Abstract
Recently, generating visually secure cipher images by compressive sensing (CS) techniques has drawn much attention among researchers. However, most of these algorithms generate cipher images based on direct bit substitution and the underlying relationship between the hidden and modified data is not considered, which reduces the visual security of cipher images. In addition, performing CS on plain images directly is inefficient, and CS decryption quality is not high enough. Thus, we design a novel cryptosystem by introducing vector quantization (VQ) into CS-based encryption based on a 3D fractional Lorenz chaotic system. In our work, CS compresses only the sparser error matrix generated from the plain and VQ images in the secret generation phase, which improves CS compression performance and the quality of decrypted images. In addition, a smooth function is used in the embedding phase to find the underlying relationship and determine relatively suitable modifiable values for the carrier image. All the secret streams are produced by updating the initial values and control parameters from the fractional chaotic system, and then utilized in CS, diffusion, and embedding. Simulation results demonstrate the effectiveness of the proposed method.
1. Introduction
With the constant advancement of the Internet and image processing technology, a mass of digital images are being generated, transmitted, and stored conveniently. Meanwhile, the data security of these transmitted images is of increasing concern due to an insecure network environment [1,2]. While encryption is considered as an effective technique to secure sensitive images, the intrinsic characteristics of digital images such as bulky data volume, high redundancy, and a strong correlation between adjacent pixels make traditional AES and DES encryption methods inefficient [3]. Therefore, specialized algorithms have been extensively developed, such as fractional chaotic systems [4], quantum computation [5], and compressive sensing (CS) [6,7,8,9].
As of now, fractional Lorenz systems have been widely applied to image encryption. For instance, Wang et al. [10] applied the fractional-order hyper-chaotic Lorenz system to image encryption to improve encryption security. Similarly, to enhance security and efficiency, He et al. [11] performed encryption on plain images using pseudorandom streams generated by the fractional Lorenz system. Badr et al. [12] considered a face image encryption with the fractional-order Lorenz chaotic system to achieve cancellable face recognition. Additionally, fractional chaotic systems have been introduced to CS-based image encryption [13,14,15,16] recently. For instance, to improve encryption security, Yan et al. [13] and Kayalvizhi et al. [14] introduced fractional-order hyper-chaotic systems into image encryption, combining CS and DNA operation. To address the issue that CS reconstruction precision is not high enough, Fan et al. [15] proposed a subdata cipher structure based on 3D fractional logistic systems. The structure verified that the bifurcation diagrams of the 3D fractional system are well-suited for encryption. To reduce CS storage space and computational complexity, Ye et al. [16] designed a color image encryption scheme based on quaternion discrete multifractional transform and CS. The scheme utilizes the chaos-based orders to improve key sensitivity. The above schemes [10,11,12,13,14,15,16] tried to encrypt visible information into meaningless or noiselike content before transmission. Unfortunately, the noiselike appearance over public channels is likely to hint at the presence of a possible cipher, thereby incurring cryptanalysis attacks on suspicious content. As a result, it is always imperative to design secure cryptosystems so that the unauthorized entities cannot differentiate the cipher images by direct visual inspection.
Bao and Zhou [17] first introduced the concept of meaningful image encryption. The plain image was encrypted into a noiselike structure by an existing encryption method, and then transformed by discrete wavelet transform (DWT) to obtain a visually meaningful cipher image. This scheme achieves the transmission of cipher image with minimal suspicion, but the volume of the cipher image is four times larger than that of the plain image, which increases the transmission cost. The work in [18] was a variant of Bao and Zhou’s scheme [17], which reduced the file size of the cipher image and improved the visual security of the decrypted image. The research in [19] was another refinement, which compressed the plain image into a secret image by CS, and then embedded the secret image into the carrier image to form a cipher image. The refinement scheme in [19] is robust, but the embedding is handled by DWT, which is not fully reversible. The schemes in [20,21] resorted to integer discrete transform (IWT) and least-significant bit (LSB) embedding to ensure reversibility. In addition, to reduce the storage space of the CS measurement matrix, Wen et al. [22] and Ping et al. [23] integrated the semitensor product (STP) technique with CS. To have stronger robustness, Zhu et al. [24] used singular value decomposition (SVD) embedding to create the final visually secure cipher images. Unfortunately, the scheme in [24] needs to transmit the unmodified carrier image into the receiver to extract the embedded information. On this basis, a series of meaningful encryption schemes are investigated to improve the visual security of the cipher image or the quality of the decrypted image [25,26,27,28]. However, when CS is directly performed on a plain image [19,20,21,22,24], there are problems of inefficiency and poor quality of the decrypted image [15]. Furthermore, the underlying relationship between the hidden and the modified data is not considered in [19,20,21,22], which reduces the visual security of the cipher image.
To overcome the above shortcomings, we detail a novel and visually secure image encryption scheme that introduces the fractional Lorenz system into CS-based cryptosystem. First, the plain image is partitioned into VQ index blocks and error compensations that are sparse enough to be compressed by CS. Then, the index information and the measurements are diffused by a pseudorandom sequence obtained by the fractional Lorenz system to obtain a noiselike secret image. Next, the secret image is hidden into the carrier image by smooth function embedding [29]. Particularly, the lifting integer wavelet transform (LIWT) is introduced to decompose the carrier image to obtain the integer coefficient matrices, and the invertible coefficient quantization [30] is performed to eliminate the energy loss of the extracted information. Finally, a visually meaningful cipher image is obtained, which is of the same resolution as the plain image and appears visually the same as the carrier image. All cipher streams are obtained by updating the control parameters of the fractional Lorenz system and then used in the generation of CS measurement matrices, diffusion of the combination matrix, and permutation of the cover image.
2. Preliminaries
2.1. Compressive Sensing
Compressive sensing (CS) asserts that the signal which is sparse or can be sparsely represented can be reconstructed from much lower samples than the conventional Nyquist–Shannon sampling theorem. In CS theory, a redundant sparse signal x of size can be sparsely represented through an orthogonal basis and measured with measurement matrix , the measured value y of size is obtained by
where and s are the sensing matrix and the transformed coefficient matrix, respectively. The dimensions need to meet the relationship that
where k denotes the number of nonzero elements of the sparse signal, and c is a constant. When requiring to reconstruct x from y, one should solve a nonconvex optimal problem as follows:
where represents the sum of absolute values of each element in a vector. There are many algorithms to reconstruct x from y, such as orthogonal match pursuit (OMP), basic pursuit (BP), and smoothed norm (SL0).
2.2. The 3D Fractional Lorenz System
The 3D Lorenz chaotic system has been widely studied as a nonlinear uncertainty system due to its complicated evolution orbits of stretching and folding [31,32]. The system is used to produce the pseudorandom sequences for subsequent encryption and embedding in our work, and its mathematical formula is depicted as follows:
where t represents the time state, are the fractional orders that equal to 0.995, and r are associated with the Prandtl number and Rayleigh number, respectively, b is the geometric factor, and , and . For a more detailed mathematical derivation, please refer to the literature [12,32].
2.3. Vector Quantization
Vector quantization (VQ), a lossy data compression technique, is a dimensionality reduction method that attempts to replace high-dimensional data with low-dimensional codeword indexes. It includes three components: codebook generator, VQ encoder, and VQ decoder. The codebook generator uses the LBG clustering algorithm [33] with the image sub-block size to yield k-dimensional codewords that constitute the codebook of size , where and . The VQ encoder exploits to compress a sized image to VQ indexes. It first groups the image into a series of sized image sub-blocks , and the j-th block content () is:
For each sub-block, the nearest codeword is found with the smallest minimum Euclidean distance from . The Euclidean between and is defined as
where represents the f-th codeword in , and is the i-th component of . At the VQ decoder side, one can exploit the trained to decode the encoded VQ indexes to reconstruct the original image.
3. The Proposed Scheme
The proposed encryption scheme is introduced in two stages, as shown in Figure 1. In the first stage, the plain image is processed into an index matrix and an error matrix via the VQ encoder and decoder. The error matrix was confused with zigzag and compressed with a CS measurement matrix to obtain the measured values. The resulting values and the index matrix are diffused toobtainher to create an invisible secret image. In the second stage, the secret image is hidden into the carrier image to generate the cipher image. The hiding procedure is implemented by a smooth function to minimize the gap between the hidden and the modified data. Below, we introduce each in the proposed scheme.
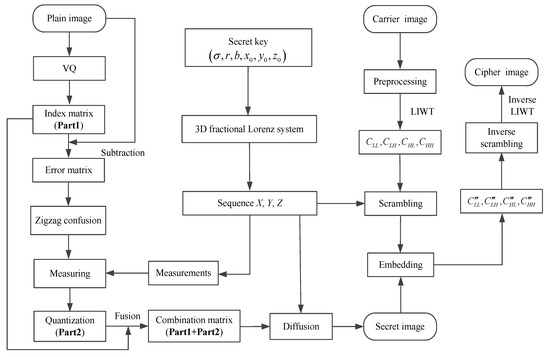
Figure 1.
The schematic of the proposed encryption process.
3.1. Encryption Process
The encryption operations begin with the following assumptions: the size of both the plain image and the carrier image is ; the plain image is divided into nonoverlapping sub-blocks , the confused error matrix is sampled by CS in block-unit way, and the size of the measurement matrix is , where and .
3.1.1. Generating Index Matrix and Error Matrix Based on VQ
Step 1: Find the best matching codeword for each sub-block and assign the corresponding index to the sub-block according to the following equation:
where , , , and is the best matching codeword index. All the assigned indexes constitute a vector as Part1 shown in Figure 1.
Step 2: Exploit the well-trained codebook to decode the index vector to obtain the reconstructed image , and subsequently calculate the error matrix using Equation (8).
Unlike previous studies that directly use CS to compress plain images, we choose the error matrix as input based on the following merits. Firstly, the error matrix has better sparsity than the plain image, and we can find a reasonable explanation from the comparable results in Figure 2a,c. Thus, the error image as CS input fully reflects the sparsity emphasized by CS theory. In this way, there is no need to investigate how to choose a suitable sparse basis. Secondly, the error matrix is used as a complement to the VQ indexes in the reconstruction stage, which helps to improve the quality of the decrypted images.

