A Quantum Key Distribution Routing Scheme for a Zero-Trust QKD Network System: A Moving Target Defense Approach
Abstract
1. Introduction
- To address the security challenges in QKD networks with untrusted relays, we propose a spatiotemporal diversification-based key distribution method. This method dynamically distributes multiple keys across various paths, ensuring high security in end-to-end key distribution while meeting diverse security requirements. The proposed approach effectively overcomes the limitations of the existing methods.
- To meet the diverse security needs of applications, an adaptive path recovery process is introduced. The system employs a penalty-based strategy to detect and exclude suspicious relay nodes from path selection. It dynamically tests compromised routes, imposes penalties, and monitors node behavior to ensure compromised nodes are excluded from participation.
- Extensive simulations were conducted under various scenarios to evaluate the performance of the proposed method. The results demonstrate that our method significantly outperforms traditional multipath methods in terms of both security and efficiency.
2. Background and Related Works
2.1. Point-to-Point QKD
2.2. Long-Distance QKD
2.3. Multipath QKD
3. System Model
3.1. Network Model
3.1.1. Trusted/Untrusted Relays
Application Layer
Controller Layer
Key Management Layer
Quantum Layer
3.1.2. Adversary Model
3.1.3. Problem Statement
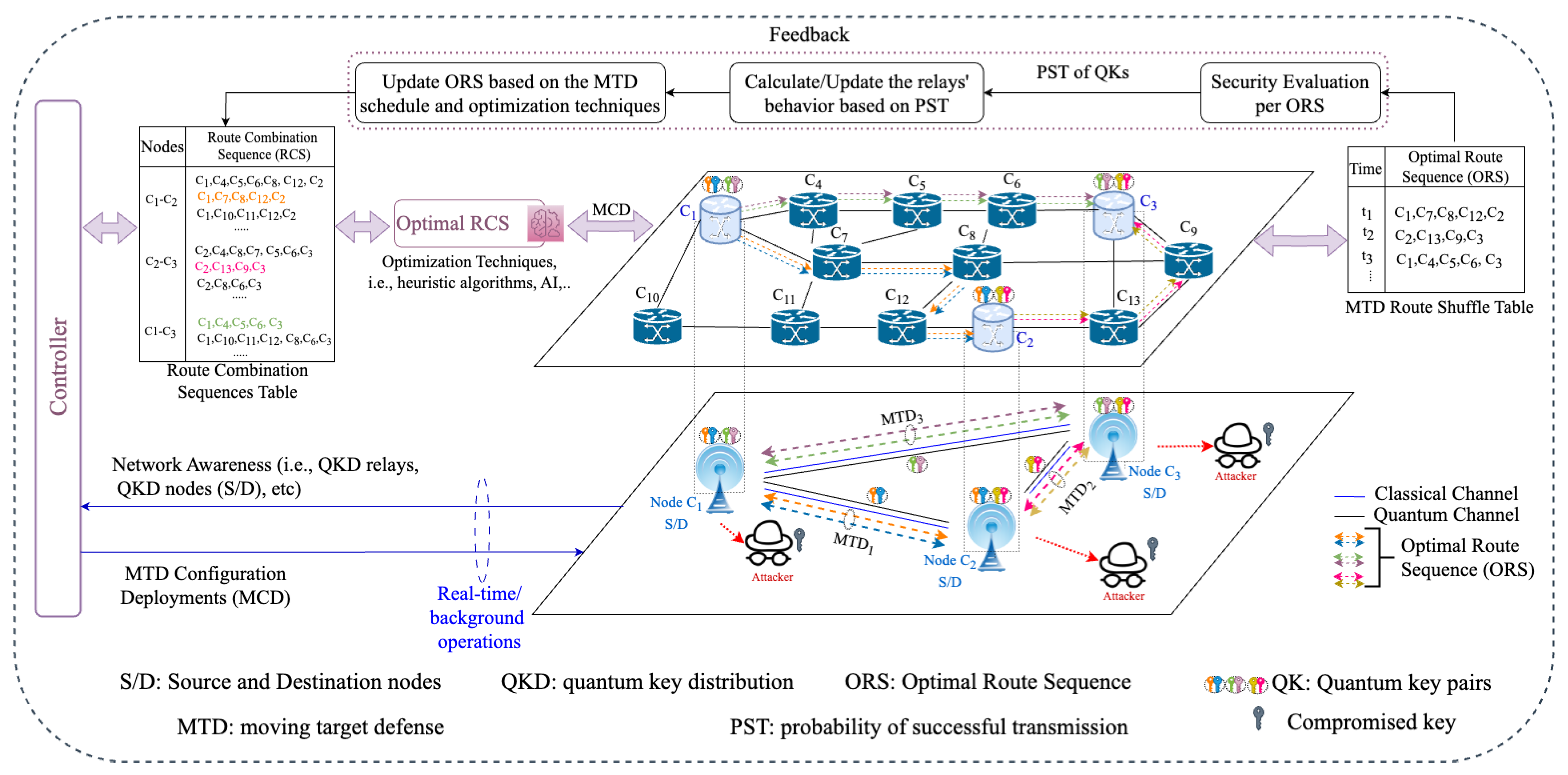
4. The Proposed Key Distribution Framework
4.1. A Spatiotemporal Diversification-Based Multipath–Multi-Key Distribution
4.1.1. Selection Phase
4.1.2. Execution Phase
4.1.3. Testing Phase
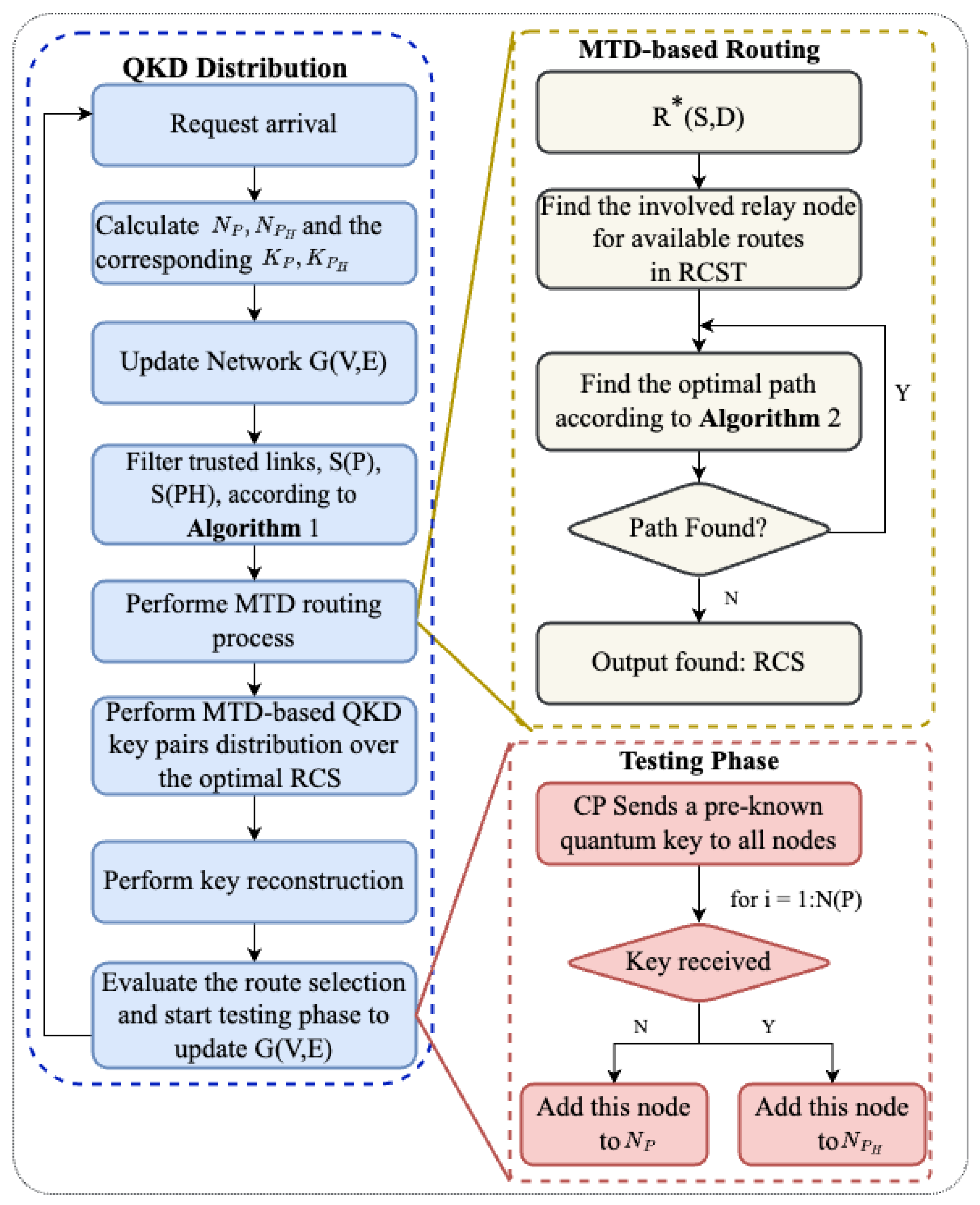
4.2. A Multipath–Multi-Key Distribution Algorithm
4.2.1. Path Selection Criteria
| Algorithm 1: Path selection algorithm. |
 |
4.2.2. Routing Procedure
4.2.3. Selection Phase
Process Overview
- Data collection: The CP collects and analyzes real-time and historical network data, including traffic patterns, previous security breaches, and ongoing threats. The data help to predict potential vulnerabilities and optimize route selections.
