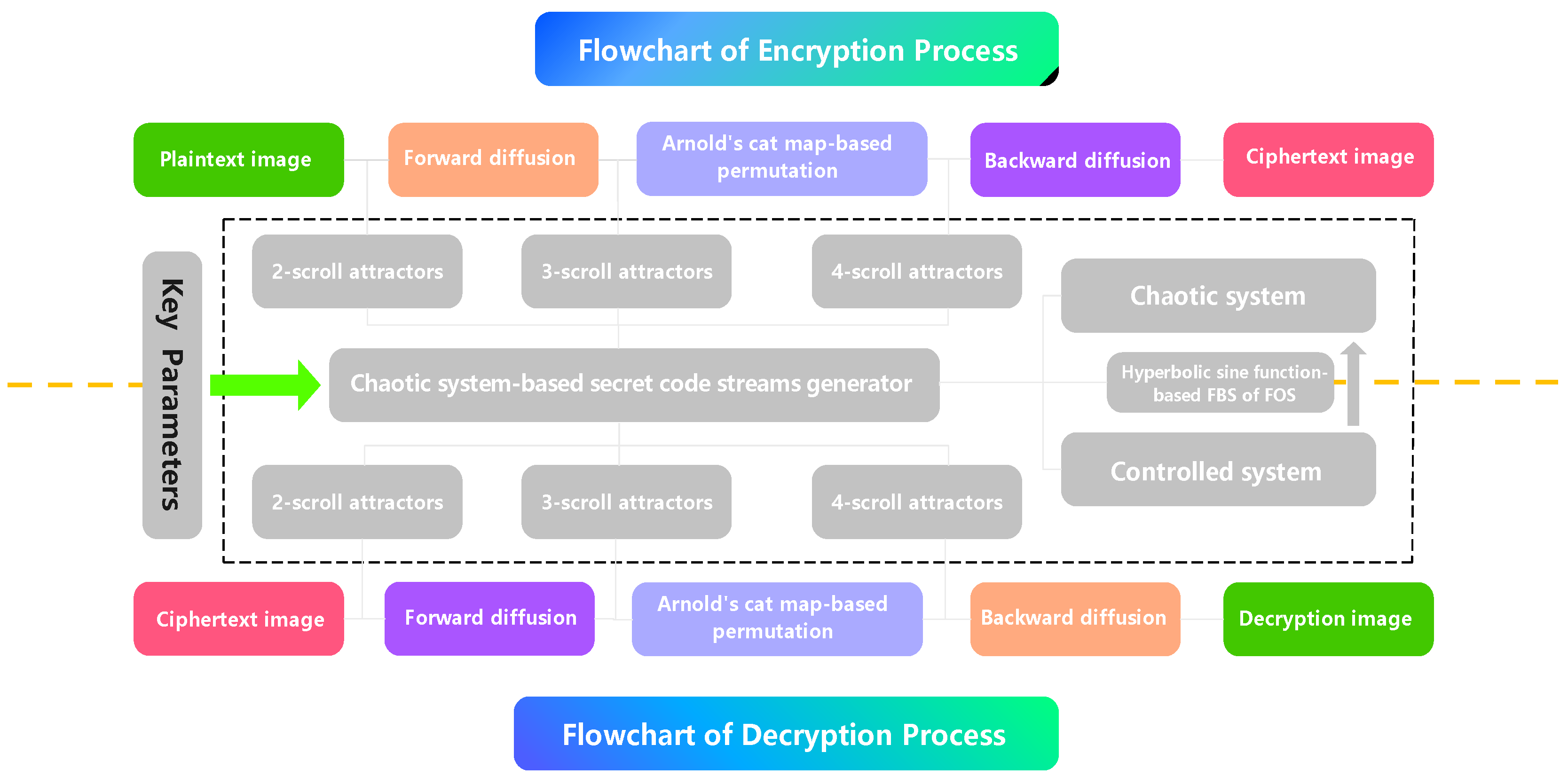
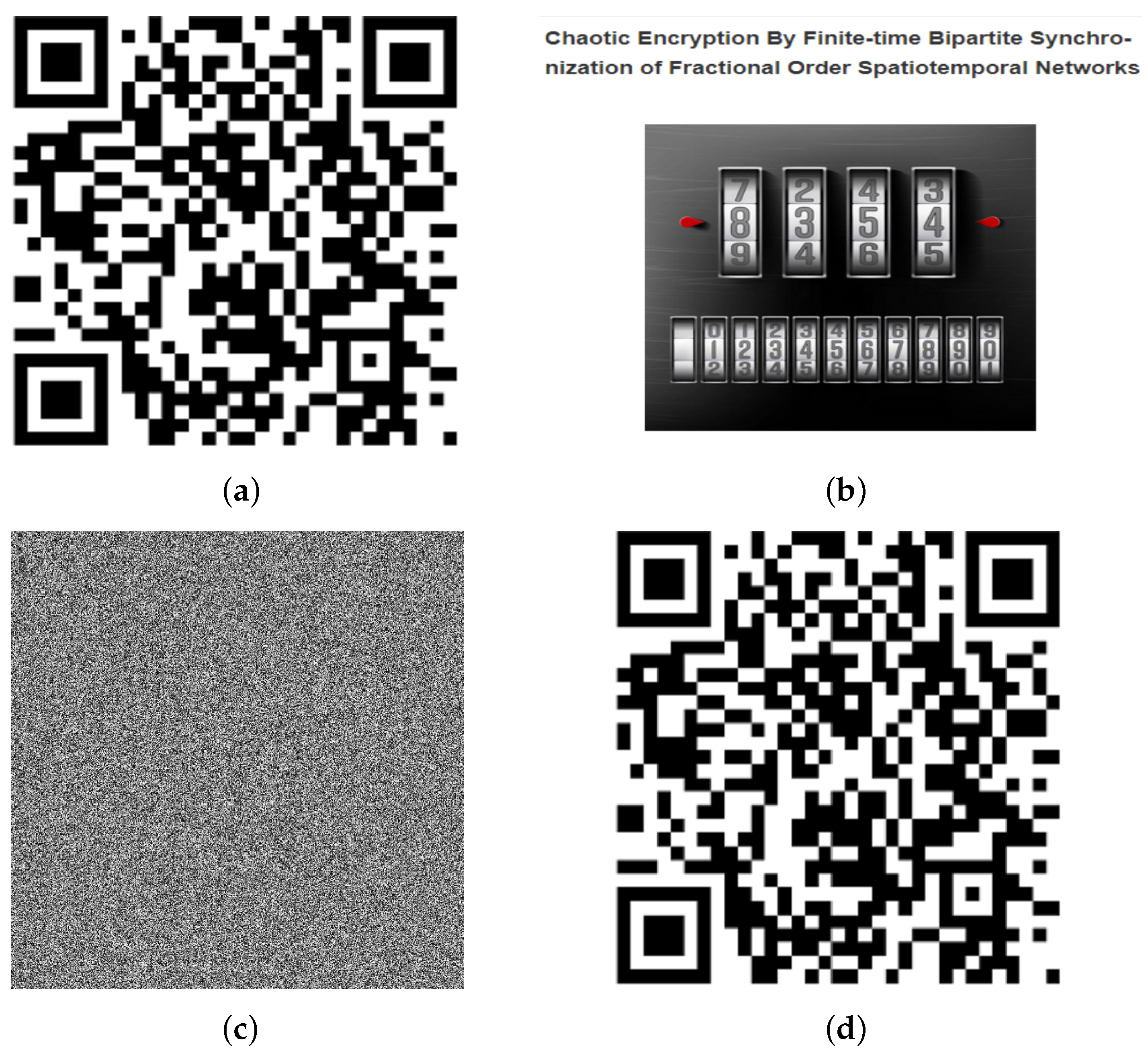
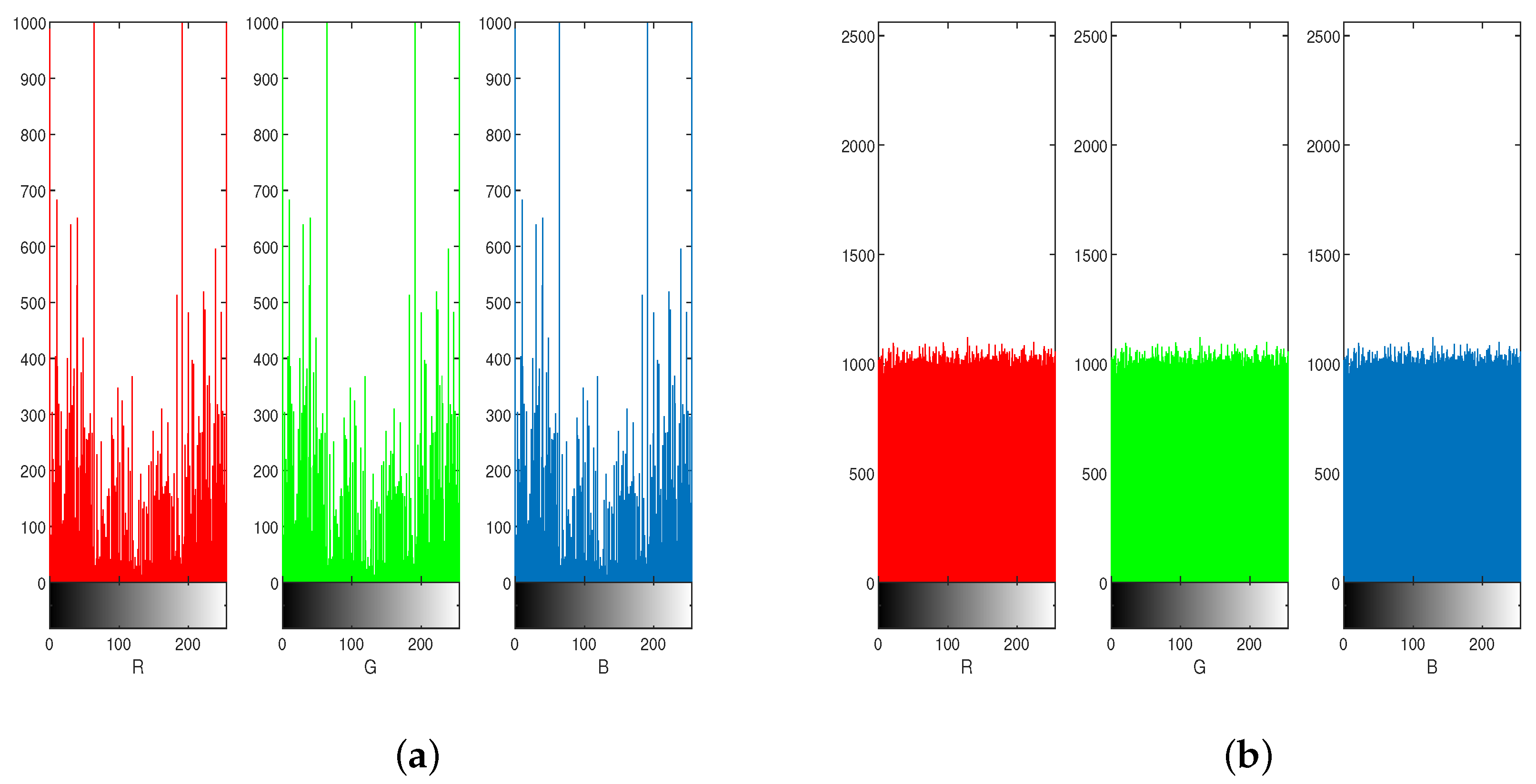
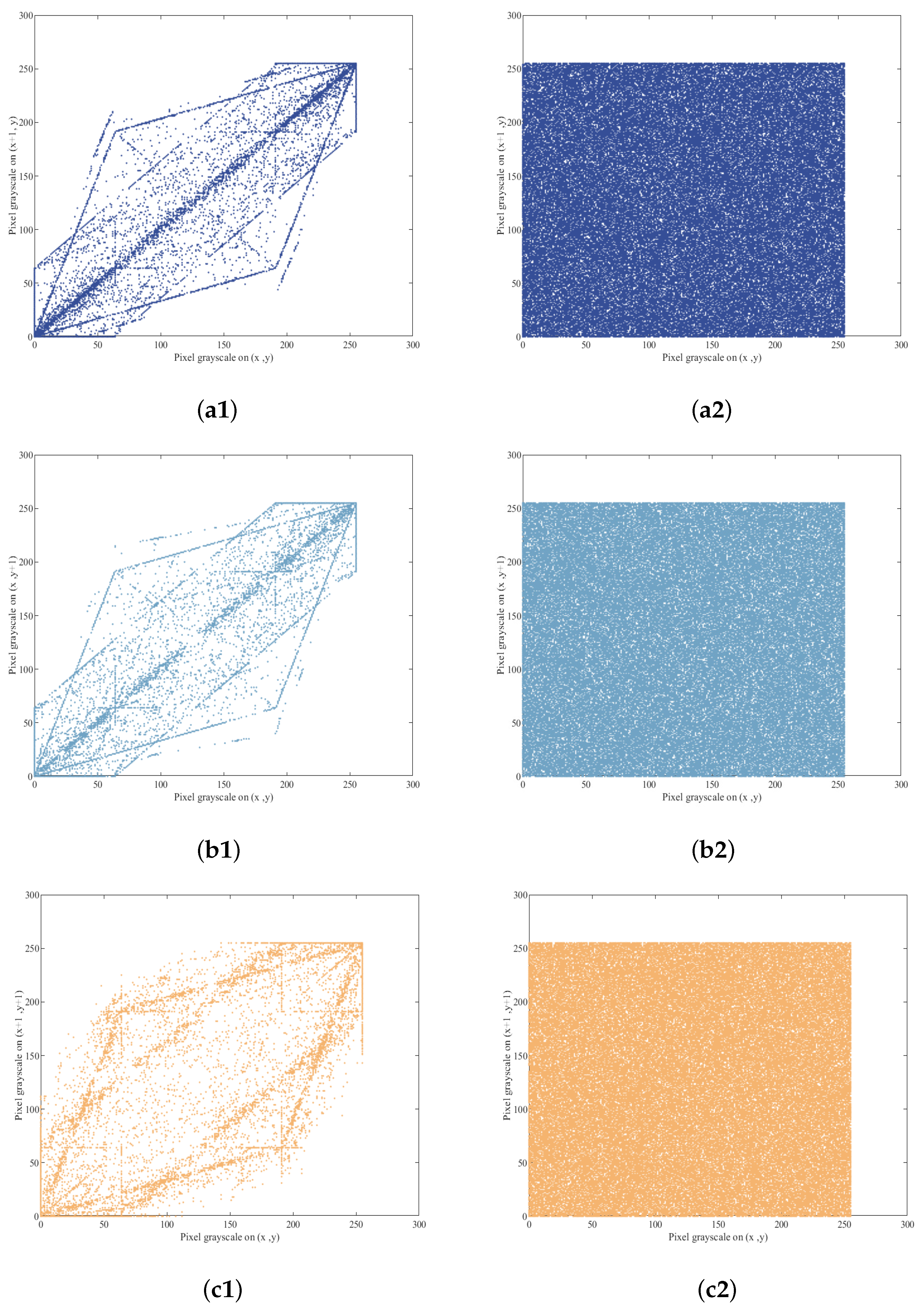
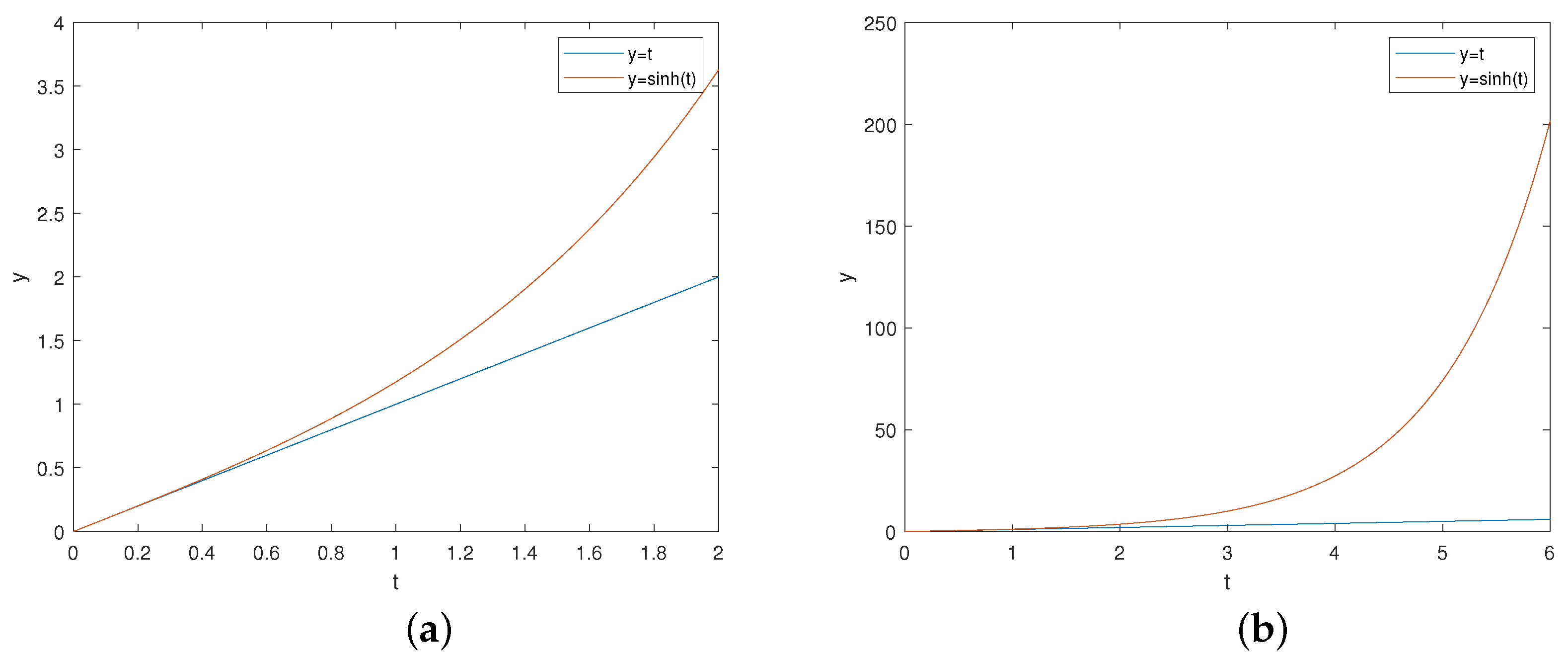1. Introduction
Recent years have witnessed the flourishing development of complex networks (CNs) across diverse fields, encompassing social networks [
1], power grids [
2] and transportation networks [
3]. Synchronization, a fundamental issue in the dynamic analysis of CNs, in which all nodes should achieve a desired performance, has attracted extensive attention from scholars. The theories and techniques developed in synchronization analyses have already been successfully applied in a broad scope of fields, such as secure communication [
4], biological engineering [
5] and image encryption [
6]. Notably, there is a widespread occurrence of diffusion phenomena with spatiotemporal properties in practical engineering scenarios, including electrons moving in a circuit to implement a neural network and the substance concentration changes that occur during chemical reactions. Therefore, CNs with a reaction term and a diffusion term, i.e., spatiotemporal networks (SNs), have captured much attention of the scholars, and some fascinating and remarkable achievements have been published [
7,
8,
9]. Nevertheless, the aforementioned works on SNs are all based on the premise that the diffusion matrix should be diagonal, posing extremely strict restrictions regarding the scope of their practical applications. Besides, there are few related works on the synchronization of SNs with anisotropic diffusion, i.e., the diffusion matrix in a general form. Hence, it is challenging but urgent to address this problem, as this would provide significant guidance in dynamic behavior analyses of SNs, which is the starting point of this work.
In another respect, due to the positive qualities of heritability and finite memory, fractional calculus has attracted widespread research interest and has already been extensively employed in various fields, including image enhancement [
10], viscoelastic systems [
11], and Lithium–ion batteries [
12]. Therefore, it is of great significance to discuss fractional calculus in both theory and practice. Since fractional calculus was incorporated into networks, abundant remarkable accomplishments have been obtained in fractional-order (FO) networks [
13,
14,
15]. Notably, Wu et al. [
13] established an FO partial differential inequality to solve the pinning synchronization of multiple FO fuzzy complex-valued delayed spatiotemporal neural networks using a decomposition approach. In [
14], projective synchronization was analyzed for FO neural networks with mixed time delays using the extended Halanay inequality. However, findings regarding the synchronization of FOSN appear limited, which prompted us to further explore this interesting and meaningful problem.
Significantly, the focus of the above-mentioned works is networks with only positive weights, meaning that the nodes in the networks are just only cooperative. In fact, competition exists in almost all complex systems, such as different companies competing for economic benefits and different countries competing to obtain military dominance. As a consequence, it is highly valuable to consider the synchronization of networks featuring both cooperation and competition. Additionally, ever since the publication of Altafini’s pioneering work [
16], bipartite synchronization (BS), in which a subset of the nodes synchronize to a desired state while the remaining nodes synchronize to the same value with the opposite sign, this has quickly emerged as a major research issue [
17,
18,
19,
20]. Xu et al. [
