A Novel Multimodal Data Fusion Framework: Enhancing Prediction and Understanding of Inter-State Cyberattacks
Abstract
1. Introduction
- Unlike previous studies that focus solely on either macro-level geopolitical analysis or micro-level technical research, we innovatively apply the concept of multimodal data fusion to the scenario of inter-state cyberattack prediction, overcoming the limitations of traditional single-source data approaches.
- We propose a novel multimodal fusion model based on GNN that can captures temporal dependencies and multi-view interactions simultaneously. That is, the temporal interaction attention mechanism captures the evolving dependencies among various data modalities over time, while the multi-view attention mechanism adaptively weights different modalities to achieve effective integration of heterogeneous data sources.
- To ensure transparency and credibility, we integrate explainable boosting machine and attention-based weight analysis. Through this approach, we identify key geopolitical and economic factors underlying cyberattacks and highlight regional disparities, providing valuable insights for policymakers and cybersecurity professionals.
2. Research Objectives
- RO1: To construct a comprehensive multimodal dataset (Section 4). By integrating data from multiple sources—cyberattack records, geopolitical news events, armed conflicts, international trade, and national attributes—we aim to provide a holistic view of cyberattack behaviors and their underlying factors. The rationale behind choosing these data sources is to incorporate diverse perspectives that offer richer context than any single data source could provide.
- RO2: To design an advanced multimodal data fusion architecture (Section 5.1). Due to the complexity (e.g., interactivity and dynamics) of bilateral relations between nations, we need to design a novel dynamic multi-view graph neural network architecture to capture both interaction features and temporal characteristics among national networks in different domains (i.e., different datasets). This model structure is intended to optimize information integration from different modalities to improve the predictive ability of inter-state cyberattacks (Section 6.2 and Section 7.2).
- RO3: To conduct interpretable analysis of inter-state cyberattacks (Section 5.2). Another primary focus of this study is to enhance the interpretability of cyberattack predictions and bridge the gap between computational methods and geopolitical analysis. We need to leverage some interpretability techniques to provide insights into key characteristics and regional patterns that influence cyberattack activities, thereby offering actionable information for decision-makers (Section 6.3 and Section 7.1).
3. Related Work
3.1. Quantitative Analysis of Inter-State Cyberattacks
3.2. Cyberattack Prediction Based on Digital Media Data
3.3. Advancements in Graph Neural Networks
3.4. Multimodal Data Fusion
3.5. Motivation and Methods
4. Dataset Creation
5. Methodology
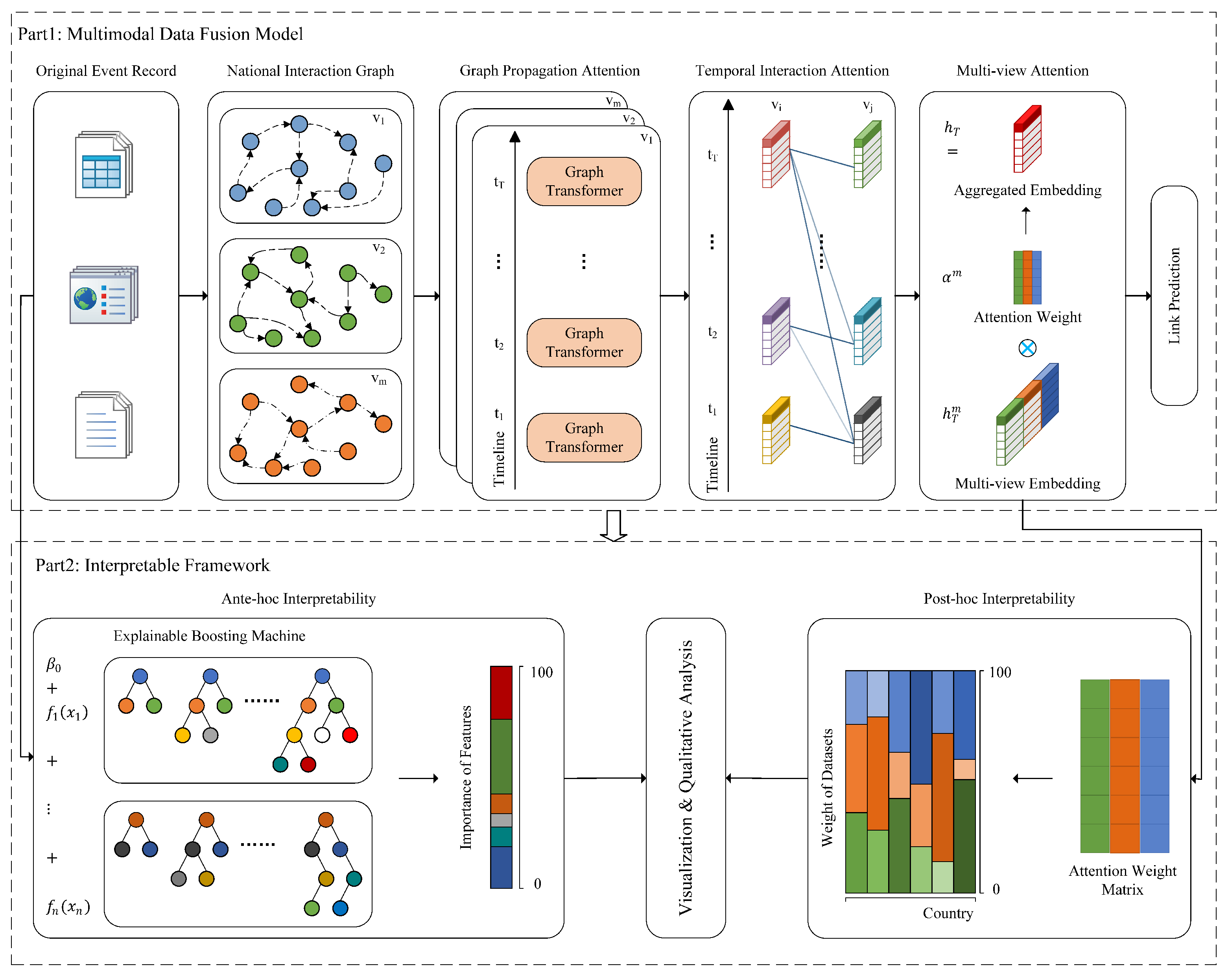
5.1. Multimodal Data Fusion Model
5.1.1. Problem Definition
5.1.2. Graph Propagation Attention
5.1.3. Temporal Interaction Attention
5.1.4. Multi-View Attention
5.1.5. Structure Evolutionary Loss for Link Prediction
5.2. Interpretable Framework
5.2.1. Ante-Hoc Interpretability
5.2.2. Post-Hoc Interpretability
6. Results
6.1. System Design and Implementation
- Data preprocessing and integration. Using a time-window approach, we perform temporal processing on cyber attack data, news event data, armed conflict data, international trade data, and national attribute data, to ensure temporal alignment of different modalities along the time axis (Section 4).
