1. Introduction
Fixed-point theory occupies a prominent position in both pure and applied mathematics, owing to its numerous applications in areas such as differential and integral equations, variational inequalities, approximation theory, equilibrium problems, fractal generation, and many others.
The Banach contraction theorem, introduced by Banach in 1922, is one of the fundamental results in fixed-point theory. This theorem guarantees the existence and uniqueness of fixed points for contraction mappings in metric fixed-point theory. Additionally, it allows various iterative schemes to converge to a fixed point. The theorem has also become a widely used method for solving existence problems in many mathematical fields.
While there have been numerous studies regarding fixed points of contractive maps, such as those discussed in [
1,
2,
3,
4], relatively little research has focused on the convergence of iterative approximations to these common fixed points.
When it comes to approximating fixed points, the well-known Banach contraction theorem employs the Picard iteration method. However, in many cases, obtaining the exact solution to a fixed-point problem is infeasible. Hence, as a result, a wide range of iterative algorithms have been developed and studied for approximating solutions to fixed-point problems [
5,
6,
7,
8,
9,
10,
11,
12,
13,
14].
The investigation of iterative methods for approximating fixed points using various types of self-mappings has gained significant attention in recent years. Researchers have introduced several iterative schemes and studied their qualitative features, including convergence, stability, and data dependency. However, non-self-mappings are typically more intricate than self-mappings and are therefore often overlooked in many cases [
5,
6,
7].
Jungck introduced the Jungck iteration scheme [
15] to approximate the fixed points for the non-self-mapping
,
where
is a Banach space and
is an arbitrary set such that
satisfies the following Jungck contraction:
In 2005, the Jungck–Mann iteration scheme and its stability for two contractive maps were first presented and discussed by Singh et al. [
12]. Within this framework, Olatinwo and Imoru [
8] and Olatinwo [
16,
17] introduced the Jungck–Ishikawa and Noor iteration schemes and exhibited how their convergence could be utilised for pairs of some generalized contractive operator for approximating the common fixed point. Chugh and Kumar [
9] presented the Jungck–SP iterative scheme, which is defined as follows:
where
are in
.
Nawab Hussain et al. [
10] presented the Jungck–CR scheme and used the more general contractive condition of Olatino [
16] to prove the stability, data dependency, and convergence of the Jungck–CR iterative scheme. The general contractive condition of Olatino [
16] is defined as follows:
Let
be a real number and let
be a monotone function such that
. If, for all
belongs to
A, we have
The Jungck–CR iterative scheme is defined by the sequence
where
and
are sequences of positive numbers in
.
Motivated by the above literature, we propose the following Jungck type iterative scheme. For
we have
which we call the Jungck–DK iterative scheme.
In this paper, we present the Jungck–DK iterative scheme for analyzing the convergence and stability of a non-self-mapping in a normed linear space. Our work is motivated by previous research in the field. To demonstrate the superior convergence rate of the Jungck–DK iterative scheme compared to other Jungck-type iterative schemes, we provide an example. Additionally, we prove data dependence results. In the final section, we showcase the practical application of the Jungck–DK iterative scheme by generating Mandelbrot and Julia sets of polynomial functions for visualizing images on both sets.
3. Convergence, Data Dependence, and Stability in an Arbitrary Banach Space
This section deals with the convergence, stability, and data dependence of the Jungck–DK iterative scheme.
Theorem 1. Let be an arbitrary set of an arbitrary Banach space and let there be two non-self-operators , which satisfy the condition (3). Consider , where is a complete subspace of and (say). For a sequence is the sequence of the Jungck–DK iterative scheme defined by (5), where , with satisfying . Then, the scheme (5) converges strongly to . Moreover, if with and satisfy the weak compatibility property, then is also a unique common fixed point of both operators.
Proof. In the beginning, we demonstrated that the Jungck–DK iterative scheme (5) converges to , where is a fixed point of and .
From (10) and (9), we have
Replacing (11) in (8) we obtain
From Equation (6), we obtain
Since
and
, therefore,
As a result, it follows from (14) that
Consequently,
Next, our claim is to show that
is a unique common fixed point of
and
. We consider that
is also a coincidence point. Then, there is
such that
. However, according to (3), we have
which means that
as
Since and are weakly compatible with (so and hence ), is a point of coincidence of and , which is unique. Then, . Thus, , and both and shared a unique fixed point . □
The next result deals with the stability of the Jungck–DK-type iterative scheme (5).
Theorem 2. Let , and satisfy all the hypotheses and requirements of Theorem 1. Then, the Jungck–DK scheme (5) is -stable.
