1. Introduction
According to [
1], there have been dramatic advancements in the drone industry, and it is estimated that the market will reach nearly USD 60 billion by 2025. Moreover, it is predicted that shipments of consumer drones will grow to USD 29 million by 2021. Additionally, the increased demand for drones in the public and private sectors is predicted to be worth around USD 100 billion in the future. To put it in perspective, in 2020, consumer drones in the United Stated sales were over USD 1.25 billion [
1].
On the other hand, 367 illegal activities were reported between October 2020 and December 2020 in the USA alone by the Federal Aviation Administration (FAA) [
2]. Considering that the reported number is only what was reported by the FAA, it is safe to assume that the number is much greater than noted. As there are many types of drones that are involved in many of the incidents, the FAA has reported that they are working closely with law enforcement to investigate and identify these incidents [
2].
Previous research has looked into multiple variations of DJI drones (e.g., DJI Phantom series and Spark) as well as some other well known manufacturers. The studies were comprehensive and provided a body of knowledge with an adequate amount of relevant content, which contributed to the unmanned aerial vehicle (UAV) forensic community. However, there was a lack of literature supporting drones weighing less than 250 g (e.g., DJI Mini 2).
Our research aims to address the lack of comprehensive forensics methods on the DJI Mini 2 drone and its necessary operational software and controllers by performing extensive experiments with multiple criminal-like scenarios. Additionally, our conducted experiments consist of related mobile software (e.g., DJI Fly app) used to operate the drone, which is populated and then forensically analyzed.
The contributions of this research are as follows:
Providing a comprehensive forensic investigation across multiple devices (e.g., drone body, SD cards, and mobile devices) associated with the drone.
Analyze several criminal-like scenarios for the DJI Mini 2 drone in the real world, utilizing multiple devices.
Testing the carrying capabilities of the DJI Mini 2 to evaluate its transporting performance for criminal activities, such as terrorist attacks and smuggling.
This paper is structured as follows:
Section 2 discusses other researches and work that have already been done in the field of UAV/drone forensics.
Section 3 demonstrates our methodology and the experiment design that was followed throughout the study.
Section 4 highlights our findings, while
Section 5 presents the discussion on the importance of our results. Finally,
Section 6 concludes this research and provides direction for future work.
2. Related Work
As highlighted in [
3], an ever-growing concern regarding UAVs would be the easy confiscation or loss of technology, as seen by drones being confiscated and thus privacy violations occurring due to the extraction of data from the device. Drones have been used as a mode of recreation, but there are many uses that companies and governments have found. Just as UAVs have the capability for good, such as collecting information to be used as evidence in lawsuits, they are easily used for malicious purposes, such as violating no-fly zones, illegal usage by criminals, or launch of areal missiles [
3]. At the conclusion, the researchers were able to access the data on the Parrot AR Drone 2.0 used in their study and access the file system via multiple connection methods. This resulted in retrieving the controller’s phone ID [
3]. Based on the results shown in the paper, it was proposed to take the Parrot AR Drone 2.0 and other drones and analyze further to extrapolate the differences in the accessibility of data.
Moreover, researchers in [
4] experimented using a DJI Spark drone in a criminal-like scenario while it is being controlled and linked to a mobile device. In this study, the mobile device utilized by the researchers was Android OS-operated, and they used DJI GO 4 application (app) v4.3.11, which was downloaded from the Android Play Store to control the drone. They found that the mobile device kept the flight data files under two recorded versions; the first is
.DAT, and the other is in
.txt files. Both formats along with media files taken during the flight were preserved under the DJI GO 4 package folder named
DJI/dji.go.v4. They also were able to find a connection between all components they used for the study, including the drone, SD card, and smartphone, using temporal rules to determine their linkage [
4].
Another recent study [
5] has demonstrated a comprehensive forensic study on DJI Mavic Air 2, utilizing multiple devices and case scenarios in which the last was a crash landing. Researchers have dealt with the damaged drone and performed digital acquisition from different components that were used in the case study (e.g., smartphone, laptop, and drone body). In addition, the researchers took into consideration two possible acquisition methodologies, the first being chip-off and the second being chip-on techniques. As a result, they were able to discover a board serial number that is treated as Personal Identifiable Information (PII), which can be linked to the drone owner/operator [
5].
Security issues continue to rise with the popularity of UAVs, and it is ever necessary for investigators to be able to forensically analyze devices used for malicious purposes [
6]. As presented in [
6], one of the primary obstacles comes from the complex and individualized structure of the drone when performing forensics analysis. One proposed solution to the challenge was creating a framework that could aid forensics investigators by providing twelve steps of systematic analysis [
6]. During the creation of the framework, five different models from multiple manufacturers were utilized. Once created, the researchers tested their proposed framework and found that it could be used for each model in the study to aid in an investigation.
In addition, researchers of [
7] have highlighted some UAV forensic challenges that are associated with the tools and guidelines/frameworks used by investigators. To tackle some of the challenges they discussed, they have proposed a process that consists of 20 steps while demonstrating it using DJI Phantom 3 as a case study. Moreover, the proposed framework integrates the probability that the UAV is used in an illegal operation, whereas researchers of [
8] have a proposed drone technical forensic investigation process that can be used in some cases. The authors have demonstrated the proposed investigation process using a Yuneec Typhoon H drone.
A recent study [
9] that further explains the analysis of drones is known as the Drone Forensics discipline. This discipline is necessary due to the need for specialized tools and analysis as drones have many enhancements that create barriers during digital forensic analysis. Information can be lost if the examiners are not properly educated or equipped. The study [
9] focused only on one manufacturer (DJI) but utilized various models to test and compare forensics tools. The methodology behind the approach was to discover which standards and procedures are best used in an investigation with DJI drones [
9]. Tools of analysis were limited to Autopsy, Paraben’s E3: Universal, and CsvView/Datcon. Despite the paper utilizing two web tools for additional data extraction at the end, it was not recommended due to the vulnerabilities and lack of reliability. It was found that file systems in different models of DJI drones contain the same standards for media files, EXIF data, spatial movement, metadata, and location [
9].
Another very recent study [
10] conducted on common drone models utilized in criminal activities demonstrates what information could be gathered to better inform a law enforcement investigation. From the six brands, investigators gathered such information as media files in the form of pictures and videos, flight patterns, locations, and owner identifications. This study continued to indicate the use of drones autonomously or by an operator. This information can dictate the form of data gathered. Illegal activities via drone use come in many forms, such as drug drops over foreign borders, contraband drops over prison fences, and unsolicited surveillance. The scenario provided in the study is based upon the before-mentioned instances of illegal use of drones and law enforcement, engaging forensic analysis to determine such information as ownership and link to crime [
10]. The study maintains that state and federal legislation has not managed to regulate drone technology and thus leaves most stakeholders vulnerable. In the end, it was concluded that due to the lack of a universal drone structure or forensic tools, continued research must be completed to determine the method of data extraction. Lastly, the researchers left more invasive methods, such as chip-off, as a last resort due to the possibility of damage.
Yousef and Iqbal [
11] used the DJI Mavic Air drone and the iPhone 6 mobile device for the basis of the experiment in pursuit of determining examiner procedures, extrapolating files that could be used as court evidence. The researchers denoted limitations regarding their process being applied to various kinds of drones and found a challenge in the duration of time allotted for drone examination. Due to time constraints, they could not find the DJI’s
.DAT and
.txt files that would have provided flight information.
Hamidi et al. [
12] focused primarily on the DJI Phantom 4 Standard drone to determine a specific procedure for analyzing the
.DAT file and extracting data from storage sources that could be used in a criminal case. The study resulted in the researchers finding considerable relevant information, which accomplished this study’s goal, but in conclusion, it was recommended to continue research on other drone types and a greater research emphasis on
.DAT and
.txt file structures based on their complexity [
12].
On the other hand, researchers in [
13] have developed Drone Open source Parser (DROP), which is an open-source parser for DJI Phantom 3 flight logs that are encrypted in the special format of
.DAT files. It takes each of the unreadable
.DAT files format, which represents a flight log, and decrypts them into
.CSV readable format. Moreover, to validate their results, they have compared their tool with the outcome of the decrypted and parsed
.txt using
http://healthydrones.com/ (accessed on 31 May 2021), which is now
https://airdata.com/ (accessed on 31 May 2021). As a result, they found that the decrypted outcome of the DROP tool in a CSV file format is almost identical to the outcome of the flight logs that are decoded and decrypted from the
.txt format. In contrast, researchers of [
14] used DJI Phantom 3 Advanced as a case study to test the ability to recover GPS data as digital evidence using DatCon tool v2.3.0, enabling them to decrypt the
.DAT files recovered from the digital forensic image of the Android smartphone used in the study.
