A Privacy-Preserving Scheme for V2V Double Auction Power Trading Based on Heterogeneous Signcryption and IoV
Abstract
1. Introduction
1.1. Related Work
1.2. Contributions
- (1)
- A privacy-preserving scheme for V2V double auction power trading based on heterogeneous signcryption and IoV is proposed. The seller EVs can charge during periods of low load in accordance with the demand response policy and earn income by selling the electricity, which not only meets the instant charging needs of EVs but also helps to reduce range anxiety.
- (2)
- A heterogeneous signcryption algorithm from a CLC-to-IBC cryptographic system is improved, utilizing ECC and integrating the aggregation method in the scheme to achieve greater computational efficiency.
- (3)
- A pseudonym mechanism is implemented for EV users engaged in V2V power trading to protect the real identities of these users. It also provides a verification algorithm to verify the information and ensures the tracking of malicious EVs and the revocation of their eligibility to participate in V2V power trading.
- (4)
- The security analysis of this scheme is carried out based on ROM, and the performance comparison analysis is carried out through experiments. The scheme has certain advantages in both communication and computational costs.
1.3. Roadmap
2. Preliminaries
2.1. Elliptic Curve Cryptography
- (1)
- Point addition: For different points, , on , the sum of points and , denoted as , is the point where the line through and intersects the elliptic curve, . If , then , determined by the intersection of the tangent line of and .
- (2)
- Point multiplication: For ; point ; and an integer, , satisfying , is defined as point added times; that is, .
2.2. Difficult Problem
- (1)
- Elliptic curve discrete logarithmic problem (ECDLP): For a given point, , where and , it is computationally difficult to find . For sufficiently small numbers, ϵ, the probability that a probabilistic polynomial time-constrained adversary, , can solve ECDLP is negligible.
- (2)
- Elliptic curve computational Diffie–Hellman (ECCDH): For a given , i.e., a tuple , where , the ECCDH problem is to compute . For a sufficiently small number, , any adversary, , can solve ECDDH with negligible probability.
2.3. Blockchain
2.4. Security Model
- Confidentiality: Data transmitted by EVs is kept secret from attackers; even eavesdroppers cannot access its contents. Only authorized entities can access it.
- Integrity: This ensures that data signed by EVs has not been modified during V2V power trading.