Proof. Suppose there is an arbitrary sequence , for where and . Let
Then, from the Jungck–DK iterative scheme (5), we have
Putting (17) & (16) in (15), we obtain
Using that
and
, we have
Hence, using Lemma 1 implies
Conversely, let us consider that
. Then, using the condition (3) and the triangular inequality, we have
From (17) & (16), we obtain
Hence, ⇒ the Jungck–DK scheme is - stable. □
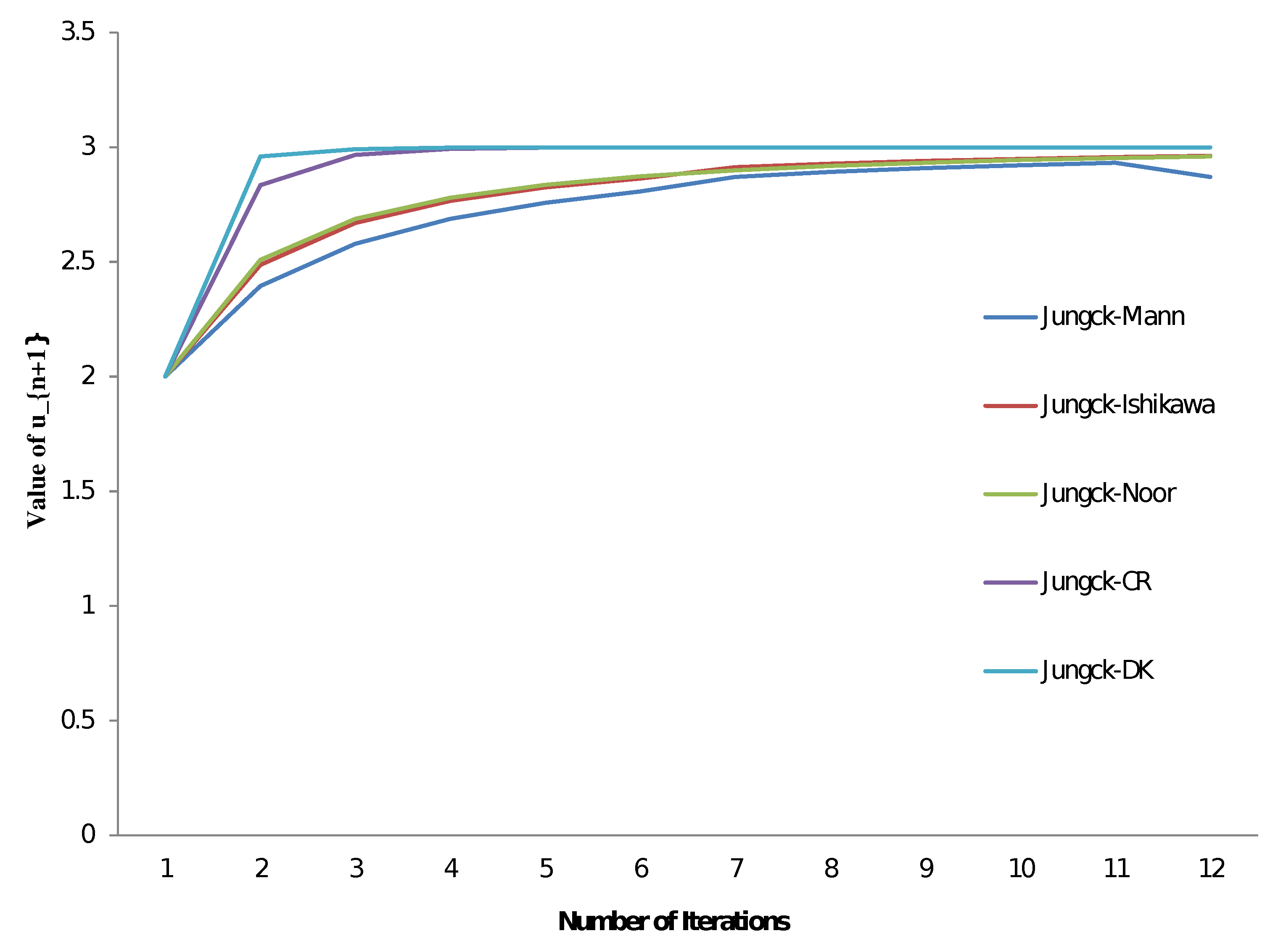
In the next theorem, we will compare the convergence behaviour of the Jungck–DK-type iterative scheme (5) with the Jungck–CR-type iterative scheme, which converges faster than all Jungck-type (Picard, Mann, Ishikawa, Noor, S, and SP) iterative schemes.
Theorem 3. Let , and satisfy all the hypotheses of Theorem 1. For , the Jungck–DK scheme (5) converges faster than the Jungck–CR scheme (4) to a fixed point
Proof. Let
(say). By using the contractive condition (3), and from the iterative scheme of Jungck–CR [
10], we have
Additionally, from Theorem 1 of the Jungck–DK iterative scheme, we have
Since
,
. Hence, from (18), we have
In conclusion, the Jungck–DK iterative scheme converges faster than the Jungck–CR scheme. □
The previous Theorem 3 can be demonstrated by the following example.
