Securing Bipartite Nonlinear Fractional-Order Multi-Agent Systems against False Data Injection Attacks (FDIAs) Considering Hostile Environment
Abstract
1. Introduction
- In contrast to [28], our work contributes to the field by integrating delayed controllers to enhance the resilience and effectiveness of multi-agent systems against false data injection attacks.
- The use of false data injection in the dynamics of followers improves the detection and mitigation of such attacks in multi-agent systems, which were not considered in the previous study [17].
- Utilizing fractional-order multi-agent systems can enhance the robustness and accuracy of detecting and mitigating false data injection attacks as compared to [29].
- Section 2: Provide background knowledge about multi-agent systems of fractional order, covering foundational concepts and initial details.
- Section 3: Present the formulation of the main result.
- Section 4: Present the stability analysis of the proposed multi-agent system.
- Section 5: Present practical examples to illustrate the effectiveness of our work.
- Section 6: Present the conclusion of the overall study.
2. Background Knowledge
2.1. Signed Graph Theory
- if
- if
- for any or
- for any and
2.2. Necessary Lemmas and Definitions
- and always
3. Issue Identification
- Follower: agents labeled as ;
- Leaders: agents labeled as .
3.1. Attack Model
3.1.1. Identification of Compromised Agents
3.1.2. Characteristics of Vulnerable Agents
- Connectivity: Agents with high connectivity or central roles in the network might be more vulnerable because compromising them can have a larger impact on the overall system.
- Lack of Security Measures: Agents that lack adequate security measures, such as encryption, authentication, or anomaly detection systems, are easier targets for attackers.
- Resource Constraints: Agents with limited computational resources might not be able to run advanced security algorithms, making them more susceptible to attacks.
- Behavioral Patterns: Agents with predictable or easily detectable patterns of behavior can be targeted more effectively by adversaries.
3.1.3. Attack Strategy Design
- State Update Equation: For any selected subset of compromised agents, agent u will update its state according to the following equation:where represents the false data injected by an adversary.
- False Data Injection: The false data are designed as follows:The term is the concrete attack strategy.
- Attack Space Expansion: The dynamical interaction between agents with m-dimensional states greatly expands the attack space, allowing for more sophisticated and coordinated attack strategies.
3.2. Hostile Interactions in Signed Digraph
3.2.1. Network Structure and Interaction Dynamics
- Node A supports Node B (+);
- Node B opposes Node C (−);
- Node C supports Node D (+);
- Node D opposes Node A (−).
3.2.2. Dynamics of Hostile Interactions
- Feedback Loops: The presence of a negative feedback loop (A → B → C → D → A) introduces instability. Such loops can lead to persistent conflicts, making it difficult for the network to reach a consensus.
- Influence Propagation: If Node A is a key opinion leader, their opposition to Node B can trigger a cascade of antagonistic interactions, polarizing the network and hindering cooperative behavior.
3.2.3. Practical Implications
- System Design: Understanding these hostile interactions helps in designing interventions to promote stability and cooperation, such as targeted conflict resolution strategies or enhanced moderation policies.
- Policy Making: For policymakers, mitigating the effects of negative interactions is crucial in maintaining harmony and functionality in critical infrastructure networks.
4. Stability Analysis of Bipartite Containment Control under FDIA
4.1. Fixed Signed Directed Networks
4.1.1. Control Objective
4.1.2. Detection and Mitigation of FDIA
- Implement residual analysis to detect anomalies in the state trajectories of agents.
- Employ statistical or machine learning-based methods to identify deviations indicative of FDIAs.
4.1.3. Control Design
- Redundancy: Incorporate redundant measurements and control paths to cross-verify data and control actions.
- Observer-Based Techniques: Design observers to estimate the true state of the system, reducing reliance on potentially compromised data.
- Adaptive Control: Implement adaptive control strategies that can adjust control parameters in real time to mitigate the effects of detected attacks.
- Fault-Tolerant Control: Develop control laws that are less sensitive to false data, ensuring system performance even when some agents are compromised.
4.1.4. Control Assumptions
- The set of compromised agents is known or can be estimated.
- The system dynamics B, , and W are accurately known.
