Privacy-Driven Classification of Contact Tracing Platforms: Architecture and Adoption Insights
Abstract
1. Introduction
- How do architectural design choices in digital contact-tracing platforms shape privacy (e.g., PII exposure and unlinkability), security (e.g., verification/notification authenticity), and observed adoption and evolution over time?
- Does a modular six-model classification provide a more informative and actionable understanding of contact-tracing architectures than the traditional centralized–decentralized split, enabling consistent comparison across deployments and clearer guidance for design and policy?
2. Related Work
3. Methodology
3.1. Scoring Transparency, Reliability, and Robustness
- Indicator set: We operationalized the evaluation into 24 indicators grouped under four pillars: Privacy (P1–P6), Security (S1–S6), Functionality (F1–F6), and Governance (G1–G6). Each indicator has a short rubric with three levels: 1 = present/explicit, 0.5 = partial/conditional/unclear, 0 = absent/contradicted. The complete indicator → evidence catalog (codes, definitions, and what qualifies for 1/0.5/0) appears in Appendix A. Indicators and scores are interpreted under the assumptions and adversaries defined in Section 3.2. Specifically, P1 operationalizes G1 (PII secrecy on public channels), P2 operationalizes G3 (unlinkability of rotating tokens), and S1/S4 operationalize G2 (authenticity of case verification and notifications).
- Scoring procedure: For each platform, raters assigned a value in {0, 0.5, 1} per indicator based on publicly documented evidence (e.g., protocol/architecture documents, privacy policies, DPIAs, verification workflows, and, where applicable, open-source repositories or external audits [6,7,39,40,41,42,43,44,46,48,49,50,51,52,53,55,56,57,58,59,60,61]). Missing or ambiguous evidence was scored 0.5 rather than left blank to preserve comparability.
- Aggregation: Pillar scores are simple arithmetic means over indicators within the pillar; the model/platform overall score is the unweighted mean over all 24 indicators:
- Notations: Symbols are defined in Appendix B, Table A8; we use for Cohen’s kappa, for indicator scores, and for sensitivity weights.
- Rater protocol (inter-rater reliability): To test reproducibility, two independent ratings were produced for six representative platforms, one per architectural model in this study (Fully Centralized, Subset Data, Bulletin Board, Indexed Data, Dedicated Servers, Custodian). Each rater coded all 24 indicators for each platform using the rubric in Table A1. We computed Cohen’s per indicator and report macro-averages by pillar.
- Model-level scores (unweighted): Averaging the two raters and then averaging platforms per model yielded model-level scores, presented in Figure 7.
- Sensitivity to indicator weights: To assess robustness to alternative priorities, we drew 1000 random weight vectors from a symmetric over the 24 indicators, recomputed weighted platform scores, and re-ranked models by the means of their platforms.
- Reproducibility artifacts: We provided Table A1 (rubric), Table A5 and Table A6 (rater matrices), and Appendix B (notation/procedures). These artifacts enable exact replication of all numbers reported here.
- Limitations: Our Scoring reflects publicly documented behavior and artifacts, which vary by jurisdiction and time; the inter-rater study covers six representative platforms (model-level inference). Baseline aggregation is unweighted to avoid hidden priorities; we mitigate subjectivity with the 1000-draw sensitivity analysis. We do not present formal cryptographic proofs, code audits, or user-level trials; these are listed as future work with explicit goals/adversaries.
3.2. Security Assumptions and Threat Model
- Assets: PII; rotating proximity tokens (e.g., RPIs/seeds); diagnosis verification codes; integrity of exposure notifications.
- Adversaries: (A1) active network attacker (Dolev–Yao) on public channels; (A2) malicious user attempting bogus uploads or re-identification; (A3) honest-but-curious backend that follows protocols but seeks extra inferences.
- Assumptions: App–server links use modern TLS; platform crypto uses OS-attested key storage and documented primitives; diagnosis codes are bound to lab workflows; ephemeral identifiers rotate as specified; consent gates uploads; no side-channel, baseband, or physical-layer attacks; the adversary does not break standard cryptography.
- Goals: (G1) PII secrecy on public channels; (G2) authenticity of case verification and notifications; (G3) unlinkability of rotating tokens at scale; (G4) data minimization and bounded retention.
- Scope: We evaluate architecture-level protections and governance controls. Formal mechanized proofs, device compromise beyond the user handset, global cross-app fusion, and side-channel/timing attacks are out of scope and noted in Discussion/Limitations.
4. Contact Tracing Platform Corpus and Mapping
5. Capabilities and Attributes Analysis
5.1. CDC Criteria
- Patient Identification: The platform enables the user to report their validated test status, relevant demographic data, data facilitating the connection with supportive services, and the best means of communication.
- Contact Elicitation: Enables the manual import of proximity data.
- Contact Notification: Enables automated notification to community contacts as per proximity, keeping the patient anonymous.
- User Involvement: Awareness spread; motivation created and confidence built.
- Availability: Rapidly deployable or successfully in use by jurisdictions.
- Trustworthiness: is Open source.
- Platform support: Supports cross-platform functionality, caching and offline data entry.
- Data Interoperability: Secure Data transfer over secondary channels (by PHAs).
- Privacy: Authorized data access only.
- Technical support: Develops/vendors provide technical support.
- Vendor Experience: Working experience in a healthcare setting.
- Contact Follow-up: Immediate exposure assessment and relevant notifications to contacts and PHAs.
- Customizability and Localization: Allow some level of customization and choice of language.
| Tools | P.I. | C.I. | C.N. | U.I. | A | T | P.S. | D.I. | P | T.S. | V.E. | C.F. | C | L |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| TraceTogether (OpenTrace) | < | < | < | < | ✦ | ✦ | ✦ | < | < | ✓ | ✓ | < | < | ✓ |
| Coronavirus Disease-19 | < | < | < | < | < | < | < | < | < | ✓ | ✓ | < | < | ✓ |
| Health Code | < | < | < | < | ✦ | < | < | < | < | ✓ | ✓ | < | < | ✖ |
| CovidSafe | < | < | < | < | ✦ | ✦ | ✦ | < | < | ✓ | ✓ | < | < | ✖ |
| StopCovid | < | < | < | < | ✦ | ✦ | ✦ | < | < | ✓ | ✓ | < | < | ✖ |
| Aarogya Setu | < | < | < | < | ✦ | ✦ | ✦ | < | < | ✓ | ✓ | < | < | ✓ |
| GAEN APIs’s Apps | < | < | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✖ | ✖ | ✦ | ✦ | ✖ |
| PACT East Coast | ✦ | ✦ | ✦ | ✦ | < | < | ✦ | ✦ | ✦ | ✖ | ✖ | ✦ | ✦ | ✓ |
| CovidSafe-PACT (West-coast) | ✦ | ✦ | ✦ | ✦ | < | < | ✦ | ✦ | ✦ | ✖ | ✖ | ✦ | ✦ | ✓ |
| SwissCoviD-DP-3T | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✖ | ✖ | ✦ | ✦ | ✓ |
| DP-3T Unlinkable | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✖ | ✖ | ✦ | ✦ | ✓ |
| CovidWatch-TCN | ✦ | ✦ | ✦ | ✦ | ✦ | < | ✦ | ✦ | ✦ | ✖ | ✖ | ✦ | ✦ | ✖ |
| Hamagen | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✦ | ✖ | ✖ | ✦ | ✦ | ✓ |
| COVID Safe Paths | ✦ | ✦ | ✦ | ✦ | < | ✦ | ✦ | ✦ | ✦ | ✖ | ✖ | ✦ | ✦ | ✓ |
5.2. Security Risks and Attacks
- Single point of risk/attack (A3): Centralized storage or broad addressability increases blast radius unless bounded by minimization, retention, role separation, and audit.
- Linkage: Correlating ephemeral identifiers with side information can re-identify users; unlinkability depends on rotation schedules and non-inverting indexes (G3).
- Denial of service (DoS): Floods of well-formed but bogus beacons/uploads drain client/server resources; rate-limits and verification gates mitigate (G2).
- Replay/relay: Re-broadcast of recently valid identifiers can trigger false matches; rotation and timestamp checks reduce impact (G2/G3).
- Traffic analysis: Observing upload/download patterns can reveal status changes; padding, batching, and uniform fetch policies reduce inferences (G1/G3).
5.3. CT Platforms’ Security Guidelines
6. Proposed Frameworks
Our Models
- Fully Centralized Model: The server manages the security keys, generates anonymous IDs, conducts contact risk analysis, and performs notification processes. Such architectures push the risk analysis and notification processes to the centralized server, and health authorities decide the rate of notifications provided by pandemic conditions. The central server plays a key role in carrying out staple functionalities such as storing encrypted PII, generating anonymous TempIDs, risk analysis, and notifications for close contacts. The server is found to be trustworthy in this architecture. Contact tracing applications, that is, TraceTogether (OpenTrace), Coronavirus Disease-19, Health Code, and CovidSafe, were examined as part of these architectures and are illustrated in Figure 1.In this role, the server starts the process by verifying the device through a telephone network. Once the device verification and user registration at the server end are completed, the server shares the encrypted pairs of tempIDs and timestamps (T). Now, the devices start contact tracing by sharing TempID, phone model, and transmitting power (TxP) with any other device in proximity to the same application installed. In addition to these values, the user’s PII is stored in the database of personal nodes. On the other hand, the server keeps the records of the user’s PII, T, TxP, and received signal strength indicator (RSSI). Whenever a user has symptoms of COVID-19, they will trigger Step 3 by sharing their unique TempID, TxP, and RSSI values with the server to perform a risk assessment that will further request the public health authority (e.g., hospital) to verify the patient information by sharing the user’s PII only. Hence, based on the hospital’s verification, the server will notify the user about a self-isolation or “no danger” message.
- 2.
- Subset Data Model: Roles are divided between user devices and servers, and the central server undertakes risk analysis and notifications. It also differs in its level of privacy, based on the type of user data stored at the server end. The protocols also vary in the notification process, that is, how vulnerable users are notified. Users are also expected to check the status of EphIDs regularly with the server to determine if they are exposed to risk. The Robert and Desire protocols and StopCovid and Aarogya Setu applications are classified under a subset data model, as shown in Figure 2.
- 3.
- Custodian Data Model: Based on the Inria-EpiOne protocol, health authorities maintain a database of tokens corresponding to infected users. Here, the server cannot locate vulnerable users with the disease without colluding with healthcare authorities. Similarly, the healthcare provider is not allowed access to randomize contact tokens without colluding further with the server. Even if the server can link a user to specific tokens or seeds in its database, no further information can be drawn. This confines the limit of exposure to the event of collusion or database breach, in contrast to a fully compartmentalized or dedicated server model.Similarly, in Figure 3, the device generates a random key Kt, computes Sidt (metadata, e.g., IP address) and Pidt (time, location), stores them, and uploads Kt to a central server that recomputes Sidt and Pidt in the same way. Again, Ridi is the real ID, for example, name, phone #, etc., and Rtest = Request for a medical test, while Widi = Warning ID about exposure.
- 4.
- Dedicated Servers Model: This is a server architecture designed based on the ConTra Corona protocol. It features a strict separation of tasks under different servers, which are submission, matching, deduplication, notification, and warning servers. Without learning the signed and encrypted public identifiers, health authorities upload them to the server, which looks up the respective registered secret identities and encrypts a pseudonym. The warning server then decrypts this later. The deduplication and submission servers share a symmetrical key. On submission arrival, the submission server marks all individual entries with a random identifier, that is, the deduplication identifier, which is encrypted with the shared symmetric key. The deduplication server decrypts the deduplication identifier and maintains only a random ‘’ for each deduplication identifier. Then, it discards all deduplication identifiers and hands all the individuals ‘’ to the warning server that publishes them to the users for further verification by healthcare.For every time period t, the device generates a random key Kt and computes Sidt (metadata, e.g., IP address) and Pidt (time, location), stores them, and uploads Kt to a central server that recomputes Sidt and Pidt in the same way. Here, Ridi is the real ID, for example, name, phone #, etc., and Rtest = Request for a medical test, while Widi = Warning ID about exposures, as shown in Figure 4.
- 5.