Figure 2.
The reconstructed results of Cameraman with the size . (a) Plain image. (b) The corresponding VQ reconstructed image. (c) The error matrix between (a,b).
3.1.2. Generating the Secret Image Based on CS and Zigzag Confusion
Step 1: Calculate the initial values of the 3D Lorenz system using three external key parameters , , and that are associated with the original plain .
Step 2: Generate the following three sequences , , where is the size of the combination matrix, and using , which are used to construct the measurement matrix, diffuse the combination matrix and scramble the coefficients of carrier image, respectively.
Step 3: Scan the error matrix via ziazag order using the given initial value in advance, where and are not greater than , to yield the confused errors .
Step 4: Set a threshold TS to alter the errors to zero if the absolute values are smaller than TS, and then divide the altered errors into nonoverlapping sub-blocks of block size .
Step 5: Construct the measurement matrix according to Algorithm 1. Then, measure each block in by use of to produce the measured values . If the sampling rate is , the length of each block in is .
| Algorithm 1: The construction of measurement matrix . |
Input: A distance d, the initial values , and control parameters . Output: The measurement matrix . (1): Iterate the 3D Lorenz system times with initial values and control parameters , abandon the preceding elements to bypass the transient state, then obtain three chaotic secret code streams , and . (2): Obtain the sequence based on . (3): Generate the sequence by sampling sequence with interval d as . (4): Obtain a more random sequence with . (5): Construct the measurement matrix according to the following formula: |
Step 6: Quantify all the elements of into a specific range of [0, 255] using the sigmoid map function in Equation (11), and obtain a novel vector as Part2.
where denotes rounding the elements to the nearest integer, , , , and max and min are the maximum and minimum elements of , respectively.
Step 7: Append all the measurement vector (Part2) to the index vector s (Part1) orderly to obtain the combination matrix , and the size of is
Note that all the index values in s are 8 bits long. If the block size and the sampling rate are set to and , respectively, then .
Step 8: Diffuse the combination matrix [15] with the sequence generated in Step 2, and obtain the secret image .
where is the j-th element of the matrix , is the j-th element of the matrix , and .
3.1.3. Embedding the Secret Image into the Carrier Image
Step 1: Preprocess the elements of the carrier of resolution into the range .
where , and is a downward rounding function.
Step 2: Perform an LIWT operation on the modified carrier , and then obtain the coefficient components , , , and , with each having the size of .
Step 3: Scramble , , and with the pseudorandom sequence generated in Section 3.1.2, and then obtain the scrambled components , and .
Step 4: Embed the secret image into the two components and by a smooth function and the component by a direct substitution, and the detailed embedding process is described in Algorithm 2.
| Algorithm 2: The embedding process. |
Input: The secret image and the scrambled components , , and . Output: The marked coefficient components , , and . (1): Stretch the secret image into a one-dimensional vector , and represent all the elements of the vector in binary as , where is the highest bit and is the lowest bit. (2): Quantify the coefficients of , , and into non-negative integers in a reversible way.
(3): Use the smooth function to embed and into the lowest three bits of the components and , respectively. The embedding process for is described as the following formula: (4): Embed into the lowest two bits of directly and keep other higher bits constant, then obtain the marked coefficient matrix . |
Step 5: Execute the inverse quantization on the marked component , and obtain .
where is the i-th element value of . Then, perform the same inverse quantization on the marked components and to generate and .
Step 6: Perform the inverse scrambling of Step 3 on the components , , and , and apply the inverse LIWT to obtain the final cipher image , which consists of the components , , , and .
Essentially, the embedding uses the smooth function to modify the lowest three bits of the carrier coefficients, rather than physically changing these coefficients by direct bit substitution. To be specific, given , . After direct bit substitution, we can obtain the modified coefficient value with a difference of . However, when the smooth function in Equation (18) is introduced, we can obtain the modified coefficient value with a difference of . The peak signal-to-noise ratio (PSNR) of the cipher image generated using the smooth function can be improved by 2 dB on average. The detailed process is shown in Algorithm 2.
The quantization process in Algorithm 2 converts the negative coefficients to the corresponding positive coefficients. For better illustration, this process is described in Figure 3. The top half of the figure represents the distribution of unquantized coefficients and the bottom half represents the distribution of quantized coefficients. The inverse quantization can be achieved if and only if , i.e., . In this way, the data expansion issue can be addressed and invertibility can be guaranteed.
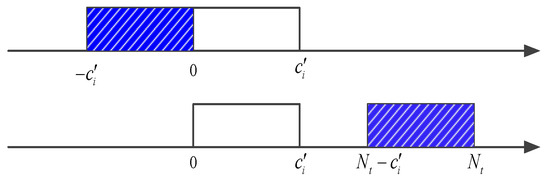
Figure 3.
The quantization process.
3.2. Decryption Process