- The attack method is either known or can be bounded.
4.1.5. Control Limitations
- High computational complexity of detection and control algorithms.
- Potential trade-offs between robustness and system performance.
- Assumptions on the attack model may not cover all possible FDIA scenarios.
- ;
- , where for any scalar, and .
4.2. Switching Signed Directed Network
- ;
- , where for any scalar, and .
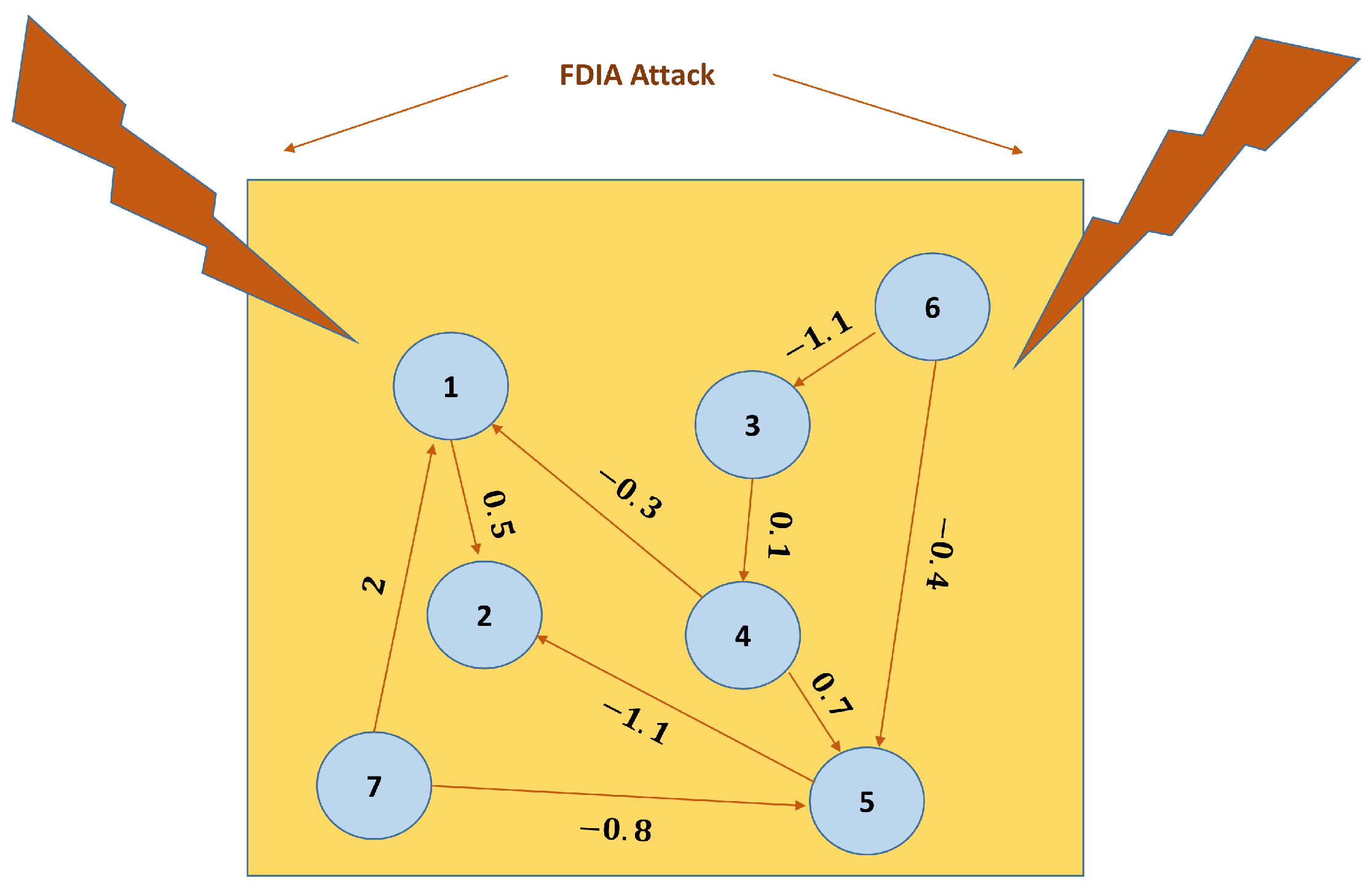
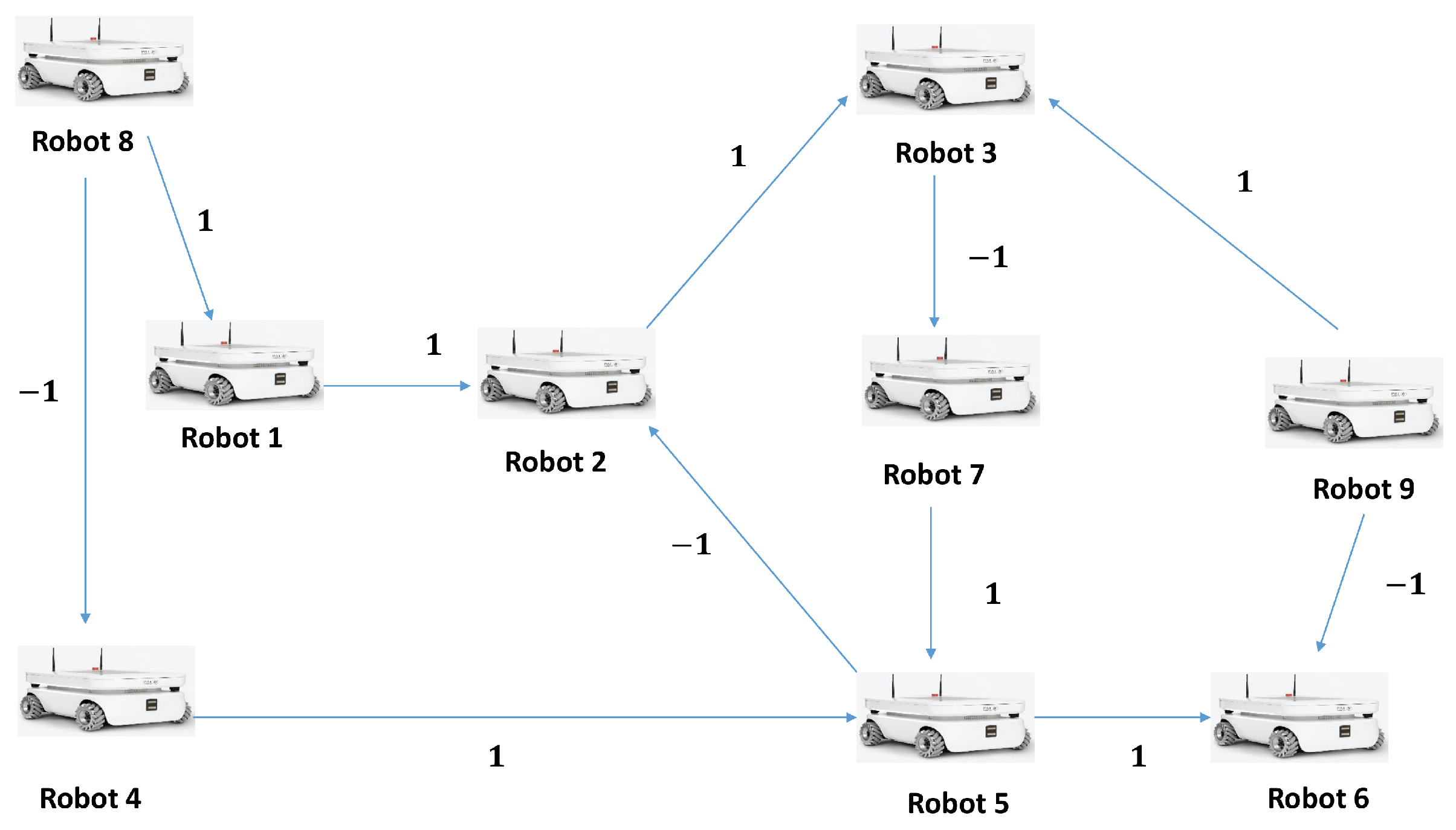
5. Numerical Illustration
Practical Example: Autonomous Warehouse Robots for Task Coordination
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Qu, C.; Sorbelli, F.B.; Singh, R.; Calyam, P.; Das, S.K. Environmentally-aware and energy-efficient multi-drone coordination and networking for disaster response. IEEE Trans. Netw. Serv. Manag. 2023, 20, 1093–1109. [Google Scholar] [CrossRef]
- Ge, X.; Han, Q.L.; Ding, L.; Wang, Y.L.; Zhang, X.M. Dynamic event-triggered distributed coordination control and its applications: A survey of trends and techniques. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 3112–3125. [Google Scholar] [CrossRef]
- Wang, H.; Feng, Y.; Tian, Y.; Wang, Z.; Hu, J.; Tomizuka, M. Towards the Next Level of Vehicle Automation through Cooperative Driving: A Roadmap from Planning and Control Perspective. IEEE Trans. Intell. Veh. 2024, 9, 4335–4347. [Google Scholar] [CrossRef]
- Khan, A.; Hassan, W.U.; Manzor, A.; Ahmed, S.; Niazi, A.U.K. Strengthening stability with centralized event-triggered control system with the disturbances and artificial time delay in wireless connected vehicle platooning (CVSs). Syst. Sci. Control Eng. 2024, 12, 2342818. [Google Scholar] [CrossRef]
- De Tuglie, E.E.; Cagnano, A.; Introna, A.; Montegiglio, P.; Passarelli, A. An Online Cooperative Control Strategy for Enhancing Microgrid Participation into Electricity Market. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4792943 (accessed on 12 April 2024).
- Wang, G.; Sun, W.; Ding, L. Cooperative control of time-delay wind power grid-connected unit under actuator saturation based on Hamiltonian method. Int. J. Electr. Power Energy Syst. 2023, 152, 109188. [Google Scholar] [CrossRef]