- Bulletin Board Model: In this framework, all the major servers’ centralized roles are transferred to the devices, while the server acts simply as a bulletin board. In addition, it aims to keep users’ identities secret from the central server. Consequently, a server security breach in this architecture would result in less information leakage. The following contact tracing applications come under this category: GAEN APIs Apps, PACT East Coast, CovidSafe-PACT (West-coast), SwissCoviD-DP-3T, Hamagen, and COVID Safe Paths.In addition to the locally stored seed data used to generate chirps, chirp data, including the received time, PII, location, and signal strength, are also stored at personal nodes. At any stage, if a user feels the symptoms of coronavirus, it voluntarily uploads its seeds and a time stamp with the central server. In this framework, the server only keeps the set of seeds and timestamps for infected users and shares them with all the devices that have come into proximity with infected users in the past few days. Regional healthcare authorities can broadcast to users directly with alerts. Overall, the risk verification and notification processes were performed at a personal node. In Figure 5, UId is the user identity information and T(tb = beginning time, te = expiry time).
- 6.
- Indexed Data Model: This design responds to the claims of a decentralized model subjected to linkage and enumeration attacks. Previously, daily keys for infected users were available to all other devices in the network. The server needs to be careful to minimize the chances of false positives, although this drawback has been claimed to be overcome within this design. Additionally, the server can be used to store encrypted pseudonyms and authentication. For instance, unlike typical decentralized structures, only compact seed data (master key, expiry time, etc.) are uploaded to the server rather than the entire list. All seeds that belong to a case can be tested easily, as they are produced and bound to the same master key.Health authorities trigger the process of contact tracing by verifying the illness that allows the user to upload encrypted information. The major difference is that the server does not share the infected users’ seeds directed toward endangered users; rather, the server shares the memory address where the infected seeds are stored at the server’s end. However, the user performs the risk verification process to provide the information that the monitor shares. Contact tracing platforms are believed to use this communication design, that is, CovidWatch–TCN, Pronto-C2, and DP-3T Unlinkable. As illustrated in Figure 6, UIdi is the user identity information, and T(tb = beginning time, te = expiry time).
7. Modular Review
7.1. Qualitative Re-Assessment
7.2. Privacy Properties
- Complete
- Need-basis
- Pseudonyms
- Nothing about data
- No-Consent
- On-demand
- Consent
- Never
- Permanently
- Until requested to delete
- Few weeks
- Two weeks
- Nobody
- PHAs
- User
- Both/Either
- Identity reveals if the central server is compromised
- Identity reveals if any server (multiple) is compromised
- Identity reveals if interacted/interacted/another user’s device is compromised
- Identity is revealed only if the user’s device is compromised
7.3. Architectural Comparison: Privacy and Security Trade-Offs
7.4. Reliability and Robustness Results
- Inter-rater reliability (Cohen’s , macro-average by pillar): Privacy 0.606 (substantial), Security 0.433 (moderate), Governance 0.468 (moderate), Functionality 0.067 (low). The lower for Functionality reflects more variable or under-specified public documentation; we clarified functional indicator definitions and cite evidence per indicator in Appendix A.
- Model-level scores (unweighted mean across 24 indicators): Bulletin Board 0.823; Custodian 0.792; Dedicated Servers 0.771; Indexed 0.708; Subset 0.615; Fully Centralized 0.583. A bar chart of model-level scores appears in Figure 7.
- Sensitivity to indicator weights (1000 draws): Using weight vectors over the 24 indicators, the Top-1 model changed in 20.5% of draws, while the Top-2 set remained the same in 63.4%. Thus, while exact ordering can shift under alternative priorities, the top tier (Bulletin Board/Custodian) remains robust across a wide range of reasonable weightings. Notation and step details appear in Appendix B (Table A7 and Table A8; Procedures B1–B2).
- Security verification status: In this study, we verified architecture-level conformance to G1–G3 under the threat model in Section 3.2 by scoring indicators P1/P2/S1/S4, reporting Cohen’s for inter-rater agreement, and stress-testing conclusions with a 1000-draw weight-sensitivity analysis. We contextualized effectiveness with operational KPIs observable in deployments, verification latency (test → code → notification), notification coverage (share rate and percent of exposed contacts notified), susceptibility to false-positive/relay, interoperability, and retention/exit compliance, when such data are available.
7.5. Trends over Time
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
| Code | Pillar | Indicator | Scoring Rubric (0/0.5/1) |
|---|---|---|---|
| P1 | Privacy | No PII on public channels (BLE/network payloads) | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| P2 | Privacy | Rotating IDs unlinkable across time/devices | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| P3 | Privacy | Data minimization (only needed metadata) | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| P4 | Privacy | Consent-bound uploads & limited scope | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| P5 | Privacy | Explicit retention limits & deletion | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| P6 | Privacy | Local-first matching by default | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| S1 | Security | Verified diagnosis upload (lab/TAN) | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| S2 | Security | Submission validation & deduplication | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| S3 | Security | Replay/relay resistance documented | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| S4 | Security | Notification authenticity (crypto) | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| S5 | Security | Abuse rate-limits/fraud controls | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| S6 | Security | Secure transport & crypto transparency | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| F1 | Functionality | Automated proximity logging (BLE/QR) | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| F2 | Functionality | End-to-end exposure notification workflow | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| F3 | Functionality | Verification & follow-up to testing/care | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| F4 | Functionality | Interoperability/federation/cross-region | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| F5 | Functionality | Offline resilience (queued updates) | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| F6 | Functionality | Opt-out & data deletion by user | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| G1 | Governance | Role separation (PHA vs. infra/keys) | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| G2 | Governance | Access controls & least privilege | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| G3 | Governance | Transparency (DPIA/privacy report) | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| G4 | Governance | Open source or external audit | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| G5 | Governance | Sunset/exit plan documented | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| G6 | Governance | Incident response & disclosure | {“1.0”: “Present/explicit”, “0.5”: “Partial/conditional/unclear”, “0.0”: “Absent/contradicted”} |
| Model | Unweighted Score |
|---|---|
| Bulletin Board Model | 0.822916667 |
| Custodian Data Model | 0.791666667 |
| Dedicated Servers Model | 0.770833333 |
| Indexed Data Model | 0.708333333 |
| Subset Data Model | 0.614583333 |
| Fully Centralized Model | 0.583333333 |
| Platform | Model | Unweighted Score |
|---|---|---|
| SwissCovid (DP-3T/GAEN) | Bulletin Board Model | 0.822917 |
| Epione (UC Berkeley) | Custodian Data Model | 0.791667 |
| ConTra Corona (research) | Dedicated Servers Model | 0.770833 |
| Pronto-C2 (research) | Indexed Data Model | 0.708333 |
| TousAntiCovid (ROBERT) | Subset Data Model | 0.614583 |
| TraceTogether (BlueTrace) | Fully Centralized Model | 0.583333 |
| Code | Kappa | Pillar |
|---|---|---|
| F1 | 0 | Functionality |
| F2 | 0 | Functionality |
| F3 | 0.4 | Functionality |
| F4 | 0 | Functionality |
| F5 | 0 | Functionality |
| F6 | 0 | Functionality |
| G1 | 1 | Governance |
| G2 | 1 | Governance |
| G3 | 0 | Governance |
| G4 | 0.142857143 | Governance |
| G5 | 0.666666667 | Governance |
| G6 | 0 | Governance |
| P1 | 0 | Privacy |
| P2 | 0.666666667 | Privacy |
| P3 | 1 | Privacy |
| P4 | 0.571428571 | Privacy |
| P5 | 0.7 | Privacy |
| P6 | 0.7 | Privacy |
| S1 | 0.6 | Security |
| S2 | 1 | Security |
| S3 | 0 | Security |
| S4 | 1 | Security |
| S5 | 0 | Security |
| S6 | 0 | Security |
IRR Sensitivity Summary
- Macro by pillar
- Functionality: Macro = 0.067
- Governance: Macro = 0.468
- Privacy: Macro = 0.606
- Security: Macro = 0.433
- Baseline model scores (unweighted)
- Bulletin Board Model: 0.823
- Custodian Data Model: 0.792
- Dedicated Servers Model: 0.771
- Indexed Data Model: 0.708
- Subset Data Model: 0.615
- Fully Centralized Model: 0.583
- Sensitivity (1000 draws)
- Baseline Top-1 model: Bulletin Board Model
- Top-1 change rate: 0.205
- Top-2 set stability: 0.634
| Platform | P1 | P2 | P3 | P4 | P5 | P6 | S1 | S2 | S3 | S4 | S5 | S6 | F1 | F2 | F3 | F4 | F5 | F6 | G1 | G2 | G3 | G4 | G5 | G6 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| TraceTogether (BlueTrace) | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 1 | 0.5 | 1 | 0.5 | 0.5 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 0.5 |
| TousAntiCovid (ROBERT early) | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 1 | 0.5 | 1 | 0.5 | 0.5 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 0.5 | 0.5 | 1 | 0.5 | 0.5 | 0.5 |
| SwissCovid (DP-3T/GAEN) | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 0.5 | 1 | 1 | 1 | 0.5 | 0.5 | 1 | 1 | 1 | 0.5 | 1 | 1 | 0.5 | 0.5 |
| Pronto-C2 (research) | 1 | 1 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 1 | 1 | 0.5 | 1 | 1 | 1 | 0.5 | 0.5 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 0.5 |
| ConTra Corona (research) | 1 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 1 | 0.5 | 0.5 | 1 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0 | 0.5 |
| Epione (UC Berkeley) | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 1 | 0.5 | 0.5 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 0.5 |
| Platform | P1 | P2 | P3 | P4 | P5 | P6 | S1 | S2 | S3 | S4 | S5 | S6 | F1 | F2 | F3 | F4 | F5 | F6 | G1 | G2 | G3 | G4 | G5 | G6 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| TraceTogether (BlueTrace) | 0.5 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 0 | 0.5 | 1 | 0.5 | 0.5 | 1 | 1 | 1 | 1 | 0 | 1 | 0 | 0.5 | 0.5 | 0.5 | 0.5 | 0 | 0.5 |
| TousAntiCovid (ROBERT early) | 1 | 0.5 | 0.5 | 1 | 0.5 | 0 | 1 | 0.5 | 1 | 0.5 | 0.5 | 0 | 1 | 0.5 | 0 | 0.5 | 1 | 0 | 0.5 | 0.5 | 1 | 0.5 | 0.5 | 0 |
| SwissCovid (DP-3T/GAEN) | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0.5 | 1 | 1 | 0.5 | 1 | 1 | 1 | 0.5 | 1 | 0.5 | 1 | 1 | 0.5 | 0.5 | 0 | 0.5 | 0.5 |
| Pronto-C2 (research) | 1 | 0.5 | 1 | 1 | 1 | 1 | 0.5 | 0.5 | 0 | 1 | 0.5 | 1 | 1 | 1 | 0.5 | 0.5 | 1 | 1 | 0.5 | 0.5 | 0.5 | 0 | 0 | 0.5 |
| ConTra Corona (research) | 1 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 1 | 1 | 0 | 0.5 | 1 | 0 | 1 | 1 | 1 | 1 | 1 | 0.5 | 1 | 0.5 | 0 | 0.5 |
| Epione (UC Berkeley) | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 | 0.5 | 1 | 0.5 | 1 | 0.5 | 0.5 | 1 | 1 | 0.5 | 0.5 | 1 | 0 | 0.5 | 0.5 |
Appendix B
| Symbol/Term | Meaning | Used in |
|---|---|---|
| PII | Personally identifiable information (e.g., name, phone, national ID) | Threat model; Privacy indicators |
| TempID | Short-lived device pseudonym used for proximity beacons | Centralized/Hybrid models |
| TEK | Temporary Exposure Key; seed from which RPIs are derived | GAEN/DP-3T (Bulletin Board) |
| RPI | Rolling Proximity Identifier broadcast to nearby devices | GAEN/DP-3T (Bulletin Board) |
| Seed | Uplinked value from which observers can recompute RPIs | Bulletin Board/Indexed |
| Index | Pointer or reference to server-side data without raw content | Indexed Data model |
| PID | Pseudonymous account/device ID used for backend association | Centralized/Subset |
| VC | Verification Code bound to a lab result for diagnosis upload | All models with case verification |
| Match (local) | On-device risk computation against downloaded data | Decentralized models |
| Match (server) | Server-side risk computation against uploaded data | Centralized/Hybrid |
| A1/A2/A3 | Adversaries: (A1) network attacker, (A2) malicious user, (A3) honest-but-curious backend | Section 3.2 Threat model |
| G1–G3 | Goals: G1 PII secrecy (public channels); G2 authenticity (verification/notifications); G3 unlinkability (rotating tokens) | Section 3.2; Section 7.4 |
| P1/P2/S1/S4 | Indicators mapping to goals: P1 → G1, P2 → G3, S1/S4 → G2 | Section 3.1 |
| TTL/Retention | Time-to-live/retention window for stored data | Privacy/Governance |
| Gateway | Cross-jurisdiction exchange service for keys/alerts | Interoperability |
| Symbol | Meaning/Definition | Domain/Units |
|---|---|---|
| Number of indicators (here F = 24) | ||
| Set of all platforms; : platforms in model m | set | |
| Score given by rater r for platform i on indicator f | {0,0.5,1} | |
| Consensus score for platform i on indicator f: mean over raters | [0, 1] | |
| Platform unweighted score: | [0, 1] | |
| Model unweighted score: | ||
| Pillar score: mean of indicators within a pillar | [0, 1] | |
| Cohen’s kappa for indicator f between two raters | [−1, 1] | |
| Macro-average kappa over indicators in pillar P | [−1, 1] | |
| Indicator weight vector, | simplex | |
| Sampling scheme for sensitivity (uniform overweight simplex) | — | |
| Weighted platform score: | [0, 1] | |
| Weighted model score: mean of | [0, 1] | |
| Top-1 change rate | Fraction of weight draws where the top model differs from unweighted baseline | [0, 1] |
| Top-2 set stability | Fraction of draws where the top-2 set matches baseline (order ignored) | [0, 1] |
| Verification/notification latency (test → code → notification) | days | |
| Positive users’ share rate (uploaded codes/positives) | [0, 1] | |
| % of exposed contacts notified | [0, 1] |
Appendix B.1. Procedure: Scoring and Aggregation
- Raters assign from public evidence (rubric Table A1).
