Security and Performance Analyses of Post-Quantum Digital Signature Algorithms and Their TLS and PKI Integrations †
Abstract
1. Introduction
Contributions and Paper Organization
2. Materials and Methods
Methodologies and Approaches
3. Background: PQC History and NIST
4. PQC Signature Schemes
4.1. Lattice-Based Signature Schemes
4.1.1. Dilithium
4.1.2. Falcon
4.2. Hash-Based Signature Schemes
SPHINCS+
5. Security Analysis Using Visualization Model
5.1. Metrics: Qubits
Qubit Cost
5.2. Lattice-Based Signatures Security and Length Trade-Off
5.3. Hash-Based Signatures Security and Length Trade-Off
6. Performance Analysis of PQC Digital Signature Algorithms
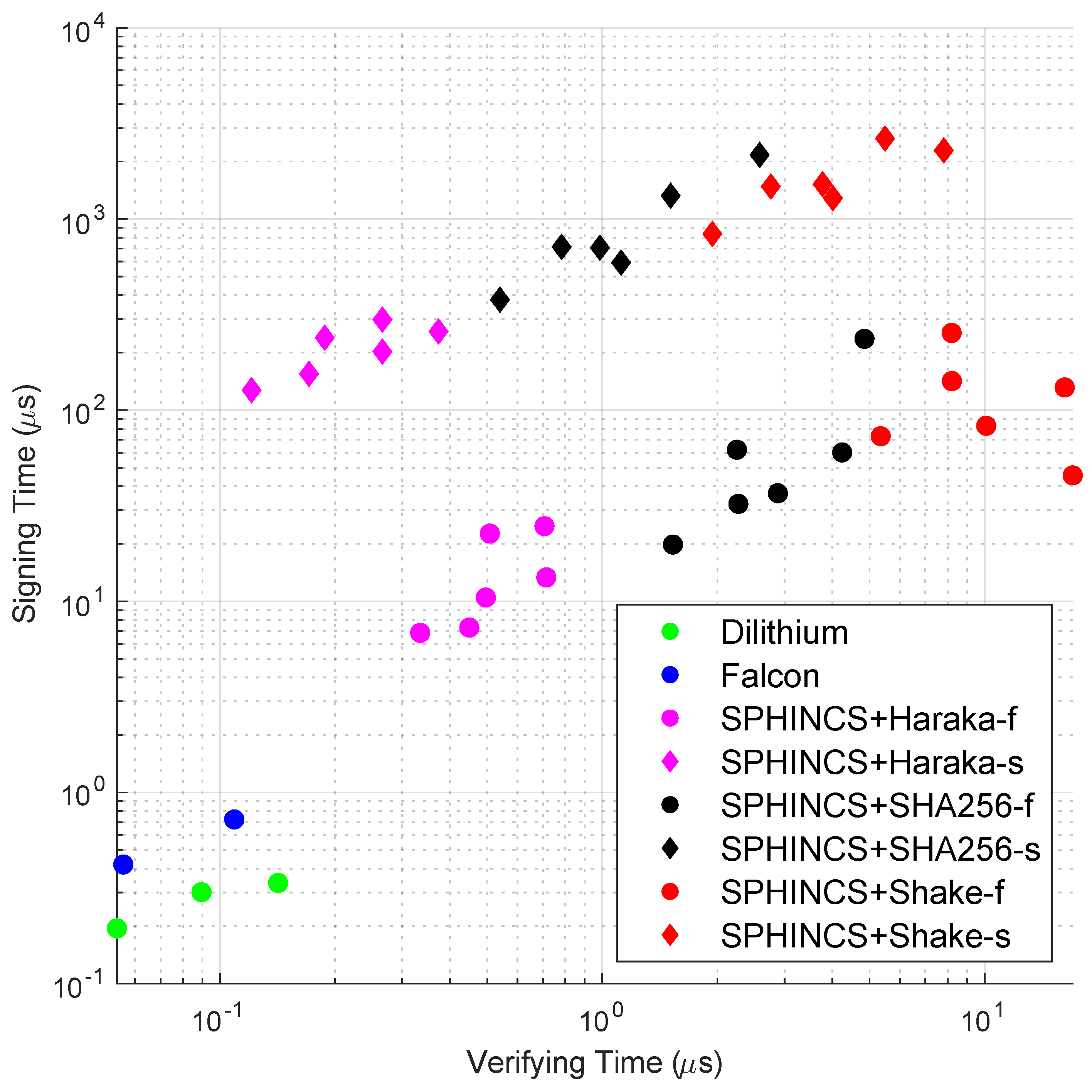
6.1. Algorithm Performances
6.2. Message Scalability Performances
6.3. Application Dependency
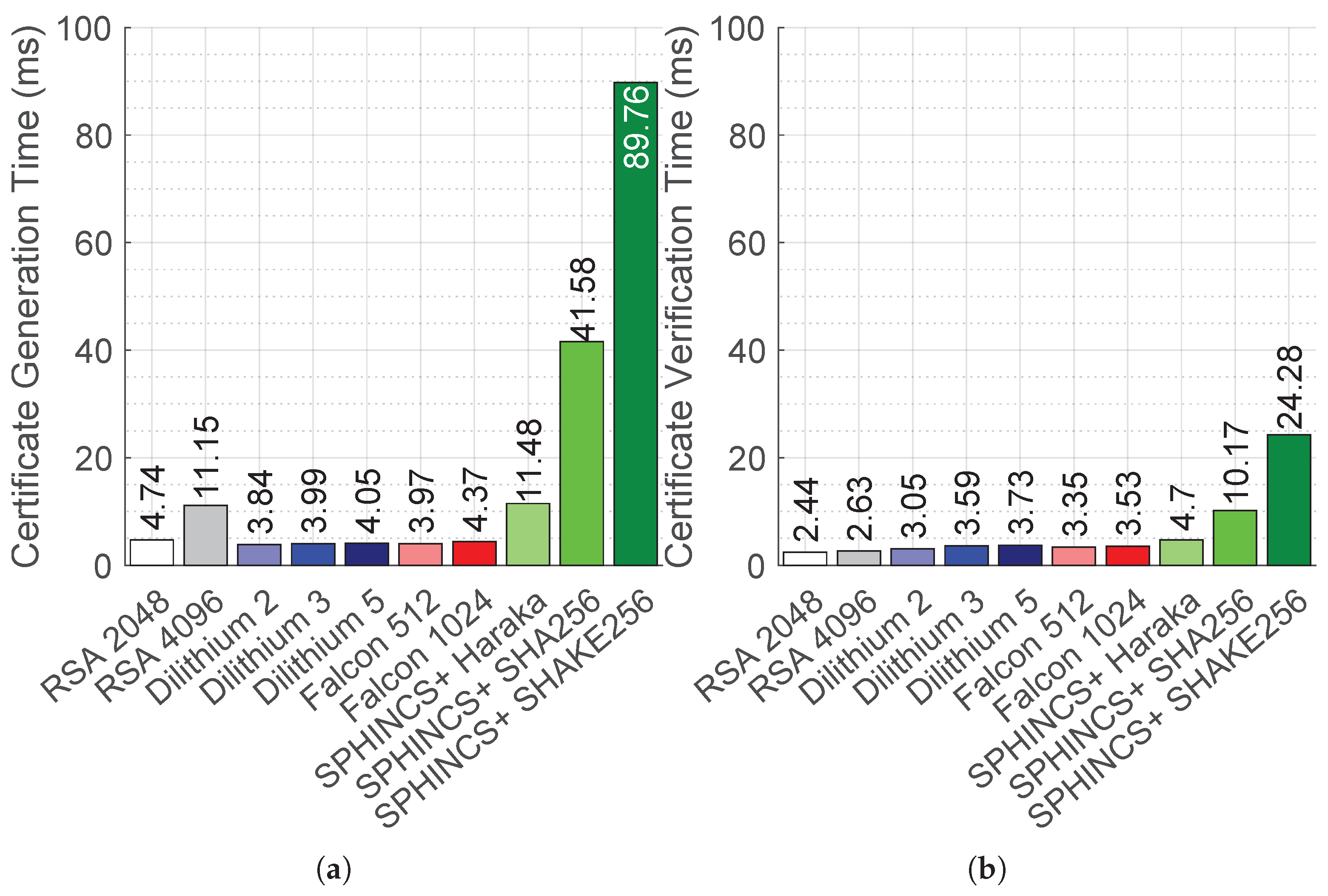
7. Performance Analysis of Integration with Public Key Infrastructure
8. Performance Analysis of Integration with TCP/IP and TLS
8.1. Packet-Level Handshake Analysis: Time Overhead
8.2. Packet-Level Handshake Analysis: Certificate Size and Server Hello
8.3. PQC Algorithm Choices with TLS Integration
9. Takeaways and Discussion
10. Related Work in PQC Analyses
10.1. PQC Digital Signature Performance Analyses in TLS and TCP/IP and Beyond
10.2. Cryptanalysis and Security Analyses
10.3. Hardware-Based PQC Analyses
11. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| NIST | National Institute of Standards and Technology |
| PQC | Post-Quantum Cryptography |
| PKI | Public Key Infrastructure |
| TLS | Transport Layer Security |
| TCP | Transmission Control Protocol |
References
- Rivest, R.L.; Shamir, A.; Adleman, L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Caelli, W.J.; Dawson, E.P.; Rea, S.A. PKI, elliptic curve cryptography, and digital signatures. Comput. Secur. 1999, 18, 47–66. [Google Scholar] [CrossRef]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Moses, T. Quantum Computing and Cryptography; Entrust Inc.: Minneapolis, MN, USA, 2009. [Google Scholar]
- Stebila, D.; Mosca, M. Post-quantum key exchange for the internet and the open quantum safe project. In Proceedings of the International Conference on Selected Areas in Cryptography, St. John’s, NL, Canada, 10–12 August 2016; pp. 14–37. [Google Scholar]
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- Chuang, I.L.; Gershenfeld, N.; Kubinec, M. Experimental implementation of fast quantum searching. Phys. Rev. Lett. 1998, 80, 3408. [Google Scholar] [CrossRef]
- Vandersypen, L.M.; Steffen, M.; Breyta, G.; Yannoni, C.S.; Sherwood, M.H.; Chuang, I.L. Experimental realization of Shor’s quantum factoring algorithm using nuclear magnetic resonance. Nature 2001, 414, 883–887. [Google Scholar] [CrossRef] [PubMed]
