Network Traffic Analysis Based on Graph Neural Networks: A Scoping Review
Abstract
1. Introduction
- Technical Workflow Framework: A structured technical workflow framework for GNN-based traffic analysis is introduced, serving as a valuable guide for researchers and practitioners.
- Comprehensive Task-Based Analysis: This review presents a thorough review of 78 studies categorized by prediction tasks. It summarizes common graph construction methods and node aggregation strategies, along with a comparative analysis of techniques in typical task scenarios.
- Challenge-Driven Perspective: A unique challenge-driven perspective is provided, analyzing how representative works tackle key traffic analysis challenges using GNN-based methods.
- Curated Resource Collection: A selection of publicly available datasets and open-source implementations is provided to support reproducible research and benchmarking in GNN-based traffic analysis.
2. Review Method
3. Related Surveys
3.1. Surveys on Network Traffic Analysis
3.2. Surveys on GNN-Based Traffic Analysis Tasks
4. Challenges and Opportunities
4.1. Challenges in Network Traffic Analysis
4.1.1. Training Data Challenges
4.1.2. Feature Extraction Challenges
4.1.3. Model Design Challenges
4.2. Advantages of GNNs
5. Background Knowledge and General Framework
5.1. GNN Background Knowledge
5.1.1. General Graph Structure
5.1.2. Graph Tasks
5.1.3. Representative GNN Architectures
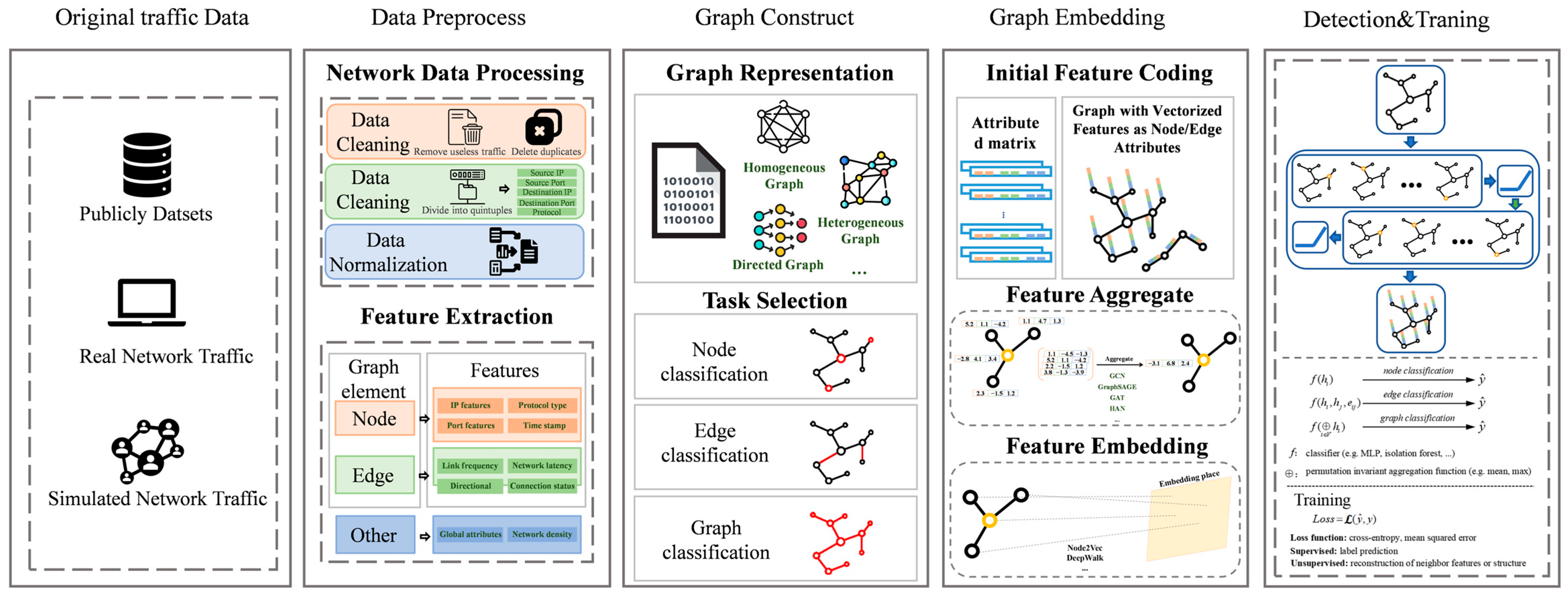
5.2. General Framework
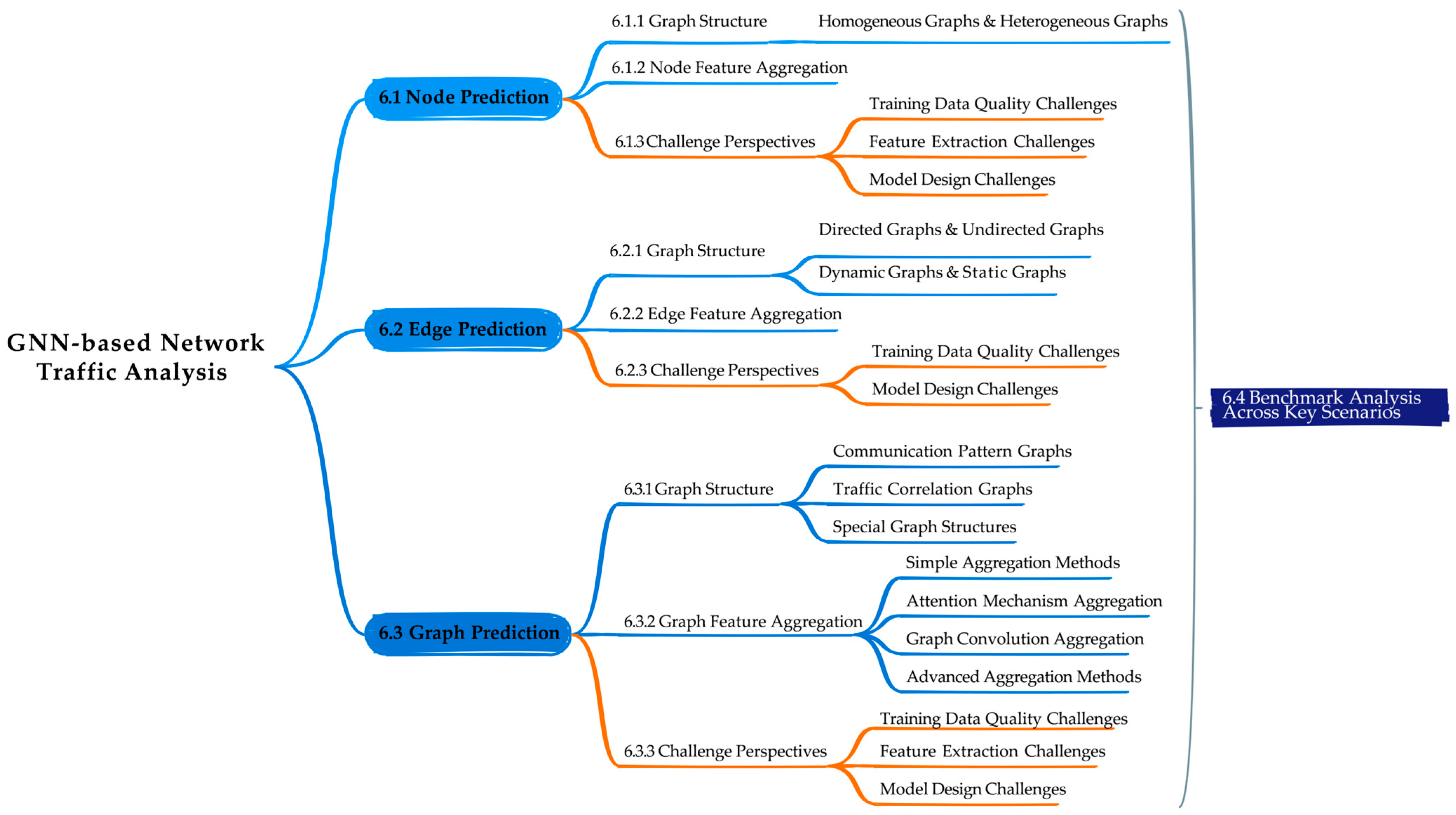
6. GNN-Based Network Traffic Analysis
6.1. Node Prediction
6.1.1. Graph Structure
6.1.2. Node Feature Aggregation
6.1.3. Challenge Perspectives
6.2. Edge Prediction
6.2.1. Graph Structure
6.2.2. Edge Feature Aggregation
6.2.3. Challenge Perspectives
6.3. Graph Prediction
6.3.1. Graph Structure
6.3.2. Graph Feature Aggregation
6.3.3. Challenge Perspectives
6.4. Benchmark Analysis Across Key Scenarios
7. Public Datasets and Open-Source Code
7.1. Public Datasets
7.2. Open-Source Code
8. Discussion
8.1. Limitations
8.2. Future Research Directions
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- International Telecommunication Union. Facts and Figures 2024. Available online: https://www.itu.int/itu-d/reports/statistics/facts-figures-2024/index/ (accessed on 27 June 2025).