- Compute consensus by averaging over raters.
- Compute platform score
- For each model m, compute
- Report pillar means and overall means (unweighted baseline).
Appendix B.2. Procedure: Weight-Sensitivity
- Sample
- For each platform, compute
- For each model, compute by averaging platforms.
- Rank models; tally Top-1 change rate and Top-2 set stability across 1000 draws.
Appendix C
Platform Notes
- Tracetogether: TraceTogether is a centralized app launched in Singapore in March 2020 to help control the COVID-19 pandemic and provide comprehensive support for PHAs (Public Health Authorities (PHAs). This open-source app was developed by the Ministry of Health, GOVTECH & SG UNITED, and as of December 2022, it has been installed by over 4.9 million users, accounting for a significant portion of Singapore’s population.TraceTogether records user interactions via Bluetooth using the BlueTrace protocol [19]. The user’s interaction history is stored locally on personal devices and cannot be accessed directly by health authorities. If a user tests positive or is in contact with an infected person, they are prompted to share their encounter history by entering a Personal Identification Number (PIN). Upon authorization, health authorities can access the interaction database using the user’s PII to trace potentially exposed individuals [49]. However, TraceTogether limits data access to PHAs by following strict guidelines and regulations. A temporary and unique identifier, rather than personal details such as name or phone number, was assigned to each user’s device. This identifier is regularly updated to enhance privacy and maintain anonymity throughout the contact-tracing process [19].
- Coronavirus Disease-19: The Coronavirus Disease-19 platform is a centralized contact tracing system utilized in South Korea. It collected and analyzed data from 323 hospitals and various governmental sources to help control the spread of COVID-19. This system gathers data from multiple sources, including security camera footage, mobile base station data, Global Positioning System (GPS), and credit card transaction records [64]. These data streams were used to identify potential hotspots, trace proximities, and map the travel logs of infected individuals.The system discloses patient contact-tracing data, including partially anonymized information such as demographics, infection status, and travel history. However, disclosing these details has raised significant privacy concerns, particularly regarding the balance between public safety and personal privacy [19]. Unlike other platforms, Coronavirus Disease-19 does not provide any self-reporting features. Additionally, the platform code has not been made publicly available, which limits the transparency of its operation. The South Korean government’s use of a multisource data collection approach for contact tracing was highly effective in controlling the spread of COVID-19. However, they continue to face scrutiny of privacy issues.
- Health Code: The Health Code is a centralized contact-tracing system implemented in more than 300 cities across China. Its primary function is to allocate a color-based QR code (green, yellow, or red) to each user to represent their health status and risk of exposure to COVID-19 [41]. The system was operated by Tencent and Ant Group, utilizing a combination of GPS tracking and QR code technology [19], mainly integrated into popular apps, such as Alipay and WeChat. With over 900 million users (~70% of China’s population), it is one of the largest contact tracing systems in the world and is used extensively in urban and rural areas for access control and movement monitoring during pandemics [41].The platform employs a centralized system that assigns users a color-coded QR code (green, yellow, and red) based on their health status and exposure risk, determining their access to public spaces and travel. Using GPS, the system tracks user locations in real-time and analyzes their duration in high-risk areas for more accurate risk assessment [1]. The Health Code collects three key data types: personal information (e.g., national ID numbers and health symptoms), spatial-temporal data from daily activities via Alipay and WeChat, and geolocation data from network operators and GPS. The system has proven effective in controlling the spread of COVID-19 through real-time tracking of user movement patterns and extensive reach; however, it has also sparked significant legal and ethical debates regarding privacy and data protection.
- COVIDSafe: COVIDSafe is a centralized contact tracing (CT) app launched by the Australian government in April 2020 with support from Amazon Web Services (AWS), with a reported user base of over 7 million downloads, reflecting substantial public participation at the national level. The app is available on the Apple Store and Google Play, and its use is voluntary. Upon downloading COVIDSafe, users register with basic details, such as name (or pseudonym), phone number, age, and postal code. The app uses a “digital handshake” through Bluetooth to exchange encrypted reference codes between nearby devices, storing them locally for 21 days, and, with user consent, uploads contact data to a centralized system if the user tests positive for COVID-19 to aid contact tracing [44,60].The app does not track real-time locations; it relies on proximity data to assess the potential exposure [65]. Despite these privacy measures, the app has been criticized for its low effectiveness owing to technical issues, such as Bluetooth limitations on specific devices and reliance on voluntary data uploads. This meant that not all potential exposures were logged or acted upon by health authorities [45,46].
- StopCovid or TousAntiCovid: TousAntiCovid, initially launched as StopCovid in France in June 2020, is a decentralized contact tracing (CT) app aimed at curbing the spread of COVID-19. Developed through a collaborative effort between INRIA (France’s National Institute for Research in Computer Science and Automation) and Fraunhofer in Germany, the app was renamed TousAntiCovid in October 2020 to align with France’s broader anti-pandemic strategy [21,48]. As of its relaunch, TousAntiCovid has been downloaded by more than 5 million users, representing around 7.4% of France’s population [21].The app uses the ROBERT protocol, which was developed for use in decentralized contact-tracing systems. This protocol generates Ephemeral IDs (EphIDs), which are temporary, anonymous identifiers exchanged between devices via Bluetooth when users come into proximity [66]. In the event of exposure, an infected individual’s EphIDs are uploaded to a server in a staggered, randomized sequence to avoid potential tracking [19]. TousAntiCovid prioritizes privacy protection using temporary EphIDs, ensuring that no location data or personal information, such as names or phone numbers, is stored or shared. Data are kept decentralized, and users have complete control over whether to upload their data following a positive COVID test [48].
- Aarogya Setu: Aarogya Setu is a centralized contact-tracing (CT) app launched by the Indian government in April 2020. It was mandatory in several workplaces and containment zones, reflecting its importance in India’s COVID-19 response strategies. Aarogya Setu was developed by the National Informatics Centre (NIC) under the Ministry of Electronics and Information Technology (MeitY). The app has been downloaded more than 214 million times, covering approximately 15.2% of India’s population. Its Android source code was published on 26 May 2020, to address concerns about transparency.The app collects PII, including names, contact information, location data (GPS coordinates), and user self-assessment data. The app also uses data mining to estimate the number of potential COVID-19 cases within a range of 500 m to 10 km from the user’s current location [19]. The app operates on a centralized architecture, where data is uploaded to government-controlled servers for processing and analysis.The transparency of the app improved when its Android source code was made public. Initially, its use was mandatory for individuals in containment zones; however, due to heightened privacy concerns, the mandate was reconsidered and gradually relaxed in subsequent waves of the pandemic, reflecting the need to balance public health measures with individual privacy rights. In addition, despite the government’s efforts to ensure data security, the centralized architecture has raised other issues regarding user consent and data management [21].
- GAEN APIs’ Apps: Apple and Google jointly developed a privacy-preserving exposure notification system in 2020 to support global contact-tracing efforts. This system provides a framework for health organizations to build decentralized apps, such as Canada’s COVID Alert and Germany’s Corona-Warn-App [61]. By April 2021, 65 applications had adopted these APIs globally, implementing the Associated Encrypted Metadata (AEM) approach for exposure notification services [39,40]. The exposure notification system uses Bluetooth Low Energy (BLE) to identify the proximity of two devices. They exchange encrypted random identifiers (EphIDs or Rolling Proximity Identifiers) stored locally on devices. The decentralized architecture ensures that contact logs remain on users’ devices unless they are shared with public health authorities. Unlike traditional contact-tracing systems, Apple and Google cannot access any data collected via these APIs. These APIs have enabled public health authorities worldwide to implement contact tracing with minimal privacy concerns by emphasizing user privacy, decentralization, and seamless cross-platform integration.
- PACT East Coast: The PACT (Private Automated Contact Tracing) East Coast protocol is a decentralized contact tracing system developed through a collaborative research effort involving prestigious institutions such as Massachusetts General Hospital, Boston University, Carnegie Mellon University, Weizmann Institute of Science, SRI International, Brown University, and Lincoln Laboratory [51]. The PACT East Coast results from an interdisciplinary collaboration between these institutions, integrating public health, computer science, and data privacy expertise. The system is not widely deployed as a national platform but is a research-driven prototype for privacy-focused contact tracing. It emphasizes a decentralized structure, ensuring that data remains local on users’ devices unless voluntarily shared. Moreover, the PACT East Coast uses BLE technology to collect anonymous chirps, that is, short signals exchanged between nearby devices. These chirps include the time of receipt and signal strength, which help determine the proximity between devices [50]. Users can also opt to record additional metadata, such as location, in their device’s local log.The app allows users to self-report their contacts, and the data can be synchronized in real-time with public health information systems. The decentralized nature of the platform ensures that users retain control over their data with optional location data collection to enhance the accuracy of exposure detection. Its cross-platform functionality and user-friendly design render it a valuable tool for research and potential public health use. However, its reliance on user-driven data uploads and limited support for PHAs may present challenges for its widespread implementation.
- COVIDSafe-PACT (West-Coast): COVIDSafe-PACT (West Coast) is a decentralized mobile contact tracing (CT) protocol designed by researchers at the University of Washington [7]. Similarly to its East Coast counterpart, the West Coast (PACT) emphasizes privacy-preserving contact tracing by keeping user data encrypted and stored locally on smartphones. Launched in Washington State, the app has been installed by over two million users, covering approximately 26% of the population. The app uses BLE to transmit pseudorandom IDs, anonymizing each device during the proximity exchanges. When two users contact each other, their smartphones broadcast and receive these anonymous IDs, which are stored locally on their devices. Like PACT (East Coast), users are voluntarily asked to upload their encounter logs to public health authorities if they test positive for COVID-19 [51].The West Coast system uses a distinct key-based mechanism to generate pseudorandom IDs. The keychain architecture is more storage-efficient, requiring fewer initial seeds (values used to create pseudoIDs) to be stored compared with the PACT East Coast [50]. This design improves the overall performance and resource management of the app. Public health authorities (PHAs) can also customize apps by introducing new data components or enforcing validation rules for data use. However, its limited language support and lack of technical assistance for public health authorities present potential barriers to its widespread customization and adoption.
- DP3T: The DP3T (Decentralized Privacy-Preserving Proximity Tracing) protocol was designed as a privacy-focused alternative to centralized contact tracing systems and was led by the Swiss Federal Institute of Technology (EPFL). It has since been adopted in various European countries as the foundation for their COVID-19 contact tracing apps, such as Switzerland’s SwissCovid, Spain’s Radar COVID, and Denmark’s Smittestop [57]. DP3T uses Bluetooth-based tracking to generate temporary anonymized identifiers called Ephemeral IDs (EphIDs) exchanged between nearby devices.Each device stores these EphIDs locally, and if a user tests positive for COVID-19, they can voluntarily upload their daily keys to the central server. The server then converts these daily keys into EphIDs, which are cross-checked against the users’ local EphIDs to determine the exposure risk. No identifiable information is shared, and no centralized database stores user movements or contacts. Although the database is unencrypted, the protocol prevents passive tracking and minimizes the risk of third-party surveillance. However, the lack of root detection features may leave an app vulnerable to malicious attacks by applications with root access, potentially exposing the local contact-tracing database.