Example 1. Consider such that and It is not difficult to remark that and are two quasi-contractive operators accomplishing the (3) condition, with 9 as their coincidence point. Take as the initial approximation; then, with and , we construct Table 1. Studying the table, we can observe the convergence of the various Jungck0type schemes to the same point Remark 1. We find that the Jungck–DK iterative scheme converges to the coincidence point in just 8 iterations, while the Jungck–Mann iterative scheme takes 229 iterations to obtain the same results. Similarly, the Jungck–Ishikawa iterative scheme takes 205 iterations, the Jungck–Noor iterative scheme takes 200 iterations, and the Jungck–CR iterative scheme takes 10 iterations. Figure 1 provides a visual representation of our convergence comparisons. Now, let us give a data dependence result for the Jungck–DK scheme.
Definition 5. Let be an arbitrary set of an arbitrary Banach space and let be two non-self-operator pairs such that and . The pair is called an approximative operator pair of if, for every and some fixed and , we have Theorem 4. Let be a Banach space, such that satisfies condition (3), where and . is a complete subset of . Assume that there exists a and such that and Let be an iterative sequence (5) with satisfying , and let be a sequence defined by Assume that and converge to and . Then, we have , where .
Proof. Using the iterative sequence (5), the iterative scheme (19), the condition (3), and Definition 5, we obtain
It is easy to show that
, which implies
Next, we consider the following estimation:
From (25) and (24), replacing (23), we obtain
Putting (26) and (22) in (21), we obtain (27), as follows:
Putting (27) in (20), we obtain
Here, .
Taking the limit on both sides, it can be seen that
Hence, using Lemma 2, we obtain
which completes the proof. □
4. Escape Criteria for Complex Fractal Generation
The iterative process of a complex function
is a frequently used method for producing fractal patterns on the complex plane
where
depends on some constants and a point
from an area of the complex plane considered [
23]. The Mandelbrot and Julia sets are two of the most well-known and extensively studied examples of fractals generated by the iterative processes of a complex function.
Benoit Mandelbrot [
24] introduced the Mandelbrot set in the 1970s, while Pierre Fatou [
25] and Gaston Julia [
25] independently created the Julia set in the early 20th century. The Julia set was initially introduced by [
26].
During his time at IBM, Mandelbrot became interested in the iterative process of complex functions and studied the works of other mathematicians in the field. He specifically explored the behavior of the Julia sets generated by the function
, and from these studies, he was able to construct the Mandelbrot set. The resulting fractal was so remarkable that Mandelbrot was astonished by its beauty and complexity [
27,
28].
Since then, a multitude of researchers have investigated various properties of the Mandelbrot and Julia sets and proposed several generalizations. One of the earliest and most apparent generalizations involved replacing Mandelbrot’s quadratic function with the
function [
29] therein.
Fixed-point theory has been instrumental in the study of the Mandelbrot and Julia sets, which are two of the most prominent examples of fractals generated by the iterative process of a complex function. Over time, mathematicians have developed several generalizations of these sets, including the use of different iteration methods derived from fixed-point theory. These techniques have been utilized to generalize Julia and Mandelbrot sets [
30,
31,
32,
33,
34].
In this study, we introduced the Jungck–DK iterative scheme to investigate complex fractals such as Julia sets and Mandelbrot sets. To extend the feedback process utilized in generating these sets, we propose a novel escape criterion for the Jungck–DK iterative scheme applied to p-degree complex polynomial functions. Our proof is also applicable to complex polynomials , where .
The following are the basic definitions for this section.
Definition 6 (Julia Set).
Let be a polynomial function that depends on . The filled Julia set of the function is defined aswhere is the n-th iteration of the function . The Julia set of the function is defined as the boundary of i.e., = .
Definition 7 (Mandelbrot Set).
For any polynomial function , the Mandelbrot set M is the set of all parameters c for which the Julia set is filled, i.e.,The Mandelbrot set can also be described in the ways below: where is any critical point of i.e.,
The escape time algorithm is used by most scientists to make pictures of Julia and Mandelbrot sets. In the algorithm, the colour of each point is related to the iterations needed to figure out if the orbit sequence tends to infinity or not. The escape criterion is what we use to decide if the orbit escapes or not. For example, for the classic Mandelbrot and Julia sets, which are defined by
, the escape criteria is the following: if there is some
such that
The part of (31) on the right is called the escape threshold (or bailout value). The threshold value used in determining whether an orbit sequence has escaped is a critical factor in the creation of Mandelbrot and Julia sets. This value may vary for each function and plays a significant role in determining the overall appearance of the fractal.