17] devised a hybrid impulsive to study the exponential BS of FO multilayer signed networks with both positive and negative impulsive effects. Ding et al. [
18] discussed the quasi-BS of complex networks via memory-based self-triggered control. In [
20], interval BS were studied in multiple neural networks with signed graphs. Nonetheless, academic studies involving the BS of FOSNs are relatively few, which strongly stimulated our research interest.
Another issue deserving attention is that the results set forth previously all concentrate on asymptotic synchronization over an infinite time scale. However, real tasks often must be finished within a limited window of time. Accordingly, based on a seminal work [
21] regarding finite-time (FN) stability, FN synchronization, where all nodes converge to the desired performance within a limited window, quickly captured the attention of multiple researchers. FN synchronization has achieved a multitude of excellent outcomes [
22,
23,
24,
25], due to its distinct superiority in terms of its quick convergence rate, high control accuracy, and anti-interference qualities. In control research domains, how to more accurately estimate settling time (ST) has consistently been one of the most prominent research hotspots. Furthermore, the hyperbolic sine function (HSF), as a generalized exponential function with some trigonometric properties, plays a fascinating role in dynamic analysis. The systems in [
26,
27] based on the HSF exhibited intricate bifurcation and strange chaotic attractors. In [
28], the HSF was introduced in sliding mode to solve the uncertain FO chaos synchronization. Following this, it is natural to consider why the HSF, with such admirable properties, could generate an excellent control effect in synchronization control. Fortunately, Xu et al. [
29] devised a novel control scheme involving an HSF and a linear term to synchronize CN within a finite time, achieving a tighter bound of ST and anti-chattering abilities. However, the HSF control law has not gained the attention it deserves, and nor has the FNBS of FOSNs. The primary challenges are summarized as follows: (1) the spatial variability, anisotropic diffusion matrix, and diffusion term pose difficulties when designing a control scheme based on Taylor expansion and HSF; (2) as the HSF control is a relatively novel method, it is challenging to improve the control scheme in [
29], and there is no straightforward method to decouple the reason for its outstanding anti-chattering qualities or its ability to achieve a tighter bound of ST. It is important to address these challenges, which was the primary motivation for this paper.
Sparked by the above discussions, the intention of the paper is to pursue the FNBS of FOSNs. The main achievements are summarized as follows:
(1) In contrast to the existing literature [
7,
30,
31], which have relatively conservative requirements for diagonal diffusion matrices, the addressed FOSN, with anisotropic diffusion, is more in accordance with the actual circumstances, in which the diffusion matrix can be non-diagonal or non-square, i.e., the number of state components is independent of the spatio dimensions.
(2) Furthermore, in order to explore the synchronization issues, two novel lemmas involving equation transformation and inequality estimate are established based on the Hadamard product, Hamiltonian operator, as well as trace, which can be further degenerated into the special circumstances listed in [
7,
32,
33].
(3) Differing strikingly from the the control protocol in [
34] involving the linear term and power-law term, a new kind of control law based on HSF is proposed to address the FNBS of FOSNs, with distinctive superiority in terms of its swifter convergence rate, the tighter bound of the ST, and the suppression of chattering.