- SwissCovid-DP-3T: SwissCovid is a decentralized, open-source contact-tracing platform based on the DP3T (Decentralized Privacy-Preserving Proximity Tracing) protocol. Developed by the Federal Office of Public Health (FOPH) in collaboration with Swiss institutions, including the Swiss Federal Institute of Technology (EPFL), the DP3T protocol was adapted for national use in Switzerland. It has garnered over 3.18 million users, representing approximately 37% of the Swiss population [52]. The app has undergone upgrades to address security concerns, including the release of an unlinkable’ version to mitigate Linking and Enumeration attack risks. The updated version ensures that EphIDs are unlinkable and cannot be used to trace or identify individuals even after downloading the daily keys of an infected person [53].The risk assessment is conducted locally on each device, minimizing the need for data sharing with health authorities. However, PHAs can customize apps by adding new data elements and adjusting validation rules. SwissCovid also allows public health authorities to define parameters for infectious range, setting thresholds such as proximity (within 6 feet) and duration (contact for 30 min or more) to determine the potential risk of transmission.
- CovidWatch–TCN: The CovidWatch (TCN Temporary Contact Numbers) is a decentralized, open-source contact-tracing app launched in the United States in partnership with ADHS-Arizona, Stanford University, and the University of Waterloo. The app has been adopted by over 10,000 users, accounting for roughly 10% of the population of the University of Waterloo [54]. Its adoption, although limited, demonstrates the importance of privacy-preserving features in contact-tracing apps, particularly in academic settings. CovidWatch generates TCNs, that is, pseudorandom identifiers, which are exchanged and stored locally on user devices during encounters. When users test positive, they can report their status, enabling others to compare their local logs to match TCNs and receive exposure notifications if a match is found [67].The app preserves privacy by not collecting personal or location data, and logs remain on the users’ devices unless they are voluntarily shared, ensuring that no central authority accesses identities or movements. The app employs end-to-end encryption to protect data exchanges, and users are notified of potential exposure without revealing the identity of the infected person. PHAs can customize features and implement data validation protocols; however, the core privacy-preserving principles of the app remain intact.
- Immuni: Immuni is a decentralized, open-source contact-tracing application based on the Pronto protocol. The Italian government developed it in collaboration with the University of Salerno, the Ministry of Health, and the Ministry for Innovation Technology, and Digitalization. Launched in 2020, the app has garnered over 19 million users, representing approximately 36.7% of Italy’s population [21,43]. A unique feature of Immuni is its use of blockchain techniques to securely share exposure data with PHAs and epidemiologists. Blockchain adds a layer of security by making data tamper-resistant and helps maintain its integrity in the contact tracing process. Despite its multilingual support and additional privacy measures, the app’s adoption rate remained modest compared with Italy’s population until April 2021. This number includes an increase driven by the app’s role in the Green Pass system, which allowed users to store their COVID-19 vaccination certificates. However, despite the many downloads, the app’s effectiveness in contact tracing remains limited because of the lack of widespread adoption and integration with local health authority systems.
- Hamagen: Hamagen, meaning “The Shield” in Hebrew, is a GPS-based contact-tracing app developed by Israel’s Ministry of Health and adopted by over 2.5 million users, representing approximately 26.9% of Israel’s population [19,21]. Hamagen compared a user’s GPS location history with a database of confirmed cases maintained by the Ministry of Health. The app emphasizes individual control over data, enables users to review discrepancies in matched locations, and reports false positives. If users confirm their presence at a reported location, the area is designated as high-risk, and this data is uploaded to the Ministry of Health’s database. Despite its GPS-based contact tracing, the app does not track users in real-time but instead compares location data to past movements stored on the device. Users also have the option to delete their data at any time, although reliance on GPS has raised privacy concerns.
- DESIRE Protocol: The decentralized and secure identification of risks of exposure (DESIRE) protocol was developed through collaboration among several European academic and research institutions, primarily led by researchers at the French National Institute for Research in Computer Science and Automation (INRIA). It is designed as a decentralized contact-tracing solution that focuses on the cryptographic separation between users’ communication data and identities. The protocol uses Private Encounter Tokens (PETs) that are cryptographically generated and exchanged during user interactions. Unlike Ephemeral IDs (EphIDs) directly tied to user identifiers, PETs are anonymized and stored separately, ensuring that no direct link can be made between individuals based on data exchanges [58]. Additionally, client-side encryption ensures that data breaches or losses at the server level do not compromise the user information [58,68]. Furthermore, the protocol prevents the aggregation of social graphs or other patterns from being constructed from users’ proximity data, making it more difficult for malicious actors to analyze communication patterns for tracking purposes.
- COVID Safe Paths: COVID Safe Paths, initially known as Private Kit, is a decentralized contact-tracing application developed by a team at MIT Media Lab led by Associate Professor Ramesh Raskar. Launched in the United States, the app has a user base of approximately 10,000 and continues to operate as a pilot project that focuses on privacy preservation. The app stores tracing histories, including contact device IDs and duration of interactions, in a plain text format within the user’s local database [6]. The app enables users to report their test results and share relevant demographic information, helping public health authorities (PHAs) track the spread of infection. The server is responsible for managing notifications and conducting risk analysis, thereby reducing the likelihood of linkage attacks and enumeration by other users [1,55]. The app also features automatic updates for communities, alerting users within 6 m of a confirmed case for 30 min or more. This feature ensures that critical exposure notifications are delivered while maintaining patient anonymity.
- ConTra Corona: ConTra Corona is a decentralized contact-tracing protocol developed by Germany’s FZI Research Center for Information Technology and the Karlsruhe Institute of Technology. The protocol powers the Corona-Warn-App, launched in March 2021, with a user base of over 48 million installations, covering approximately 58% of Germany’s population. Although ConTra Corona shares some characteristics with hybrid architectures, it significantly diverges from protocols such as DESIRE by focusing on DDH (Decisional Diffie-Hellman) based authentication rather than simply generating IDs [42].Each device in the system generates anonymous IDs that are exchanged via Bluetooth and uploaded to the central server upon detection of disease exposure. Utilizing DDH key exchange prevents linkage attacks, which can compromise the user’s anonymity [69]. Additionally, the protocol mandates that Public Health Authorities (PHAs) verify the authenticity of COVID-19 reports and the identity of individuals uploading their data, thus minimizing the risk of DoS attacks.
- EpiOne: EpiOne is a privacy-preserving contact-tracing protocol developed by a research team led by the University of California at Berkeley, with a modest user base through its app, epione.net Patients, with over 500 users. EpiOne’s emphasis on privacy stems from its ability to prevent interactions and social graph analysis [59]. It uses a private set intersection protocol, that is, a cryptographic method that allows devices to generate and exchange random IDs (tokens) based on a shared seed [21]. The system tracks both sent and received tokens, and if a user’s tests are positive for an infection, they share their seed with public health authorities, who can recreate the tokens sent to the server. By ensuring that neither the server nor the user has complete access to each other’s data, EpiOne aims to safeguard the anonymity of users and prevent the misuse of the contact history.
Appendix D
Security Guidelines and Case Notes
- Security Risks and AttacksOur earlier analysis focused on the characteristics of various tools and assessed the general attributes attached to each tool. We primarily evaluated the user experience with these Contact Tracing (CT) platforms, granting access only to authorized individuals within the scope of privacy considerations, which only superficially addressed privacy properties. Although this approach offers insights into the quality of tools based on user experience, it needs to effectively highlight the efficacy of CT systems in specific healthcare jurisdictions, particularly concerning privacy and security issues. To address this, we identified potential attacks that could target these systems, thereby posing threats to privacy and security. These findings are detailed and summarized in Table 3 and Table 4, which provide a comprehensive overview of vulnerabilities across different platforms.
- Single Point of Risk/Attack: A primary concern among users revolves around the potential misuse of their data by government officials for purposes other than contact tracing. For instance, despite the initial assurance that Singapore’s contact tracing app would be solely used for combating COVID-19, it was later reported that police could access its data for criminal investigations [70]. To address these privacy concerns, specific app designs and architectures, such as PACT East Coast, COVID-Safe PACT, DP-3T Unlinkable, and the PRONTO-C2 protocol, aim to anonymize user data. They generate unidentified IDs for devices, thereby preventing servers from linking them to individuals’ personal data. These distributed designs confine data management to the users’ smartphones, keeping PII off the server and allowing users to assess their health status independently. This decentralized approach reduces the risk of a single point of failure, such as a compromised central server [71,72,73]. Moreover, the decentralized architecture typically involves a minimally used central server, mainly for broadcasting and functioning as a middleware between patients and hospitals. As a result, it is less susceptible to a range of server-based attacks, thus enhancing overall data security.
- Linkage Attack: Here, a client attempts to de-anonymize another client’s PII by correlating the anonymous data transmitted during communication with the additional data collected through secondary channels. This method of associating an obscure ID with a client’s known PII is called a linkage attack. For instance, CovidWatch, which adopts a decentralized approach, logs interactions and includes details such as day, time, duration, location, and gender. Suppose that a user receives a notification of potential exposure. In this case, they can identify the person they were exposed to by matching their interaction records with the time and duration indicated in the received chirps. In centralized systems, such as the Health Code, it is more feasible to de-anonymize close interactions. However, identifying a specific case is challenging because app users need access to a set of pseudonymous/Temp IDs for comparison. However, identification is possible when a quarantined user receives a contact alert after meeting only a single person. In such cases, the pseudoIDs can be linked to a specific user by cross-referencing factors such as the advertised mobile model number, contact duration, and uniqueness of the interaction [18,19,74,75]. Hybrid protocols such as DESIRE are typically considered unlinkable and do not share Private Encounter Tokens (PETs) from infected clients with other users. They conduct risk analysis and send alerts, such as centralized systems, mitigating the risks of linkage attacks and preserving anonymity.
- Denial Of Service (DOS): This attack aims to deplete the resources (such as power and bandwidth) available in a system, which can be a client device or server. In this context, we consider a scenario in which an attacker introduces false interaction chirps into a contact-tracing ecosystem. Although the server initially processes these fake interactions in a centralized architecture, it discards them after completing the validity check. Conversely, verifying the authenticity of the received chips in a decentralized system is challenging if they are correctly formatted to appear legitimate. This inability to effectively filter out false data can lead to resource drainage and potential disruptions in the decentralized contact tracing process.
- Replay/Relay Attack: This type of attack is considered one of the simplest methods to execute against users of a contact-tracing (CT) application. An attacker can intercept and rebroadcast the content transmitted by a user, either at the exact location to extend its reach or later. This is known as a replay attack, mainly when the bogus content carries a legitimate identifier such as a TempID or chirp. Otherwise, it falls under a DoS attack. In this context, a chirp is usually created using a pseudorandom function, incorporating TempID and the current time. In centralized applications such as BlueTrace, where pseudoIDs have a short lifespan (typically 15 min), a replay attack can be executed before TempID expires. If someone who receives this rebroadcast message later tests positive for COVID-19, the original sender might be falsely identified as a close contact and advised to undergo testing, leading to a false positive. In decentralized apps, such as PACT and DP3T, the systems check the shared timestamp of all stored chirps against the creation time of each rebroadcast chirp. They are likely to accept only those chirps where the timestamps match, a measure to guard against replay attacks. However, an attack can occur a minute before the chirp expires. In centralized designs, the victim is the originator of the replayed message. By contrast, in decentralized models, the victims are multiple recipients of the replayed message. Hybrid models, such as Inria-EpiOne, still have vulnerabilities to relay attacks because symmetrical data could exist in the PET table managed by two hosts with malicious intent. However, because only one user receives the replayed EphID and the calculated PETs are only accessible to the recipient, replay attacks are less feasible. If the recipient of a replayed system tests positive, the replayed PETs cannot be matched with any other PET, further reducing the risk of successful replay attacks.
