1. Introduction
Drones, or UAVs, have transformed numerous industries, including transportation, industrial inspections, disaster recovery, security, and agriculture, by leveraging IoD technology [
1]. UAVs are crucial in package delivery, surveillance, and military operations [
2]. However, the increasing reliance on UAVs for critical tasks exposes them to malicious attacks that threaten their confidentiality, integrity, and availability (CIA). Notably, cyberattacks targeting drones include GPS spoofing, malware, unauthorized manipulations, and skyjacking. Among these, DoS attacks pose a significant challenge by compromising the availability of drone services through network overload [
3]. Such attacks aim to saturate communication bandwidth, rendering drones incapable of normal operation and inaccessible to legitimate users, severely degrading service quality and jeopardizing public safety.
The IoD environment further complicates security with vulnerabilities related to risks such as data interception, unauthorized access, and privacy infringements [
4]. Consequently, there are pressing security concerns associated with UAV operations in Software-Defined Networking (SDN) frameworks, where traditional security measures may be inadequate [
5]. Current countermeasures against DoS attacks exhibit limitations, such as high latency, inadequate real-time adaptation, and poor scalability. Furthermore, existing solutions often lack effective response mechanisms to mitigate risks during an attack. To enhance the performance of IDS and bolster the security, reliability, and integrity of UAV operations in critical applications, significant improvements are necessary [
6].
Machine learning and deep learning algorithms are increasingly integrated into UAV systems for threat detection and prediction [
7]. Several applications harness the synergy between drones and AI techniques [
8,
9]. However, successful implementation relies on adequate datasets that accurately represent real-world scenarios [
9]. This paper proposes a novel intrusion detection system utilizing machine learning to detect and mitigate DoS attacks, extending our previous review [
10]. Recent research has also highlighted the efficacy of various machine learning models in identifying DDoS attacks within UAV communication systems, with Random Forest demonstrating superior classification performance [
11]. Its ensemble learning capabilities make it particularly suitable for deployment in UAV network security applications, especially given its ability to differentiate effectively between normal and attack instances. While other models, such as XGBoost and Gradient Boosting, showed competitive results, their limitations in recall contributed to higher false negative rates. In contrast, SVM and logistic regression struggled with complex decision boundaries, resulting in lower prediction accuracy.
DoS attacks represent one of the most critical threats, potentially disrupting service availability and compromising essential functions. Cyberattacks targeting contemporary ICT systems like the IoD are increasingly prevalent, with evidence highlighting the risks and repercussions of such incidents. The impact of these attacks can range from integrity issues to significant challenges concerning availability and confidentiality [
12]. Therefore, it is crucial to design and implement systems that meet stringent security criteria, including identifying active threats as key countermeasures. IDSs are recognized as effective tools for the prompt detection of these attacks [
13]. Despite ongoing advancements, existing IDS solutions for IoD face challenges such as high false positive rates, resource constraints on drones, poor adaptation to evolving attack patterns, and a lack of standardized datasets for evaluation [
14]. Comprehensive analyses synthesizing available research are also scarce. Previous studies have reviewed the state-of-the-art in IDS for IoT, emphasizing machine learning model effectiveness and prevailing challenges and future research directions [
15].
The motivation for this paper is driven by the insufficient detection and mitigation techniques for DoS attacks targeting UAVs, the significant impact of such attacks on operational capabilities, and associated public safety concerns. This paper’s aim is to contribute significantly to the security and reliability of UAV deployments in critical sectors through our proposed solution.
In summary, the paper is structured as follows:
Section 2 provides a literature review of related works.
Section 3 details the methodology and proposed system design;
Section 4 showcases system interfaces;
Section 5 discusses implementation details;
Section 6 presents experimental results; and
Section 7 addresses professional, ethical, legal, and social implications. Finally,
Section 8 concludes the paper and outlines future directions.
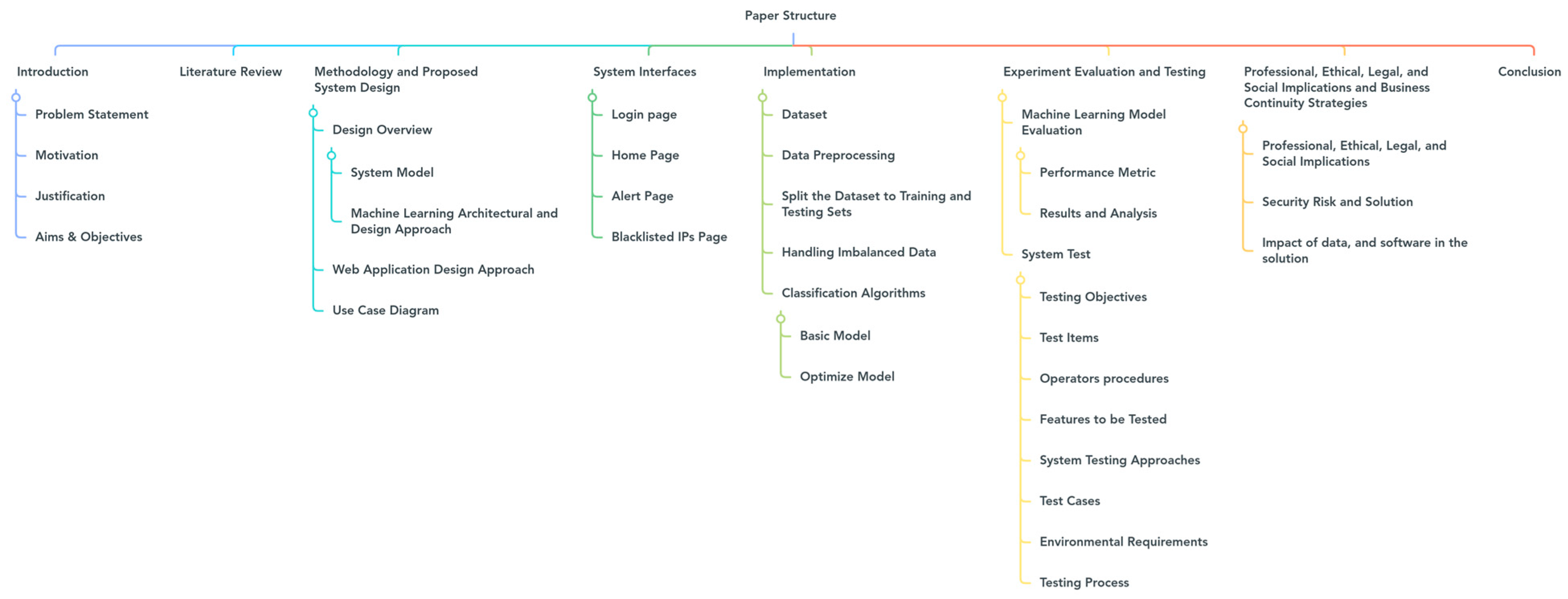
Figure 1 illustrates the paper organization for each section.
2. Literature Review
This section presents a review of related works identified using the PRISMA method. We searched the Scopus database with the following query: (“detect” AND (“Denial of Service” OR “DoS”) AND (“Internet of Drones” OR “IoD”) AND (“machine learning” OR “ML”). Papers classified as reviews, conference proceedings, or book chapters were excluded, resulting in a total of nine studies for analysis.
One study utilizing the UNSW-NB15 intrusion detection dataset serves as the foundation for training and testing models. It employs two feature selection techniques: singular value decomposition (SVD) and principal component analysis (PCA). The study classifies the modified feature space using various methods, including convolutional neural networks (CNNs), stochastic gradient descent, and ridge regression (RR). Its ability to manage both binary and multiclass classification contributes to its popularity. The results indicate that PCA and SVD significantly enhance the accuracy of classification frameworks, leading to superior performance in intrusion detection systems (IDSs). Notably, the accuracy of the Ridge Regression classifier improved from 98.13% to an exceptional level in binary classification tasks [
10].
Another study proposes a cybersecurity architecture for the Internet of Things (IoT) drones. This system employs a voting ensemble of machine learning algorithms, analyzing data from multiple sources, including network information, drones, and sensors, to identify security patterns and detect attacks. Architecture integrates advanced technologies such as machine learning, artificial intelligence, data fusion, and anomaly detection, creating a robust and adaptable security solution. By leveraging sophisticated algorithms, the framework can recognize both known and unexpected threats, facilitating timely responses and mitigation strategies. When tested on a drone dataset, the framework achieved an impressive accuracy rate of 99.89% in real-time cyberattack detection, outperforming previous methods. A dynamically created merged dataset was utilized to evaluate the framework’s performance in terms of accuracy, recall, precision, and F1-score, demonstrating the effectiveness of the RegressionNet model in accurately detecting various types of attacks [
11].
A different approach focuses on IoT-based UAV networks, employing machine learning approaches to identify anomalous activity. This research introduces a novel method for leveraging machine learning within flying ad hoc networks (FANETs), which consist of collaborating UAVs, orbiting satellites, and ground-based stations. In this architecture, UAVs collect data, while IoT sensor nodes are deployed on the ground. The cognitive lightweight-LR strategy used in this study effectively balances high accuracy with a reduced rate of false alarms. Performance evaluation is conducted using the UNSW-NB15 dataset, demonstrating the method’s effectiveness in detecting anomalies within the network [
16].
Security remains a critical issue across various fields of study today. One approach to identifying potential online attacks is through a FANET-based intrusion detection system (IDS) [
2]. A novel algorithm, CSODAE-ID, has been developed and validated for intrusion detection within the Internet of Drones (IoD) environment. Initially, the CSODAE-ID approach preprocesses the data, followed by feature selection using the MDHO-FS method. Intrusions in the IoD domain are then classified using an autoencoder (AE) technique, and hyperparameter tuning is performed with the Crystal Structure Optimization (CSO) algorithm, inspired by crystal lattice formations. The model’s performance is evaluated through extensive simulations, demonstrating a high accuracy of 99.12% and showing that the CSODAE-ID model outperforms contemporary methods.
Fog computing emerges as an innovative solution to enhance networking, computing, and storage capabilities in the Internet of Vehicles (IoVs). However, significant privacy and security risks pose challenges for smart cities. These risks, particularly during information sharing among mobile nodes, create barriers for fog-assisted IoVs (Fa-IoVs). Addressing these security anomalies is essential for the effective network interactions of Fa-IoVs. Ensuring smooth communication in this context reduces the likelihood of data loss, latency, and communication overhead. This study aims to identify research gaps within the Fa-IoVs network and introduces CAaDet (convolutional autoencoder-aided anomaly detection), a dynamic deep learning-based approach to enhance security [
3].
Furthermore, another study proposes a novel hybrid detection system for intrusions that utilizes machine learning techniques to manage uneven network traffic data [
6]. The algorithms employed include XGBoost, Mini-VGGNet, long short-term memory (LSTM), and AlexNet. The importance of various features for enhancing detection accuracy and interpretability is assessed using the Random Forest Regressor. To ensure the effectiveness of the intrusion detection system (IDS), it is crucial to address the inherent class imbalance present in network data. The proposed method incorporates a combination of undersampling techniques for majority classes and oversampling methods for minority classes during data preparation. This balanced representation of network traffic data enables the IDS to better identify rare or unique intrusions, reducing bias toward the majority class. Feature extraction with the Random Forest Regressor serves dual purposes. It identifies particularly relevant characteristics in system traffic data that are essential for intrusion detection. Additionally, it allows the model to prioritize and focus on these key features during training, thereby enhancing detection accuracy while minimizing computational complexity.
In addition, another method is proposed: a deep learning-based hybrid approach utilizing generative adversarial networks (GANs) to identify malicious intruders [
17]. This method features a distributed IDS controller that has been evaluated on the NSL-KDD dataset, demonstrating enhanced effectiveness in detecting Distributed Denial-of-Service (DDoS) attacks. To detect these attacks, experimental results are calculated using predetermined threshold values. The findings indicate that the HD-GAN model achieves superior intrusion detection, characterized by higher precision, recall, reliability, and F-measure, along with a lower false-positive rate (FPR).