- Wheatley, M. D-Wave debuts new 5000-qubit quantum computer. 2019. Available online: https://www.dwavequantum.com/company/newsroom/media-coverage/techrepublic-d-wave-announces-5-000-qubit-fifth-generation-quantum-annealer/ (accessed on 1 June 2025).
- Kelly, J. A preview of Bristlecone, Google’s new quantum processor. Google Research Blog. 2018. Available online: https://research.google/blog/a-preview-of-bristlecone-googles-new-quantum-processor/ (accessed on 1 June 2025).
- Alsina, D.; Latorre, J.I. Experimental test of Mermin inequalities on a five-qubit quantum computer. Phys. Rev. A 2016, 94, 012314. [Google Scholar] [CrossRef]
- Castelvecchi, D. IBM’s quantum cloud computer goes commercial. Nat. News 2017, 543, 159. [Google Scholar] [CrossRef] [PubMed]
- Alagic, G.; Alagic, G.; Alperin-Sheriff, J.; Apon, D.; Cooper, D.; Dang, Q.; Liu, Y.K.; Miller, C.; Moody, D.; Peralta, R.; et al. Status Report on the First Round of the NIST Post-Quantum Cryptography Standardization Process; US Department of Commerce, National Institute of Standards and Technology: Gaithersburg, MD, USA, 2019. [Google Scholar]
- Fips, P. 186-4: Federal Information Processing Standards Publication. Digital Signature Standard (DSS); Information Technology Laboratory, National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2013; pp. 20899–20900. [Google Scholar]
- Brassard, G.; Høyer, P.; Tapp, A. Quantum cryptanalysis of hash and claw-free functions. ACM Sigact News 1997, 28, 14–19. [Google Scholar]
- Alagic, G.; Alperin-Sheriff, J.; Apon, D.; Cooper, D.; Dang, Q.; Kelsey, J.; Liu, Y.K.; Miller, C.; Moody, D.; Peralta, R.; et al. Status Report on the Second Round of the NIST Post-Quantum Cryptography Standardization Process; US Department of Commerce, NIST: Gaithersburg, MD, USA, 2020. [Google Scholar]
- Status Report on the First Round of the Additional Digital Signature Schemes for the NIST Post-Quantum Cryptography Standardization Process. Available online: https://nvlpubs.nist.gov/nistpubs/ir/2024/NIST.IR.8528.pdf (accessed on 1 September 2020).
- Tao, C.; Petzoldt, A.; Ding, J. Efficient key recovery for all HFE signature variants. In Proceedings of the Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2021; pp. 70–93. [Google Scholar]
- Beullens, W. Improved cryptanalysis of UOV and rainbow. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, 17–21 October 2021; pp. 348–373. [Google Scholar]
- Beullens, W.; Breaking rainbow takes a weekend on a laptop. Cryptology ePrint Archive. 2022. Available online: https://eprint.iacr.org/2022/214 (accessed on 1 June 2025).
- Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schwabe, P.; Seiler, G.; Stehlé, D. Crystals-dilithium: A lattice-based digital signature scheme. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2018, 2018, 238–268. [Google Scholar] [CrossRef]
- Fouque, P.A.; Hoffstein, J.; Kirchner, P.; Lyubashevsky, V.; Pornin, T.; Prest, T.; Ricosset, T.; Seiler, G.; Whyte, W.; Zhang, Z. Falcon: Fast-Fourier Lattice-Based Compact Signatures over NTRU; Submission to the NIST’s post-quantum cryptography standardization process; NIST: Gaithersburg, MD, USA, 2018. [Google Scholar]
- Bernstein, D.J.; Hülsing, A.; Kölbl, S.; Niederhagen, R.; Rijneveld, J.; Schwabe, P. The SPHINCS+ signature framework. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 2129–2146. [Google Scholar]
- Regev, O. Lattice-based cryptography. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2006; pp. 131–141. [Google Scholar]
- Nejatollahi, H.; Dutt, N.; Ray, S.; Regazzoni, F.; Banerjee, I.; Cammarota, R. Post-quantum lattice-based cryptography implementations: A survey. ACM Comput. Surv. (CSUR) 2019, 51, 1–41. [Google Scholar] [CrossRef]
- Lamport, L. Constructing digital signatures from a one way function. 1979. Available online: https://www.microsoft.com/en-us/research/wp-content/uploads/2016/12/Constructing-Digital-Signatures-from-a-One-Way-Function.pdf (accessed on 1 June 2025).
- Merkle, R.C. A certified digital signature. In Proceedings of the Conference on the Theory and Application of Cryptology; Springer: Berlin/Heidelberg, Germany, 1989; pp. 218–238. [Google Scholar]
- Alkim, E.; Ducas, L.; Pöppelmann, T.; Schwabe, P. Post-quantum key exchange—A new hope. In Proceedings of the 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, USA, 10–12 August 2016; pp. 327–343. [Google Scholar]
- Gao, Y.L.; Chen, X.B.; Chen, Y.L.; Sun, Y.; Niu, X.X.; Yang, Y.X. A secure cryptocurrency scheme based on post-quantum blockchain. IEEE Access 2018, 6, 27205–27213. [Google Scholar] [CrossRef]
- Whyte, W.; Weimerskirch, A.; Kumar, V.; Hehn, T. A security credential management system for V2V communications. In Proceedings of the 2013 IEEE Vehicular Networking Conference, Boston, MA, USA, 16–18 December 2013; pp. 1–8. [Google Scholar] [CrossRef]
- Chen, C.; Chang, S.; Hu, Y.; Chen, Y. Protecting vehicular networks privacy in the presence of a single adversarial authority. In Proceedings of the 2017 IEEE Conference on Communications and Network Security (CNS), Las Vegas, NV, USA, 9–11 October 2017; pp. 1–9. [Google Scholar] [CrossRef]
- Brecht, B.; Therriault, D.; Weimerskirch, A.; Whyte, W.; Kumar, V.; Hehn, T.; Goudy, R. A Security Credential Management System for V2X Communications. IEEE Trans. Intell. Transp. Syst. 2018, 19, 3850–3871. [Google Scholar] [CrossRef]
- Jacobson, V.; Leres, C.; McCanne, S. TCPDUMP Public Repository 2003. Available online: https://www.tcpdump.org/ (accessed on 1 June 2025).
- Wireshark Tool. Available online: https://www.wireshark.org (accessed on 1 September 2020).
- Sikeridis, D.; Kampanakis, P.; Devetsikiotis, M. Post-Quantum Authentication in TLS 1.3: A Performance Study. IACR Cryptology ePrint Archive. 2020. Available online: https://eprint.iacr.org/2020/071 (accessed on 1 June 2025).
- Basu, K.; Soni, D.; Nabeel, M.; Karri, R. NIST Post-Quantum Cryptography-A Hardware Evaluation Study. Cryptology ePrint Archive. 2019. Available online: https://eprint.iacr.org/2019/047 (accessed on 1 June 2025).
- Raavi, M.; Wuthier, S.; Zhou, X.; Chang, S.Y. Post-Quantum QUIC Protocol in Cloud Networking. In Proceedings of the 2023 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Gothenburg, Sweden, 6–9 June 2023; pp. 573–578. [Google Scholar] [CrossRef]
- Raavi, M.; Wuthier, S.; Chandramouli, P.; Zhou, X.; Chang, S.Y. QUIC Protocol with Post-quantum Authentication. In International Conference on Information Security; Susilo, W., Chen, X., Guo, F., Zhang, Y., Intan, R., Eds.; Springer International Publishing: Cham, Switzerland, 2022; pp. 84–91. [Google Scholar]
- Raavi, M.; Wuthier, S.; Chandramouli, P.; Balytskyi, Y.; Zhou, X.; Chang, S.Y. Security comparisons and performance analyses of post-quantum signature algorithms. In International Conference on Applied Cryptography and Network Security; Springer: Berlin/Heidelberg, Germany, 2021; pp. 424–447. [Google Scholar]
- Raavi, M.; Chandramouli, P.; Wuthier, S.; Zhou, X.; Chang, S.Y. Performance Characterization of Post-Quantum Digital Certificates. In Proceedings of the 2021 International Conference on Computer Communications and Networks (ICCCN), Athens, Greece, 19–22 July 2021; pp. 1–9. [Google Scholar]
- Hines, K.; Raavi, M.; Villeneuve, J.; Wuthier, S.; Moreno-Colin, J.; Bai, Y.; Chang, S. Post-quantum cipher power analysis in lightweight devices. In Proceedings of the 15th ACM Conference on Security and Privacy in Wireless and Mobile Networks, San Antonio, TX, USA, 16–19 May 2022; pp. 282–284. [Google Scholar]
- Döberl, C.; Eibner, W.; Gärtner, S.; Kos, M.; Kutschera, F.; Ramacher, S. Quantum-resistant End-to-End Secure Messaging and Email Communication. In Proceedings of the 18th International Conference on Availability, Reliability and Security, 2023, ARES ’23, New York, NY, USA, 29 August–1 September 2023. [Google Scholar] [CrossRef]
- Mandev, R.; Kavun, E.B. Performance Comparison of Post-Quantum Signature Algorithms Through An Android Email Application Plug-in. In Proceedings of the 2023 IEEE International Conference on Omni-layer Intelligent Systems (COINS), Berlin, Germany, 23–25 July 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Raavi, M.; Wuthier, S.; Chang, S. Securing Post-Quantum DNSSEC Against Fragmentation Mis-Association Threat. In Proceedings of the ICC 2024—IEEE International Conference on Communications, Denver, CO, USA, 9–13 June 2024; pp. 97–102. [Google Scholar] [CrossRef]
- Goertzen, J.; Stebila, D. Post-Quantum Signatures in DNSSEC via Request-Based Fragmentation. In International Conference on Post-Quantum Cryptography; Johansson, T., Smith-Tone, D., Eds.; Springer Nature: Cham, Switzerland, 2023; pp. 535–564. [Google Scholar]
- Khan, Q.; Purification, S.; Cheruiyot, R.; Kim, J.; Kim, I.; Chang, S.Y. Post-Quantum Digital Signature and Authentication for eSIM in 5G Mobile Networking. In Proceedings of the IEEE Silicon Valley Cybersecurity Conference (SVCC), Fremont, CA, USA, 23–25 June 2025. [Google Scholar]
- Bettale, L.; Dottax, E.; Grémy, L. Post-Quantum Secure Channel Protocols for eSIMs; Cryptology ePrint Archive 2024. Available online: https://eprint.iacr.org/2024/2005 (accessed on 1 June 2025).