- Traffic Analysis Attack: In this scenario, malicious entities, whether individuals, applications, or organizations, aim to exploit the contact-tracing system by capturing temporary identifiers and seeds from recorded interactions. They then attempted to link these identifiers or chirps to additional information obtained through other means. Furthermore, an adversary that is capable of intercepting messages initiates a traffic analysis attack. The attacker’s goal is to identify users who have tested positive for COVID-19, because only those confirmed as infected are authorized to upload their seeds to the server. This attack leverages the observation of network traffic patterns to infer sensitive information, explicitly targeting the identification of infected individuals in the contact-tracing process.
- 2.
- CT Platforms’ Security GuidelinesBased on our ad hoc analysis, this study aims to shed light on additional findings concerning security vulnerabilities in contact-tracing (CT) platforms and guide the discussion on general security guidelines for these systems. For instance, the TraceTogether app, which utilizes a centralized approach, faces significant privacy risks. A notable concern in its design is the inclusion of a support repository for third-party customers, specifically, the Zendesk SDK. This setup enables remote debugging from WebView, thereby creating a potential security loophole. An attacker can exploit this to dump content from WebView, posing a threat to the privacy and security of the app’s users [49]. When users input sensitive information, such as passwords and personal identity details, into a WebView with debugging enabled, this presents an opportunity for hackers. They can employ remote debugging tools to inspect all elements on a webpage, potentially accessing private data. As a security measure for TraceTogether, it is crucial to ensure that WebView is not left in debugging mode in the device’s release version.On the other hand, Coronavirus Disease-19 Solutions that utilize GPS, a characteristic of centralized systems, may encounter risks associated with mass surveillance [56]. The foundation of an app’s security is laid during the development phase. Development teams must adhere to mobile security guidelines such as those provided by the Open Web Application Security Project (OWASP) Mobile Security Testing Guide [26]. These guidelines can significantly enhance an app’s security posture and protect it against potential threats.The provisional legislative system in CovidSafe does a creditworthy job of answering privacy issues, but is not yet entirely defensive. This system relies on the right of the courts to issue warrants to access and review data obtained by the application, surveillance powers, preservation of information, and distribution to local law enforcement authorities. There are broader concerns regarding users’ willingness to consent to using their data by contact-tracing apps. For example, although StopCovid is an open-source application, this openness means that its source code is accessible to the public. This accessibility, if not properly managed and secured, can expose software to various threats. An attacker may exploit this to discreetly breach the app processes. To safeguard against such vulnerabilities, protection strategies must extend beyond merely modifying the code. This includes altering the app’s data and resources, updating the device APIs with which it interacts, and dynamically managing the contents of the app’s memory [69,76]. These comprehensive measures are essential to ensure the security and integrity of the application, particularly given its open-source nature.Although Aarogya Setu effectively tracks a user’s location and requires constant Bluetooth access, this can be intrusive from a security and privacy standpoint. Similarly, cooperative protocols such as West Coast (PACT) are susceptible to linkage and enumeration attacks. This vulnerability arises because seeds from compromised users are sent to the registry and shared with others. These seeds can be used to link identity to anonymous data. In contrast, the DP3T architecture, which recognizes the susceptibility of decentralized systems to such attacks, implements measures such as database encryption and root detection [57]. This approach enhances the security of sensitive data, particularly at the startup of an application, to prevent data breaches and protect the database from unauthorized extraction. However, if the database containing timestamps and contact IDs were compromised, it could be exploited for adversary linkage attacks. With sufficient data gathered, attackers can use this information to track movements and identify individuals through linkage attacks. This scenario underscores the importance of robust security measures in contact-tracing apps to protect against potential breaches and misuse of sensitive data [64].In addition, the DESIRE server takes on the role of risk mitigation and notification, eliminating the potential risks associated with clients in decentralized versions that could lead to Enumeration and Linkage attacks. This centralized approach helps bolster security. However, COVID Safe Paths has faced several vulnerabilities, as highlighted in a published report on 14 May 2020, in CVE-2020-12857. The COVID Safe app incorrectly retains GATT characteristics, such as Temp-IDs, for an extended period rather than regularly clearing them out [46,60]. This oversight means that if an attacker intercepts the data during a transaction, they can potentially monitor the transaction in the long run, posing a security risk to users. This underscores the importance of promptly clearing sensitive data to enhance the security of contact tracing apps.
References
- Mann, M.; Mitchell, P.; Foth, M. Between surveillance and technological solutionism: A critique of privacy-preserving apps for COVID-19 contact-tracing. New Media Soc. 2024, 26, 4099–4117. [Google Scholar] [CrossRef]
- Gvili, Y. Security Analysis of the COVID-19 Contact Tracing Specifications by Apple Inc. and Google Inc. 2020, 2020/428. Available online: https://eprint.iacr.org/2020/428 (accessed on 24 October 2024).
- Liu, J.K.; Au, M.H.; Yuen, T.H.; Zuo, C.; Wang, J.; Sakzad, A.; Luo, X.; Li, L.; Choo, K.K.R. Privacy-Preserving COVID-19 Contact Tracing App: A Zero-Knowledge Proof Approach. Cryptology ePrint Archive. 2020. Available online: https://eprint.iacr.org/2020/528 (accessed on 23 October 2024).
- Simko, L.; Calo, R.; Roesner, F.; Kohno, T. COVID-19 Contact Tracing and Privacy: Studying Opinion and Preferences. arXiv 2020, arXiv:2005.06056. [Google Scholar] [CrossRef]
- Fitzsimons, J.K.; Mantri, A.; Pisarczyk, R.; Rainforth, T.; Zhao, Z. A note on blind contact tracing at scale with applications to the COVID-19 pandemic. In Proceedings of the 15th International Conference on Availability, Reliability and Security, Dublin, Ireland, 25–28 August 2020; ACM: New York, NY, USA, 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Contact Tracing Is Failing in Many States. Here’s Why—The New York Times. Available online: https://www.nytimes.com/2020/07/31/health/covid-contact-tracing-tests.html (accessed on 24 October 2024).
- Chan, J.; Foster, D.; Gollakota, S.; Horvitz, E.; Jaeger, J.; Kakade, S.; Kohno, T.; Langford, J.; Larson, J.; Sharma, P.; et al. PACT: Privacy Sensitive Protocols and Mechanisms for Mobile Contact Tracing. arXiv 2020, arXiv:2004.03544. [Google Scholar] [CrossRef]
- Williams, S.N.; Armitage, C.J.; Tampe, T.; Dienes, K. Public attitudes towards COVID-19 contact tracing apps: A UK-based focus group study. Health Expect. 2021, 24, 377–385. [Google Scholar] [CrossRef] [PubMed]
- Oliver, N.; Lepri, B.; Sterly, H.; Lambiotte, R.; Deletaille, S.; De Nadai, M.; Letouzé, E.; Salah, A.A.; Benjamins, R.; Cattuto, C.; et al. Mobile phone data for informing public health actions across the COVID-19 pandemic life cycle. Sci. Adv. 2020, 6, eabc0764. [Google Scholar] [CrossRef]
- Martin, T.; Karopoulos, G.; Hernández-Ramos, J.L.; Kambourakis, G.; Fovino, I.N. Demystifying COVID-19 Digital Contact Tracing: A Survey on Frameworks and Mobile Apps. Wirel. Commun. Mob. Comput. 2020, 2020, 8851429. [Google Scholar] [CrossRef]
- Bulchandani, V.B.; Shivam, S.; Moudgalya, S.; Sondhi, S.L. Digital herd immunity and COVID-19. Phys. Biol. 2021, 18, 045004. [Google Scholar] [CrossRef]
- PRIME PubMed|Impact of Delays on Effectiveness of Contact Tracing Strategies for COVID-19: A Modelling Study. Available online: https://www.unboundmedicine.com/medline/citation/32682487/Impact_of_delays_on_effectiveness_of_contact_trac-ing_strategies_for_COVID_19 (accessed on 23 October 2024).
- Reichert, L.; Brack, S.; Scheuermann, B. Privacy-Preserving Contact Tracing of COVID-19 Patients. Cryptology ePrint Archive. 2020. Available online: https://eprint.iacr.org/2020/375 (accessed on 24 October 2024).
- Dar, A.B.; Lone, A.H.; Zahoor, S.; Khan, A.A.; Naaz, R. Applicability of mobile contact tracing in fighting pandemic (COVID-19): Issues, challenges and solutions. Comput. Sci. Rev. 2020, 38, 100307. [Google Scholar] [CrossRef]
- Hekmati, A.; Ramachandran, G.; Krishnamachari, B. CONTAIN: Privacy-oriented contact tracing protocols for epidemics. In Proceedings of the 2021 IFIP/IEEE International Symposium on Integrated Network Management (IM), Bordeaux, France, 17–21 May 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 872–877. Available online: https://ieeexplore.ieee.org/abstract/document/9464051/ (accessed on 23 October 2024).
- Zhang, H.; She, D.; Qian, Z. Android Root and its Providers: A Double-Edged Sword. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; ACM: New York, NY, USA, 2015; pp. 1093–1104. [Google Scholar] [CrossRef]
- Geist, D.; Nigmatullin, M.; Bierens, R. Jailbreak/Root Detection Evasion Study on iOS and Android. MSc System and Network Engineering. 2016. Available online: https://rp.os3.nl/2015-2016/p51/report.pdf (accessed on 23 October 2024).
- Cho, H.; Ippolito, D.; Yu, Y.W. Contact Tracing Mobile Apps for COVID-19: Privacy Considerations and Related Trade-offs. arXiv 2020, arXiv:2003.11511. [Google Scholar] [CrossRef]
- Sun, R.; Wang, W.; Xue, M.; Tyson, G.; Camtepe, S.; Ranasinghe, D. Vetting Security and Privacy of Global COVID-19 Contact Tracing Applications. arXiv 2020, arXiv:2006.10933. [Google Scholar] [CrossRef]
- Krishnan, A.S.; Yang, Y.; Schaumont, P. Risk and Architecture factors in Digital Exposure Notification. 2020, 2020/582. Available online: https://eprint.iacr.org/2020/582 (accessed on 24 October 2024).
- Ahmed, N.; Michelin, R.A.; Xue, W.; Ruj, S.; Malaney, R.; Kanhere, S.S.; Seneviratne, A.; Hu, W.; Janicke, H.; Jha, S.K. A survey of COVID-19 contact tracing apps. IEEE Access 2020, 8, 134577–134601. [Google Scholar] [CrossRef]
- Alanzi, T. A Review of Mobile Applications Available in the App and Google Play Stores Used During the COVID-19 Outbreak. J. Multidiscip. Healthc. 2021, 14, 45–57. [Google Scholar] [CrossRef]
- Vinuesa, R.; Theodorou, A.; Battaglini, M.; Dignum, V. A socio-technical framework for digital contact tracing. Results Eng. 2020, 8, 100163. [Google Scholar] [CrossRef]
- Jacob, S.; Lawarée, J. The adoption of contact tracing applications of COVID-19 by European governments. Policy Des. Pract. 2020, 4, 44–58. [Google Scholar] [CrossRef]
- Abtahi, A.; Payer, M.; Aminifar, A. DP-ACT: Decentralized Privacy-Preserving Asymmetric Digital Contact Tracing. Proc. Priv. Enhancing Technol. (PoPETs) 2024, 2024, 330–342. [Google Scholar] [CrossRef]
- Akinbi, A.; Forshaw, M.; Blinkhorn, V. Contact tracing apps for the COVID-19 pandemic: A systematic literature review of challenges and future directions for neo-liberal societies. Health Inf. Sci. Syst. 2021, 9, 18. [Google Scholar] [CrossRef]
- Shahroz, M.; Ahmad, F.; Younis, M.S.; Ahmad, N.; Boulos, M.N.K.; Vinuesa, R.; Qadir, J. COVID-19 digital contact tracing applications and techniques: A review post initial deployments. Transp. Eng. 2021, 5, 100072. [Google Scholar] [CrossRef]
- Ho, K.K.; Chiu, D.K.; Sayama, K.L. When privacy, distrust, and misinformation cause worry about using COVID-19 contact-tracing apps. IEEE Internet Comput. 2023, 27, 7–12. [Google Scholar] [CrossRef]
- Jalabneh, R.; Syed, H.Z.; Pillai, S.; Apu, E.H.; Hussein, M.R.; Kabir, R.; Arafat, S.Y.; Majumder, M.A.A.; Saxena, S.K. Use of Mobile Phone Apps for Contact Tracing to Control the COVID-19 Pandemic: A Literature Review. SSRN, 2020; Preprint. [Google Scholar] [CrossRef]
- Kuo, K.-M. Antecedents Predicting Digital Contact Tracing Acceptance: A Systematic Review and Meta-Analysis. BMC Med. Inform. Decis. Mak. 2023, 23, 212. [Google Scholar] [CrossRef]
- Digital Contact Tracing Applications During COVID-19: A Scoping Review About Public Acceptance. Available online: https://www.mdpi.com/2227-9709/8/3/48 (accessed on 24 October 2024).