The decryption process is the inverse of the encryption process. Figure 4 illustrates the schematic of the process. Firstly, the secret image is extracted from the received cipher image, then the plain image is restored according to the extracted secret image. The LIWT ensures an integer to an integer transform, and the subsequent coefficient quantization operation ensures conversion reversibility.
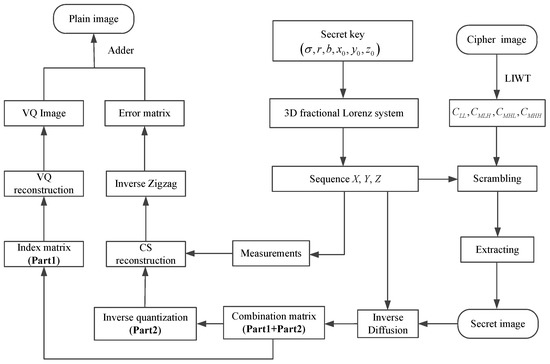
Figure 4.
The schematic of the proposed decryption process.
3.2.1. Extracting the Secret Image from the Cipher Image
Step 1: Apply the LIWT to the cipher image, and then obtain the coefficient components , , , and .
Step 2: Scramble , , and to obtain the components , , and , and quantize them into non-negative integer components , , and .
Step 3: Transform the elements of components , , and into their binary formats, and pick out the lowest 3 bits from as , the lowest 3 bits from as , and the lowest 2 bits from as .
Step 4: Recombine the binary bits into 8-bit representation and change it to decimal format to obtain the vector , then obtain the secret image by converting into rows and columns.
3.2.2. Recovering the Plain Image
Step 1: Conduct the inverse diffusion on the extracted secret image to obtain the combination image , and then obtain the index vector as in Part1 and the measurement vector as in Part2.
Step 2: Perform the inverse sigmoid quantization on according to Equation (19), and obtain the measured values .
Step 3: Execute the OMP reconstruction algorithm on as the following equation:
Step 4: Manipulate the inverse zigzag confusion (IZC) on the recovered sparse error matrix by the following equation:
Step 5: Execute the VQ reconstruction algorithm on Part1, and then obtain the lossy VQ reconstruction image .
Step 6: Obtain the decrypted image via adding the reconstructed error matrix to the corresponding reconstructed image .
In order to better explain the process of the proposed algorithm, we take a specific image matrix as an example to theoretically analyze the effectiveness of the proposed algorithm. Since our algorithm consists of three preliminary parts: the VQ process, the error compression process, and the secret image embedding process, we explain the proposed method from these three aspects. In the VQ encoding process, the input image matrix is encoded into 4 codeword indexes, then the lossy VQ image matrix of equal size is generated by the VQ decoding process, and the error matrix e is generated using Equation (8). In the error compression process, a measurement matrix of size is first generated using the fractional Lorenz system, and then the measured value P of size is generated by compressing the error matrix with . On this basis, the combined matrix is obtained, and the percentage is of the input image matrix. In the embedding process, the secret image can be embedded into the coefficient matrices of the carrier image using the smoothing function, which is the usual information hiding process.
4. Simulation and Performance Analyses
In this section, the simulation results of the proposed visual secure encryption algorithm are presented, and performance analyses are elaborated from the aspects of image encryption and decryption results, key sensitivity, histogram and correlation analyses, information entropy analysis, chosen plaintext attack (CPA), noise and data loss attacks, running efficiency analysis, and comparison analysis. All experiments are conducted on a 64-bit Windows 7 PC with 16.0 GB random-access memory (RAM) and Inter(R) Core(TM) i7-4770 CPU @ 3.40 GHz, and the platform is MATLAB R2012b. The sized or images including Lena, Barbara, Baboon, Jet, Woman, Peppers, Cameraman, and Goldhill are selected as the plain images and carrier images, respectively. In the VQ phase, we utilize a trained codebook with 256 codewords of length 16 to encode and decode the plain images, and the image sub-block size of this process is set as . In the CS phase, the block size of the sampling is set as , and the default sampling rate is and the threshold is TS = 25.
4.1. Simulation Results
In this subsection, we analyze and discuss the encryption and decryption results of the proposed scheme. In addition, the selections of the carrier images and the settings of the threshold TS are essential for the encryption and reconstruction effect. Thus, we also evaluate them in detail in the following contents.
4.1.1. Encryption and Decryption Results
Figure 5 presents the encryption and decryption results. The sized Lena, Baboon, Woman, and Cameraman as the plain images, in conjunction with the same-sized Barbara, Jet, Peppers, and Goldhill as the carrier images, are tested successively. As we can observe from the visual perception, the secret images were compressed to a quarter of the corresponding plain images, and their appearances resemble noiselike contents. In addition, the cipher images are obtained that are visually the same as the associated carrier images. Thus, if they are saved and transmitted among other natural images, the underlying attacks are not conscious of them. In another aspect, the reconstructed error matrices and the decoded VQ images are combined to recover the plain images, as displayed in Figure 6. The reconstructed error matrices merely fulfill information compensation to the corresponding decoded VQ images, illustrating that the decrypted images have higher visual quality while maintaining the compression performance.
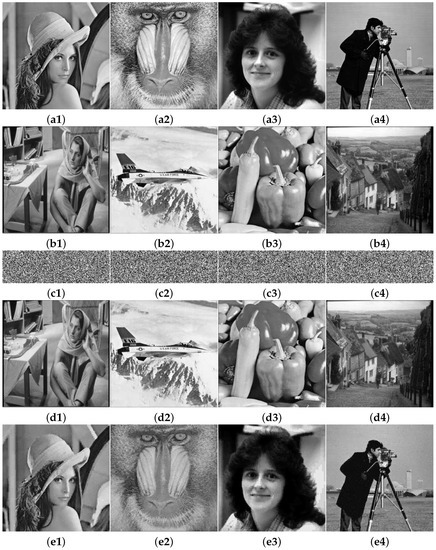
Figure 5.
Simulation results of the proposed scheme. (a1–a4) Four plain images: Lena, Baboon, Woman, and Cameraman size . (b1–b4) Four carrier images: Barbara, Jet, Peppers, and Goldhill size . (c1–c4) The corresponding secret images. (d1–d4) The corresponding cipher images. (e1–e4) The corresponding decrypted images.
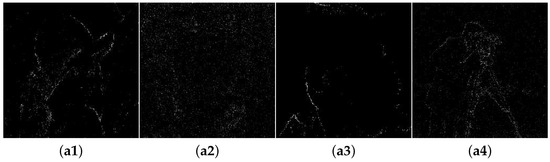