- Li, L.; Du, L.; Hu, Y. Cooperative control method of multiple spacecraft formation based on graphtheory. J. Comput. Methods Sci. Eng. 2024, 24, 1237–1251. [Google Scholar] [CrossRef]
- Xv, H.; Sun, Y.; Zhao, Y.; Peng, M.; Zhang, S. Joint beam scheduling and beamforming design for cooperative positioning in multi-beam LEO satellite networks. IEEE Trans. Veh. Technol. 2023, 73, 5276–5287. [Google Scholar] [CrossRef]
- Naderolasli, A.; Shojaei, K.; Chatraei, A. Leader-follower formation control of Euler-Lagrange systems with limited field-of-view and saturating actuators: A case study for tractor-trailer wheeled mobile robots. Eur. J. Control 2024, 75, 100903. [Google Scholar] [CrossRef]
- Zhou, Y.; Zhang, H.; Mu, Y.; Wang, Y. Cooperative Containment Control for Multiagent Systems With Reduced-Order Protocols. IEEE Trans. Cybern. 2023, 54, 3823–3831. [Google Scholar] [CrossRef]
- Xiang, C.; Jing, H.; Changfan, Z.; Xinliang, H.; Miaoying, Z. Fixed time containment control of multi-agent system under multi-source mismatched disturbance. Meas. Control 2024, 57, 794–805. [Google Scholar] [CrossRef]
- Miao, S.; Su, H. Behaviors of matrix-weighted networks with antagonistic interactions. Appl. Math. Comput. 2024, 467, 128490. [Google Scholar] [CrossRef]
- Liu, X.; Zhang, Y.; Xu, Y.; Li, M.; Herrera-Viedma, E. A consensus model for group decision-making with personalized individual self-confidence and trust semantics: A perspective on dynamic social network interactions. Inf. Sci. 2023, 627, 147–168. [Google Scholar] [CrossRef]
- Gu, L.; De Meester, L.; Yang, Z. The role of prey and predator identity in eliciting inducible defenses of Daphnia. Ecology 2023, 104, e4033. [Google Scholar] [CrossRef] [PubMed]
- Yan, L.; Liu, J.; Chen, C.P.; Zhang, Y.; Wu, Z.; Liu, Z. Game-based adaptive fuzzy optimal bipartite containment of nonlinear multi-agent systems. IEEE Trans. Fuzzy Syst. 2023, 32, 1455–1465. [Google Scholar] [CrossRef]
- Błaszczyk, L.; Ćwiek-Kupczyńska, H.; Hoppe Gromadzka, K.; Basińska-Barczak, A.; Stępień, Ł.; Kaczmarek, J.; Lenc, L. Containment of Fusarium culmorum and its mycotoxins in various biological systems by antagonistic Trichoderma and Clonostachys strains. J. Fungi 2023, 9, 289. [Google Scholar] [CrossRef] [PubMed]