Moreover, a study proposes an intrusion detection system (IDS) that employs a group classifier in conjunction with Tuna Swarm Optimization (TSO) to fine-tune hyperparameters and enhance detection accuracy for attacks within an Internet of Things (IoT) context [
18]. The publicly available message queue telemetry transport (MQTT) network dataset is utilized to categorize the data into several groups: SlowLoris, malformed, brute force, flood, DoS, and valid. Before balancing the data using the synthetic minority oversampling technique (SMOTE) and conducting feature extraction with recursive feature elimination (RFE), the dataset is initially preprocessed to eliminate potential outliers. Lastly, the optimized parameters obtained through TSO, combined with the ensemble classifier, significantly enhance the detection of IoT attacks, achieving a classification accuracy of 99.12%. Additionally, a study presents a technique utilizing the reinforcement learning-based gradient monitored (RLGM) mechanism to identify jamming attacks [
19]. The RLGM approach preserves safe zones and reduces gradient variance, thereby improving the accuracy of the learning objective. Moreover, RLGM selects the precise set of parameters required by the network during the training phase, facilitating rapid training progress. By employing automatically adjusted weights, RLGM generates the foundational deep network structure through spontaneous derivation during training. Our proposed strategy outperforms traditional non-machine learning approaches, such as GA-AOMDV, as well as other reinforcement learning methods, including Federated RL and Deep Q-Learning (DQL).
In 2025, researchers are exploring AI-driven safety and security measures for UAVs, ranging from machine learning to large language models [
20]. Furthermore, a hybrid detection system integrating machine learning algorithms such as XGBoost and LSTM is proposed to manage uneven network traffic data. This system addresses class imbalance through undersampling and oversampling techniques, enhancing the detection of rare intrusions [
21]. Another study explored machine learning techniques to detect DoS attacks in IoD environments, reviewing various machine learning algorithms, and highlighting their strengths and limitations in securing UAV networks [
22]. Another study in 2024 proposes a cybersecurity architecture leveraging machine learning and IoT technologies within the IoD framework, using IoT-enabled sensors to collect and analyze data [
23]. Also in 2025, a study introduces a risk-sensitive PPO algorithm and proposes a training framework incorporating multi-head to address challenges in reinforcement learning-based missile evasion algorithms [
24,
25]. These recent advancements highlight the ongoing efforts to develop robust and efficient security solutions for the evolving landscape of UAV networks.
Recent research continues to emphasize the importance of machine learning in enhancing UAV security. For example, a study from 2024 proposes an autoencoder-based machine learning intrusion detection method for UAV communications, relying on an autoencoder neural network to extract important features from original data, which are then fed to machine learning models for classifying attack types [
26]. Another study in 2025 employs traditional ML-based algorithms for detecting DDoS attacks and botnet activity in UAV networks [
27]. Furthermore, the cross-layer convolutional attention network (CLCAN) has been introduced as a novel IDS architecture for IoD networks, demonstrating high accuracy (98.4%), recall (98.7%), and F1-score (98.1%) in detecting complex cyber threats [
28]. These recent advancements highlight the ongoing efforts to develop robust and efficient security solutions for the evolving landscape of UAV networks.
Table 1 summarizes the related works on IDS in IoD.
Based on the bibliometric analysis of publication years and the co-occurrence of authors’ keywords, as illustrated in
Figure 2, all selected studies were conducted in 2022 or later. Over the past year, topics related to security within the Internet of Drones (IoD) have gained significant traction. This trend underscores the importance and novelty of this area of research.
3. Methodology and Proposed System Design
3.1. Design Overview
The ML-based IDS should emphasize a user-friendly design. To ensure a positive user experience, the system must be cohesive and easy to navigate. It is essential to develop architecture and components that seamlessly integrate and fulfill all requirements outlined in the Software Requirements Specification (SRS). Furthermore, the system should meet user expectations by providing accurate results and efficient services. By achieving these goals, network administrators will be more inclined to utilize the system whenever necessary, contributing to a secure Internet of Drones (IoD) environment.
3.2. System Model
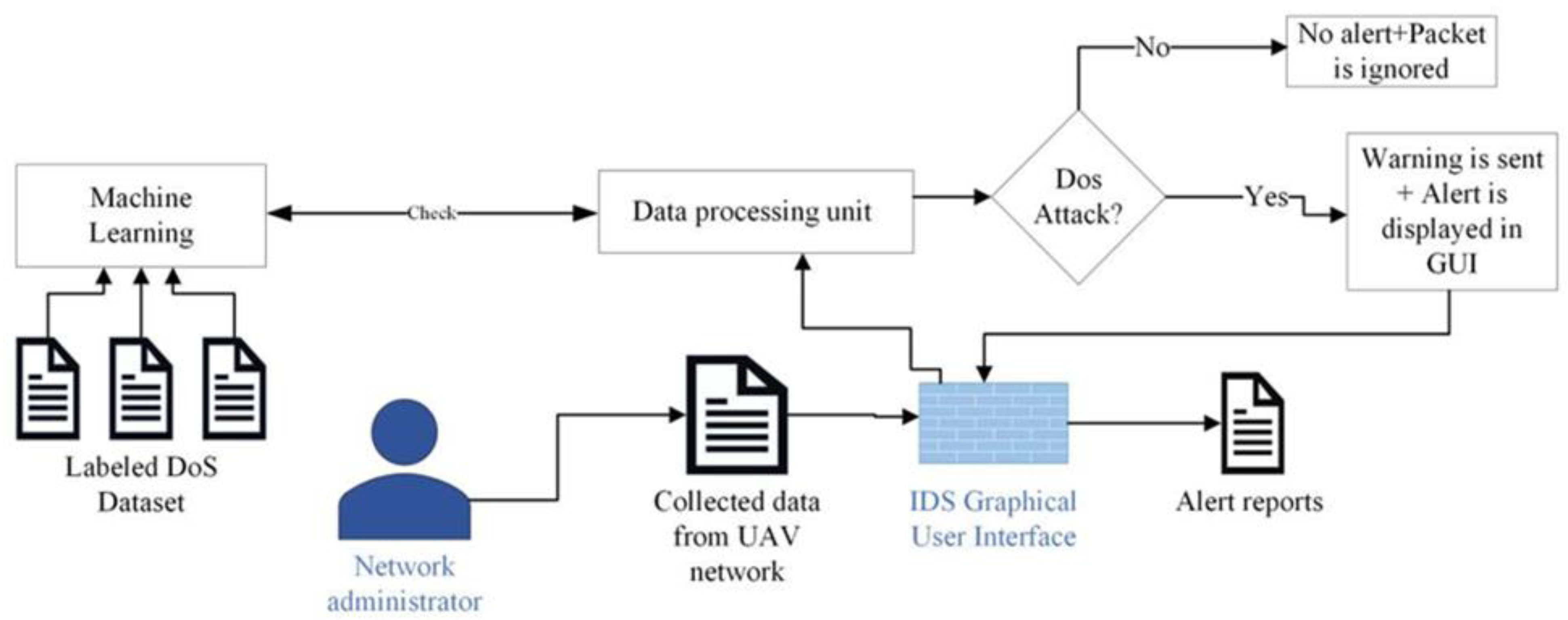
Figure 3 illustrates our proposed IDS system model, DroneDefender, which operates as follows:
The network administrator logs into the system through the IDS GUI web application and uploads the network traffic collected from the UAV network they manage. The data processing unit utilizes a reliable labeled dataset, CIC-IDS 2018, serving as the knowledge base for the IDS system. The IDS applies to the Random Forest (RF) machine learning algorithm for classification, using selected features relevant to detecting DoS attacks on UAV networks. If a DoS attack is detected, a warning is sent via email, including the source IP address of the attacker and the time of the alert. These alert details are also visible to the administrator in the GUI, and a report of the alerts can be generated upon request. Additionally, the source IP address associated with the DoS attack packets will be added to a blacklist, allowing network administrators to implement mitigation measures. If no DoS attack is detected, no alert is generated, and the packet is ignored.
3.3. Machine Learning Architectural and Design Approach
Within our system, we have chosen Python as the programming language for training machine learning models using Random Forest (RF) algorithms and for developing the web application. The Random Forest (RF) algorithm has consistently shown strong performance in previous UAV/IoD intrusion detection research because of its robustness, resilience against noise, ability to cope with high-dimensional traffic functions, and efficacy with imbalanced datasets. RF is more useful for UAVs and edge-constrained scenarios where delay and resource utilization are crucial, since it offers great accuracy with much less processing overhead than computationally costly deep learning models like LSTM. Furthermore, findings from earlier research show that RF detects DoS assaults on par with or even better than popular classifiers like SVM, KNN, LR, and MLP. In line with these conclusions, our data verify that RF maintains operational viability while offering dependable detection accuracy. Additionally, results from previous studies demonstrate that RF identifies DoS attacks as well as or even better than well-known classifiers like SVM, KNN, LR, and MLP. According to these findings, our results confirm that RF provides reliable detection accuracy while retaining operational viability.
Several Python libraries and frameworks will be effectively employed in constructing the project.
Scikit-learn, commonly referred to as sklearn, is a popular Python machine learning package that offers an extensive collection of tools and techniques for a wide range of tasks, including model selection, regression, clustering, dimensionality reduction, and classification.
Pandas is a well-known open-source Python library for analyzing and manipulating data. It simplifies working with structured data, such as tabular data and time series, through its robust data structures and operations. Pandas are built on top of NumPy and are frequently used alongside other libraries for tasks such as data analysis and machine learning.
NumPy is a core Python package designed for numerical computations. Its powerful array object and array-manipulating functions enable efficient mathematical operations on large datasets. NumPy is widely used in the scientific and data analysis communities.
Finally, Matplotlib is a popular Python library for creating interactive, animated, and static visualizations. It provides a wealth of tools for generating various types of plots, including histograms, line graphs, scatter plots, and bar charts, among others.