- Bito, S.; Hayashi, Y.; Fujita, T.; Takahashi, I.; Arai, H.; Yonemura, S. Survey of Citizens’ Preferences for Combined Contact Tracing App Features During a Pandemic: Conjoint Analysis. JMIR Public Health Surveill. 2024, 10, e53340. [Google Scholar] [CrossRef]
- Palmer, A.; Sharma, S.; Nagpal, J.; Kimani, V.; Mai, F.; Ahmed, Z. Identifying Barriers to the Adoption of Digital Contact Tracing Apps in England: Semistructured Interview Study with Professionals Involved in the Pandemic Response. JMIR Form. Res. 2024, 8, e56000. [Google Scholar] [CrossRef] [PubMed]
- Elers, P.; Emery, T.; Derrett, S.; Chambers, T. Barriers to Adopting Digital Contact Tracing for COVID-19: Experiences in New Zealand. Health Expect. 2024, 27, 395–404. [Google Scholar] [CrossRef] [PubMed]
- Geenen, C.; Raymenants, J.; Gorissen, S.; Thibaut, J.; McVernon, J.; Lorent, N.; André, E. Individual-Level Analysis of Digital Proximity Tracing for COVID-19 in Belgium Highlights Major Bottlenecks. Nat. Commun. 2023, 14, 6897. [Google Scholar] [CrossRef] [PubMed]
- Kendall, M.; Tsallis, D.; Wymant, C.; Di Francia, A.; Balogun, Y.; Didelot, X.; Ferretti, L.; Fraser, C. Epidemiological Impacts of the NHS COVID-19 App in England and Wales Throughout Its First Year. Nat. Commun. 2023, 14, 1005. [Google Scholar] [CrossRef]
- Leng, T.; Hill, E.M.; Keeling, M.J.; Tildesley, M.J.; Thompson, R.N. The Effect of Notification Window Length on the Epidemio-logical Impact of COVID-19 Contact-Tracing Mobile Applications. Commun. Med. 2022, 2, 69. [Google Scholar] [CrossRef]
- Masel, J.; Petrie, J.I.M.; Bay, J.; Ebbers, W.; Sharan, A.; Leibrand, S.M.; Gebhard, A.; Zimmerman, S. Combatting SARS-CoV-2 with Digital Contact Tracing and Notification: Navigating Six Points of Failure. JMIR Public Health Surveill. 2023, 9, e49560. [Google Scholar] [CrossRef]
- Privacy-Preserving Contact Tracing—Apple and Google. Apple. Available online: https://www.apple.com/covid19/contacttracing (accessed on 24 October 2024).
- Exposure Notifications: Helping Fight COVID-19—Google. Available online: https://blog.google/inside-google/company-announcements/update-exposure-notifications/ (accessed on 16 September 2025).
- Liang, F. COVID-19 and Health Code: How Digital Platforms Tackle the Pandemic in China. Soc. Media + Soc. 2020, 6, 2056305120947657. [Google Scholar] [CrossRef]
- Beskorovajnov, W.; Dörre, F.; Hartung, G.; Koch, A.; Müller-Quade, J.; Strufe, T. ConTra Corona: Contact Tracing against the Coronavirus by Bridging the Centralized–Decentralized Divide for Stronger Privacy. In Advances in Cryptology—ASIACRYPT; Tibouchi, M., Wang, H., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2021; Volume 13091, pp. 665–695. [Google Scholar] [CrossRef]
- Avitabile, G.; Botta, V.; Iovino, V.; Visconti, I. Towards Defeating Mass Surveillance and SARS-CoV-2: The Pronto-c2 Fully Decentralized Automatic Contact Tracing System. Cryptology ePrint Archive. 2020. Available online: https://eprint.iacr.org/2020/493 (accessed on 24 October 2024).
- COVIDSafe. GitHub. Available online: https://github.com/AU-COVIDSafe (accessed on 23 October 2024).
- Cohney, S.; Cheong, M. COVID Down Under: Where did Australia’s pandemic apps go wrong? In Proceedings of the 2023 IEEE International Symposium on Ethics in Engineering, Science, and Technology (ETHICS), West Lafayette, IN, USA, 18–20 May 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–8. Available online: https://ieeexplore.ieee.org/abstract/document/10154912/ (accessed on 24 October 2024).
- COVIDSafe Assessment 3: COVIDSafe Application Functionality, Privacy Policy and Collection Notices|OAIC. Available online: https://www.oaic.gov.au/privacy/privacy-assessments-and-decisions/privacy-assessments/covidsafe-assessment-3-covidsafe-application-functionality,-privacy-policy-and-collection-notices (accessed on 24 October 2024).
- StopCOVID: France’s Controversial Tracing App Ready by June, Government Says|Euronews. Available online: https://www.euronews.com/my-europe/2020/04/29/coronavirus-french-mps-approve-covid-19-tracing-app-despite-privacy-concerns (accessed on 23 October 2024).
- TousAntiCovid Sources GitLab. GitLab. Available online: https://gitlab.inria.fr/stopcovid19 (accessed on 24 October 2024).
- Opentrace-Calibration/Trial Methodologies.md at Master Opentrace-Community/Opentrace-Calibration. GitHub. Available online: https://github.com/opentrace-community/opentrace-calibration/blob/master/Trial%20Methodologies.md (accessed on 23 October 2024).
- Rivest, R.L.; Callas, J.; Canetti, R.; Esvelt, K.; Gillmor, D.K.; Kalai, Y.T.; Lysyanskaya, A.; Norige, A.; Raskar, R.; Shamir, A.; et al. The PACT protocol specification. In Private Automated Contact Tracing Team; Tech. Rep. 0.1; MIT: Cambridge, MA, USA, 2020. [Google Scholar]
- PACT: Private Automated Contact Tracing. Available online: https://github.com/mitll/PACT (accessed on 16 September 2025).
- Swiss Tracing App Goes on Trial. ETH Zurich. Available online: https://ethz.ch/en/news-and-events/eth-news/news/2020/05/swiss-covid-app.html (accessed on 24 October 2024).
- Vaudenay, S.; Vuagnoux, M. Analysis of Swisscovid. 2020. Available online: https://infoscience.epfl.ch/record/278048 (accessed on 24 October 2024).
- Covid Watch. GitHub. Available online: https://github.com/covidwatchorg (accessed on 24 October 2024).
- Raskar, R.; Nadeau, G.; Werner, J.; Barbar, R.; Mehra, A.; Harp, G.; Leopoldseder, M.; Wilson, B.; Flakoll, D.; Vepakomma, P.; et al. COVID-19 Contact-Tracing Mobile Apps: Evaluation and Assessment for Decision Makers. arXiv 2020, arXiv:2006.05812. [Google Scholar] [CrossRef]
- Kang, H.; Kwon, S.; Kim, E. COVID-19 Health System Response Monitor: Republic of Korea. 2020. Available online: https://apps.who.int/iris/bitstream/handle/10665/337371/9789290228219-eng.pdf (accessed on 24 October 2024).
- DP^3T. GitHub. Available online: https://github.com/DP-3T (accessed on 24 October 2024).
- Bielova, N.; Boutet, A.; Castelluccia, C.; Cunche, M.; Lauradoux, C.; Le Métayer, D.; Roca, V. DESIRE: A Third Way for a European Exposure Notification System (SUMMARY-EN). Ph.D. Thesis, Inria, Le Chesnay-Rocquencourt, France, 2020. Available online: https://inria.hal.science/hal-02570172/ (accessed on 24 October 2024).
- Trieu, N.; Shehata, K.; Saxena, P.; Shokri, R.; Song, D. Epione: Lightweight Contact Tracing with Strong Privacy. arXiv 2020, arXiv:2004.13293. [Google Scholar] [CrossRef]
- COVIDSafe Legislation|Attorney-General’s Department. Available online: https://www.ag.gov.au/rights-and-protections/privacy/covidsafe-legislation (accessed on 23 October 2024).
- Project Aurora: A New Open Source Solution for the Google Apple Exposure Notification API. Available online: https://www.pathcheck.org/blogs/en/blog/a-new-open-source-solution-for-the-google-apple-exposure-notification-api (accessed on 16 September 2025).
- Preliminary Criteria for the Evaluation of Digital Contact Tracing Tools for COVID-19: Preliminary Criteria for the Evaluation of Digital Contact Tracing Tools for COVID-19. Available online: https://stacks.cdc.gov/view/cdc/87515 (accessed on 24 October 2024).
- Path-Check/Safeplaces-Dct-App. (12 October 2024). TypeScript. PathCheck Foundation. Available online: https://github.com/Path-Check/safeplaces-dct-app (accessed on 24 October 2024).
- Shen, Y.; Wang, F.; Jin, H. Defending against user identity linkage attack across multiple online social networks. In Proceedings of the 23rd International Conference on World Wide Web, Seoul, Republic of Korea, 7–11 April 2014; ACM: New York, NY, USA, 2014; pp. 375–376. [Google Scholar] [CrossRef]
- COVIDSafe. Available online: https://covidsafe.cs.washington.edu/ (accessed on 24 October 2024).
- ROBERT-Proximity-Tracing/Documents. (20 May 2024). HTML. ROBERT—ROBust and Privacy-presERving Proximity Tracing Protocol. Available online: https://github.com/ROBERT-proximity-tracing/documents (accessed on 23 October 2024).
- TCNCoalition/TCN. (8 July 2024). Rust. TCN Coalition. Available online: https://github.com/TCNCoalition/TCN (accessed on 24 October 2024).
- COVID Contact Tracing App Report. Avira. Available online: https://www.avira.com/en/covid-contact-tracing-app-report (accessed on 24 October 2024).