- Path enumeration: Utilizing algorithms like those described in Section 4.2.1, the CP enumerates all possible paths that could potentially connect S and D. This enumeration considers not only the shortest paths but also alternative routes that may offer greater security against potential eavesdropping or quantum attacks. Techniques such as the tandem queue decomposition (TQD) policy are utilized to achieve secure and efficient packet routing by considering time-varying key availability and link capacities [41].
- Optimization and selection: Each potential route combination is evaluated as presented in Algorithm 1, which assesses routes based on their security probability and operational efficiency. The algorithm prioritizes routes with the highest security metrics, ensuring compliance with quantum security standards. To provide a more comprehensive assessment of route security, metrics such as the quantum bit error rate (QBER) and key generation rates (KGR) could be incorporated into the optimization process [43].
- Threshold evaluation: The security probability of each proposed distribution is compared against a predefined threshold , which represents the minimum acceptable security level, typically set above the standard achieved by classical Dijkstra-based routing methods. This threshold should be set according to the specific security requirements of the network and can be dynamically adjusted to respond to evolving threats [44].
- Iterative improvement: If the selected route combination (RCS, R) meets the security and efficiency criteria, it serves as a baseline for further optimization in subsequent iterations. This iterative process continues until no significant improvements in the route combinations are found, ensuring that the network adapts dynamically to changing conditions and requirements [45].
MTD-Based Multi-Pathfinding
- Path optimization: For each pair of keys, the CP utilizes feedback from previous distributions and current network data to select the most secure and efficient paths. This step is vital to maintaining high security, especially in environments with dynamic threat landscapes. To enhance this process, an adaptive routing strategy that considers key consumption and link state information is implemented [46].
- Dynamic adaptation: The optimization algorithm continuously adjusts the selected paths based on real-time feedback and network conditions. This dynamic adaptation mitigates new or evolving threats, ensuring that the key distribution remains secure [45].