- Sperotto, A.; Sadre, R.; Van Vliet, F.; Pras, A. A Labeled Data Set for Flow-Based Intrusion Detection. In IP Operations and Management; Nunzi, G., Scoglio, C., Li, X., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5843, pp. 39–50. [Google Scholar] [CrossRef]
- Fogla, P.; Lee, W. Evading Network Anomaly Detection Systems: Formal Reasoning and Practical Techniques. In Proceedings of the 13th ACM Conference on Computer and Communications Security (CCS 2006), Alexandria, VA, USA, 30 October–3 November 2006; pp. 59–68. [Google Scholar] [CrossRef]
- Finsterbusch, M.; Richter, C.; Rocha, E. A Survey of Payload-Based Traffic Classification Approaches. IEEE Commun. Surv. Tutor. 2014, 16, 1135–1156. [Google Scholar] [CrossRef]
- Mishra, P.; Varadharajan, V.; Tupakula, U. A Detailed Investigation and Analysis of Using Machine Learning Techniques for Intrusion Detection. IEEE Commun. Surv. Tutor. 2019, 21, 686–728. [Google Scholar] [CrossRef]
- Gibert, D.; Mateu, C.; Planes, J. The Rise of Machine Learning for Detection and Classification of Malware: Research Developments, Trends and Challenges. J. Netw. Comput. Appl. 2020, 153, 102526. [Google Scholar] [CrossRef]
- Wang, Q.; Xie, M.; Wu, Z.; Dong, Y. Network Intrusion Detection and Dynamic Defense Method Based on Unsupervised Machine Learning. In Proceedings of the 2023 International Conference on Computer Simulation and Modeling, Information Security (CSMIS), Buenos Aires, Argentina, 15–17 November 2023; pp. 75–80. [Google Scholar] [CrossRef]
- Ren, Y. Analysis of Network Intrusion Detection Based on Machine Learning. In Proceedings of the 2022 4th International Conference on Artificial Intelligence and Advanced Manufacturing (AIAM), Hamburg, Germany, 7–9 October 2022; pp. 699–702. [Google Scholar] [CrossRef]
- Zhang, J.; Pan, L.; Han, Q.-L.; Chen, C.; Wen, S.; Xiang, Y. Deep Learning Based Attack Detection for Cyber-Physical System Cybersecurity: A Survey. IEEE/CAA J. Autom. Sin. 2022, 9, 377–391. [Google Scholar] [CrossRef]
- Pan, Y.; Zhang, X.; Jiang, H.; Li, C. A Network Traffic Classification Method Based on Graph Convolution and LSTM. IEEE Access 2021, 9, 158261–158272. [Google Scholar] [CrossRef]
- Xue, Y.; Wang, D.; Zhang, L. Traffic Classification: Issues and Challenges. J. Commun. 2013, 8, 240–248. [Google Scholar] [CrossRef]
- Lotfollahi, M.; Jafari Siavoshani, M.; Shirali Hossein Zade, R. Deep Packet: A Novel Approach for Encrypted Traffic Classification Using Deep Learning. Soft Comput. 2020, 24, 1999–2012. [Google Scholar] [CrossRef]
- Li, Y.; Xie, S.; Wan, Z.; Lv, H.; Song, H.; Lv, Z. Graph-powered Learning Methods in the Internet of Things: A Survey. Mach. Learn. Appl. 2023, 11, 100441. [Google Scholar] [CrossRef]
- Shen, Y.; Li, Q.; Xu, C.; Chang, C.; Yin, Q. Graph-based Context Learning Network for Infrared Small Target Detection. Neurocomputing 2025, 616, 128949. [Google Scholar] [CrossRef]
- Subedi, R.; Wei, L.; Gao, W.; Chakraborty, S.; Liu, Y. Empowering Active Learning for 3D Molecular Graphs with Geometric Graph Isomorphism. In Proceedings of the 38th Conference on Neural Information Processing Systems (NeurIPS), Vancouver, BC, Canada, 10–16 December 2024; Curran Associates Inc.: Red Hook, NY, USA, 2024; pp. 1–14. Available online: https://dl.acm.org/doi/10.5555/3737916.3739679 (accessed on 27 June 2025).
- Tan, J.; Jin, H.; Zhang, H.; Zhang, Y.; Chang, D.; Liu, X.; Zhang, H. A Survey: When Moving Target Defense Meets Game Theory. Comput. Sci. Rev. 2023, 48, 100544. [Google Scholar] [CrossRef]
- He, W.; Tan, J.; Guo, Y.; Shang, K.; Zhang, H. A Deep Reinforcement Learning-based Deception Asset Selection Algorithm in Differential Games. IEEE Trans. Inf. Forensics Secur. 2024, 19, 8353–8368. [Google Scholar] [CrossRef]
- Goli, Y.D.; Ambika, R. Network Traffic Classification Techniques—A Review. In Proceedings of the 2018 International Conference on Computational Techniques, Electronics and Mechanical Systems (CTEMS), Theni, India, 21–22 December 2018; IEEE: New York, NY, USA, 2018; pp. 231–236. [Google Scholar] [CrossRef]
- Bhatla, N.; Malik, M. Network Traffic Classification Techniques: A Review. In Computational Intelligence for Engineering and Management Applications; Lecture Notes in Electrical Engineering, 1045; Springer: Singapore, 2023; pp. 371–388. [Google Scholar] [CrossRef]
- Azab, A.; Khasawneh, M.; Alrabaee, S.; Choo, K.-K.R.; Sarsour, M. Network Traffic Classification: Techniques, Datasets, and Challenges. Digit. Commun. Netw. 2022, 10, 676–692. [Google Scholar] [CrossRef]
- Getman, A.I.; Ikonnikova, M.K. A Survey of Network Traffic Classification Methods Using Machine Learning. Program. Comput. Softw. 2022, 48, 413–423. [Google Scholar] [CrossRef]
- Papadogiannaki, E.; Ioannidis, S. A Survey on Encrypted Network Traffic Analysis Applications, Techniques, and Countermeasures. ACM Comput. Surv. 2021, 54, 123:1–123:35. [Google Scholar] [CrossRef]
- Meng, S.; Ke, Y.; Li, X.; Zhang, L.; Kou, J.; Yu, S.; Li, Q.; Xu, K. Machine Learning-Powered Encrypted Network Traffic Analysis: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2023, 25, 791–824. [Google Scholar] [CrossRef]
- Bilot, T.; El Madhoun, N.; Al Agha, K.; Zouaoui, A. Graph Neural Networks for Intrusion Detection: A Survey. IEEE Access 2023, 11, 49114–49139. [Google Scholar] [CrossRef]
- Zhong, M.; Lin, M.; Zhang, C.; Xu, Z. A Survey on Graph Neural Networks for Intrusion Detection Systems: Methods, Trends and Challenges. Comput. Secur. 2024, 141, 103821. [Google Scholar] [CrossRef]
- Dong, G.; Tang, M.; Wang, Z.; Gao, J.; Guo, S.; Cai, L.; Gutierrez, R.; Campbel, B.; Barnes, L.E.; Boukhechba, M. Graph Neural Networks in IoT: A Survey. ACM Trans. Sens. Netw. 2023, 19, 47. [Google Scholar] [CrossRef]
- Danesh Pazho, A.; Alinezhad Noghre, G.; Purkayastha, A.A.; Vempati, J.; Martin, O.; Tabkhi, H. A Survey of Graph-based Deep Learning for Anomaly Detection in Distributed Systems. IEEE Trans. Knowl. Data Eng. 2024, 36, 1–20. [Google Scholar] [CrossRef]
- Yan, B.; Yang, C.; Shi, C. Graph Mining for Cybersecurity: A Survey. ACM Trans. Knowl. Discov. Data 2024, 18, 47. [Google Scholar] [CrossRef]
- Bilot, T.; El Madhoun, N.; Al Agha, K.; Zouaoui, A. A Survey on Malware Detection with Graph Representation Learning. ACM Comput. Surv. 2024, 56, 278. [Google Scholar] [CrossRef]
- He, M.; Wang, X.; Zhou, J.; Xi, Y.; Jin, L.; Wang, X. Deep-Feature-Based Autoencoder Network for Few-Shot Malicious Traffic Detection. Secur. Commun. Netw. 2021, 2021, 6659022. [Google Scholar] [CrossRef]
- Xu, C.; Shen, J.; Du, X. A Method of Few-Shot Network Intrusion Detection Based on Meta-Learning Framework. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3540–3552. [Google Scholar] [CrossRef]
- Liu, J.; Xiao, Q.; Xin, L.; Wang, Q.; Yao, Y.; Jiang, Z. M3F: A Novel Multi-Session and Multi-Protocol Based Malware Traffic Fingerprinting. Comput. Netw. 2023, 227, 109723. [Google Scholar] [CrossRef]
- Zhao, J.; Li, Q.; Hong, Y.; Shen, M. MetaRockETC: Adaptive Encrypted Traffic Classification in Complex Network Environments via Time Series Analysis and Meta-Learning. IEEE Trans. Netw. Serv. Manag. 2024, 21, 2460–2476. [Google Scholar] [CrossRef]
- Ma, W.; Liu, R.; Li, K.; Yan, S.; Guo, J. An Adversarial Domain Adaptation Approach Combining Dual Domain Pairing Strategy for IoT Intrusion Detection under Few-Shot Samples. Inf. Sci. 2023, 629, 719–745. [Google Scholar] [CrossRef]
- Niu, W.; Ma, X.; Lin, S.; Wang, S.; Qian, X.; Lin, X.; Wang, Y.; Ren, B. PatDNN: Achieving Real-Time DNN Execution on Mobile Devices with Pattern-based Weight Pruning. In Proceedings of the 25th International Conference on Architectural Support for Programming Languages and Operating Systems (ASPLOS), Lausanne, Switzerland, 16–20 March 2020; pp. 907–922. [Google Scholar] [CrossRef]
- He, M.; Huang, Y.; Wang, X.; Wei, P.; Wang, X. A Lightweight and Efficient IoT Intrusion Detection Method Based on Feature Grouping. IEEE Internet Things J. 2024, 11, 2935–2949. [Google Scholar] [CrossRef]
- Maniriho, P.; Mahmood, A.N.; Chowdhury, M.J.M. A Survey of Recent Advances in Deep Learning Models for Detecting Malware in Desktop and Mobile Platforms. ACM Comput. Surv. 2024, 56, 145. [Google Scholar] [CrossRef]
- Hamilton, W.L. The Graph Neural Network Model. In Graph Representation Learning; Springer: Cham, Switzerland, 2020; pp. 51–70. [Google Scholar] [CrossRef]
- Kipf, T.N.; Welling, M. Semi-Supervised Classification with Graph Convolutional Networks. In Proceedings of the 5th International Conference on Learning Representations (ICLR), Toulon, France, 24–26 April 2017. [Google Scholar]
- Kim, J.; Kim, T.; Kim, S.; Hong, S.; Shin, J. Edge-labeling Graph Neural Network for Few-Shot Learning. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), Long Beach, CA, USA, 15–20 June 2019; pp. 11575–11584. [Google Scholar] [CrossRef]
- Veličković, P.; Cucurull, G.; Casanova, A.; Romero, A.; Liò, P.; Bengio, Y. Graph Attention Networks. In Proceedings of the 6th International Conference on Learning Representations (ICLR), Vancouver, BC, Canada, 30 April–3 May 2018. [Google Scholar]
- Xu, K.; Hu, W.; Leskovec, J.; Jegelka, S. How Powerful Are Graph Neural Networks? In Proceedings of the 7th International Conference on Learning Representations (ICLR), New Orleans, LA, USA, 6–9 May 2019.