- Multimodal data fusion modeling. We use graph neural networks and attention mechanisms to achieve multimodal data fusion (Section 5.1). First, a static graph neural network is utilized to capture the structural relationships among nodes within each data modality. Then, temporal interaction attention and multi-view attention mechanisms are applied to adaptively weight and integrate information across different modalities.
- Model training and evaluation. We design comparative experiments to validate the effectiveness of the proposed model (Section 6.2). Specifically, the dataset is divided into training, validation and test sets in a chronological order with a ratio of 7:2:1 to ensure effective generalization of the model on future data. The model adopts a single-layer architecture with 16 attention heads and a hidden layer dimension of 256. We use AdamW as the optimizer, set the learning rate to 0.005 and the dropout rate to 0.5, along with an early stopping strategy to prevent overfitting. We use precision, recall, F1-score, and accuracy to evaluate the prediction effect of the model. All experiments are conducted on an NVIDIA RTX 3090 GPU and implemented using PyTorch 2.5.1.
- Ante-hoc interpretability analysis. We employ the EBM to analyze input data and quantify the contribution of each feature as well as pairwise interaction terms to the model’s predictions (Section 6.3.1).
- Post-hoc interpretability Analysis. We extract the attention weights from the multi-view attention module. This allows us to visually represent the proportion of attention allocated to each data modality when making predictions for a given country (Section 6.3.2).
6.2. Validation of the Proposed Model
6.2.1. Comparison of Benchmark Experimental Results
6.2.2. Benefits of Multimodal Data Fusion
6.3. Interpretability of the Proposed Model
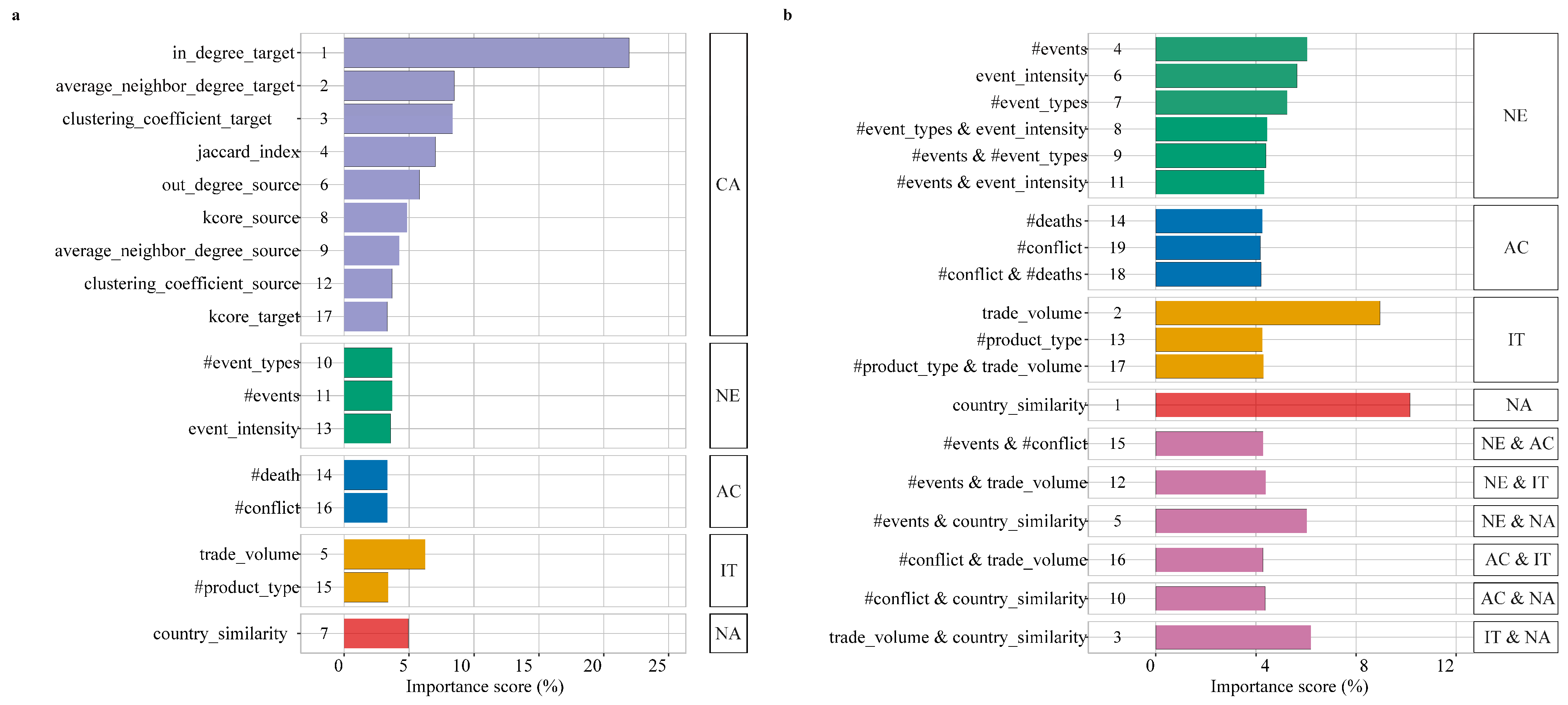
6.3.1. Feature Importance Analysis
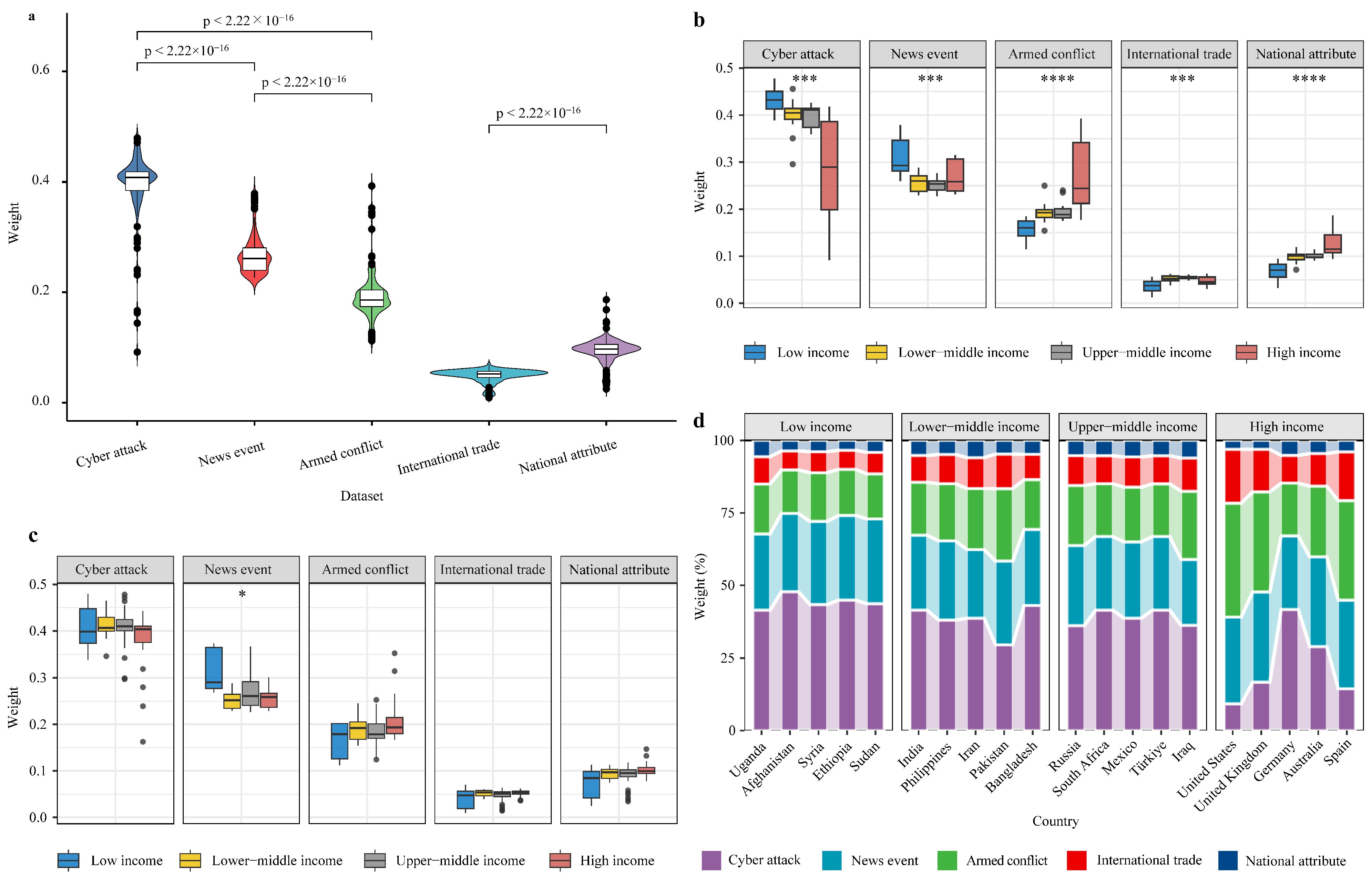
6.3.2. Attention Weight Analysis
7. Discussion
7.1. The Main Factors Affecting the Prediction of Cyberattacks
7.1.1. Feature Diversity Is Momentous for Prediction
7.1.2. Inter-State Cyberattacks Exhibit Distinct Spatial Differences
7.2. Advantages of the Proposed Method
7.2.1. Enhanced Prediction and Theoretical Insights into Cyberattack Behaviors
7.2.2. Broader Applicability to Other State Behaviors
7.3. Limitations and Future Works
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ramadhan, I. The Implication of Cyberspace Towards State Geopolitics. Politicon J. Ilmu Polit. 2021, 3, 161–184. [Google Scholar] [CrossRef]