- Termination: The algorithm terminates when all possible secure paths have been optimized or when all key pairs have been successfully assigned secure paths for distribution. Establishing clear termination criteria based on network performance metrics ensures efficient resource utilization.
4.2.4. Execution Phase
4.2.5. Inspection/Test Phase
Penalty Assignment Mechanism
Node and Link Compromise Detection
Time as a Correction Factor
4.3. A Multipath–Multi-Key Distribution Algorithm Complexity Analysis
- (1)
- The path selection process uses an improved KSP algorithm, specifically an optimized version of Yen’s algorithm, to identify secure and disjoint paths for key distribution. The computational complexity of Yen’s algorithm for finding K shortest paths in a graph G(V,E) with nodes and edges is [23]. In addition, a correlation-based path optimization step is introduced to minimize redundancy and reduce attack surfaces, adding an overhead of . Therefore, the overall complexity of the path selection phase is .
- (2)
- The routing procedure employs an adaptive security-aware ExDijkstra algorithm, which evaluates paths based on a multiplicative security probability metric instead of an additive shortest-path criterion. The traditional Dijkstra algorithm has a complexity of , but with additional security computations, the proposed model introduces an overhead P for security evaluations, leading to a worst-case complexity of . Furthermore, the inspection module dynamically evaluates the trustworthiness of the nodes and enforces penalties for compromised relays. This phase consists of compromised node detection (, where M is the number of monitored relays). Combining these components, the total complexity of the proposed model is given by . Since the number of selected paths (K) and monitored nodes (M) is significantly smaller than the total number of network nodes (m) and edges (n), the proposed algorithm remains computationally efficient and scalable.
5. Transmission Model of Multipath QKD Network-Based Zero-Trust Relays
5.1. Selection Phase: Mathematical Representation
5.2. Execution Phase: Probabilistic Model
5.3. Behavior Inspection Module
5.3.1. Penalty Assignment
5.3.2. Reward Function for Network Adjustments
5.4. Efficiency and Security Trade-Off
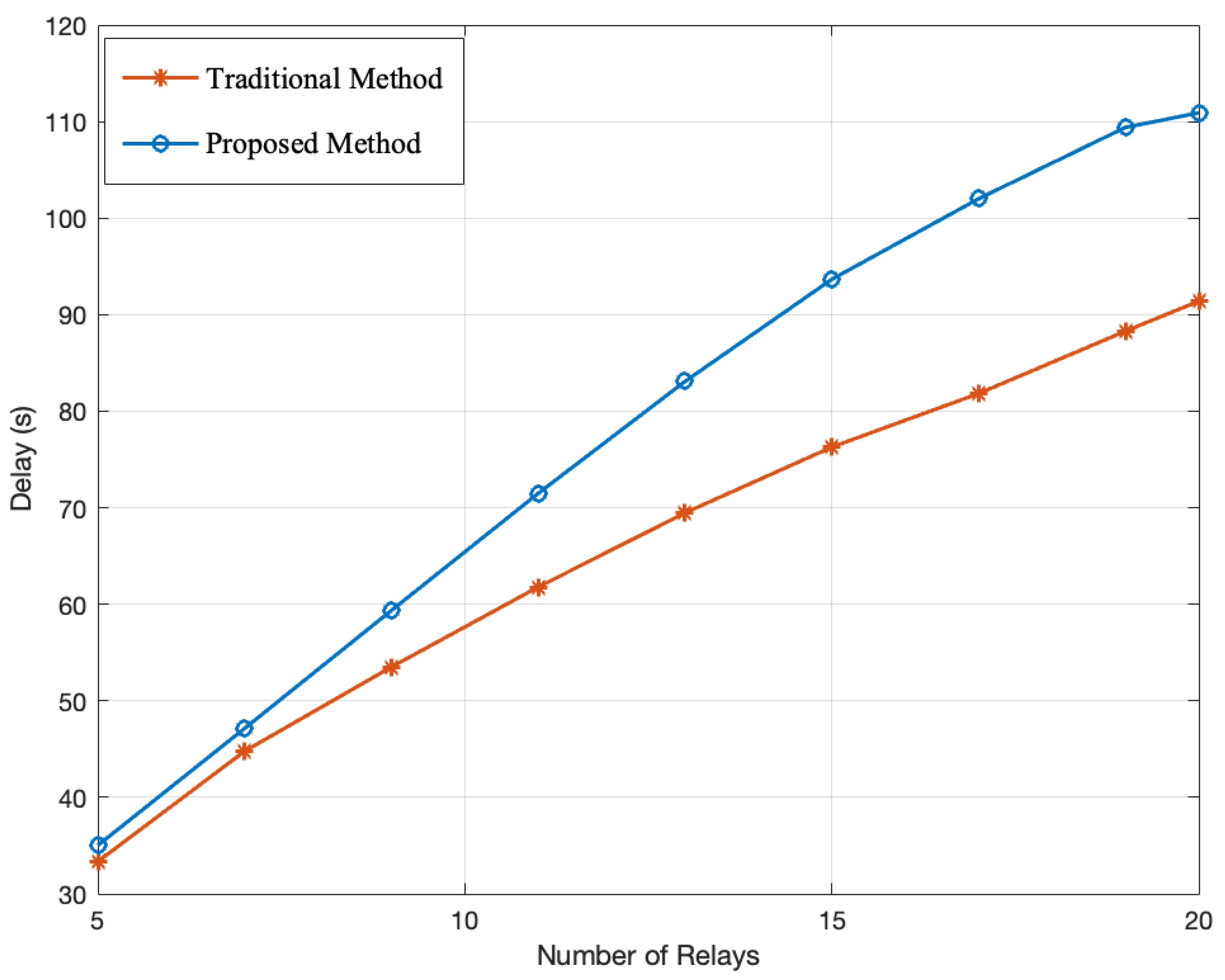
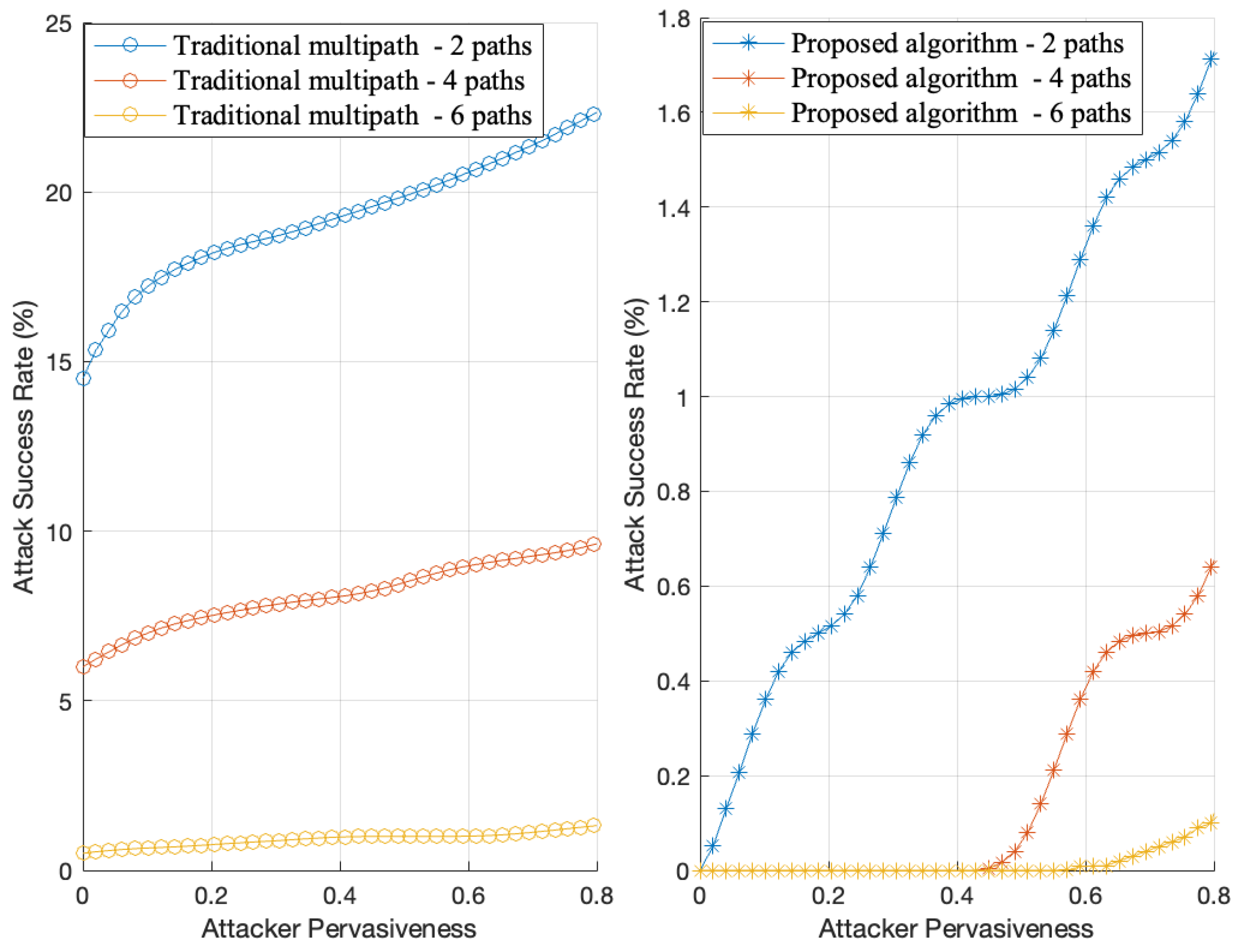
6. Performance Evaluation
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Arute, F.; Arya, K.; Babbush, R.; Bacon, D.; Bardin, J.C.; Barends, R.; Biswas, R.; Boixo, S.; Brandao, F.G.; Buell, D.A.; et al. Quantum supremacy using a programmable superconducting processor. Nature 2019, 574, 505–510. [Google Scholar] [PubMed]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Wootters, W.K.; Zurek, W.H. A single quantum cannot be cloned. Nature 1982, 299, 802–803. [Google Scholar]
