Face Liveness Detection Using Artificial Intelligence Techniques: A Systematic Literature Review and Future Directions
Abstract
1. Introduction
1.1. Significance and Relevance
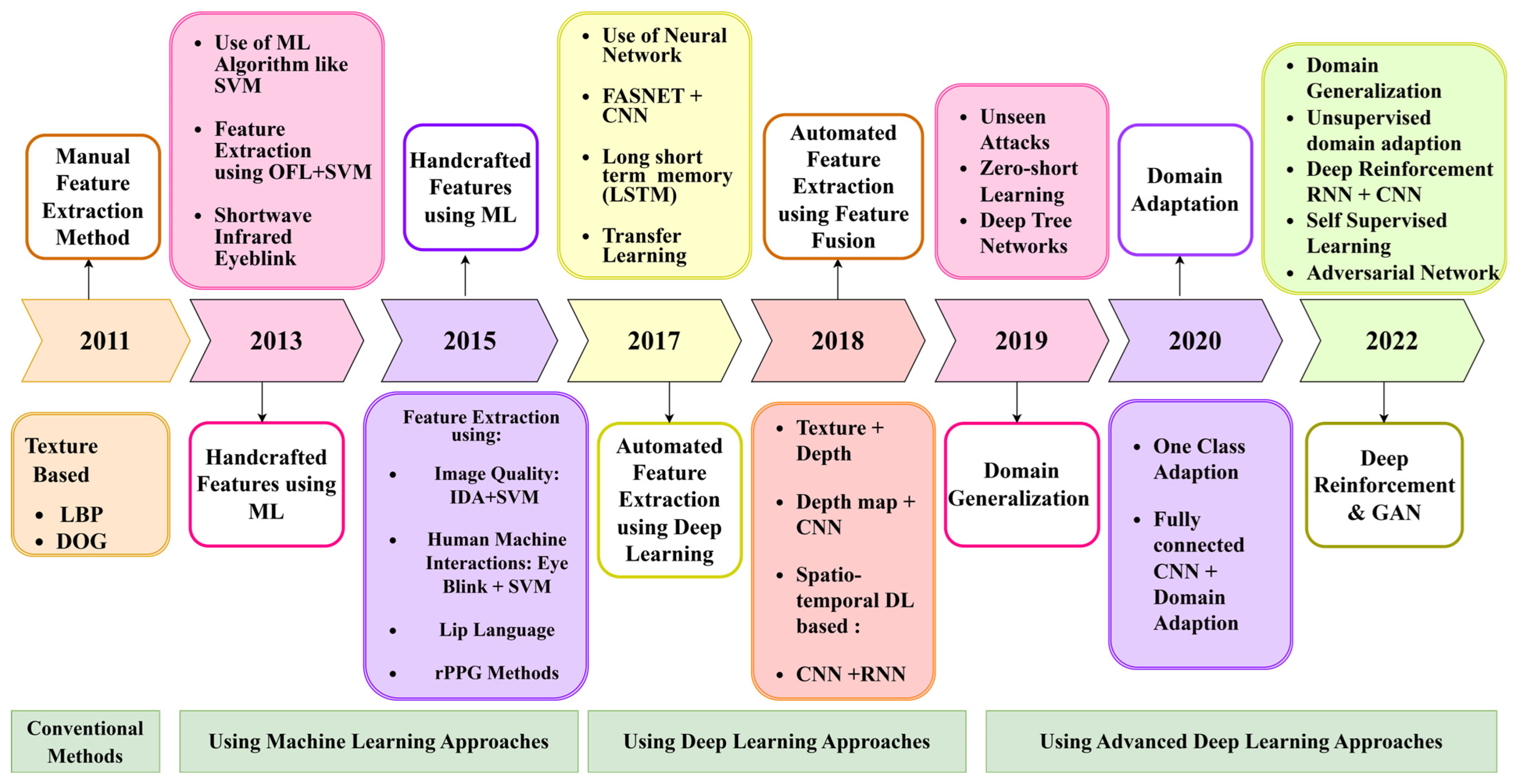
1.2. Evolution of Face Biometric Liveness Authentication
1.3. Prior Research
1.4. Motivation
1.5. Research Goals
1.6. Contributions of the Study
- An exhaustive survey of studies identified using the PRISMA Approach for face liveness detection using AI approaches, including Machine Learning and Deep Learning.
- A thorough examination of the quantity and consistency of standard datasets is carefully investigated.
- Feature extraction and Classification methods, Challenges, and issues in face liveness detection are discussed.
- Various evaluation metrics used in face liveness detection are discussed.
- Future research directions and open perspectives are conceptualized to assist researchers in selecting the best solution for robust face liveness detection in face biometric authentication systems.
1.7. Limitations of the Study
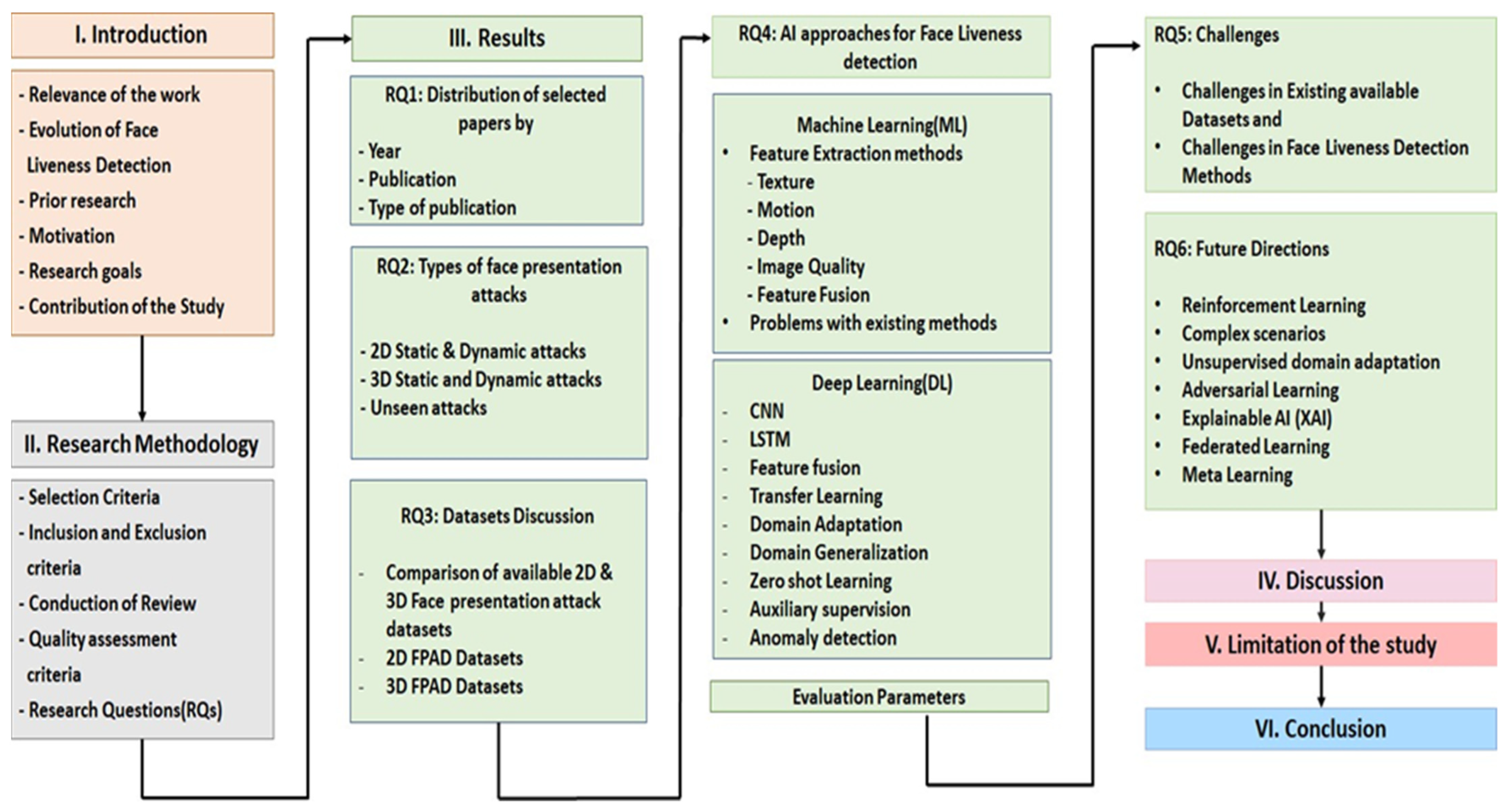
2. Research Methodology
2.1. Inclusion and Exclusion Criteria
- (i)
- Abstract-based screening: Disqualify irrelevant research papers based on knowledge and keywords in research abstracts. Abstracts of research papers that met at least 40% of the inclusion criteria were considered for the following steps.
- (ii)
- Full-text screening: The authors eliminated research papers that did not address or contribute to the search query in Table 5, i.e., abstracts that only represented minor aspects of the search query.
- (iii)
- Quality-analysis step: The remaining research papers were subjected to a quality assessment, and those that did not meet any of the following requirements were eliminated:
- (iv)
- C1: Findings and outcomes must include in research articles.
- (v)
- C2: The findings of research publications are supported by empirical evidence.
- (vi)
- C3: The research goals and findings must be well presented.
- (vii)
- C4: Appropriate and sufficient references must use in research papers.
