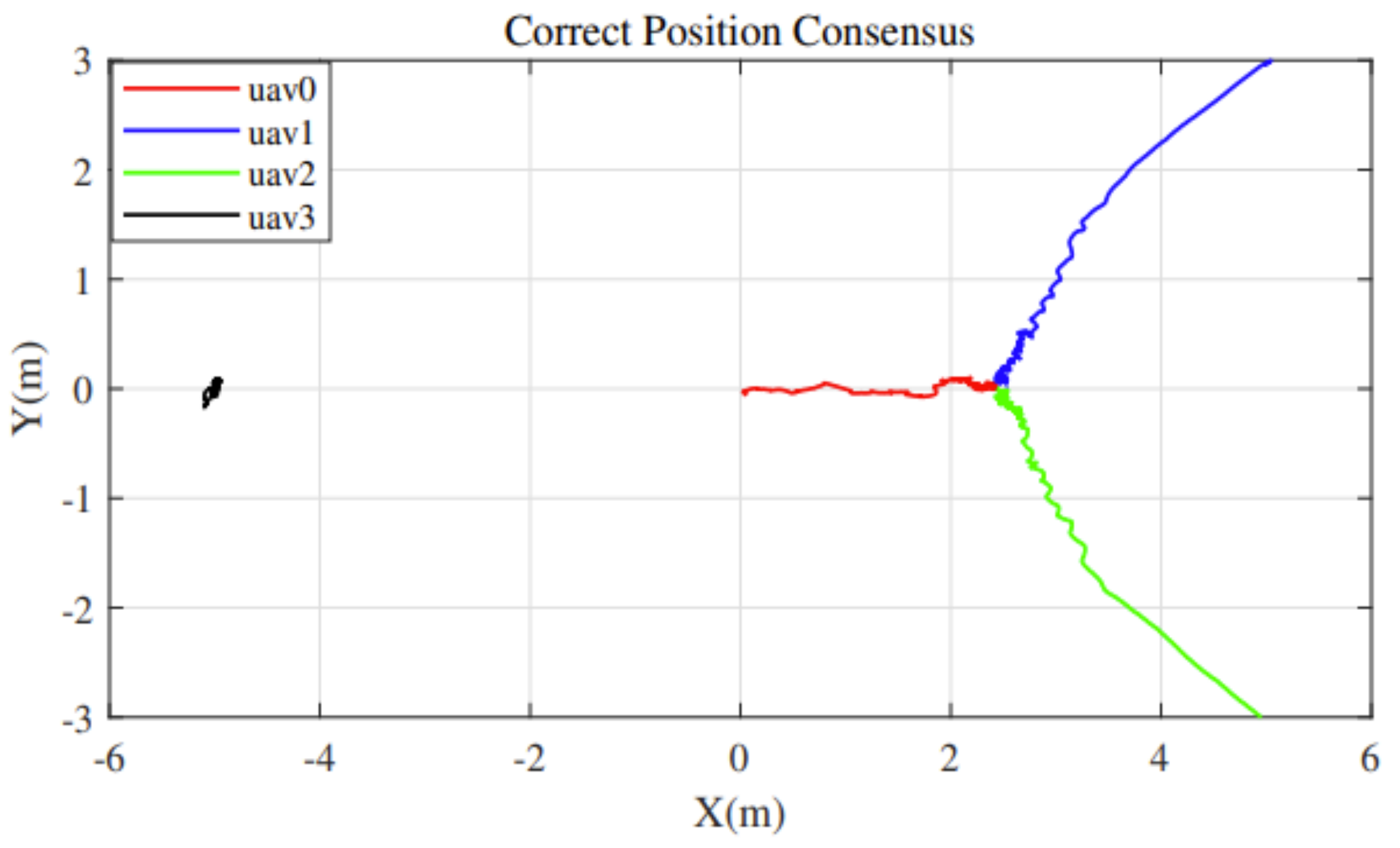
5.1. Position Consensus
In this subsection, we consider the case where one of the four quadrotors hovers at the original place during the experiment. The location of the four quadrotors are
separately as shown in
Figure 5. The quadrotor at
is designed as the malfunctional one. The four quadrotors are set in offboard mode and act upon our consensus protocol after they reach different heights in order to avoid
Z-direction collision.