- Wang, S.; Yin, Z.Q.; He, D.Y.; Chen, W.; Wang, R.Q.; Ye, P.; Zhou, Y.; Fan-Yuan, G.J.; Wang, F.X.; Chen, W.; et al. Twin-field quantum key distribution over 830-km fibre. Nat. Photonics 2022, 16, 154–161. [Google Scholar]
- Chen, Y.A.; Zhang, Q.; Chen, T.Y.; Cai, W.Q.; Liao, S.K.; Zhang, J.; Chen, K.; Yin, J.; Ren, J.G.; Chen, Z.; et al. An integrated space-to-ground quantum communication network over 4600 kilometres. Nature 2021, 589, 214–219. [Google Scholar]
- Boone, K.; Bourgoin, J.P.; Meyer-Scott, E.; Heshami, K.; Jennewein, T.; Simon, C. Entanglement over global distances via quantum repeaters with satellite links. Phys. Rev. A 2015, 91, 052325. [Google Scholar]
- James, P.; Laschet, S.; Ramacher, S.; Torresetti, L. Key management systems for large-scale quantum key distribution networks. In Proceedings of the 18th International Conference on Availability, Reliability and Security, Benevento, Italy, 29 August–1 September 2023; pp. 1–9. [Google Scholar]
- Baskar, S.; Roberts, M.K.; Sridhar, K. Long-Distance Secure Communication Based on Quantum Repeater Deployment with Quantum-Key Distribution. In Proceedings of the 2024 3rd International Conference on Artificial Intelligence for Internet of Things (AIIoT), Vellore, India, 3–4 May 2024; pp. 1–6. [Google Scholar]
- Cao, Y.; Zhao, Y.; Wang, Q.; Zhang, J.; Ng, S.X.; Hanzo, L. The evolution of quantum key distribution networks: On the road to the qinternet. IEEE Commun. Surv. Tutor. 2022, 24, 839–894. [Google Scholar] [CrossRef]
- Mehic, M.; Niemiec, M.; Rass, S.; Ma, J.; Peev, M.; Aguado, A.; Martin, V.; Schauer, S.; Poppe, A.; Pacher, C.; et al. Quantum key distribution: A networking perspective. ACM Comput. Surv. CSUR 2020, 53, 1–41. [Google Scholar] [CrossRef]
- Gisin, N.; Fasel, S.; Kraus, B.; Zbinden, H.; Ribordy, G. Trojan-horse attacks on quantum-key-distribution systems. Phys. Rev. A—At. Mol. Opt. Phys. 2006, 73, 022320. [Google Scholar] [CrossRef]
- Tedeschi, P.; Sciancalepore, S.; Di Pietro, R. Satellite-based communications security: A survey of threats, solutions, and research challenges. Comput. Netw. 2022, 216, 109246. [Google Scholar]
- Suhail, M.; Kaif, M. Quantum Hacking: Challenges and Countermeasures. Int. J. Multidiscip. Res. 2023, 5, 23058046. [Google Scholar]
- Sibson, P.; Erven, C.; Godfrey, M.; Miki, S.; Yamashita, T.; Fujiwara, M.; Sasaki, M.; Terai, H.; Tanner, M.G.; Natarajan, C.M.; et al. Chip-based quantum key distribution. Nat. Commun. 2017, 8, 13984. [Google Scholar] [CrossRef] [PubMed]
- Lo, H.K.; Curty, M.; Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef]
- Zhou, H.; Lv, K.; Huang, L.; Ma, X. Quantum network: Security assessment and key management. IEEE/ACM Trans. Netw. 2022, 30, 1328–1339. [Google Scholar]
- Wen, H.; Han, Z.; Zhao, Y.; Guo, G.; Hong, P. Multiple stochastic paths scheme on partially-trusted relay quantum key distribution network. Sci. China Inf. Sci. 2009, 52, 18–22. [Google Scholar] [CrossRef]