2.2. Conduction of SR
3. Results
3.1. RQ1 Distribution of Publication Trends Related to Face Liveness Detection
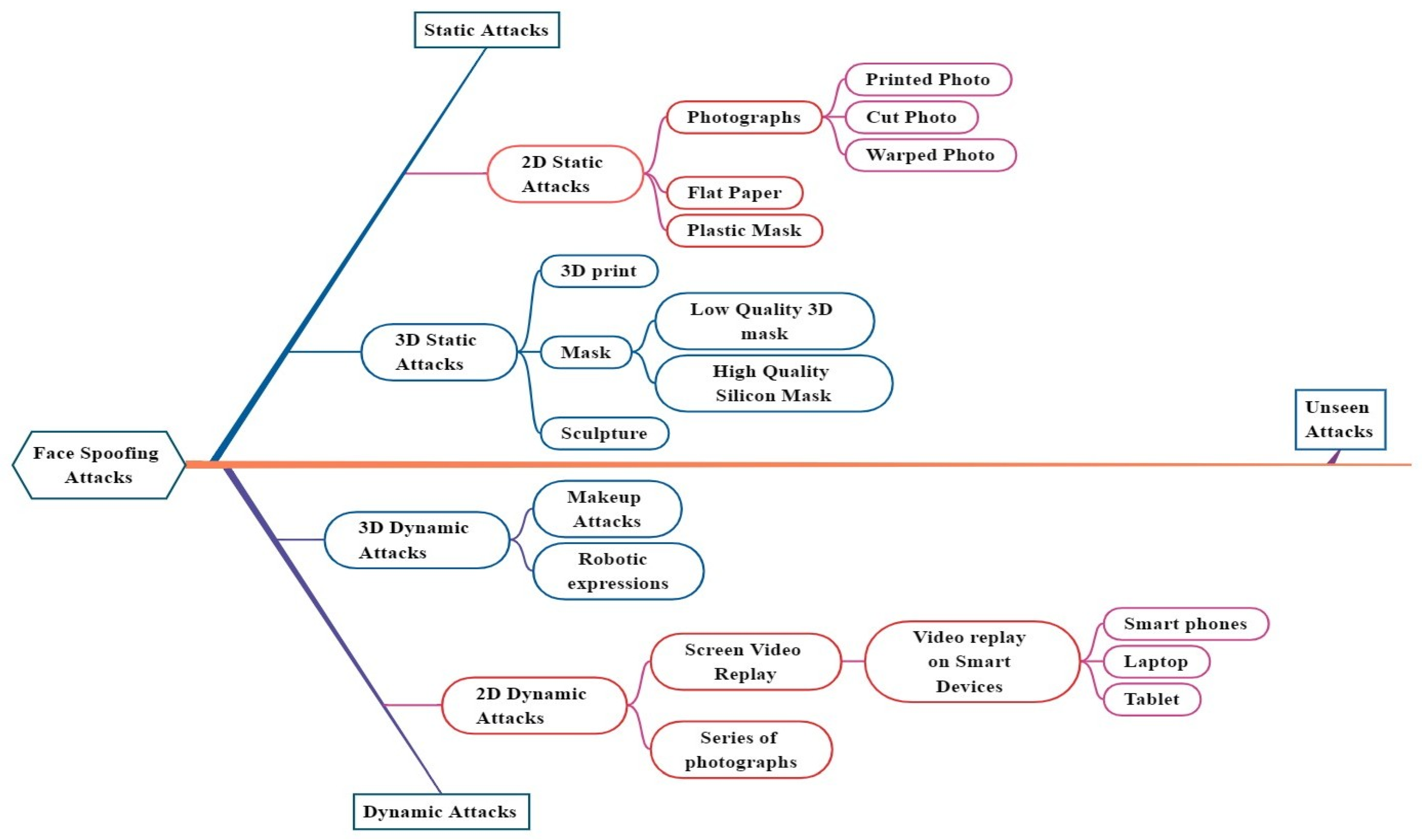
3.2. RQ2 Face Spoofing Attacks
3.2.1. 2D Static & Dynamic Attacks
3.2.2. 3D Static & Dynamic Attacks
3.3. RQ3 Standard Benchmark Datasets Used for Face Liveness Detection
4. RQ4 Artificial Intelligence for Face Liveness Detection
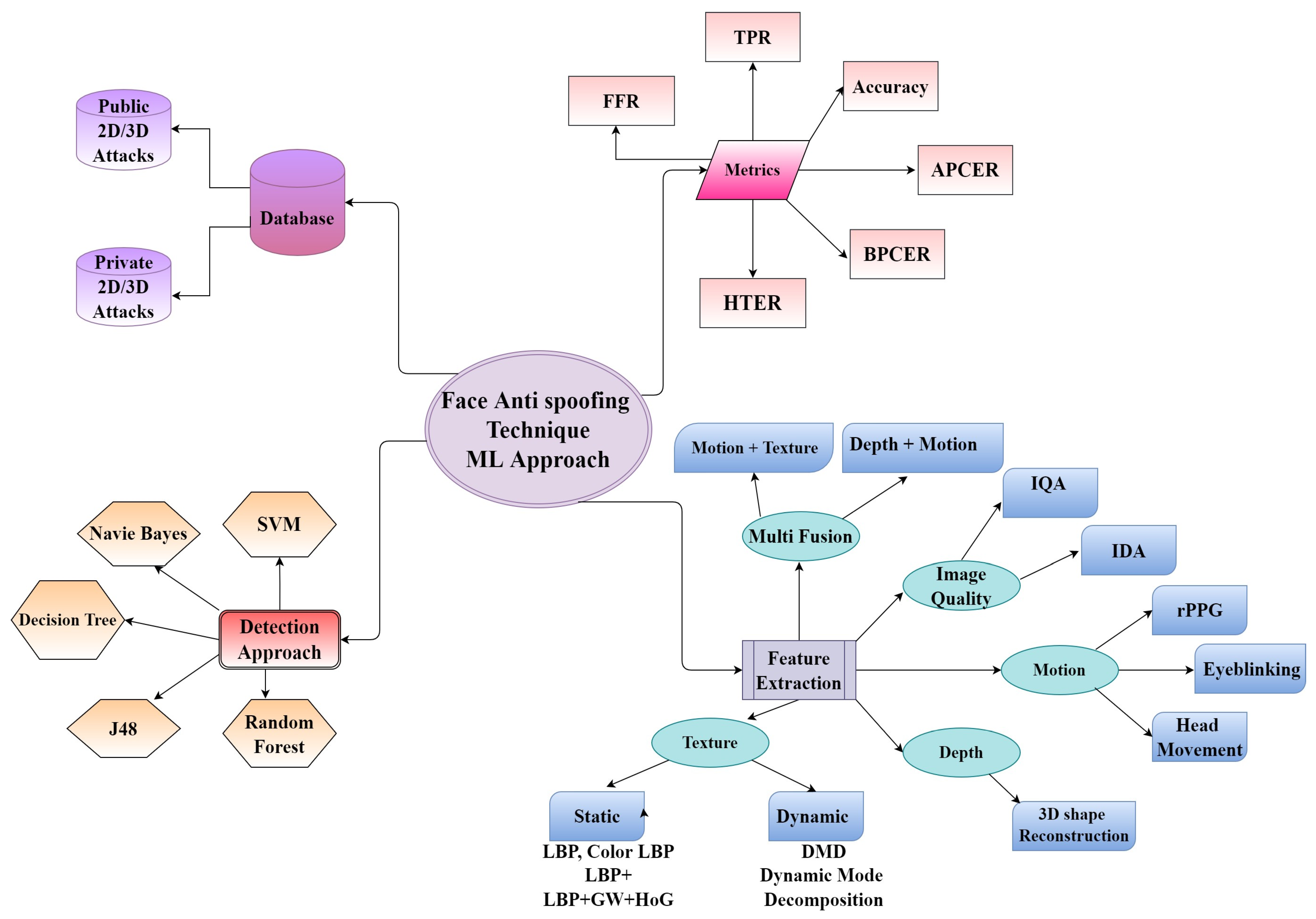
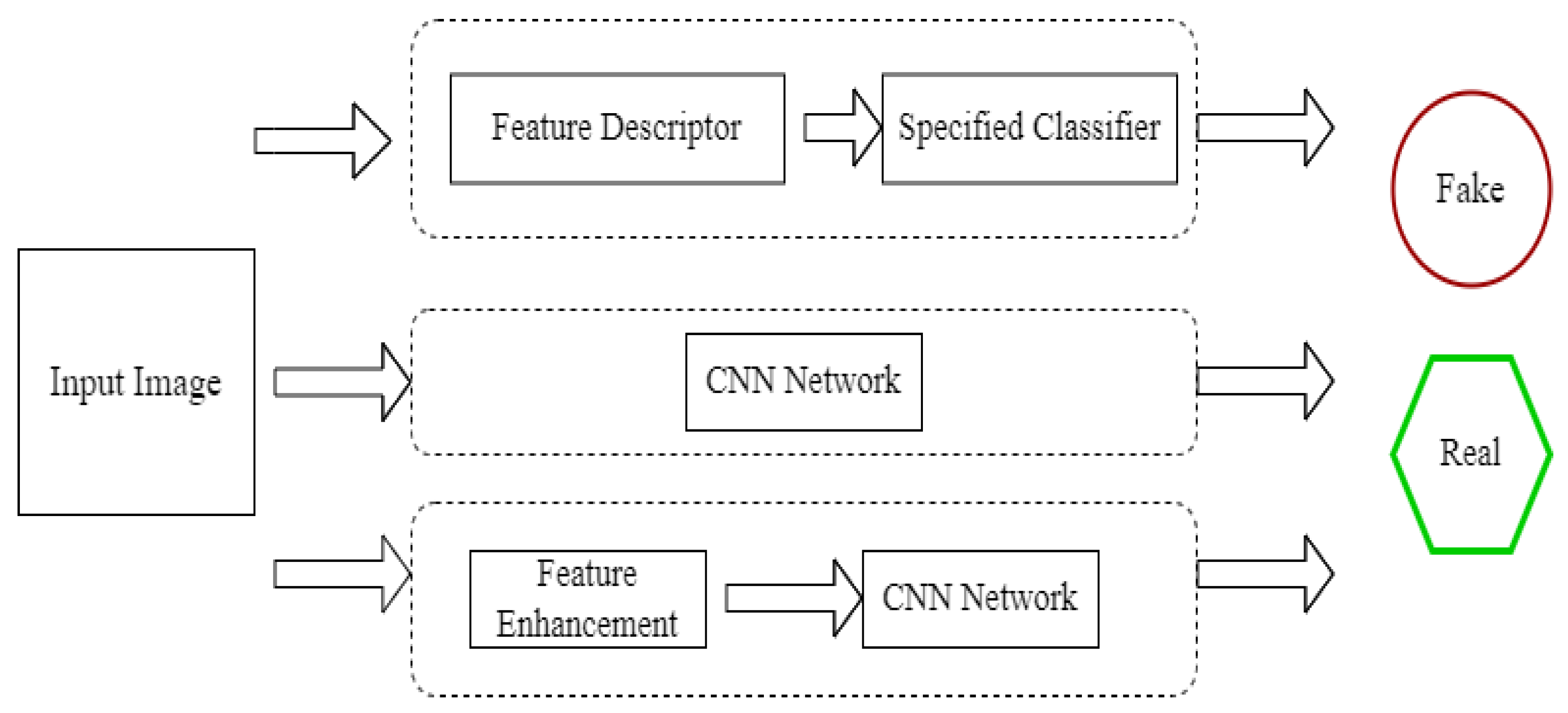
4.1. Machine Learning and Feature Extraction Methods for FLD
4.1.1. Texture-Based Feature Extraction
4.1.2. Motion-Based Feature Extraction
4.1.3. Depth-Based Feature Extraction
4.1.4. Image Quality-Based Feature Extraction
4.1.5. Problems in Existing Techniques
4.2. Deep Learning in FLD
4.3. Transfer Learning in Face Liveness Detection (FLD)
4.3.1. Domain Adaptation (DA) in FLD
4.3.2. Domain Generalization (DG) in FLD
4.4. Zero-Shot Learning in Face Liveness Detection
4.5. Anomaly Detection in Face Liveness Detection
5. RQ4 Evaluation Metrics
6. RQ 5 Limitations of Face Liveness Detection Methods
6.1. Limitations Existing Databases for Face Liveness Detection
6.2. Limitations of Existing Face Liveness Detection Techniques
7. RQ6 Future Directions
8. Discussion
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Sébastien, M.S.; Nixon, J.F.; Marcel, N.E. Handbook of Biometric Anti-Spoofing, 2nd ed.; Springer: Cham, Switzerland, 2019. [Google Scholar] [CrossRef]
- Sharma, S.B.; Dhall, I.; Nayak, S.R.; Chatterjee, P. Reliable Biometric Authentication with Privacy Protection. Adv. Commun. Devices Netw. 2023, 902, 233–249. [Google Scholar]
- Biometrics Recognition Using Deep Learning: A Survey. Available online: https://doi.org/10.1007/s10462-022-10237-x (accessed on 8 December 2022).