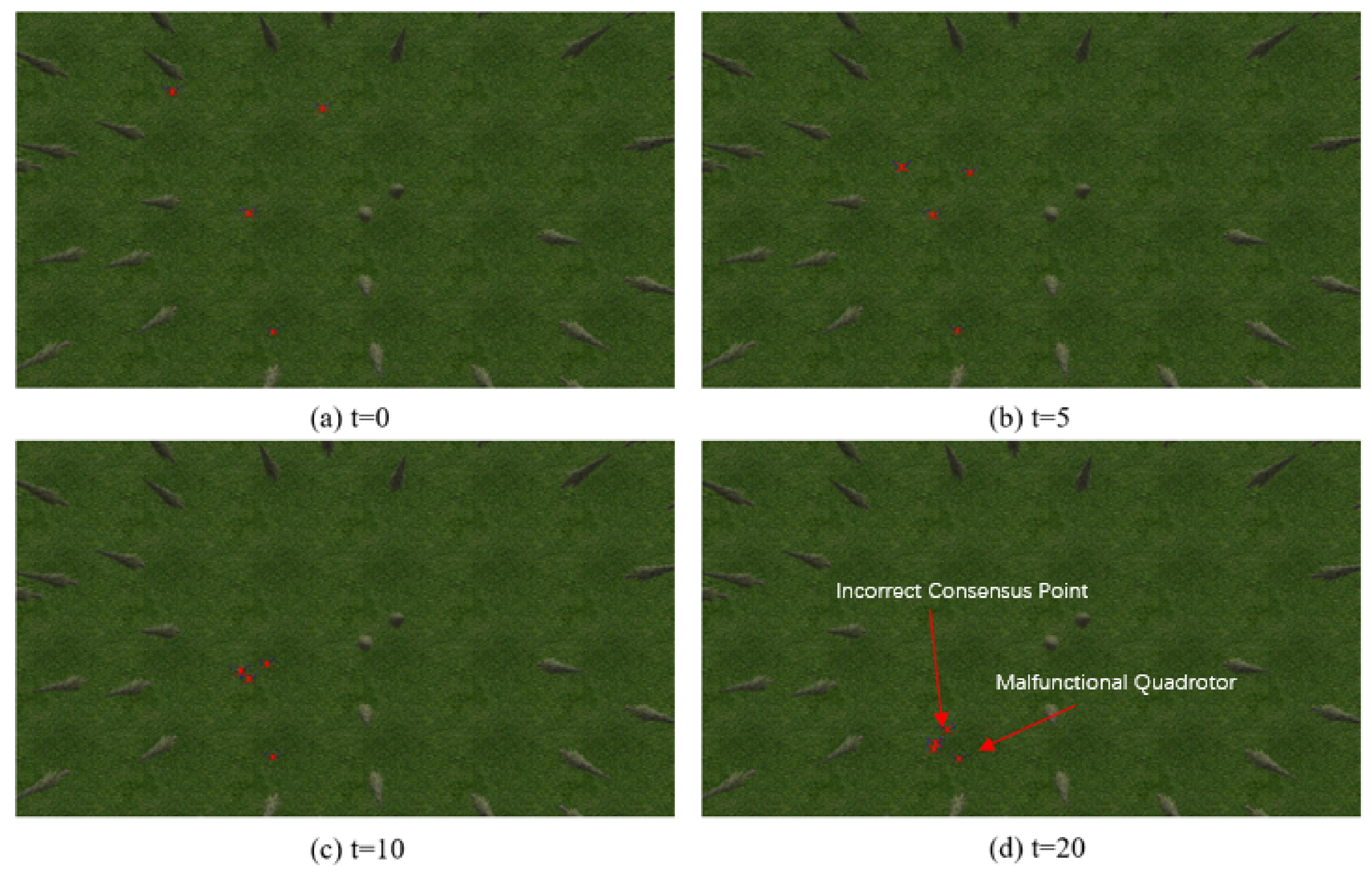
In the
Figure 6, we present the actual movement of the four quadrotors with time under the adaptive consensus protocol. As the malfunctional quadrotor will hover at its original place after it takes off, its trust value will continue going down because its location prediction doesn’t match with its movement. The legitimate quadrotors are able to identify the malfunctional one to eliminate its effect on the whole swarm system by setting its weight to zero in the consensus protocol. Eventually, the legitimate quadrotors reach their center nearly at
.