- Yang, Z.; Yang, D.; Dyer, C.; He, X.; Smola, A.; Hovy, E. Hierarchical Attention Networks for Document Classification. In Proceedings of the 2016 Conference of the North American Chapter of the Association for Computational Linguistics: Human Language Technologies (NAACL HLT), San Diego, CA, USA, 12–17 June 2016; pp. 1480–1489. [Google Scholar] [CrossRef]
- Dvorak, S.; Prochazka, P.; Bajer, L. GNN-Based Malicious Network Entities Identification in Large-Scale Network Data. In Proceedings of the 2022 IEEE/IFIP Network Operations and Management Symposium (NOMS), Budapest, Hungary, 25–29 April 2022; pp. 1–4. [Google Scholar] [CrossRef]
- Zhou, X.; Liang, W.; Li, W.; Yan, K.; Shimizu, S.; Wang, K.I.-K. Hierarchical Adversarial Attacks Against Graph-Neural-Network-Based IoT Network Intrusion Detection System. IEEE Internet Things J. 2022, 9, 9310–9319. [Google Scholar] [CrossRef]
- Bakar, R.A.; De Marinis, L.; Cugini, F.; Tornatore, M.; Svaluto Moreolo, M.; Wang, J.; Chaux, C.; Velasco, L. FTG-net-e: A Hierarchical Ensemble Graph Neural Network for DDoS Attack Detection. Comput. Netw. 2024, 245, 110508. [Google Scholar] [CrossRef]
- Shen, L.; Fang, M.; Xu, J. GHGDroid: Global Heterogeneous Graph-Based Android Malware Detection. Comput. Secur. 2024, 141, 103846. [Google Scholar] [CrossRef]
- Liu, Z.; Chen, C.; Yang, X.; Hu, J.; Ding, K.; Wang, Y.; Xiong, H. Heterogeneous Graph Neural Networks for Malicious Account Detection. arXiv 2020, arXiv:2002.12307. [Google Scholar] [CrossRef]
- Presekal, A.; Stefanov, A.; Rajkumar, V.S.; Palensky, P. Attack Graph Model for Cyber-Physical Power Systems Using Hybrid Deep Learning. IEEE Trans. Smart Grid 2023, 14, 4007–4020. [Google Scholar] [CrossRef]
- Wu, Y.; Dai, H.-N.; Tang, H. Graph Neural Networks for Anomaly Detection in Industrial Internet of Things. IEEE Internet Things J. 2022, 9, 9214–9231. [Google Scholar] [CrossRef]
- Li, G.; Zhang, F.; Pang, J.; Zhang, T.; Pan, M.; Li, X.; Zhang, C. Functional Scenario Classification for Android Applications Using GNNs. In Proceedings of the 13th Asia-Pacific Symposium on Internetware (Internetware ‘22), Wuhan, China, 17–18 December 2022. [Google Scholar] [CrossRef]
- Gu, Z.; Gou, G.; Liu, C.; Chen, Y.; Zhang, X.; Lin, Z.; Xiong, G.; Jia, W. Let Gambling Hide Nowhere: Detecting Illegal Mobile Gambling Apps Via Heterogeneous Graph-Based Encrypted Traffic Analysis. Comput. Netw. 2024, 243, 110278. [Google Scholar] [CrossRef]
- Zhang, J.; Liu, X.; Yan, Q.; Liu, B.; Sun, M.; Peng, H.; Lu, J.; Yang, Q.; Wei, T. Multi-attributed Heterogeneous Graph Convolutional Network for Bot Detection. Inf. Sci. 2020, 537, 380–393. [Google Scholar] [CrossRef]
- Simon, M.; Pitner, T.; Safarik, V.; Blazek, L.; Dobias, J.; Hanacek, P. Malicious Internet Entity Detection Using Local Graph Inference. IEEE Trans. Inf. Forensics Secur. 2024, 19, 3554–3566. [Google Scholar] [CrossRef]
- Chowdhury, S.; Khanzadeh, M.; Akula, R.; Zhang, F.; Zhang, S.; Medal, H.; Marufuzzaman, M.; Bian, L. Botnet Detection Using Graph-Based Feature Clustering. J. Big Data 2017, 4, 14. [Google Scholar] [CrossRef]
- Yueping, H.; Qi, L.; Yanqing, Y.; Meng, S. Graph Based Encrypted Malicious Traffic Detection with Hybrid Analysis of Multi-View Features. Inf. Sci. 2023, 644, 119229. [Google Scholar] [CrossRef]
- Tao, J.; Lin, J.; Zhang, S. MVAN: Multi-View Attention Networks for Real Money Trading Detection in Online Games. In Proceedings of the 25th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Anchorage, AK, USA, 4–8 August 2019; pp. 2536–2546. [Google Scholar] [CrossRef]
- Zhang, Y.; Yang, C.; Huang, K.; Li, Y. Intrusion Detection of Industrial Internet-of-Things Based on Reconstructed Graph Neural Networks. IEEE Trans. Netw. Sci. Eng. 2023, 10, 2894–2905. [Google Scholar] [CrossRef]
- Deng, X.; Zhu, J.; Pei, X.; Zhang, L.; Ling, Z.; Xue, K. Flow Topology-Based Graph Convolutional Network for Intrusion Detection in Label-Limited IoT Networks. IEEE Trans. Netw. Serv. Manag. 2023, 20, 684–696. [Google Scholar] [CrossRef]
- Zhang, S.; Yin, J.; Li, Z.; Yang, R.; Du, M.; Li, R. Node-Imbalance Learning on Heterogeneous Graph for Pirated Video Website Detection. In Proceedings of the 2022 IEEE 25th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Hangzhou, China, 4–6 May 2022; pp. 834–840. [Google Scholar] [CrossRef]
- Liu, J.; Zheng, J.; Wu, J.; Zheng, Z. FA-GNN: Filter and Augment Graph Neural Networks for Account Classification in Ethereum. IEEE Trans. Netw. Sci. Eng. 2022, 9, 2579–2588. [Google Scholar] [CrossRef]
- Lin, D.; Wu, J.; Huang, T.; Lin, K.; Zheng, Z. Who is Who on Ethereum? Account Labeling Using Heterophilic Graph Convolutional Network. IEEE Trans. Syst. Man Cybern. Syst. 2024, 54, 1541–1553. [Google Scholar] [CrossRef]
- Xie, F.; Cao, Z.; Xu, Y.; Chen, L.; Zheng, Z. Graph Neural Network and Multi-View Learning Based Mobile Application Recommendation in Heterogeneous Graphs. In Proceedings of the 2020 IEEE International Conference on Services Computing (SCC), Virtual, Beijing, China, 18–24 October 2020; pp. 100–107. [Google Scholar] [CrossRef]
- Dou, Y.; Liu, Z.; Sun, L.; Deng, Y.; Peng, H.; Yu, P.S. Enhancing Graph Neural Network-Based Fraud Detectors Against Camouflaged Fraudsters. In Proceedings of the 29th ACM International Conference on Information & Knowledge Management (CIKM), Virtual Event, Ireland, 19–23 October 2020; pp. 315–324. [Google Scholar] [CrossRef]
- Hei, Y.; Yang, R.; Peng, H.; Wang, L.; Liu, X.; Kang, Y. Hawk: Rapid Android Malware Detection Through Heterogeneous Graph Attention Networks. IEEE Trans. Neural Netw. Learn. Syst. 2024, 35, 4703–4717. [Google Scholar] [CrossRef] [PubMed]