- Vanberghen, C. Cyberspace and the 21st Century Arms Race. 2023. Available online: https://digitalsociety.eui.eu/publication/cyberspace-and-the-21st-century-arms-race/ (accessed on 3 July 2024).
- ASD. ASD Cyber Threat Report 2022–2023. 2023. Available online: https://www.cyber.gov.au/about-us/view-all-content/reports-and-statistics/asd-cyber-threat-report-july-2022-june-2023 (accessed on 3 July 2024).
- Asal, V.; Mauslein, J.; Murdie, A.; Young, J.; Cousins, K.; Bronk, C. Repression, Education, and Politically Motivated Cyberattacks. J. Glob. Secur. Stud. 2016, 1, 235–247. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, Y.; Lee, C.C.; Li, J.; Hunter, L.Y.; Albert, C.D.; Garrett, E.; Rutland, J. Democracy and Cyberconflict: How Regime Type Affects State-Sponsored Cyberattacks. J. Cyber Policy 2022, 7, 72–94. [Google Scholar]
- Chen, S.; Hao, M.; Ding, F.; Jiang, D.; Dong, J.; Zhang, S.; Guo, Q.; Gao, C. Exploring the Global Geography of Cybercrime and Its Driving Forces. Humanit. Soc. Sci. Commun. 2023, 10, 71. [Google Scholar] [CrossRef]
- Kumar, S.; Carley, K.M. Understanding DDoS Cyber-Attacks Using Social Media Analytics. In Proceedings of the 2016 IEEE Conference on Intelligence and Security Informatics (ISI), Tucson, AZ, USA, 28–30 September 2016; pp. 231–236. [Google Scholar]
- Ben Fredj, O.; Mihoub, A.; Krichen, M.; Cheikhrouhou, O.; Derhab, A. CyberSecurity Attack Prediction: A Deep Learning Approach. In Proceedings of the 13th International Conference on Security of Information and Networks, Istanbul, Turkey, 4–6 November 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 1–6. [Google Scholar]
- Wu, S.; Wang, B.; Wang, Z.; Fan, S.; Yang, J.; Li, J. Joint Prediction on Security Event and Time Interval through Deep Learning. Comput. Secur. 2022, 117, 102696. [Google Scholar] [CrossRef]
- Chen, Y.Z.; Huang, Z.G.; Xu, S.; Lai, Y.C. Spatiotemporal Patterns and Predictability of Cyberattacks. PLoS ONE 2015, 10, e0124472. [Google Scholar] [CrossRef]
- Werner, G.; Yang, S.; McConky, K. Time Series Forecasting of Cyber Attack Intensity. In Proceedings of the 12th Annual Conference on Cyber and Information Security Research, Oak Ridge, TN, USA, 4–6 April 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 1–3. [Google Scholar]
- Xu, M.; Schweitzer, K.M.; Bateman, R.M.; Xu, S. Modeling and Predicting Cyber Hacking Breaches. IEEE Trans. Inf. Forensics Secur. 2017, 13, 2856–2871. [Google Scholar] [CrossRef]
- Maness, R.C.; Valeriano, B.; Jensen, B.; Hedgecock, K.; Macias, J. The Dyadic Cyber Incident and Campaign Data (DCID). 2022. Available online: https://drryanmaness.wixsite.com/cyberconflict/cyber-conflict-dataset (accessed on 16 March 2024).