- Dachman-Soled, D.; Ducas, L.; Gong, H.; Rossi, M. LWE with Side Information: Attacks and Concrete Security Estimation. IACR Cryptol. ePrint Arch. 2020, 2020, 292. [Google Scholar]
- Ravi, P.; Jhanwar, M.P.; Howe, J.; Chattopadhyay, A.; Bhasin, S. Exploiting determinism in lattice-based signatures: Practical fault attacks on pqm4 implementations of NIST candidates. In Proceedings of the 2019 ACM Asia Conference on Computer and Communications Security, Auckland, New Zealand, 9–12 July 2019; pp. 427–440. [Google Scholar]
- Aikata, A.; Mert, A.C.; Imran, M.; Pagliarini, S.; Roy, S.S. KaLi: A Crystal for Post-Quantum Security Using Kyber and Dilithium. IEEE Trans. Circuits Syst. Regul. Pap. 2023, 70, 747–758. [Google Scholar] [CrossRef]
- Beckwith, L.; Nguyen, D.T.; Gaj, K. Hardware Accelerators for Digital Signature Algorithms Dilithium and FALCON. IEEE Des. Test 2024, 41, 27–35. [Google Scholar] [CrossRef]
- Matteo, S.D.; Sarno, I.; Saponara, S. CRYPHTOR: A Memory-Unified NTT-Based Hardware Accelerator for Post-Quantum CRYSTALS Algorithms. IEEE Access 2024, 12, 25501–25511. [Google Scholar] [CrossRef]
- Beckwith, L.; Nguyen, D.T.; Gaj, K. High-Performance Hardware Implementation of CRYSTALS-Dilithium. In Proceedings of the 2021 International Conference on Field-Programmable Technology (ICFPT), Auckland, New Zealand, 6–10 December 2021; pp. 1–10. [Google Scholar] [CrossRef]
- Land, G.; Sasdrich, P.; Güneysu, T. A Hard Crystal-Implementing Dilithium on Reconfigurable Hardware. In Proceedings of the Smart Card Research and Advanced Applications, Birmingham, UK, 7–9 November 2022; Grosso, V., Pöppelmann, T., Eds.; Springer International Publishing: Cham, Switzerland, 2022; pp. 210–230. [Google Scholar] [CrossRef]