- Ross, A.; Jain, A.K. Biometrics, Overview. In Encyclopedia of Biometrics; Springer: Boston, MA, USA, 2015; pp. 289–294. [Google Scholar] [CrossRef]
- Cabana, P.F. Technical and Legal Challenges of the Use of Automated Facial Recognition Technologies for Law Enforcement and Forensic Purposes. In Artificial Intelligence, Social Harms and Human Rights; Završnik, A., Simončič, K., Eds.; Springer International Publishing: Cham, Switzerland, 2023; pp. 35–54. [Google Scholar] [CrossRef]
- FRB Report. “Market Research Report,” marketsandmarkets.com, 2021. Available online: https://www.marketsandmarkets.com/PressRelease (accessed on 8 December 2022).
- Kalmani, S.; Dilna, U. Application of Computer Vision for Multi-Layered Security to ATM Machine using Deep Learning Concept. In Proceedings of the 2022 International Conference on Applied Artificial Intelligence and Computing (ICAAIC), Online, 9–11 May 2022; pp. 999–1004. [Google Scholar] [CrossRef]
- Enhancing Bank Security System using Face Recognition, Iris Scanner and Palm Vein Technology. In Proceedings of the 2018 3rd International Conference On Internet of Things: Smart Innovation and Usages (IoT-SIU), Bhimtal, India, 23–24 February 2018. [CrossRef]
- Ali, O.; AlAhmad, A.; Kahtan, H. A review of advanced technologies available to improve the healthcare performance during COVID-19 pandemic. Procedia Comput. Sci. 2023, 217, 205–216. [Google Scholar] [CrossRef] [PubMed]
- Martins, B.O.; Lidén, K.; Jumbert, M.G. Border security and the digitalisation of sovereignty: Insights from EU borderwork. Eur. Secur. 2022, 31, 475–494. [Google Scholar] [CrossRef]
- Andrejevic, M.; Selwyn, N. Facial recognition technology in schools: Critical questions and concerns. Learn. Media Technol. 2020, 45, 115–128. [Google Scholar] [CrossRef]
- SonarGuard: Ultrasonic Face Liveness Detection on Mobile Devices. Available online: https://doi.org/10.1109/tcsvt.2023.3236303 (accessed on 8 December 2022).
- Ming, Z.; Visani, M.; Luqman, M.M.; Burie, J.-C. A Survey on Anti-Spoofing Methods for Facial Recognition with RGB Cameras of Generic Consumer Devices. J. Imaging 2020, 6, 139. [Google Scholar] [CrossRef]
- Liu, H.; Zheng, C.; Li, D.; Shen, X.; Lin, K.; Wang, J.; Zhang, Z.; Zhang, Z.; Xiong, N.N. EDMF: Efficient Deep Matrix Factorization with Review Feature Learning for Industrial Recommender System. IEEE Trans. Ind. Inform. 2022, 18, 4361–4371. [Google Scholar] [CrossRef]
- Liu, T.; Wang, J.; Yang, B.; Wang, X. NGDNet: Nonuniform Gaussian-label distribution learning for infrared head pose estimation and on-task behavior understanding in the classroom. Neurocomputing 2021, 436, 210–220. [Google Scholar] [CrossRef]
- Liu, T.; Wang, J.; Yang, B.; Wang, X. Facial expression recognition method with multi-label distribution learning for non-verbal behavior understanding in the classroom. Infrared Phys. Technol. 2021, 112, 103594. [Google Scholar] [CrossRef]
- Liu, H.; Liu, T.; Zhang, Z.; Sangaiah, A.K.; Yang, B.; Li, Y. ARHPE: Asymmetric Relation-Aware Representation Learning for Head Pose Estimation in Industrial Human–Computer Interaction. IEEE Trans. Ind. Inform. 2022, 18, 7107–7117. [Google Scholar] [CrossRef]
- Liu, H.; Liu, T.; Chen, Y.; Zhang, Z.; Li, Y.-F. EHPE: Skeleton Cues-based Gaussian Coordinate Encoding for Efficient Human Pose Estimation. IEEE Trans. Multimedia. 2022, 1–12. [Google Scholar] [CrossRef]
- Liu, H.; Fang, S.; Zhang, Z.; Li, D.; Lin, K.; Wang, J. MFDNet: Collaborative Poses Perception and Matrix Fisher Distribution for Head Pose Estimation. IEEE Trans. Multimedia 2022, 24, 2449–2460. [Google Scholar] [CrossRef]
- Garg, D.; Jain, P.; Kotecha, K.; Goel, P.; Varadarajan, V. An Efficient Multi-Scale Anchor Box Approach to Detect Partial Faces from a Video Sequence. Big Data Cogn. Comput. 2022, 6, 9. [Google Scholar] [CrossRef]
- Xie, X.; Bian, J.; Lai, J. Review on face liveness detection. J. Image Graph. 2022, 27, 63–87. [Google Scholar] [CrossRef]
- Costa-Pazo, A.; Pérez-Cabo, D.; Jiménez-Cabello, D.; Alba-Castro, J.L.; Vazquez-Fernandez, E. Face presentation attack detection. A comprehensive evaluation of the generalisation problem. IET Biom. 2021, 10, 408–429. [Google Scholar] [CrossRef]
- Khade, S.; Gite, S.; Pradhan, B. Iris Liveness Detection Using Multiple Deep Convolution Networks. Big Data Cogn. Comput. 2022, 6, 67. [Google Scholar] [CrossRef]
- Khade, S.; Gite, S.; Thepade, S.D.; Pradhan, B.; Alamri, A. Detection of Iris Presentation Attacks Using Feature Fusion of Thepade’s Sorted Block Truncation Coding with Gray-Level Co-Occurrence Matrix Features. Sensors 2021, 21, 7408. [Google Scholar] [CrossRef]
- Zhang, M.; Zeng, K.; Wang, J. A Survey on Face Anti-Spoofing Algorithms. J. Inf. Hiding Priv. Prot. 2020, 2, 21–34. [Google Scholar] [CrossRef]
- Raheem, E.A.; Ahmad, S.M.S.; Adnan, W.A.W. Insight on face liveness detection: A systematic literature review. Int. J. Electr. Comput. Eng. 2019, 9, 5165–5175. [Google Scholar] [CrossRef]
- Ramachandra, R.; Busch, C. Presentation Attack Detection Methods for Face Recognition Systems: A comprehensive survey. ACM Comput. Surv. 2017, 50, 1–37. [Google Scholar] [CrossRef]
- Komulainen, J.; Boulkenafet, Z.; Akhtar, Z. Review of Face Presentation Attack Detection Competitions; Springer International Publishing: Cham, Switzerland, 2019; pp. 291–317. [Google Scholar] [CrossRef]
- Yu, Z.; Qin, Y.; Li, X.; Zhao, C.; Lei, Z.; Zhao, G. Deep Learning for Face Anti-Spoofing: A Survey. arXiv 2021. Available online: http://arxiv.org/abs/2106.14948 (accessed on 8 December 2022).
- Abdullakutty, F.; Elyan, E.; Johnston, P. A review of state-of-the-art in Face Presentation Attack Detection: From early development to advanced deep learning and multi-modal fusion methods. Inf. Fusion 2021, 75, 55–69. [Google Scholar] [CrossRef]
- Purnapatra, S.; Smalt, N.; Bahmani, K.; Das, P.; Yambay, D.; Mohammadi, A.; George, A.; Bourlai, T.; Marcel, S.; Schuckers, S.; et al. Face Liveness Detection Competition (LivDet-Face)—2021. IEEE Int. Jt. Conf. Biom. IJCB 2021, 1–10. [Google Scholar] [CrossRef]
- Kowalski, M. A Study on Presentation Attack Detection in Thermal Infrared. Sensors 2020, 20, 3988. [Google Scholar] [CrossRef]
- Ghaffar, I.A.; Mohd, M.N.H. Presentation attack detection for face recognition on smartphones: A comprehensive review. J. Telecommun. Electron. Comput. Eng. 2017, 9, 33–38. [Google Scholar]
- Kenneth, M.O.; Sulaimon, B.A.; Abdulhamid, S.M.; Ochei, L.C. A Systematic Literature Review on Face Morphing Attack Detection (MAD). Illum. Artif. Intell. Cybersecur. Forensics 2022, 109, 139–172. [Google Scholar] [CrossRef]
- A Bibliometric Analysis of Face Presentation Attacks based on Domain Adaptation. Available online: https://digitalcommons.unl.edu/libphilprac/5454/ (accessed on 18 December 2022).
- Moher, D.; Liberati, A.; Tetzlaff, J.; Altman, D.G. Preferred reporting items for systematic reviews and meta-analyses: The PRISMA statement. BMJ 2009, 339, 332–336. [Google Scholar] [CrossRef]
- Panic, N.; Leoncini, E.; de Belvis, G.; Ricciardi, W.; Boccia, S. Evaluation of the Endorsement of the Preferred Reporting Items for Systematic Reviews and Meta-Analysis (PRISMA) Statement on the Quality of Published Systematic Review and Meta-Analyses. PLoS ONE 2013, 8, e83138. [Google Scholar] [CrossRef]
- Rathgeb, C.; Drozdowski, P.; Busch, C. Detection of Makeup Presentation Attacks based on Deep Face Representations. Int. Conf. Pattern Recognit. (ICPR) 2021, 3443–3450. [Google Scholar] [CrossRef]
- Boulkenafet, Z.; Komulainen, J.; Li, L.; Feng, X.; Hadid, A. OULU-NPU: A mobile face presentation attack database with real-world variations. In Proceedings of the 2017 12th IEEE International Conference on Automatic Face & Gesture Recognition (FG 2017), Washington, DC, USA, 30 May–3 June 2017; pp. 612–618. [Google Scholar] [CrossRef]
- On the Effectiveness of Local Binary Patterns in Face Anti-Spoofing. Available online: https://www.semanticscholar.org/paper/On-the-effectiveness-of-local-binary-patterns-in-Chingovska-Anjos/30648c20ffa148e2d15cb705abfb8a1650f652df (accessed on 18 December 2022).