- Gandhi, R.; Sharma, A.; Mahoney, W.; Sousan, W.; Zhu, Q.; Laplante, P. Dimensions of Cyber-Attacks: Cultural, Social, Economic, and Political. IEEE Technol. Soc. Mag. 2011, 30, 28–38. [Google Scholar] [CrossRef]
- Kazemi, S.M.; Goel, R.; Jain, K.; Kobyzev, I.; Sethi, A.; Forsyth, P.; Poupart, P. Representation Learning for Dynamic Graphs: A Survey. J. Mach. Learn. Res. 2020, 21, 1–73. [Google Scholar]
- Barros, C.D.T.; Mendonça, M.R.F.; Vieira, A.B.; Ziviani, A. A Survey on Embedding Dynamic Graphs. ACM Comput. Surv. 2021, 55, 1–37. [Google Scholar] [CrossRef]
- Yu, B.; Yin, H.; Zhu, Z. Spatio-temporal graph convolutional networks: A deep learning framework for traffic forecasting. In Proceedings of the 27th International Joint Conference on Artificial Intelligence, Stockholm, Sweden, 13–19 July 2018; AAAI Press: Freiburg, Germany, 2018; pp. 3634–3640. [Google Scholar]
- Pareja, A.; Domeniconi, G.; Chen, J.; Ma, T.; Suzumura, T.; Kanezashi, H.; Kaler, T.; Schardl, T.B.; Leiserson, C.E. EvolveGCN: Evolving Graph Convolutional Networks for Dynamic Graphs. Proc. AAAI Conf. Artif. Intell. 2019, 34, 5363–5370. [Google Scholar] [CrossRef]
- Behrouz, A.; Seltzer, M. Anomaly Detection in Multiplex Dynamic Networks: From Blockchain Security to Brain Disease Prediction. arXiv 2022, arXiv:2211.08378. [Google Scholar]
- Li, L.; Duan, L.; Wang, J.; Xie, G.; He, C.; Chen, Z.; Deng, S. Transformer-Based Representation Learning on Temporal Heterogeneous Graphs. In Proceedings of the Asia-Pacific Web (APWeb) and Web-Age Information Management (WAIM) Joint International Conference on Web and Big Data, Nanjing, China, 11–13 August 2022; pp. 385–400. [Google Scholar]
- Hunter, L.Y.; Albert, C.D.; Garrett, E. Factors That Motivate State-Sponsored Cyberattacks. Cyber Def. Rev. 2021, 6, 111–128. [Google Scholar]
- Kumar, S.; Carley, K.M. Approaches to Understanding the Motivations behind Cyber Attacks. In Proceedings of the 2016 IEEE Conference on Intelligence and Security Informatics (ISI), Tucson, AZ, USA, 28–30 September 2016; pp. 307–309. [Google Scholar]
- Akoto, W. International Trade and Cyber Conflict: Decomposing the Effect of Trade on State-Sponsored Cyber Attacks. J. Peace Res. 2021, 58, 1083–1097. [Google Scholar] [CrossRef]
- González-Manzano, L.; de Fuentes, J.M.; Ramos, C.; Sánchez, A.; Quispe, F. Identifying Key Relationships between Nation-State Cyberattacks and Geopolitical and Economic Factors: A Model. Secur. Commun. Netw. 2022, 2022, 5784674. [Google Scholar] [CrossRef]
- Deng, S.; Ning, Y. A Survey on Societal Event Forecasting with Deep Learning. arXiv 2021, arXiv:2112.06345. [Google Scholar]
- Iyda, J.J.; Geetha, P. An Improved Deep Belief Neural Network Based Civil Unrest Event Forecasting in Twitter. Appl. Intell. 2023, 53, 5714–5731. [Google Scholar] [CrossRef]
- Brandt, P.T.; D’Orazio, V.; Khan, L.; Li, Y.F.; Osorio, J.; Sianan, M. Conflict Forecasting with Event Data and Spatio-Temporal Graph Convolutional Networks. Int. Interact. 2022, 48, 800–822. [Google Scholar] [CrossRef]
- Gallotti, R.; Valle, F.; Castaldo, N.; Sacco, P.; De Domenico, M. Assessing the Risks of ‘Infodemics’ in Response to COVID-19 Epidemics. Nat. Hum. Behav. 2020, 4, 1285–1293. [Google Scholar] [CrossRef]
- Wang, Z.; Zhang, Y. DDoS Event Forecasting Using Twitter Data. In Proceedings of the Twenty-Sixth International Joint Conference on Artificial Intelligence, Melbourne, Australia, 19–25 August 2017; pp. 4151–4157. [Google Scholar]
- Deb, A.; Lerman, K.; Ferrara, E. Predicting Cyber-Events by Leveraging Hacker Sentiment. Information 2018, 9, 280. [Google Scholar] [CrossRef]
- Pechi, D. Predicting Cyber-Attacks Using Neural Language Models of Sociopolitical Events. 2019. Available online: https://danpechi.github.io/Dan%20Pechi%20Thesis.pdf (accessed on 24 June 2024).