(4) Compared to the controller in [
29], our devised HSF control law considers the effects of spatiotemporal information even without linear terms, which is more concise and effective. Differing from the controller in [
7,
35], the sign function is not contained in the devised HSF control law, avoiding chatter and improving the smoothness of the control input.
The work is organized as follows.
Section 2 provides some necessary preliminaries and the model description. In
Section 3, the HSF control is considered via a comparative analysis with two additional specific control protocols. Some simulations are carried out to support our findings in
Section 4. In
Section 5, the application of our results in image encryption is presented.
Notations. Denote
and
. Let
, and
represent the space of real numbers, the n-dimensional Euclidean space, and the
real matrices, respectively.
.
is the set of all positive integers.
represents the diagonal matrix. ⊗,
, and
denote the Kronecker product, column vector with all zero elements, and column vector with of all ones, respectively. For any
,
and
signify the transposition of matrix Z and negative semi-definite matrix Z, respectively:
,
. For the symmetric matrix Z,
is the maximum eigenvalue. For any
,
. ∘ denotes the Hadamard product:
;
;
.vec(·) symbolizes the straightening operation.
2. Preliminaries and Model Description
In this section, some essential definitions, lemmas, and assumptions are presented, along with the model description.
Definition 1 ([
36])
. The fractional-order Caputo derivative of
is defined byLet
be derivable with regard to t and
.
Definition 2 ([
36])
. The fractional-order Caputo derivative of continuous differentiable function
with regard to t is defined by Definition 3 ([
37])
. A signed graph
is structurally balanced if it has a bipartite division of nodes,
and
such that
and
. Assumption 1. The topology graph
of the addressed network is strongly connected and structurally balanced.
Assumption 2. For nonlinear function
:
, there exists a positive constant
such that for any vectors
, Lemma 1 ([
36])
. According to the properties of
, Lemma 2 ([
36])
. According to the properties of
, suppose that
is integrable with regard to Ω. Let then, Lemma 3 ([
30])
. (Wirtinger inequality) Suppose that
is a continuous and square integrable function satisfying
or
; then, Lemma 4 ([
38])
. (Generalized Gauss–Ostrogradskii Theorem) Suppose that Ω is a bounded closed region with a piecewise-smooth boundary surface
and
,
; then, where n is a outward-pointing unit normal vector determined by the areal element of
. For convenience, the above equation is denoted as follows: Lemma 5 ([
39])
. Suppose that function
, and function
is C-regular (positive definite, regular and radially unbounded) if there are constants
and
such that then,
converges to the origin within the ST
. The
is estimated using the following equation: Remark 1. Equations (1) and (2) are the fundamental definitions of fractional-order Caputo derivative and fractional-order Caputo partial derivative. Equations (3) and (4) provide the essential calculation rules for the later calculation of the Caputo derivative. Equations (5) and (6) provide the key tools needed to analyze the anisotropic diffusion term. Equation (7) presents the crucial inequality estimate for the FN convergence problem and the ST can be described using Equation (8). Consider a kind of FOSN with
N vertices, described as follows:
where
,
,
signifies the spatiotemporal state vector of the
ith node and region
is an open bounded domain with a smooth boundary
.
is the interior of region
,
is the boundary of region
. ∇ represents the Hamiltonian operator.
denotes the diffusion coefficient matrix,
.
.
and
are the coefficient matrices.
:
is a continuous vector function and satisfies
.
g stands for the coupling strength.
depicts the internal coupling matrix.
depicts the external coupling matrix,
, where
unless there is no direct link from node
j to node
i.
is the control protocol that is to be devised.
Remark 2. Compared with [7,30,31], the anisotropic diffusion is adequately taken into account in the FOSN (9) using the Hadamard product and Hamiltonian operator, and the diffusion matrix can be non-diagonal or non-square. On the one hand, the diffusion matrix characterizes the spatiotemporal diffusion phenomenon. Therefore, it is required to be diagonal in [7,30,31], indicating that the diffusion weights of each node’s state component for different spatial dimensions should all be the same. However, the above construction is relatively conservative and incompatible with typical spatiotemporal neural networks. On the other hand, if the diffusion matrix is a diagonal matrix, this implies that the number of state components for the network nodes must match the number of spatiotemporal dimensions, resulting in an extraordinary idealized model. Considering these two points, our addressed network aligns more closely with real-life scenarios. Remark 3. It is noteworthy that when the diffusion matrix in FOSN (9) is diagonal, the model can transform into the one considered in [7,30,31]. When the diffusion matrix in an FOSN (9) collapses into a scalar, the model can reduce to the one discussed in [32]. When n is equal to 1 in FOSN (9), the model can revert to the version of the spatiotemporal neural network model in [33]. This proves that the network presented in this paper is more universal. The initial condition and the Dirichlet boundary condition of FOSN (
9) are derived as follows:
The corresponding isolated orbit is provided by the following equation:
where
represents the state vector of the isolated node. The initial condition and the Dirichlet boundary condition is shown as follows:
As per the properties of the Laplacian matrix, the FOSN (
9) can be transitioned into the following:
where
, and
.
In the light of Assumption 1, there must be a gauge transformation matrix
and
. Hence,
, where
, for
and
, for
. Therefore, the FOSN (
13) can be collated as follows:
where
.
Take
for the synchronization error. Using the FOSN (
14) and (
11), the homologous error system can be derived as follows:
where
. The initial condition and Dirichlet boundary condition are given by the following:
Let
,
,
.
Definition 4 ([
40])
. The FOSN (9) and (11) are said to be FTBS provided that there is a constant
, such that
,
for any
.
is regarded as the ST. For simplicity of representation, suppose
.
,
is a column vector.
,
.
,
is a row vector.
,
.
Lemma 6. For
, the following equation transformation is satisfied: Proof. Moreover,
From (17)–(19), one can deduce that
□
Lemma 7. For
, the following can be derived: Proof. Based on Lemma 3 and Lemma 4,
□
Remark 4. Compared to the studies in [7,30,31] concerning spatiotemporal networks with a diagonal diffusion matrix, Lemma 6 establishes an equality transformation for the anisotropic diffusion term, employing the vector’s inner product, the Hadamard product, and the Hamiltonian operator. Based on the matrix–vector relations, this equation transformation reveals a more concise structure and highlights a more integrated understanding of the anisotropic diffusion term at the vector level, facilitating further research into the complex dynamic behaviors of SNs. Remark 5. Based on the trace results, vector straightening operation, Hadamard product, and Hamiltonian operator, Lemma 7 establishes an inequality estimate involving the anisotropic diffusion term in an effective and more compact form, which serves as the basis for the synchronization analysis later.
Remark 6. Notably, when the anisotropic diffusion matrix is diagonal, the conclusions of Lemmas 6 and 7 are in accordance with those in [7,30,31]. In addition, if the anisotropic diffusion matrix becomes a scalar, the results of Lemmas 6 and 7 also match the ones in [32]. More importantly, if
, Lemmas 6 and 7 are compatible with the results for the spatiotemporal neural network model in [33], demonstrating the broader applicability of Lemmas 6 and 7. 4. Numerical Simulations
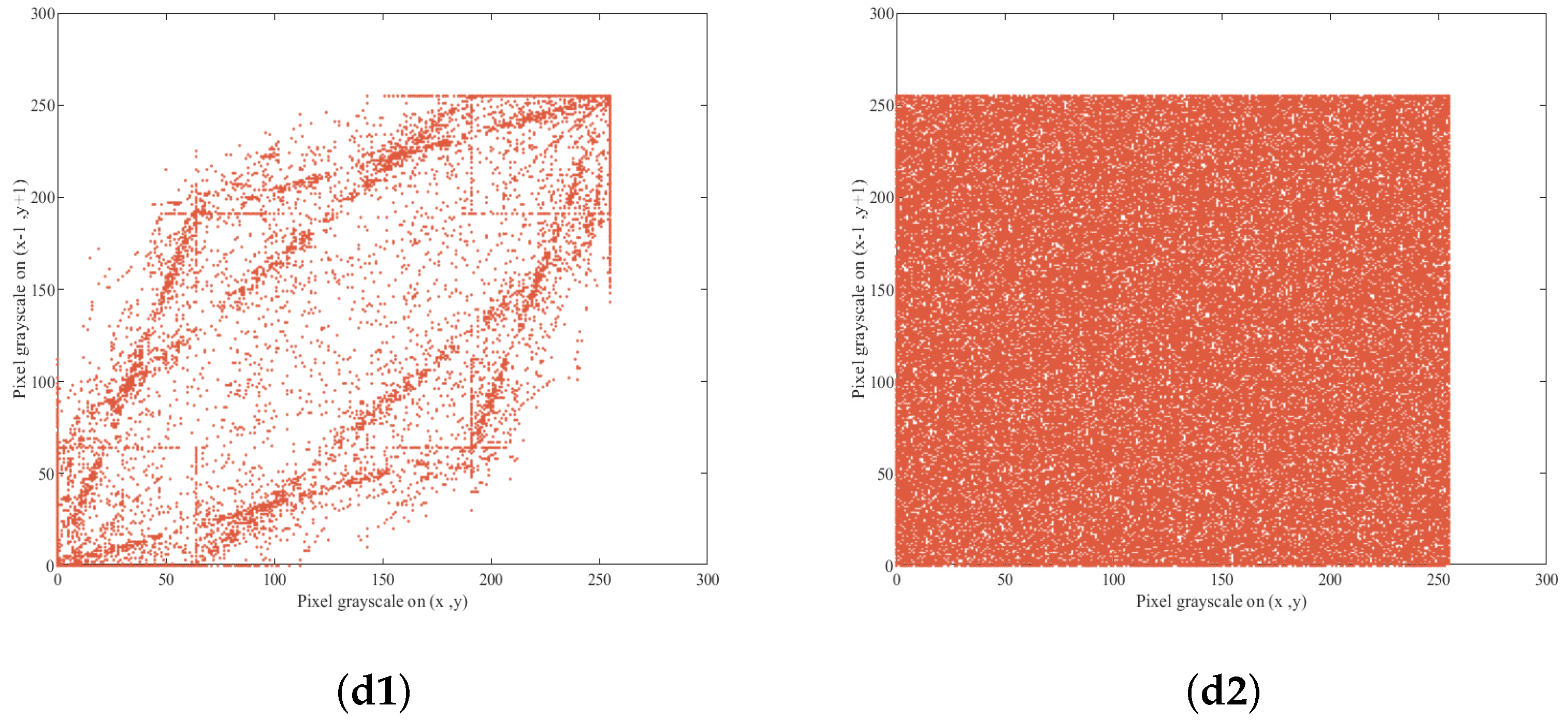
In this section, some numerical experiments are provided to show the feasibility of the proposed control laws for FOSNs. All the simulations took place in the environment of MATLAB R2023a in Intel(R) Core(TM) i7-8750HQ CPU @2.20GHZ, a 64 bit operating system.