- Agarwal, A.; Yadav, D.; Kohli, N.; Singh, R.; Vatsa, M.; Noore, A. Face Presentation Attack with Latex Masks in Multispectral Videos. IEEE Comput. Soc. Conf. Comput. Vis. Pattern Recognit. Workshops 2017, 275–283. [Google Scholar] [CrossRef]
- Erdogmus, N.; Marcel, S. Spoofing in 2D face recognition with 3D masks and anti-spoofing with Kinect. In Proceedings of the IEEE 6th International Conference on Biometrics: Theory, Applications and Systems, BTAS, Arlington, VA, USA, 29 September 2013; pp. 1–6. [Google Scholar] [CrossRef]
- Tan, X.; Li, Y.; Liu, J.; Jiang, L. Face liveness detection from a single image with sparse low rank bilinear discriminative model. In Proceedings of the European Conference on Computer Vision, Heraklion, Greece, 5–11 September 2010; pp. 504–517. [Google Scholar] [CrossRef]
- de Souza, G.B.; Papa, J.P.; Marana, A.N. On the Learning of Deep Local Features for Robust Face Spoofing Detection. In Proceedings of the 31st Conference on Graphics, Patterns and Images, SIBGRAPI, Paraná, Brazil, 29 October–1 November 2018; pp. 258–265. [Google Scholar] [CrossRef]
- Li, J.; Zhang, X.; Zhang, Y.; Wang, H.; Yang, F. Face Liveness Detection Based on Multiple Feature Descriptors. In Proceedings of the 2019 International Conference on Technologies and Applications of Artificial Intelligence, TAAI, Kaohsiung, Taiwan, 21–23 November 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Shilpa, S.; Sajeena, A. Hybrid Deep Learning Approach for Face Spoofing Detection. In Proceedings of the International Conference on Intelligent Computing and Control Systems, ICCS, Madurai, India, 15–17 May 2019; pp. 412–416. [Google Scholar] [CrossRef]
- Chen, B.; Yang, W.; Wang, S. Generalized Face Antispoofing by Learning to Fuse Features from High- and Low-Frequency Domains. IEEE MultiMedia 2021, 28, 56–64. [Google Scholar] [CrossRef]
- Nguyen, D.T.; Pham, T.D.; Baek, N.R.; Park, K.R. Combining Deep and Handcrafted Image Features for Presentation Attack Detection in Face Recognition Systems Using Visible-Light Camera Sensors. Sensors 2018, 18, 699. [Google Scholar] [CrossRef]
- Perumal, R.S.; Santosh, K.C.; Chandra Mouli, P.V.S.S.R. Learning Deep Feature Representation for Face Spoofing. In Recent Trends in Image Processing and Pattern Recognition. RTIP2R 2018. Communications in Computer and Information Science; Springer Nature: Singapore, 2019; Volume 1035, pp. 178–185. [Google Scholar]
- Song, X.; Zhao, X.; Fang, L.; Lin, T. Discriminative representation combinations for accurate face spoofing detection. Pattern Recognit. 2019, 85, 220–231. [Google Scholar] [CrossRef]
- Zuo, Y.; Gao, W.; Wang, J. Face Liveness Detection Algorithm based on Livenesslight Network. In Proceedings of the 2020 International Conference on High Performance Big Data and Intelligent Systems, HPBD and IS, Shenzhen, China, 23 May 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Wen, D.; Han, H.; Jain, A.K. Face Spoof Detection With Image Distortion Analysis. IEEE Trans. Inf. Forensics Secur. 2015, 10, 746–761. [Google Scholar] [CrossRef]
- Chen, B.; Yang, W.; Li, H.; Wang, S.; Kwong, S. Camera Invariant Feature Learning for Generalized Face Anti-Spoofing. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2477–2492. [Google Scholar] [CrossRef]
- Cai, R.; Li, H.; Wang, S.; Chen, C.; Kot, A.C. DRL-FAS: A Novel Framework Based on Deep Reinforcement Learning for Face Anti-Spoofing. IEEE Trans. Inf. Forensics Secur. 2021, 16, 937–951. [Google Scholar] [CrossRef]
- Guo, J.; Zhu, X.; Xiao, J.; Lei, Z.; Wan, G.; Li, S.Z. Improving Face Anti-Spoofing by 3D Virtual Synthesis. In Proceedings of the 2019 International Conference on Biometrics (ICB), Crete, Greece, 4–7 June 2019. [Google Scholar] [CrossRef]
- Zhang, Z.; Yan, J.; Liu, S.; Lei, Z.; Yi, D.; Li, S.Z. A face antispoofing database with diverse attacks. In Proceedings of the 2012 5th IAPR International Conference on BIOMETRICS (ICB), New Delhi, India, 29 March–1 April 2012; pp. 26–31. [Google Scholar] [CrossRef]
- Li, H.; Wang, S.; He, P.; Rocha, A.D.R. Face Anti-Spoofing with Deep Neural Network Distillation. IEEE J. Sel. Top. Signal Process. 2020, 14, 933–946. [Google Scholar] [CrossRef]
- Yang, J.; Lei, Z.; Yi, D.; Li, S.Z. Person-Specific Face Antispoofing with Subject Domain Adaptation. IEEE Trans. Inf. Forensics Secur. 2015, 10, 797–809. [Google Scholar] [CrossRef]
- Transfer Learning Using Convolutional Neural Networks for Face Anti-Spoofing. Available online: https://doi.org/10.1007/978-3-319-59876-5_4 (accessed on 8 December 2022).
- Vareto, R.H.; Diniz, M.A.; Schwartz, W.R. Face De-spoofing: Anti-spoofing via Noise Modeling. Progress in Pattern Recognition, Image Analysis, Computer Vision, and Applications. CIARP 2019. Lect. Notes Comput. Sci. 2019, 11217, 187–197. [Google Scholar] [CrossRef]
- Liu, Y.; Stehouwer, J.; Jourabloo, A.; Liu, X. Deep Tree Learning for Zero-Shot Face Anti-Spoofing. Proc. IEEE Comput. Soc. Conf. Comput. Vis. Pattern Recognit. 2019, 4675–4684. [Google Scholar] [CrossRef]
- Vareto, R.H.; Schwartz, W.R. Face spoofing detection via ensemble of classifiers toward low-power devices. Pattern Anal. Appl. 2020, 24, 511–521. [Google Scholar] [CrossRef]
- Zhang, B.; Tondi, B.; Barni, M. Adversarial examples for replay attacks against CNN-based face recognition with anti-spoofing capability. Comput. Vis. Image Underst. 2020, 197–198, 102988. [Google Scholar] [CrossRef]
- Rehman, Y.A.U.; Po, L.M.; Liu, M. Deep learning for face anti-spoofing: An end-to-end approach. Signal Processing—Algorithms, Architectures, Arrangements, and Applications Conference Proceedings, SPA. IEEE 2017, 195–200. [Google Scholar] [CrossRef]
- Ying, X.; Li, X.; Chuah, M.C. LiveFace: A Multi-task CNN for Fast Face-Authentication. In Proceedings of the 17th IEEE International Conference on Machine Learning and Applications, ICMLA, Orlando, FL, USA, 17–20 December 2018; pp. 955–960. [Google Scholar] [CrossRef]
- Nikitin, M.Y.; Konushin, V.S.; Konushin, A.S. Face anti-spoofing with joint spoofing medium detection and eye blinking analysis. Comput. Opt. 2019, 43, 618–626. [Google Scholar] [CrossRef]
- Chen, H.; Hu, G.; Lei, Z.; Chen, Y.; Robertson, N.M.; Li, S.Z. Attention-Based Two-Stream Convolutional Networks for Face Spoofing Detection. IEEE Trans. Inf. Forensics Secur. 2019, 15, 578–593. [Google Scholar] [CrossRef]
- Erdogmus, N.; Marcel, S. Spoofing Face Recognition With 3D Masks. IEEE Trans. Inf. Forensics Secur. 2014, 9, 1084–1097. [Google Scholar] [CrossRef]
- Te, G.; Hu, W.; Guo, Z. Exploring Hypergraph Representation On Face Anti-Spoofing Beyond 2d Attacks. In Proceedings of the IEEE International Conference on Multimedia and Expo (ICME), London, UK, 6–10 July 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Agarwal, A.; Singh, R.; Vatsa, M. Face anti-spoofing using Haralick features. In Proceedings of the 2016 IEEE 8th International Conference on Biometrics Theory, Applications and Systems (BTAS), Niagara Falls, NY, USA, 6–9 September 2016. [Google Scholar] [CrossRef]
- Bousnina, N.; Zheng, L.; Mikram, M.; Ghouzali, S.; Minaoui, K. Unraveling robustness of deep face anti-spoofing models against pixel attacks. Multimedia Tools Appl. 2021, 80, 7229–7246. [Google Scholar] [CrossRef]
- Mehta, S.; Uberoi, A.; Agarwal, A.; Vatsa, M.; Singh, R. Crafting A Panoptic Face Presentation Attack Detector. In Proceedings of the 2019 International Conference on Biometrics, ICB 2019, Crete, Greece, 4–7 June 2019. [Google Scholar] [CrossRef]
- Tu, X.; Zhang, H.; Xie, M.; Luo, Y.; Zhang, Y.; Ma, Z. Deep transfer across domains for face antispoofing. J. Electron. Imaging 2019, 28. [Google Scholar] [CrossRef]
- Chen, B.; Yang, W.; Wang, S. Face Anti-Spoofing by Fusing High and Low Frequency Features for Advanced Generalization Capability. In Proceedings of the 3rd International Conference on Multimedia Information Processing and Retrieval, MIPR 2020, Guangdong, China, 6–8 August 2020; pp. 199–204. [Google Scholar] [CrossRef]
- Shao, R.; Lan, X.; Li, J.; Yuen, P.C. Multi-Adversarial Discriminative Deep Domain Generalization for Face Presentation Attack Detection. In Proceedings of the IEEE Computer Society Conference on Computer Vision and Pattern Recognition, San Juan, PR, USA, 17–19 June 1997; pp. 10015–10023. [Google Scholar] [CrossRef]
- Patel, K.; Han, H.; Jain, A.K. Secure Face Unlock: Spoof Detection on Smartphones. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2268–2283. [Google Scholar] [CrossRef]
- Wang, G.; Han, H.; Shan, S.; Chen, X. Improving Cross-database Face Presentation Attack Detection via Adversarial Domain Adaptation. In Proceedings of the 2019 International Conference on Biometrics, ICB, Crete, Greece, 4–7 June 2019. [Google Scholar] [CrossRef]
- Muhammad, U.; Hadid, A. Face Anti-spoofing using Hybrid Residual Learning Framework. In Proceedings of the 2019 International Conference on Biometrics, ICB, Crete, Greece, 4–7 June 2019. [Google Scholar] [CrossRef]
- Nagpal, C.; Dubey, S.R. A Performance Evaluation of Convolutional Neural Networks for Face Anti Spoofing. In Proceedings of the International Joint Conference on Neural Networks, Budapest, Hungary, 14–19 July 2019. [Google Scholar] [CrossRef]
- Sun, Y.; Xiong, H.; Yiu, S.M. Understanding deep face anti-spoofing: From the perspective of data. Vis. Comput. 2021, 37, 1015–1028. [Google Scholar] [CrossRef]
- Patel, K.; Han, H.; Jain, A.K. Cross-Database Face Antispoofing with Robust Feature Representation. Available online: https://doi.org/10.1007/978-3-319-46654-5_67 (accessed on 8 December 2022).