Figure 6.
The reconstruction details. (a1–a4) The reconstructed error matrices. (b1–b4) The decoded VQ images.
To analyze the similarities between two images quantitatively, the commonly used PSNR and mean structural similarity (MSSIM) [34], which are based on statistical models for images in the spatial domain, are exploited in this paper. The numerical results with smooth function and without smooth function (i.e., direct bit substitution) are given in Table 1, where PSNRdec represents the PSNR value between the plain image and corresponding decrypted image, and PSNRcip and MSSIMcip represent the PSNR and MSSIM values between the carrier image and corresponding cipher image, respectively. We can see that when the smooth function is introduced, all PSNRcip values are greater than 42 dB, and the MSSIMcip values are larger than 0.9970, which are higher than those generated without the use of the smooth function. After employing the smoothing function, the quality of each cipher image is promoted by more than 2 dB, indicating that the introduced smooth function and the quantization of the coefficient sign exert significant efficacy. Besides, the PSNRdec values with the sized carrier images and plain images are higher than those of the corresponding sized images, except for the Baboon texture image. Thus, the image size affects the decryption quality. In conclusion, the results mentioned above indicate that our method produces visually secure cipher images for transmission and offers satisfactory visual quality for both cipher and decrypted images.

Table 1.
PSNR and MSSIM values of simulation results.
4.1.2. Influence of Different Carrier Images on Encryption and Decryption
The LIWT operation converts the carrier pixel values to integer coefficient values and the subsequent quantization operation handles the signs of the generated coefficients in a reversible manner. Thus, these operations do not cause energy loss to the extracted secret image. Additionally, the invertible embedding and extraction processes ensure the integrity of the extracted information. However, the truncation errors from the rounding operation perhaps lead to the loss of error information and further degrade the quality of the decrypted image to some degree. To evaluate the influence of different carrier images on the simulation results, the and images of Woman are encrypted and then embedded into four different carrier images: Barbara, Jet, Lena, and Goldhill, respectively. Table 2 lists the calculated PSNRdec, PSNRcip, and MSSIMcip values with and without the smooth function. It can be seen that even when testing different carrier images, the PSNRdec values are still very similar and vary within a very narrow interval, verifying that different carrier images have little effect on the quality of decrypted images. Moreover, when the smooth function is utilized, all PSNRcip values are greater than 42 dB, and the MSSIMcip values are larger than 0.9970, which are greater than the corresponding PSNRcip and MSSIMcip values generated without the smooth function. Thus, the introduced smooth function effectively improves the visual security of cipher images.