- Wu, Z.; Chen, R.; Wang, Y.; Wang, Q.; Peng, W. An Efficient Hardware Implementation of Crystal-Dilithium on FPGA. In Proceedings of the Information Security and Privacy; Zhu, T., Li, Y., Eds.; Springer: Singapore, 2024; pp. 64–83. [Google Scholar] [CrossRef]
- Lee, Y.; Youn, J.; Nam, K.; Jung, H.H.; Cho, M.; Na, J.; Park, J.Y.; Jeon, S.; Kang, B.G.; Oh, H.; et al. An Efficient Hardware/Software Co-Design for FALCON on Low-End Embedded Systems. IEEE Access 2024, 12, 57947–57958. [Google Scholar] [CrossRef]
- Schmid, M.; Amiet, D.; Wendler, J.; Zbinden, P.; Wei, T. Falcon Takes Off—A Hardware Implementation of the Falcon Signature Scheme; Cryptology ePrint Archive 2023. Available online: https://eprint.iacr.org/2023/1885 (accessed on 1 June 2025).
- Alsuhli, G.; Saleh, H.; Al-Qutayri, M.; Mohammad, B.; Stouraitis, T. Area and Power Efficient FFT/IFFT Processor for FALCON Post-Quantum Cryptography. IEEE Trans. Emerg. Top. Comput. 2024, 1–16. [Google Scholar] [CrossRef]
- Ouyang, Y.; Zhu, Y.; Zhu, W.; Yang, B.; Zhang, Z.; Wang, H.; Tao, Q.; Zhu, M.; Wei, S.; Liu, L. FalconSign: An Efficient and High-Throughput Hardware Architecture for Falcon Signature Generation. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2025, 2025, 203–226. [Google Scholar] [CrossRef]