- Li, A.; Qin, Z.; Liu, R.; Yang, Y.; Li, D. Spam Review Detection with Graph Convolutional Networks. In Proceedings of the 28th ACM International Conference on Information and Knowledge Management (CIKM), Beijing, China, 3–7 November 2019; pp. 2703–2711. [Google Scholar] [CrossRef]
- Zheng, L.; Li, Z.; Li, J.; Li, Z.; Gao, J. AddGraph: Anomaly Detection in Dynamic Graph Using Attention-Based Temporal GCN. In Proceedings of the 28th International Joint Conference on Artificial Intelligence (IJCAI), Macao, China, 10–16 August 2019; pp. 4419–4425. [Google Scholar] [CrossRef]
- Xu, P.; Lu, G.; Li, Y.; Xu, C. EE-GCN: A Graph Convolutional Network Based Intrusion Detection Method for IIoT. In Proceedings of the 2023 5th International Conference on Natural Language Processing (ICNLP), Guangzhou, China, 24–26 March 2023; pp. 338–344. [Google Scholar] [CrossRef]
- Xu, R.; Wu, G.; Wang, W.; Gao, X.; He, A.; Zhang, Z. Applying Self-Supervised Learning to Network Intrusion Detection for Network Flows with Graph Neural Network. Comput. Netw. 2024, 248, 110495. [Google Scholar] [CrossRef]
- Fu, C.; Li, Q.; Xu, K. Detecting Unknown Encrypted Malicious Traffic in Real Time via Flow Interaction Graph Analysis. In Proceedings of the 30th Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 27 February–3 March 2023. [Google Scholar] [CrossRef]
- Baahmed, A.R.E.; Andresini, G.; Robardet, C.; Appice, A. Using Graph Neural Networks for the Detection and Explanation of Network Intrusions. In Proceedings of the European Conference on Machine Learning (ECML 2023), Torino, Italy, 18–22 September 2023; pp. 201–216. [Google Scholar] [CrossRef]
- Duan, G.; Lv, H.; Wang, H.; Feng, G.; Li, X. Practical Cyber Attack Detection with Continuous Temporal Graph in Dynamic Network System. IEEE Trans. Inf. Forensics Secur. 2024, 19, 4851–4864. [Google Scholar] [CrossRef]
- Yang, Z.; Pei, W.; Chen, M.; Yue, C. WTAGRAPH: Web Tracking and Advertising Detection Using Graph Neural Networks. In Proceedings of the 43rd IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 23–26 May 2022; pp. 1540–1557. [Google Scholar] [CrossRef]
- Caville, E.; Lo, W.W.; Layeghy, S.; Portmann, M. Anomal-E: A Self-Supervised Network Intrusion Detection System Based on Graph Neural Networks. Knowl.-Based Syst. 2022, 258, 110030. [Google Scholar] [CrossRef]
- Song, J.; Qu, X.; Hu, Z.; Li, Z.; Gao, J.; Zhang, J. A Subgraph-Based Knowledge Reasoning Method for Collective Fraud Detection in E-Commerce. Neurocomputing 2021, 461, 587–597. [Google Scholar] [CrossRef]
- Nguyen, H.C.; Kashef, R. TS-IDS: Traffic-Aware Self-Supervised Learning for IoT Network Intrusion Detection. Knowl.-Based Syst. 2023, 279, 110966. [Google Scholar] [CrossRef]
- Altaf, T.; Wang, X.; Ni, W.; Yu, G.; Liu, R.P.; Braun, R. A New Concatenated Multigraph Neural Network for IoT Intrusion Detection. Internet Things 2023, 22, 100818. [Google Scholar] [CrossRef]
- Duan, G.; Lv, H.; Wang, H.; Feng, G. Application of a Dynamic Line Graph Neural Network for Intrusion Detection with Semisupervised Learning. IEEE Trans. Inform. Forensics Secur. 2023, 18, 699–714. [Google Scholar] [CrossRef]
- Gu, Z.; Lopez, D.T.; Alrahis, L.; Sinanoglu, O. Always be Pre-Training: Representation Learning for Network Intrusion Detection with GNNs. arXiv 2024, arXiv:2402.18986. [Google Scholar] [CrossRef]
- Chang, X.; Ren, P.; Xu, P.; Li, Z.; Chen, X.; Hauptmann, A. A Comprehensive Survey of Scene Graphs: Generation and Application. IEEE Trans. Pattern Anal. Mach. Intell. 2023, 45, 1–26. [Google Scholar] [CrossRef] [PubMed]
- Wu, S.; Sun, F.; Zhang, W.; Xie, X.; Cui, B. Graph Neural Networks in Recommender Systems: A Survey. ACM Comput. Surv. 2022, 55, 97. [Google Scholar] [CrossRef]
- Shen, M.; Zhang, J.; Zhu, L.; Xu, K.; Du, X. Accurate Decentralized Application Identification via Encrypted Traffic Analysis Using Graph Neural Networks. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2367–2380. [Google Scholar] [CrossRef]
- Chen, Z.; Cheng, G.; Niu, D.; Qiu, X.; Zhao, Y.; Zhou, Y. WFF-EGNN: Encrypted Traffic Classification Based on Weaved Flow Fragment via Ensemble Graph Neural Networks. IEEE Trans. Mach. Learn. Commun. Netw. 2023, 1, 389–411. [Google Scholar] [CrossRef]
- Han, Y.; Wang, X.; He, M.; Wang, X.; Guo, S. Intrusion Detection for Encrypted Flows Using Single Feature Based on Graph Integration Theory. IEEE Internet Things J. 2024, 11, 17589–17601. [Google Scholar] [CrossRef]
- Gao, B.; Liu, W.; Liu, G.; Nie, F. Resource Knowledge-Driven Heterogeneous Graph Learning for Website Fingerprinting. IEEE Trans. Cogn. Commun. Netw. 2024, 10, 968–981. [Google Scholar] [CrossRef]
- Xu, H.; Li, S.; Cheng, Z.; Qin, R.; Xie, J.; Sun, P. TrafficGCN: Mobile Application Encrypted Traffic Classification Based on GCN. In Proceedings of the 2022 IEEE Global Communications Conference (GLOBECOM), Rio de Janeiro, Brazil, 4–8 December 2022; pp. 891–896. [Google Scholar] [CrossRef]
- Feng, P.; Wei, D.; Li, Q.; Wang, Q.; Hu, Y.; Xi, N.; Ma, J. GlareShell: Graph Learning-Based PHP Webshell Detection for Web Server of Industrial Internet. Comput. Netw. 2024, 245, 110406. [Google Scholar] [CrossRef]
- Kisanga, P.; Woungang, I.; Traoré, I.; Carvalho, G.H.S. Network Anomaly Detection Using a Graph Neural Network. In Proceedings of the 2023 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 20–23 February 2023; pp. 61–65. [Google Scholar] [CrossRef]
- Li, H.; Chasaki, D. Heterogeneous GNN with Express Edges for Intrusion Detection in Cyber-Physical Systems. In Proceedings of the 2024 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 19–22 February 2024; pp. 523–529. [Google Scholar] [CrossRef]