- Zimmermann, B.M.; Fiske, A.; Prainsack, B.; Hangel, N.; McLennan, S.; Buyx, A. Early perceptions of COVID-19 contact tracing apps in German-speaking countries: Comparative mixed methods study. J. Med. Internet Res. 2021, 23, e25525. [Google Scholar] [CrossRef]
- Abbas, R.; Michael, K. COVID-19 contact trace app deployments: Learnings from Australia and Singapore. IEEE Consum. Electron. Mag. 2020, 9, 65–70. [Google Scholar] [CrossRef]
- Bengio, Y.; Janda, R.; Yu, Y.W.; Ippolito, D.; Jarvie, M.; Pilat, D.; Struck, B.; Krastev, S.; Sharma, A. The need for privacy with public digital contact tracing during the COVID-19 pandemic. Lancet Digit. Health 2020, 2, e342–e344. [Google Scholar] [CrossRef]
- McLachlan, S.; Lucas, P.; Dube, K.; Hitman, G.A.; Osman, M.; Kyrimi, E.; Neil, M.; Fenton, N.E. Bluetooth Smartphone Apps: Are they the most private and effective solution for COVID-19 contact tracing? arXiv 2020, arXiv:2005.06621. [Google Scholar] [CrossRef]
- Li, T.; Faklaris, C.; King, J.; Agarwal, Y.; Dabbish, L.; Hong, J.I. Decentralized is not risk-free: Understanding public perceptions of privacy-utility trade-offs in COVID-19 contact-tracing apps. arXiv 2020, arXiv:2005.11957. [Google Scholar]
- Browne, C.; Gulbudak, H.; Webb, G. Modeling contact tracing in outbreaks with application to Ebola. J. Theor. Biol. 2015, 384, 33–49. [Google Scholar] [CrossRef] [PubMed]
- Sinha, P.; Paterson, A.E. Contact tracing: Can ‘Big tech’come to the rescue, and if so, at what cost? EClinicalMedicine 2020, 24, 100412. Available online: https://www.thelancet.com/journals/eclinm/article/PIIS2589-5370(20)30156-5/fulltext (accessed on 23 October 2024). [CrossRef] [PubMed]
- Shubina, V.; Holcer, S.; Gould, M.; Lohan, E.S. Survey of decentralized solutions with mobile devices for user location tracking, proximity detection, and contact tracing in the COVID-19 era. Data 2020, 5, 87. [Google Scholar] [CrossRef]

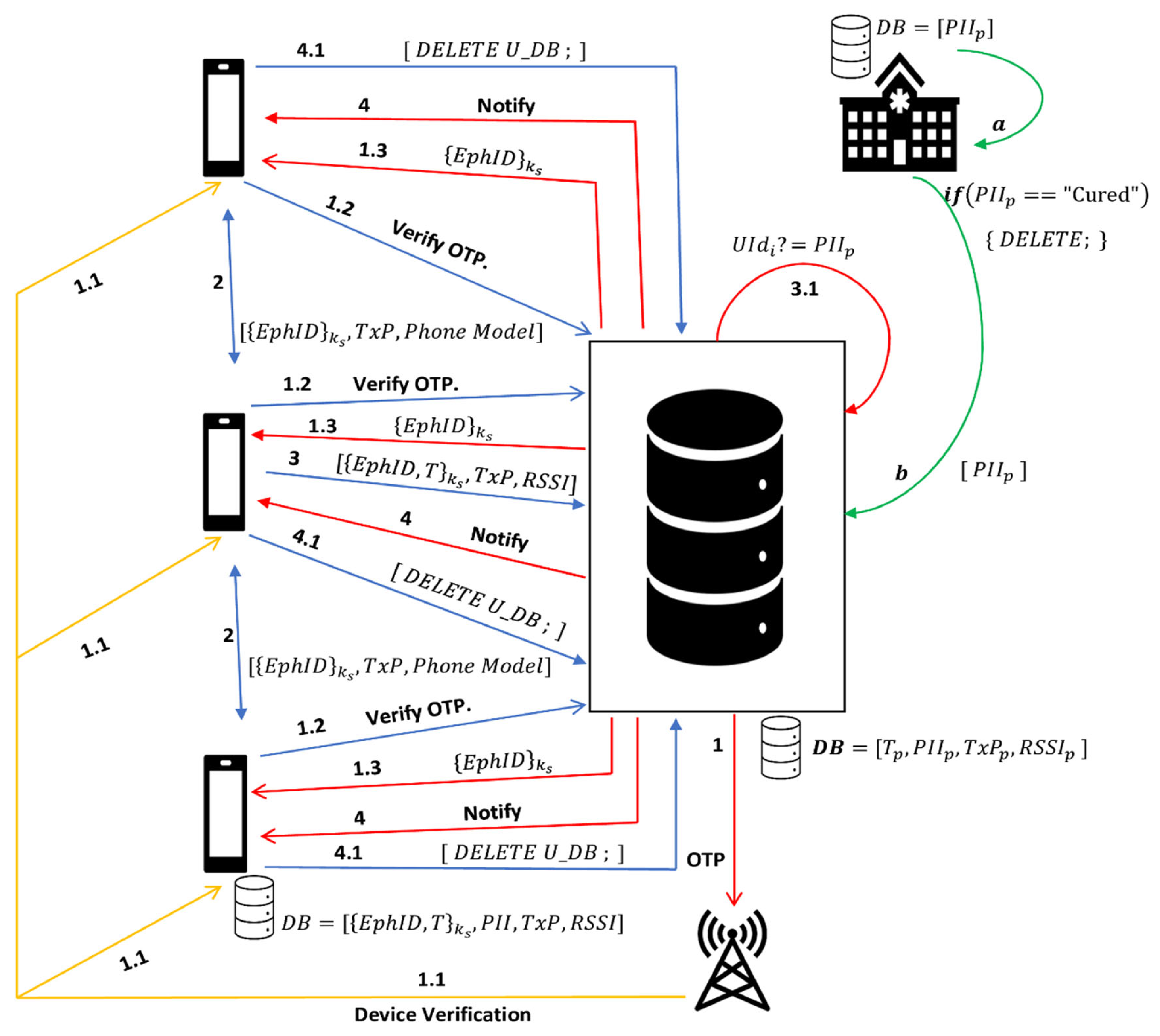

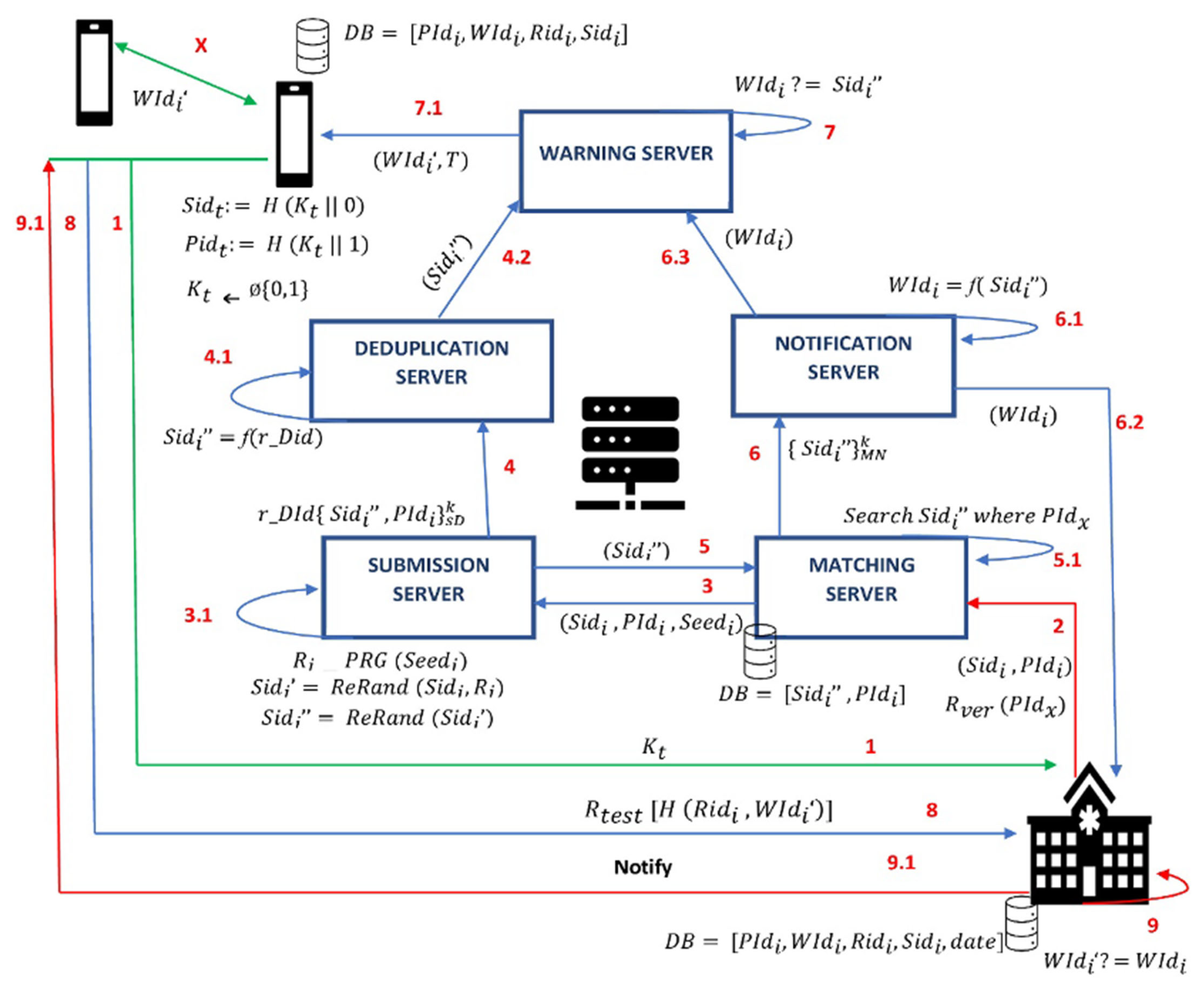
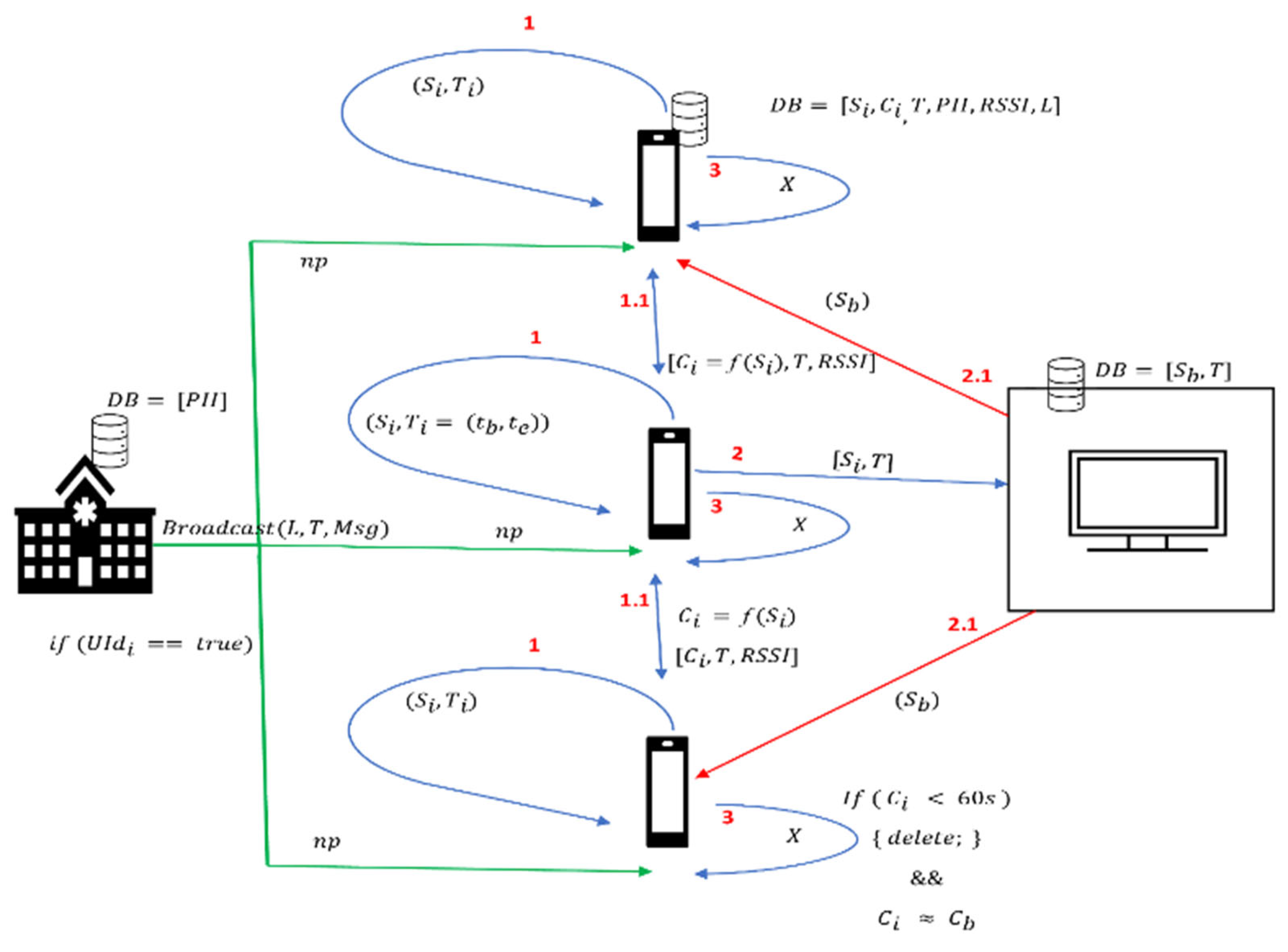




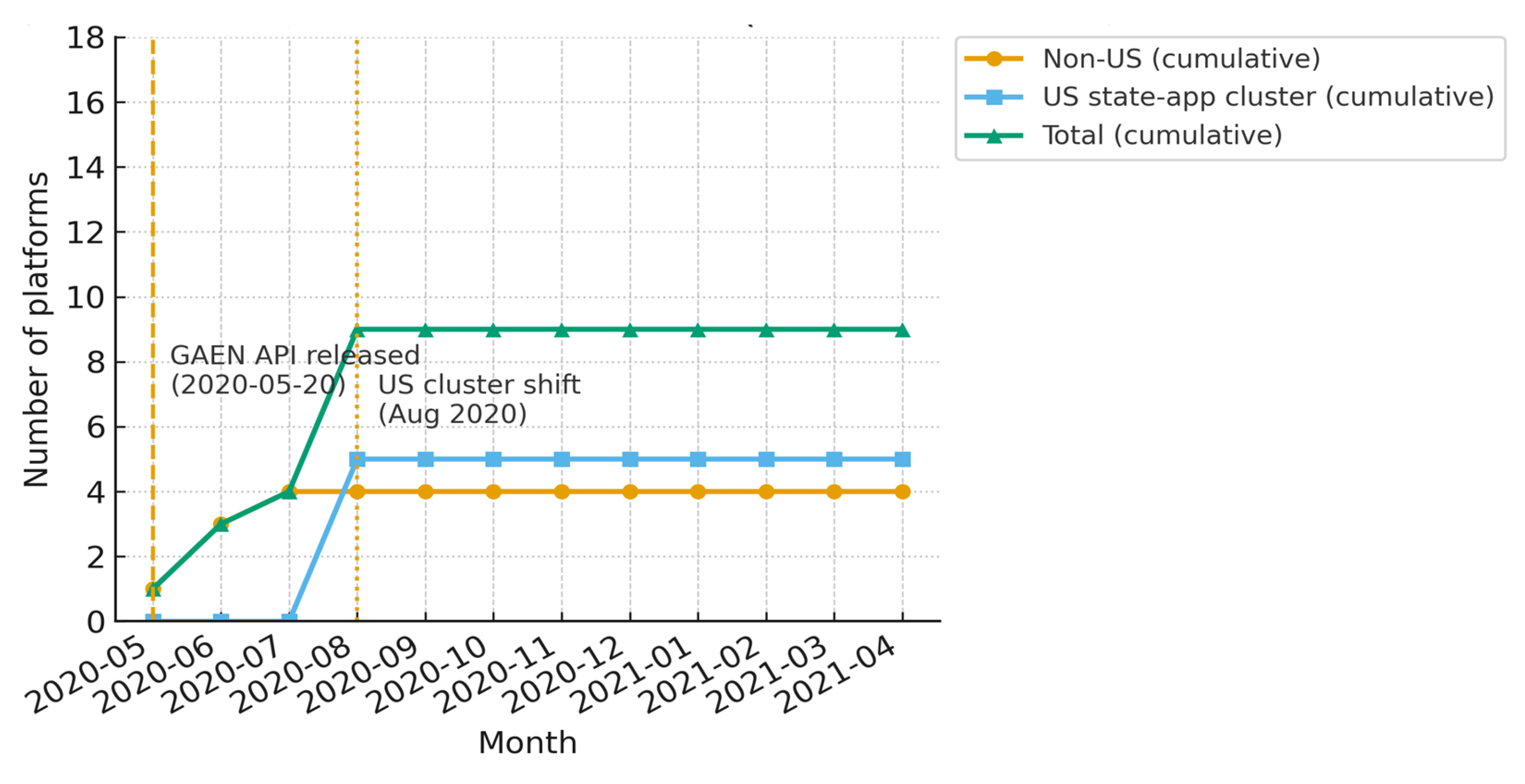
| # | CT Solutions | Developer | Deployed | Platform | Source Code | User Base + |
|---|---|---|---|---|---|---|
| 1 | GAEN APIs [39,40] | Apple & Google | 37 Countries (Globally) | API | ✓ | Millions of users by 65 Apps |
| 2 | Health Code [41] | Tencent and Ant Group | China | Framework | ✖ | 900 million |
| 3 | Aarogya Setu [21] | NIC, India | India | Android/iOS | ✓ | 214 million |
| 4 | ConTra Corona [42] | FZI Research Center, Germany | Germany | Protocol | ✓ | 48 million |
| 5 | Immuni (Pronto-C2) [21,43] | Italian Government | Italy | Android/iOS | ✖ | 19 million |
| 6 | CovidSafe [44,45,46] | Australian Government | Australia | Android/iOS | ✓ | 7 million |
| 7 | StopCovid/TousAntiCovid [21,47,48] | INRIA & Fraunhofer | France | Android/iOS | ✓ | 5 million |
| 8 | TraceTogether (OpenTrace) [49] | Ministry of Health, GOVTECH & SG UNITED | Singapore | Android/iOS | ✓ | 4.9 million |
| 9 | Hamagen [19,21] | Israeli Ministry of Health | Israel | Android/iOS | ✓ | 2.5 million |
| 10 | CovidSafe-PACT (West-coast) [7,50,51] | University of Washington | USA | Protocol | ✓ | 2 million |
| 11 | SwissCovid-DP-3T [52,53] | FOPH, Switzerland | Switzerland | Android/iOS | ✓ | 1 million |
| 12 | CovidWatch–TCN [54] | ADHS-Arizona, Stanford University, and the University of Waterloo | Waterloo, Canada | Android/iOS | ✓ | 10k |
| 13 | COVID Safe Paths (Private Kit) [6,55] | MIT Media Lab | USA | Android/iOS | ✓ | 10k |
| 14 | Coronavirus Disease-19 [19,56] | South Korean Government | South Korea | Website | ✖ | – |
| 15 | DP3T [57] | Swiss Federal Institute of Technology (EPFL) | Europe | Protocol | ✓ | – |
| 16 | DESIRE protocol [58] | INRIA, France | – | Protocol | ✖ | – |
| 17 | EpiOne [59] | UC Berkeley, USA | – | Protocol | ✖ | – |
| 18 | PACT East Coast [50,51] | MIT, USA | – | Protocol | ✓ | – |
| Architecture | Primary Privacy Exposure Points | PII at Risk/Data Items | Re-identification Vectors | Other Notes |
|---|---|---|---|---|
| Centralized Apps | User end; Server end; Secondary channels | All user data stored or referenced centrally | Linkage via secondary channels (e.g., correlating app/broadcast metadata) | Susceptible to contact-advertising message correlation; proximity detection concerns reported |
| Decentralized Apps | User end; Secondary channels | Seeds & chirps on devices; uploads are keys/seeds | Traffic analysis/linkage via side information | False positives are possible by relaying chirps (if mitigations are weak) |
| Hybrid Apps | User end; Secondary channels | Risk of PII de-anonymization in some flows | Correlation of anonymous broadcast data via secondary channels | Similar proximity/advertising concerns if broadcasts are linkable |
| Architecture | Server/User-ID Protection Threats | Consequences If Server Is Compromised | Typical Attack Surfaces | Relative Difficulty |
|---|---|---|---|---|