Furthermore, in a recent case study [
15], researchers have assessed and highlighted important differences in the capabilities of widely used UAV forensic software and tools (e.g., Autopsy, Cellebrite, and Datcon). Although they found that the DatCon tool was able to decrypt the
.DAT file and convert it to a readable CSV file format, other tools used in the study have varied results regarding decryption of the
.DAT files even though some were using the DatCon module. The study highlights the importance of validation and cross-checking results using multiple tools.
Many developments have been integrated into forensics software to detect and acquire drone equipment. For instance, Cellebrite now supports the acquisition of many DJI types (e.g., Inspire 2, Mavic Pro, Mavic Pro 2, Mavic Air, Phantom 3 and 4, and Spark) but not the Mini 2. Despite the efforts and previous research, many questions remain unanswered regarding drone forensics, particularly the new models, such as DJI Mini 2.
3. Methodology
Malicious drone usage can be conducted in many ways, and based on the given scenario, the investigation will differ. This is due to drones varying in manufacturer, technical capabilities, version, and even size. In addition, when it comes to drone investigation techniques during real-life crimes, the drone might not be the only place to look for evidence. Applications used to operate, set up, and even update the drones can supplement and complement the existing evidence found on the device or used as primary evidence if deemed appropriate. This is to aid in finding possible connections between the software and the drone to help future investigations.
3.1. Experiment Design
During real-life crimes, when the digital evidence is involved and the devices are ceased, very rarely, only information populated on those devices will be related to the crime. Filtering through the information presents challenges, especially when it comes to large storage capacities and unknown file structures. For this study, we decided to eliminate unwanted information not related to the case study by controlling the environment as much as our resources allowed us. This ensured that the data populated during the study would be easier to filter through and unwanted cross-contamination from another unrelated action was eliminated, providing comprehensive research from the beginning of the case to the end without any additional steps.
The logic behind the selected devices for the study came from the extensive prior research conducted. The research has shown that these devices are most commonly used, available to the general public without any restrictions or prior requirements, and they are reasonably inexpensive. An additional reason for particularly choosing the DJI Mini 2 drone was the lack of research in the literature and digital forensics investigations. A full list of the devices utilized to create the case study scenarios and conduct the experiment for the research is listed in
Table 1. Moreover, to find valuable information, this study and research followed best practices to acquire and examine the forensic images of the associated devices. For the two smartphones used in this study, we followed the data population and examination guidelines suggested by the National Institute of Standards and Technology (NIST) [
16].
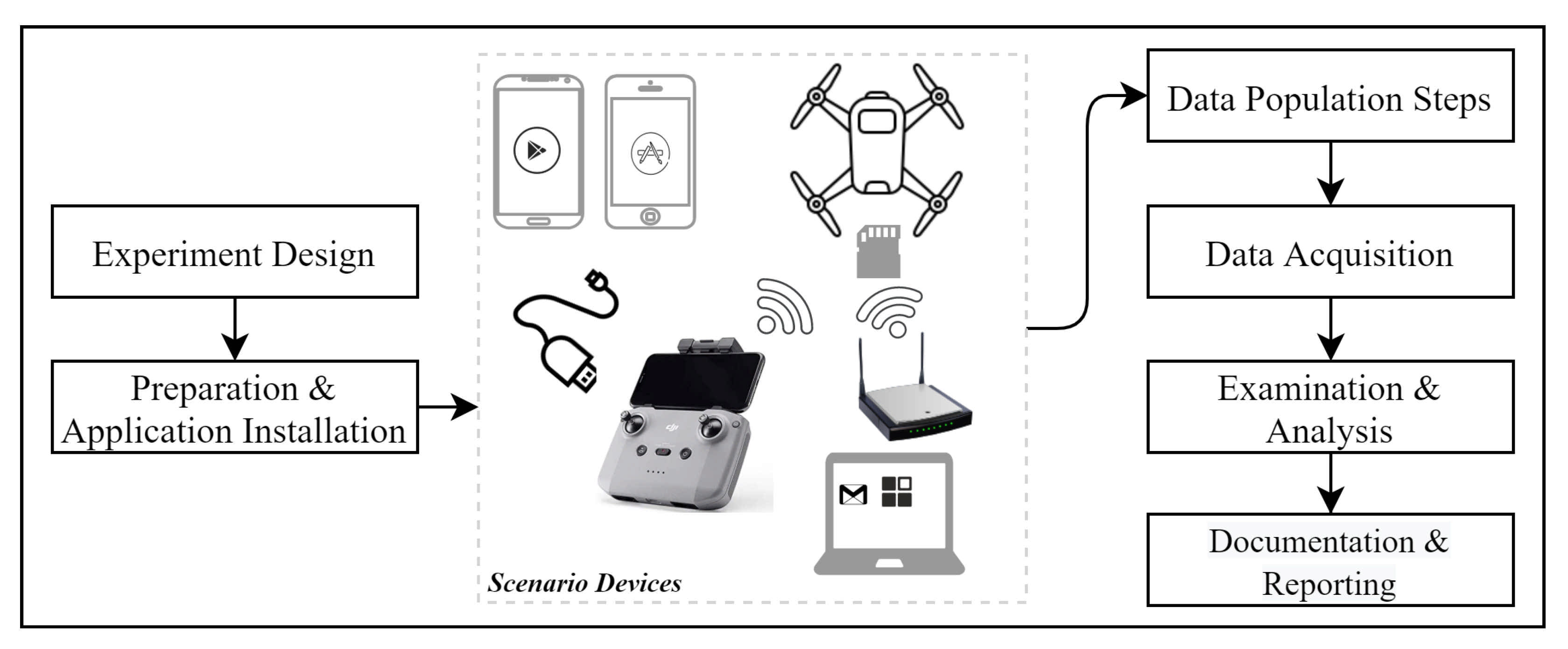
In addition,
Figure 1 shows the complete methodology involving all the processes and components utilized. Each of the phases will be discussed in detail to outline the steps that were taken into consideration.
3.2. Application Installation and Preparation
Prior to working with the mobile phones and the drone, a brand-new WiFi Service Set IDentifier (SSID) was created for the devices to use during the study. Setting up a new wireless network further ensures control of the environment. The device used as a wireless router was a TP-Link (TL-WR1043N v5) with OpenWRT (19.07.5 r11257-5090152ae3). To set up the case study scenario and ensure no previous data were present, SD cards and smartphones were wiped and restored to factory settings. DJI Mini 2 was not susceptible to this process since the drone and its associated remote controller were new and never used previously. Additionally, Google Inc. Gmail service was used as the email provider and a primary account to set up iCloud, Apple Appstore, Google Play Store, and an associated user account for DJI-related applications (apps). Next, the software necessary to operate the drone during the flight (i.e., DJI Fly) was installed on both phones running Android and iOS.
Various digital forensics software tools were used to acquire and analyze the data. In this research, we used resources that included open-source tools (i.e., Autopsy [
17]) that were complemented with proprietary tools such as Magnet AXIOM, and Cellebrite UFED 4PC, which are used worldwide by law enforcement agencies and practitioners [
18,
19]. These tools were also used for cross-validation.
Table 2 lists all tools that are used in all phases of the experiment (i.e., data population, acquisition, and analysis).
3.2.1. iOS Setup
The iOS mobile device used for the study was an iPhone 7 with iOS version 13.3.1. After connecting to the WiFi network we created, we logged into the App Store using a previously activated Gmail account and downloaded the DJI Fly app (Version 1.3.1 (440)). Upon download, we opened the app and followed the default options. The DJI Fly application initially presented a video and then asked for enabling Bluetooth, location, and notification service. We selected “only while using the app”. The next prompt was if we wanted to participate in the DJI product improvement, and we selected “not now”. Lastly, upon logging into the DJI Fly application using the Gmail account, we were notified about geo-zone restrictions and selected “agree”. After the previous process, the app was ready for the connection with the drone.