- Khan, A.; Niazi, A.U.K.; Rehman, S.; Ahmed, S. Hostile-based bipartite containment control of nonlinear fractional multi-agent systems with input delays: A signed graph approach under disturbance and switching networks. AIMS Math. 2024, 9, 12678–12699. [Google Scholar] [CrossRef]
- Luo, X.; Zhao, C.; Fang, C.; He, J. Submodularity-based false data injection attack scheme in multi-agent dynamical systems. Automatica 2024, 160, 111426. [Google Scholar] [CrossRef]
- Dibaji, S.M.; Pirani, M.; Flamholz, D.B.; Annaswamy, A.M.; Johansson, K.H.; Chakrabortty, A. A systems and control perspective of CPS security. Annu. Rev. Control 2019, 47, 394–411. [Google Scholar] [CrossRef]
- Ren, H.; Cheng, Z.; Qin, J.; Lu, R. Deception attacks on event-triggered distributed consensus estimation for nonlinear systems. Automatica 2023, 154, 111100. [Google Scholar] [CrossRef]
- de Neira, A.B.; Kantarci, B.; Nogueira, M. Distributed denial of service attack prediction: Challenges, open issues and opportunities. Comput. Netw. 2023, 222, 109553. [Google Scholar] [CrossRef]
- Ma, R.; Hu, Z.; Yang, H.; Jiang, Y.; Huo, M.; Luo, H.; Yang, R. Adversarial FDI attack monitoring: Toward secure defense of industrial electronics. IEEE Ind. Electron. Mag. 2023, 18, 48–57. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, H.; Shi, Z.; Gao, Z. Neural-network-based finite-time bipartite containment control for fractional-order multi-agent systems. IEEE Trans. Neural Netw. Learn. Syst. 2022, 34, 7418–7429. [Google Scholar] [CrossRef] [PubMed]
- Yaghoubi, Z.; Talebi, H.A. Cluster consensus of fractional-order non-linear multi-agent systems with switching topology and time-delays via impulsive control. Int. J. Syst. Sci. 2020, 51, 1685–1698. [Google Scholar] [CrossRef]
- Zhang, C.; Qin, J.; Ma, Q.; Shi, Y.; Kang, Y. On containment for linear systems with switching topologies: A novel state transition matrix perspective. IEEE Trans. Cybern. 2020, 52, 1061–1072. [Google Scholar] [CrossRef] [PubMed]