We next present the actual trajectory of the four quadrotors under the proposed protocol through the rosbag record in
Figure 7. The black one which was designed as a malfunctional one will hover at the original place. In addition, the other three will reach their center, not affected by the malfunctional one which in this case is UAV3.
We next present the comparison test. We use the normal consensus protocol that each quadrotor assigns the same weight to its connected neighbors and they will not change weight during the experiment.
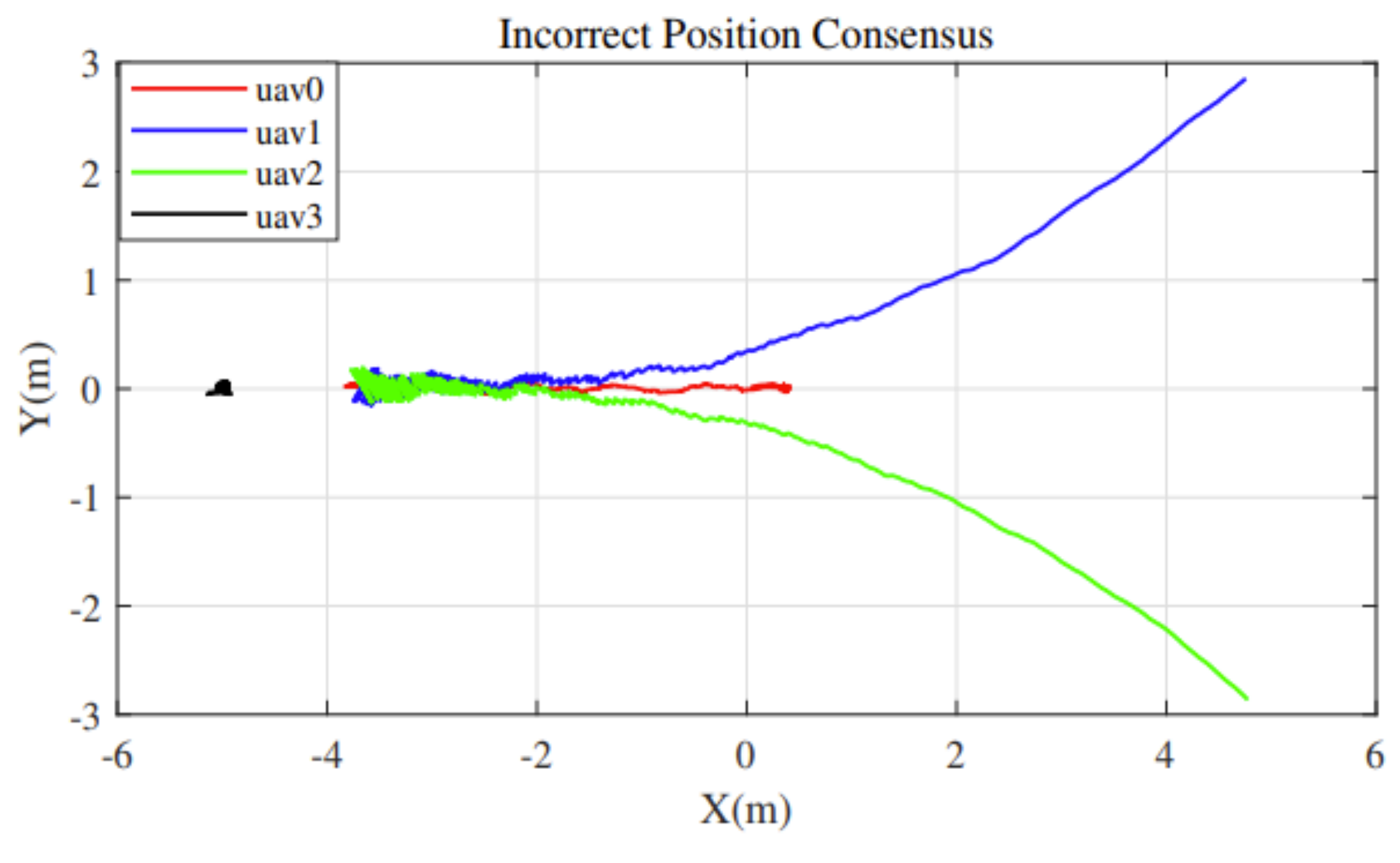
We can see from the
Figure 8 that if the presence of the malfunctional quadrotor is not taken into consideration or the swarm system fail to identify the malfunctional one. The remaining three legitimate quadrotors will be severely affected as they mistakenly classify the malfunctional quadrotor as a trustworthy one. As the weight of the malfunctional quadrotors is not zero, others will try to reach consensus with it, leading to deviation. However, the swarm system will gradually fly towards
, exactly the place where the malfunctional one is hovering.