3.2.2. Android Setup
The Android device used in this study was a rooted Samsung Galaxy s7 running Android 8.0.0. The DJI Fly app had no official version available in the Android Play Store, so v1.3.0 was downloaded as an APK file and then installed on the phone. As a connection to the internet, the phone was connected to the WiFi access point created for this study, acquiring the time and accurate GPS location. Upon opening the DJI Fly app, the prompted messages asked for several permissions (e.g., notification and location services, and access to photos), which were all agreed to. The app on the Samsung Galaxy S7, similarly to the iPhone 7, asked us to either log in or create an account, where we chose to log in, since we already had the account credentials used when we downloaded the iPhone’s app.
3.2.3. Laptops
Three laptops were used during the experiment, Lenovo G570 (Model 4334), HP Pavilion dv6 (dv6-7003em), and MacBook Pro (15-inch, 2018 running 2.9 GHz 6-core Intel i9). The Lenovo laptop had a Windows 10 Home (10.0.19042) operating system, used to set up the accounts, manage the WiFi network, and root the android phone. The HP Pavilion laptop with Linux Kali (Release: 2020.4) was set up to look for any interaction between the drone and the controller. For this, we utilized the monitor mode capability allowing the wireless card (Intel AC7260) to see 802.11 management frames and Wireshark (v3.2.7) capturing the frames on different channels. Although there was no need for the iPhone 7 to be jailbroken when acquiring the iPhone device using Cellebrite, there is a need for the device to be jailbroken using Magnet ACQUIRE because it does not offer jailbreaking for the investigator. Therefore, we needed the MacBook Pro laptop to jailbreak the iPhone using the Checkra1n app (beta 0.12.2).
3.2.4. Drone
The DJI Mini 2 drone used for this study was a brand new unit. Therefore, we made sure that it was fully charged and equipped with an empty external SD card. To simulate an attacker opening the drone and testing it before the deployment, we logged on to the app and operated once before the data population scenarios using the iPhone 7. All associated applications to operate the drone were installed on the phone used in this study.
Devices used in this study are presented in
Figure 2. Moreover, the figure includes additional items, which will be explained in detail further in the paper.
3.2.5. Machines Used for Investigations
In this study, two forensic workstations equipped with the same tools were used across all phases of the study to validate the results and eliminate any known software limitations. Additionally, to prevent any software bias, all acquired data were examined with at least two different software solutions if applicable. The first machine was equipped with Intel(R) Core(TM) i7-8700 CPU @ 3.20GHz, with 16 GB RAM, Windows 10 Education 20H2, while the second was equipped with Intel i9-10900K processor, NVIDIA GeForce RTX™ 3070 graphics card, and 32GB of RAM memory running X version of Windows 10 Pro. Note that this study does not consider the performance of the forensic processes performed on different workstations.
3.3. Data Population
Following the initial setup of the DJI Mini 2 and confirming the proper functionality (i.e., operating and flying it once), the drone was taken out to a location for the data population. The data population consisted of flying the drone in various patterns and altitudes while gathering images, videos, and other data. The process was completed on both iPhone 7 and Samsung Galaxy s7 utilizing the DJI Fly application for drone controlling and flying.
During travel from the setup location of the drone to the location of the data population, we left the drone powered on. In addition, two phones were utilized to navigate to the location using native map apps (i.e., Google Maps for Android, Apple Maps for iPhone).
Upon reaching the location, we flew the drone in 4 different scenarios on the first test day and additional flights for testing weight carrying capabilities on another day (i.e., Scenario 5). We discuss these scenarios in detail in the following
Section 3.3.1,
Section 3.3.2,
Section 3.3.3,
Section 3.3.4 and
Section 3.3.5. Moreover,
Table 3 illustrates the scenarios in detail. Note that all times used in this study are based on Eastern Time.
3.3.1. Scenario 1
This scenario was designed to portray a criminal-like action where a malicious user would purchase a drone that does not require any prior paperwork, and it is widely used. The user sets up the drone using a personal mobile device (i.e., iPhone 7) to make it operational. The user first tests the drone to make sure that it is working as expected for the action. Once the test is completed, the user leaves for the location where the drone will be flown from. Once arrived, the user prepares the drone and confirms the home location before the flight. The user flies the drone to the desired location and flies it back. During the flight, the user was able to take videos and photos of the flight.
This type of scenario can be applied to many different real-life situations where malicious users utilize the drone to drop off payloads and perform reconnaissance, etc.
3.3.2. Scenario 2
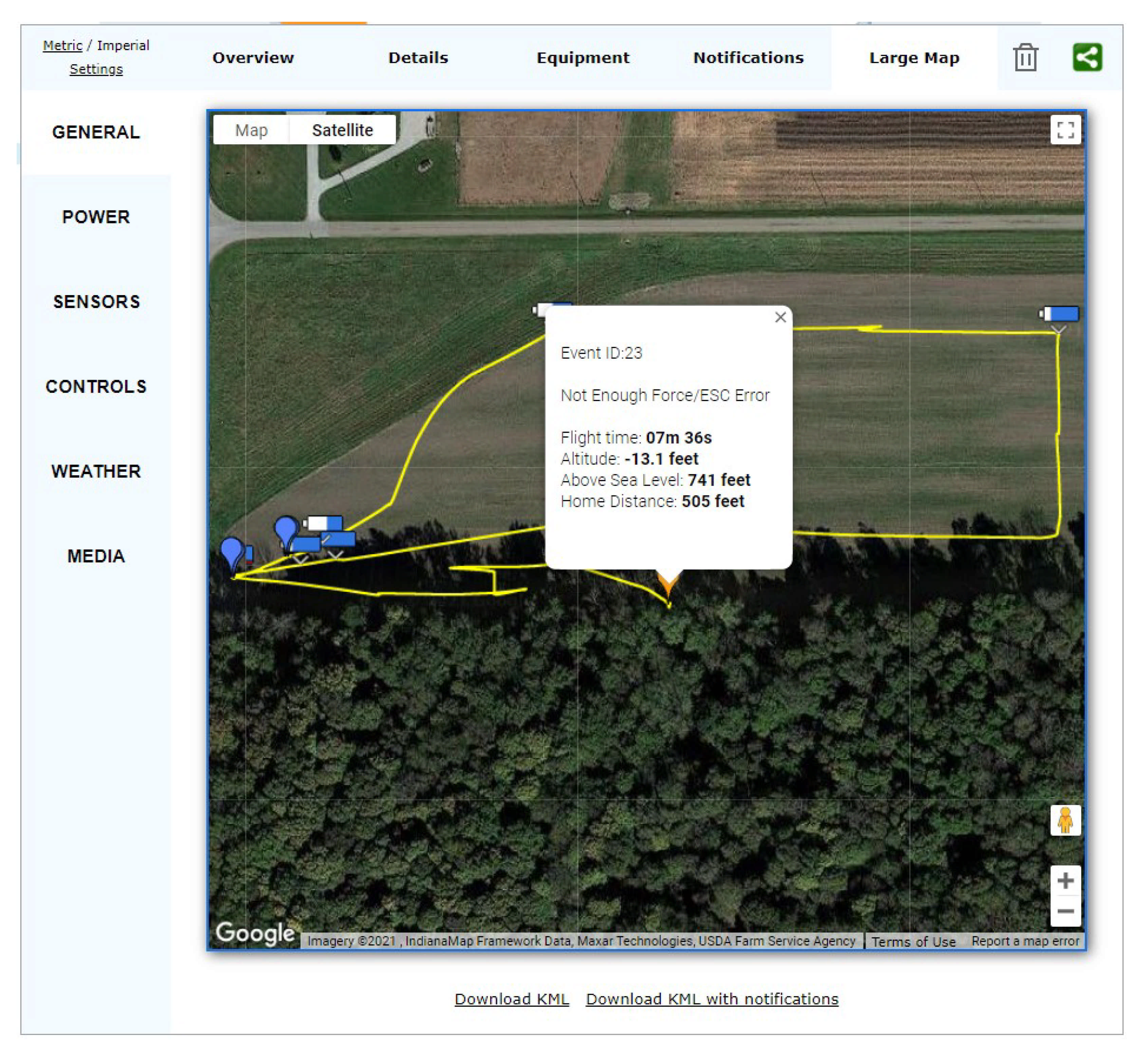
In this scenario, the same device was used as in Scenario 1 but only to perform a one-way flight. The reason behind designing a one-way flight is that we tried simulating the drone being captured or destroyed, hence not returning back. While catching the drone in this scenario, we tried shutting the drone by force clicking and holding the turn-off button; however, we could not turn it off while flying. During the process of capturing, the drone was turned off immediately by rotating it 180 degrees (i.e., top of the drone facing the ground).