3.4. Web Application Design Approach
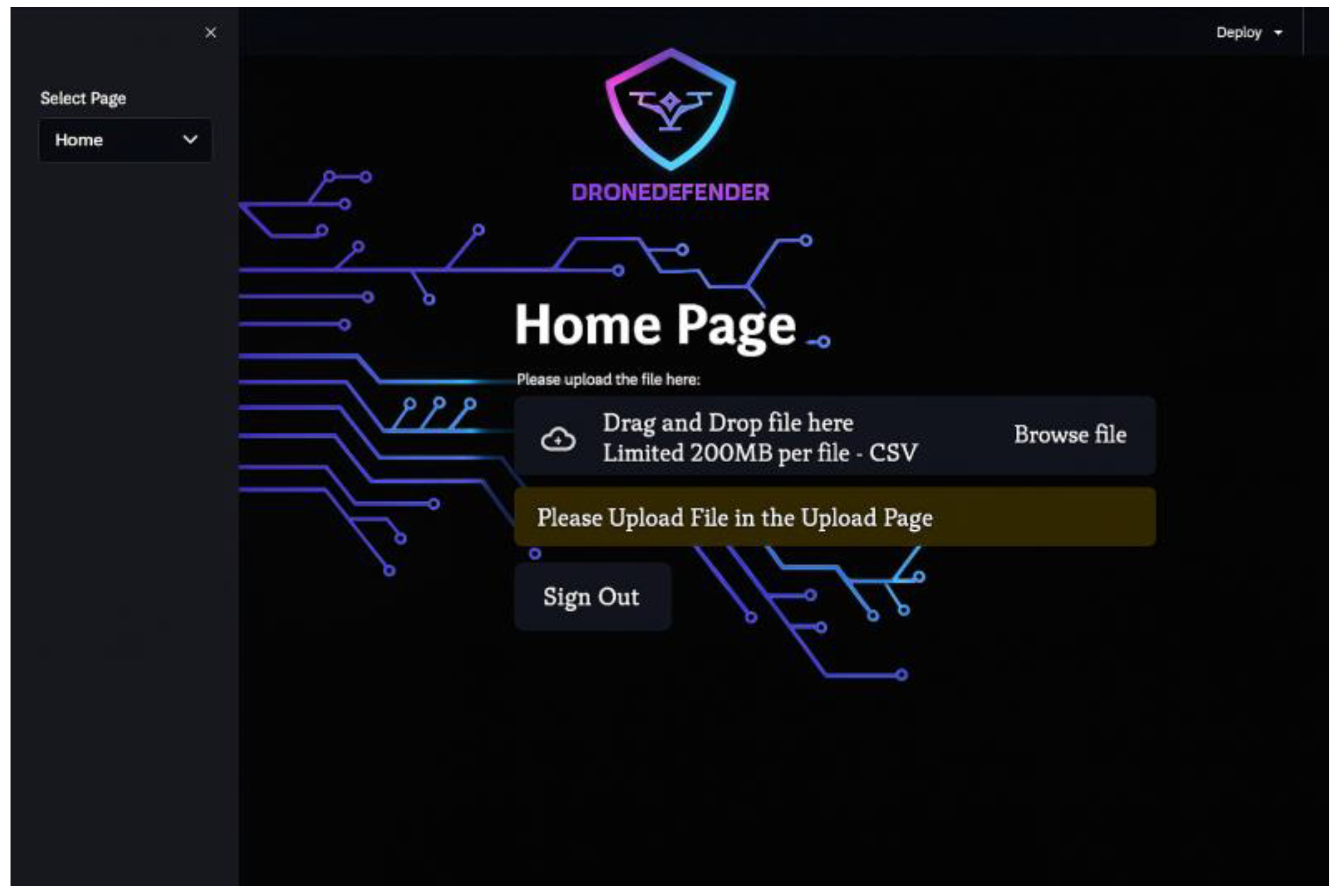
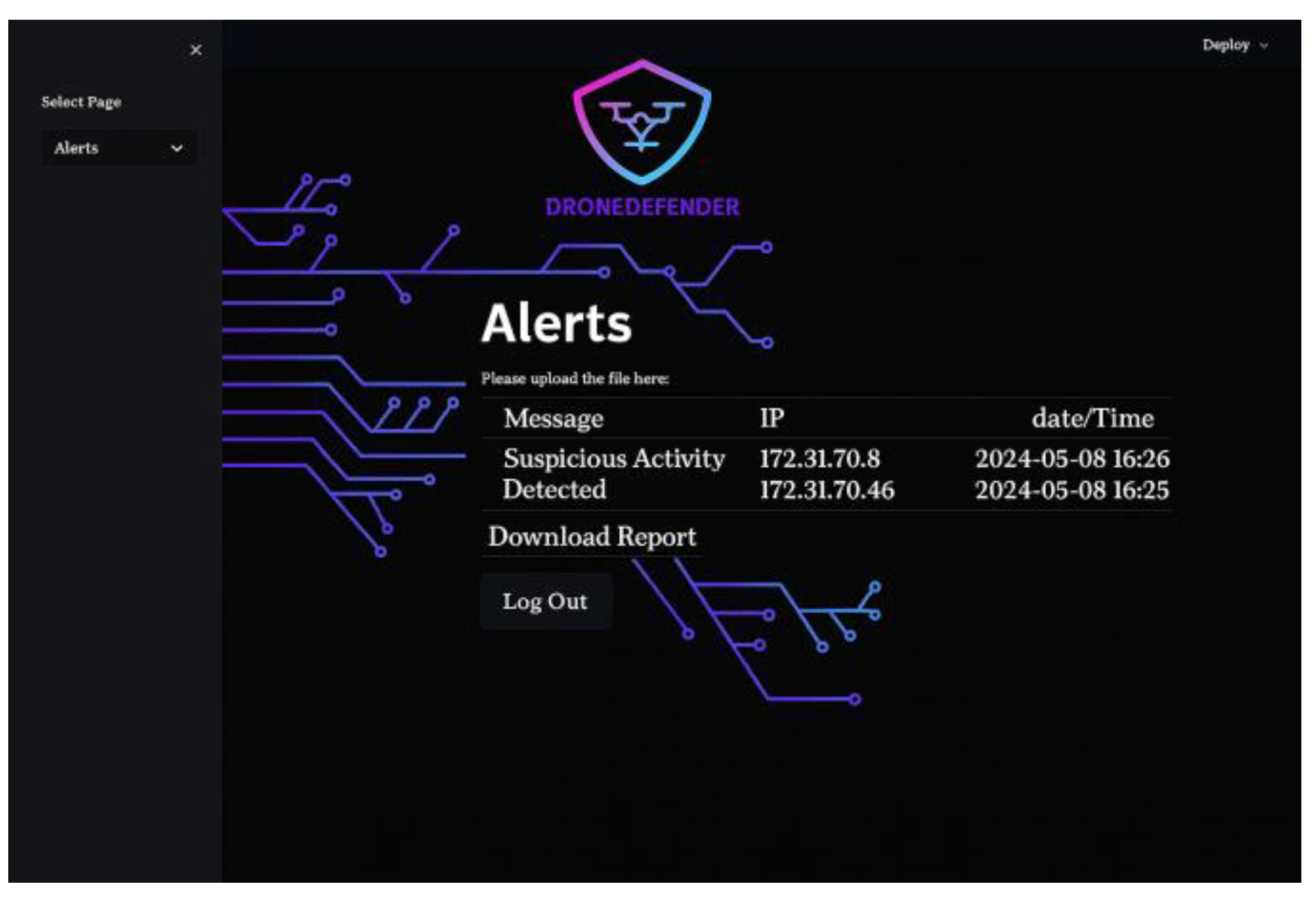
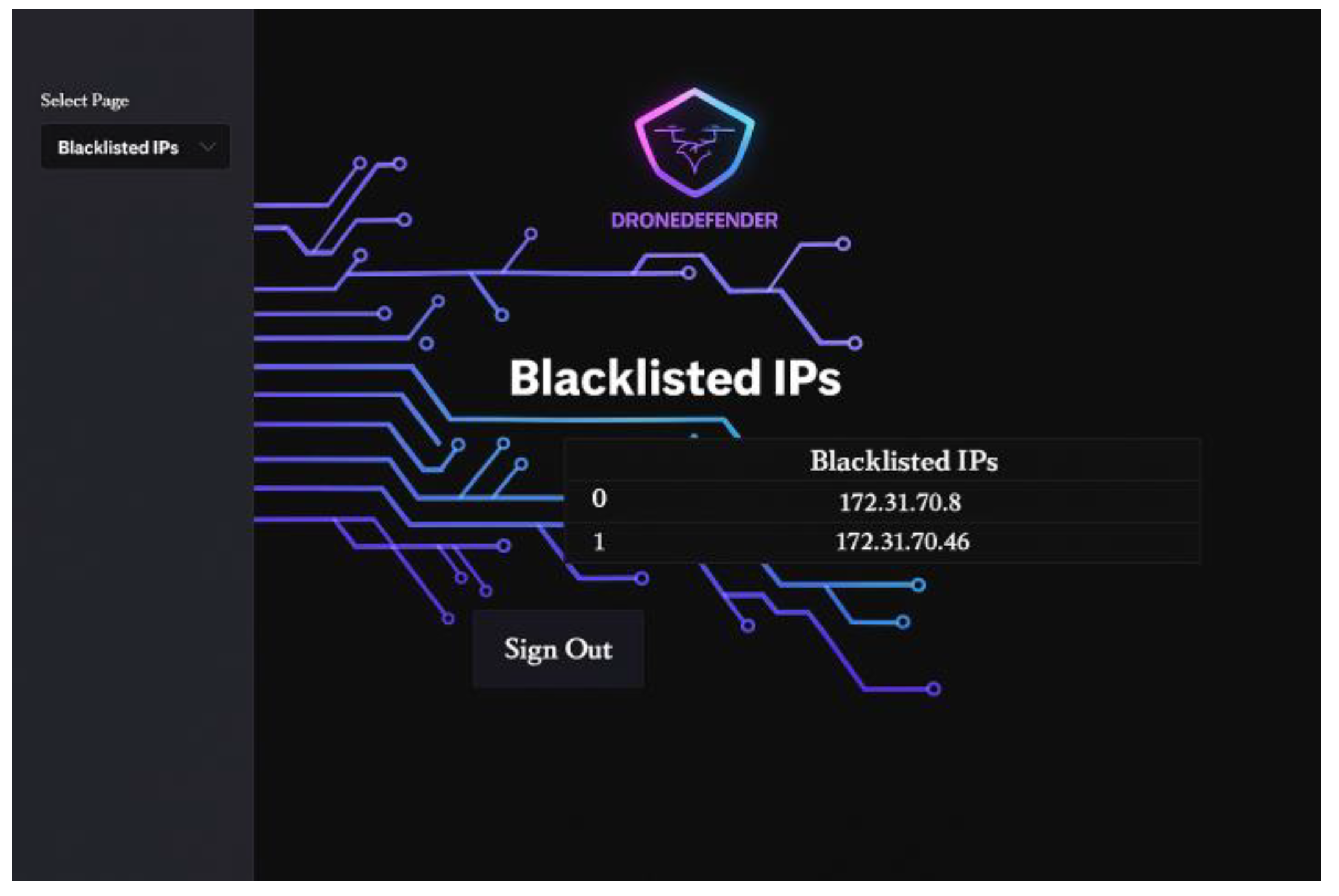
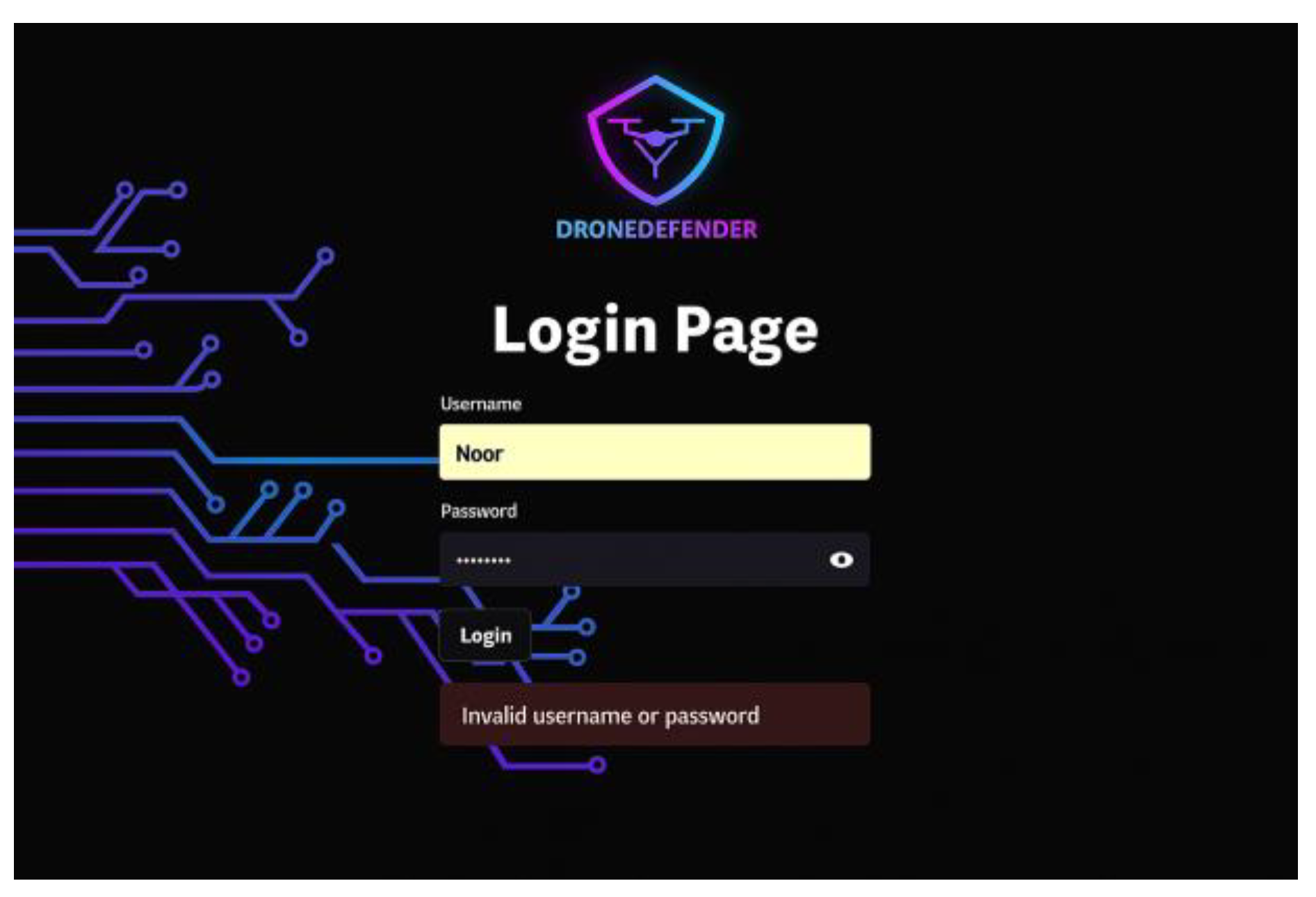
The primary purpose of this web application is to enable the network administrator to utilize the trained machine learning model to analyze, detect, and identify DoS attack patterns within the uploaded UAV network traffic data file, as well as to view the results. The application consists of four straightforward interfaces. The login interface authenticates the provided username and password credentials against the pre-registered admin information stored in the database. The home page displays the uploaded dataset after the feature selection process, allowing administrators to manually analyze the network traffic based on selected features relevant to detecting DoS attack patterns. Additionally, the home page shows the percentages of correct predictions for each class produced by the machine learning model after processing the uploaded data. The Alerts and Blacklisted IPs interface presents tables of generated alerts and blacklisted IPs (source IPs of attackers), respectively.