- Galbally, J.; Satta, R. Three-dimensional and two-and-a-half-dimensional face recognition spoofing using three-dimensional printed models. IET Biom. 2016, 5, 83–91. [Google Scholar] [CrossRef]
- Steiner, H.; Kolb, A.; Jung, N. Reliable face anti-spoofing using multispectral SWIR imaging. In Proceedings of the 2016 International Conference on Biometrics, ICB, Halmstad, Sweden, 13–16 June 2016. [Google Scholar] [CrossRef]
- Jia, S.; Guo, G.; Xu, Z. A survey on 3D mask presentation attack detection and countermeasures. Pattern Recognit. 2020, 98, 107032. [Google Scholar] [CrossRef]
- de Freitas, T.; Komulaine, J.; Anjos, A.; De Martino, J.M.; Hadid, A.; Pietikäinen, M.; Marcel, S. PereiraFace Liveness Detection using Dynamic Texture. EURASIP J. Image Video Process 2014, 2, 1–15. Available online: https://jivp.eurasipjournals.com/content/2014/1/2 (accessed on 8 December 2022).
- Liu, S.; Yang, B.; Yuen, P.C.; Zhao, G. A 3D Mask Face Anti-Spoofing Database with Real World Variations. In Proceedings of the IEEE Computer Society Conference on Computer Vision and Pattern Recognition Workshops, Las Vegas, NV, USA, 26 June–1 July 2016; pp. 1551–1557. [Google Scholar] [CrossRef]
- Li, X.; Wan, J.; Jin, Y.; Liu, A.; Guo, G.; Li, S.Z. 3DPC-Net: 3D Point Cloud Network for Face Anti-spoofing. In Proceedings of the IJCB 2020—IEEE/IAPR International Joint Conference on Biometrics, Houston, TX, USA, 28 September–1 October 2020. [Google Scholar] [CrossRef]
- Xu, Z.; Li, S. Learning temporal features using LSTM-CNN architecture for face. In Proceedings of the 2015 IAPR Asian Conference on Pattern Recognition, Kuala Lumpur, Malaysia, 3–6 November 2015; pp. 141–145. [Google Scholar]
- Thepade, S.; Jagdale, P.; Bhingurde, A.; Erandole, S. Novel Face Liveness Detection Using Fusion of Features and Machine Learning Classifiers. In Proceedings of the 2020 IEEE International Conference on Informatics, IoT, and Enabling Technologies, ICIoT, Doha, Qatar, 2–5 February 2020; pp. 141–145. [Google Scholar] [CrossRef]
- Manjani, I.; Tariyal, S.; Vatsa, M.; Singh, R.; Majumdar, A. Detecting Silicone Mask-Based Presentation Attack via Deep Dictionary Learning. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1713–1723. [Google Scholar] [CrossRef]
- Jia, S.; Hu, C.; Guo, G.; Xu, Z. A Database for Face Presentation Attack Using Wax Figure Faces. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Trento, Italy, 9–10 September 2019; pp. 39–47. [Google Scholar] [CrossRef]
- Sun, W.; Song, Y.; Chen, C.; Huang, J.; Kot, A.C. Face Spoofing Detection Based on Local Ternary Label Supervision in Fully Convolutional Networks. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3181–3196. [Google Scholar] [CrossRef]
- Bhattacharjee, S.; Marcel, S. What You Can’t See Can Help You—Extended-Range Imaging for 3D-Mask Presentation Attack Detection. In Proceedings of the 2017 International Conference of the Biometrics Special Interest Group (BIOSIG), Darmstadt, Germany, 20–22 September 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Liu, Y.; Jourabloo, A.; Liu, X. Learning Deep Models for Face Anti-Spoofing: Binary or Auxiliary Supervision. In Proceedings of the IEEE Computer Society Conference on Computer Vision and Pattern Recognition, Salt Lake City, UT, USA, 18–23 June 2018. [Google Scholar] [CrossRef]
- Ito, K.; Kimura, A.; Aoki, T. Performance Evaluation of Face Anti-Spoofing Method Using Deep Metric Learning from a Few Frames of Face Video. In Proceedings of the 2020 Asia-Pacific Signal and Information Processing Association Annual Summit and Conference, APSIPA ASC 2020, Auckland, New Zealand, 7–10 December 2020; pp. 1414–1419. [Google Scholar]
- Li, X.; Wu, W.; Li, T.; Su, Y.; Yang, L. Face Liveness Detection Based on Parallel CNN. J. Phys. Conf. Ser. 2021, 1549, 042069. [Google Scholar] [CrossRef]
- Liu, A.; Tan, Z.; Wan, J.; Escalera, S.; Guo, G.; Li, S.Z. CASIA-SURF CeFA: A Benchmark for Multi-modal Cross-ethnicity Face Anti-spoofing. In Proceedings of the 2021 IEEE Winter Conference on Applications of Computer Vision (WACV), Waikoloa, HI, USA, 3–7 January 2021; pp. 1178–1186. [Google Scholar] [CrossRef]
- Liu, A.; Tan, Z.; Li, X.; Wan, J.; Escalera, S.; Guo, G.; Li, S.Z. Static and dynamic fusion for multi-modal cross-ethnicity face anti-spoofing. arXiv 2019, arXiv:Abs/1912.0, 2019. [Google Scholar]
- Liu, A.; Zhao, C.; Yu, Z.; Wan, J.; Su, A.; Liu, X.; Tan, Z.; Escalera, S.; Xing, J.; Liang, Y.; et al. Contrastive Context-Aware Learning for 3D High-Fidelity Mask Face Presentation Attack Detection. IEEE Trans. Inf. Forensics Secur. 2022, 17, 2497–2507. [Google Scholar] [CrossRef]
- Arashloo, S.R. Unseen Face Presentation Attack Detection Using Sparse Multiple Kernel Fisher Null-Space. IEEE Trans. Circuits Syst. Video Technol. 2021, 31, 4084–4095. [Google Scholar] [CrossRef]
- Peixoto, B.; Michelassi, C.; Rocha, A. Face liveness detection under bad illumination conditions. In Proceedings of the 2011 18th IEEE International Conference on Image Processing, Brussels, Belgium, 11–14 September 2011; pp. 3557–3560. [Google Scholar] [CrossRef]
- Hassanien, A.E. Advances in Intelligent Systems and Computing 723 Mohamed Mostafa Editors. In Proceedings of the the International Conference on Advanced Machine Learning Technologies and Applications (AMLTA2018) 2020, Cairo, Egypt, 22–24 February 2018. [Google Scholar]
- Li, H.; Li, W.; Cao, H.; Wang, S.; Huang, F.; Kot, A.C. Unsupervised Domain Adaptation for Face Anti-Spoofing. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1794–1809. [Google Scholar] [CrossRef]
- Ghofrani, A.; Toroghi, R.M.; Tabatabaie, S.M. Attention-Based Face AntiSpoofing of RGB Camera using a Minimal End-2-End Neural Network. Iranian Conference on Machine Vision and Image Processing, MVIP. In Proceedings of the Iranian Conference on Machine Vision and Image Processing, MVIP, Qom, Iran, 18–20 February 2020. [Google Scholar] [CrossRef]
- Liu, W.; Wei, X.; Lei, T.; Wang, X.; Meng, H.; Nandi, A.K. Data-Fusion-Based Two-Stage Cascade Framework for Multimodality Face Anti-Spoofing. IEEE Trans. Cogn. Dev. Syst. 2021, 14, 672–683. [Google Scholar] [CrossRef]
- George, A.; Mostaani, Z.; Geissenbuhler, D.; Nikisins, O.; Anjos, A.; Marcel, S. Biometric Face Presentation Attack Detection With Multi-Channel Convolutional Neural Network. IEEE Trans. Inf. Forensics Secur. 2020, 15, 42–55. [Google Scholar] [CrossRef]
- Amir Mohammadi, S.M.; Bhattacharjee, S. Domain Adaptation for Generalization of Face Presentation Attack Detection in Mobile Settengs with Minimal Information. In Proceedings of the ICASSP 2020–2020 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Barcelona, Spain, 4–8 May 2020; pp. 1001–1005. [Google Scholar] [CrossRef]
- Nikisins, O.; George, A.; Marcel, S. Domain Adaptation in Multi-Channel Autoencoder based Features for Robust Face Anti-Spoofing. In Proceedings of the 2019 International Conference on Biometrics, ICB, Crete, Greece, 4–7 June 2019. [Google Scholar] [CrossRef]
- Yu, Z.; Wan, J.; Qin, Y.; Li, X.; Li, S.Z.; Zhao, G. NAS-FAS: Static-Dynamic Central Difference Network Search for Face Anti-Spoofing. IEEE Trans. Pattern Anal. Mach. Intell. 2020, 43, 3005–3023. [Google Scholar] [CrossRef]
- Komulainen, J.; Hadid, A.; Pietikainen, M. Face spoofing detection from single images using texture and local shape analysis. IET Biom. 2012, 1, 3–10. [Google Scholar] [CrossRef]
- Boulkenafet, Z.; Komulainen, J.; Hadid, A. Face anti-spoofing based on color texture analysis. In Proceedings of the International Conference on Image Processing, ICIP, Bordeaux, France, 16–19 October 2015; Volume 2015, pp. 2636–2640. [Google Scholar] [CrossRef]
- Lu, L.; Yu, J.; Chen, Y.; Liu, H.; Zhu, Y.; Liu, Y.; Li, M. LipPass: Lip Reading-based User Authentication on Smartphones Leveraging Acoustic Signals. In Proceedings of the IEEE INFOCOM, Honolulu, HI, USA, 16–19 April 2018; pp. 1466–1474. [Google Scholar] [CrossRef]
- Singh, A.K.; Joshi, P.; Nandi, G.C. Face recognition with liveness detection using eye and mouth movement. In Proceedings of the 2014 International Conference on Signal Propagation and Computer Technology, ICSPCT, Rajasthan, India, 12–13 July 2014; pp. 592–597. [Google Scholar] [CrossRef]
- Smiatacz, M. Liveness Measurements Using Optical Flow for Biometric Person Authentication. Metrol. Meas. Syst. 2012, 19, 257–268. [Google Scholar] [CrossRef]
- Li, J.; Wang, Y.; Tan, T.; Jain, A.K. Live face detection based on the analysis of Fourier spectra. Biom. Technol. Hum. Identif. 2004, 5404, 296–304. [Google Scholar] [CrossRef]
- Kollreider, K.; Fronthaler, H.; Bigun, J. Non-intrusive liveness detection by face images. Image Vis. Comput. 2009, 27, 233–244. [Google Scholar] [CrossRef]
- Ning, X.; Li, W.; Wei, M.; Sun, L.; Dong, X. Face Anti-spoofing based on Deep Stack Generalization Networks. In Proceedings of the 7th International Conference on Pattern Recognition Applications and Methods—ICPRAM 2018, Funchal, Portugal, 16–18 January 2018; pp. 317–323. [Google Scholar] [CrossRef]
- Li, L.; Feng, X.; Boulkenafet, Z.; Xia, Z.; Li, M.; Hadid, A. An original face anti-spoofing approach using partial convolutional neural network. In Proceedings of the 2016 6th International Conference on Image Processing Theory, Tools and Applications, IPTA, Oulu, Finland, 12–15 December 2016. [Google Scholar] [CrossRef]
- Tirunagari, S.; Poh, N.; Windridge, D.; Iorliam, A.; Suki, N.; Ho, A.T.S. Detection of Face Spoofing Using Visual Dynamics. IEEE Trans. Inf. Forensics Secur. 2015, 10, 762–777. [Google Scholar] [CrossRef]
- Liu, S.-Q.; Lan, X.; Yuen, P.C. Remote Photoplethysmography Correspondence Feature for 3D Mask Face Presentation Attack Detection. In Computer Vision—ECCV 2018. ECCV 2018. Lecture Notes in Computer Science; Ferrari, V., Hebert, M., Sminchisescu, C., Weiss, Y., Eds.; Springer: Cham, Swizterland, 2018; Volume 11220, pp. 577–594. [Google Scholar] [CrossRef]
- Yang, J.; Lei, Z.; Li, S.Z. Learn Convolutional Neural Network for Face Anti-Spoofing. 2014. Available online: https://arxiv.org/abs/1408.5601 (accessed on 15 September 2022).