3.3.3. Scenario 3
The scenario follows a similar process and the idea behind the malicious use as in Scenario 1 with few differences. First, instead of iPhone 7 as a mobile device connected to the controller, the device used was Samsung Galaxy 7. Second, the timestamps of the flight were different, as well as the flying path.
3.3.4. Scenario 4
This scenario follows the methodology of Scenario 2 except using Samsung Galaxy S7 instead of iPhone 7 as a mobile device. Just like other scenarios, this one has different timestamps of the flight and flying path.
3.3.5. Scenario 5
In this last scenario, we decided to test the carrying capabilities of the DJI Mini 2 drone using the iPhone 7 with multiple flights. This scenario was conducted at a separate location and on a different day than the previous four scenarios. The reasoning behind the test was to see the maximum carrying capacity and any difference between carrying payloads using multiple methods. The exact times of this flight scenario were not recorded in
Table 3 due to multiple short flights; while trying to determine the maximum carrying capacity, only the date of the flight was recorded.
This scenario shows the capabilities of the drone and what potential malicious items that are similar to the size and weight the drone can carry. Maximum carrying capacity can play a big role during the malicious act where dangerous items can be transported, dropped, and deployed.
3.4. Acquisition
To ensure that we made the most out of the two smartphone devices and gain privileged status, we performed jailbreak and rooting operations for the iPhone and Samsung devices, respectively, as previously discussed. This was required to create physical forensic images using Cellebrite UFED, Magnet AXIOM Process, and Magnet Acquire. The SD card used in the case scenario was acquired using Cellebrite’s Memory Card Reader with write blocker capability (see
Figure 3).
Additionally,
Table 4 presents the devices and tools used, the version of the tools, and image creation date and time in detail.
4. Analysis and Findings
In this phase of the experiment, we gathered, analyzed, and compared the previously populated data. The comparison of the collected data was achieved by utilizing multiple digital forensics tools. We started by analyzing the images created by the acquisition tools.
Table 5 explains the symbols used in
Table 6, which illustrates the findings from our analysis using the three initial forensics tools utilized for this study.
4.1. iOS Analysis
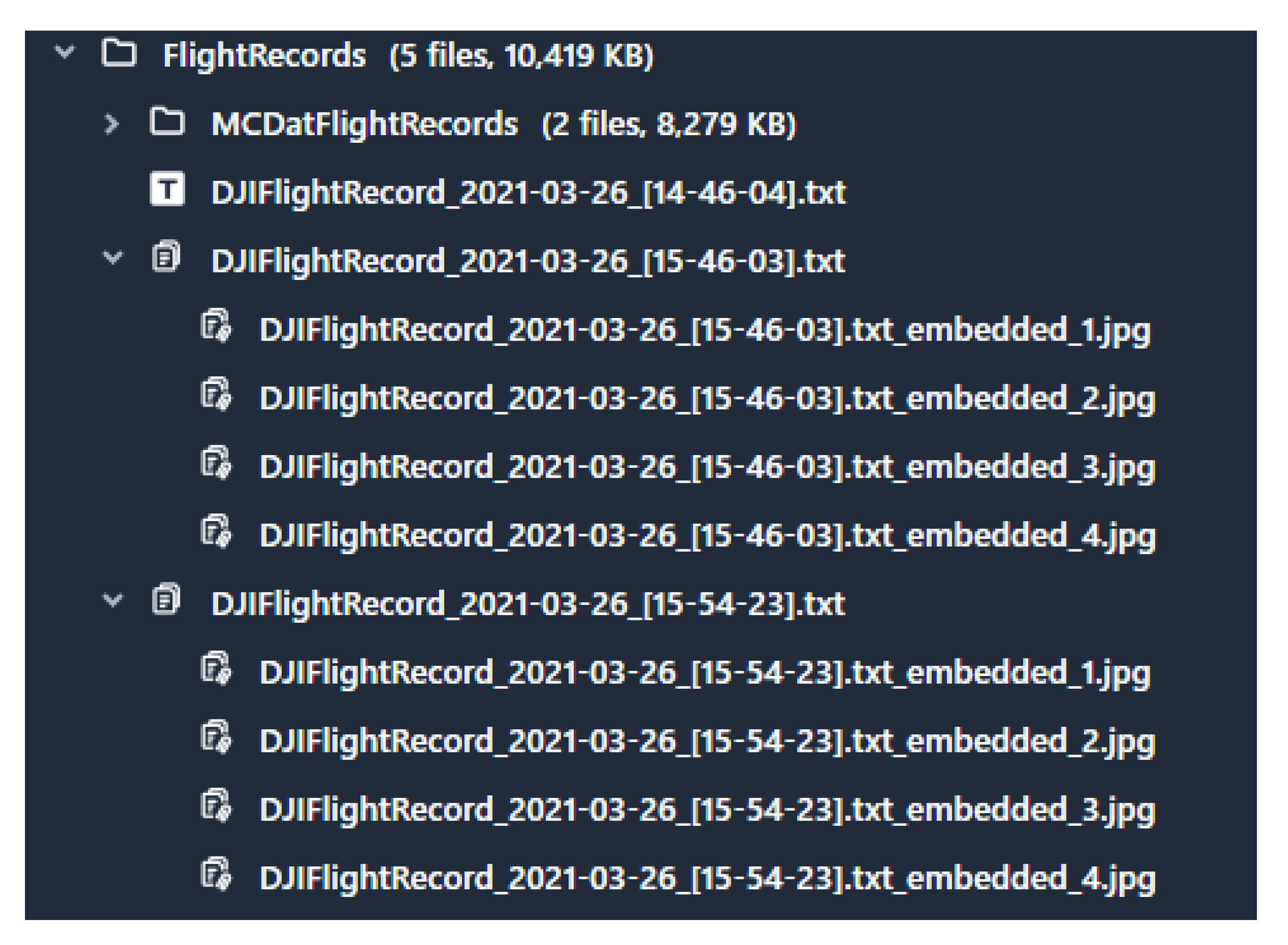
Following the first acquisition that was done after the first day of our experiment, we were able to find two .DAT and three .txt files; however, all the files discovered were encrypted. The reason that there are only two .DAT files compared to three .txt files is because it goes back to the difference in how these files were written. We believe that each .txt file represents a complete flight from take-off to land operation, where each .DAT file represents data when the drone is connected to a smartphone and is turned on to the drone shot-off. For instance, the first .DAT file represents the initial flight conducted before the scenarios, and the second .DAT file represents Scenario 1 and Scenario 2 where we did not turn the drone off between these two scenarios, resulting in one .DAT file.
The encrypted
.txt files were recovered from the
DarArchive\root\private\var\mobile\Containers\Data\Application/38FA31DB-9A11-4365-9083-8657C089F83D\Documents\FlightRecords\ folder on the iPhone, where the encrypted
.DAT flight logs can be recovered from the following path
DarArchive\root\private\var\mobile\Containers\Data\Application\38FA31DB-9A11-4365-9083-8657C089F83D\Documents\FlightRecords\MCDatFlightRecords\. Unfortunately, none of the digital forensics tools (i.e., Autopsy, Cellebrite, and Magnet Axiom) were able to decrypt the
.DAT or
.txt files that store the flight records. One major difference in the comparison of the tools is that Cellebrite was able to extract four
.jpg images from each of the
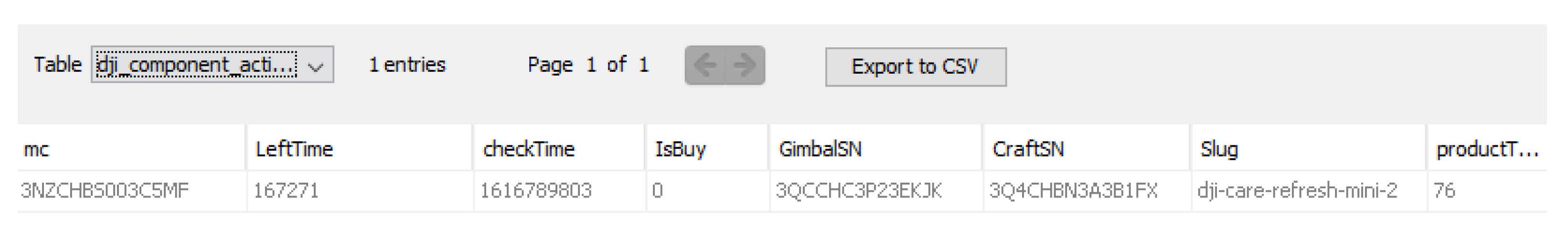
.txt flight logs. These images represent what possibly could be high-quality thumbnails or images showing the location at the beginning of the flight.