| Centralized Apps | Single point of failure/attack; weak auth on BLE contact info | Broad data exposure (all user data) | DoS; Replay/Relay; Linkage attacks | Easy |
| Decentralized Apps | Less central SPOF; risks shift to key distribution and client integrity | Access to seeds/chirps may enable graph inference if combined with side info | Traffic analysis; DoS; Limited replay; Relay; Linkage | Hard |
| Hybrid Apps | Mixed: partial central services + device-side matching; correlation risks | PII de-anonymization possible if joins occur | DoS; Relay; Linkage (esp. via secondary channels) | Hard |
| Server Model | Device End | Server End | Health Authority |
|---|---|---|---|
| Fully Centralized Model | |||
| Subset Data Model | |||
| Bulletin Board Model | |||
| Indexed Data Model | |||
| Dedicated Servers Model | |||
| Custodian Data Model |
| Server Models | Patient Identification | Contact Elicitation | Contact Notification | User Involvement | Availability | Trustworthiness | Platform Support | Data Interoperability | Privacy | Technical Support | Vendor Experience | Contact Follow-up | Customizability and Localization |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Fully Centralized Model | 4 | 1 | 2 | 2 | 4 | 2 | 3 | 3 | 2 | 3 | 3 | 4 | 3 |
| Subset Data Model | 4 | 1 | 2 | 3 | 2 | 3 | 3 | 3 | 2 | 3 | 3 | 4 | 3 |
| Bulletin Board Model | 2 | 4 | 4 | 2 | 3 | 4 | 4 | 4 | 4 | 4 | 1 | 2 | 4 |
| Indexed Data Model | 2 | 4 | 4 | 2 | 2 | 4 | 2 | 4 | 4 | 2 | 1 | 2 | 2 |
| Dedicated Servers Model | 3 | 2 | 4 | 2 | 1 | 4 | 1 | 4 | 3 | 1 | 4 | 4 | 1 |
| Custodian Data Model | 3 | 2 | 3 | 2 | 1 | 1 | 1 | 3 | 3 | 1 | 4 | 4 | 1 |
| Attributes | Fully Centralized Model | Subset Data Model | Bulletin Board Model | Indexed Data Model | Dedicated Servers Model | Custodian Data Model |
|---|---|---|---|---|---|---|
| PHAs Data Access | 1 | 2 | 3 | 3 | 2 | 2 |
| PHAs Access Criteria | 1 | 1 | 4 | 4 | 3 | 3 |
| PHAs Data Longevity | 1 | 2 | 4 | 4 | 3 | 3 |
| PHAs Data Request | 1 | 1 | 4 | 4 | 2 | 2 |
| Users’ Risk of Anonymization | 1 | 1 | 3 | 4 | 4 | 2 |
| Total | 5 | 7 | 18 | 19 | 14 | 12 |
| Model | Control Type | Key Security Risks | Privacy Level | Strengths |
|---|---|---|---|---|
| Fully Centralized | Government | Single point of failure, mass data breach | Low | Centralized control, full data visibility |
| Subset Data Model | Government/User Shared | Linkage attacks, limited anonymization | Medium | Partial data isolation, improved privacy over full centralization |
| Custodian Data Model | User-Controlled | Data integrity issues, potential user mismanagement | High | User maintains control over exposure and health status data |
| Dedicated Servers | Government/3rd Parties | DoS attacks on segmented servers | High | Segmented risk zones, scalable and resilient infrastructure |
| Bulletin Board Model | Anonymous Relay Server | Traffic analysis, replay attacks, metadata correlation | Very High | Strong anonymity, public exposure keys without direct identifiers |
| Indexed Data Model | Mixed Control | Index leakage, possible metadata profiling | Medium-High | Fast retrieval with partial anonymity, balance of privacy and speed |
| CT Solutions | Deployed | Source Code Release Date | Switch Date to GAEN API |
|---|---|---|---|
| GAEN APIs | 37 Countries (Globally) | 20 May 2020 | N/A |
| Health Code | China | × | × |
| Aarogya Setu | India | June 2020 | × |
| ConTra Corona | Germany | 16 June 2020 | July 2020 |
| CovidSafe-PACT (West-coast) | USA | Novembre 2020 | August 2020 |
| Immuni (Pronto-C2) | Italy | 25 May, 2020 | 1 June, 2020 |
| StopCovid/TousAntiCovid | France | June 2020 | × |
| TraceTogether (OpenTrace) | Singapore | 29 March 2020 | × |
| CovidSafe | Australia | 8 May 2020 | × |
| SwissCoviD-DP-3T | Switzerland | 26 May 2020 | June 2020 |
| DP-3T Unlinkable | Europe | April 2020 | May 2020 |
| Hamagen | Israel | July 2020 | × |
| Coronavirus Disease-19 | South Korea | × | × |
| CovidWatch–TCN | Arizona, USA | April 2020 | August 2020 |
| COVID Safe Paths (Private Kit) | USA | June 2020 | August 2020 |
| DESIRE protocol | - | × | N/A |
| EpiOne | - | × | August 2020 |
| PACT East Coast | - | August 2020 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Anwar, S.; Anderson, J. Privacy-Driven Classification of Contact Tracing Platforms: Architecture and Adoption Insights. Cryptography 2025, 9, 60. https://doi.org/10.3390/cryptography9040060
Anwar S, Anderson J. Privacy-Driven Classification of Contact Tracing Platforms: Architecture and Adoption Insights. Cryptography. 2025; 9(4):60. https://doi.org/10.3390/cryptography9040060
Chicago/Turabian StyleAnwar, Sidra, and Jonathan Anderson. 2025. "Privacy-Driven Classification of Contact Tracing Platforms: Architecture and Adoption Insights" Cryptography 9, no. 4: 60. https://doi.org/10.3390/cryptography9040060
APA StyleAnwar, S., & Anderson, J. (2025). Privacy-Driven Classification of Contact Tracing Platforms: Architecture and Adoption Insights. Cryptography, 9(4), 60. https://doi.org/10.3390/cryptography9040060