- Dai, Y.; Song, Y.; Tian, J.; Wang, Z. High-Throughput Hardware Implementation for Haraka in SPHINCS+. In Proceedings of the 2023 24th International Symposium on Quality Electronic Design (ISQED), San Francisco, CA, USA, 5–7 April 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Karl, P.; Schupp, J.; Sigl, G. The Impact of Hash Primitives and Communication Overhead for Hardware-Accelerated SPHINCS+. In Proceedings of the Constructive Side-Channel Analysis and Secure Design; Wacquez, R., Homma, N., Eds.; Springer International Publishing: Cham, Switzerland, 2024; pp. 221–239. [Google Scholar] [CrossRef]
- Amiet, D.; Leuenberger, L.; Curiger, A.; Zbinden, P. FPGA-based SPHINCS+ Implementations: Mind the Glitch. In Proceedings of the 2020 23rd Euromicro Conference on Digital System Design (DSD), Kranj, Slovenia, 26–28 August 2020; pp. 229–237. [Google Scholar] [CrossRef]
- Berthet, Q.; Upegui, A.; Gantel, L.; Duc, A.; Traverso, G. An Area-Efficient SPHINCS+ Post-Quantum Signature Coprocessor. In Proceedings of the 2021 IEEE International Parallel and Distributed Processing Symposium Workshops (IPDPSW), Portland, OR, USA, 17–21 June 2021; pp. 180–187. [Google Scholar] [CrossRef]
- Lopez-Valdivieso, J.; Cumplido, R. Design and Implementation of Hardware-Software Architecture Based on Hashes for SPHINCS+. ACM Trans. Reconfig. Technol. Syst. 2024, 17, 54:1–54:22. [Google Scholar] [CrossRef]
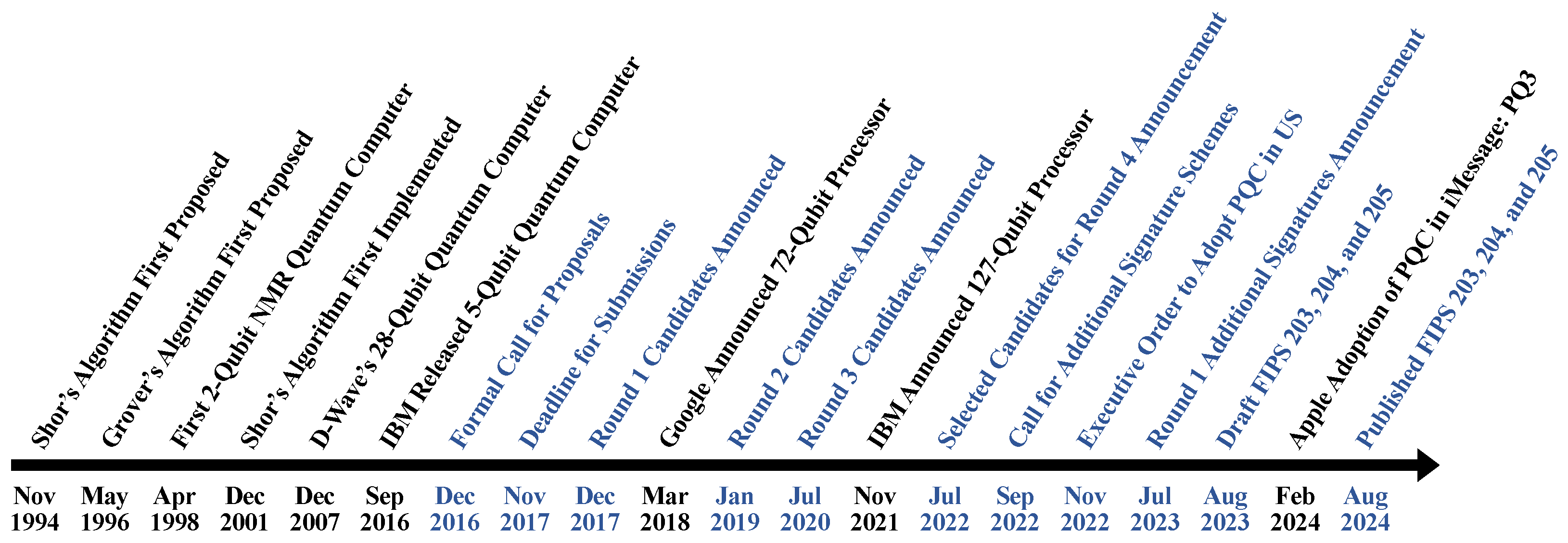
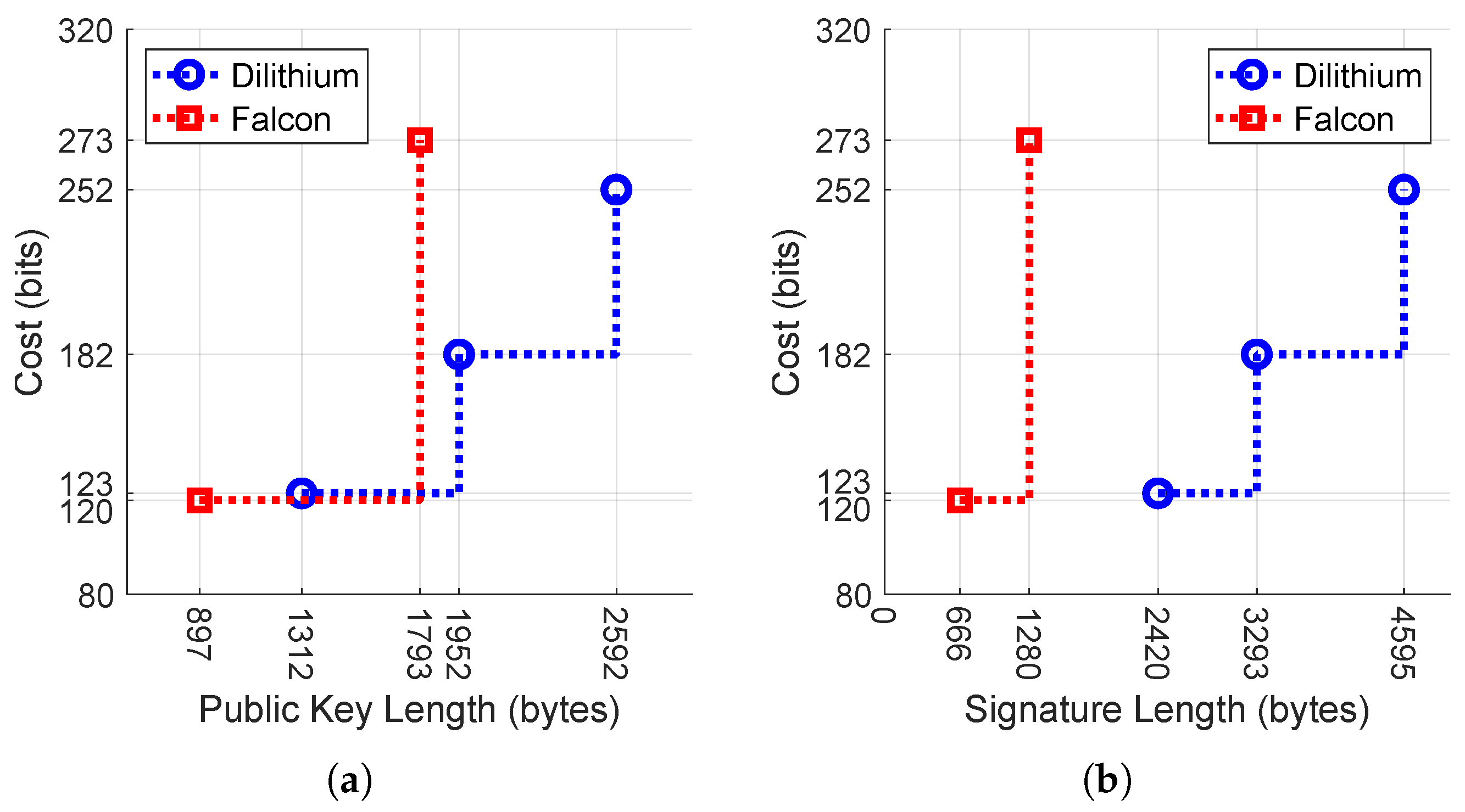
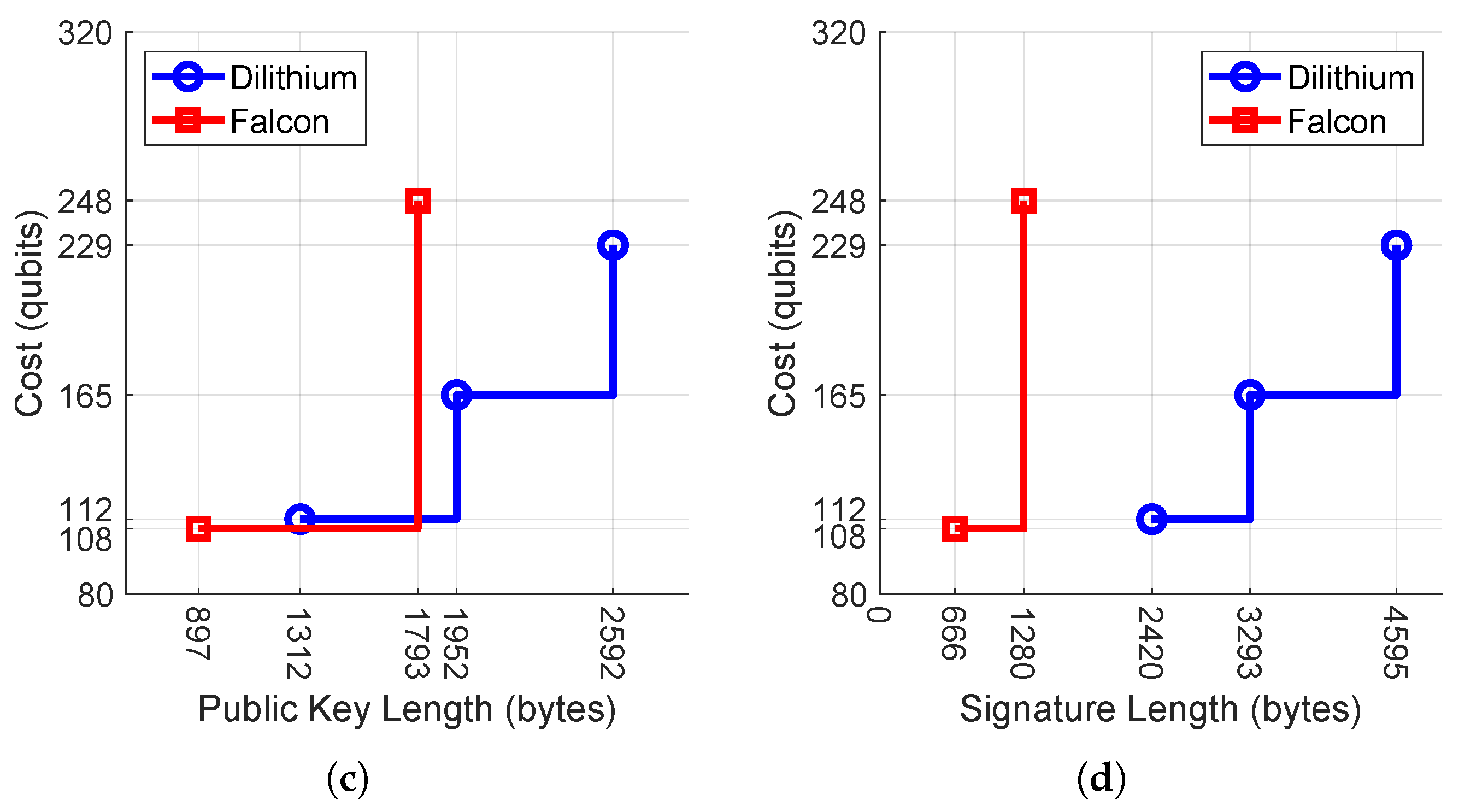
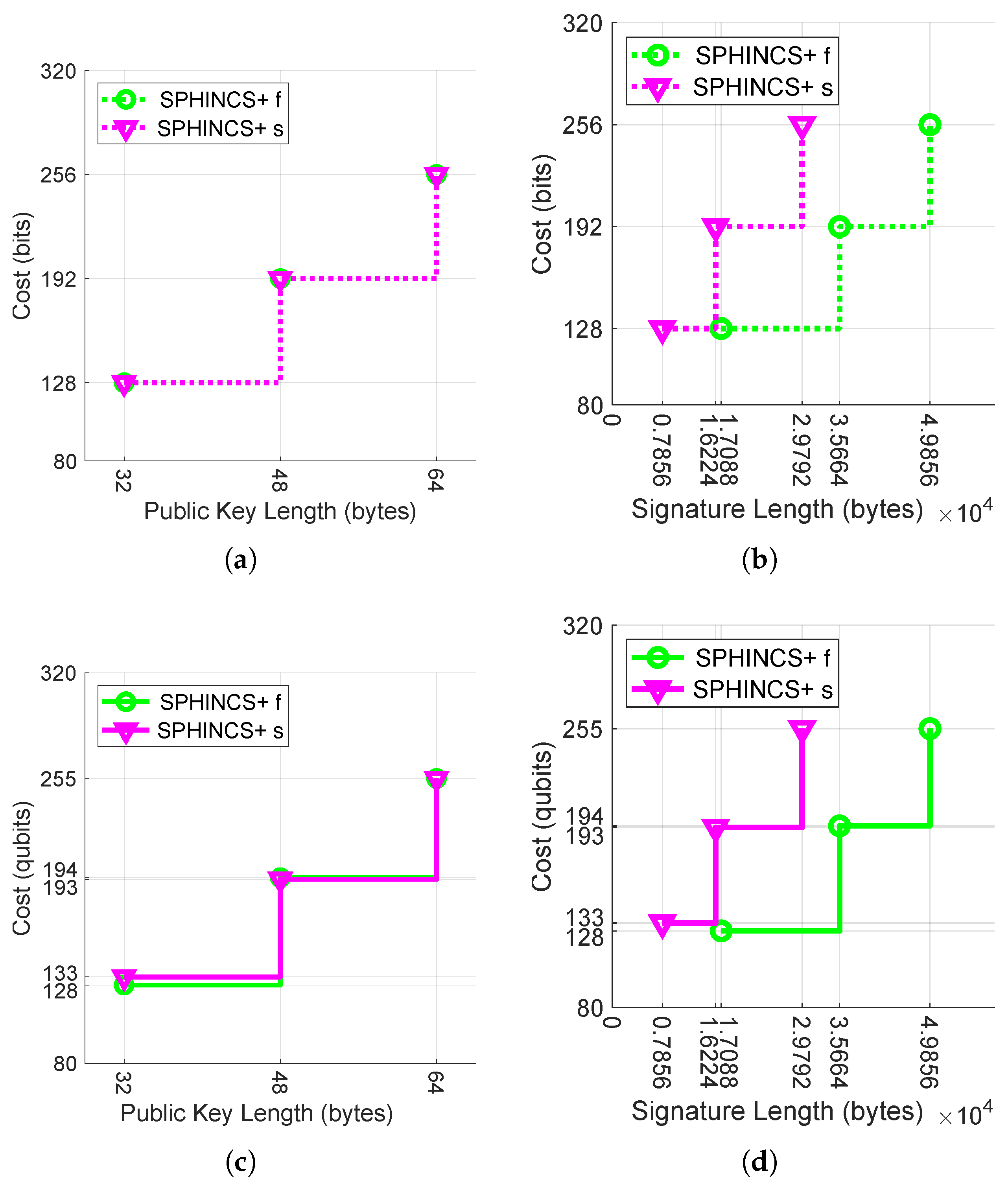
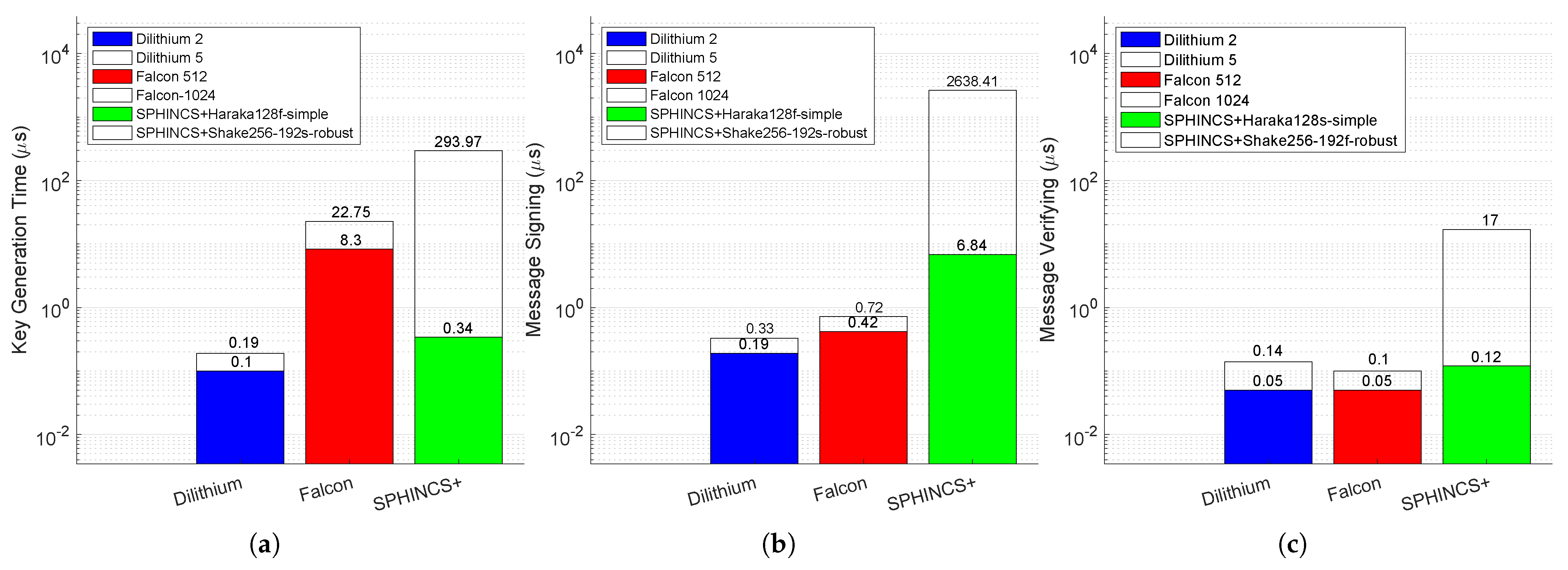
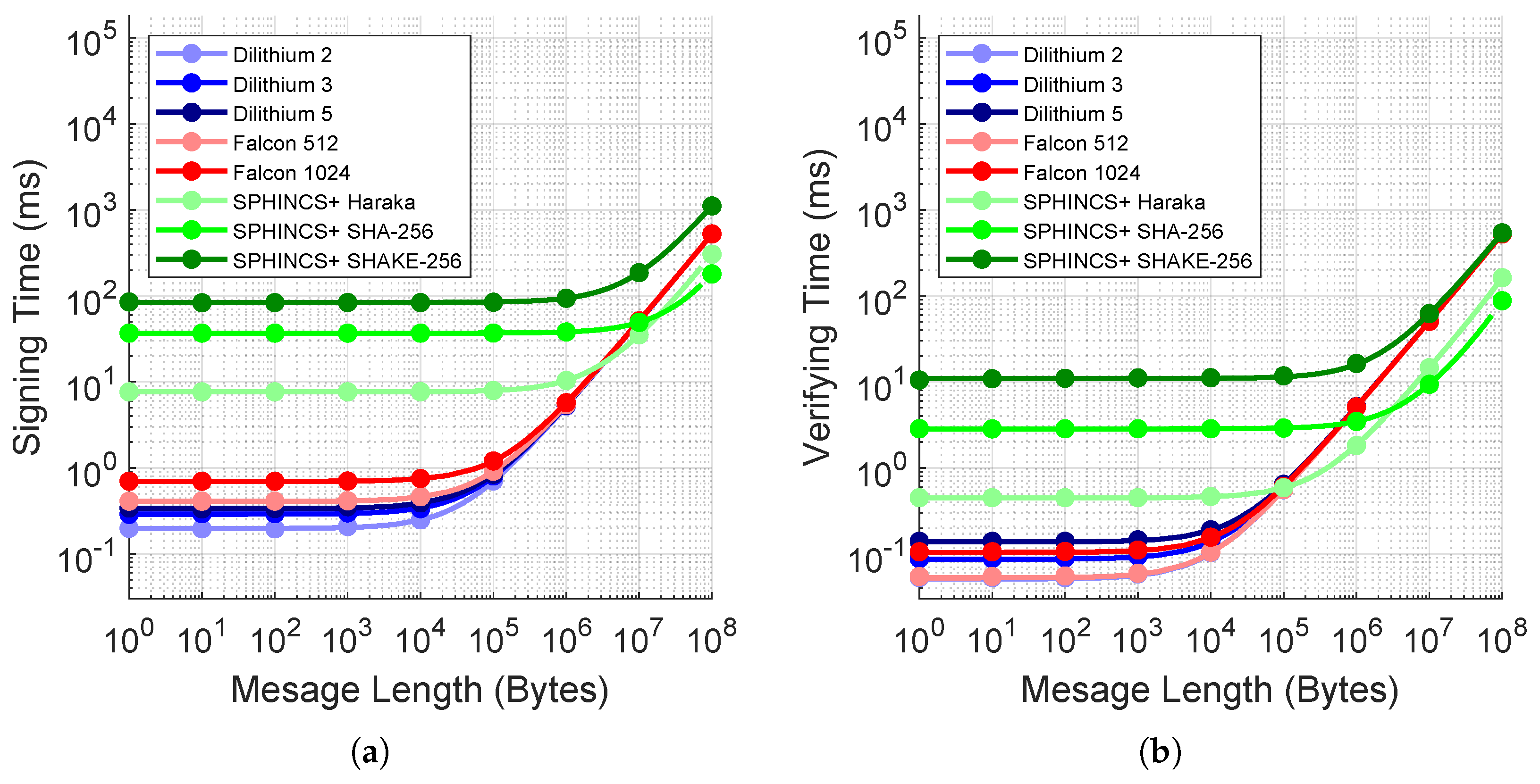

| Security Category | Reference Algorithm | Classical Bit Cost | Qubit Security | Circuit Size to Break the Algorithm [13] |
|---|---|---|---|---|
| 1 | AES 128 | 128 (key search) | 64 (Grover [6]) | quantum gates or classical gates |