Figure 4 illustrates the screenshot taken from Cellebrite.
Moreover, we were able to recover significant PII that can help in investigations. First, we were able to recover the location of the first time that the iPhone was used to connect to the drone (i.e., in our study, it was the setup location) from
Application\38FA31DB-9A11-4365-9083-8657C089F83D\Library\.space_db\flysafe_dji_flight_dynamic_areas.db database inside a table named
dynamic_geofence_amba_record. We believe that this location was acquired from the phone and not the drone because the first time we operated the drone was inside a building, and the drone was not able to detect GPS signals.
Figure 5 illustrates the user geolocation finding.
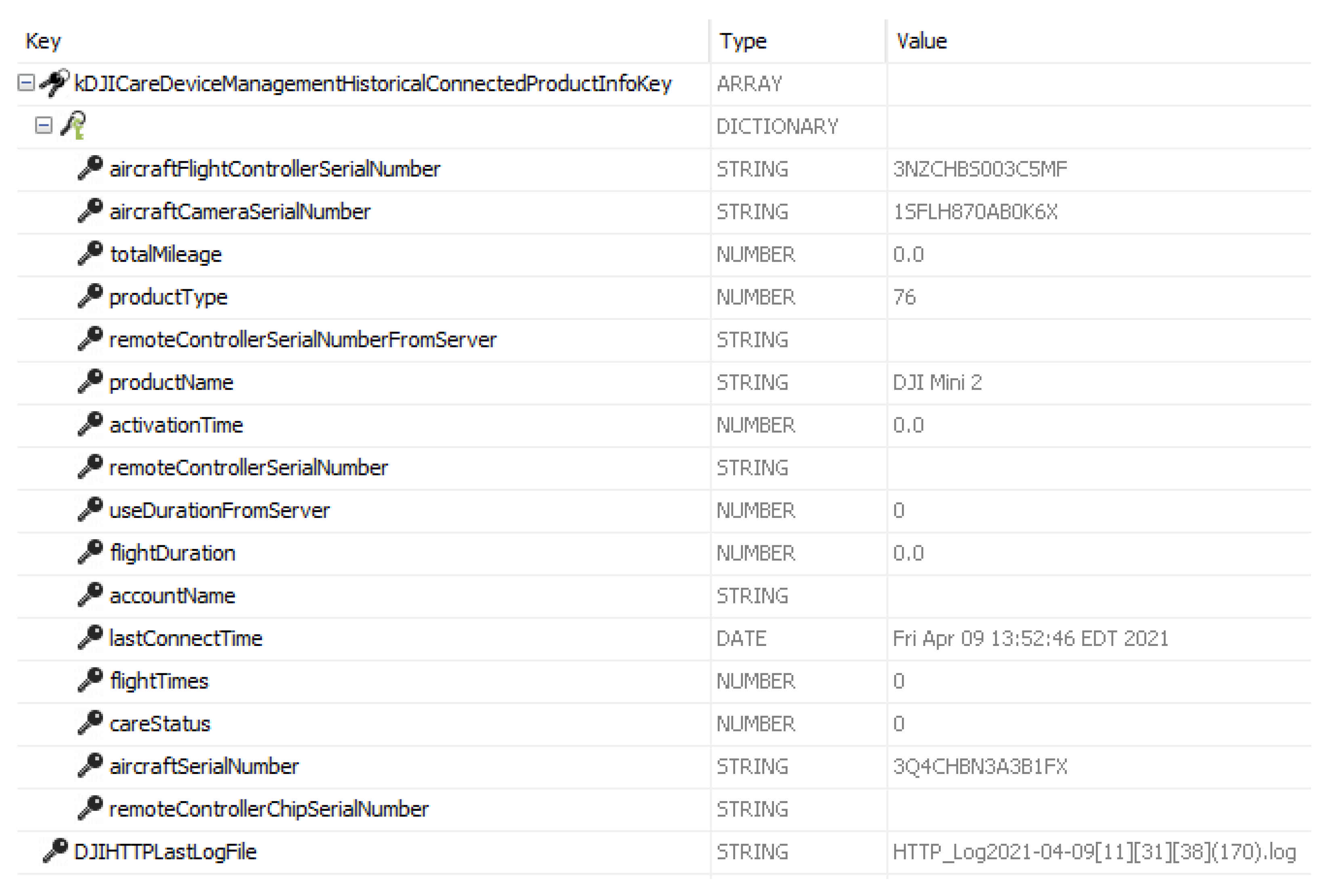
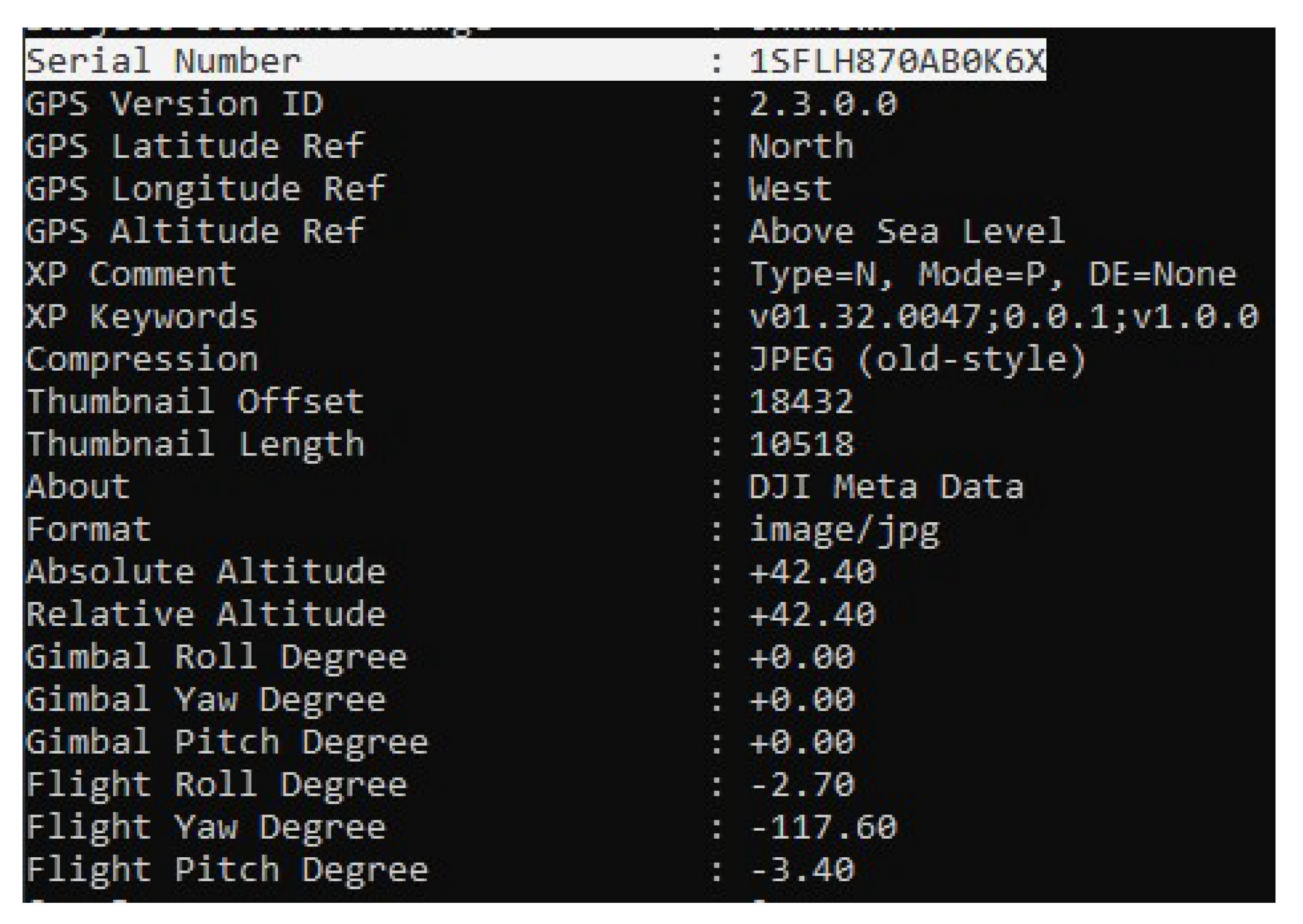
Other PIIs, such as the email that is used for app login, activation timestamp, DJI model name, last connected time, uptime, and aircraft camera serial number were recovered from
Application\38FA31DB-9A11-4365-9083-8657C089F83D\Library\Preferences\com.dji.golite.plist.