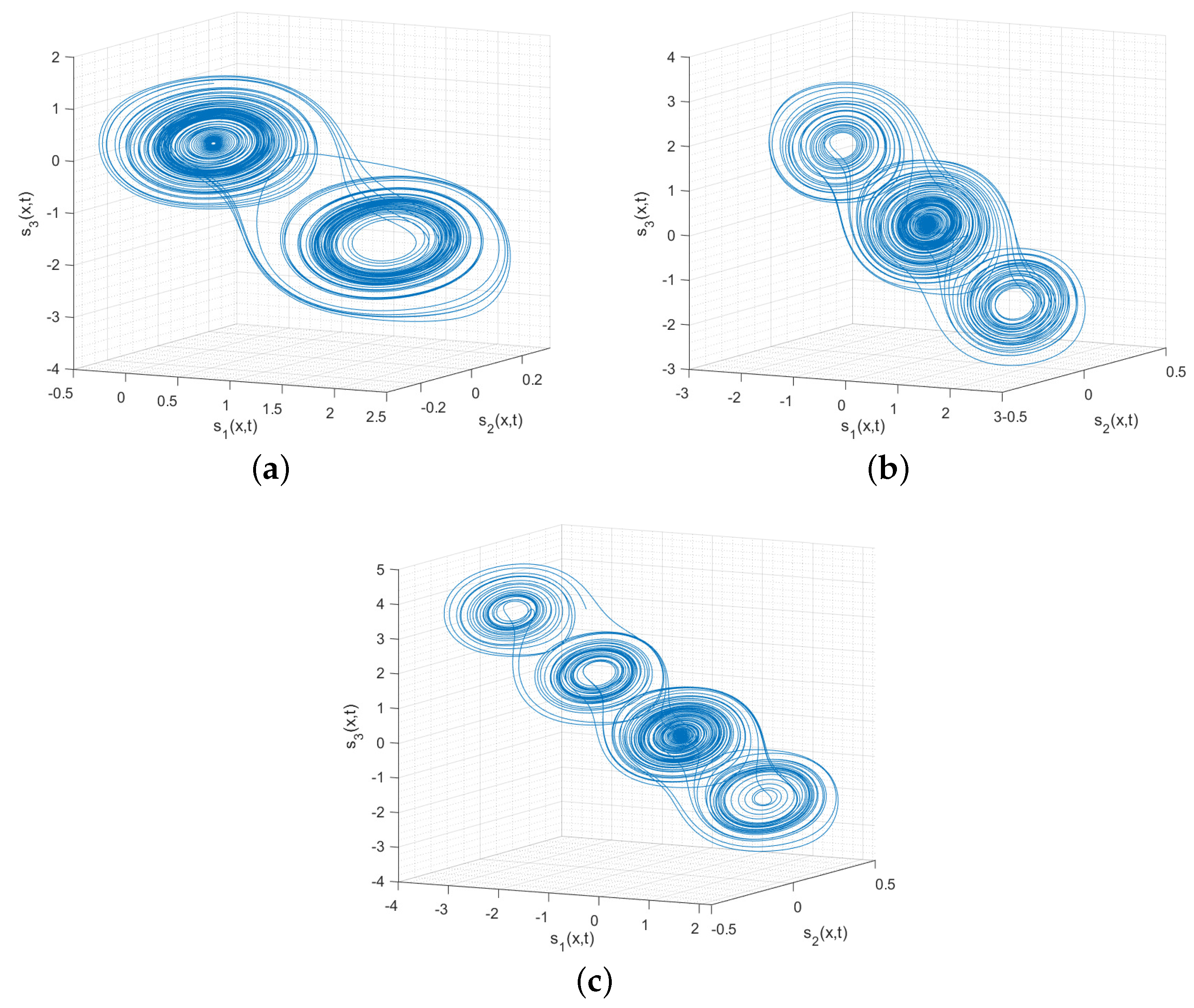
Example 1. Triggered by the improved Chua’s circuit in [43], the following isolated node system is established:where
,
and
,
,
,
,
.
,
. The initial condition is
. The phase portraits of
,
, and
are simulated in Figure 1. When
, the phase trajectory clearly has a 2-scroll chaotic attractor. When
, the phase portrait clearly has a 3-scroll chaotic attractor, and when
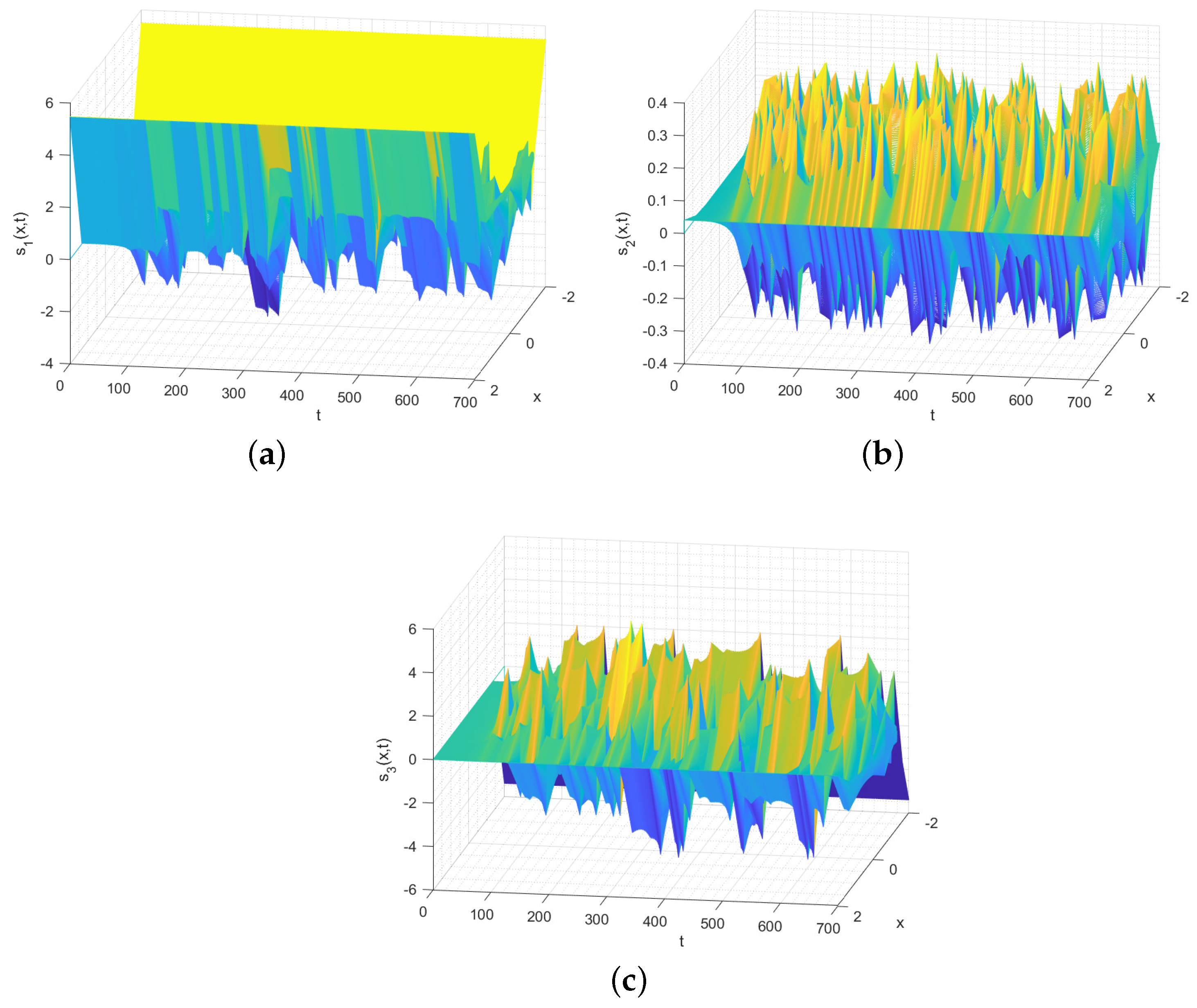
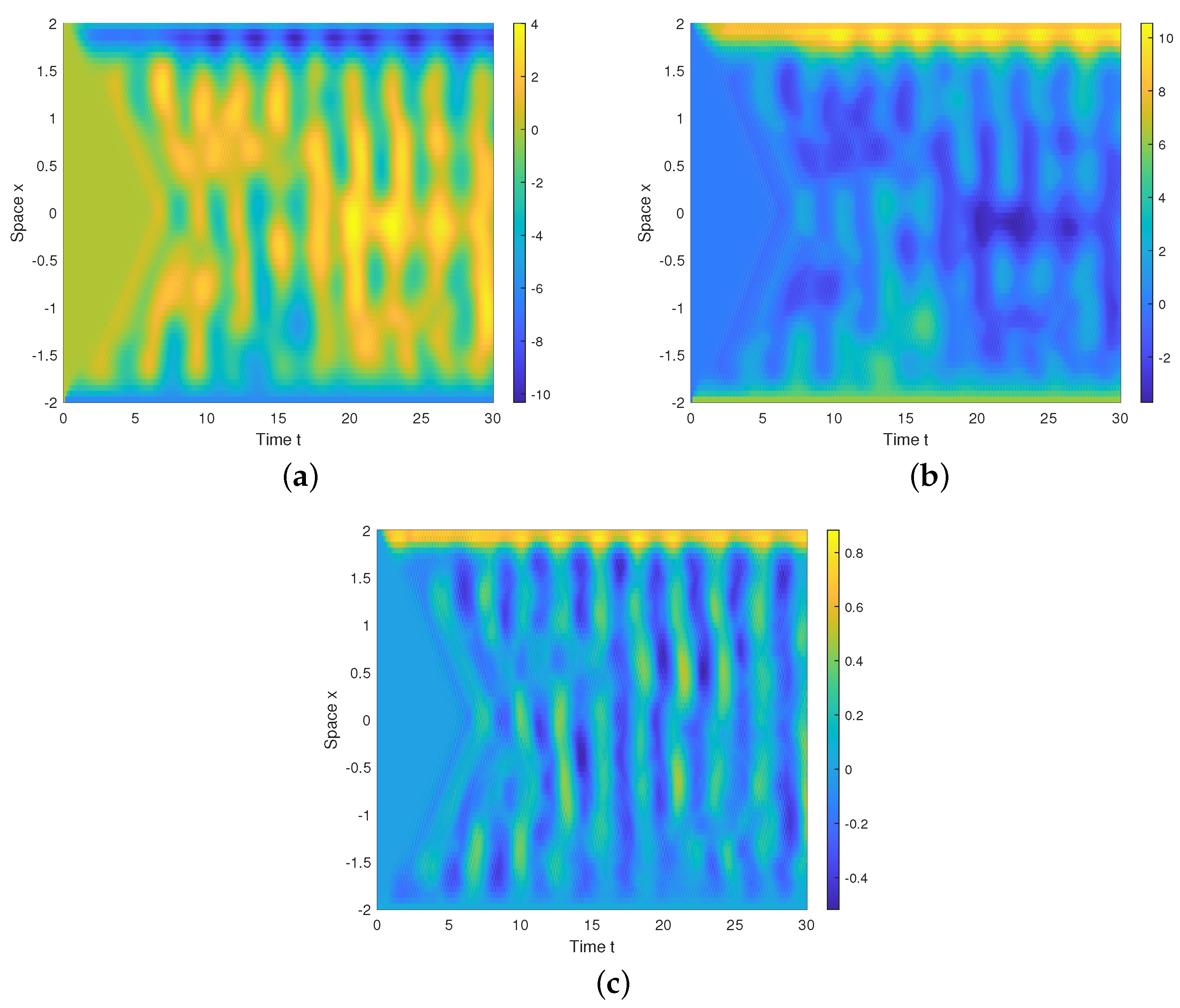
, the phase portrait clearly has a 4-scroll chaotic attractor. It is so interesting that diverse forms of multi-scroll chaotic attractors could be generated from a deterministic system. The spatiotemporal evolutions of
,
and
are simulated in Figure 2. The Turing patterns of
,
and
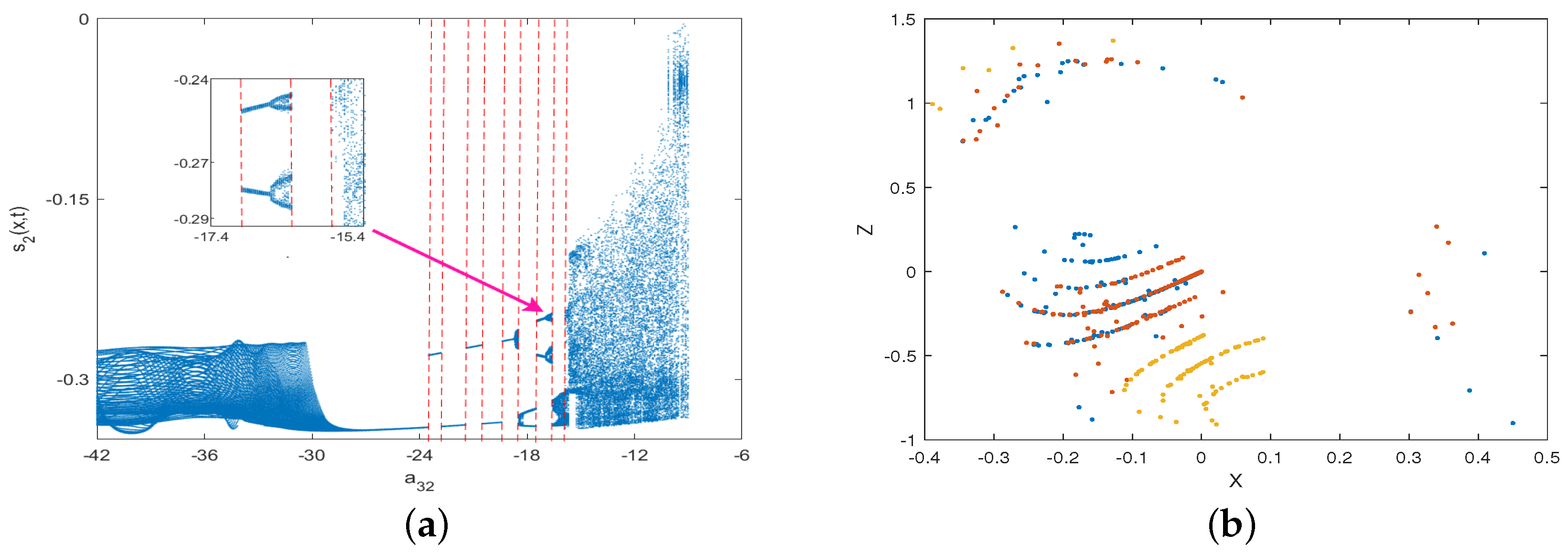
are simulated in Figure 3. The patterns reveal that the system (40) is Turing instability. Figure 4a exhibits the bifurcation diagram with bifurcation parameter
. Following careful observation, the system state undergoes period-1 orbit, period-2 orbit, and period-4 orbit, and ultimately enters a chaotic region. Interestingly, as the system state passes through period-doubling bifurcation routed to chaos, the bifurcation diagram makes some amazing jumps, indicating that the system exhibits complex chaotic behavior. Therefore, it has better resistance to attacks in image encryption and decryption. Furthermore, it is apparent that the system falls in the chaotic region within the parameters of Example 1. Additionally, there are some dense points with fractal structures in the Poincaré map on the plane
in Figure 4b, providing additional evidence that the system is indeed chaotic. This was the primary motivation behind our application of the theoretical results to the image encryption. Remark 11. Based on the analysis of the phase portrait, spatiotemporal evolution, bifurcation diagram, Poincaré map, and Turing pattern, the established system (40) is demonstrated to be a chaotic system with strong chaos properties, which set the basis for applying the obtained synchronization results to image encryption.