We utilized Python’s Streamlit and SQLite libraries to build the database of pre-registered admin accounts and to develop the web application. Streamlit, an open-source library, simplifies the creation of web applications using Python scripts, enabling data visualization, user interface development, and integration of machine learning models. This approach streamlines the integration of our trained model with web interfaces, as all code for both the web application and machine learning model development remains within the Python environment.
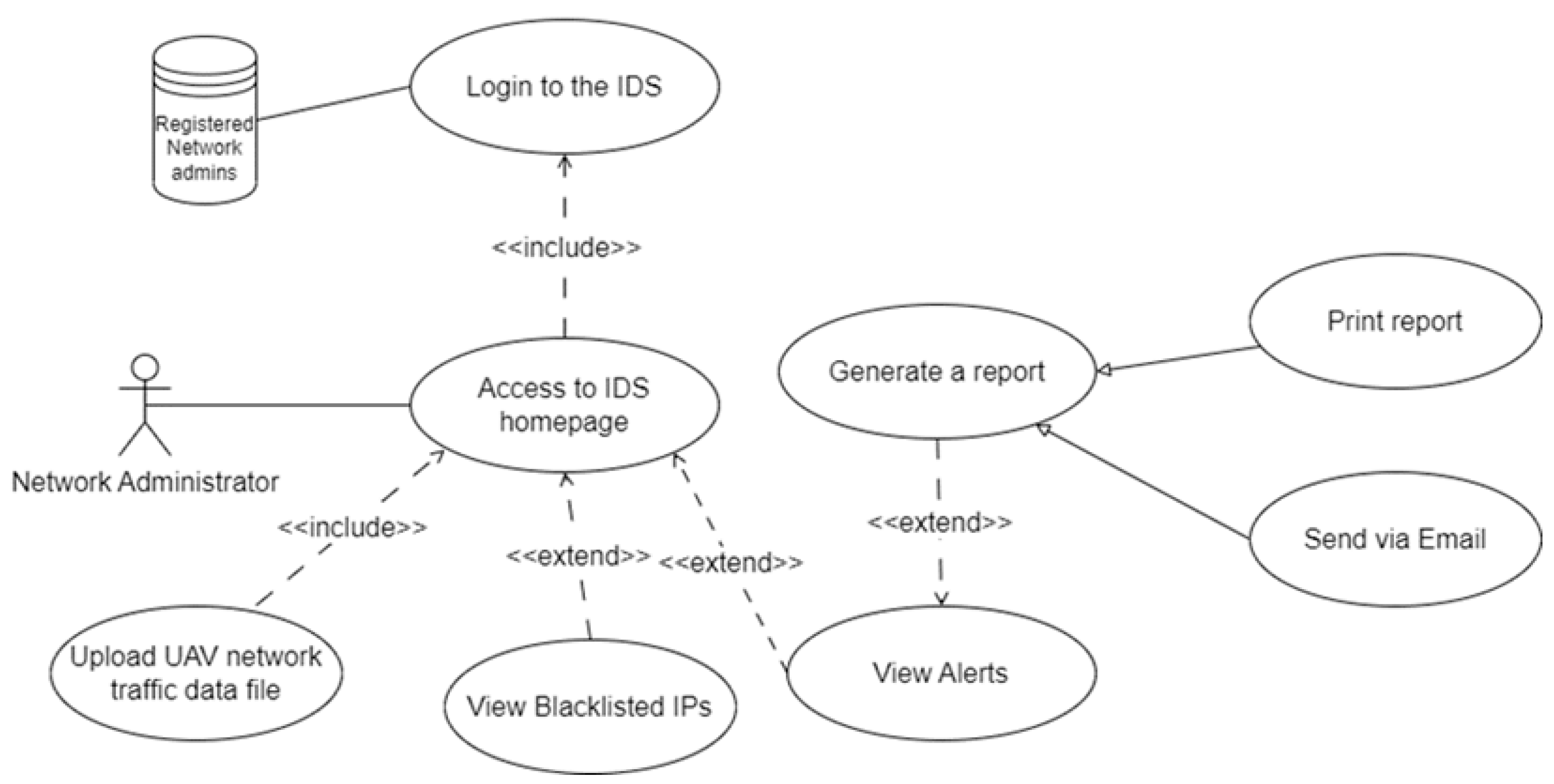
Figure 4 shows a use case diagram that illustrates how the network administrators interact with the IDS GUI interfaces.
6. Experiment Evaluation and Testing
6.1. Machine Learning Model Evaluation
The measurable metrics used to assess a model’s performance include the confusion matrix, accuracy, recall, precision, and F1-score. These metrics evaluate the effectiveness of specific features of the model.
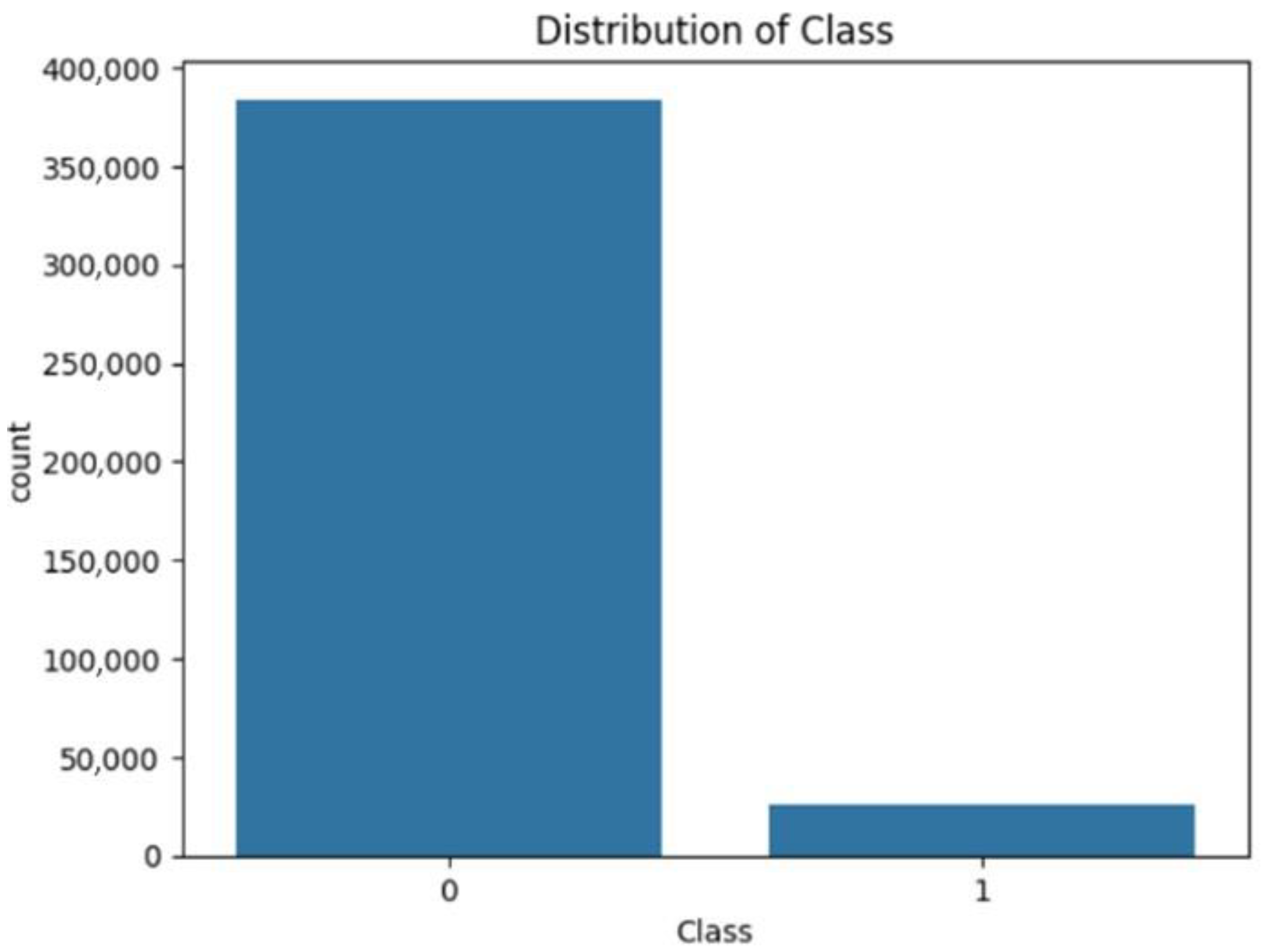
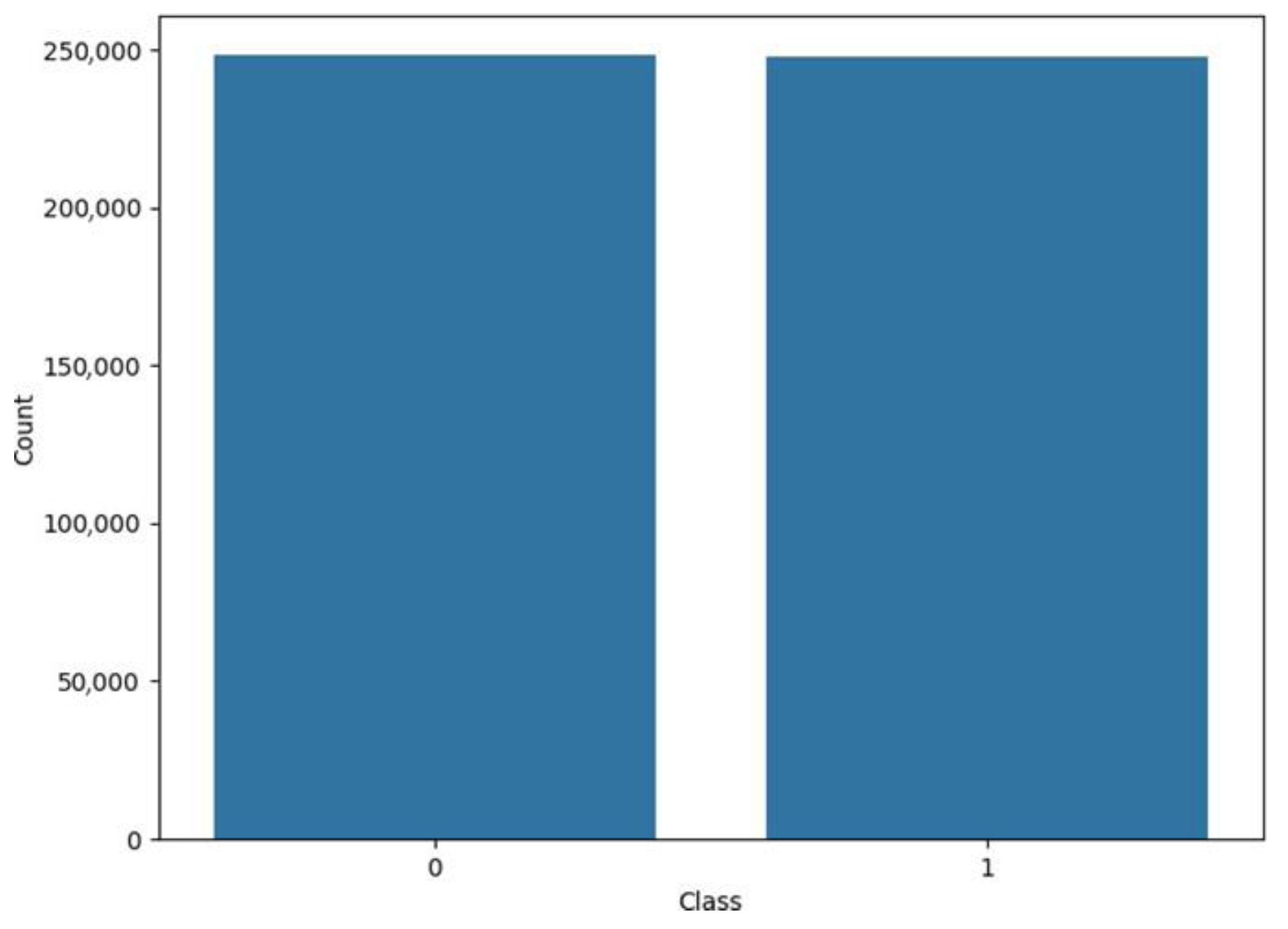
The CIC-IDS2018 dataset was first cleaned, duplicates were eliminated, labels were combined into binary classes, and only the 13 GA-selected DoS-relevant characteristics were kept in order to make the assessment process more understandable. In order to maintain the original class distribution, the dataset was subsequently split into 70% training and 30% testing using a stratified split (random state = 42). Crucially, SMOTEENN was limited to the training phase, guaranteeing that the test set did not contain any artificial samples or resampled data. Grid search with cross-validation was used to optimize the model solely on the training data in order to reduce overfitting. The completed model was then assessed once on the unaltered test split. Together, these actions end due to optimistic bias and data leakage. Although the resultant near-perfect performance might seem abnormally high, it is compatible with (i) the categorization into setting, (ii) the exceptional discriminative strength of the chosen features, and (iii) Random Forest’s aptitude for this sort of dataset—a pattern that has also been seen in previous publications.