- Lakha, B.; Duran, J.; Serra, E.; Spezzano, F. Prediction of Future Nation-initiated Cyberattacks from News-based Political Event Graph. In Proceedings of the 2023 IEEE 10th International Conference on Data Science and Advanced Analytics (DSAA), Thessaloniki, Greece, 9–13 October 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–8. [Google Scholar]
- Wu, Z.; Pan, S.; Chen, F.; Long, G.; Zhang, C.; Yu, P.S. A Comprehensive Survey on Graph Neural Networks. IEEE Trans. Neural Netw. Learn. Syst. 2021, 32, 4–24. [Google Scholar] [CrossRef]
- Wu, S.; Sun, F.; Zhang, W.; Xie, X.; Cui, B. Graph Neural Networks in Recommender Systems: A Survey. ACM Comput. Surv. 2022, 55, 1–37. [Google Scholar] [CrossRef]
- Kipf, T.N.; Welling, M. Semi-Supervised Classification with Graph Convolutional Networks. arXiv 2017, arXiv:1609.02907. [Google Scholar]
- Hamilton, W.L.; Ying, R.; Leskovec, J. Inductive Representation Learning on Large Graphs. In Proceedings of the 31st International Conference on Neural Information Processing Systems, Long Beach, CA, USA, 4–9 December 2017; Curran Associates Inc.: Red Hook, NY, USA, 2017; pp. 1025–1035. [Google Scholar]
- Veličković, P.; Cucurull, G.; Casanova, A.; Romero, A.; Liò, P.; Bengio, Y. Graph Attention Networks. In Proceedings of the International Conference on Learning Representations, Vancouver, BC, Canada, 30 April–3 May 2018. [Google Scholar]
- Xu, D.; Ruan, C.; Korpeoglu, E.; Kumar, S.; Achan, K. Inductive Representation Learning on Temporal Graphs. arXiv 2020, arXiv:2002.07962. [Google Scholar]
- Sankar, A.; Wu, Y.; Gou, L.; Zhang, W.; Yang, H. Dysat: Deep neural representation learning on dynamic graphs via self-attention networks. In Proceedings of the 13th International Conference on Web Search and Data Mining, Houston, TX, USA, 3–7 February 2020; Volume 35, pp. 519–527. [Google Scholar]
- Ata, S.K.; Fang, Y.; Wu, M.; Shi, J.; Kwoh, C.K.; Li, X. Multi-View Collaborative Network Embedding. ACM Trans. Knowl. Discov. Data 2021, 15, 1–18. [Google Scholar] [CrossRef]
- Xiao, S.; Li, J.; Lu, J.; Huang, S.; Zeng, B.; Wang, S. Graph Neural Networks for Multi-View Learning: A Taxonomic Review. Artif. Intell. Rev. 2024, 57, 341. [Google Scholar] [CrossRef]
- Xue, H.; Yang, L.; Jiang, W.; Wei, Y.; Hu, Y.; Lin, Y. Modeling Dynamic Heterogeneous Network for Link Prediction Using Hierarchical Attention with Temporal RNN. In Machine Learning and Knowledge Discovery in Databases. ECML PKDD 2020. Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Pawłowski, M.; Wróblewska, A.; Sysko-Romańczuk, S. Effective Techniques for Multimodal Data Fusion: A Comparative Analysis. Sensors 2023, 23, 2381. [Google Scholar] [CrossRef]
- Zhao, F.; Zhang, C.; Geng, B. Deep Multimodal Data Fusion. ACM Comput. Surv. 2024, 56, 1–36. [Google Scholar] [CrossRef]
- Lahat, D.; Adali, T.; Jutten, C. Multimodal Data Fusion: An Overview of Methods, Challenges, and Prospects. Proc. IEEE 2015, 103, 1449–1477. [Google Scholar] [CrossRef]
- Chandrasekaran, G.; Nguyen, T.N.; Hemanth, D.J. Multimodal Sentimental Analysis for Social Media Applications: A Comprehensive Review. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2021, 11, e1415. [Google Scholar] [CrossRef]
- Gandhi, A.; Adhvaryu, K.; Poria, S.; Cambria, E.; Hussain, A. Multimodal Sentiment Analysis: A Systematic Review of History, Datasets, Multimodal Fusion Methods, Applications, Challenges and Future Directions. Inf. Fusion 2023, 91, 424–444. [Google Scholar] [CrossRef]
- Yin, H.; Yang, S.; Song, X.; Liu, W.; Li, J. Deep Fusion of Multimodal Features for Social Media Retweet Time Prediction. World Wide Web 2021, 24, 1027–1044. [Google Scholar] [CrossRef]
- Liu, Z.; Yang, T.; Chen, W.; Chen, J.; Li, Q.; Zhang, J. Sentiment Analysis of Social Media Comments Based on Multimodal Attention Fusion Network. Appl. Soft Comput. 2024, 164, 112011. [Google Scholar] [CrossRef]
- Wang, J.; Yang, S.; Zhao, H.; Yang, Y. Social Media Popularity Prediction with Multimodal Hierarchical Fusion Model. Comput. Speech Lang. 2023, 80, 101490. [Google Scholar] [CrossRef]
- Mondal, M.; Khayati, M.; Sandlin, H.Â.; Cudré-Mauroux, P. A Survey of Multimodal Event Detection Based on Data Fusion. VLDB J. 2025, 34, 1–25. [Google Scholar] [CrossRef]
- Zou, Z.; Gan, H.; Huang, Q.; Cai, T.; Cao, K. Disaster Image Classification by Fusing Multimodal Social Media Data. ISPRS Int. J. Geo-Inf. 2021, 10, 636. [Google Scholar] [CrossRef]
- Algiriyage, N.; Prasanna, R.; Stock, K.; Doyle, E.E.H.; Johnston, D. Multi-Source Multimodal Data and Deep Learning for Disaster Response: A Systematic Review. SN Comput. Sci. 2022, 3, 92. [Google Scholar] [CrossRef]
- Li, J.; Hong, D.; Gao, L.; Yao, J.; Zheng, K.; Zhang, B.; Chanussot, J. Deep Learning in Multimodal Remote Sensing Data Fusion: A Comprehensive Review. Int. J. Appl. Earth Obs. Geoinf. 2022, 112, 102926. [Google Scholar] [CrossRef]
- Luo, L.; Li, B.; Qi, C. Spatiotemporal Multi-graph Convolutional Network-based Provincial-day-level Terrorism Risk Prediction. Risk Anal. 2024, 44, 1514–1534. [Google Scholar] [CrossRef]
- Jiang, D.; Wu, J.; Ding, F.; Ide, T.; Scheffran, J.; Helman, D.; Zhang, S.; Qian, Y.; Fu, J.; Chen, S.; et al. An Integrated Deep-Learning and Multi-Level Framework for Understanding the Behavior of Terrorist Groups. Heliyon 2023, 9, e18895. [Google Scholar] [CrossRef]
- Arbor, N. Digital Attack Map: Top Daily DDoS Attacks Worldwid. 2020. Available online: https://www.digitalattackmap.com/ (accessed on 24 June 2024).
- Nejjari, N.; Lahlou, S.; Fadi, O.; Zkik, K.; Oudani, M.; Benbrahim, H. Conflict Spectrum: An Empirical Study of Geopolitical Cyber Threats from a Social Network Perspective. In Proceedings of the 2021 Eighth International Conference on Social Network Analysis, Management and Security (SNAMS), Gandia, Spain, 6–9 December 2021; pp. 1–7. [Google Scholar]
- Boschee, E.; Lautenschlager, J.; O’Brien, S.; Shellman, S.; Starz, J.; Ward, M. ICEWS Coded Event Data. 2015. Available online: https://dataverse.harvard.edu/dataset.xhtml?persistentId=doi:10.7910/DVN/28075 (accessed on 24 June 2024).