Figure 6 shows flight controller serial number, camera serial number, product name, last connect time, and the drone serial number. Moreover,
Figure 7 displays the last connected email used to fly a drone, and
Figure 8 shows the first time the iPhone was connected to the drone after the user finished with the activation process.
Another finding worth mentioning, in the scenario where the drone was captured, is that the camera on the drone kept recording for another 20 s even though it was flipped upside down, and the propellers were not spinning.
Although we compared the acquisition after the first day that consisted of the first two scenarios for the iPhone (see
Section 3.3.1 and
Section 3.3.2) and the acquisition after Scenario 5 (see
Section 3.3.5), the uptime did not change. On the other hand, the last connection recorded has changed and updated following the second acquisition that was performed after Scenario 5 to when the drone was last connected to the application using this iPhone. In addition, in
\private\var\mobile\Containers\Data\Application\38FA31DB-9A11-4365-9083-8657C089F83D\Documents\Tmp\DJISyncLog_2021-03-26_[13-36-13].txt file, we found records stored that convey the DJI drone sync with the phone/server, and the timestamps are similar to the scenarios.
4.2. Android Analysis
Similar to iOS analysis, we were able to discover both .txt and .DAT file types in an encrypted form. The .txt files containing flight logs were recovered from \data\media\0\DJI\dji.go.v5\FlightRecord folder, and the .DAT files were recovered from the \data\media\0\DJI\dji.go.v5\FlightRecord\MCDatFlightRecords\ folder.
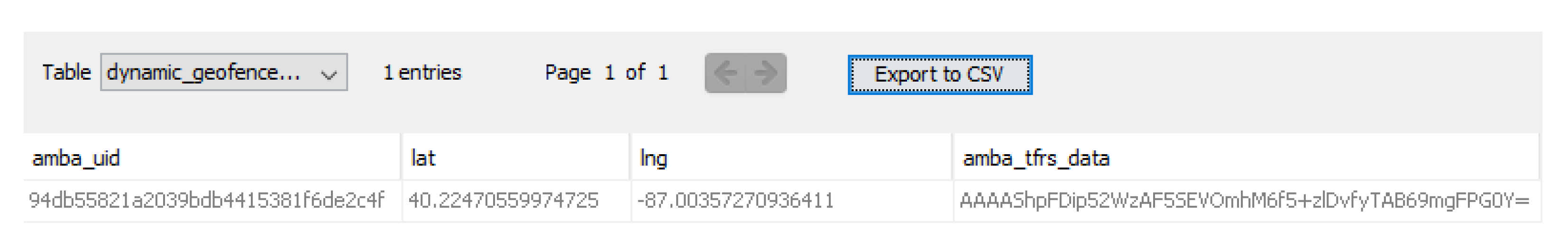
Regarding PII, the location of the first time that the phone connected to the drone was recovered from the table named
dynamic_geofence_amba_record inside the following database
\data\data\dji.go.v5\databases\flysafe_dji_flight_dynamic_areas.db. Other similar PII to the ones recovered from iPhone (e.g., DJI model name, and aircraft camera serial number) can be recovered from the
\data\data\dji.go.v5\databases\dji.db database.
Figure 9 demonstrates the geolocation values (longtitute and latitute) recovered from the
dynamic_geofence_amba_record table, where
Figure 10 shows the drone serial number along with other valuable information.
Moreover, we were able to recover a thumbnail image showing an image captured from when the iPhone was controlling the drone; the image recovered from the following path
\data\media\0\DJI\dji.go.v5\CACHE_IMAGE\ImageCaches\. On the other hand, the video captured during Scenario 4 (see
Section 3.3.4) was cut off and not complete, whereas for the iPhone (see
Section 3.3.2), it was complete. Additionally, it appears that Cellebrite was not able to extract any images embedded inside the
.txt flight logs on Android.
4.3. SD Card Analysis
Analyzing and examining the external SD card revealed that the SD card is storing media files taken during the flight and some encrypted logs. Although these logs are not the flight path logs, we were unable to decrypt them despite our efforts. On the other hand, all recovered videos have locations associated with them (see
Figure 11). In addition, we were able to access media files from both phones and all four scenarios where the SD card was used. Even the video recorded during Scenario 4 (see
Section 3.3.4) is found to be complete. Both the pictures and videos stored in the SD card can be recovered from the
\img_Dump_001.bin\vol_vol2\DCIM\100MEDIA folder.
In addition, we were able to use ExifTool to recover the camera serial number from the pictures taken.
Figure 12 demonstrates the recovered camera serial number and plenty of other information.
4.4. Carrying Capacity Analysis
The first step of the carrying capacity drone analysis was to determine the overall weight of the drone. The drone was placed on the scale (Perfect Portion) and measured at 240 g (±3 g) compared to the 249 g of marketed weight. Next, the fishing line measuring 60 cm was tied to the bottom of the drone with an attached plastic box where the weights were added. The weight of the plastic box with the fishing line added up to 36 g, making the overall weight of the drone and box 276 g. Weights were added between each flight until the drone was not able to take off. The maximum capacity that the drone was able to lift was around 300 g (including the plastic box, weight, and the line). Although the drone was able to lift that amount of weight during the take-off and flight, it could not maneuver easily. Therefore, the next step was to determine the optimal capacity that the drone could carry and maneuver without any problems.
For this experiment, we started removing weights (starting at 300 g) until we were satisfied that the drone operations were restored to normal. The weight we determined in which the drone can restore its normal flight was around 250 g. It is important to note that during the flight, we were experiencing high winds and that it is quite possible that the carrying capacity can vary during different flying conditions.
As our last experiment, we decided to place the weights and the box on top of the drone. The drone was able to carry and fly with 250 g attached to it. Moreover, we observed more responsiveness from the drone when the weights were attached on top of the drone compared to hanging and swinging below it.
Figure 13 depicts the setup used during this analysis.
4.5. Data Analysis
As discussed earlier,
.DAT and
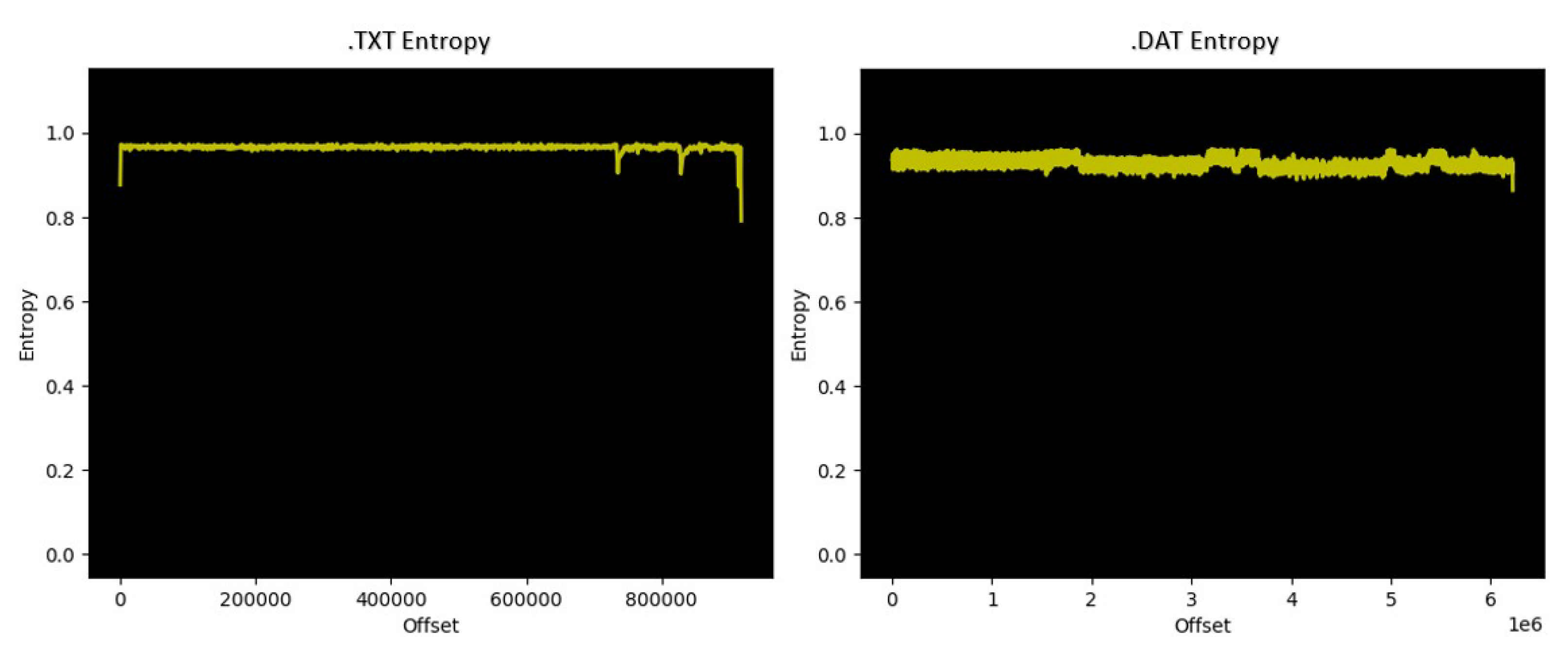
.txt flight logs/records were not recognized by the forensics tools used in this study because they were encrypted. Therefore, we ran an entropy analysis using the Binwalk tool (v2.2.0) [
20] to calculate each file’s entropy score.