Example 2. Consider the following FOSN, with six nodes:where
,
,
,
,
The initial condition is
,
,
,
,
,
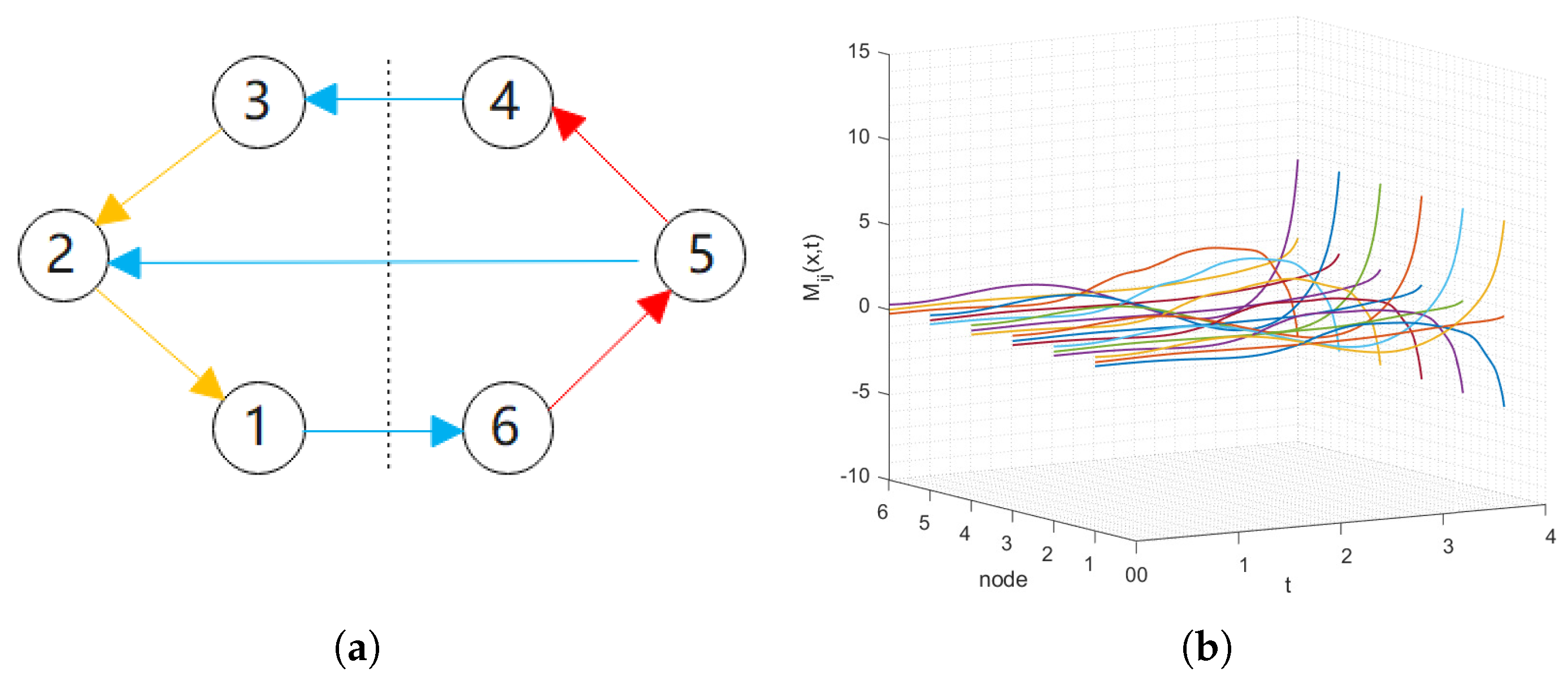
. The network topology of FOSN (41) is depicted in Figure 5a, which indicates that the signed networks are structurally balanced with
, and
. In Figure 5a, the red lines and the yellow lines represent the cooperation relationship by positive weights and the blue lines indicate the competition relationship using negative weights, respectively. The time evolutions of
without control are demonstrated in Figure 5b and the spatiotemporal evolutions are presented in Figure 6 with contour map, indicating that the isolated orbit is not self-stability. Figure 7 represents the states of the systems (40) with FOSN (41), signifying that they cannot achieve bipartite synchronization without control. Then, the parameters of the control protocol (20) are selected as
. The time evolutions of
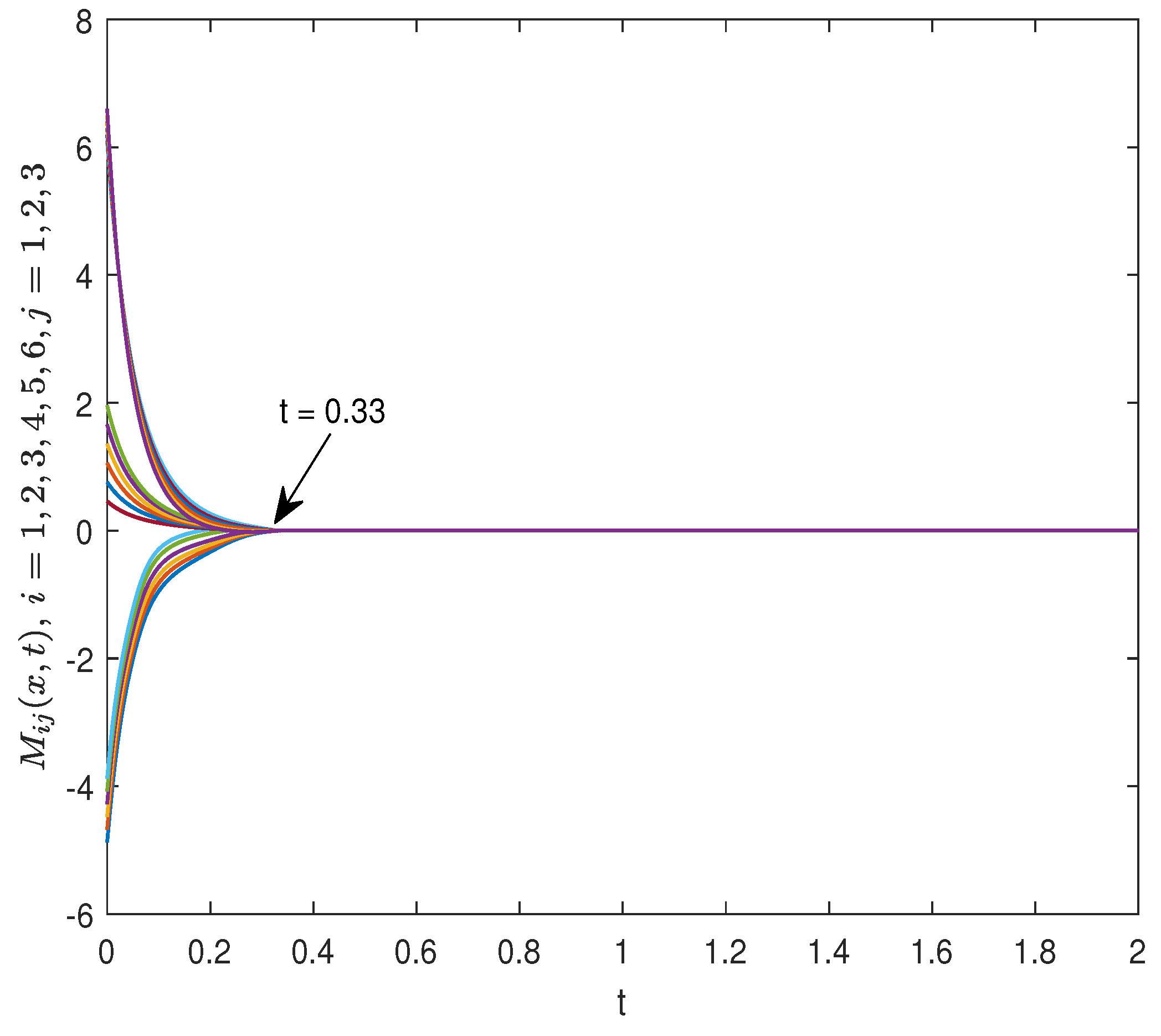
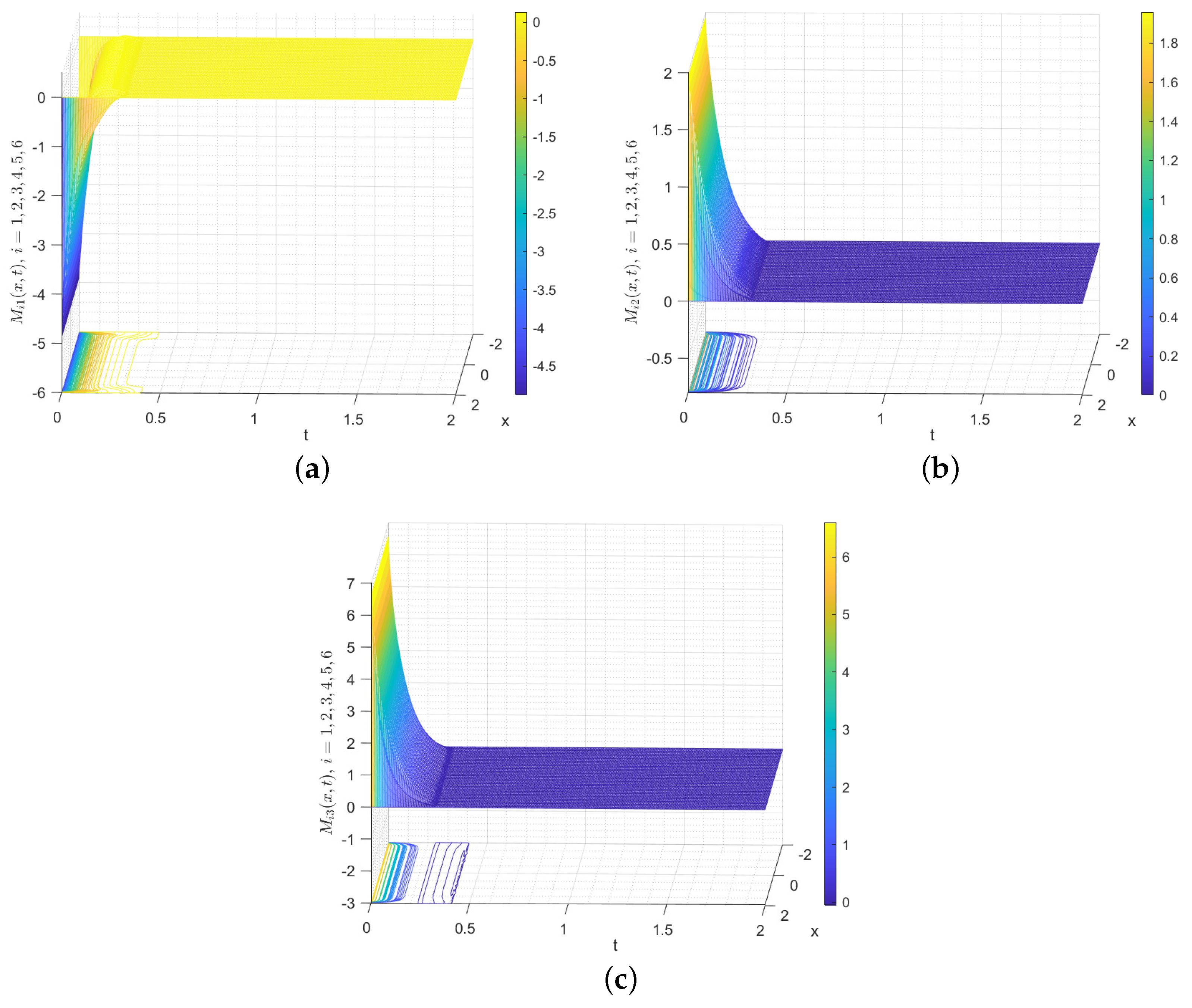