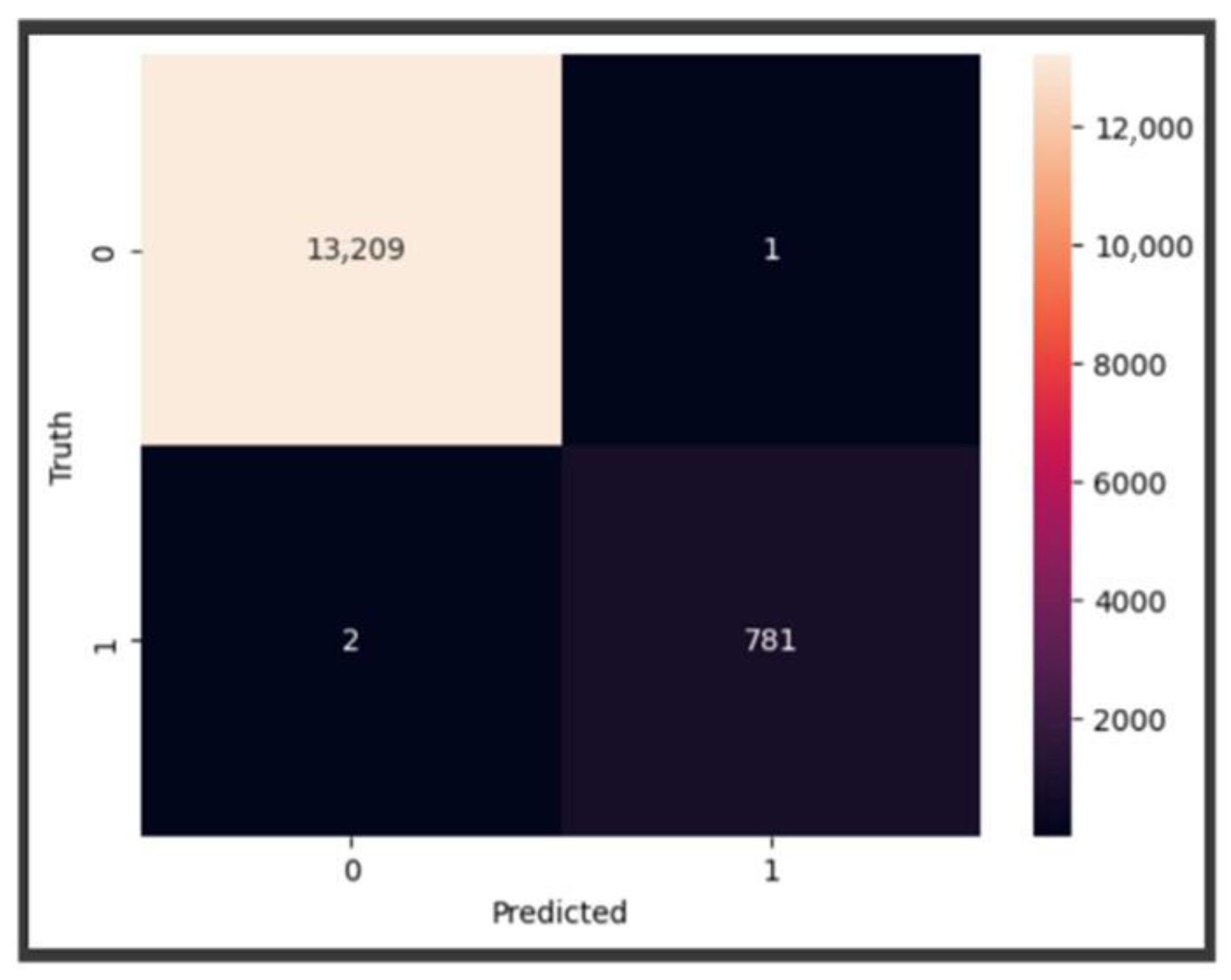
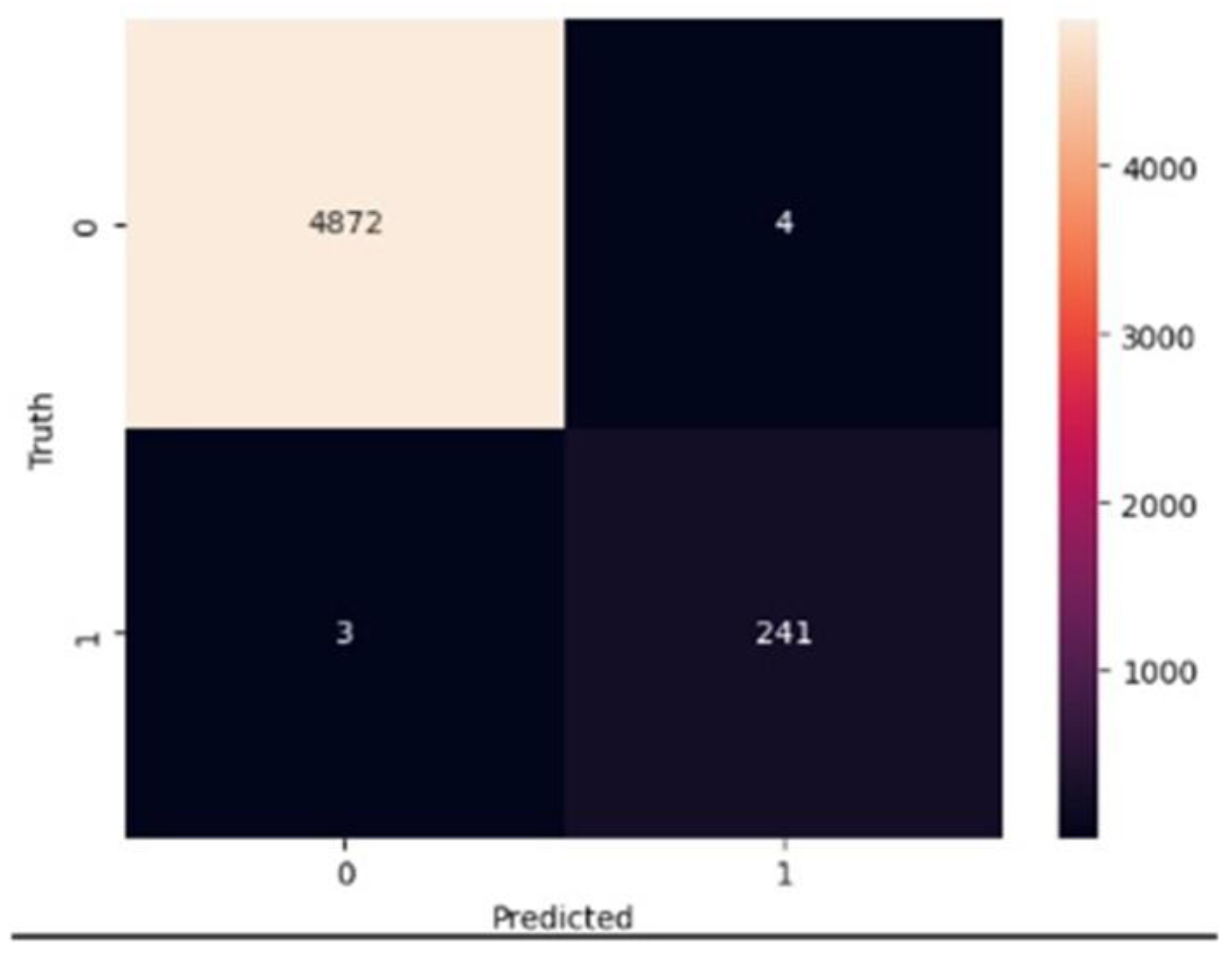
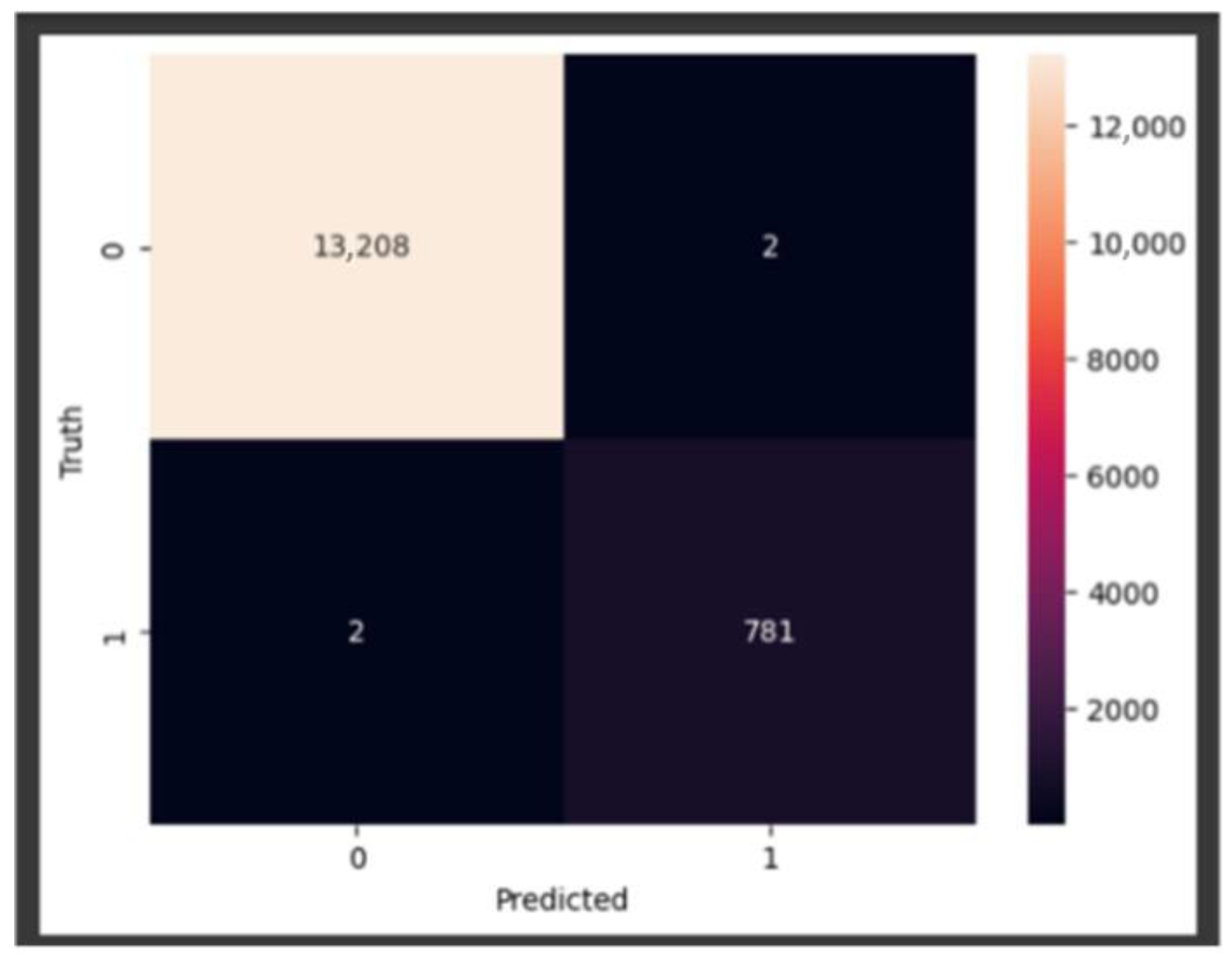
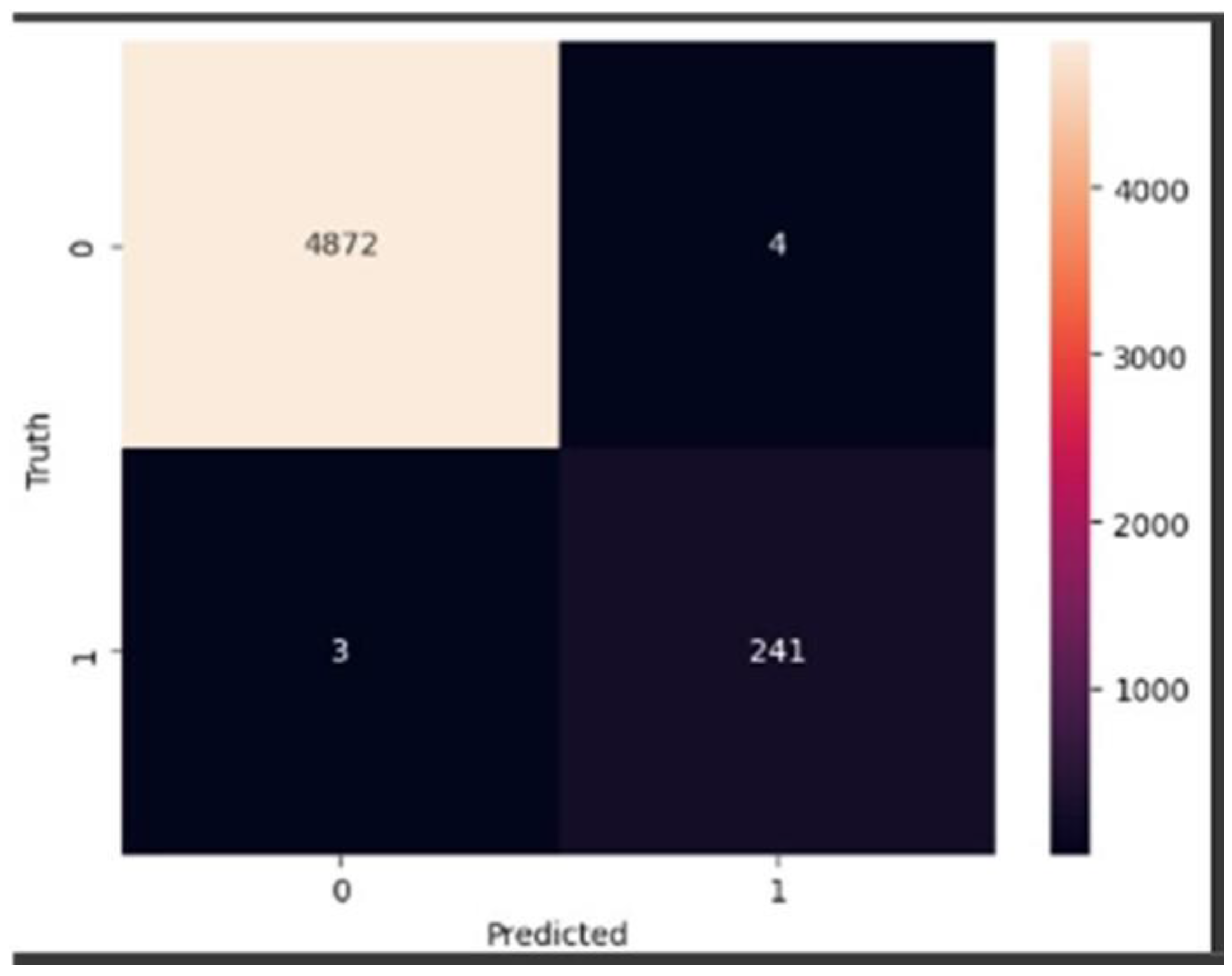
Confusion Matrix: This table represents the model’s performance on a test dataset with known true values. It allows observation of the model’s accuracy by displaying the number of true and false predictions in a four-cell layout: true positives (TP), true negatives (TN), false positives (FP), and false negatives (FN), as shown in
Table 4.
Accuracy: This metric indicates the overall accuracy of the model, calculated by dividing the total number of true predictions by the total number of observations.
Table 5 presents a comparison of the performance metrics for various versions of Random Forest (RF) and XGBoost models. It evaluates the effects of using default model parameters versus optimized “best” parameters, as well as the impact of the SMOTEENN data preprocessing technique. The key findings are as follows:
The basic RF model using default parameters and the original dataset achieved an impressive testing accuracy of 99.99%, with perfect scores of 100% for recall, precision, and F1-score.
When the same basic RF model was trained on the SMOTEENN preprocessed data, the testing accuracy slightly decreased to 99.92%, while recall, precision, and F1-score remained at the perfect 100% level.
The optimized RF model with the best parameters, when trained on the original data, maintained a high testing accuracy of 99.99% and perfect scores across all other metrics.
Similarly, the optimized RF model with the best parameters, using the SMOTEENN preprocessed data, exhibited a testing accuracy of 99.93% and perfect 100% scores for recall, precision, and F1-score.
The results of the optimized XGBoost model with the best parameter results of the original data and SMOTEENN are very similar.
Figure 11,
Figure 12,
Figure 13 and
Figure 14 depict the actual versus predicted values for the model under different conditions. The first two plots (
Figure 11 and
Figure 12) showcase the basic RF model without parameter optimization, utilizing the SMOTEENN preprocessed data and the original dataset, respectively. The basic model has difficulty accurately predicting the minority class when trained on the original data, but its performance shows improvement when trained on the SMOTEENN data.
Figure 15 and
Figure 16 illustrate the optimized RF model with the best parameter settings, using both the original dataset and the SMOTEENN preprocessed data. The optimized model shows a better alignment between actual and predicted values, particularly when trained on the SMOTEENN data. This trend indicates that both parameter optimization and the application of the SMOTEENN data preprocessing technique can enhance the performance of the Random Forest classifier. The optimized model with SMOTEENN data demonstrates the most balanced and accurate predictions, underscoring the significance of model tuning and data preparation in improving the effectiveness of machine learning models. Additionally, we achieved a higher accuracy rate than reported in the paper [
31], which noted an accuracy of 96.2%. Our work utilized the same dataset and algorithm, Random Forest, highlighting the improvements made.
6.2. Website System Test
In this section, we discuss the objectives of the testing plan, along with its background, methodology, and scope. We also identify the features of DroneDefender that will undergo testing. The plan encompasses the testing approach, pass/fail criteria, testing processes, activities, cases, responsibilities, requirements, and resources.
The primary goal of the testing plan is to verify that DroneDefender meets all functional requirements while ensuring that the website provides a user-friendly interface for network administrators. It is essential that only pre-registered network administrators log onto the website, and that the machine learning model accurately processes the uploaded data. Additionally, the results generated by the model must be correctly displayed on the web interfaces, and the alerts of reports should contain accurate and sufficient information. Ultimately, the plan aims to ensure that DroneDefender successfully passes all testing activities.
Testing will cover user functions, such as logging into DroneDefender, successfully uploading network traffic data files, viewing blacklisted IPs, and extracting alert reports. It will also address system functions, including the validation of login credentials, confirmation that uploaded files are in the correct CSV format, processing of the uploaded data, sending email alerts to the main administrator in the event of detected DoS attacks, and displaying the required information on the website’s pages, including Home, Alerts, and Blacklisted IPs.