- Kostyuk, N.; Zhukov, Y.M. Invisible Digital Front: Can Cyber Attacks Shape Battlefield Events? J. Confl. Resolut. 2019, 63, 317–347. [Google Scholar] [CrossRef]
- Willett, M. The Cyber Dimension of the Russia–Ukraine War. In Survival: October–November 2022; Routledge: Abingdon, UK, 2022; pp. 7–26. [Google Scholar]
- Davies, S.; Engström, G.; Pettersson, T.; Öberg, M. Organized violence 1989–2023, and the prevalence of organized crime groups. J. Peace Res. 2024, 61, 673–693. [Google Scholar] [CrossRef]
- Brett, N. Economic Information Warfare: Classifying Cyber-attacks against Commodity Value Chains. In Proceedings of the ICCWS 2019 14th International Conference on Cyber Warfare and Security: ICCWS 2019, Stellenbosch, South Africa, 28 February–1 March 2019; pp. 448–455. [Google Scholar]
- Conte, M.; Cotterlaz, P.; Mayer, T. The CEPII Gravity Database. 2022. Available online: https://ideas.repec.org/p/cii/cepidt/2022-05.html (accessed on 13 May 2024).
- Valev, N. TheGlobalEconomy.com: Learning Resources and Data on the World Economy. 2024. Available online: https://www.theglobaleconomy.com/ (accessed on 11 May 2024).
- Mezzour, G.; Carley, L.R.; Carley, K.M. Global Mapping of Cyber Attacks. 2014. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2729302 (accessed on 4 July 2024).
- Levesque, F.L.; Fernandez, J.M.; Somayaji, A. National-Level Risk Assessment: A Multi-Country Study of Malware Infections. In Proceedings of the Workshop on the Economics of Information Security (WEIS), Berkeley, CA, USA, 13–14 June 2016; pp. 1–30. [Google Scholar]
- Shi, Y.; Huang, Z.; Feng, S.; Zhong, H.; Wang, W.; Sun, Y. Masked Label Prediction: Unified Message Passing Model for Semi-Supervised Classification. arXiv 2021, arXiv:2009.03509. [Google Scholar]
- Dwivedi, V.P.; Bresson, X. A Generalization of Transformer Networks to Graphs. arXiv 2021, arXiv:2012.09699. [Google Scholar]
- Li, M.; Ye, Z.; Zhao, H.; Xiao, Y.; Cao, S. Detecting Social Robots Based on Multi-view Graph Transformer. In Proceedings of the CCF Conference on Big Data. Communications in Computer and Information Science; Springer Nature: Berlin/Heidelberg, Germany, 2023; pp. 136–148. [Google Scholar]
- Wei, X.; Zhang, T.; Li, Y.; Zhang, Y.; Wu, F. Multi-Modality Cross Attention Network for Image and Sentence Matching. In Proceedings of the 2020 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), Seattle, WA, USA, 13–19 June 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 10938–10947. [Google Scholar]
- Yang, W.; Zhang, H.; Lim, J.B.; Zhang, Y.; Meng, H. A new chiller fault diagnosis method under the imbalanced data environment via combining an improved generative adversarial network with an enhanced deep extreme learning machine. Eng. Appl. Artif. Intell. 2024, 137, 109218. [Google Scholar] [CrossRef]
- Lou, Y.; Caruana, R.; Gehrke, J. Intelligible Models for Classification and Regression. In Proceedings of the 18th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Beijing China, 12–16 August 2012; ACM: New York, NY, USA, 2012; pp. 150–158. [Google Scholar]
- Nori, H.; Jenkins, S.; Koch, P.; Caruana, R. InterpretML: A Unified Framework for Machine Learning Interpretability. arXiv 2019, arXiv:1909.09223. [Google Scholar]
- Alahmadi, R.; Almujibah, H.; Alotaibi, S.; Alsharif, M.; Bakri, M. Explainable Boosting Machine: A Contemporary Glass-Box Model to Analyze Work Zone-Related Road Traffic Crashes. Safety 2023, 9, 83. [Google Scholar] [CrossRef]
- Peng, C.Y.J.; Lee, K.L.; Ingersoll, G.M. An Introduction to Logistic Regression Analysis and Reporting. J. Educ. Res. 2002, 96, 3–14. [Google Scholar] [CrossRef]
- Ke, G.; Meng, Q.; Finley, T.; Wang, T.; Chen, W.; Ma, W.; Ye, Q.; Liu, T.Y. LightGBM: A Highly Efficient Gradient Boosting Decision Tree. In Proceedings of the Advances in Neural Information Processing Systems; Curran Associates, Inc.: Long Beach, CA, USA, 2017; Volume 30. [Google Scholar]
- Grover, A.; Leskovec, J. node2vec: Scalable feature learning for networks. In Proceedings of the 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. Association for Computing Machinery, San Francisco, CA, USA, 13–17 August 2016; pp. 855–864. [Google Scholar]
- Ribeiro, L.F.; Saverese, P.H.; Figueiredo, D.R. struc2vec: Learning node representations from structural identity. In Proceedings of the 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Halifax, NS, Canada, 13–17 August 2017; pp. 385–394. [Google Scholar]
- Rampášek, L.; Galkin, M.; Dwivedi, V.P.; Luu, A.T.; Wolf, G.; Beaini, D. Recipe for a General, Powerful, Scalable Graph Transformer. Adv. Neural Inf. Process. Syst. 2022, 35, 14501–14515. [Google Scholar]
- Tailor, S.A.; Opolka, F.; Lio, P.; Lane, N.D. Adaptive Filters for Low-Latency and Memory-Efficient Graph Neural Networks. In Proceedings of the International Conference on Learning Representations, Virtual, 25–29 April 2022. [Google Scholar]
- Brody, S.; Alon, U.; Yahav, E. How Attentive are Graph Attention Networks? In Proceedings of the International Conference on Learning Representations, Virtual, 25–29 April 2022. [Google Scholar]
- Yu, L.; Sun, L.; Du, B.; Liu, C.; Xiong, H.; Lv, W. Predicting Temporal Sets with Deep Neural Networks. In Proceedings of the 26th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, New York, NY, USA, 6–10 July 2020; pp. 1083–1091. [Google Scholar]