Figure 14 illustrates the outcome of the tool after running it on both files for Scenario 1 (see
Section 3.3.1). As shown in
Figure 14, the results showed very high entropy scores throughout both files.
Following the literature review, many resources suggested using different tools in an attempt to decrypt the
.DAT files generated during the scenarios. The most used freeware tool to decrypt
.DAT files is the DatCon [
21]. Even though the website stated the model of our drone was not supported, we tested it regardless. It turned out to be true, and the
.DAT files could not be decrypted. As an alternative solution to examine the contents of the
.DAT files, we found the website airdata.com. Airdata helps pilots and others (e.g., researchers) by providing fleet drone management, as well as crash-prevention information [
22]. After the registration of a free account, we were able to upload our
.DAT files and decrypt them successfully.
Despite the ability of airdata.com to decrypt the .DAT files, we also tried to decrypt .txt files; however, the process was not successful. Moreover, airdata.com allows the user to download the decrypted .DAT files in KML, GPX, CSV, and original formats. Therefore, to ensure data integrity, we compared the outcome of the downloaded CSV file once after the decryption, the second time after deleting the file and enabling the web tool to decrypt it again. Interestingly, we found that the checksum values using the MD5 hashing algorithm of the two downloaded CSV files match, meaning that the tool provides consistent decryption results.
While the main motive behind the website (airdata.com) was not to provide digital forensic services to the end-users but to give pilots crash-prevention information and manage large fleets of drones, we found this website very beneficial during our study [
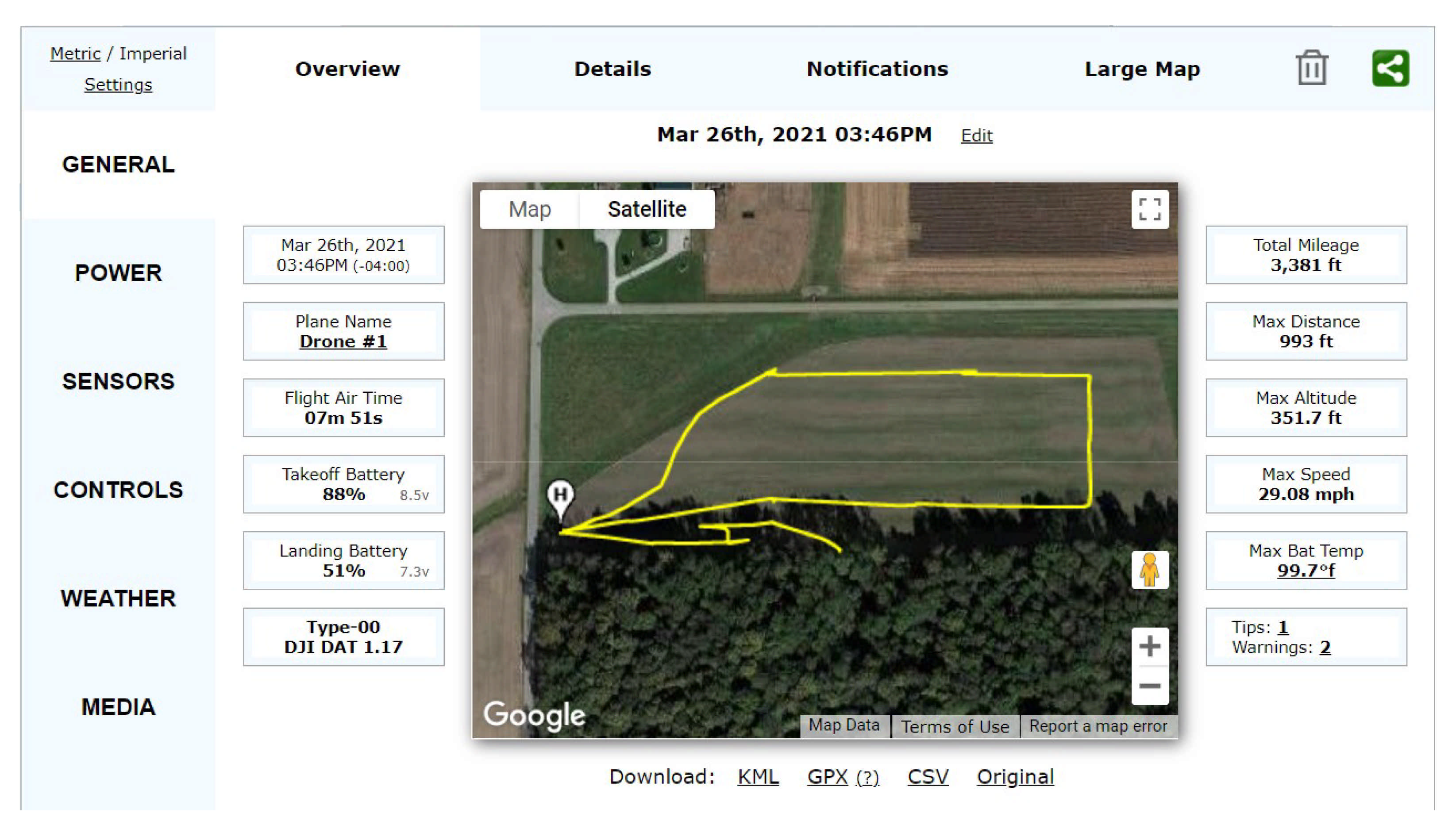
22]. Its intuitive user interface and detailed analysis of the log files allowed us to visualize flight patterns, altitudes, battery levels, controls sent to the drone, error codes, and many more. A screenshot in
Figure 15 shows the user interface of the airdata.com web tool during the analysis process of Scenario 1 and Scenario 2. Moreover,
Figure 16 illustrates the weather tab that contains wind speed faced during one of the flights in Scenario 5.
One important finding is we could not have a matching location (i.e., drone flight location and iPhone cached location) from the cached locations recovered from the iPhone in the first acquisition using Magnet Acquire. However, we were able to find matching locations for the drone and the iPhone after the second acquisition using Magnet Acquire. This is due to the fact that the iPhone keeps the cached locations for a certain time (approximately one week), and our first Magnet acquisition was more than seven days apart from the day we flew the drone. However, we were able to find the matching location in the second acquisition because it was performed within seven days. In addition, in the first Cellebrite acquisition for Scenarios 1 and 2, we were able to match the user location with the cached locations on the drone flight records because it was less than a week from the scenario. We recovered the iPhone cached locations from the ZRTCLLOCATIONMO table located in the \private\var\mobile\Library\Caches\com.apple.routined\Cache.sqlite database.