- Wang, G.; Han, H.; Shan, S.; Chen, X. Unsupervised Adversarial Domain Adaptation for Cross-Domain Face Presentation Attack Detection. IEEE Trans. Inf. Forensics Secur. 2021, 16, 56–69. [Google Scholar] [CrossRef]
- Wang, Z.; Zhao, C.; Qin, Y.; Zhou, Q.; Qi, G.; Wan, J.; Lei, Z. Exploiting Temporal and Depth Information for Multi-Frame Face Anti-Spoofing. 2018. Available online: https://arxiv.org/abs/1811.05118 (accessed on 10 October 2022).
- 3D Mask Face Anti-Spoofing with Remote Photoplethysmography. Available online: https://doi.org/10.1007/978-3-319-46478-7_6 (accessed on 10 October 2022).
- Li, H.; Wang, S.; Kot, A.C. Face spoofing detection with image quality regression. In Proceedings of the 2016 6th International Conference on Image Processing Theory, Tools and Applications, IPTA, Oulu, Finland, 12–15 December 2016. [Google Scholar] [CrossRef]
- Singh, A.K.; Joshi, P.; Nandi, G. Face liveness detection through face structure analysis. Int. J. Appl. Pattern Recognit. 2014, 1, 338–360. [Google Scholar] [CrossRef]
- George, A.; Marcel, S. Deep Pixel-wise Binary Supervision for Face Presentation Attack Detection. In Proceedings of the 2019 International Conference on Biometrics, ICB, Crete, Greece, 4–7 June 2019. [Google Scholar] [CrossRef]
- Jatain, R.; Jailia, M. Authentication and Facial Expression Analysis System using Deep Transfer Learning Approach. In Proceedings of the 2022 6th International Conference on Computing Methodologies and Communication (ICCMC), Tamil Nadu, India, 29–31 March 2022; pp. 1209–1214. [Google Scholar] [CrossRef]
- Muhammad, U.; Yu, Z.; Komulainen, J. Self-supervised 2D face presentation attack detection via temporal sequence sampling. Pattern Recognit. Lett. 2022, 156, 15–22. [Google Scholar] [CrossRef]
- Li, Z.; Cai, R.; Li, H.; Lam, K.-Y.; Hu, Y.; Kot, A.C. One-Class Knowledge Distillation for Face Presentation Attack Detection. IEEE Trans. Inf. Forensics Secur. 2022, 17, 2137–2150. [Google Scholar] [CrossRef]
- Li, H.; He, P.; Wang, S.; Rocha, A.; Jiang, X.; Kot, A.C. Learning Generalized Deep Feature Representation for Face Anti-Spoofing. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2639–2652. [Google Scholar] [CrossRef]
- Zhou, F.; Gao, C.; Chen, F.; Li, C.; Li, X.; Yang, F.; Zhao, Y. Face Anti-Spoofing Based on Multi-layer Domain Adaptation. In Proceedings of the 2019 IEEE International Conference on Multimedia & Expo Workshops, Shanghai, China, 8–12 July 2019; pp. 192–197. [Google Scholar] [CrossRef]
- Qin, Y.; Zhang, W.; Shi, J.; Wang, Z.; Yan, L. One-class adaptation face anti-spoofing with loss function search. Neurocomputing 2020, 417, 384–395. [Google Scholar] [CrossRef]
- Sun, W.; Song, Y.; Zhao, H.; Jin, Z. A Face Spoofing Detection Method Based on Domain Adaptation and Lossless Size Adaptation. IEEE Access 2020, 8, 66553–66563. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, X. Physics-Guided Spoof Trace Disentanglement for Generic Face Anti-Spoofing. arXiv 2020, 14, 1–16. Available online: https://arxiv.org/abs/2012.05185 (accessed on 12 November 2022).
- Jia, Y.; Zhang, J.; Shan, S.; Chen, X. Single-Side Domain Generalization for Face Anti-Spoofing. In Proceedings of the IEEE Computer Society Conference on Computer Vision and Pattern Recognition, Washington, DC, USA, 16–18 June 2020; pp. 8481–8490. [Google Scholar] [CrossRef]
- Saha, S.; Xu, W.; Kanakis, M.; Georgoulis, S.; Chen, Y.; Paudel, D.P.; Van Gool, L. Domain Agnostic Feature Learning for Image and Video Based Face Anti-spoofing. IEEE Comput. Soc. Conf. Comput. Vis. Pattern Recognit. Workshops 2020, 2020, 3490–3499. [Google Scholar] [CrossRef]
- Tu, X.; Ma, Z.; Zhao, J.; Du, G.; Xie, M.; Feng, J. Learning Generalizable and Identity-Discriminative Representations for Face Anti-Spoofing. ACM Trans. Intell. Syst. Technol. 2020, 11, 5. [Google Scholar] [CrossRef]
- Deb, D.; Jain, A.K. Look Locally Infer Globally: A Generalizable Face Anti-Spoofing Approach. IEEE Trans. Inf. Forensics Secur. 2021, 16, 1143–1157. [Google Scholar] [CrossRef]
- Kotwal, K.; Bhattacharjee, S.; Abbet, P.; Mostaani, Z.; Wei, H.; Wenkang, X.; Yaxi, Z.; Marcel, S. Domain-Specific Adaptation of CNN for Detecting Face Presentation Attacks in NIR. IEEE Trans. Biom. Behav. Identit Sci. 2022, 4, 135–147. [Google Scholar] [CrossRef]
- Perez-Cabo, D.; Jimenez-Cabello, D.; Costa-Pazo, A.; Lopez-Sastre, R.J. Deep Anomaly Detection for Generalized Face Anti-Spoofing. IEEE Comput. Soc. Conf. Comput. Vis. Pattern Recognition. Work. 2019, 1591–1600. [Google Scholar] [CrossRef]
- Li, Z.; Li, H.; Lam, K.-Y.; Kot, A.C. Unseen Face Presentation Attack Detection with Hypersphere Loss. In Proceedings of the ICASSP, IEEE International Conference on Acoustics, Speech and Signal Processing, Barcelona, Spain, 4–8 May 2020; Volume 2020, pp. 2852–2856. [Google Scholar] [CrossRef]
- Koshy, R.; Mahmood, A. Enhanced Deep Learning Architectures for Face Liveness Detection for Static and Video Sequences. Entropy 2020, 22, 1186. [Google Scholar] [CrossRef]
- Fatemifar, S.; Arashloo, S.R.; Awais, M.; Kittler, J. Client-specific anomaly detection for face presentation attack detection. Pattern Recognit. 2021, 112, 107696. [Google Scholar] [CrossRef]
- Nikisins, O.; Mohammadi, A.; Anjos, A.; Marcel, S. On Effectiveness of Anomaly Detection Approaches against Unseen Presentation Attacks in Face Anti-spoofing. In Proceedings of the 2018 International Conference on Biometrics, ICB, Gold Coast, Australia, 20–23 February 2018; pp. 75–81. [Google Scholar] [CrossRef]
- Baweja, Y.; Oza, P.; Perera, P.; Patel, V.M. Anomaly Detection-Based Unknown Face Presentation Attack Detection. In Proceedings of the IJCB 2020—IEEE/IAPR International Joint Conference on Biometrics, Houston, TX, USA, 28 September–1 October 2020. [Google Scholar] [CrossRef]
- Shao, R.; Perera, P.; Yuen, P.C.; Patel, V.M. Federated Generalized Face Presentation Attack Detection. Comput. Vis. Pattern Recognit. 2021, 14, 1–13. Available online: https://arxiv.org/abs/2104.06595 (accessed on 22 November 2022). [CrossRef]
- Nguyen, D.T.; Pham, T.D.; Batchuluun, G.; Noh, K.J.; Park, K.R. Presentation Attack Face Image Generation Based on a Deep Generative Adversarial Network. Sensors 2020, 20, 1810. [Google Scholar] [CrossRef] [PubMed]
- Liu, A.; Tan, Z.; Wan, J.; Liang, Y.; Lei, Z.; Guo, G.; Li, S.Z. Face Anti-Spoofing via Adversarial Cross-Modality Translation. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2759–2772. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, J.; Bian, Y.; Cai, Y.; Wang, C.; Pu, S. Self-Domain Adaptation for Face Anti-Spoofing. Proc. Conf. AAAI Artif. Intell. 2021, 35, 2746–2754. [Google Scholar] [CrossRef]
- Jia, Y.; Zhang, J.; Shan, S. Dual-Branch Meta-Learning Network with Distribution Alignment for Face Anti-Spoofing. IEEE Trans. Inf. Forensics Secur. 2022, 17, 138–151. [Google Scholar] [CrossRef]
- Cai, R.; Li, Z.; Wan, R.; Li, H.; Hu, Y.; Kot, A.C. Learning Meta Pattern for Face Anti-Spoofing. IEEE Trans. Inf. Forensics Secur. 2022, 17, 1201–1213. [Google Scholar] [CrossRef]
- Perez-Cabo, D.; Jimenez-Cabello, D.; Costa-Pazo, A.; Lopez-Sastre, R.J. Learning to Learn Face-PAD: A lifelong learning approach. In Proceedings of the 2020 IEEE International Joint Conference on Biometrics (IJCB), Houston, TX, USA, 28 September–1 October 2020; pp. 1–9. [Google Scholar] [CrossRef]




| Application Domain | Usage |
|---|---|
| Security and Law enforcement | Identify and track criminals, and accelerate investigations [5] |
| Banking and Retail | Customer verifications through eKYC, used in the authentication of banking applications, Cardless ATM Transactions, online account creations, and digital payments such as apple pay [7,8] |
| Health Sector | Detecting genetic disease, tracking patient’s effect of medications, and Health insurance records management [9] |
| Immigration and border checks | Face recognition for identity checks is implemented at various airports in European countries [10] |
| Education | Campus Security, attendance monitoring, and increasing learning engagement [11] |
| Mobile Devices | FaceID in smartphones such as Apple, Samsung, Motorola, and OnePlus [12] |
| Ref. | Objectives and Topics | Observation and Limitations | Type |
|---|---|---|---|
| [28] 2017 | It includes state-of-the-art methods for face presentation attack detection and respective labs in the domain. It also describes challenges and competitions in the same domain. | Not following the PRISMA approach, the focus is on challenges and competitions from 2011 to 2017. | Review |