under the control protocol (20) are depicted in Figure 8, which show that
gradually converges to 0 over time. Furthermore, the estimated upper bound for ST is 18.03. However,
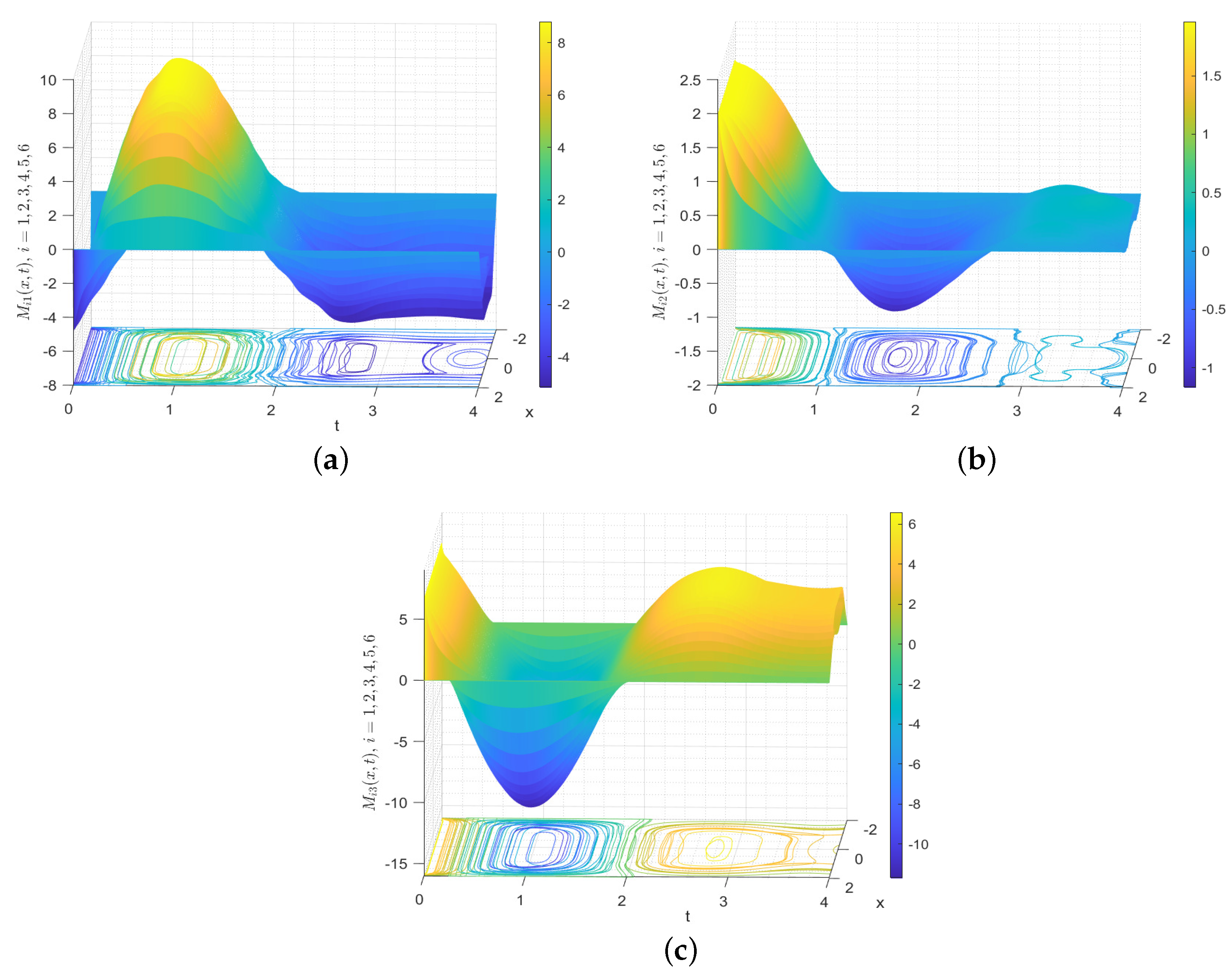
seems to already be very close to zero at 0.33, which indicates that the control protocol (20) deserves further investigation. Figure 9 presents the spatiotemporal evolutions of
with contour map, which make it clear that
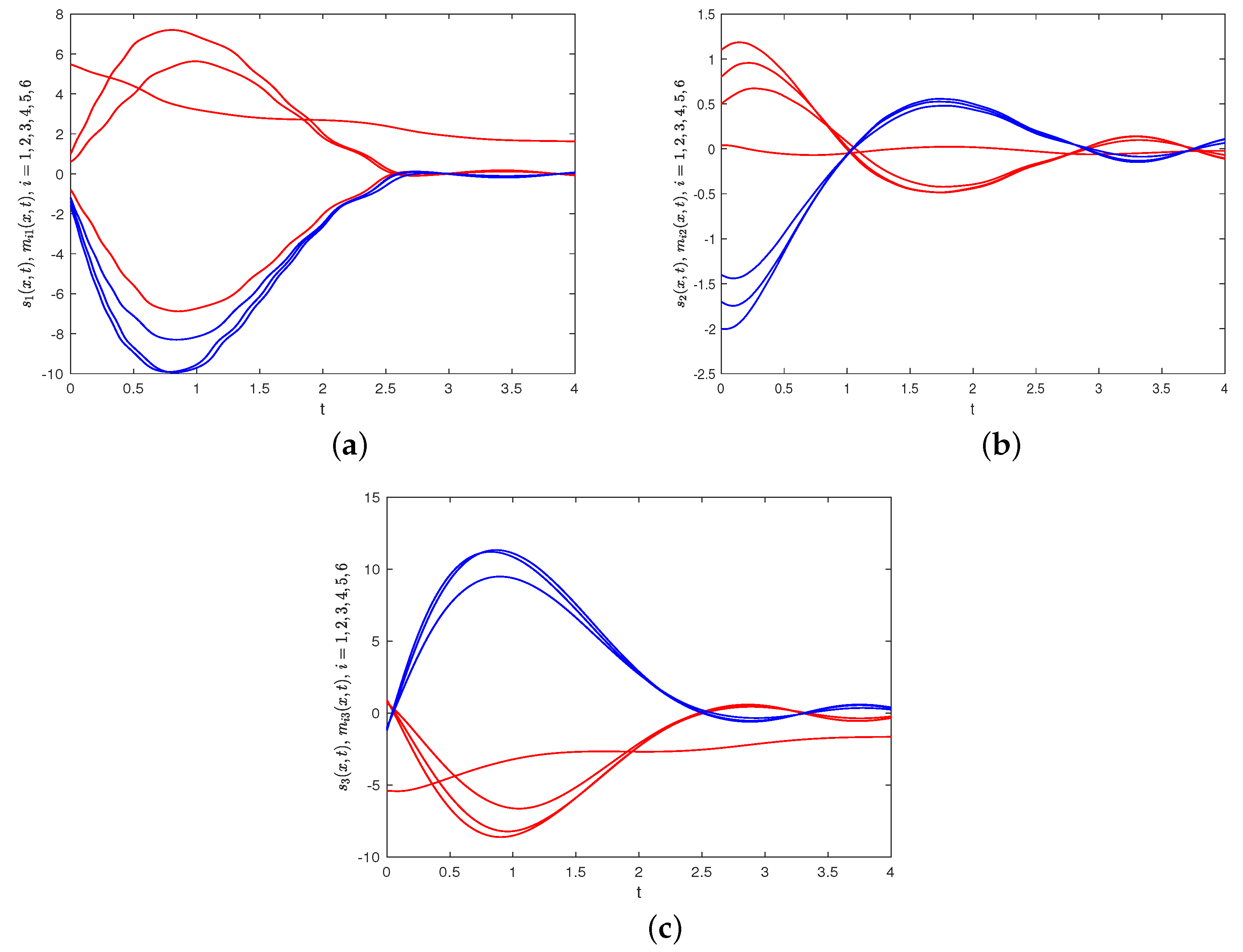
gradually converges to 0 without any alteration in height. The time evolutions for each component of
and
are depicted in Figure 10, which indicate that the states of the network nodes in system (40) and FOSN (41) ultimately achieve BS. Therefore, FNBS is achieved for the system (40) with FOSN (41) which verifies the correctness of the developed control protocol (20).
Example 3. The example will simulate system (40) with FOSN (41) under the HSF control protocol (30) with linear term in Theorem 2.