- Yao, X.; Chen, X.; Liu, H.; Sun, L.; He, L. Adaptive sliding-mode synchronization of the memristor-based sixth-order uncertain chaotic system and its application in image encryption. Front. Phys. 2022, 10, 863668. [Google Scholar] [CrossRef]
- Amullen, E.; Lin, H.; Kalbarczyk, Z.; Keel, L. Multi-agent system for detecting false data injection attacks against the power grid. In Proceedings of the 2nd Annual Industrial Control System Security Workshop, Los Angeles, CA, USA, 6 December 2016; pp. 38–44. [Google Scholar]
- Zhang, S.Q.; Che, W.W.; Deng, C. Observer-based event-triggered secure synchronization control for multi-agent systems under false data injection attacks. Int. J. Robust Nonlinear Control 2022, 32, 4843–4860. [Google Scholar] [CrossRef]
- Tahoun, A.H.; Arafa, M. Cooperative control for cyber–physical multi-agent networked control systems with unknown false data-injection and replay cyber-attacks. ISA Trans. 2021, 110, 1–14. [Google Scholar] [CrossRef]
- Troparevsky, M.I.; Seminara, S.A.; Fabio, M.A. A review of fractional differential equations and a numerical method to solve some boundary value problems. In Nonlinear Systems-Theoretical Aspects and Recent Applications; IntechOpen Limited: London, UK, 2019. [Google Scholar]
- Yuan, J.; Chen, T. Observer-based adaptive neural network dynamic surface bipartite containment control for switched fractional-order multi-agent systems. Int. J. Adapt. Control Signal Process. 2022, 36, 1619–1646. [Google Scholar] [CrossRef]
- Huang, Y.B.; He, Y.; An, J.; Wu, M. Polynomial-type Lyapunov–Krasovskii functional and Jacobi–Bessel inequality: Further results on stability analysis of time-delay systems. IEEE Trans. Autom. Control 2020, 66, 2905–2912. [Google Scholar] [CrossRef]
- Liu, S.; Yang, R.; Zhou, X.F.; Jiang, W.; Li, X.; Zhao, X.W. Stability analysis of fractional delayed equations and its applications on consensus of multi-agent systems. Commun. Nonlinear Sci. Numer. Simul. 2019, 73, 351–362. [Google Scholar] [CrossRef]
- Hu, J.; Yu, J.; Cao, J. Distributed containment control for nonlinear multi-agent systems with time-delayed protocol. Asian J. Control 2016, 18, 747–756. [Google Scholar] [CrossRef]