| [27] 2019 | It discusses a systematic review using the PRISMA approach. It focuses on liveness indications, particularly as a guide for determining the best solution for various spoofing issues. | In a review of research articles published between 2014–2017, the number of research articles studied is only 65, and a detailed analysis of available databases was explored. The focus is only on liveness indicator clues & lack of new trends in the research area since 2017. | Systematic Literature Review |
| [24] 2020 | It discusses the typology of presentation attacks and detection methods in various databases available for 2D and 3D attacks. Challenges, evolutions, and current trends face PAD and provide new perspectives on future research. | Not followed PRISMA approach, more focus on RGB-based methods, sensor-based PAD methods not explored in detail; more advanced research directions need to explore | Review |
| [25] 2020 | It discusses the texture, motion, multi-fusion-based face anti-spoofing methods, and available 2D attack databases. It also describes various face anti-spoofing techniques, including CNN, texture feature descriptors, and motion-based techniques. | Not followed PRISMA approach, for discussion, only last four years 2015–2019, The focus is only on deep learning-based solutions. Databases not extensively reviewed. Future directions are not discussed. | Review |
| [26] 2020 | It includes explicit feature extraction approaches based on image texture, image quality, computer interaction, depth analysis, deep learning feature extraction, transfer learning, feature integration, and domain generalization. | Few research articles were used in the study, lack of discussion of available databases for PAD, and very few future directions were explored. | Review |
| [36] 2021 | It discusses the international competitions conducted on unimodal and multi-model face presentation attack detection. | It includes the latest five competitions from 2019 to 2021, Not following the PRISMA approach. | Review |
| [30] 2021 | It includes advanced deep learning and multi-modal fusion-based methods for FPAD; an in-depth technical review is conducted, including recent deep learning approaches, datasets, and evaluation metrics. | Not following the PRISMA approach, it focuses on in-depth deep learning and a multi-modal approach, including research articles up to 2021. | Review |
| [31] 2021 | It includes deep learning methods and datasets used for the face anti-spoofing problem. It also discusses techniques for sensor-based approaches. | The PRISMA approach needs to be followed; more focus is given to deep learning methods, and advanced research directions need to be explored. | Review |
| Number | Research Questions | Motivations | Answered in Section |
|---|---|---|---|
| RQ1 | What is the distribution of published papers related to face liveness detection methods by year, publication, and publication type? | It aids in determining when, where, and who conducted the research studies. | Section 3, Section 3.1 |
| RQ2 | What are the various attacks against a facial recognition system? | It aids in exploring the different types of attacks performed on face recognition systems. | Section 3, Section 3.2 |
| RQ3 | What are the different datasets available for different types of presentation attacks? | It assists in locating a dataset with appropriate training and testing data for good research outcomes. | Section 3, Section 3.3 |
| RQ4 | What are the main methods related to artificial intelligence for face presentation attack detection? And what are the evaluation metrics used in Face liveness detection? | It aids in identifying appropriate artificial intelligence approaches for today’s facial biometric applications. It helps to select the appropriate evaluation metrics for performance measures. | Section 4, Section 5 |
| RQ5 | What are the main challenges and problems faced by existing face anti-spoofing techniques? | It aids in exploring the fundamental issues that occur when studying face presentation attacks and the benefits and limitations of current solutions. | Section 6, Section 6.1, Section 6.2, Section 7 |
| RQ6 | What are future directions for a robust and reliable face liveness detection system? | It aids in finding important research avenues that have yet to explore | Section 7 |
| Fundamental Keyword | “Face Anti-Spoofing” |
|---|---|
| “Face Anti-spoofing” | “Face Liveness detection,” “Face Presentation Attacks,” “Artificial Intelligence,” and “Domain Adaptation.” |
| Secondary Keywords | “Machine Learning,” “Deep Learning,” “Domain Generalization,” Reinforcement Learning, “Face Biometric spoofing.” |
| Database | Query | # Initial Result |
|---|---|---|
| Scopus | ((machine learning) OR (Deep Learning) (Artificial Intelligence) OR (Domain Adaptation) OR (Domain Generalization) OR (Reinforcement Learning)) AND ((Face Anti Spoofing) OR (Face Presentation Attacks) OR (Face Liveness Detection) OR (Face Biometric Spoofing)) | 283 |
| Web of Science (WoS) | 188 |
| Inclusion Criteria |
| Articles should be original research articles instead of review/survey articles. |
| Research articles that were released between 2011 to 22. |
| Research papers/articles should include search keywords in the title, abstract, or full text of research articles. |
| Research articles that answer at least one research question. |
| The developed solution should aim at resolving issues with Face presentation attack detection. |
| Exclusion Criteria |
| Articles that are written in languages other than English |
| Duplicate research articles |
| Research articles with the unavailability of full text |
| Research articles that are not relevant to face liveness detection, face presentation attacks, face anti-spoofing |
| Dataset | Year | # Subjects | # Samples (Real/Fake) | Resolution | Type of Attack & Mode (Static or Dynamic) (2D or 3D) | Created by | Used in Literature |
|---|---|---|---|---|---|---|---|
| NUAA [43] | 2008 | 15 | 5105/ 7509 | 640 × 840 | Photo Attack (2D static) | Nanjing University of Aeronautics and Astronautics. | [44,45,46,47,48,49,50,51,52] |
| Replay-Attack [40] | 2011–2012 | 50 | 300/ 1000 | 320 × 240 | Photo Attack (2D Static)/Video Replay Attack (2D dynamic) | IDIAP Research Institute | [53,54,55,56,57,58,59,60,61,62,63,64] |
| CASIA-FASD [56] | 2012 | 50 | 150/450 | 640 × 480 1280 × 720 1920 × 1050 | Photo Attack (cut, printed, wrapped)-2D Static/Video Replay Attack (Dynamic) | IDIAP Research Institute | [64,65,66,67,68] |
| Morpho | 2013 | 20 | 406 | - | 2D + 3D Mask attacks | MORPHO | [69] |
| 3DMAD [42] | 2013 | 17 | 255 (170/ 85) | 640 × 480 | 3D mask paper attack | Idiap Research Institute | [70,71,72,73] |
| MSU-MFSD [74] | 2015 | 35 | 110/ 330 | 1920 × 1080 | Printed Photo attacks (2D Static), 2 × Video attacks (Dynamic) | Michigan State University | [60,75,76,77,78,79,80,81] |
| MSU-USSA [82] | 2016 | 1140 | 1140/9120 v | 1920 × 1080 | Printed photos, photos display (Static), 3× video replays (Dynamic) | Michigan State University | [57,83] |
| 3DFS-DB [83] | 2016 | 26 | 520 v | 640 × 480 | 3D mask attacks | Institute for the Protection and Security of the Citizen | [76,81] |
| BRSU [84] | 2016 | 137 | 141 | - | Multispectral SWIR 2D/3D attacks | Bonn-Rhein-Sieg University of Applied Sciences | [85,86] |
| HKBU-MAR [87] | 2016 | 12 | 1008 v (504/ 504) | 1280 × 720, 800 × 600 | 3D Mask attacks | University of OULU | [88,89] |
| OULU-NPU [39] | 2017 | 55 | 990/ 3960 v | Different Resolutions | Photo Attack/Video Replay Attack (2D) | OULU University | [90] |
| SMAD [91] | 2017 | Online | 130 (65/65)v | - | Silicon Mask attack | IIT Jodhpur | [73,92,93] |
| MLFP [41] | 2017 | 10 | 1350 (150/ 1200) | Different resolution | 3D late× Masks attacks, 2D Paper print Mask Attack | IIIT Delhi | [68] |
| ERPA [94] | 2017 | 5 | 86 | - | Silicone masks | Idiap Research Institute | [69] |
| SiW [95] | 2018 | 165 | 1320/3300 v | 1920 × 1080 | Printed Paper (High/Low Quality) (2D) | Michigan State University | [71] |
| ROSE-YOUTU [73] | 2018 | 20 | 3350 | 640 × 480 1280 × 720 | printed paper attack, video replay attack, paper masking attack, cropped mask, full mask, and upper mask | Tencent Corporation and the NTU ROSE Lab | [74] |
| CASIA-SURF [96] | 2019 | 1000 | 3000/18,000 v | Real Sense RGB Cam 1280 × 720 | Flat-cut/Wrapped-cut Photos (Eyes, Nose, Mouth) (2DStatic) | Institute of Automation, Chinese Academy of Sciences (CASIA) | [76,77,80] |