The parameters of the control protocol (30) were designed as
and the estimated upper bound for ST was 18.03. These parameters were selected to emphasize the excellent control performance of the HSF control protocol in comparison with this method by Algorithm 1.| Algorithm 1 Parameter selection for contrasting control protocol (20) with (30) |
| Input : Controlled system parameters |
| Output : Control parameters |
| START |
| Step 1 : Design identical control gains in linear terms for (20) and (30), meeting the conditions of (21) and (31), respectively; |
| Step 2 : By setting (28) equal to (33), one can obtain the following:
; |
| Step 3 : Using Step 2, one can determine the ST in (29), which is naturally equal to the result in (34) due to Lemma (5). |
| EXIT |
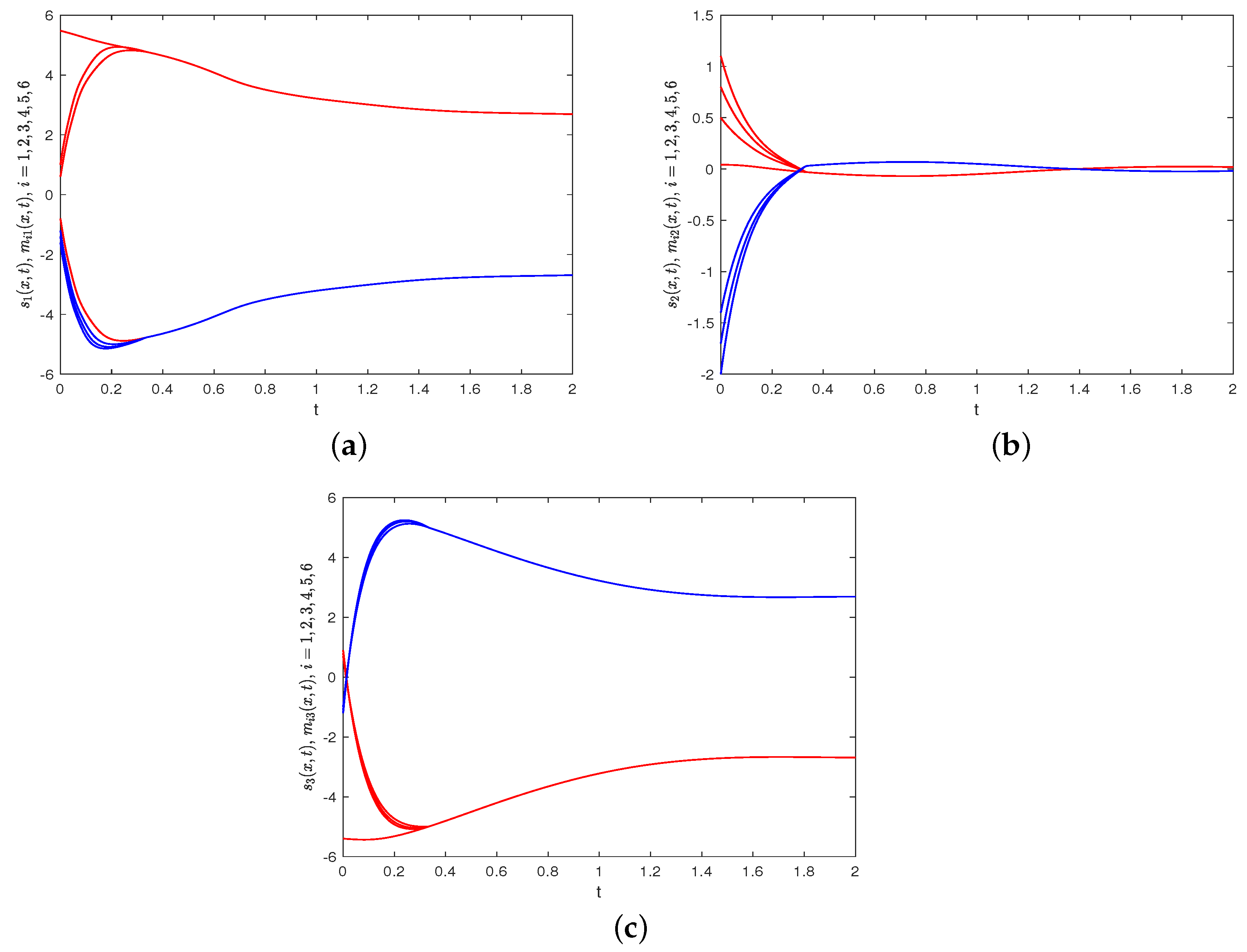
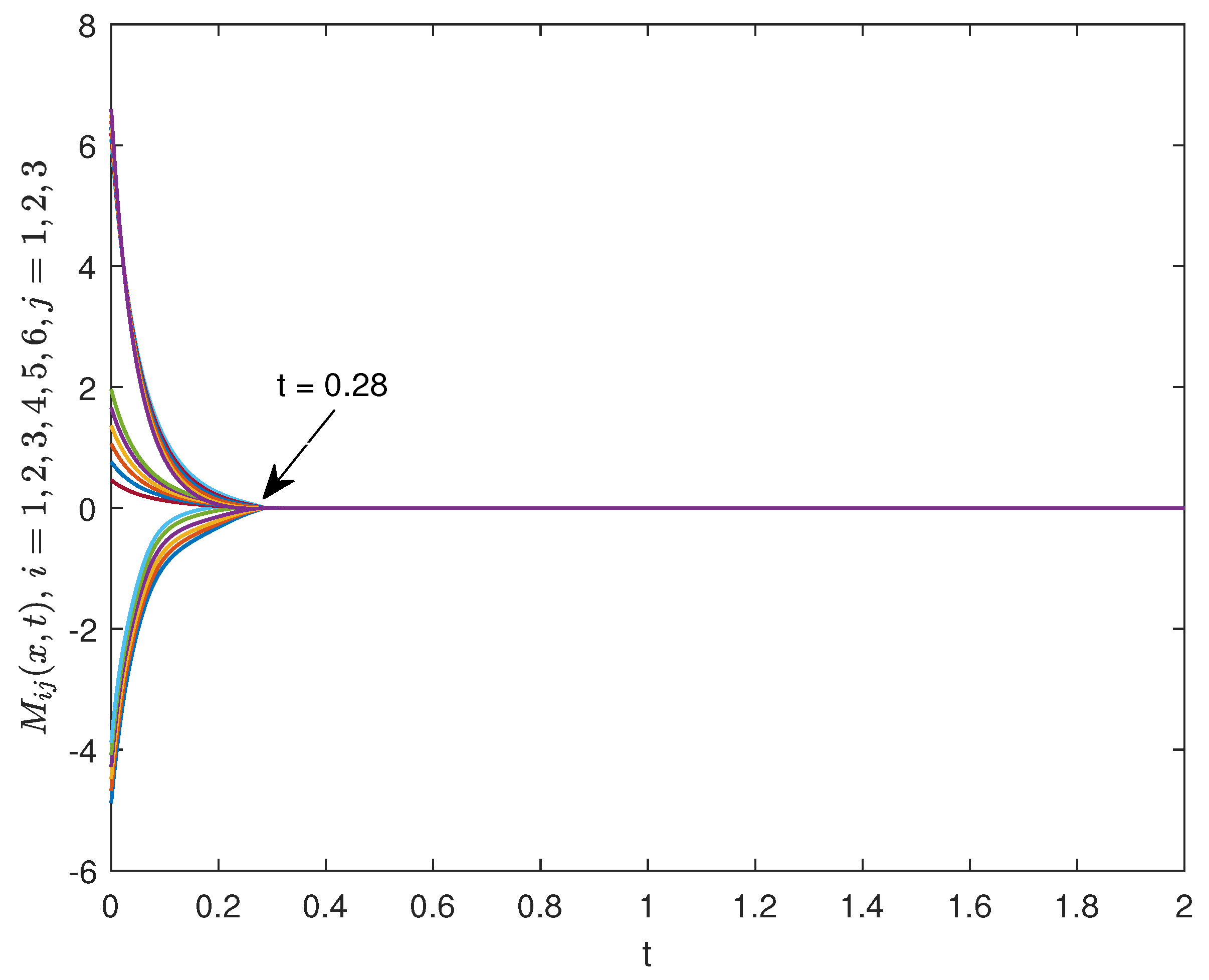
The time evolutions of
under the control protocol (30) are depicted in Figure 11, which show that
gradually converges to 0 as time evolves. Furthermore, the estimated upper bound for ST is 18.03. However, it is worth considering that
seems to already be very close to zero at 0.28, which indicates that the introduction of the HSF had produced positive effect. Figure 12 describes the spatiotemporal evolutions of
with a contour map, which make it clear that
gradually converges to 0 in its spatiotemporal evolution without any alteration in height. The time evolutions of each component of
and
are depicted in Figure 13, which show that the states of the network nodes in system (40) and FOSN (41) ultimately achieve BS. Therefore, FNBS is achieved for the system (40) with FOSN (41), which verifies the correctness of the developed control protocol (30).
Remark 12. In order to make a clearer distinction between the control protocol (20) and (30), specific control parameters were selected according to Algorithm 1, guaranteeing that the estimated STs in (29) and (34) were the same. Also, the theoretical control effects were the same under the identical power-law presented in (28) and (33). As shown in Figure 8 and Figure 11, the error converges more quickly under the control protocol (30), indicating that the introduction of the HSF can reduce the convergence time and strengthen the control performance, which is tremendously significant for practical engineering applications. Example 4. This example will simulate the system (40) with FOSN (41) under HSF control law without linear term in Theorem 3.
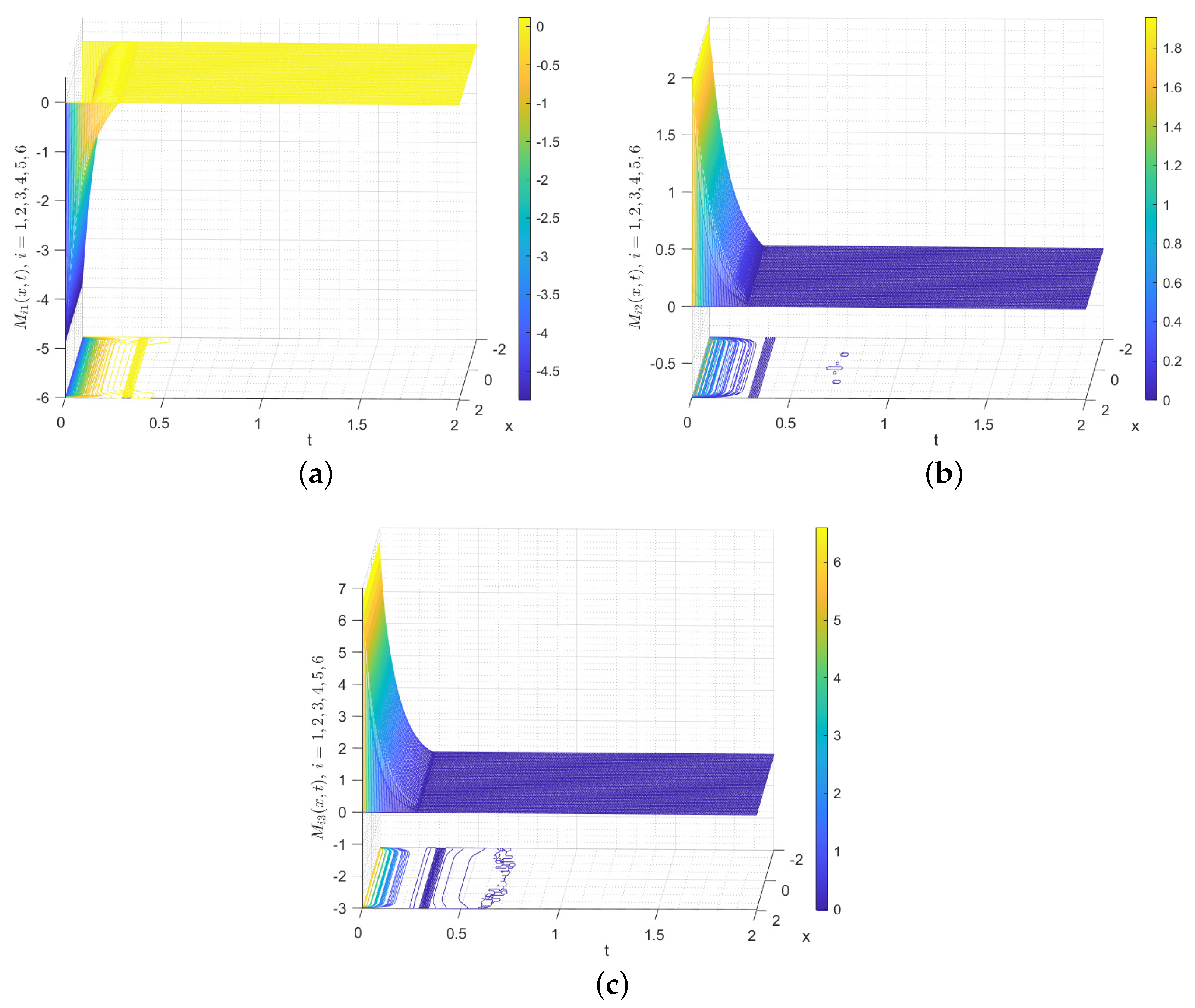
The control parameters of (35) are designed as follows:
. The time evolutions of
under the control law (35) are depicted in Figure 14, which show that
gradually converges to 0. The estimated upper bound for ST is 1.12. Figure 15 describes the spatiotemporal evolutions of
with contour map, which makes it clear that