- Wang, J.; Xue, W.; Wang, C.; Wang, J. Research on Multi-path Quantum Key Distribution Scheme without Public Nodes Based on Trust Relaying. In Proceedings of the 2023 5th International Conference on Information Technology and Computer Communications, Tianjin, China, 15–17 June 2023; pp. 6–11. [Google Scholar]
- Wang, M.; Li, J.; Xue, K.; Li, R.; Yu, N.; Li, Y.; Liu, Y.; Sun, Q.; Lu, J. A segment-based multipath distribution method in partially-trusted relay quantum networks. IEEE Commun. Mag. 2023, 61, 184–190. [Google Scholar] [CrossRef]
- Sharma, P.; Agrawal, A.; Bhatia, V.; Prakash, S.; Mishra, A.K. Quantum key distribution secured optical networks: A survey. OJ-COMS 2021, 2, 2049–2083. [Google Scholar] [CrossRef]
- Zhang, Q.; Xu, F.; Chen, Y.A.; Peng, C.Z.; Pan, J.W. Large scale quantum key distribution: Challenges and solutions. Opt. Express 2018, 26, 24260–24273. [Google Scholar] [CrossRef]
- Kong, P.Y. Routing with Minimum Activated Trusted Nodes in Quantum Key Distribution Networks for Secure Communications. IEEE Internet Things J. 2024, 11, 15219–15228. [Google Scholar] [CrossRef]
- Chen, L.Q.; Chen, J.Q.; Chen, Q.Y.; Zhao, Y.L. A quantum key distribution routing scheme for hybrid-trusted QKD network system. Quantum Inf. Process. 2023, 22, 75. [Google Scholar] [CrossRef]
- Li, M.; Zhang, Q.; Gatto, A.; Bregni, S.; Verticale, G.; Tornatore, M. DRL-based progressive recovery for quantum-key-distribution networks. J. Opt. Commun. Netw. 2024, 16, E36–E47. [Google Scholar]
- Sharma, P.; Bhatia, V.; Prakash, S. Routing Based on Deep Reinforcement Learning in Quantum Key Distribution-secured Optical Networks. In Proceedings of the IEEE International Conference on ANTS, Jaipur, India, 17–20 December 2023; pp. 1–5. [Google Scholar]
- Yu, X.; Liu, Y.; Zou, X.; Cao, Y.; Zhao, Y.; Nag, A.; Zhang, J. Secret-key provisioning with collaborative routing in partially-trusted-relay-based quantum-key-distribution-secured optical networks. J. Light. Technol. 2022, 40, 3530–3545. [Google Scholar]
- Xu, S.; Zhao, Y.; Huang, L.; Qiao, C. Routing and Photon Source Provisioning in Quantum Key Distribution Networks. In Proceedings of the IEEE INFOCOM, Vancouver, BC, Canada, 20–23 May 2024; pp. 1411–1420. [Google Scholar]
- Sutcliffe, E.; Beghelli, A. Multiuser entanglement distribution in quantum networks using multipath routing. IEEE Trans. Quantum Eng. 2023, 4, 1–15. [Google Scholar]
- Kiktenko, E.O.; Tayduganov, A.; Fedorov, A.K. Routing Algorithm Within the Multiple Non-Overlapping Paths’ Approach for Quantum Key Distribution Networks. Entropy 2024, 26, 1102. [Google Scholar] [CrossRef] [PubMed]
- Lin, X.; Hou, G.; Lin, W.; Chen, K. Quantum key distribution in partially-trusted QKD ring networks. In Proceedings of the IEEE 3rd ICISCAE, Dalian, China, 27–29 September 2020; pp. 33–36. [Google Scholar]