- Ahsan, M.; Ma, Q. Bipartite containment control of multi-agent systems. In Proceedings of the 2019 IEEE/ASME International Conference on Advanced Intelligent Mechatronics (AIM), Hong Kong, China, 8–12 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 895–900. [Google Scholar]
- Liu, S.; Yang, R.; Li, X.; Xiao, J. Global attractiveness and consensus for Riemann–Liouville’s nonlinear fractional systems with mixed time-delays. Chaos Solitons Fractals 2021, 143, 110577. [Google Scholar] [CrossRef]
- Yang, R.; Liu, S.; Li, X.; Zhao, X.W.; Pan, G. Consensus of fractional-order delayed multi-agent systems in Riemann–Liouville sense. Neurocomputing 2020, 396, 123–129. [Google Scholar] [CrossRef]





Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Louati, H.; Rehman, S.; Imtiaz, F.; AlBasheir, N.A.; Al-Rezami, A.Y.; Almazah, M.M.A.; Niazi, A.U.K. Securing Bipartite Nonlinear Fractional-Order Multi-Agent Systems against False Data Injection Attacks (FDIAs) Considering Hostile Environment. Fractal Fract. 2024, 8, 430. https://doi.org/10.3390/fractalfract8070430
Louati H, Rehman S, Imtiaz F, AlBasheir NA, Al-Rezami AY, Almazah MMA, Niazi AUK. Securing Bipartite Nonlinear Fractional-Order Multi-Agent Systems against False Data Injection Attacks (FDIAs) Considering Hostile Environment. Fractal and Fractional. 2024; 8(7):430. https://doi.org/10.3390/fractalfract8070430
Chicago/Turabian StyleLouati, Hanen, Saadia Rehman, Farhat Imtiaz, Nafisa A. AlBasheir, Afrah Y. Al-Rezami, Mohammed M. A. Almazah, and Azmat Ullah Khan Niazi. 2024. "Securing Bipartite Nonlinear Fractional-Order Multi-Agent Systems against False Data Injection Attacks (FDIAs) Considering Hostile Environment" Fractal and Fractional 8, no. 7: 430. https://doi.org/10.3390/fractalfract8070430
APA StyleLouati, H., Rehman, S., Imtiaz, F., AlBasheir, N. A., Al-Rezami, A. Y., Almazah, M. M. A., & Niazi, A. U. K. (2024). Securing Bipartite Nonlinear Fractional-Order Multi-Agent Systems against False Data Injection Attacks (FDIAs) Considering Hostile Environment. Fractal and Fractional, 8(7), 430. https://doi.org/10.3390/fractalfract8070430