The website development code will be thoroughly reviewed to confirm that DroneDefender is prepared for deployment in a production environment. This review will encompass all front-end functionalities, including the operation of buttons and user input for logging in and uploading files. Additionally, all code related to various functions will be assessed, from the network administrator’s login process to the display of results generated by the machine learning model, as well as the sending of alert emails and the extraction of alert reports. Each aspect will be checked against the required outcomes to ensure full functionality and readiness.
The features of DroneDefender that will be tested include the following: the network administrator login process, which restricts access to only pre-registered admins saved in the database; the successful uploading of files in the correct format; and the detection of DoS attacks through integration with the trained machine learning model. Additionally, the machine learning model must demonstrate acceptable results and accuracy. Timely email alerts should be generated in the event of a DoS attack detection, and the source IP addresses of such attacks must be displayed on the “Blacklisted IPs” page. Finally, the system should allow logged-in network administrators to generate and extract alert reports as needed.
Component Testing: Every area of the system will be tested individually, including admin login, uploading network data traffic, DoS attack detection, the accuracy of results from the machine learning model, and alert report generation. Following this, integration testing will combine the system components.
The testing technique will involve providing the tested components with both valid and invalid data to ensure that appropriate inputs yield relevant results, while also displaying error messages for incorrect login credentials or inappropriate file types. The completion criteria stipulate that each component must function as intended and handle errors appropriately.
The system testing approaches are as follows:
Integration Testing: Once individual component testing is complete, integration testing will be conducted by gradually merging the components and evaluating their interactions. The primary objective of this testing phase is to ensure successful integration and verify that the system interfaces are properly linked with the database tables of pre-registered network admins and the machine learning model.
Performance Testing: DroneDefender must operate as expected, without interruptions that could disrupt functionality. The system should upload a dataset from the user and process it to produce accurate results. To test DroneDefender’s performance, the dataset will be uploaded for processing by the machine learning model to detect suspicious behavior in network traffic, leading to the generation of alerts and blacklisting of suspicious IP addresses.
Interface Testing: The web interfaces of DroneDefender will be evaluated to ensure they function correctly and communicate effectively with the intended network administrator. This testing will confirm that the interfaces are user-friendly, clear, and easy to navigate.
Security Testing: Security measures will be put in place to ensure that passwords and sensitive information are neither hardcoded in the code nor visible in the database. All network administrator passwords will be salted, hashed, and securely stored in the database table for admins.
6.3. Test Cases
The testing environment can operate on any PC or laptop with suitable hardware. The software requirements include several Python packages: Pandas 2.1.x, SQLite3.42.0, NumPy 1.26.4, VSCode, Streamlit 1.38.0, Matplotlib 3.8, and hashlib 3.1.
During the implementation phase, a comprehensive software testing plan must be developed alongside the system functionalities. After the testing procedures are completed as shown in
Table 6 and
Table 7, the system should align with user needs. Ultimately, team members will have the opportunity to showcase their work and provide detailed insights into the system’s features for those interested in protecting their UAVs from DoS attacks as shown in
Table 8 and
Table 9. The testing tasks include the following:
Setting up the hardware environment.
Preparing for the software environment.
Conducting test cases.
Troubleshooting testing errors.
Maintaining the system consistently.
Table 6.
Network administrator login’s test case.
Table 6.
Network administrator login’s test case.
| Test Case | Network Administrator Login |
|---|
| Pre-requisite | |
| Test Procedure | Access DroneDefender web application. Fill in the username and password fields. Press the “Login” button. In case of an invalid login credential, an error message is displayed. Complete the log-in process, as shown in Figure 16.
|
| Expected Result | |
Table 7.
Network traffic data file upload’s test case.
Table 7.