- Nahar, N.; Andersson, K.; Schelén, O.; Saguna, S. A Survey on Zero Trust Architecture: Applications and Challenges of 6G Networks. IEEE Access 2024, 12, 94753–94764. [Google Scholar]
- Lin, J.; Jiang, Q.; Zhang, W.; Lin, Z.; Du, X. Quantum-Enhanced Zero Trust Security: Evolution, Implementation, and Application. In Proceedings of the 2024 International Conference on Quantum Communications, Networking, and Computing (QCNC), Kanazawa, Japan, 1–3 July 2024; pp. 211–215. [Google Scholar]
- Peev, M.; Martin, V.; Brito, J.P.; Ortíz, L.; Fred Fung, C.H.; Brito Méndez, R.; Buruaga, J.S.; Vicente, R.J.; Sebastian-Lombrana, A.J.; Setien, J.; et al. Quantum Key Distribution Network Architectures. In Proceedings of the 2024 International Conference on Quantum Communications, Networking, and Computing (QCNC), Kanazawa, Japan, 1–3 July 2024; pp. 320–326. [Google Scholar]
- Kashyap, S.; Bhushan, B.; Kumar, A.; Nand, P. Quantum blockchain approach for security enhancement in cyberworld. In Multimedia Technologies in the Internet of Things Environment; Springer: Singapore, 2022; Volume 3, pp. 1–22. [Google Scholar]
- Vyas, N.; Mendes, P. Relaxing Trust Assumptions on Quantum Key Distribution Networks. arXiv 2024, arXiv:2402.13136. [Google Scholar]
- Laudenbach, F.; Pacher, C.; Fung, C.H.F.; Poppe, A.; Peev, M.; Schrenk, B.; Hentschel, M.; Walther, P.; Hübel, H. Continuous-variable quantum key distribution with Gaussian modulation—The theory of practical implementations. Adv. Quantum Technol. 2018, 1, 1800011. [Google Scholar]
- Yen, J.Y. Finding the k shortest loopless paths in a network. Manag. Sci. 1971, 17, 712–716. [Google Scholar]
- Miao, M.; Fang, S.; Wu, W.; Yuan, X.; Bi, L. Minimum Path Cost Multi-path Routing Algorithm with No Intersecting Links in Quantum Key Distribution Networks. In Proceedings of the 2023 IEEE 6th International Conference on Information Systems and Computer Aided Education (ICISCAE), Dalian, China, 23–25 September 2023; pp. 232–237. [Google Scholar]
- Kumar, P.; Kundu, N.K.; Kar, B. Quantum Key Distribution Routing Protocol in Quantum Networks: Overview and Challenges. arXiv 2024, arXiv:2407.13156. [Google Scholar]
- Al Zoobi, A.; Coudert, D.; Nisse, N. Space and time trade-off for the k shortest simple paths problem. In Proceedings of the SEA 2020—18th International Symposium on Experimental Algorithms, Catania, Italy, 16–18 June 2020; Volume 160, p. 13. [Google Scholar]
- Akhtar, M.S.; G, K.; B, V.; Sinha, A. Fast and Secure Routing Algorithms for Quantum Key Distribution Networks. IEEE/ACM Trans. Netw. 2023, 31, 2281–2296. [Google Scholar]
- Bi, L.; Miao, M.; Di, X. A dynamic-routing algorithm based on a virtual quantum key distribution network. Appl. Sci. 2023, 13, 8690. [Google Scholar] [CrossRef]
- Johann, T.; Wenning, M.; Giemsa, D.; Dochhan, A.; Gunkel, M.; Fehenberger, T.; Pachnicke, S. Comparison and optimization of different routing methods for meshed QKD networks using trusted nodes. J. Opt. Commun. Netw. 2024, 16, 382–391. [Google Scholar]