gradually converges to 0 during its spatiotemporal evolutione without any alteration in height. The time evolution of each component of
and
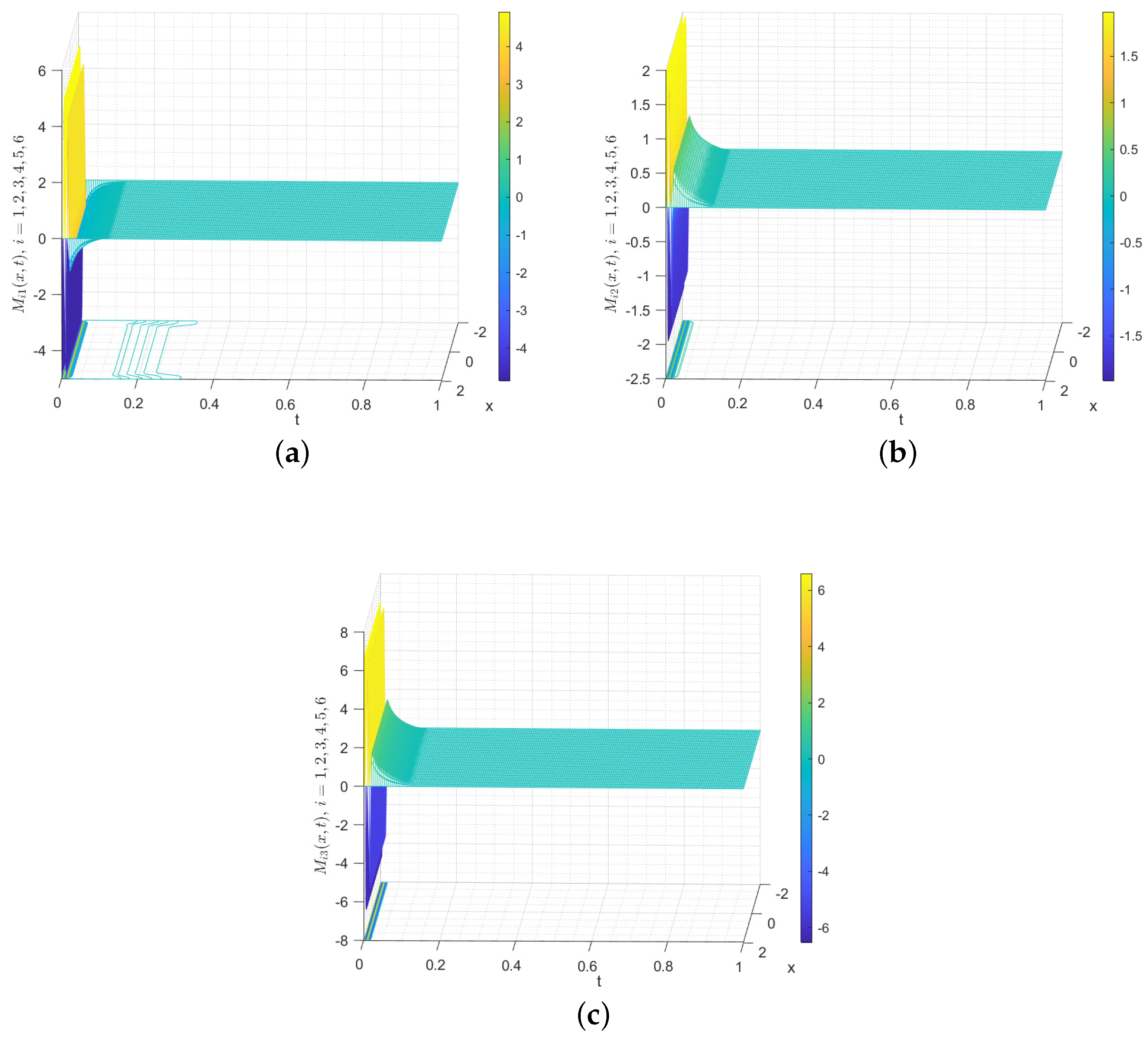
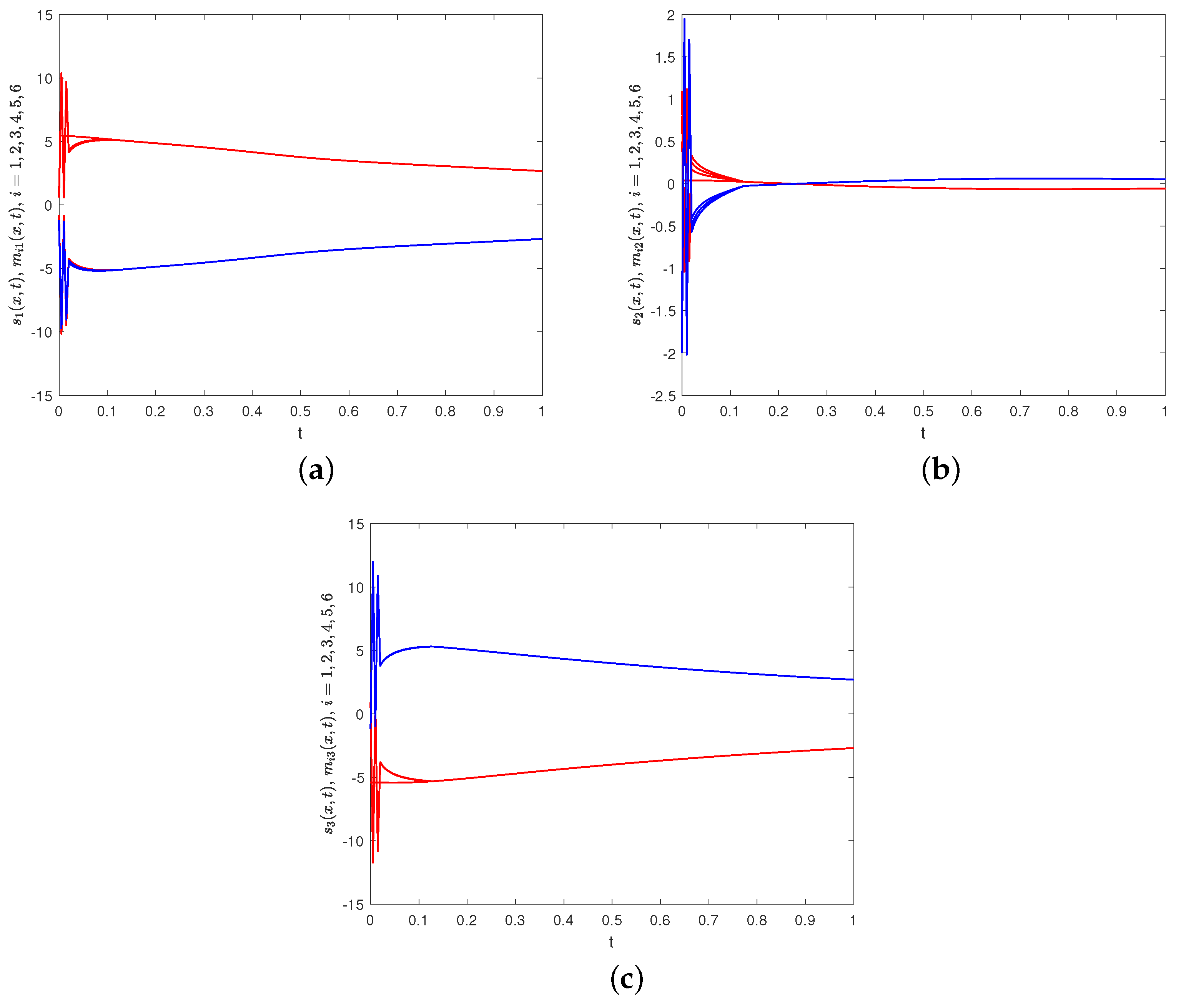
are depicted in Figure 16, which indicate that the states of the network nodes in system (40) and FOSN (41) ultimately achieve BS. Therefore, FNBS is achieved for system (40) with FOSN (41), which verifies the correctness of the developed control law (35).
Remark 13. In contrast to the control protocol (20) in polynomial form and the control protocol (30) which incorporates the linear term as well as the HSF, the control law (35) not only has fewer control parameters and a simpler exhibition without the linear terms, but also effectively reduces the ST (ST (35) < ST (30) < ST (20)) under smaller control gains. The superiority of the control law (35) based on the HSF is attested by its swifter convergence rate, the tighter bound of ST, and the suppression of chattering both in theory and simulations. This is extremely significant in practical applications, especially in engineering problems requiring a high control intensity or rapid control response.
Using the controller designed in [
7]:
.
Figure 17a describes the control inputs of the control law (35) in this work and [
7].
Figure 17b depicts the synchronization error of the control law (35) in this work and [
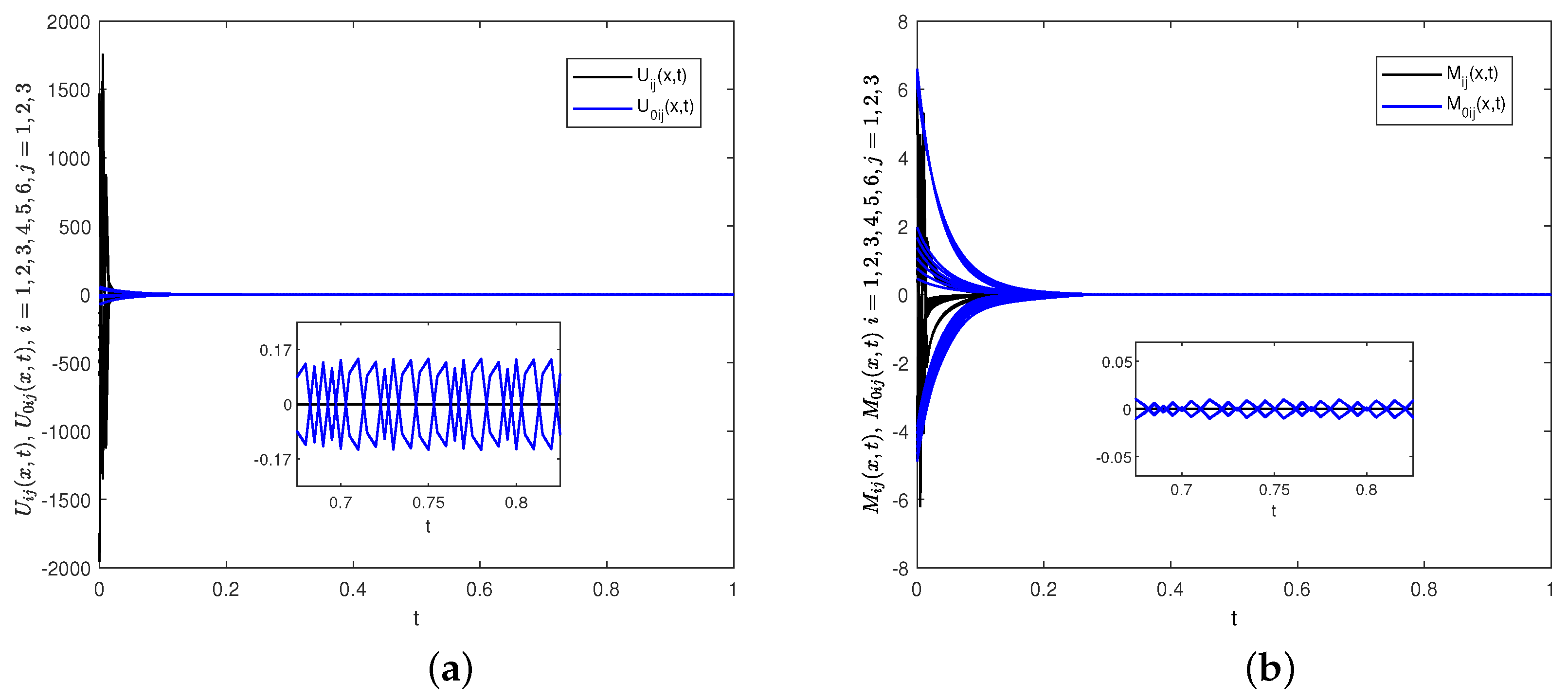
7]. As shown in
Figure 17a,b, the control law (35) effectively avoids chattering, increases the smoothness of the control input, and reduces the ST, which further validates the theoretical analysis results presented in Remark 8.
Example 5. This example will simulate the HSF to explore why it has excellent qualities in terms of its control performance.
The equivalence measure of the HSF
is
, for
.
, for
. The evolutions of
and
are depicted in Figure 18. It indicate that the HSF can provide control inputs at an exponential function level, yielding very noticeable control effects. This elucidates why the the error convergence rate is much faster under the control law (35) compared to the control protocols (20) and (30). Subsequently, we conducted a further analysis for the effectiveness of the control law (35), by applying the methodology of sensitivity analysis. By performing these calculations, one can derive
, where c is a positive constant and
. In other words, the absolute value of the partial derivative of
with respect to σ equals the product of the exponential function and the power function, which shows that parameter σ significantly influences this control effect. The analysis regarding δ was similar, so it will not be shown again here. These results indicate that the control intensity is very convenient to adjust, which is a desired feature in practical scenarios.