- Cui, T.; Gou, G.; Xiong, G.; Li, Z.; Cui, M.; Liu, C. SiamHAN: IPv6 Address Correlation Attacks on TLS Encrypted Traffic via Siamese Heterogeneous Graph Attention Network. In Proceedings of the 30th USENIX Security Symposium, Virtual Event, 11–13 August 2021; pp. 4329–4346. [Google Scholar] [CrossRef]
- Zhang, H.; Yu, L.; Xiao, X.; Li, Q.; Mercaldo, F.; Luo, X.; Liu, Q. TFE-GNN: A Temporal Fusion Encoder Using Graph Neural Networks for Fine-Grained Encrypted Traffic Classification. In Proceedings of the ACM Web Conference 2023 (WWW ‘23), Austin, TX, USA, 30 April–4 May 2023; pp. 2066–2075. [Google Scholar] [CrossRef]
- Hu, G.; Xiao, X.; Shen, M.; Zhang, B.; Yan, X.; Liu, Y. TCGNN: Packet-Grained Network Traffic Classification via Graph Neural Networks. Eng. Appl. Artif. Intell. 2023, 123, 106531. [Google Scholar] [CrossRef]
- Okonkwo, Z.; Foo, E.; Hou, Z.; Li, Q.; Jadidi, Z. Encrypted Network Traffic Classification with Higher Order Graph Neural Network. In Proceedings of the 28th Australasian Conference on Information Security and Privacy (ACISP 2023), Melbourne, VIC, Australia, 5–7 July 2023; pp. 630–650. [Google Scholar] [CrossRef]
- Huoh, T.-L.; Luo, Y.; Li, P.; Zhang, T. Flow-Based Encrypted Network Traffic Classification with Graph Neural Networks. IEEE Trans. Netw. Serv. Manag. 2023, 20, 1224–1237. [Google Scholar] [CrossRef]
- Yang, J.; Jiang, X.; Lei, Y.; Liang, W.; Ma, Z.; Li, S. MTSecurity: Privacy-Preserving Malicious Traffic Classification Using Graph Neural Network and Transformer. IEEE Trans. Netw. Serv. Manag. 2024, 21, 3583–3597. [Google Scholar] [CrossRef]
- Fu, C.; Li, Q.; Xu, K. Flow Interaction Graph Analysis: Unknown Encrypted Malicious Traffic Detection. IEEE/ACM Trans. Netw. 2024, 32, 2972–2987. [Google Scholar] [CrossRef]
- Zhao, R.; Deng, X.; Wang, Y.; Chen, L.; Liu, M.; Xue, Z.; Wang, Y. Flow Sequence-Based Anonymity Network Traffic Identification with Residual Graph Convolutional Networks. In Proceedings of the 2022 IEEE/ACM 30th International Symposium on Quality of Service (IWQoS 2022), Oslo, Norway, 10–12 June 2022; pp. 1–10. [Google Scholar] [CrossRef]
- Wang, C.; Zhu, H. Wrongdoing Monitor: A Graph-Based Behavioral Anomaly Detection in Cyber Security. IEEE Trans. Inf. Forensics Secur. 2022, 17, 2703–2718. [Google Scholar] [CrossRef]
- Zhang, H.; Zeng, K.; Lin, S. Federated Graph Neural Network for Fast Anomaly Detection in Controller Area Networks. IEEE Trans. Inf. Forensics Secur. 2023, 18, 1566–1579. [Google Scholar] [CrossRef]
- Zhu, Y.; Tao, J.; Wang, H.; Yu, L.; Luo, Y.; Qi, T.; Wang, Z.; Xu, Y. DGNN: Accurate Darknet Application Classification Adopting Attention Graph Neural Network. IEEE Trans. Netw. Serv. Manag. 2024, 21, 1258–1273. [Google Scholar] [CrossRef]
- Pham, T.-D.; Ho, T.-L.; Truong-Huu, T.; Cao, T.-D.; Truong, H.-L. MAppGraph: Mobile-App Classification on Encrypted Network Traffic Using Deep Graph Convolution Neural Networks. In Proceedings of the 37th Annual Computer Security Applications Conference (ACSAC 2021), Virtual Event, 6–10 December 2021; pp. 1025–1038. [Google Scholar] [CrossRef]
- Pei, X.; Yu, L.; Tian, S. AMalNet: A Deep Learning Framework Based on Graph Convolutional Networks for Malware Detection. Comput. Secur. 2020, 93, 101792. [Google Scholar] [CrossRef]
- Guo, T.; Cui, B. Web Page Classification Based on Graph Neural Network. In Innovative Mobile and Internet Services in Ubiquitous Computing; Barolli, L., Yim, K., Chen, H.-C., Eds.; Lecture Notes in Networks and Systems; Springer: Cham, Switzerland, 2022; Volume 279, pp. 188–198. [Google Scholar] [CrossRef]
- Wu, Z.; Pan, S.; Chen, F.; Long, G.; Zhang, C.; Yu, P.S. A Comprehensive Survey on Graph Neural Networks. IEEE Trans. Neural Netw. Learn. Syst. 2021, 32, 4–24. [Google Scholar] [CrossRef]
- Fan, W.; Ma, Y.; Li, Q.; He, Y.; Zhao, E.; Tang, J.; Yin, D. Graph Neural Networks for Social Recommendation. In Proceedings of the 2019 World Wide Web Conference (WWW ‘19), San Francisco, CA, USA, 13–17 May 2019; pp. 417–426. [Google Scholar] [CrossRef]
- Li, Y.; Chen, X.; Tang, W.; Zhu, Y.; Han, Z.; Yue, Y. Interaction Matters: Encrypted Traffic Classification via Status-Based Interactive Behavior Graph. Appl. Soft Comput. 2024, 155, 111423. [Google Scholar] [CrossRef]
- Busch, J.; Kocheturov, A.; Tresp, V.; Seidl, T. NF-GNN: Network Flow Graph Neural Networks for Malware Detection and Classification. In Proceedings of the 33rd International Conference on Scientific and Statistical Database Management (SSDBM 2021), Tampa, FL, USA, 6–7 July 2021; pp. 121–132. [Google Scholar] [CrossRef]
- Yu, L.; Tao, J.; Xu, Y.; Sun, W.; Wang, Z. TLS Fingerprint for Encrypted Malicious Traffic Detection with Attributed Graph Kernel. Comput. Netw. 2024, 247, 110475. [Google Scholar] [CrossRef]
- Qin, Z.-Q.; Xu, H.-Z.; Ma, X.-K.; Wang, Y.-J. Interaction Context-Aware Network Behavior Anomaly Detection for Discovering Unknown Attacks. Secur. Commun. Netw. 2022, 2022, 3595304. [Google Scholar] [CrossRef]
- Wang, L.; Ma, X.; Li, N.; Lv, Q.; Wang, Y.; Huang, W.; Chen, H. TGPrint: Attack Fingerprint Classification on Encrypted Network Traffic Based Graph Convolution Attention Networks. Comput. Secur. 2023, 135, 103466. [Google Scholar] [CrossRef]
- Garcia, S.; Grill, M.; Stiborek, J.; Zunino, A. An Empirical Comparison of Botnet Detection Methods. Comput. Secur. 2014, 45, 100–123. [Google Scholar] [CrossRef]
- Song, H.M.; Kim, H.K. CAN Signal Extraction and Translation Dataset; HCRL: Seoul, Republic of Korea, 2020; Available online: https://ocslab.hksecurity.net/Datasets/can-signal-extraction-and-translation-dataset (accessed on 27 June 2025).