Escape time algorithms are commonly used in the generation of Mandelbrot and Julia sets. Algorithm 1 represents the escape time algorithm for creating the Mandelbrot set, while Algorithm 2 depicts the corresponding method for generating Julia sets. These algorithms rely on the determination of the number of iterations needed for the orbit sequence of each point to escape, which is then used to assign a color value to the corresponding point on the fractal.
In fixed-point theory, there are many theorems and ways to find the fixed points. Iteratively drawing closer to fixed points is the main idea behind this theory. We use iterative processes of the Jungck–DK (5) type, as in the following:
| Algorithm 1: Generation of a Mandelbrot set. |
| Require: A polynomial function , with area , K no of iterations, where and are fixed parameters, and colormap[0..] is a colormap with C colors. |
| Ensure: Mandelbrot set for the area |
| For
do |
| R= Calculate escape threshold |
|
| critical point of |
| While
do |
|
|
|
| If
|
| break |
|
| else if |
|
| colour with |
| end for |
| Algorithm 2: Generation of Julia set. |
| Require: A polynomial function , with an area , where K represents the number of iterations, and are fixed parameters, and colormap[0..]is a colormap with C colors. |
| Ensure: Mandelbrot set for area |
| For
do |
| R= Calculate escape threshold |
|
| critical point of |
| Whiledo |
|
|
|
| If
|
| break |
|
| else If |
|
| colour with |
| end for |
It is worth noting that the Jungck–DK iteration is distinct from the previously mentioned iterations, such as the Picard, Jungck–Mann, Jungck–Ishikawa, Jungck–Noor, or Jungck–CR iterations. As such, applying the Jungck–DK iteration leads to the generation of a completely novel orbit, resulting in the creation of a new fractal set with unique characteristics.
In the case of the Jungck–DK iteration, there are two mappings involved, which means that the number of mappings used in the iteration must be taken into consideration when replacing the Picard orbit with the Jungck–DK orbit. To address this, we follow a specific procedure.
Let be a polynomial function. We can break down into two mappings, and , such that and is an injective function. In addition to this reconstruction, a new escape criterion for the mappings and Equation (32) must also be derived.
The escape criterion for a specific class of polynomials, namely , can be presented as follows.
Let , where and . To reconstruct , we define and .