Table 2.
PSNR and MSSIM values for different carrier images.
4.1.3. Influence of Threshold TS on Encryption and Decryption
Here, we also evaluate the influence of threshold TS on the encryption and decryption effect. Firstly, four plain images including Woman, Lena, Baboon, and Cameraman are encrypted in turn, and then embedded in four carrier images Barbara, Jet, Peppers, and Goldhill, respectively. The test procedure for the images of size is the same. Figure 7 plots the relationship between TS and PSNR. As shown, regardless of the plain image or image size used, the PSNR values initially increase and then gradually decrease as TS increases. The maximum PSNR value fluctuates with the selection of plain image. Moreover, for the same plain image but with different sizes, the maximum PSNR value still varies with the setting of TS. Thus, the threshold TS influences the decryption of the plain image. A reasonable recommendation is to set the threshold TS to 25.
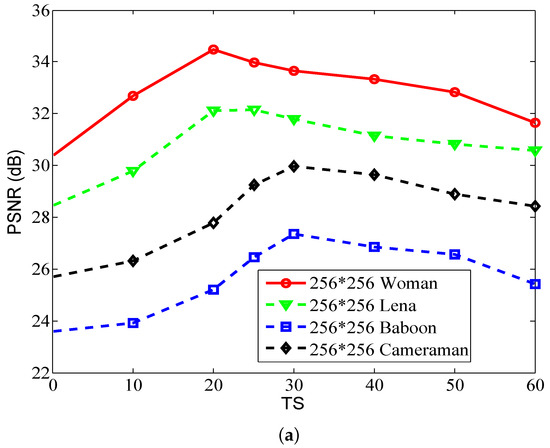
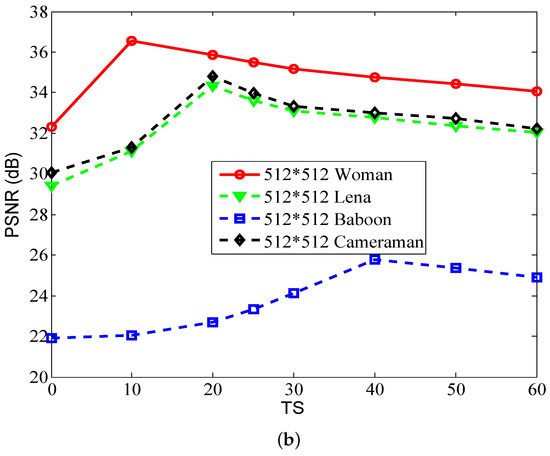
Figure 7.
PSNR vs. TS for different plain images. (a) . (b) .
4.2. Performance Analyses
In this section, performance analyses are assessed from key sensitivity analysis, histogram analysis, correlation analysis, information entropy analysis, CPA attack, noise attack, data loss attack, and running efficiency analysis. In what follows, we analyze and discuss them successively.
4.2.1. Key Space and Sensitive Analysis
Key space refers to the total number of different keys used in the encryption algorithm. As described in Equation (9), the initialization processes of three initial values for the fractional Lorenz system depends on three external keys with 17 decimals. Therefore, the total key space is , which is enough to resist against a brute-force attack. Key sensitivity is a property that allows a robust encryption design to yield a completely different output by making subtle changes to the keys used. The plain image Woman () and the carrier image Peppers () (see Figure 5(a3,b3) are subjected to the proposed algorithm with the correct key , and the subtly modified keys , , and . The corresponding decrypted images are displayed in Figure 8. As one would expect, when the key is changed subtly, the corresponding decrypted image is noisy and cannot provide any visual information, implying that the decryption process is sensitive to the used keys.
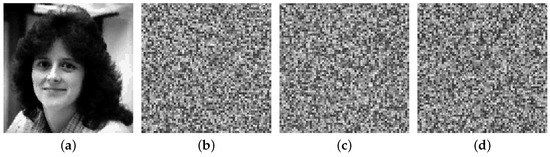
Figure 8.
Key sensitivity analysis in decryption process. (a–d) The decrypted images, respectively, with correct key; the modified keys , , and .
In another aspect, the four keys are utilized to encrypt the same plain image Woman, and the generated secret images and the final cipher images are presented in Figure 9a–d,e–h, respectively. The differential images between the original and modified secret images are shown in Figure 9i–k. As can be observed, minor changes to the keys used can cause significant changes to the secret images. However, the corresponding cipher images are visible and appear identical to each other, which means the cipher images can be transmitted securely over a public channel.
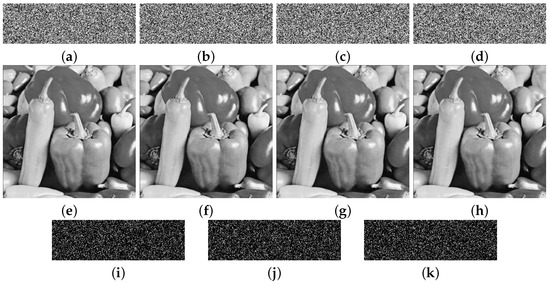
Figure 9.
Key sensitivity analysis in encryption process. (a–d) The secret images, respectively, with correct key; the modified keys , , and . (e–h) The corresponding cipher images. (i) Differential image between (a,b). (j) Differential image between (a,c). (k) Differential image between (a,d).
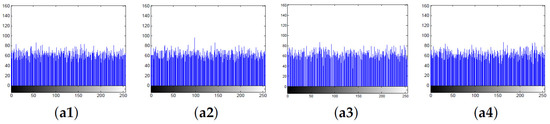
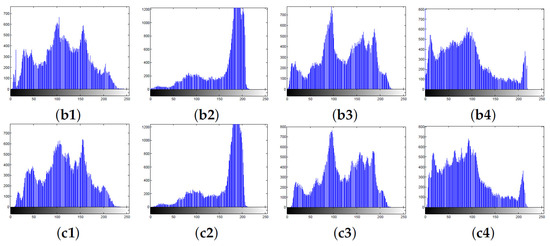
4.2.2. Histogram Analysis
The histogram of an image depicts the probability density distribution of discrete pixel values, plotted on the horizontal axis with 0–255 gray levels and on the vertical axis with the corresponding frequencies. A secure cryptosystem should obtain the secret image with a flat histogram distribution to resist statistic attacks. In this paper, the plain image and the corresponding carrier image are the same as those in Section 4.1.1. The histogram distributions of the secret image, the carrier image, and the cipher image are shown in Figure 10, respectively. As seen, the histograms of the secret images are flat and similar to each other; on the contrary, the histograms of the cipher images are uneven and look the same as the carrier images. Thus, the attacker cannot obtain valuable information from the histogram distributions of the cipher images to recover the plaintext information. This shows that our scheme can provide acceptable visual security without raising suspicion in transmission.
4.2.3. Correlation Analysis
The correlation between adjacent pixels is often used as one of the important criteria to evaluate the security performance of the existing cryptosystems. For natural images, there is strong correlation between adjacent pixels; however, it can be greatly weakened by secure cryptographic cryptosystems. The correlation coefficient (CC) is calculated as
where and are the adjacent pixel values, and is the total number of selected pixel pairs. In the experiment, we randomly choose 2000 adjacent pixel pairs in horizontal, vertical, and diagonal directions to calculate the correlation between adjacent pixels. The sized images Woman and Peppers are used as the plain image and carrier image, respectively. Figure 11 and Table 3 show the correlation results. We can see that the plain image, carrier image, and cipher image have a strong correlation with correlation coefficients close to 1, and the secret image has weaker correlation with corresponding correlation coefficient close to 0. In addition, the correlation plots in the third column of Figure 11 are similar to those in the fourth column, so it is not easy to distinguish the cipher image from the corresponding carrier image. In short, the correlation of the plain image is effectively broken by the encryption design, and the correlation of the carrier image is well-preserved with the smoothing function embedding.
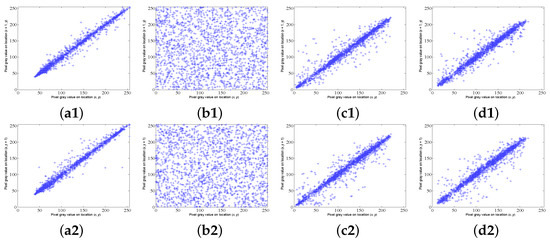
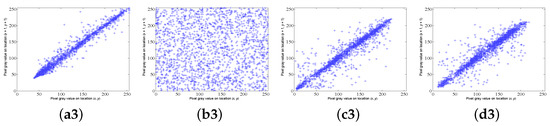
Figure 11.
Correlation analysis. (a1–a3) Correlation plots of the plain image Woman in horizontal, vertical, and diagonal directions. (b1–b3) Correlation plots of the secret image in horizontal, vertical, and diagonal directions. (c1–c3) Correlation plots of the carrier image Peppers in horizontal, vertical, and diagonal directions. (d1–d3) Correlation plots of the cipher image in horizontal, vertical, and diagonal directions.