- Authentication: Any attempt by an attacker to modify transmitted data should be detected, ensuring that only authorized entities can access the transmitted data.
- Non-repudiation: This prevents EVs from repudiating previously sent data. If accepted by a communicating entity, this action cannot be denied.
3. Scheme Design and Realization
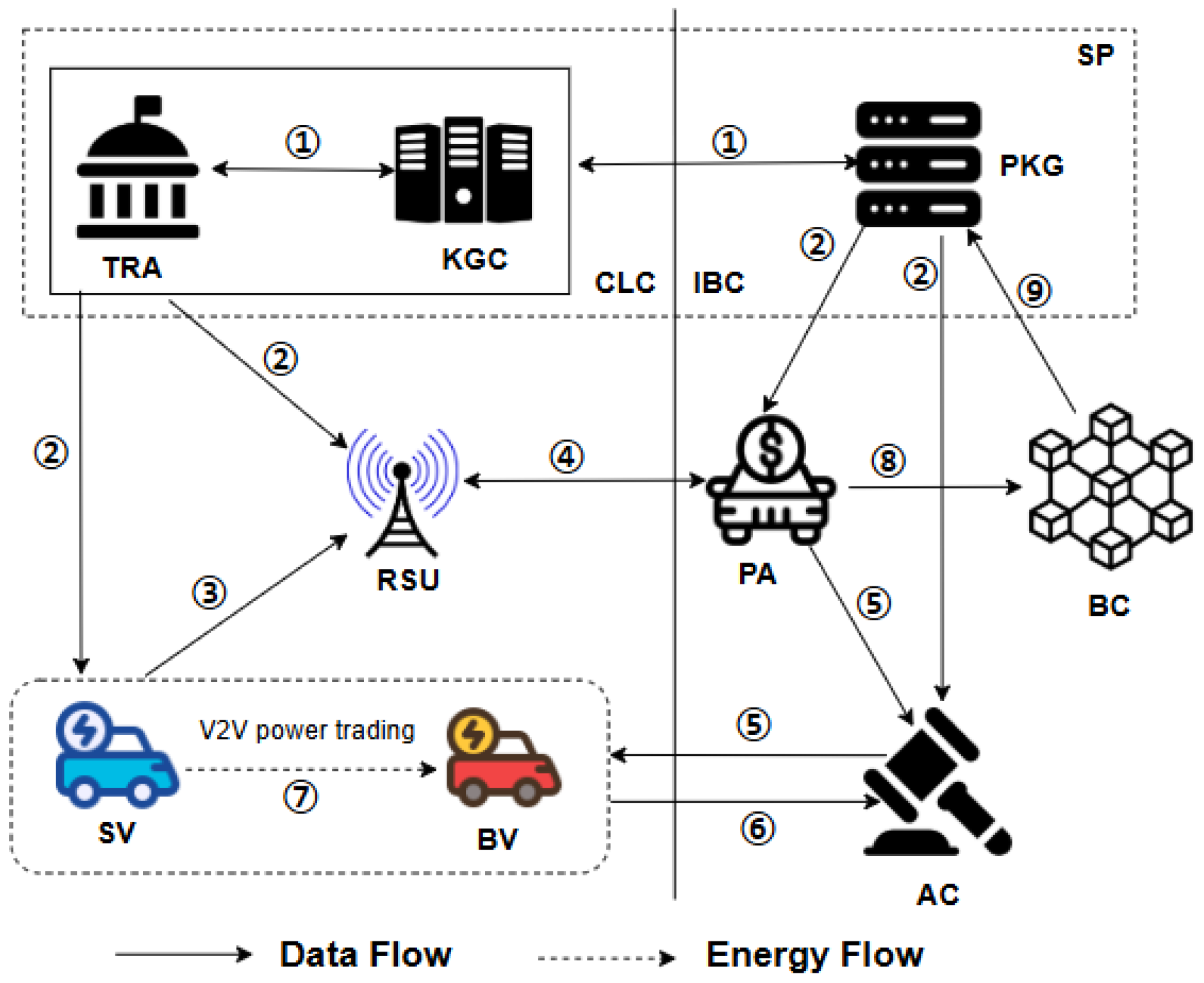
3.1. Scheme Overall Design Framework
3.1.1. Scheme Design Ideas
3.1.2. Scheme Model
3.1.3. Scheme Execution Process
- (1)
- The TRA, KGC, and PKG generate master keys and system parameters.
- (2)
- The TRA combines the KGC to generate keys for the RSU, and the PKG generates keys for the PA and AC. The EVs send their real identities to the TRA, which maintains the list, ; generates pseudonyms; and sends them to the KGC. The KGC generates partial private keys for them and maintains the pseudonym list, , to supervise the pseudonyms. The EVs combine their own secret values and partial private keys to generate their own public and private keys.
- (3)
- The EVs signencrypt their own transaction plans and send them to the surrounding RSUs.
- (4)
- The RSU validates the collected information, consolidates it, and forwards it to the PA. The PA verifies the authenticity and legitimacy of the aggregated information and decrypts it to obtain the specific transaction plan. The PA then calls the smart contract deployed in the BC and independently determines the winning SV based on the principle of price priority. Finally, the initial list of matched transactions is forwarded to the AC.
- (5)
- The AC collects auction information through the PA and obtains the initial list of matched transactions. If a BV wins the auction out of multiple SVs, the AC creates a winner set and transmits it to the corresponding BV for the final selection.
- (6)
- The BV selects the intended SV from the winner set for the transaction. After receiving the transaction plan selected by the BV, the AC deletes the remaining results from the set and sends the plan to the PA.
- (7)
- The successfully matched pair of EVs conducts the transaction based on the agreed-upon transaction information, including price, volume, and location.
- (8)
- Upon transaction completion, both EVs sign the record and submit it to the PA. The PA then validates the record via a consensus algorithm. Once consensus is achieved, the record is uploaded to the BC for review by the EVs, PA, and TRA.
- (9)
- If the TRA receives a complaint, it will check the electricity transactions on the BC to identify malicious EVs and then combine with the KGC to track the real identity and revoke its participation qualification.