Theorem 5. Assume that , and , where . Define as above in (32), where ; then as
Proof. Since
and
, we have
As
,
Hence,
implies that
Since and , therefore, . Thus, , which implies .
In the third step of iteration, we have
As and thus . By consequence, we have Therefore, there exists such that
Consequently, In particular,
Thus, by applying the same argument repeatedly, . In this way, the orbit of z tends to infinity. Hence, we obtain as . □
4.1. Examples
In this section, we demonstrate the Jungck–DK iterative orbit and the escape criterion from Theorem 5 by generating several examples of images from the Mandelbrot and Julia sets. The pictures were made with ’s implementation of the escape algorithm.
4.1.1. Examples of Mandelbrot Sets in Jungck–DK Orbit
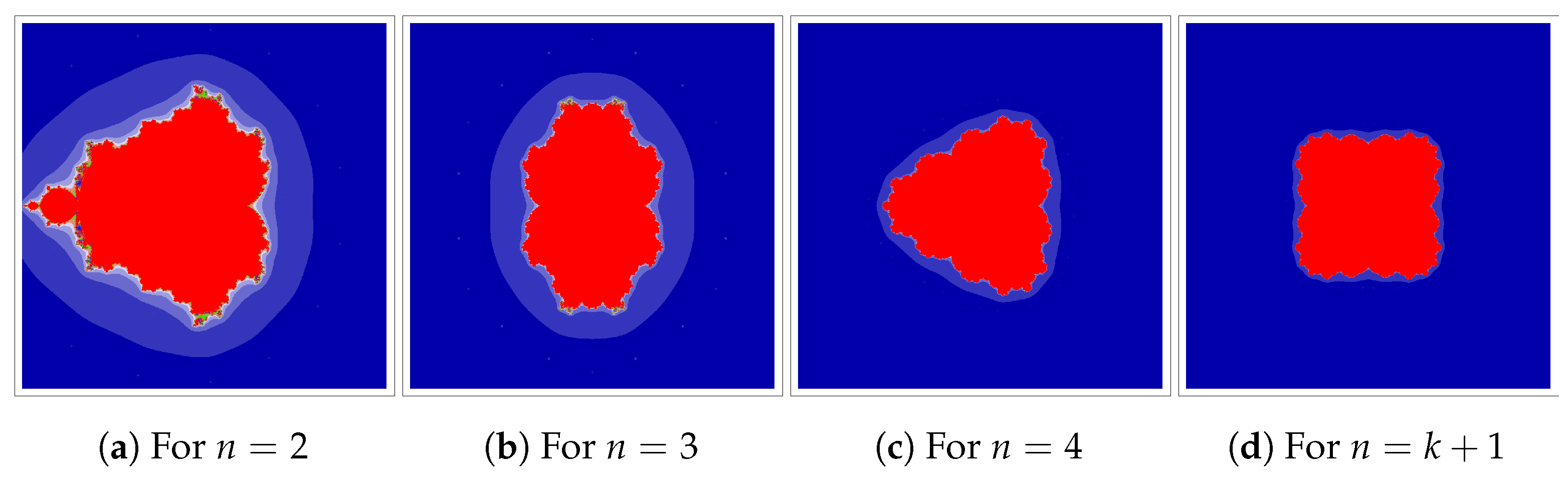
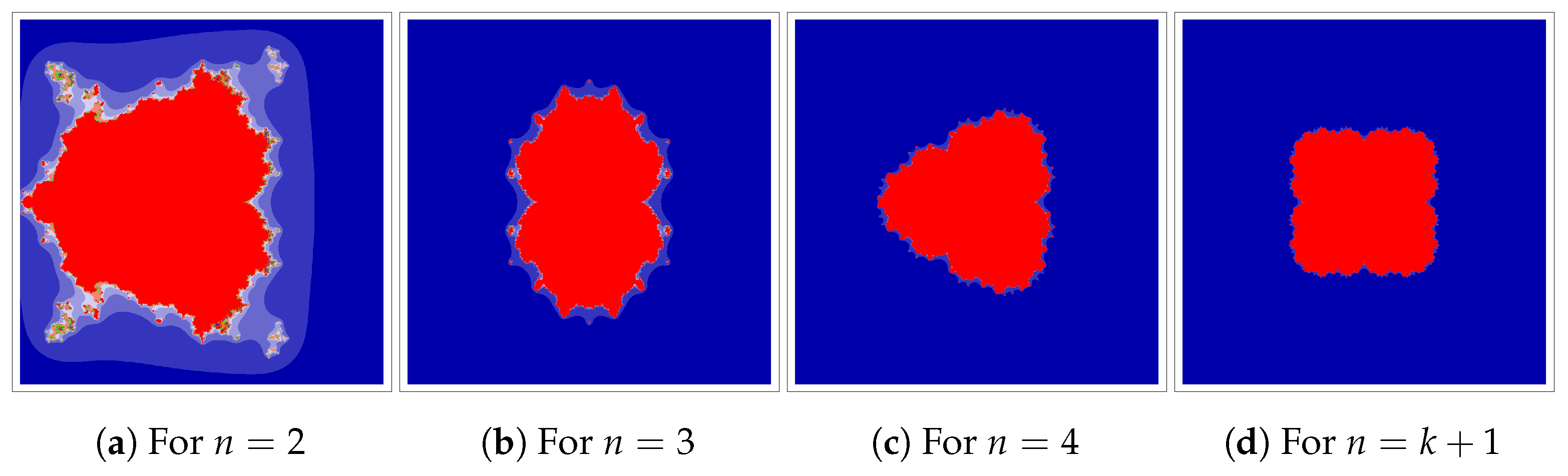
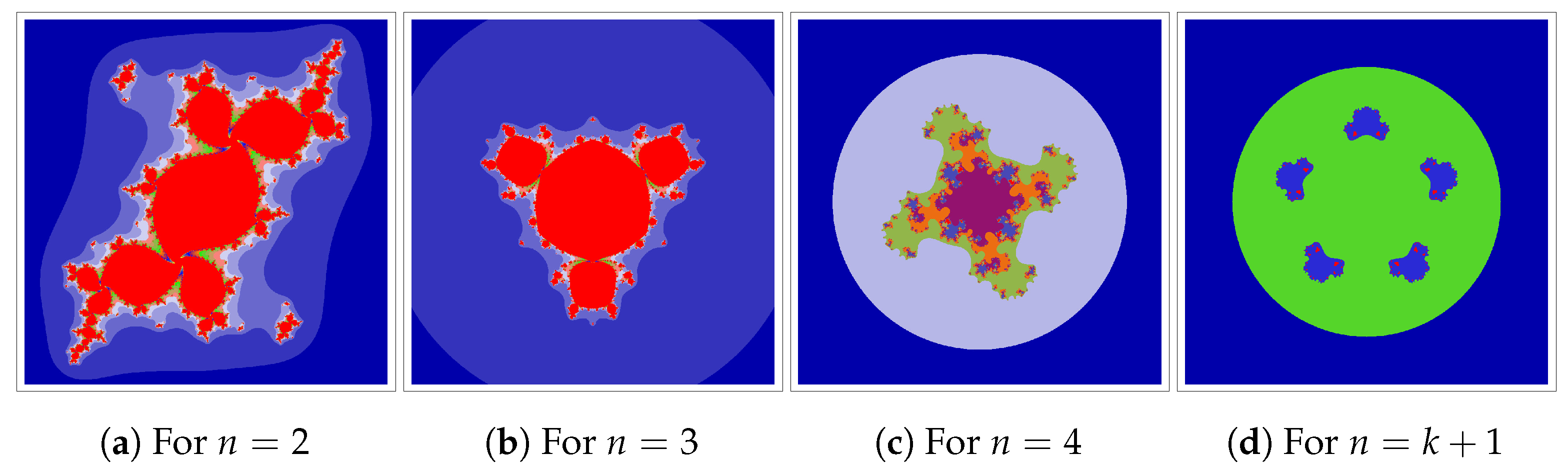
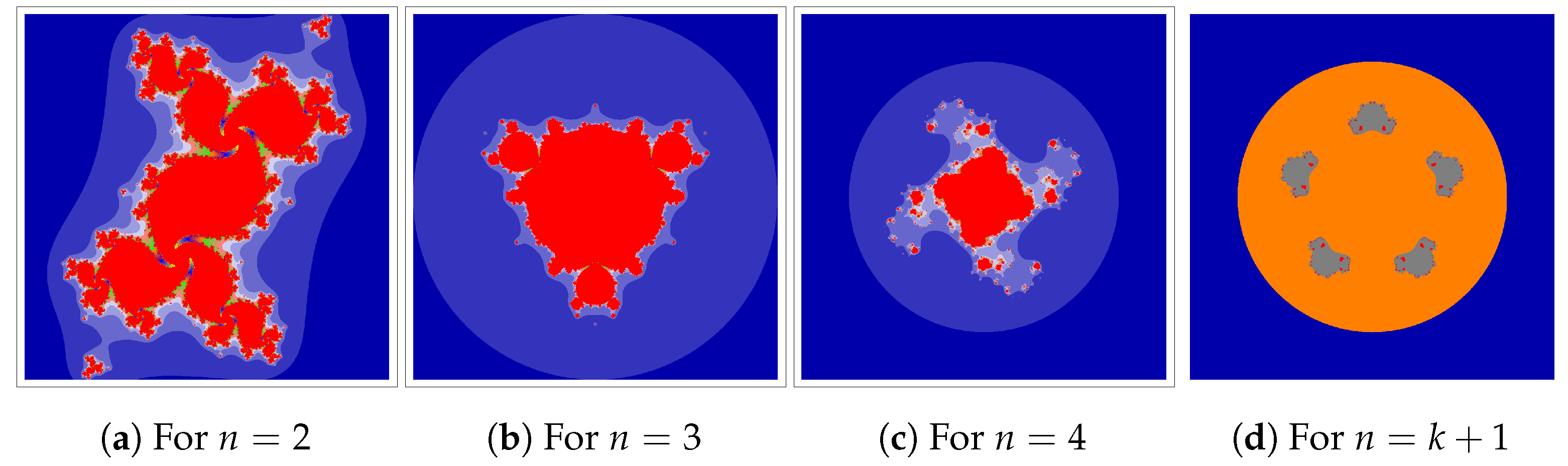
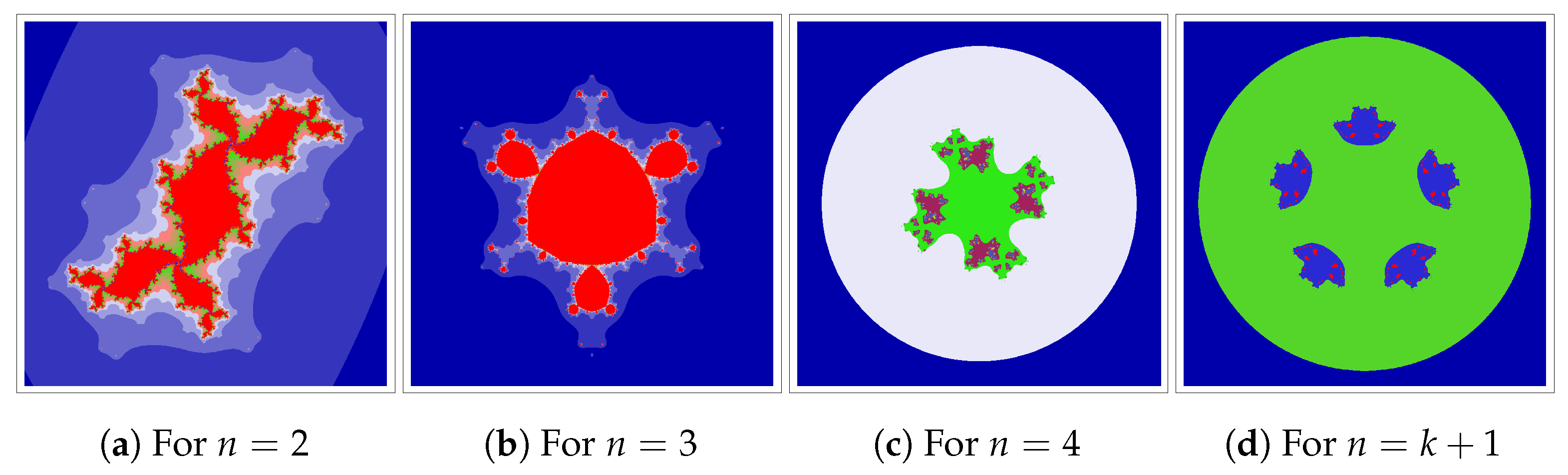
We start with an example outlining how the Jungck–DK iteration can be used. We will use
at
and 4. In
Figure 2,
Figure 3,
Figure 4 and
Figure 5, we fix
and change the parameters
and
of iteration. We can observe that varying
and
values in the Jungck–DK method has a substantial effect on the shape of the resulting set.