- Bai, J.; Zhu, J.; Song, Y.; Zhao, L.; Hou, Z.; Du, R.; Li, H. A3T-GCN: Attention Temporal Graph Convolutional Network for Traffic Forecasting. ISPRS Int. J. Geo-Inf. 2021, 10, 485. [Google Scholar] [CrossRef]
- Panagopoulos, G.; Nikolentzos, G.; Vazirgiannis, M. Transfer Graph Neural Networks for Pandemic Forecasting. Proc. AAAI Conf. Artif. Intell. 2021, 35, 4838–4845. [Google Scholar] [CrossRef]
- Bhatti, U.A.; Tang, H.; Wu, G.; Marjan, S.; Hussain, A. Deep Learning with Graph Convolutional Networks: An Overview and Latest Applications in Computational Intelligence. Int. J. Intell. Syst. 2023, 2023, 1–28. [Google Scholar] [CrossRef]
- Ju, W.; Fang, Z.; Gu, Y.; Liu, Z.; Long, Q.; Qiao, Z.; Qin, Y.; Shen, J.; Sun, F.; Xiao, Z.; et al. A Comprehensive Survey on Deep Graph Representation Learning. Neural Netw. 2024, 173, 106207. [Google Scholar] [CrossRef]
- Gibney, E.; Lotero, L.; Cardillo, A.; Hurtado, R.; Gomez-Gardenes, J. Where Is Russia’s Cyberwar? Researchers Decipher Its Strategy. Nature 2022, 603, 775–776. [Google Scholar] [CrossRef] [PubMed]
- Spelta, A.; Pecora, N.; Pagnottoni, P. Assessing Harmfulness and Vulnerability in Global Bipartite Networks of Terrorist-Target Relationships. Soc. Netw. 2023, 72, 22–34. [Google Scholar] [CrossRef]
- Holt, T.J.; Freilich, J.D.; Chermak, S.M. Exploring the Subculture of Ideologically Motivated Cyber-Attackers. J. Contemp. Crim. Justice 2017, 33, 212–233. [Google Scholar] [CrossRef]
- Azubuike, C.F. Cyber Security and International Conflicts: An Analysis of State-Sponsored Cyber Attacks. Nnamdi Azikiwe J. Political Sci. 2023, 8, 101–114. [Google Scholar]
- Netolická, V.; Mareš, M. Arms Race “in Cyberspace”—A Case Study of Iran and Israel. Comp. Strategy 2018, 37, 414–429. [Google Scholar] [CrossRef]
- Dehnavi, E.A.; Fiedler, R.A. Cyber Security As A New Strategic Issue in the Middle East: A Case Study of Persian Gulf and North African Countries. Riv. Ital. Di Filos. Anal. Jr. 2023, 14, 599–606. [Google Scholar]
- Sumari, A.D.W.; Gunawan, D.; Munthaha, F. Cyberspace operations as multiplier power in asymmetric conflict. In Proceedings of the International Conference on Cyber Warfare and Security. Academic Conferences International Limited, West Lafayette, IN, USA, 24–25 March 2014; p. 324. [Google Scholar]
- Li, T.Y. Asymmetry in the Digital Age: Cyber Deterrence Strategies for Small States. J. Strateg. Secur. 2024, 17, 71–88. [Google Scholar] [CrossRef]
- Kausch, K. Cheap Havoc: How Cyber-Geopolitics Will Destabilize the Middle East. 2022. Available online: https://www.jstor.org/stable/resrep18776 (accessed on 4 July 2024).
- Bendiek, A.; Metzger, T. Deterrence theory in the cyber-century. In INFORMATIK 2015; Gesellschaft für Informatik eV: Bonn, Germany, 2015; pp. 553–570. [Google Scholar]
- Smeets, M. The Strategic Promise of Offensive Cyber Operations. Strateg. Stud. Q. 2018, 12, 90–113. [Google Scholar]
- Huskaj, G.; Blix, F.; Axelsson, S. A Theory of Offensive Cyberspace Operations and Its Policy and Strategy Implications. In Proceedings of the 23rd European Conference on Cyber Warfare and Security, Jyvaskyla, Finland, 27–28 June 2024; pp. 214–223. [Google Scholar]
- Tang, M. Huawei Versus the United States? The Geopolitics of Exterritorial Internet Infrastructure. Int. J. Commun. 2020, 14, 4556–4577. [Google Scholar]
- Ran, T.; Liu, Z. “The Russia-Ukraine War” or “The US-Russia War”? Thematic Analysis of Global Times’ Coverage of the Russia-Ukraine War. Media Asia 2024, 51, 3–32. [Google Scholar] [CrossRef]
- XinHuaNet. The United States’ Global Confrontation and Conflict: 1979–2020. 2021. Available online: http://www.xinhuanet.com/2021-12/13/c_1128158270.htm (accessed on 4 July 2024).
- Kozera, C.; Bernat, P.; Gürer, C.; Popławski, B.; Sözer, M. Game of Proxies—Towards a New Model of Warfare: Experiences from the CAR, Libya, Mali, Syria, and Ukraine. Secur. Def. Q. 2020, 31, 77–97. [Google Scholar] [CrossRef]
- Gold, J. The Five Eyes and Offensive Cyber Capabilities: Building a ‘Cyber Deterrence Initiative’. 2020. Available online: https://ccdcoe.org/library/publications/the-five-eyes-and-offensive-cyber-capabilities-building-a-cyber-deterrence-initiative/ (accessed on 4 July 2024).
- BBC. US ‘Launched Cyber-Attack on Iran Weapons Systems’. 2019. Available online: https://www.bbc.com/news/world-us-canada-48735097 (accessed on 4 July 2024).
- Sykulski, L. Old Methods in the New Framework: Strategy of Grey Zones in Hybrid Warfare. Strateg. XXI Natl. Def. Coll. 2021, 1, 162–170. [Google Scholar] [CrossRef]
- Dziwisz, D. Rethinking Future Conflicts. Politeja 2024, 21, 281–309. [Google Scholar] [CrossRef]
- Van der Togt, T. In search of a European Russia strategy. Atl. Perspect. 2020, 44, 36–41. [Google Scholar]
- Jensen, B.; Valeriano, B.; Maness, R. Fancy Bears and Digital Trolls: Cyber Strategy with a Russian Twist. In Military Strategy in the 21st Century; Routledge: Abingdon, UK, 2020; pp. 58–80. [Google Scholar]
- Guchua, A.; Zedelashvili, T.; Giorgadze, G. Geopolitics of the Russia-Ukraine War and Russian cyber attacks on Ukraine-Georgia and expected threats. Ukr. Policymaker 2022, 10, 26–36. [Google Scholar] [CrossRef]