| 2 | SHA3-256 | 128 (collision) | 85 (Brassard [15]) | classical gates |
| 3 | AES 192 | 192 (key search) | 96 (Grover [6]) | quantum gates or classical gates |
| 4 | SHA3-384 | 192 (collsion) | 128 (Brassard [15]) | classical gates |
| 5 | AES 256 | 256 (key search) | 128 (Grover [6]) | quantum gates or classical gates |
| 6 | SHA3-512 | 256 (collision) | 170 (Brassard [15]) | classical gates |
| Algorithm | Scheme | Parameters | Security Level |
|---|---|---|---|
| Dilithium | Lattice-based | Dilithium 2 | 1 |
| Dilithium 3 | 3 | ||
| Dilithium 5 | 5 | ||
| Falcon | Lattice-based | Falcon 512 | 1 |
| Falcon 1024 | 5 | ||
| SPHINCS+ | Hash-based | SPHINCS+-128s SPHINCS+-128f | 1 |
| SPHINCS+-192s SPHINCS+-192f | 3 | ||
| SPHINCS+-256s SPHINCS+-256f | 5 |
| Algorithm | LoBF (Signing Time) | LoBF (Verifying Time) |
|---|---|---|
| Dilithium 2 | ||
| Dilithium 3 | ||
| Dilithium 5 | ||
| Falcon 512 | ||
| Falcon 1024 | ||
| SPHINCS+-Haraka | ||
| SPHINCS+-SHA-256 | ||
| SPHINCS+-SHAKE256 |
| Algorithm | Time (ms) | CPU ± CI | CS (B) | TSS (B) | SHP | SHS (B) | HP | CS/SHS | SHP/HP |
|---|---|---|---|---|---|---|---|---|---|
| Dilithium 2 | 3.71 | 23.90% ± 2.14% | 5340 | 6607 | 2 | 6541 | 8.78 | 0.816 | 0.22 |
| Dilithium 3 | 3.98 | 27.33% ± 2.10% | 7391 | 8754 | 2 | 8688 | 9.49 | 0.851 | 0.211 |
| Dilithium 5 | 4.31 | 31.29% ± 0.51% | 10,020 | 12,237 | 3 | 12,171 | 10.58 | 0.823 | 0.283 |
| Falcon 512 | 3.83 | 29.84% ± 0.47% | 2358 | 2645 | 1 | 2579 | 8.06 | 0.914 | 0.124 |
| Falcon 1024 | 4.54 | 31.43% ± 0.61% | 4426 | 4788 | 2 | 4722 | 8.16 | 0.937 | 0.245 |