4.1.2. Examples of Julia Sets in Jungck–DK Orbit
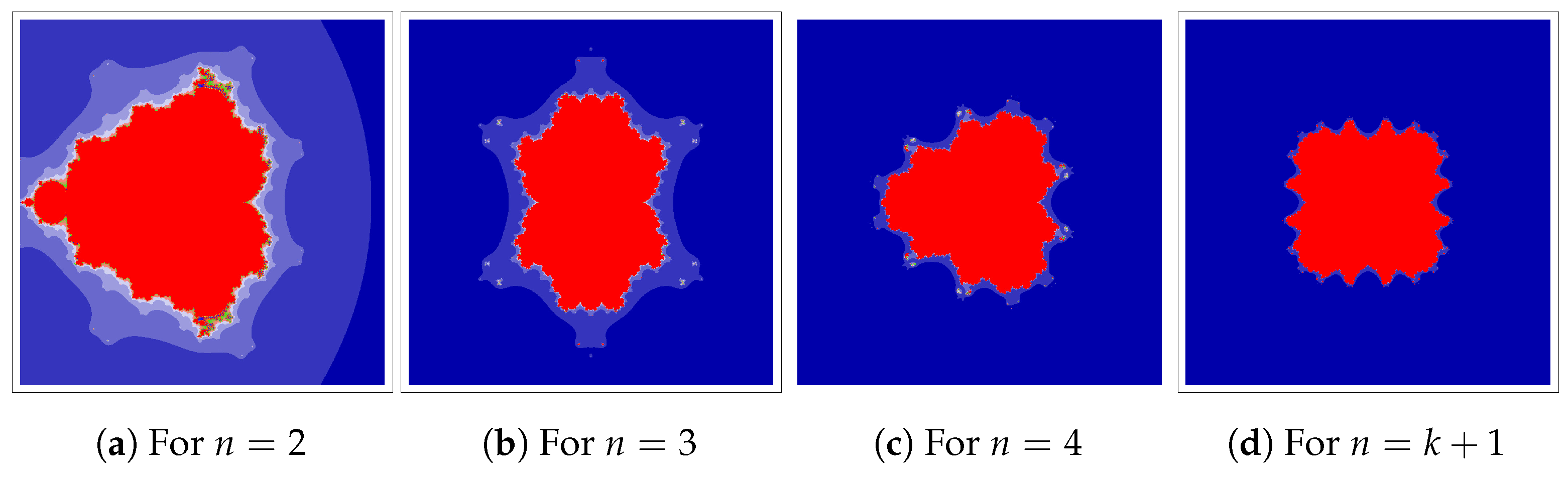
In the following example, a Julia set for
at
and 4, is generated using the Jungck–DK iteration. The images were obtained for
and
and for different parameters
and
Changing the parameters of the Jungck–DK iteration allows us to obtain different Julia set shapes, as shown in
Figure 6,
Figure 7,
Figure 8 and
Figure 9, for the same generating polynomial.