- Chen, L.Q.; Zhao, M.N.; Yu, K.L.; Tu, T.Y.; Zhao, Y.L.; Wang, Y.C. ADA-QKDN: A new quantum key distribution network routing scheme based on application demand adaptation. Quantum Inf. Process. 2021, 20, 1–22. [Google Scholar]
- Li, X. Dynamic Link State Routing Scheme for Quantum Key Distribution Network. In Proceedings of the 2023 IEEE 15th International Conference on Advanced Infocomm Technology (ICAIT), Hefei, China, 13–16 October 2023; pp. 267–272. [Google Scholar]
- van Duijn, T.; Verschoor, S.R.; Rommel, S.; Monroy, I.T. Routing Strategies for Quantum Key Distribution Networks based on Trusted Relay Nodes. In Proceedings of the 2024 International Conference on Optical Network Design and Modeling (ONDM), Madrid, Spain, 6–9 May 2024. [Google Scholar]
- Biswas, S.; Goswami, R.S.; Reddy, K.H.K. A cluster-based quantum key distribution with dynamic node selection: An improved approach for scalability and security in quantum communication. Quantum Mach. Intell. 2024, 6, 63. [Google Scholar]
- Luo, Y.; Li, Q.; Mao, H.K. Distributed information-theoretical secure protocols for quantum key distribution networks against malicious nodes. J. Opt. Commun. Netw. 2024, 16, 956–968. [Google Scholar]
- Lella, E.; Schmid, G. On the Security of Quantum Key Distribution Networks. Cryptography 2023, 7, 53. [Google Scholar] [CrossRef]
- Barnett, S.M.; Phoenix, S.J. Securing a quantum key distribution relay network using secret sharing. In Proceedings of the IEEE GCC Conference and Exhibition (GCC), Dubai, United Arab Emirates, 19–22 February 2011; pp. 143–145. [Google Scholar]
- Ma, C.; Guo, Y.; Su, J. A multiple paths scheme with labels for key distribution on quantum key distribution network. In Proceedings of the IAEAC, Chongqing, China, 25–26 March 2017; pp. 2513–2517. [Google Scholar]




| Variable | Definition |
|---|---|
| The ith routing path selected for key distribution | |
| K | Global key reconstructed at the destination |
| Security probability of relay node j | |
| Security state of the path i, (1: secure, 0: insecure) | |
| Temporal penalty imposed on node j at time t | |
| Penalty weight assigned to relay node j | |
| Adjusted security probability of path | |
| Combined security fraction between source node A and destination node B | |
| Minimum acceptable security threshold | |
| Multiplicative security probability metric for path evaluation | |
| Path correlation metric for evaluating path diversity | |
| Dynamically adjusted correlation threshold for path security evaluation | |
| Scaling factor used in path correlation threshold calculation | |
| Penalty weight assigned to node j based on historical compromise data | |
| Incremental penalty adjustment for nodes detected as compromised | |
| Reward function for network adjustments considering node security states | |
| Weights assigned in the reward function to compromised and secure nodes, respectively | |