3.1.4. Scheme Symbol Definition
3.2. Scheme Detailed Realization
3.2.1. System Parameter Setting
3.2.2. PA and AC Registration (IBC)
3.2.3. EVs and RSU Registration (CLC)
3.2.4. EVs Generate Heterogeneous Signcryption
3.2.5. RSU Generate Aggregated Signcryption
3.2.6. PA Verification and Decryption
3.2.7. V2V Transaction Matching
3.2.8. Transaction Consensus and Upload
3.2.9. Malicious EV Tracking and Revocation
4. Scheme Analysis
4.1. Correctness
- (1)
- The proof of correctness of the partial private keys is shown in Equation (5):
- (2)
- The proof of correctness of the single signcryption verification is as follows, as shown in Equation (6):
- (3)
- The proof of correctness of the aggregated signcryption verification is as follows, as shown in Equation (7):
- (4)
- The proof of the correctness of the ciphertext decryption is as follows, as shown in Equation (8):
- (5)
- The proof of the correctness of pseudonymous tracking is as follows, as shown in Equation (9):
4.2. Security Analysis
4.2.1. Unforgeability
4.2.2. Dual System Parameters
4.2.3. Authentication
4.2.4. Non-Repudiation and Traceability
4.2.5. Resistance to Attacks
- (1)
- Anti-replay attack: Both pseudonymous and signed information have a timestamp, which can be used to determine whether they have expired, thus resisting replay attacks.
- (2)
- Anti-tampering attack: Transaction information needs to verify whether Equation (4) is true. Any tampering will ensure that it cannot pass the verification, so it can resist tampering attacks.
- (3)
- Anti-man-in-the-middle attack: The aggregation process uses the small index test technology, which is known in [30] to be able to resist man-in-the-middle attacks during batch verification.
4.3. Privacy Analysis
4.3.1. Information Confidentiality and Integrity
4.3.2. Anonymity
4.3.3. Unlinkability
5. Performance Analysis
5.1. Computational Analysis
5.2. Communication Analysis
5.3. Security Function Analysis
6. Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Zeng, L.; Li, C.; Li, Z.; Shahidehpour, M.; Zhou, B.; Zhou, Q. Hierarchical bipartite graph matching method for transactive V2V power exchange in distribution power system. IEEE Trans. Smart Grid 2020, 12, 301–311. [Google Scholar] [CrossRef]
- Khaleel, M.; Nassar, Y.; El-Khozondar, H.J.; Elmnifi, M.; Rajab, Z.; Yaghoubi, E.; Yaghoubi, E. Electric vehicles in China, Europe, and the United States: Current trend and market comparison. Int. J. Electr. Eng. Sustain. 2024, 2, 1–20. [Google Scholar]
- Liu, S.; Ni, Q.; Cao, Y.; Cui, J.; Tian, D.; Zhuang, Y. A Reservation-Based Vehicle-to-Vehicle Charging Service Under Constraint of Parking Duration. IEEE Syst. J. 2022, 17, 176–187. [Google Scholar] [CrossRef]
- Zhang, K.; Liu, S.; Cao, Y.; Lin, H.; Kang, J.; Ai, H. A review on optimization of V2V charging services in intelligent transportation environment. Chin. J. Internet Things 2025, 9, 51–69. [Google Scholar]
- Ju, Z.; Li, Y. Vehicle-to-Vehicle Energy Sharing Scheme: A Privacy-Preserving Solution Based on Local Differential Privacy Method. IEEE Netw. 2024, 38, 106–112. [Google Scholar] [CrossRef]
- Zhang, Q.; Su, Y.; Wu, X.; Zhu, Y.; Hu, Y. Electricity trade strategy of regional electric vehicle coalitions based on blockchain. Electr. Power Syst. Res. 2022, 204, 107667. [Google Scholar] [CrossRef]
- Zhang, S.; Zheng, K.; Wang, B. A V2V electricity transaction scheme with privacy protection based on the Internet of vehicles and consortium blockchain. Int. J. Electr. Power Energy Syst. 2024, 157, 109789. [Google Scholar] [CrossRef]