Table 3.
Correlation coefficients among adjacent pixels.
4.2.4. Information Entropy Analysis
Information entropy is one of the important metrics to evaluate cryptographic security [35,36]. For a meaningful encryption system, the closer the information entropy of the encrypted image is to the carrier image entropy value, the better the encryption effect. The formula of entropy value is as follows:
where is the probability of . Table 4 lists the entropy results of different plain images embedded into the same carrier image ’Lena’. From this, it can be obtained that the entropy value of the encrypted image is close to that of the carrier image and the entropy value of the reconstructed image is close to that of the plain image, so the algorithm in this paper can effectively resist the information entropy attack.

Table 4.
Information entropy results.
4.2.5. Cpa Attack
A known plaintext attack (KPA) refers to a cryptanalytic model in which an attacker tries to reveal key association information with prior knowledge of the plaintext and the corresponding ciphertext. Compared with KPA, CPA is more powerful than KPA in that the attacker can choose any plaintext and generate the corresponding ciphertext to reveal key-related information. If an encryption scheme is resistant to a CPA attack, it is undoubtedly also resistant to a KPA attack. Based on this, a secure image encryption mechanism should be able to resist CPA. In our scheme, although the plain image changes only one bit of information, the generated secret image has obvious differences, which is due to the chaotic initial values of the fractional Lorenz system associated with the plaintext content. Chaos is extremely sensitive to the initial values, and a slightly changed plain image will generate different initial values, thus generating a different pseudorandom sequence and a completely different secret image. Based on the above analysis, the algorithm in this paper can resist a CPA attack.
4.2.6. Noise Attack
The cipher images may be interfered with by noise pollution when stored and transmitted in a public channel. Therefore, in this part, we test the proposed encryption algorithm against noise attacks. The cipher image Peppers is separately polluted by noise intensities 0.00001, 0.0001, 0.0005, 0.001, 0.005, and 0.01, and the noisy cipher images and the corresponding decrypted images are illustrated in Figure 12. As can be seen in Figure 12 and Table 5, when the noisy intensity varies from 0.00001 to 0.01, the PSNR value of the decrypted image Woman decreases accordingly from 32.5193 dB to 14.1350 dB. In addition, one can see that there are several smaller destroyed squares in the decrypted images, which are different from these neighbor pixels. These small squares correspond to those VQ indexes that are damaged in the cipher image. Whereas the pixels located in the destroyed blocks cannot be recovered, these destroyed blocks imply that our method has the ability to detect inconspicuous potential attacks and locate tampering.


Figure 12.
Robustness test results against noise attack with the sized plain image Woman and the same size carrier image Peppers. (a–f) Noise intensities, respectively, with 0.00001, 0.0001, 0.0005, 0.001, 0.005, and 0.01. (g–l) The corresponding decrypted images.

Table 5.
PSNR values under different salt and pepper noise attack.
4.2.7. Data Loss Attack
To test the robustness against data loss attacks, the cipher image Peppers is assigned 0 by different size squares, and the cipher images and the corresponding decrypted images are shown in Figure 13. The data loss sizes of the cipher images in the first row of Figure 13 are , , , and , and the images in the second row correspond to the decrypted images. It can be seen from Figure 13(b1–b4) that some indexes in the tampered cipher image are destroyed, which further maps the block content of the decrypted image. In addition, Table 6 lists the PSNR, MSSIM, and CC values of the decrypted images. It can be seen that the PSNR value of the decrypted image decreases gradually as the data loss square of the cipher images increases. Moreover, the PSNR value of the decrypted image decreases from 28.9935 dB to 14.2427 dB. Based on the calculated PSNR, MSSIM, and CC values, it is clear that the proposed encryption algorithm can resist data loss attacks to a certain extent.


Figure 13.
Robustness test against data loss. (a1) data loss. (a2) data loss. (a3) data loss. (a4) data loss. (b1) The decrypted image of (a1). (b2) The decrypted image of (a2). (b3) The decrypted image of (a3). (b4) The decrypted image of (a4).

Table 6.
PSNR, MSSIM and CC values of decrypted image for different data loss.
4.2.8. Running Efficiency Analysis
Running efficiency is an important metric for encryption performance, especially for testing real-time application scenarios. Table 7, Table 8, Table 9 and Table 10 list the encryption time and decryption time for different size images. The size of the carrier image is kept the same as that of the plain image. ’Compression’ denotes the CS compression process, ’Diffusion’ denotes the diffusion process of the measurements and VQ indexes, ’Embedding’ denotes the total process of embedding the secret image into the three coefficient matrices of the carrier image, and ’Reconstruction’ denotes the decryption process of the plain image. It can be seen that the average time consumed for encryption ranges from 5.7973 s to 23.4203 s and for decryption from 5.1673 s to 20.9303 s when the size of the original image changes from to . For the encryption process, the time spent on compression and diffusion is very small, and about all time is spent on smooth function embedding. When the image size is enlarged, more data is needed for embedding, and therefore, more time is consumed. As for the decryption process, the time spent on reconstruction accounts for about of the total time regardless of the image size chosen, while the time spent on the inverse diffusion is almost negligible. Based on the above data analysis, the proposed method is very suitable for the encryption and decryption of small and medium-sized images. When testing larger images, assistance from the cloud is essential, where encryption occurs locally and decryption is performed on the cloud.

Table 7.
Encryption time for images of size (Unit: s).

Table 8.
Decryption time for images of size (Unit: s).

Table 9.
Encryption time for images of size (Unit: s).