- Arp, D.; Spreitzenbarth, M.; Hübner, M.; Gascon, H.; Rieck, K.; Siemens, C.E.R.T. DREBIN: Effective and Explainable Detection of Android Malware in Your Pocket. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 23–26 February 2014. [Google Scholar] [CrossRef]
- Lashkari, A.H.; Kadir, A.F.A.; Taheri, L.; Ghorbani, A.A. Toward Developing a Systematic Approach to Generate Benchmark Android Malware Datasets and Classification. In Proceedings of the 2018 International Carnahan Conference on Security Technology (ICCST), Montreal, QC, Canada, 22–25 October 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Praguard. Public Malware Traffic Dataset. Available online: https://github.com/Praguard (accessed on 27 June 2025).
- Li, E.; Wang, L.; Song, B. Fault Diagnosis of Power Transformers With Membership Degree. IEEE Access 2019, 7, 28791–28798. [Google Scholar] [CrossRef]
- Alsaedi, A.; Moustafa, N.; Tari, Z.; Mahmood, A.; Anwar, A. TON_IoT Telemetry Dataset: A New Generation Dataset of IoT and IIoT for Data-Driven Intrusion Detection Systems. IEEE Access 2020, 8, 165130–165150. [Google Scholar] [CrossRef]
- Moustafa, N.; Slay, J. UNSW-NB15: A Comprehensive Data Set for Network Intrusion Detection Systems (UNSW-NB15 Network Data Set). In Proceedings of the 2015 Military Communications and Information Systems Conference (MilCIS), Canberra, ACT, Australia, 10–12 November 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Sarhan, M.; Layeghy, S.; Portmann, M. Evaluating standard feature sets towards increased generalisability and explainability of MLbased network intrusion detection. Big Data Res. 2020, 30, 100359. [Google Scholar] [CrossRef]
- Lashkari, A.H.; Kaur, G.; Rahali, A. DIDarknet: A Contemporary Approach to Detect and Characterize the Darknet Traffic Using Deep Image Learning. In Proceedings of the 10th International Conference on Communication and Network Security (ICCNS), Tokyo, Japan, 27–29 November 2020; pp. 1–13. [Google Scholar] [CrossRef]
- Lashkari, A.H.; Draper-Gil, G.; Mamun, M.S.I.; Ghorbani, A.A. Characterization of Tor Traffic Using Time Based Features. In Proceedings of the 3rd International Conference on Information Systems Security and Privacy (ICISSP), Porto, Portugal, 19–21 February 2017; pp. 253–262. [Google Scholar] [CrossRef]
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward the Development of a New Intrusion Detection System for the Internet of Things. In Proceedings of the 2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Song, J.; Takakura, H.; Okabe, Y.; Eto, M.; Inoue, D.; Nakao, K. Statistical Analysis of Honeypot Data and Building of Kyoto 2006+ Dataset for NIDS Evaluation. In Proceedings of the First Workshop on Building Analysis Datasets and Gathering Experience Returns for Security (BADGERS ‘11), Chicago, IL, USA, 21 October 2011; pp. 29–36. [Google Scholar] [CrossRef]
- Allix, K.; Bissyandé, T.F.; Klein, J.; Le Traon, Y. AndroZoo: Collecting Millions of Android Apps for the Research Community. In Proceedings of the 13th International Conference on Mining Software Repositories (MSR), Austin, TX, USA, 14–15 May 2016; pp. 468–471. [Google Scholar] [CrossRef]
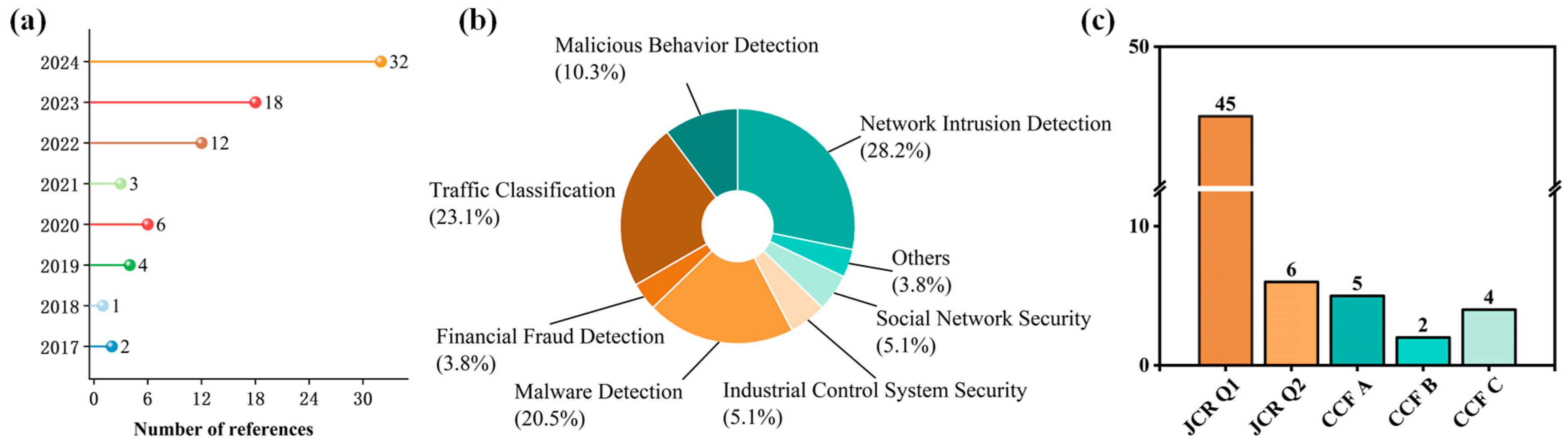
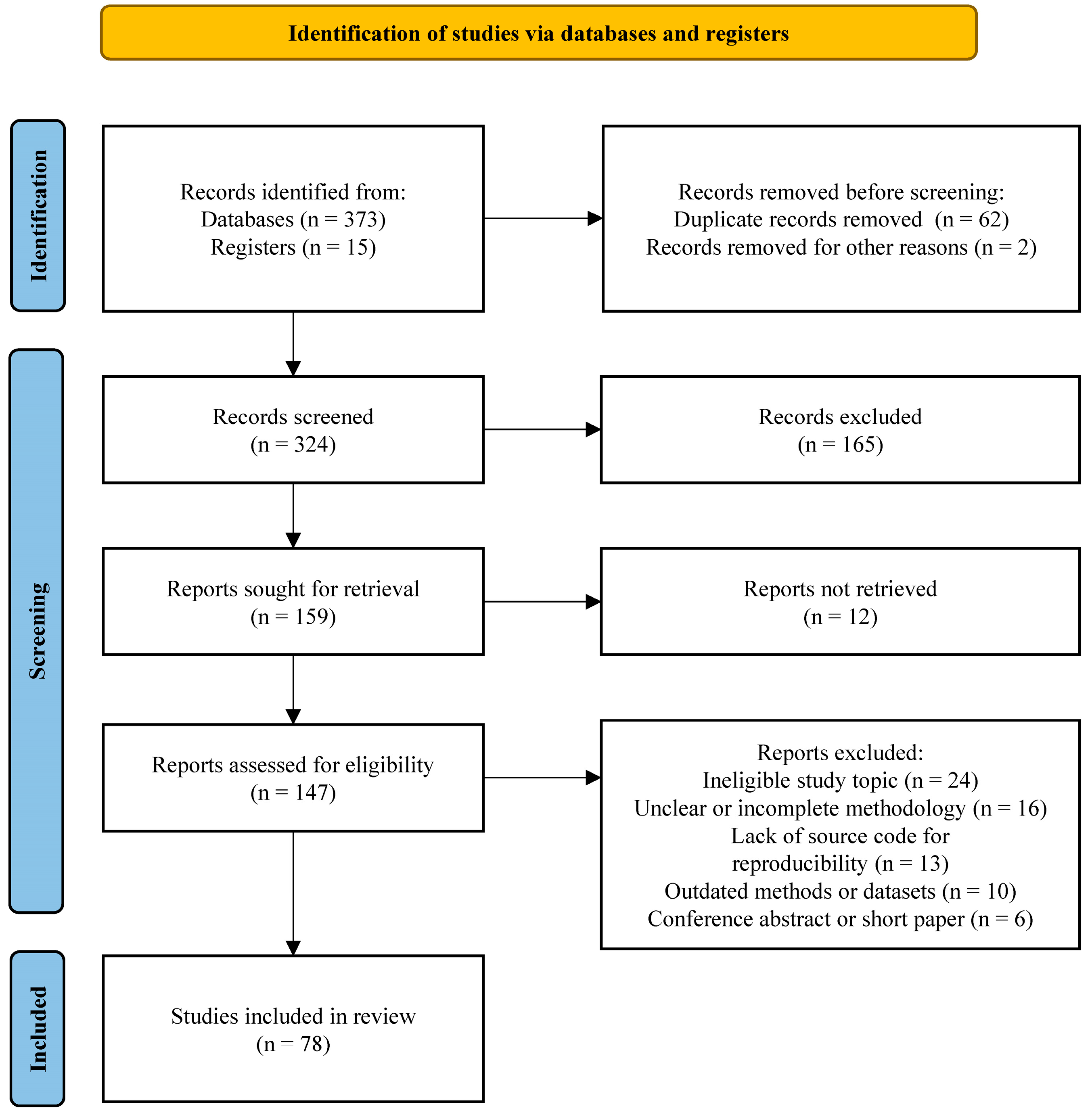
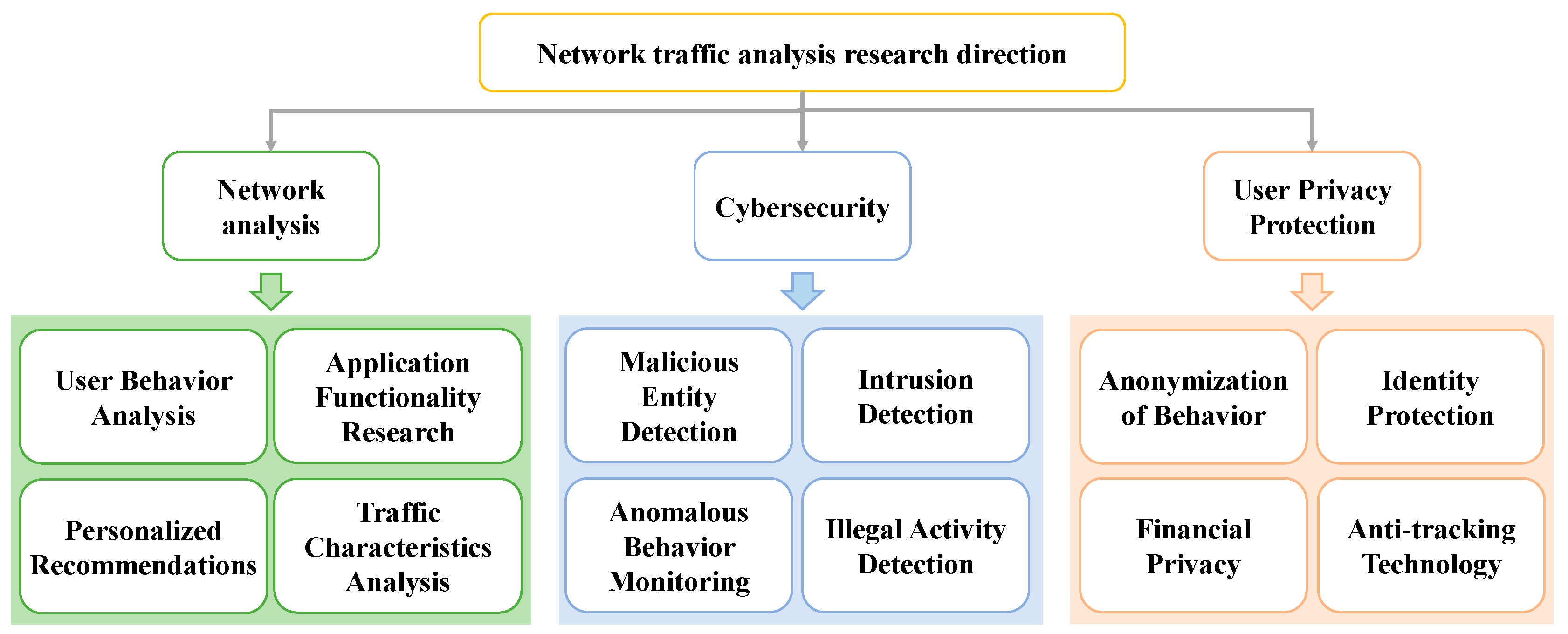
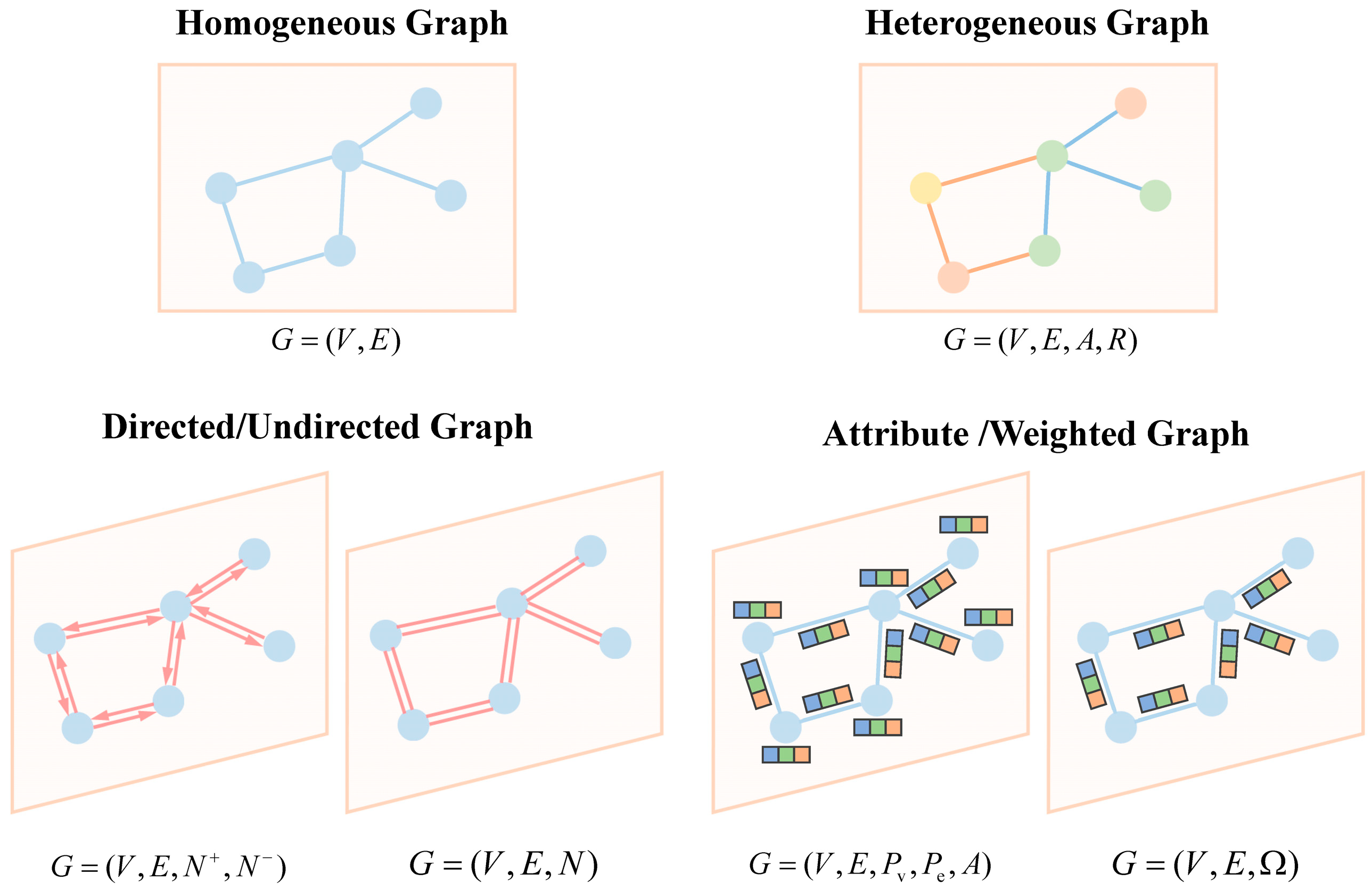
| Surveys | Year | Task | Survey Content | |
|---|---|---|---|---|
| Traffic Analysis | Goli et al. [18] | 2018 | Real-time traffic analysis | Machine learning |
| Bhatla et al. [19] | 2023 | Network traffic analysis | Machine learning | |
| Azab et al. [20] | 2022 | Encrypted traffic analysis | Machine learning | |
| Getman et al. [21] | 2022 | Encrypted traffic analysis | Deep learning | |
| Papadogiannaki et al. [22] | 2021 | Encrypted traffic analysis | Machine learning | |
| Meng et al. [23] | 2023 | Encrypted traffic analysis | Machine, Deep and Graph learning | |
| GNN-based Traffic Analysis | Bilot et al. [24] | 2024 | Intrusion detection | GNN |
| Zhong et al. [25] | 2024 | Intrusion detection | GNN | |
| Dong et al. [26] | 2024 | IoT security | GNN | |
| Pazho et al. [27] | 2023 | Anomaly detection | GNN | |
| Yan et al. [28] | 2024 | Network infrastructure security | GNN | |
| Madhoun et al. [29] | 2023 | Malware detection | GNN | |
| Our Survey | 2025 | Traffic analysis | GNN | |
| Architecture | Key Features | Aggregation Methods | Attention Mechanism | Use Cases |
|---|---|---|---|---|
| GNN | Message passing, iterative updates | Neighborhood aggregation | No | General tasks, node classification |
| GCN | Spectral convolution, localized | Neighborhood averaging | No | Node/graph classification, link prediction |
| GraphSAGE | Inductive learning, scalable | Sampling-based aggregation | No | Large-scale analysis, inductive learning |
| Edge-GraphSAGE | Edge-level prediction, combines node and edge features | Node and edge feature aggregation | No | Edge prediction, relationship analysis |
| GAT | Attention-based weighting | Attention-weighted aggregation | Yes (edge-level) | Node/graph classification |
| GIN | Graph isomorphism-inspired, learnable epsilon | Sum aggregation with epsilon weighting | No | Graph/node classification |
| HAN | Meta-path-based heterogeneous processing | Meta-path guided aggregation | Yes (node and semantic level) | Heterogeneous graph analysis |
| Paper | Model | Year | Task | Graph Type | Modules | Learning |
|---|---|---|---|---|---|---|
| [55] | - | 2017 | Botnet detection | Homogeneous graph | SOM | Unsupervised |
| [63] | GVARec | 2020 | Mobile application recommendation | Heterogeneous graph | GCN, GAT | Supervised |