- Wang, Y.; Jia, X.; Bao, Y.; Cao, Y.; Wen, J. Efficient and Provably Secure Offline/Online Heterogeneous Signcryption Scheme for VANETs. IEEE Internet Things J. 2024, 11, 41248–41260. [Google Scholar] [CrossRef]
- Li, Z.; Lei, X.; Shang, Y.; Jia, Y.; Jian, L. A genuine V2V market mechanism aiming for maximum revenue of each EV owner based on non-cooperative game model. J. Clean. Prod. 2023, 414, 137586. [Google Scholar] [CrossRef]
- Liu, H.; Zhang, Y.; Zheng, S.; Li, Y. Electric Vehicle Power Trading Mechanism Based on Blockchain and Smart Contract in V2G Network. IEEE Access 2019, 7, 160546–160558. [Google Scholar] [CrossRef]
- Luo, L.; Feng, J.; Yu, H.; Sun, G. Blockchain-enabled two-way auction mechanism for electricity trading in internet of electric vehicles. IEEE Internet Things J. 2021, 9, 8105–8118. [Google Scholar] [CrossRef]
- Xu, Y.; Wang, S.; Long, C. A Vehicle-to-vehicle Energy Trading Platform Using Double Auction with High Flexibility. In Proceedings of the 2021 IEEE PES Innovative Smart Grid Technologies Europe (ISGT Europe), Espoo, Finland, 18–21 October 2021; pp. 1–5. [Google Scholar]
- Boneh, D.; Gentry, C.; Lynn, B.; Shacham, H. Aggregate and verifiably encrypted signatures from bilinear maps. In Proceedings of the Advances in Cryptology—EUROCRYPT 2003: International Conference on the Theory and Applications of Cryptographic Techniques, Warsaw, Poland, 4–8 May 2003; Proceedings 22. Springer: Berlin/Heidelberg, Germany, 2003. [Google Scholar]
- Zheng, Y. Digital signcryption or how to achieve cost (signature & encryption) ≪ cost (signature)+ cost (encryption). In Proceedings of the Advances in Cryptology—CRYPTO’97: 17th Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 1997. [Google Scholar]
- Chen, H.; Zhou, M.; Hou, Y.; Zhao, J.; Xiao, C.; Guo, P. Certificateless Aggregate Signcryption Scheme with Publicly Verifiable Pairless Operation. J. Front. Comput. Sci. Technol. 2022, 16, 2519. [Google Scholar]
- Dohare, I.; Singh, K.; Ahmadian, A.; Mohan, S.; M, P.K.R. Certificateless Aggregated Signcryption Scheme (CLASS) for Cloud-Fog Centric Industry 4.0. IEEE Trans. Ind. Inform. 2022, 18, 6349–6357. [Google Scholar] [CrossRef]
- Dai, C.; Xu, Z. Pairing-Free Certificateless Aggregate Signcryption Scheme for Vehicular Sensor Networks. IEEE Internet Things J. 2023, 10, 5063–5072. [Google Scholar] [CrossRef]
- Jin, C.; Zhu, H.; Qin, W.; Chen, Z.; Jin, Y.; Shan, J. Heterogeneous online/offline signcryption for secure communication in Internet of Things. J. Syst. Archit. 2022, 127, 102522. [Google Scholar] [CrossRef]
- Ali, I.; Lawrence, T.; Omala, A.A.; Li, F. An Efficient Hybrid Signcryption Scheme with Conditional Privacy-Preservation for Heterogeneous Vehicular Communication in VANETs. IEEE Trans. Veh. Technol. 2020, 69, 11266–11280. [Google Scholar] [CrossRef]
- Niu, S.; Yan, S.; Lu, R.; Zhou, S.; Zhang, M. Privacy-Preserving Heterogeneous Aggregated Signcryption Scheme in V2V Internet of Vehicles. Comput. Eng. 2022, 48, 20–27+36. [Google Scholar] [CrossRef]
- Pan, X.; Jin, Y.; Wang, Z.; Li, F. A pairing-free heterogeneous signcryption scheme for unmanned aerial vehicles. IEEE Internet Things J. 2022, 9, 19426–19437. [Google Scholar] [CrossRef]
- Zhou, M.; Fan, X. Online/offline heterogeneous signcryption scheme with multi-ciphertext equalitytest in internet of vehicles. Chin. J. Telecommun. Sci. 2025, 1–17. Available online: https://link.cnki.net/urlid/11.2103.TN.20250925.1828.002 (accessed on 4 November 2025).