Table 10.
Decryption time for images of size (Unit: s).
4.3. Comparison with the Existing Work
In this subsection, visual security and compression performance of the proposed scheme are discussed and compared with other related schemes successively.
4.3.1. Visual Security
From the aspect of visual security, the appearance of the cipher image is closer to that of the carrier image, and greater visual security is obtained. In the simulation, the plain image and carrier image have the same size, and the volume of the cipher image is equal to that of the carrier image. The PSNR and MSSIM values between the carrier images and cipher images of our scheme and schemes [19,20,24] are given in Table 10. The carrier images and cipher images of all compared schemes have the same pixel resolution, i.e., . The compression rate of the compared schemes [19,20,24] is fixed to 1/4, which is the same as our scheme, but the difference is that our compression rate consists of two parts: a 1/16 index matrix and a 3/16 error matrix. From the results listed in Table 11, we can find that the proposed scheme outperforms all the compared schemes in terms of PSNR and SSIM values of the cipher images. The reasons for this are summarized below.

Table 11.
Comparison of the PSNR and MSSIM values of cipher images.
(i): We use the LIWT transform to convert the carrier pixel values to integer coefficient components, and there are no errors in the inverse LIWT transform.
(ii): The quantization operation on the generated coefficients is reversible, which makes it free from energy loss.
(iii): We introduce a smoothing function in the embedding process, which is essential to reduce the numerical differences between the hidden and modified data.
In addition, we also subject the carrier and cipher images of size to our algorithm, and compare the PSNR and SSIM values of the decrypted images of the proposed scheme and other schemes [19,20,21]. These results are listed in Table 12. It can be found that the PSNR and MSSIM values in our scheme are larger than the corresponding values in the schemes [19,20], so combining CS and VQ leads to an improvement in the quality of the decrypted images. The PSNR and MSSIM values in the schemes [20,21] are fixed, which means that the decryption results are independent of the carrier image used, indicating that the embedding and extraction processes of both methods is fully reversible. On the other hand, the SSIM values of the scheme in [21] are better than our scheme, while the PSNR values are smaller than ours. Therefore, the scheme in [21] and the proposed scheme have different aspects of advantages and both have better visual security.

Table 12.
Comparison of the PSNR values of decrypted images.
4.3.2. Compression Performance
In the rest of the subsection, we further evaluate the compression and encryption performance of the proposed scheme. Specifically, the image Lena of size as the plain image is firstly processed by the VQ encoder to generate the index matrix and the error matrix. Then, the generated error matrix is confused and compressed by CS, and the VQ index matrix and the measurements are fused together and encrypted by the diffusion process. The decryption process is the reverse process of encryption, and the final decrypted image is generated by supplementing the reconstructed error matrix to the decoded VQ indexes. The PSNR values of the decrypted images at different compression ratios are calculated and compared with other related schemes in [19,21,24]. All compared methods use the Lena of size as the plain image and the OMP algorithm as the CS reconstruction algorithm. Table 13 shows the results. It can be seen that the proposed encryption design achieves more satisfactory compression performance compared with the schemes in [19,21,24].