| [47] | - | 2022 | IoT network intrusion detection | Homogeneous graph | GCN, GIN | Supervised |
| [59] | FT-GCN | 2023 | Intrusion detection | Homogeneous graph | TAGCN | Supervised |
| [49] | CyResGrid | 2023 | Anomaly detection | Homogeneous graph | GCN, LSTM | Supervised |
| [56] | MalDiscovery | 2023 | Encrypted malicious traffic detection | Homogeneous graph | GraphSAGE | Supervised |
| [45] | FTG-Net-E | 2024 | DDoS attack detection | Homogeneous graph | GCN | Supervised |
| [62] | KYC-GCN | 2024 | Account labeling | Heterogeneous graph | GCN | Supervised |
| [52] | - | 2024 | Illegal mobile gambling apps | Heterogeneous graph | HAN | Supervised |
| [46] | GHGDroid | 2024 | Android malware detection | Homogeneous graph | GCN | Supervised |
| [65] | MSGAT++ | 2024 | Rapid android malware detection | Heterogeneous graph | HIN, GAT | Supervised |
| Paper | Model | Year | Task | Graph Type | Modules | Learning | |
|---|---|---|---|---|---|---|---|
| [75] | R-GIN | 2021 | Fraud detection | Undirected | Dynamic | GIN | Supervised |
| [73] | WTAGRAPH | 2022 | Web tracking detection | Directed | Static | GNN | Supervised |
| [74] | Anomal-E | 2022 | Intrusion detection | Directed | Dynamic | Edge-GraphSAGE | Self-supervised |
| [76] | TS-IDS | 2023 | IoT intrusion detection | Directed | Dynamic | GAT | Self-supervised |
| [68] | EE-GCN | 2023 | IoT intrusion detection | Directed | Static | GCN | Supervised |
| [70] | HyperVision | 2023 | Malicious traffic detecting | Directed | Dynamic | GNN | Unsupervised |
| [71] | - | 2023 | Intrusion detection | Directed | Static | Edge-GraphSAGE | Supervised |
| [78] | - | 2023 | Intrusion detection | Undirected | Dynamic | GNN | Semi-supervised |
| [77] | - | 2023 | IoT intrusion detection | Directed | Static | GCN, GAT | Supervised |
| [69] | - | 2024 | Intrusion detection | Undirected | Static | GAT | Self-supervised |
| [79] | - | 2024 | Intrusion detection | Directed | Static | Edge-GraphSAGE | Self-supervised |
| [72] | CTGNN | 2024 | Intrusion detection | Undirected | Dynamic | GNN | Supervised |
| Paper | Model | Year | Task | Graph Type | Modules | Learning | |
|---|---|---|---|---|---|---|---|
| [90] | SIAMHAN | 2020 | IPv6 address correlation attacks | Undirected | Static | HAN | Supervised |
| [107] | NF-GNN | 2021 | Malware detection | Directed | Dynamic | GNN | Supervised |
| [109] | XNBAD | 2022 | Anomaly detection | Undirected | Dynamic | GraphSAGE | Supervised |
| [98] | - | 2022 | Anomaly detection | Undirected | Static | GAT | Supervised |
| [86] | TrafficGCN | 2022 | Encrypted traffic classification | Undirected | Static | GCN | Supervised |
| [88] | - | 2023 | Anomaly detection | Directed | Static | GCN | Supervised |
| [83] | WFF-EGNN | 2023 | Encrypted traffic classification | Directed | Static | GCN | Supervised |
| [91] | TFE-GNN | 2023 | Encrypted traffic classification | Undirected | Static | GraphSAGE | Supervised |
| [92] | TCGNN | 2023 | Network traffic classification | Undirected | Static | GCN | Supervised |
| [93] | - | 2023 | Network traffic classification | Directed | Static | GraphConv | Supervised |
| [106] | IBGC | 2024 | Encrypted traffic classification | Directed | Dynamic | GraphSAGE | Supervised |
| [85] | RKHSTGCN | 2024 | Website fingerprinting | Undirected | Dynamic | HAN | Supervised |
| [84] | - | 2024 | Intrusion detection | Undirected | Dynamic | GCN, GIN, GAT | Supervised |
| Method | Graph Type | Model | Accuracy | F1-Score | Key Advantages |
|---|---|---|---|---|---|
| Chowdhury et al. [55] | Directed Graph | Basic GNN | 99% | - | Efficient search (0.1% nodes) |
| Hong et al. [56] | Attributed Graph | GraphSAGE | 99.9% | - | Multi-view feature fusion |
| Zhang et al. [53] | Heterogeneous Graph | HGCN | 99.27% | 93.26% | High-order semantic modeling |
| Method | Prediction Level | Model | Accuracy | F1-Score | Training Paradigm |
|---|---|---|---|---|---|
| Deng et al. [59] | Edge | Edge-GraphSAGE | 98.18% | 88.45% | Self-supervised |
| Caville et al. [74] | Node | TAGCN | 98.7% | - | Supervised |
| Han et al. [84] | Graph | GIN | 98.42% | - | Supervised |
| Method | Graph Type | Model | Accuracy | F1-Score | Specialization |
|---|---|---|---|---|---|
| Duan et al. [78] | Attributed Graph | CTGNN | 99.98% | 99.96% | New behavior detection |
| Gu et al. [79] | Line Graph | DLGNN | 99.8% | 99.85% | Label-efficient |
| Li et al. [89] | Heterogeneous Graph | RGCN | - | 97.78% | Multi-graph fusion |
| Dataset | Category | Task | Link | Reference | Related Work |
|---|---|---|---|---|---|
| MCFP | Public | Malicious Traffic Detection | https://mcfp.felk.cvut.cz/publicDatasets, accessed on 22 October 2025. | - | [56] |
| JusticePC | Self-made | Malicious Account Detection | https://github.com/fuxiAIlab/JusticePC, accessed on 22 October 2025. | [48] | [48] |
| Pirated Video Websites Dataset | Self-made | Pirated Video Website Detection | https://github.com/lirenjieArthur/pirated-video-websites, accessed on 22 October 2025. | [51] | [51] |
| MAWI | Public | Detecting Encrypted Malicious Traffic | http://mawi.wide.ad.jp/mawi, accessed on 22 October 2025. | [62] | [62] |
| Malicious Traffic Encryption Dataset | Self-made | Malicious Traffic Encryption Detection | https://github.com/fuchuanpu/HyperVision, accessed on 22 October 2025. | [63] | [63] |
| Yelp | Public | E-commerce Fraud Detection | http://odds.cs.stonybrook.edu/yelpchi-dataset, accessed on 20 June 2025. | [66] | [66,75] |
| Amazon | Public | E-commerce Fraud Detection | http://jmcauley.ucsd.edu/data/amazon, accessed on 22 October 2025. | [66] | [66] |