| WMCA [78] | 2019 | 72 | 1679(347/ 1332) | 1920 × 1080 1260 × 720 320 × 240 | 2D, 3D attacks 2D prints, video and photo replays, mannequin heads, paper, silicone, and rigid masks | Idiap Research Institute | [79,97] |
| CASIA-SURF CeFA [98] | 2020 | 1607 (3 Different Ethnicity) | 1800/5400 v | 299 × 299 | Print attack, Replay Attack, 3D print, IR, Infrared, 2D & 3D attack Subsets | Institute of Automation, Chinese Academy of Sciences (CASIA) | [82] |
| CASIA-SURF 3DMASK [99] | 2020 | 48 | 1152 (288/ 864) v | 30 fps and 1080 p resolution | 3Dmask attacks | Institute of Automation, Chinese Academy of Sciences (CASIA) | [83] |
| HiFi Mask [100] | 2021 | 75 | 54,600 v | - | 3D Mask attacks | Institute of Automation, Chinese Academy of Sciences (CASIA) | [84] |
| VFPAD [101] | 2022 | 24 male and 16 female with different ethnicity’s | 5836 v (4046/1790) | - | photo prints, replay attack, rigid 3D, silicon 3D mask attacks | Idiap Research Institute | [101] |
| Feature Extracted | Methodology Used | Attacks Identified |
|---|---|---|
| Static Texture Based | Texture Feature extraction from Input Image Frequency Texture: 2D FFT Spatial Textures: DoG [111]
| Photo Attack, Video Replay Attack, 3D mask Attack of Low Quality |
| Dynamic Texture-Based | ||
| Non-Invasive Motion-based Feature Extraction methods | Static Photo Attacks Photo & 3D mask attack, Low-quality Video Replay Attack | |
| Invasive Motion-based Feature Extraction methods |
| |
| rPPG Motion-based Feature Extraction methods | ||
| 3D Shape-Based (Depth-based) | Reconstructing Sparse 3D Face [117] | Planner Photo Attack |
| Pseudo Depth Map | CNN Based, NAS Based [109], 3D cloud point network [126] | Video Replay Attack |
| Ref. and Year | Methodology | Domain Adaptation(DA)/Domain Generalization (DG) | Datasets Used | Performance Metrics and Model Performances | Intra- Database Testing | Cross-Database Testing |
|---|---|---|---|---|---|---|
| [58] 2015 | Person-Specific Domain Adaptation | DA | CASIA Dataset, Replay- Attack | Half Total Error Rate (HTER):1.40% (in case of Replay-attack dataset), 10.54% (in case of CASIA Dataset) | Y | N |
| [97] 2018 | Unsupervised Domain Adaptation framework | DA | Own Dataset-Rose- Youtu liveness database | Half Total Error Rate—27.70% | Y | Y |
| [131] 2018 | generalized deep feature representation for spatial and temporal information using 3D CNN | DG | Idiap Replay-Attack, CASIA Face Anti Spoofing, MSU mobile face spoofing database | Half Total error rate (HTER): 24.70% | Y | Y |
| [78] 2019 | Adversarial Domain Adaptation | DA | MSU-MFSD, Replay- Attack, CASIA FASD | Half Total Error Rate—20.30%, Equal Error Rate—3.20% | Y | Y |
| [132] 2019 | Maximum Mean Discrepancy (MMD) to multi-layer network distribution adaptation | DA | Replay-Attack, CASIA FASD (CBSR) | Half Total Error Rate: 0.6% (Intra-tests), HTER 34.30% (Inter-tests), Equal Error Rate:0.30%, (Intra-tests) | Y | Y |
| [76] 2019 | a multi-adversarial deep domain generalization performed under a dual-force triplet-mining constraint. | DG | CASIA-MFSD, Idiap Replay-Attack, MSU-MFSD, and Oulu-NPU datasets | Half Total Error Rate (HTER): 27.98% and Area Under Curve (AUC): 80.02% | N | Y |
| [133] 2020 | (OCA-FAS) one-class adaptation face anti-spoofing | DA | OULU-NPU | Average classification error rate(ACER): 1.69% | N | Y |
| [134] 2020 | (FCN-DA-LSA) Fully Convolutional Network with Domain Adaptation and Lossless Size Adaptation | DA | CASIA-FASD, Replay-Attack dataset, and OULU-NPU dataset | Half Total Error Rate: 21.83% | N | Y |
| [135] 2020 | One class domain adaptation using domain-guided pruning of CNN | DA | OULU-NPU, Replay-Mobile, SWAN, WMCA, and IJB-C. | AUC, ROC, APCER | Y | Y |
| [136] 2020 | single-side domain generalization framework (SSDG) | DG | OULUNPU, CASIA- FASD, Idiap Replay- Attack, and MSU-MFSD | Half Total Error Rate (HTER):7.38% and Area Under Curve (AUC): 97.17% | Y | Y |
| [137] 2020 | Domain-agnostic feature learning | DG | Oulu-NPU, CASIA- MFSD, Idiap Replay- Attack, MSU-MFSD | Half Total Error Rate (HTER): 14.00% and ACER: 8.05% | N | Y |
| [138] 2020 | Total Pairwise Confusion (TPC)loss and Fast Domain Adaptation (FDA) | DG | CASIA-FASD, Replay-Attack, MSU-MFSD, Oulu-NPU, SiW | HTER:26.30% | Y | Y |
| [122] 2021 | (DR-UDA)Unsupervised adversarial domain adaptation with disentangled representation | DA | Idiap Replay-Attack, CASIA Face Anti Spoofing, MSU-MFSD, ROSEYoutu, and Oulu-NPU use the RGB modality of the CASIA- SURF | Half Total Error Rate (HTER): 28.70%, Equal Error Rate (EER): 3.20% | Y | Y |
| [139] 2021 | (SSR-FCN) Self-Supervised Regional Fully Convolutional Network | DG | Spoof-in-the-Wild with Multiple Attacks (SiW- M), Oulu-NPU, CASIA-FASD & Replay-Attack | Average Classification error rate (ACER): 2.80%, Half Total Error Rate (HTER): 19.90% | N | Y |
| [53] 2021 | Camera Invariant Feature Learning for Generalized Face Anti-Spoofing | DG | CASIA-FASD, Replay-Attack Oulu-NPU, and MSU-MFSD | Equal Error Rate (EER): 0.89%, HTER: 17.60% for cross-dataset evaluation | Y | Y |
| [129] 2022 | A self-supervised approach using temporal sequence sampling | DG | CASIA-FASD, Replay-Attack, OULU-NPU, and MSU-MFSD | HTER: 5.90% (in a cross-dataset test for the Replay attack dataset) and 15.90% (in cross-dataset testing for CASIA-FASD), ACER: 0.10% (in an Intra-dataset test for OULU-NPU) | Y | Y |
| [140] 2022 | Domain Specific adaptation with CNN using Near Infrared | DA | in-Vehicle Face Presentation Attack Dataset | APCER—0.92%, BPCER—0.91%, ACER—0.91% | Y | Y |
| Ref. and Year | Method for Anomaly Detection | Dataset Used | Performance Metrics and Model Performance | Intra- Database Testing | Cross-Database Testing |
|---|---|---|---|---|---|
| [141] 2018 | A GMM anomaly detector and aggregated database | Aggregated database of 3 datasets Replay- Attack, Replay-Mobile, and MSU MFSD | HTER: 11.90% | Y | Y |
| [140] 2019 | a deep metric learning model | GPAD is the world’s largest aggregated dataset, combining more than ten datasets into two levels of classification to reflect four fundamental components of anti-spoofing: attacks, lightning, capturing gadgets, and resolving | Attack Presentation Classification Error Rate (APCER): 14.28%, Bonafide presentation Classification Error Rate (BPCER): 5.99%, and Aver- age Classification Error Rate (ACER): 10.14%., Half Total Error (HTER): 5.41% | Y | Y |
| [142] 2020 | A hypersphere loss function | CASIA-FASD, Replay- Attack and MSU-MFSD databases, SiW-M database | ACER: 15.80% and EER: 15.20%, Area under the curve (AUC): 96.20% | Y | N |
| [143] 2020 | HOG-based face detection VGG Face base feature extraction, Pseudo negative sampling | Replay-Attack, Rose-You, OULU-NPU, and Spoof in Wild | Average Classification Error Rate (ACER):20.74%, Attack Presentation Classification Error Rate (APCER): 25.04%, Bona-fide Presentation Classification Error Rate (BPCER): 16.53% | Y | Y |
| [109] 2021 | multiple kernel fusion for anomaly detection in unseen presentations | Replay- Mobile, Replay attack, OULU-NPU, MSU-MFSD | ACER: 5.58%, AUC:100%, EER: 0.00%, HTER: 0.00% | Y | Y |
| [144] 2021 | client-specific one-class adaptation-based anomaly detection | Replay attack, Replay Mobile, ROSE-YOUTU | HTER: 8.13% | Y | Y |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khairnar, S.; Gite, S.; Kotecha, K.; Thepade, S.D. Face Liveness Detection Using Artificial Intelligence Techniques: A Systematic Literature Review and Future Directions. Big Data Cogn. Comput. 2023, 7, 37. https://doi.org/10.3390/bdcc7010037
Khairnar S, Gite S, Kotecha K, Thepade SD. Face Liveness Detection Using Artificial Intelligence Techniques: A Systematic Literature Review and Future Directions. Big Data and Cognitive Computing. 2023; 7(1):37. https://doi.org/10.3390/bdcc7010037
Chicago/Turabian StyleKhairnar, Smita, Shilpa Gite, Ketan Kotecha, and Sudeep D. Thepade. 2023. "Face Liveness Detection Using Artificial Intelligence Techniques: A Systematic Literature Review and Future Directions" Big Data and Cognitive Computing 7, no. 1: 37. https://doi.org/10.3390/bdcc7010037
APA StyleKhairnar, S., Gite, S., Kotecha, K., & Thepade, S. D. (2023). Face Liveness Detection Using Artificial Intelligence Techniques: A Systematic Literature Review and Future Directions. Big Data and Cognitive Computing, 7(1), 37. https://doi.org/10.3390/bdcc7010037