| SPHINCS+-Haraka | 14.34 | 35.38% ± 0.85% | 23,442 | 35,149 | 8 | 34,621 | 21.65 | 0.677 | 0.369 |
| SPHINCS+-SHA-256 | 53.73 | 36.08% ± 0.96% | 23,442 | 35,137 | 7 | 34,621 | 20.48 | 0.677 | 0.341 |
| SPHINCS+-SHAKE256 | 110.02 | 36.63% ± 0.87% | 23,442 | 35,083 | 7 | 34,612 | 20.38 | 0.677 | 0.341 |
| RSA 2048 | 3.46 | 17.16% ± 0.58% | 1000 | 1319 | 1 | 1253 | 8 | 0.798 | 0.115 |
| RSA 4096 | 11.64 | 20.22% ± 0.63% | 1696 | 2006 | 1 | 1940 | 8.02 | 0.874 | 0.124 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Raavi, M.; Khan, Q.; Wuthier, S.; Chandramouli, P.; Balytskyi, Y.; Chang, S.-Y. Security and Performance Analyses of Post-Quantum Digital Signature Algorithms and Their TLS and PKI Integrations. Cryptography 2025, 9, 38. https://doi.org/10.3390/cryptography9020038
Raavi M, Khan Q, Wuthier S, Chandramouli P, Balytskyi Y, Chang S-Y. Security and Performance Analyses of Post-Quantum Digital Signature Algorithms and Their TLS and PKI Integrations. Cryptography. 2025; 9(2):38. https://doi.org/10.3390/cryptography9020038
Chicago/Turabian StyleRaavi, Manohar, Qaiser Khan, Simeon Wuthier, Pranav Chandramouli, Yaroslav Balytskyi, and Sang-Yoon Chang. 2025. "Security and Performance Analyses of Post-Quantum Digital Signature Algorithms and Their TLS and PKI Integrations" Cryptography 9, no. 2: 38. https://doi.org/10.3390/cryptography9020038
APA StyleRaavi, M., Khan, Q., Wuthier, S., Chandramouli, P., Balytskyi, Y., & Chang, S.-Y. (2025). Security and Performance Analyses of Post-Quantum Digital Signature Algorithms and Their TLS and PKI Integrations. Cryptography, 9(2), 38. https://doi.org/10.3390/cryptography9020038