| CERNET-2022-Service | Self-made | Encrypted Traffic Classification | https://data.iptas.edu.cn/web/tbps, accessed on 22 October 2025. | [77] | [77] |
| Mobile Application Traffic Dataset | Self-made | Encrypted network traffic | https://soeai.github.io/MAppGraph, accessed on 20 June 2025. | [88] | [88] |
| CTU-13 | Public | Bot Detection | https://www.stratosphereips.org/datasets-ctu13, accessed on 22 October 2025. | [111] | [53,55,56] |
| CAN Signal Extraction and Translation | Public | CAN Intrusion Detection | https://ocslab.hksecurity.net/Datasets/can-signal-extraction-and-translation-dataset, accessed on 22 October 2025. | [112] | [77] |
| DREBIN | Public | Android Malware | https://www.sec.cs.tu-bs.de/people/arp/drebin, accessed on 22 October 2025. | [113] | [46] |
| CICAndMal2017 | Public | Malware Detection | https://www.cic.gc.ca, accessed on 22 October 2025. | [114] | [65] |
| Praguard | Public | Malware Traffic | https://github.com/Praguard, accessed on 20 June 2025. | [115] | [107] |
| SGCC | Public | Anomaly Detection in Industrial IoT | https://github.com/henryRDlab/ElectricityTheftDetection, accessed on 22 October 2025. | [116] | [58] |
| BoT-IoT | Public | Intrusion Detection | https://ieee-dataport.org/documents/bot-iot-dataset, accessed on 22 October 2025. | [117] | [68,76,78] |
| ToN-IoT | Public | Intrusion Detection | https://research.unsw.edu.au/projects/toniot-dataset, accessed on 22 October 2025. | [117] | [68,72,78,79,89] |
| CSE-CIC-IDS2018 | Public | Intrusion Detection | https://www.unb.ca/cic/datasets/ids-2018.html, accessed on 22 October 2025. | [117] | [66,76,110] |
| UNSW-NB15 | Public | Intrusion Detection | https://www.unsw.edu.au/engineering/our-story/our-research/cyber-security-research/unsw-nb15-dataset, accessed on 20 June 2025. | [118] | [59,74,84] |
| BoT-IoT-V2 | Public | Intrusion Detection | https://github.com/UNSW-NB15/NF-BoT-IoT-v2, accessed on 22 October 2025. | [119] | [78] |
| ToN-IoT-V2 | Public | Intrusion Detection | https://github.com/UNSW-NB15/NF-ToN-IoT-v2, accessed on 22 October 2025. | [119] | [78] |
| CSE-CIC-IDS2018-V2 | Public | Intrusion Detection | https://github.com/UNSW-NB15/NF-CSE-CIC-IDS2018-v2, accessed on 22 October 2025. | [119] | [74,78] |
| CIC-Darknet2020 | Public | Intrusion Detection | https://www.unb.ca/cic/datasets/malmem-2020.html, accessed on 20 June 2025. | [120] | [59,100] |
| ISCX-Tor2016 | Public | Network Traffic Classification | https://www.unb.ca/research/iscx/datasets/tor-dataset.html, accessed on 22 October 2025. | [121] | [59,97] |
| ISCX-Vpn2016 | Public | Network Traffic Classification | https://www.unb.ca/cic/datasets/vpn-2016.html, accessed on 20 June 2025. | [121] | [83] |
| UNB-ISCX | Public | Intrusion Detection | https://www.unb.ca/cic/datasets/malmem-2020.html, accessed on 20 June 2025. | [122] | [92,94] |
| Kyoto | Public | Network Traffic Classification | http://www.takakura.com/Kyoto_data, accessed on 22 October 2025. | [123] | [98] |
| AndroZoo | Public | Encrypted Mobile App Traffic | https://androzoo.uni.lu, accessed on 22 October 2025. | [124] | [102] |
| Year | Model | Task | Framework | GitHub | Related Work |
|---|---|---|---|---|---|
| 2023 | MalDiscovery | Malicious Traffic Detection | - | http://github.com/NatsuHB/MalDiscovery, accessed on 22 October 2025. | [56] |
| 2019 | MVAN | Real Currency Transaction Detection | TensorFlow | https://github.com/fuxiAIlab/MVAN, accessed on 22 October 2025. | [57] |
| 2020 | CARE-GNN | Cybercrime Detection | Pytorch | https://github.com/safe-graph/DGFraud, accessed on 22 October 2025. | [64] |
| 2024 | HAWK | Android Malware Classification | TensorFlow | https://github.com/RingBDStack/HAWK, accessed on 22 October 2025. | [65] |
| 2023 | TS-IDS | IoT Network Intrusion Detection | Pytorch | https://github.com/hoangntc/TS-IDS, accessed on 22 October 2025. | [76] |
| 2023 | HyperVision | Encrypted Malicious Traffic Detection | - | https://github.com/fuchuanpu/HyperVision, accessed on 22 October 2025. | [77] |
| 2022 | E-GNNExplainer | Network Intrusion Detection | - | https://github.com/EagleEye1107/E-GNNExplainer, accessed on 22 October 2025. | [71] |
| 2024 | IBGC | Encrypted Network Traffic Classification | - | https://github.com/martinallee/ibgc, accessed on 22 October 2025. | [106] |
| 2022 | BIG | Anomaly Detection | - | https://github.com/SlothfulZhu/Wrongdoing-Monitor, accessed on 22 October 2025. | [98] |
| 2021 | MAppGraph | Encrypted Network Traffic Classification | - | https://soeai.github.io/MAppGraph, accessed on 22 October 2025. | [101] |
| 2024 | TLSFingerprint | Encrypted Malicious Traffic Detection | Pytorch | https://github.com/wesly2000/TLSFingerprint, accessed on 22 October 2025. | [108] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, R.; Zhao, J.; Zhang, H.; He, L.; Li, H.; Huang, M. Network Traffic Analysis Based on Graph Neural Networks: A Scoping Review. Big Data Cogn. Comput. 2025, 9, 270. https://doi.org/10.3390/bdcc9110270
Wang R, Zhao J, Zhang H, He L, Li H, Huang M. Network Traffic Analysis Based on Graph Neural Networks: A Scoping Review. Big Data and Cognitive Computing. 2025; 9(11):270. https://doi.org/10.3390/bdcc9110270
Chicago/Turabian StyleWang, Ruonan, Jinjing Zhao, Hongzheng Zhang, Liqiang He, Hu Li, and Minhuan Huang. 2025. "Network Traffic Analysis Based on Graph Neural Networks: A Scoping Review" Big Data and Cognitive Computing 9, no. 11: 270. https://doi.org/10.3390/bdcc9110270
APA StyleWang, R., Zhao, J., Zhang, H., He, L., Li, H., & Huang, M. (2025). Network Traffic Analysis Based on Graph Neural Networks: A Scoping Review. Big Data and Cognitive Computing, 9(11), 270. https://doi.org/10.3390/bdcc9110270