Network traffic data file upload’s test case.
| Test Case | Upload Network Traffic Data |
|---|
| Pre-requisite | |
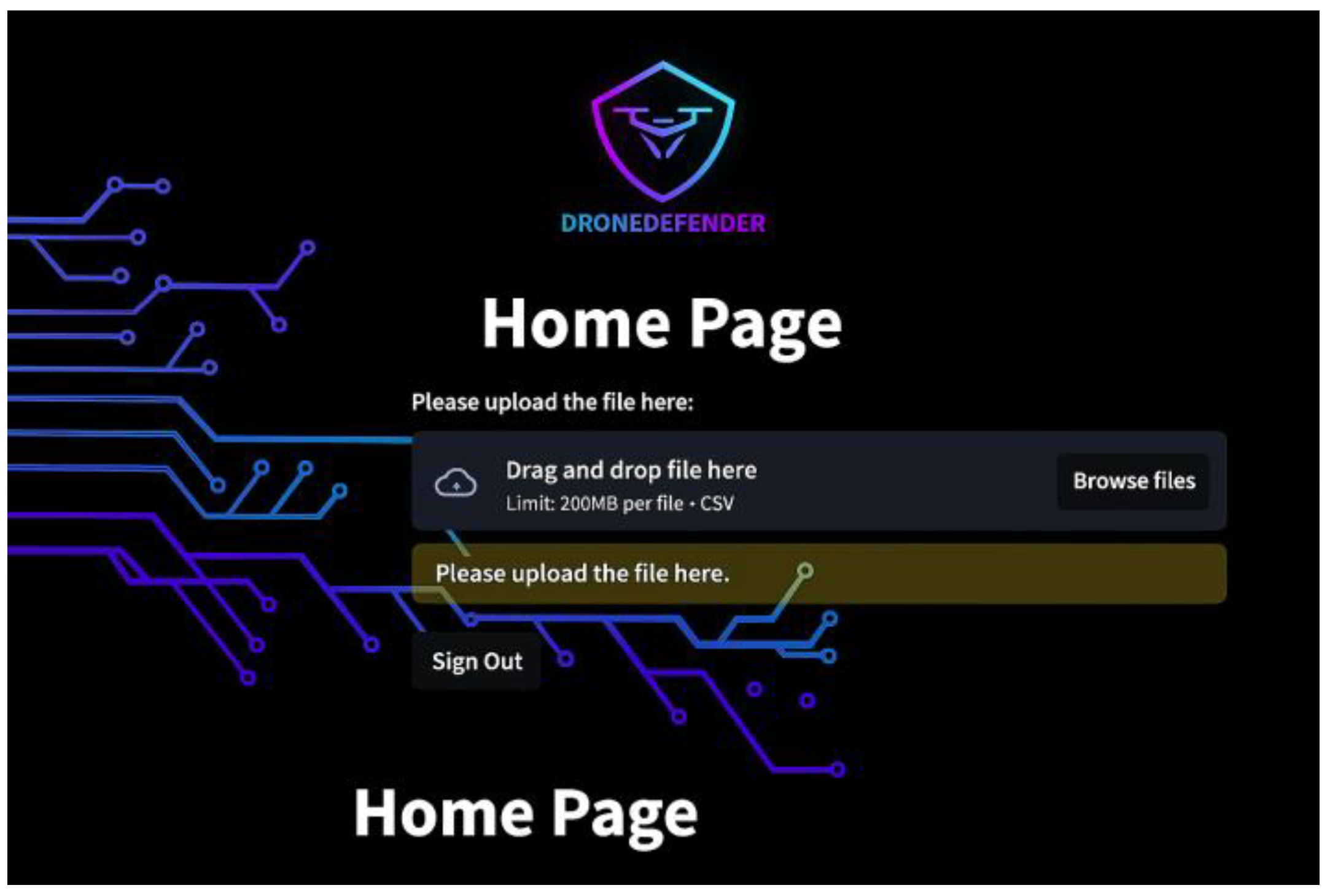
| Test Procedure | Select to upload a file, as shown in Figure 17. Choose the desired file to upload. Verify that the file is uploaded in the correct format. Show error message if no file is uploaded or if the format is incorrect (system only accepts CSV).
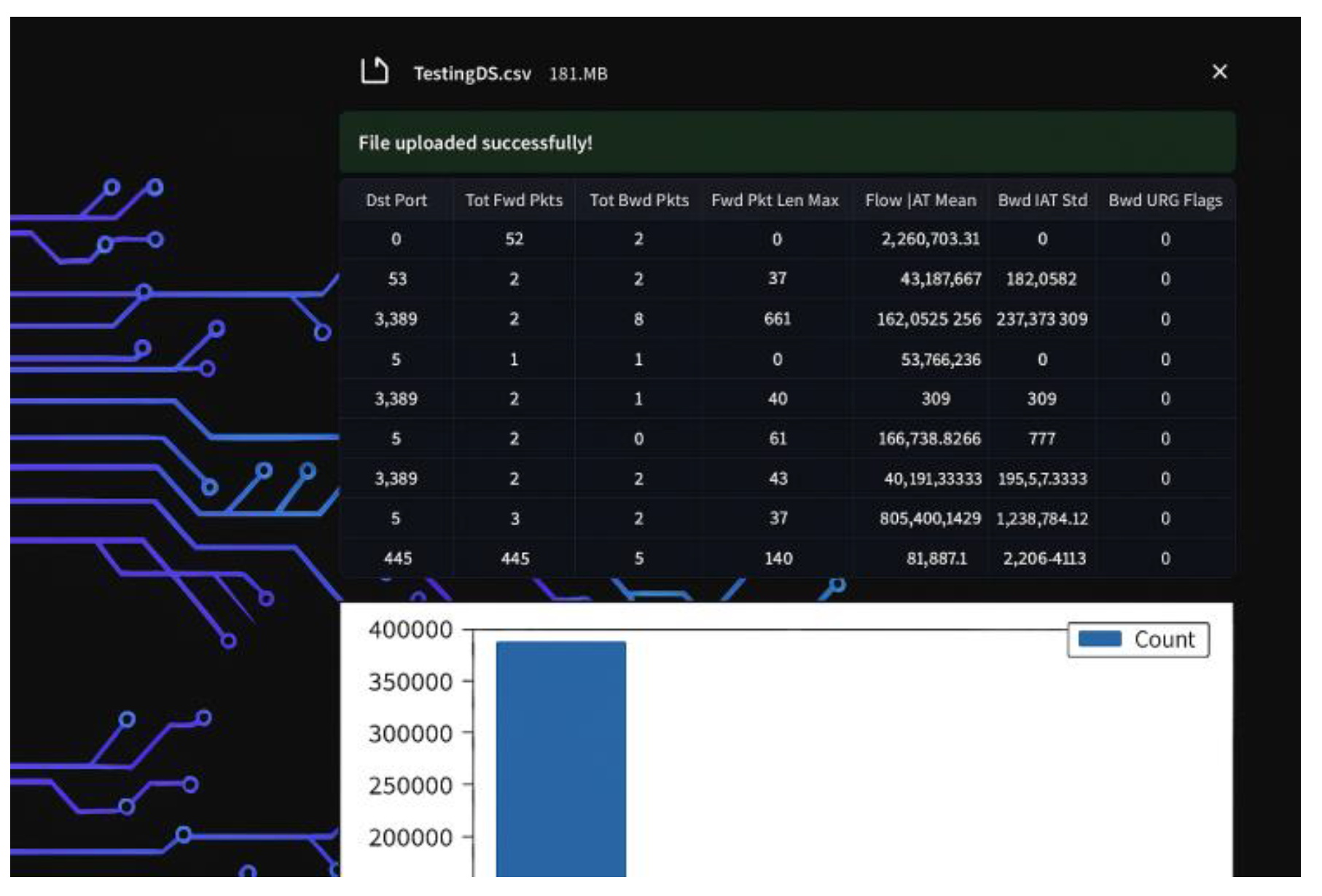
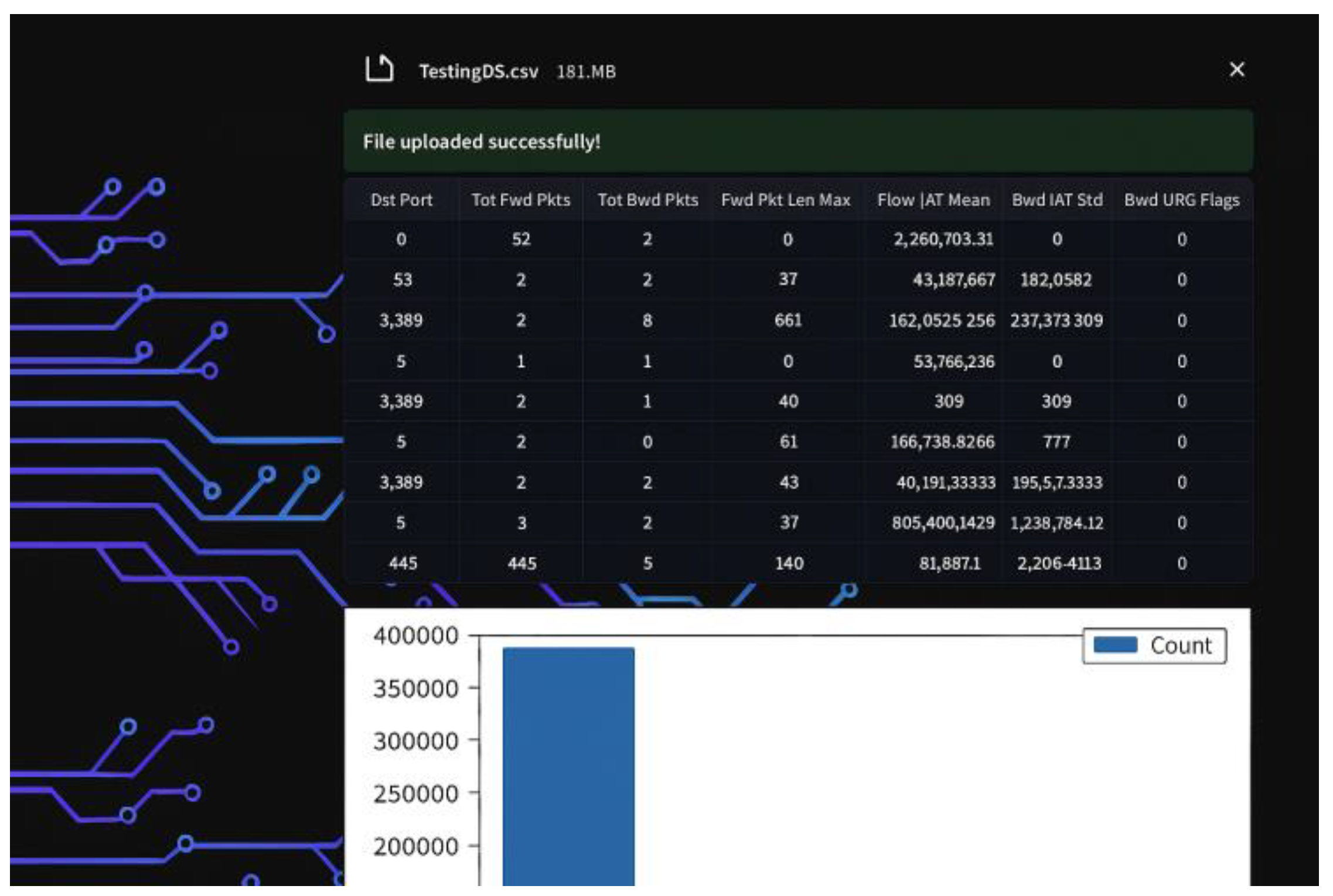
|
| Expected Result | A message indicating successful file upload will be displayed, and a bar chart graph of the packet counts for each IP address found in the input file will be shown, as in Figure 18.
|
Figure 17.
After uploading the traffic data interface.
Figure 17.
After uploading the traffic data interface.
Figure 18.
Home page with correct predictions.
Figure 18.
Home page with correct predictions.
Table 8.
DoS attack detection’s test case.
Table 8.