| Transmission delay associated with path | |
| Performance metrics balancing security and efficiency between nodes A and B | |
| Scaling coefficients balance security and efficiency in the metric | |
| Maximum radius for penalizing nodes near compromised links | |
| Temporal penalty imposed on node j at time t based on proximity to compromised links |
| Metric | Description | Proposed vs. Traditional Method |
|---|---|---|
| Execution time | Multipath QKD | Higher due to additional security processes, while traditional methods have lower execution time but lack adaptive security mechanisms. |
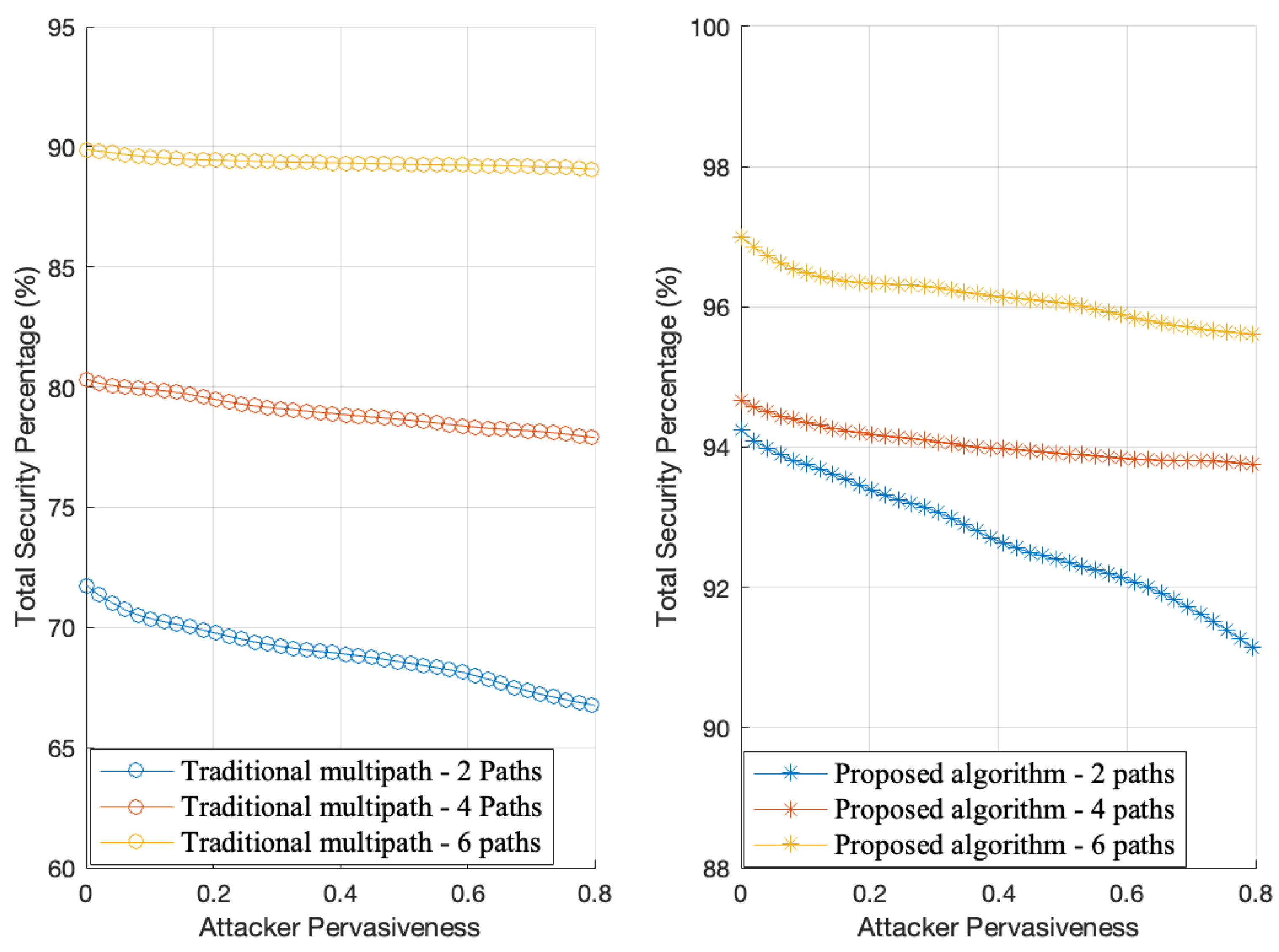
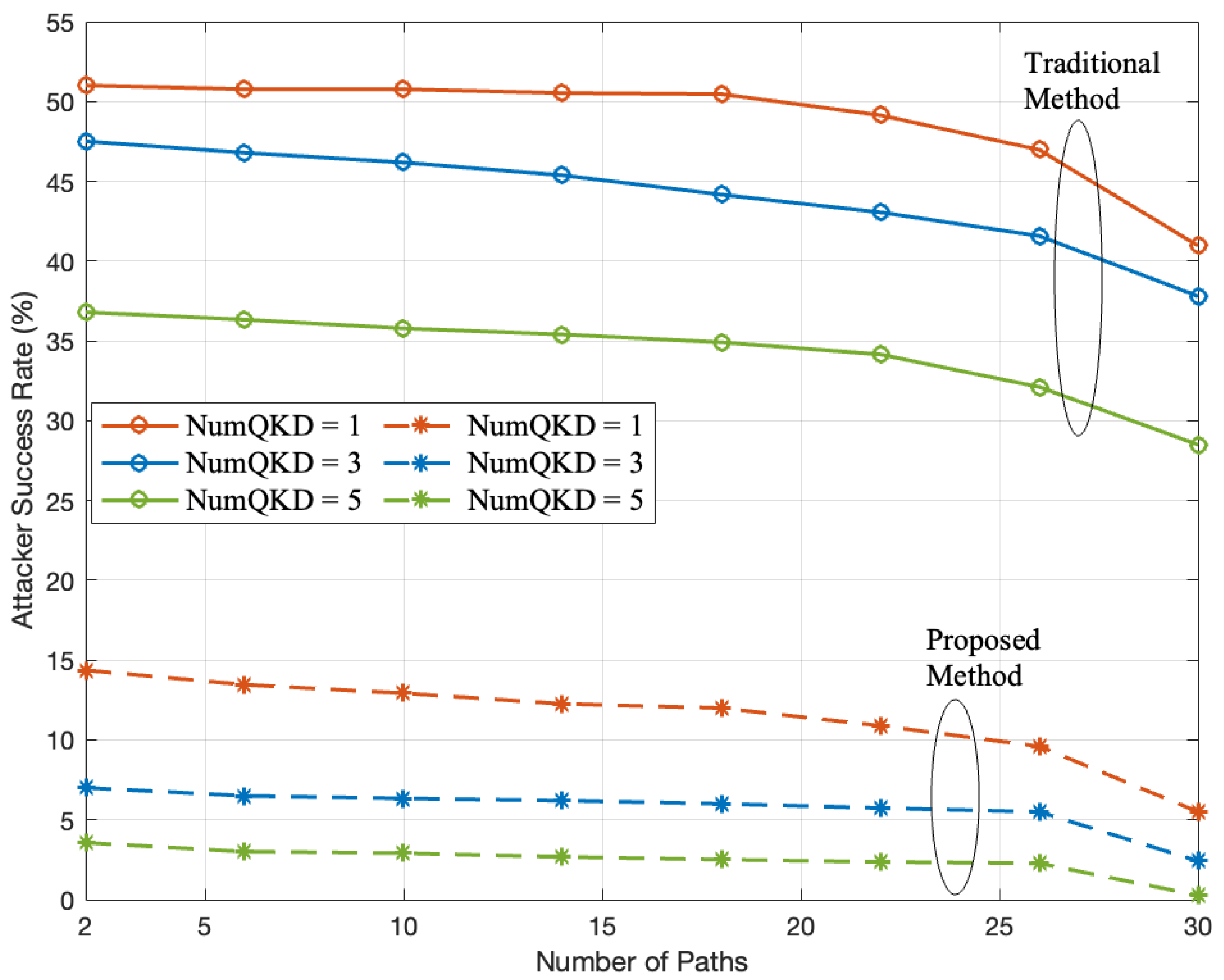
| Attack success rate | 20% attacker pervasiveness | 97.22% lower than traditional methods; |
| Single key transmission | 91.42% lower than traditional methods; | |
| Multiple QKD pairs | 75% lower than traditional methods. | |
| Total security percentage | 20% attacker pervasiveness | 35% higher than traditional methods; |
| 80% attacker pervasiveness | 90% overall security retained, while traditional methods experience a significant security drop. | |
| Security enhancement | Increasing QKD pairs | 79.6% improvement over traditional methods; |
| Single key transmission | 71.15% higher than traditional methods, which are less resilient to attacks. | |
| Impact of multipath selection on attack resilience | Adaptive path selection | Higher resilience in the proposed method as the number of paths increases, whereas traditional methods remain more susceptible to attacks. |
| Effectiveness against interception | Multipath routing strategy | 86.04% stronger defense against interception compared to traditional methods. |
| Success rate improvement | Adaptive multipath strategy | Nearly double the success rate compared to traditional methods. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ghourab, E.M.; Azab, M.; Gračanin, D. A Quantum Key Distribution Routing Scheme for a Zero-Trust QKD Network System: A Moving Target Defense Approach. Big Data Cogn. Comput. 2025, 9, 76. https://doi.org/10.3390/bdcc9040076
Ghourab EM, Azab M, Gračanin D. A Quantum Key Distribution Routing Scheme for a Zero-Trust QKD Network System: A Moving Target Defense Approach. Big Data and Cognitive Computing. 2025; 9(4):76. https://doi.org/10.3390/bdcc9040076
Chicago/Turabian StyleGhourab, Esraa M., Mohamed Azab, and Denis Gračanin. 2025. "A Quantum Key Distribution Routing Scheme for a Zero-Trust QKD Network System: A Moving Target Defense Approach" Big Data and Cognitive Computing 9, no. 4: 76. https://doi.org/10.3390/bdcc9040076
APA StyleGhourab, E. M., Azab, M., & Gračanin, D. (2025). A Quantum Key Distribution Routing Scheme for a Zero-Trust QKD Network System: A Moving Target Defense Approach. Big Data and Cognitive Computing, 9(4), 76. https://doi.org/10.3390/bdcc9040076