- Park, J.H.; Kwon, H.Y. Cyberattack detection model using community detection and text analysis on social media. ICT Express 2022, 8, 499–506. [Google Scholar] [CrossRef]
- Abusaqer, M.; Benaoumeur Senouci, M.; Magel, K. Twitter User Sentiments Analysis: Health System Cyberattacks Case Study. In Proceedings of the 2023 International Conference on Artificial Intelligence in Information and Communication (ICAIIC), Bali, Indonesia, 20–23 February 2023; pp. 18–24. [Google Scholar]
- Serrano, S.; Smith, N.A. Is Attention Interpretable? In Proceedings of the 57th Annual Meeting of the Association for Computational Linguistics, Florence, Italy, 28 July–2 August 2019. [Google Scholar]
- Jain, S.; Wallace, B.C. Attention is not Explanation. In Proceedings of the 2019 Conference of the North American Chapter of the Association for Computational Linguistics: Human Language Technologies, Volume 1 (Long and Short Papers), Minneapolis, MN, USA, 2–7 June 2019. [Google Scholar]
- Zhao, W.X.; Zhou, K.; Li, J.; Tang, T.; Wang, X.; Hou, Y.; Min, Y.; Zhang, B.; Zhang, J.; Dong, Z.; et al. A survey of large language models. arXiv 2023, arXiv:2303.18223. [Google Scholar]
- Chen, Z.; Mao, H.; Li, H.; Jin, W.; Wen, H.; Wei, X.; Wang, S.; Yin, D.; Fan, W.; Liu, H.; et al. Exploring the Potential of Large Language Models (LLMs)in Learning on Graphs. SIGKDD Explor. Newsl. 2024, 25, 42–61. [Google Scholar] [CrossRef]
- Jin, B.; Liu, G.; Han, C.; Jiang, M.; Ji, H.; Han, J. Large Language Models on Graphs: A Comprehensive Survey. IEEE Trans. Knowl. Data Eng. 2024, 36, 8622–8642. [Google Scholar] [CrossRef]
| Data | Time Scale | #Snapshots | #Nodes/Snapshot | #Edges/Snapshot | #Edge Features |
|---|---|---|---|---|---|
| Cyber attack | Day | 366 | 220 | 1681 | 3 |
| News event | Day | 366 | 179 | 495 | 2 |
| Armed conflict | Day | 366 | 66 | 201 | 2 |
| International trade | Year | 1 | 210 | 29,488 | 2 |
| National similarity | Year | 1 | 222 | 49,062 | 1 |
| Model Types | Models | Precision | Recall | F1 | Accuracy |
|---|---|---|---|---|---|
| Traditional machine learning models | LR | 0.878 ± 0.029 | 0.711 ± 0.102 | 0.783 ± 0.070 | 0.807 ± 0.052 |
| GBDT | 0.880 ± 0.035 | 0.713 ± 0.102 | 0.784 ± 0.070 | 0.808 ± 0.054 | |
| Random walk-based graph embedding models | node2vec | 0.712 ± 0.027 | 0.843 ± 0.076 | 0.771 ± 0.044 | 0.752 ± 0.040 |
| struc2vec | 0.722 ± 0.028 | 0.783 ± 0.076 | 0.750 ± 0.047 | 0.742 ± 0.041 | |
| Static graph neural network models | GCN | 0.749 ± 0.008 | 0.795 ± 0.043 | 0.768 ± 0.020 | 0.763 ± 0.011 |
| GraphSAGE | 0.776 ± 0.005 | 0.878 ± 0.018 | 0.824 ± 0.007 | 0.812 ± 0.006 | |
| GPS | 0.829 ± 0.017 | 0.778 ± 0.065 | 0.800 ± 0.027 | 0.808 ± 0.018 | |
| EGC | 0.803 ± 0.010 | 0.836 ± 0.024 | 0.818 ± 0.011 | 0.816 ± 0.008 | |
| GATv2 | 0.779 ± 0.003 | 0.887 ± 0.018 | 0.829 ± 0.007 | 0.817 ± 0.006 | |
| Dynamic graph neural network models | STGCN | 0.809 ± 0.006 | 0.843 ± 0.013 | 0.825 ± 0.007 | 0.823 ± 0.006 |
| DySAT | 0.786 ± 0.008 | 0.872 ± 0.014 | 0.826 ± 0.007 | 0.817 ± 0.006 | |
| DNNTSP | 0.805 ± 0.009 | 0.854 ± 0.009 | 0.828 ± 0.008 | 0.824 ± 0.008 | |
| A3T-GCN | 0.751 ± 0.008 | 0.851 ± 0.026 | 0.797 ± 0.012 | 0.784 ± 0.009 | |
| MPNN+LSTM | 0.805 ± 0.014 | 0.843 ± 0.023 | 0.822 ± 0.010 | 0.819 ± 0.009 | |
| Dynamic multi-view graph neural network models | Our method | 0.821 ± 0.008 | 0.856 ± 0.017 | 0.838 ± 0.006 | 0.835 ± 0.005 |
| Datasets | Metric | |||||||
|---|---|---|---|---|---|---|---|---|
| Cyber Attack | News Event | Armed Conflict | International Trade | National Attribute | Precision | Recall | F1 | Accuracy |
| ✓ | 0.780 ± 0.011 | 0.871 ± 0.018 | 0.822 ± 0.007 | 0.813 ± 0.007 | ||||
| ✓ | ✓ | 0.820 ± 0.013 | 0.853 ± 0.022 | 0.836 ± 0.007 | 0.833 ± 0.006 | |||
| ✓ | ✓ | 0.824 ± 0.014 | 0.846 ± 0.024 | 0.834 ± 0.014 | 0.833 ± 0.012 | |||
| ✓ | ✓ | 0.821 ± 0.005 | 0.851 ± 0.022 | 0.835 ± 0.010 | 0.833 ± 0.008 | |||
| ✓ | ✓ | 0.821 ± 0.009 | 0.850 ± 0.022 | 0.834 ± 0.008 | 0.832 ± 0.006 | |||
| ✓ | ✓ | ✓ | ✓ | ✓ | 0.821 ± 0.008 | 0.856 ± 0.017 | 0.838 ± 0.006 | 0.835 ± 0.005 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dong, J.; Hao, M.; Ding, F.; Chen, S.; Wu, J.; Zhuo, J.; Jiang, D. A Novel Multimodal Data Fusion Framework: Enhancing Prediction and Understanding of Inter-State Cyberattacks. Big Data Cogn. Comput. 2025, 9, 63. https://doi.org/10.3390/bdcc9030063
Dong J, Hao M, Ding F, Chen S, Wu J, Zhuo J, Jiang D. A Novel Multimodal Data Fusion Framework: Enhancing Prediction and Understanding of Inter-State Cyberattacks. Big Data and Cognitive Computing. 2025; 9(3):63. https://doi.org/10.3390/bdcc9030063
Chicago/Turabian StyleDong, Jiping, Mengmeng Hao, Fangyu Ding, Shuai Chen, Jiajie Wu, Jun Zhuo, and Dong Jiang. 2025. "A Novel Multimodal Data Fusion Framework: Enhancing Prediction and Understanding of Inter-State Cyberattacks" Big Data and Cognitive Computing 9, no. 3: 63. https://doi.org/10.3390/bdcc9030063
APA StyleDong, J., Hao, M., Ding, F., Chen, S., Wu, J., Zhuo, J., & Jiang, D. (2025). A Novel Multimodal Data Fusion Framework: Enhancing Prediction and Understanding of Inter-State Cyberattacks. Big Data and Cognitive Computing, 9(3), 63. https://doi.org/10.3390/bdcc9030063