DoS attack detection’s test case.
| Test Case | DoS Attack Detection |
|---|
| Pre-requisite | |
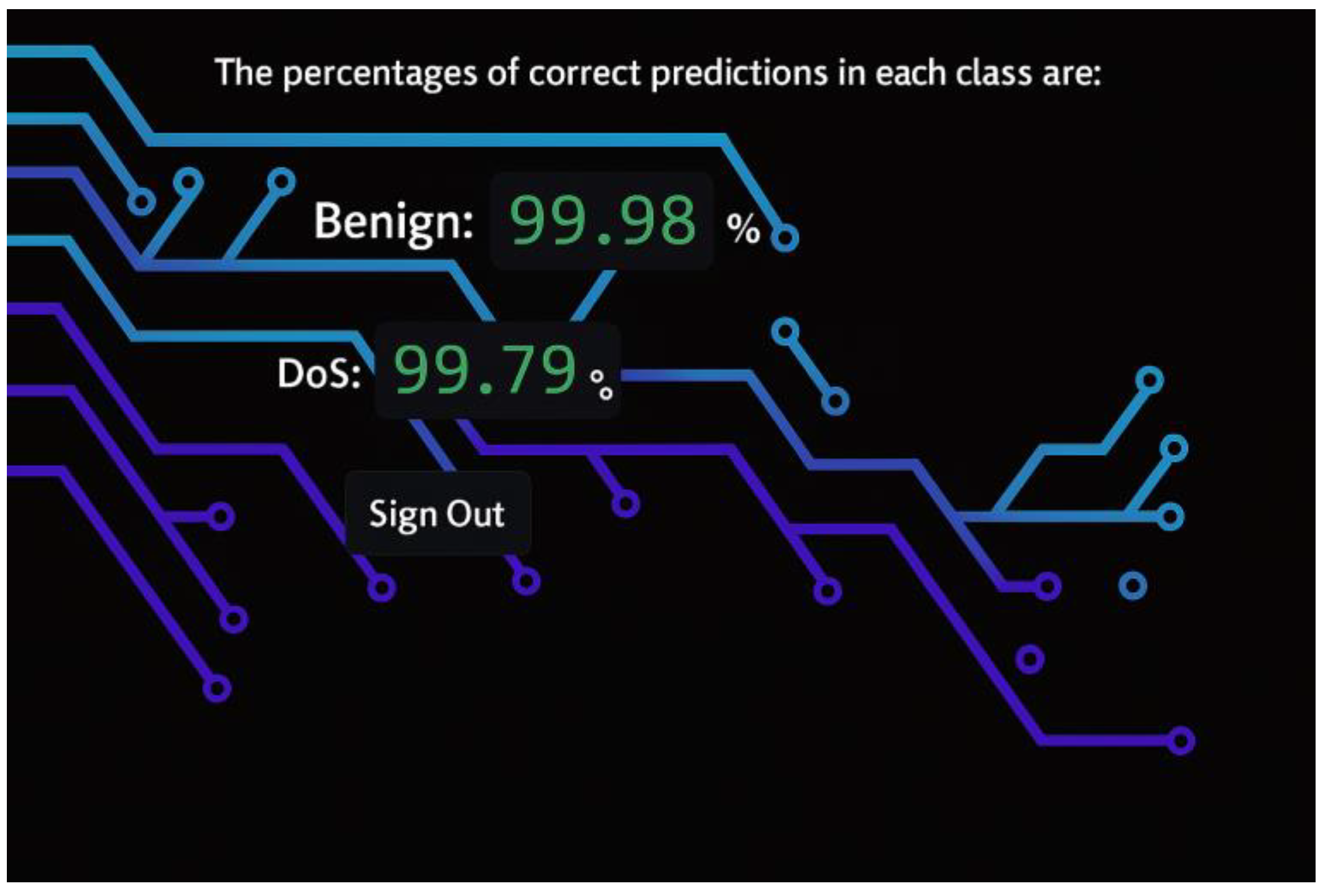
| Test Procedure | The uploaded file is sent to the trained ML model. The ML model processes and detects DoS attack patterns. The ML prediction results of each class (Benign, DoS) are obtained from the model.
|
| Expected Result | The percentages of correct predictions in each class (Benign, DoS) will be displayed for the network administrator on the home page (as shown in Figure 19). A version of the uploaded file (after feature selection and removal of unnecessary columns) will be displayed on the admin homepage (as shown in Figure 19).
|
Figure 19.
Home page with uploaded file after feature selection.
Figure 19.
Home page with uploaded file after feature selection.
Table 9.
Alert generation and report extraction’s test case.
Table 9.
Alert generation and report extraction’s test case.
| Test Case | Alert Generation |
|---|
| Pre-requisite | |
| Test Procedure | |
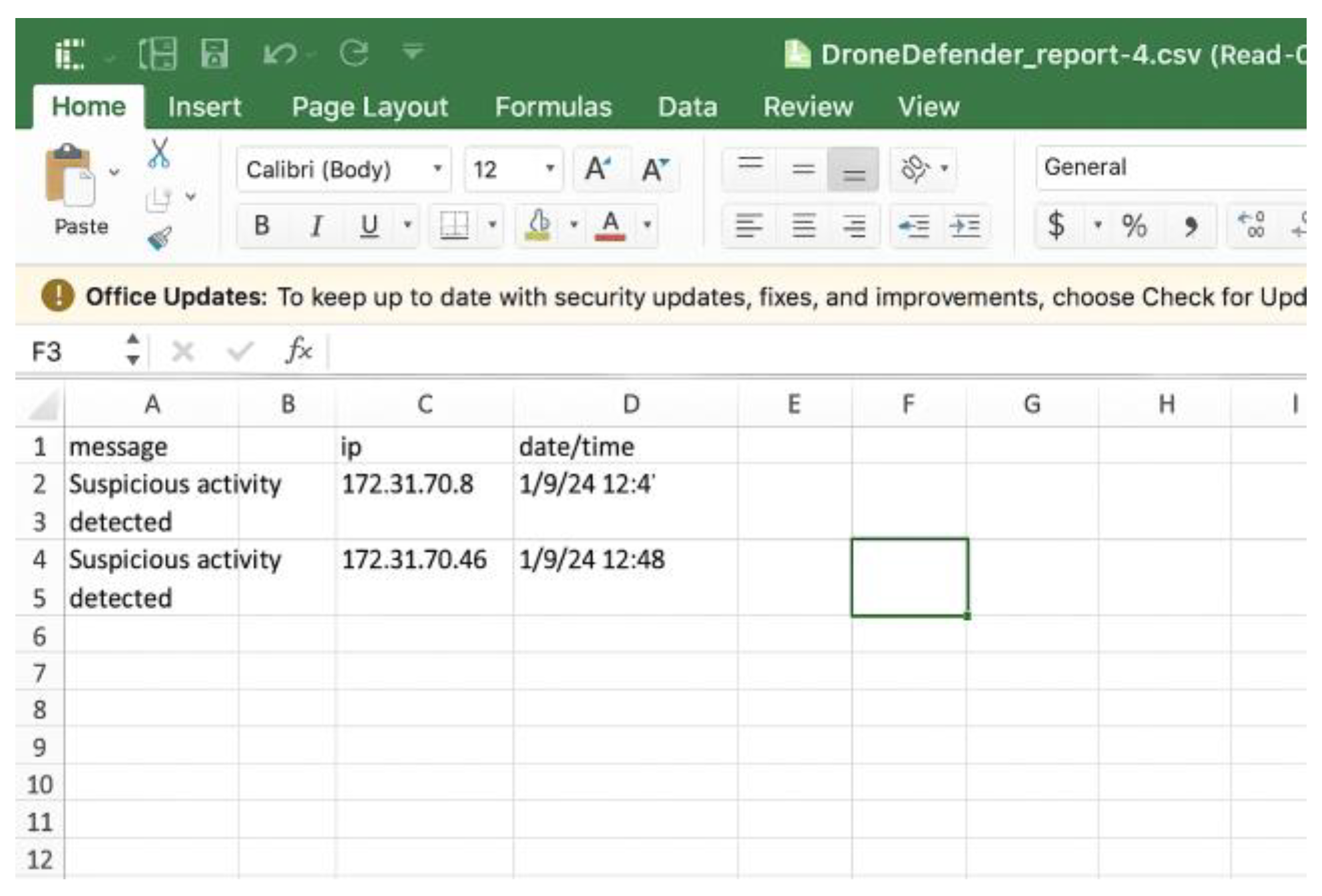
| Expected Result | Emails with alert details (DoS attack detection) are automatically sent. A table displaying suspicious activity, source IP address, and alert date/time is shown on the “Alerts” page. The admin can generate a CSV report of the alerts (as shown in Figure 20).
|
Figure 20.
Downloaded CSV file.
Figure 20.
Downloaded CSV file.
6.4. Real-Time Deployment and System Feasibility
Real-Time Operation and Latency:
Using a standard edge-computing environment similar to UAV ground stations (Intel i7, 16 GB RAM; Raspberry Pi-class evaluation underway), we assessed the trained Random Forest model. Processing in real-time under DoS attack situations is made possible by the model’s typical inference latency of 2.4–4.1 ms per flow. These metrics have been included, and the buffering delay-free processing of streamed packet batches has been made clear.
Resource Consumption & Processing Overhead:
We tracked CPU usage and model footprint. The model is suitable for lightweight ground nodes or fog/edge gateways rather than taxing UAV onboard systems because it requires less than 35 MB of memory, and CPU utilization stays below 18% at peak detection load. These findings are now stated clearly.
Deployment Model Clarification:
The proposed deployment architecture is now stated in unambiguous terms: By evaluating UAV traffic at the ground station/controller or fog gateway, DroneDefender functions as a lightweight edge-layer intrusion detection system (IDS) that avoids UAV onboard computing limits while guaranteeing real-time security response capabilities.
8. Conclusions
This paper has made significant contributions to the fields of cybersecurity and machine learning by developing an integrated system capable of accurately identifying DoS attack patterns on IoD networks. Through comprehensive testing and evaluation, we have demonstrated the system’s effectiveness in detecting and mitigating these attacks, thereby strengthening the security posture of IoD networks. We achieved an impressive 99.93% accuracy using the Random Forest algorithm with an optimized model, following the balancing of the CIC-IDS 2018 dataset through the SMOTEENN method, as detailed in [
31].
Despite being a widely recognized benchmark for assessing DoS detection, CIC-IDS2018 is still a generic wired network traffic dataset compared to one collected directly from UAV or IoD environments. Consequently, it effectively captures a variety of network-layer attack behaviors, packet-flow dynamics, and DoS traffic features that are also relevant to UAV communication. However, it falls short in addressing some aspects unique to UAVs, such as dynamic mobility architecture changes, intermittent connectivity, wireless link fluctuations, and transmission constraints related to drones. Therefore, although our findings indicate that the proposed model has substantial detection capability, they should be regarded as proof of feasibility rather than a complete substitute for actual IoD operational testing.
In order to further enhance realism and UAV specificity, future work will focus on evaluating the model using drone-generated traffic or IoD-specific datasets and incorporating wireless-layer and mobility-aware features. Looking ahead, several opportunities for boosting effectiveness and expanding impact arise. Firstly, exploring additional machine learning algorithms and techniques tailored to the distinctive characteristics of IoD networks could further enhance our model’s accuracy and efficiency in detecting DoS attacks. Additionally, conducting more comprehensive testing in diverse real-world environments, including field trials with UAV networks, would provide valuable insights into the model’s performance under varying conditions.
In order to facilitate continuous analysis of UAV traffic streams instead of relying solely on batch-uploaded data, a key approach is to adjust the system for live or near real-time monitoring. Optimizing the model for low memory consumption, reduced latency, and rapid processing will be essential to ensure practicality on integrated or lightweight gateway devices, since many IoD systems operate on resource-constrained edge or fog nodes in actual deployments. Additionally, incorporating other UAV-relevant threats into the current DoS-focused design—such as spoofing, hacking, man-in-the-middle attacks, and shifting anomalous behaviors—will enhance it and bolster its defensive capabilities. To further bridge the gap between experimental evaluation and real-world IoD deployment, it remains important to validate the system using IoD-specific or UAV-provided datasets and, ultimately, field trials.
Integrating anomaly detection mechanisms and reinforcement learning strategies could bolster the model’s adaptability to shifting threat landscapes. Finally, ongoing monitoring and updating of the model based on emerging threat intelligence and evolving attack vectors are crucial to ensure its long-term relevance and effectiveness in protecting IoD networks against DoS attacks.