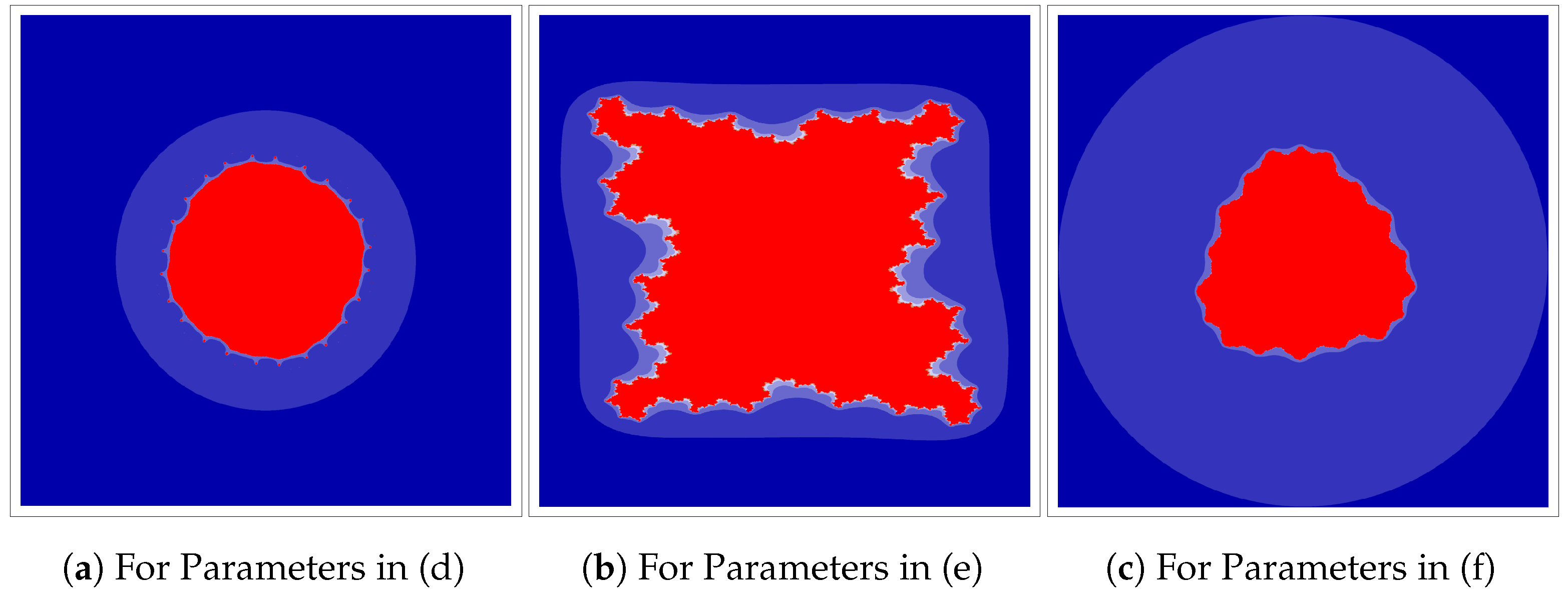
In the second example, various Julia sets generated using the Jungck–DK iteration are presented. The following parameters were utilised in order to generate the images of Julia sets shown in
Figure 10 and
Figure 11.
- (a)
, , a Jungck–DK iteration with
- (b)
, , a Jungck–DK iteration with
- (c)
, , a Jungck–DK iteration with
- (d)
, , a Jungck–DK iteration with
- (e)
, , a Jungck–DK iteration with
- (f)
, , a Jungck–DK iteration with
Using various combinations of the parameters, such as polynomials, Jungck–DK iteration parameters, etc., we are able to generate artistically applicable fractal patterns with a great deal of diversity.
5. Conclusions
In this paper, we propose and analyze the Jungck–DK iterative scheme for approximating fixed points. Our main contributions are summarized as follows. Firstly, we demonstrate the stability and faster convergence of the Jungck–DK iterative scheme compared to other Jungck-type schemes, such as the Jungck–CR, Jungck–SP, and Jungck–S schemes. Secondly, we provide a numerical example to illustrate the rate of convergence and prove the data dependence result for the Jungck–DK iterative scheme. Lastly, we apply the Jungck–DK iterative scheme to calculate the escape criteria of polynomial functions, generating distinct images of the Mandelbrot and Julia sets.
Therefore, these fractals have become useful in diverse scientific and engineering applications. Through our analysis of Julia sets, we have found that the size of the explored fractals is dependent on the parameters and , while the shape and symmetry are influenced by the parameters a and c. Furthermore, as we increase the value of n, the area occupied by the fractals decreases.
Concerning new directions of research, Nandal et al. [
35] developed a generalized viscosity approximation method in the context of a Hilbert space, which was applied to a range of problems, such as variational inequalities, convex feasibility problems, and fixed-point problems. These applications demonstrated the versatility and usefulness of the proposed iterative method in fixed-point theory. Building on this, it will be very interesting to explore the potential of this method in generating fractals, particularly Julia and Mandelbrot sets. Moreover, using our iterative method, a new type of viscosity approximation method can be found, which can be used as an effective tool for generating fractals with complex structures.