We also present the actual trajectory of the four quadrotors under normal consensus protocol through the rosbag record.
Figure 9 clearly shows that with the malfunctional quadrotor UAV3 hovering at
, the remaining three legitimate quadrotors drift to UAV3’s location, indicating the severe consequence the misclassification brings about.
Notice that UAV0 whose original location is will first move forward due to two quadrotors locating ahead of it, and then drift backward to the malfunctional UAV3.
Compared with the actual movement under adaptive consensus, in which the true consensus point should be near the center of the three legitimate quadrotors’ original spawn location, that is , the normal consensus leads to severe deviation.
In this case, our protocol gives out only a relative error at X-location, which is quite acceptable when considering a physical swarm system. While the comparison test gives out a relative error of , which is unacceptable. This numerically demonstrates the improvement of our method.
5.2. Velocity Consensus
In this section, we extend our theory to velocity consensus and a more typical case will be discussed. We consider a four quadrotors swarm system that tries to fly through a forest while maintaining velocity consensus, and unfortunately, one of the quadrotors hit the tree and is trapped on the branches. Based on the same adaptive consensus protocol, we redesign the trust value and update the trust matrix based on the new function.
We list out the new trust design as the following equation:
Notice that the trust function is designed specifically for our experiment. When the malfunctional occurs, i.e., the quadrotor hit the obstacle, the movement of it per second will be very close to zeros, and when we place the measurement in the denominator, the reciprocal will be very large. As result, it can tell the difference between those which are still functioning and the one which hit the trees. Besides, the extra value is specialized for the situation when the movement is zero. And with its strong relation with , the greater the will lead to a faster descent in trust value, guaranteeing the quick response to the collision.
We provide the result by MATLAB and GAZEBO separately. In addition, the UAV3 is designed as the one will hit trees after flying for a while:
We set the swarm flying along the X-direction and maintain a lozenge formation. Y-direction velocity and position are not considered in the simulation. We can observe from the
Figure 10 that with the unexpected malfunction at
, the X-velocity of UAV3 will become zero and resulting in the velocity decrease of the other three legitimate quadrotors. With our proposed trust values based consensus protocol, the remaining three are able to identify the malfunctional quadrotors, restore their velocity and reach velocity consensus.
We next present the GAZEBO simulation to illustrate a more realistic case.
As can be seen from the graphics, at
, UAV3 hit the trees and fell to the ground. The three legitimate quadrotors would slow down as they were lowering the trust values, but eventually, they identified the malfunctional quadrotor and disconnected from it. As result, they were able to continue their flying and maintained their consensus, even if the fourth one hit the tree and stopped moving, which indicates the effectiveness of our proposed method (
Figure 11).
6. Conclusions
This work considers the problem of quadrotor swarm consensus in the presence of malfunctional quadrotors. Specifically, we propose a consensus protocol based on the trust value evaluation of each quadrotor’s neighboring quadrotors. We show that with the proper trust value design and the proposed consensus protocol:
(1) Correct classification of malfunctional and legitimate quadrotors can be achieved. The legitimate quadrotors can avoid potential risks by eliminating the effect of the malfunctional quadrotor.
(2) Almost sure that the remaining legitimate quadrotors are able to reach convergence even when malfunctional quadrotors occur.
(3) The deviation of the converged limit is much more improved than the one with a simple protocol not taking trust into consideration, which is acceptable and can be applied in physical swarms system.
Additionally, we show that our performance can be applied to a wide range of situations, such as velocity consensus, with different designed trust values and will guarantee more accuracy with more information observed. Taken together, these results point to the inherent value of quantifying and exploiting trust between quadrotors for consensus. Furthermore, with the theoretical derivations and mathematical proofs to guarantee the feasibility of our method and the certain noises to simulate the possible disturbance in reality, we believe that the tests in reality which we are currently working on will still be promising, such as the simulations as they have much in similarity such as gravity, collisions and sensors. All in all, we believe that the proposed method and framework of this article hold promise for a wide range of different purpose swarm systems.