Moreover, we wanted to confirm that the drone or the controller was not beaconing any management frames during the flight. We matched the channels by setting the same channel and frequency on the app and the wireless card on the laptop. We then opened Wireshark (v3.2.7) and filtered DJI’s Media Access Control (MAC) address. Since we did not want the filter for a specific MAC address, we created a byte-offset capture filter for the first three octets unique to each manufacturer, such as DJI. The filters did not show any MAC addresses related to the DJI. The probable reason for this is because the drone is using OcuSync 2.0, which is a wireless transmission protocol used in these newer types of drones when transmitting video feeds over long distances.
Although the user interface on both iOS and Android devices looked similar, one major difference we spotted was the password character limitation when accessing the accounts before the flight.
Lastly, during the capturing scenarios of the drone operations on both iOS and Android mobile devices, we tried shutting off the drone first while in flight by pressing and then holding the power button. However, this method did not work. When we flipped the drone upside down, the propellers stopped, and we were able to suspend the drone operations. This illustrated how this drone can be best captured without causing damage to the drone.
5. Discussion
During the course of this study, we experienced several difficulties with the digital forensic tools when it came to decrypting the flight records. Therefore, we can safely conclude that there is no one tool that would be superior in drone forensics, as discussed in
Section 4 in detail. It is important to note that during these types of investigations, the investigators need to utilize multiple techniques and sources to find and examine data. As we have shown, the tool that was able to decrypt the
.DAT files was not intended for digital forensics investigations; however, it was able to decrypt and then analyze the flight logs.
Moreover, current digital forensics tools could not recognize the drone when connected directly to the forensics machine. This is because this model of the drone is new, and it is found that this model is not equipped with storing data internally. However, that does not imply that the internal memory of some sort does not exist. This leaves the door open for further analysis, such as chip-off analysis, which is out of the scope of this research.
As it was discussed in
Section 4.4, the carrying capability of the DJI Mini 2 drone was more than we expected. The ability to carry more than its weight should be very concerning when thinking about malicious activities that can be performed easily without being detected. Furthermore, another consideration is that this type of drone does not require any previous paperwork or registration, which leaves law enforcement agencies with no ability to track back to the owner or a malicious actor. At the time of this writing, there are no major changes expected in FAA rules regarding micro drones (e.g., DJI Mini 2) at least until 2023 [
23], leaving room for malicious activities.
Security concerns arose when the DJI Fly app was not in the official Android Play Store, and it had to be downloaded as an APK file and then installed on the mobile device. This presents great security concerns since the owner of the device does not always have the latest version (i.e., updated version) of the app. In addition, the app can contain malicious code placed by accident or on purpose. It is also possible that malicious code can be introduced or hard-coded into the APK file, which leads to vulnerable mobile devices used by the end-users.
During the initial setup of the drone, we were able to fly the drone without a GPS signal successfully, further indicating anti-forensic challenges to hide any PII related to the location. As a result, these challenges will make the investigation challenging, even if they consist only of the phone and the drone with the controller.
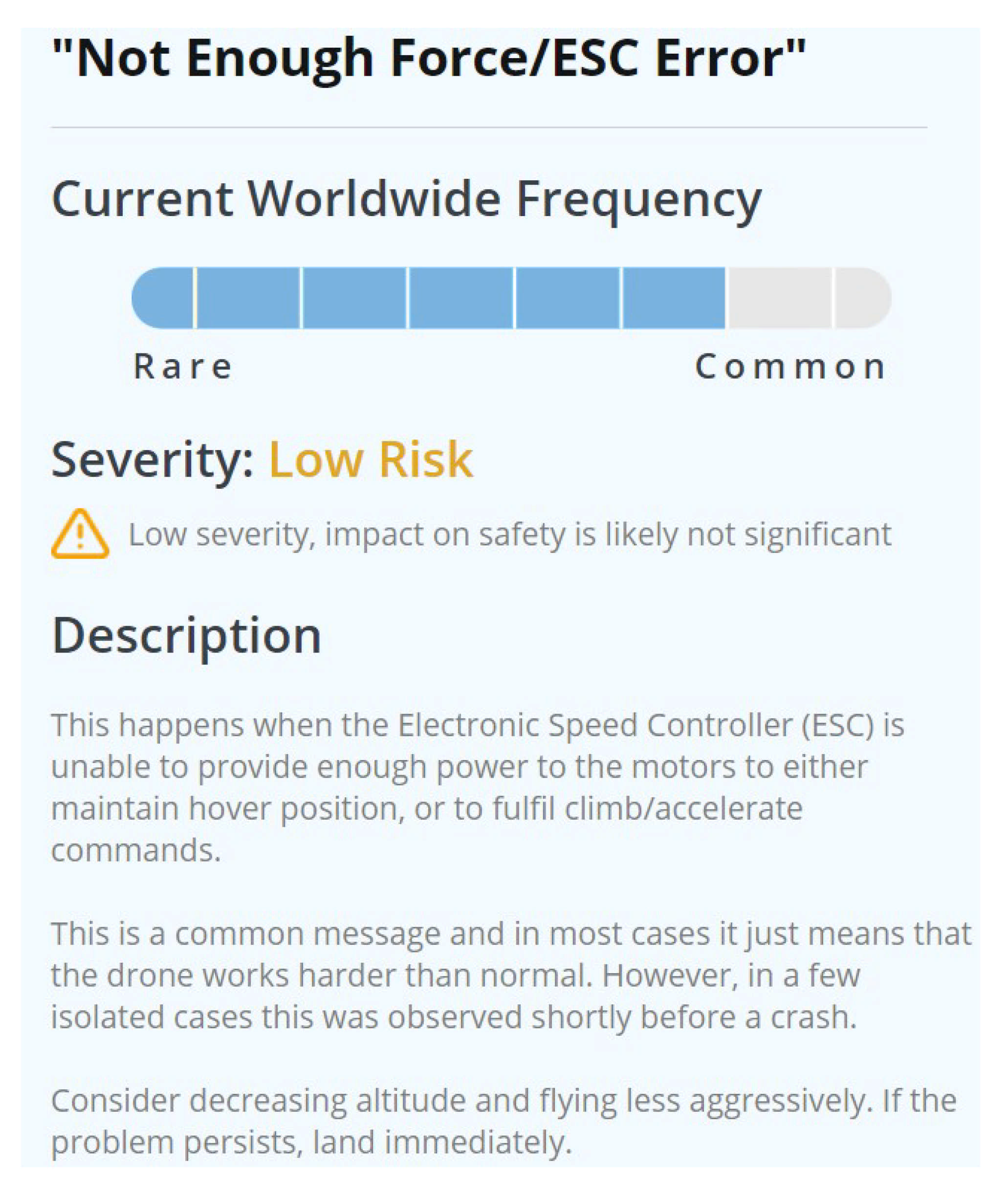
The error codes were found during the examination of the
.DAT files via the airdata.com website. These errors showed a possibility to discover if the drone was carrying a load while operating. The error code: “Not Enough Force/ESC Error” was repeated continuously during the weight testing flights.
Figure 17 shows the definition of this error code according to the
airdata.com wiki page for notification [
24]. Moreover,
Figure 18 demonstrates the error code while the drone is being captured in Scenario 2 (see
Section 3.3.2).
6. Conclusions and Future Work
Drone usage over the last few years, especially in recreational uses, has dramatically increased in production. This increase greatly affects law enforcement agencies that are trying to battle malicious drone usage. In this case study, we had complete control over all stages of the conducted comprehensive experiment on the DJI Mini 2 drone to utilize it in creating criminal-like scenarios. Similar scenarios are likely to be committed for nefarious activities in the real world by malicious users. While the findings of this study are limited to only one UAV (i.e., DJI Mini 2), it is important to note that the availability, price, and lack of regulations for the drone make it easy to conduct criminal-like activities. That is why having a comprehensive study on the drone can help forensic investigators when faced with similar scenarios. As discovered in our analysis, the carrying capacity of the DJI Mini 2 is more than the weight of the drone itself, which might be used by malicious actors in different scenarios such as dropping contraband materials on prisons or smuggling drugs over borders, etc.
For future work, we plan to perform chip-off data extracting and analysis. This may be very useful due to the ability to acquire data from the drone body, which would reveal insightful information, as seen from previous research. Moreover, a further experiment can be performed to check how battery usage is affected when carrying various weights. Finally, an examination of OcuSync 2.0 transmission technology can be performed to experiment on communication methods between the devices by applying a UAV kill chain to identify possible intrusion vulnerabilities.