- Li, D.; Guo, Q.; Feng, J. Distributed power transaction privacy settlement model based on blockchain. Power Syst. Technol. 2023, 47, 3608–3624. [Google Scholar]
- Yu, S.; Cao, Q.; Wang, C.; Xu, G.; Ma, H.; Zhu, Y.; Peng, Y.; Jia, Y. Efficient ECC-Based Conditional Privacy-Preserving Aggregation Signature Scheme in V2V. IEEE Trans. Veh. Technol. 2023, 72, 15028–15039. [Google Scholar] [CrossRef]
- Wang, X.; Wei, T.; Kong, L.; He, L.; Wu, F.; Chen, G. ECASS: Edge computing based auxiliary sensing system for self-driving vehicles. J. Syst. Archit. 2019, 97, 258–268. [Google Scholar] [CrossRef]
- Zhong, H.; Chen, L.; Cui, J.; Zhang, J.; Bolodurina, I.; Liu, L. Secure and Lightweight Conditional Privacy-Preserving Authentication for Fog-Based Vehicular Ad Hoc Networks. IEEE Internet Things J. 2022, 9, 8485–8497. [Google Scholar] [CrossRef]
- Aktar, S.; Bärtschi, A.; Badawy, A.H.A.; Eidenbenz, S. A divide-and-conquer approach to Dicke state preparation. IEEE Trans. Quantum Eng. 2022, 3, 3101816. [Google Scholar] [CrossRef]
- Yang, Q.; Li, D.; An, D.; Yu, W.; Fu, X.; Yang, X.; Zhao, W. Towards incentive for electrical vehicles demand response with location privacy guaranteeing in microgrids. IEEE Trans. Dependable Secur. Comput. 2022, 19, 131–148. [Google Scholar] [CrossRef]
- Jiang, W.; Wu, X.; Song, M.; Qin, J.; Jia, Z. A scalable Byzantine fault tolerance algorithm based on a tree topology network. IEEE Access 2023, 11, 33509–33519. [Google Scholar] [CrossRef]
- Pointcheval, D.; Stern, J. Security arguments for digital signatures and blind signatures. J. Cryptol. 2000, 13, 361–396. [Google Scholar] [CrossRef]
- Cremers, C.J. The scyther tool: Verification, falsification, and analysis of securityprotocols: Tool paper. In Proceedings of the International Conference on Computer Aided Verification, Princeton, NJ, USA, 7–14 July 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 414–418. [Google Scholar]
- Imghoure, A.; El-Yahyaoui, A.; Omary, F. ECDSA-based certificateless conditional privacy-preserving authentication scheme in Vehicular Ad Hoc Network. Veh. Commun. 2022, 37, 100504. [Google Scholar]




| Symbol | Meaning |
|---|---|
| SP | Service provider |
| KGC | Key generation center |
| TRA | Trust regulatory authority |
| PKG | Private key generator |
| BV/SV | Buyer/seller electric vehicle |
| RSU | Roadside units |
| PA | Platform agent |
| AC | Auction center |
| BC | Blockchain |
| Symbol | Meaning |
|---|---|
| Bitwise XOR operation | |
| One-way secure hash function | |
| Order and generators of group G | |
| The set of positive integers smaller than q | |
| Elliptic curves over finite fields | |
| System security parameter | |
| KGC’s master private key and public key | |
| TRA’s master private and public key | |
| PKG master key and public key | |
| Electricity transaction information | |
| Heterogeneous signcryption information | |
| M | Aggregated signcryption information |
| Symbol | Meaning | Running Time (ms) |
|---|---|---|
| Biliner pairing operation | 4.2110 | |
| Biliner pairing point addition | 0.0964 | |
| Biliner pairing scalar multiplication | 1.8192 | |
| Elliptic curve point addition | 0.0018 | |
| Elliptic curve scalar multiplication | 0.4420 | |
| Map-to-point hash function | 4.4060 | |
| Small exponent test technique multiplication operation | 0.0278 | |
| Modular exponentiation | 0.0271 |
| Reference | Signcryption (ms) | Single Verification (ms) | Aggregated Verification (ms) | Environment |
|---|---|---|---|---|
| Ref. [18] | CLC → IBC | |||
| Ref. [19] | IBC → PKI | |||
| Ref. [20] | PKI → IBC | |||
| Ref. [21] | IBC → PKI | |||
| Ref. [22] | ) | CLC → PKI | ||
| Our Scheme | CLC → IBC |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, S.; Huang, Y.; Wang, B. A Privacy-Preserving Scheme for V2V Double Auction Power Trading Based on Heterogeneous Signcryption and IoV. Cryptography 2025, 9, 71. https://doi.org/10.3390/cryptography9040071
Zhang S, Huang Y, Wang B. A Privacy-Preserving Scheme for V2V Double Auction Power Trading Based on Heterogeneous Signcryption and IoV. Cryptography. 2025; 9(4):71. https://doi.org/10.3390/cryptography9040071
Chicago/Turabian StyleZhang, Shaomin, Yiheng Huang, and Baoyi Wang. 2025. "A Privacy-Preserving Scheme for V2V Double Auction Power Trading Based on Heterogeneous Signcryption and IoV" Cryptography 9, no. 4: 71. https://doi.org/10.3390/cryptography9040071
APA StyleZhang, S., Huang, Y., & Wang, B. (2025). A Privacy-Preserving Scheme for V2V Double Auction Power Trading Based on Heterogeneous Signcryption and IoV. Cryptography, 9(4), 71. https://doi.org/10.3390/cryptography9040071