Table 13.
Comparison of the PSNR values of decrypted images under different compression ratios.
5. Conclusions
This paper proposes a visually secure image encryption scheme based on a fractional chaotic system and CS technology. In our method, the fractional chaotic system is used to generate the measurement matrix and improve the encryption and embedding effect. Besides, the smooth function and coefficient quantization are used to improve the visual security of the cipher images. Simulation results and performance analyses are performed for images of different sizes to verify the improvements on the visual security of the cipher images and the visual quality of the corresponding decrypted images. The excellent performance proves that the proposed scheme can be an effective solution for protecting digital images from suspicion and attacks during storage and transmission.
Author Contributions
Data curation, Investigation, Methodology, writing—original draft preparation, H.R., J.C. and M.L.; Funding acquisition, Project administration, writing—review and editing, S.N. and Z.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by The Fundamental Research Funds for the Central Universities (No.500421126), start-up grant for doctoral research at Henan Normal University (QD2021096), the National Natural Science Foundation of China (No.61370195), and the Joint Funds of the National Natural Science Foundation of China (No. U1536121).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
All data, models, or code generated or used during the study are available from the corresponding author by request.
Acknowledgments
The authors would like to thank all the anonymous referees for their constructive comments and suggestions.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Zhang, J.; Bhuiyan, M.; Yang, X.; Singh, A.; Hsu, D.; Luo, E. Trustworthy Tarobtain Tracking with Collaborative Deep Reinforcement Learning in EdgeAI-Aided IoT. IEEE Trans Ind. Inf. 2022, 18, 1301–1309. [Google Scholar] [CrossRef]
- Zhang, J.; Bhuiyan, M.; Yang, X.; Wang, T.; Hayajneh, T.; Xu, X. Reliable Detection of Adversary Concealed Behaviors in EdgeAI Assisted IoT. IEEE Internet Things J. 2022, 1–10. [Google Scholar] [CrossRef]
- Chen, J.; Zhu, Z.; Fu, C.; Zhang, L.; Zhang, Y. An efficient image encryption scheme using lookup table-based confusion and diffusion. Nonlinear Dyn. 2015, 81, 1151–1161. [Google Scholar] [CrossRef]
- Wu, G.; Baleanu, D.; Lin, Z. Image encryption technique based on fractional chaotic time series. J. Vib. Control 2016, 22, 2092–2099. [Google Scholar] [CrossRef]
- Zhou, N.; Yan, X.; Liang, H.; Tao, X.; Li, G. Multi-image encryption scheme based on quantum 3D Arnold transform and scaled Zhongtang chaotic system. Quantum Inf. Process. 2018, 17, 338. [Google Scholar] [CrossRef]
- Patel, S.; Vaish, A. A novel image coding through the chaos theory and compressed sensing. In Proceedings of the International Conference on Data Science and Applications, Kolkata, India, 26–27 March 2022; Volume 287, pp. 615–623. [Google Scholar]
- Lu, P.; Xu, Z.; Lu, X.; Liu, X. Digital image information encryption based on Compressive Sensing and double random-phase encoding technique. Optik 2013, 124, 2514–2518. [Google Scholar] [CrossRef]
- Patel, S.; Vaish, A. A systematic survey on Image Encryption using Compressive Sensing. J. Sci. Res. 2020, 64, 391–396. [Google Scholar] [CrossRef]
- Vaish, A.; Patel, S. A sparse representation based compression of fused images using WDR coding. J. King. Saud. Univ.-Comput. Inf. Sci. 2022, in press. [Google Scholar] [CrossRef]
- Wang, Z.; Huang, X.; Li, Y.; Song, X. A new image encryption algorithm based on the fractional-order hyperchaotic Lorenz system. Chin. Phys. B 2013, 22, 010504. [Google Scholar] [CrossRef]
- He, J.; Yu, S.; Cai, J. A method for image encryption based on fractional-order hyperchaotic systems. J. Appl. Anal. Comput. 2015, 5, 197–209. [Google Scholar]
- Badr, I.; Radwan, A.; El-Rabaie, E.; Said, L.; El Banby, G.; El-Shafai, W.; Abd El-Samie, F. Cancellable face recognition based on fractional-order Lorenz chaotic system and Haar wavelet fusion. Digit. Signal Process. 2021, 116, 103103. [Google Scholar] [CrossRef]
- Yang, Y.; Guan, B.; Li, J.; Li, D.; Zhou, Y.; Shi, W. Image compression-encryption scheme based on fractional order hyper-chaotic systems combined with 2D compressed sensing and DNA encoding. Opt. Laser Technol. 2019, 119, 105661. [Google Scholar] [CrossRef]
- Kayalvizhi, S.; Malarvizhi, S. A novel encrypted compressive sensing of images based on fractional order hyper chaotic Chen system and DNA operations. Multimed. Tools Appl. 2020, 79, 3957–3974. [Google Scholar] [CrossRef]
- Fan, H.; Zhou, K.; Zhang, E.; Wen, W.; Li, M. Subdata image encryption scheme based on compressive sensing and vector quantization. Neural Comput. Appl. 2020, 1, 1–17. [Google Scholar] [CrossRef]
- Ye, H.; Dai, J.; Wen, S.; Gong, L.; Zhang, W. Color image encryption scheme based on quaternion discrete multi-fractional random transform and compressive sensing. Opt. Appl. 2021, 51, 349–364. [Google Scholar]
- Bao, L.; Zhou, Y. Image encryption: Generating visually meaningful encrypted images. Inf. Sci. 2015, 324, 197–207. [Google Scholar] [CrossRef]
- Musanna, F.; Kumar, S. Generating visually coherent encrypted images with reversible data hiding in wavelet domain by fusing chaos and pairing function. Comput. Commun. 2020, 162, 12–30. [Google Scholar] [CrossRef]
- Chai, X.; Gan, Z.; Chen, Y.; Zhang, Y. A visually secure image encryption scheme based on compressive sensing. Signal Process. 2017, 134, 35–51. [Google Scholar] [CrossRef] [Green Version]
- Wang, H.; Xiao, D.; Li, M.; Xiang, Y.; Li, X. A visually secure image encryption scheme based on parallel compressive sensing. Signal Process. 2019, 155, 218–232. [Google Scholar] [CrossRef]
- Chai, X.; Wu, H.; Gan, Z.; Zhang, Y.; Chen, Y.; Kent, W. An efficient visually meaningful image compression and encryption scheme based on compressive sensing and dynamic LSB embedding. Opt. Laser Eng. 2020, 124, 105837. [Google Scholar] [CrossRef]
- Wen, W.; Hong, Y.; Fang, Y.; Li, M.; Li, M. A visually secure image encryption scheme based on semi-tensor product compressed sensing. Signal Process. 2020, 173, 107580. [Google Scholar] [CrossRef]
- Ping, P.; Yang, X.; Zhang, X.; Mao, Y.; Khalid, H. Generating visually secure encrypted images by partial block pairing-substitution and semi-tensor product compressed sensing. Digit. Signal Process. 2022, 120, 103263. [Google Scholar] [CrossRef]
- Zhu, L.; Song, H.; Zhang, X.; Yan, M.; Zhang, T.; Wang, X.; Xu, J. A robust meaningful image encryption scheme based on block compressive sensing and SVD embedding. Signal Process. 2020, 175, 107629. [Google Scholar] [CrossRef]
- Wang, X.; Ren, Q.; Jiang, D. An adjustable visual image cryptosystem based on 6D hyperchaotic system and compressive sensing. Nonlinear Dyn. 2021, 104, 4543–4567. [Google Scholar] [CrossRef]
- Chai, X.; Wu, H.; Gan, Z.; Han, D.; Zhang, Y.; Chen, Y. An efficient approach for encrypting double color images into a visually meaningful cipher image using 2D compressive sensing. Inf. Sci. 2021, 556, 305–340. [Google Scholar] [CrossRef]
- Huo, D.; Zhu, Z.; Wei, L.; Han, C.; Zhou, X. A visually secure image encryption scheme based on 2D compressive sensing and integer wavelet transform embedding. Opt. Commun. 2021, 492, 126976. [Google Scholar] [CrossRef]
- Wang, K.; Liu, M.; Zhang, Z.; Gao, T. Optimized visually meaningful image embedding strategy based on compressive sensing and 2D DWT-SVD. Multimed Tools Appl. 2022, 81, 20175–20199. [Google Scholar] [CrossRef]
- Lee, T.; Lin, S. Dual watermark for image tamper detection and recovery. Pattern Recogn. 2008, 41, 3497–3506. [Google Scholar] [CrossRef]
- Zheng, P.; Huang, J. Discrete wavelet transform and data expansion reduction in homomorphic encrypted domain. IEEE Trans. Image Process. 2013, 22, 2455–2468. [Google Scholar] [CrossRef]
- Yang, S.; Chen, C.; Yau, H. Control of chaos in Lorenz system. Chaos Soliton. Fract. 2002, 13, 767–780. [Google Scholar] [CrossRef]
- Wang, S.; Wu, R. Dynamic analysis of a 5D fractional-order hyperchaotic system. Int. J. Control Autom. Syst. 2017, 15, 1003–1010. [Google Scholar] [CrossRef]
- Linde, Y.; Buzo, A.; Gray, R. An algorithm for vector quantizer design. IEEE Trans. Commun. 1980, 28, 84–95. [Google Scholar] [CrossRef] [Green Version]
- Wang, Z.; Bovik, A.; Sheikh, H.; Simoncelli, E. Image quality assessment: From error visibility to structural similarity. IEEE Trans. Image Process. 2004, 13, 600–612. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Alvarez, G.; Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 2006, 16, 2129–2151. [Google Scholar] [CrossRef] [Green Version]
- Murillo-Escobar, M.; Meranza-Castillón, M.; López-Gutiérrez, R.; Cruz-Hernandez, C. Suggested integral analysis for chaos-based image cryptosystems. Entropy 2019, 21, 815. [Google Scholar] [CrossRef] [PubMed] [Green Version]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).