1. Introduction
Quantum Computing is an emerging field that is transforming the computing paradigm, with exponentially more computational capability than classical computers. The basic unit of quantum computation is ‘Qubit’, which has the property to exist in a superposition of 0 and 1 simultaneously, in comparison to a Bit, which can only be either 0 or 1 at any given time [
1,
2]. Leading companies such as IBM, Microsoft, and D-Wave Systems are providing cloud-based access to Quantum Computers, enabling the development and implementation of quantum applications and algorithms.
This research paper introduces a novel Quantum Computing-based Physical Unclonable Functions (QPUF) design, exploring the potential of Quantum Computing for enhanced security in Industrial Internet-of-Things (IIoT) applications. The proposed Quantum PUF Circuit is a novel quantum logic gates-based circuit evaluated on IBM quantum computers. It enhances security in smart electronics by enabling a quantum hardware-generated PUF key to be used as a unique device identity. This work proposes a new QPUF topology, incorporating Hadamard, CNOT, Pauli-X, and Ry gates, for deployment in a QPUF driven by quantum superposition and entanglement principles. The experimental evaluation of the proposed QPUF on IBM superconducting quantum hardware validates its feasibility, with its key metrics evaluated to showcase its potential for the Quantum Security-by-Design (QSbD) of IIoT.
Securing an IIoT involves enhancing its resilience against malicious cyberattacks. Unauthorized access or a breach in the IIoT network, which could be either due to an actuator executing industrial operations based on commands or a smart sensor performing data collection, can compromise the security of the entire industrial environment. Ensuring the trustworthiness of these devices is essential to counter any potential cyber threats [
3,
4,
5]. From a communication perspective, where IIoT communicates with an edge gateway or cloud, snipping or network traffic snooping attacks can expose secure information, enabling malicious entities to seize control and corrupt the commands. Furthermore, data security and privacy are essential and require robust regulatory mechanisms to protect sensitive information [
3]. Quantum cybersecurity solutions can address the security gaps in all the above scenarios, particularly QPUF, ensuring the reliability of IIoT systems at the physical layer while performing various tasks, such as machinery fault detection, data sensing, actuation, and relay protection. The trustworthiness of the physical layer of these devices, ensuring data integrity, is an essential factor for the control and analysis of the business layer [
6,
7].
1.1. PUF Overview
PUF is a hardware security primitive that utilizes hardware intrinsic device properties for the generation of cryptographic keys by utilizing device-level variations to generate a unique bit stream of 0 and 1 as output, which cannot be regenerated due to the manufacturing process variations between each device [
8,
9]. A PUF primitive captures process variations by mapping a given challenge input to a unique binary response, typically represented as a sequence of 0 s and 1 s, which can serve as a key. PUFs are classified as strong and weak based on the intrinsic properties utilized to generate cryptographic keys such as variations in the power-up of a memory cell, oscillator frequency variations, and logic circuit path delays. PUF designs are classified based on the cryptographic key generation capability. PUFs that support a higher number of Challenge–Response pairs (CRP) are strong PUFs, while PUF designs that support a minimal number of CRPs are weak PUFs. SRAM and DRAM PUFs, which are deployed based on variations in memory cells, are weak, whereas the Arbiter and Ring Oscillator PUFs deployed based on frequency and delay variations in an IC are strong PUFs [
8,
10].
Once generated from the PUF module, a key will be unique to a challenge input and cannot be regenerated on another device, even with the same PUF design and input. Ideally, a PUF-generated key should exhibit a hamming distance of 50%, indicating the percentage of differing bit positions among the responses from a device. The ideal intra-hamming distance, which measures intra-response variations within the same device under various conditions, should range between 40 and 50%. Prominent PUF key evaluation metrics are summarized below [
6,
8]:
Diffuseness: The diffuseness of a PUF in a device represents the degree of variation in PUF responses to varying challenge inputs. It quantifies the variation in responses due to the slightest changes in challenge inputs.
Reliability: A PUF on a device should be able to generate the same response for a challenge input under varying environmental and operating conditions. The percentage of reliability represents the stability of a PUF in regenerating a response under varying conditions.
Uniqueness: The uniqueness of a PUF quantifies the variation in PUF responses when tested on different devices. This is calculated by obtaining the average inter-hamming distance of the responses for a PUF on different devices. The uniqueness value is proportional to the process variation and the ideal uniqueness of a PUF should be around 50%.
Uniformity: PUF’s uniformity is a measure of the probability that each bit in the PUF response key is either 0 or 1. The ideal uniformity of a PUF is 50%, indicating a unique distribution of 1 s and 0 s in a PUF response, providing maximum randomness and security.
1.2. Quantum Physical Unclonable Functions for Secure I-CPS
Quantum Physical Unclonable Functions (QPUF) is a primitive that generates a unique fingerprint for a quantum computer, leveraging the inherent randomness of quantum hardware driven by the principle of quantum mechanics [
11,
12]. A QPUF-generated response for each quantum hardware can ensure security and privacy in quantum information processing and communication. QPUF harnesses unique quantum hardware variable parameters, more specifically qubit coherence, decoherence times, and gate errors across various quantum computers [
13,
14].
This work explores the scope of Quantum-assisted cybersecurity in industrial IoT applications by implementing QPUF technology on Quantum Hardware. Quantum computing’s potential in advancing computational capability to the next level surely has great potential in Industry 4.0. This work aims to leverage the potential of SbD in Quantum computing for IIoT security by proposing a QPUF-based device authentication and access control mechanism that ensures the security of the device, firmware, and network communication in IIoT. Executing QPUF-based security solutions in I-CPS can improve the efficiency of industrial operations, particularly as IIoT frameworks increasingly rely on cloud computing [
5]. Most PUF-based security solutions work by connecting physical hardware for the extraction and validation of keys [
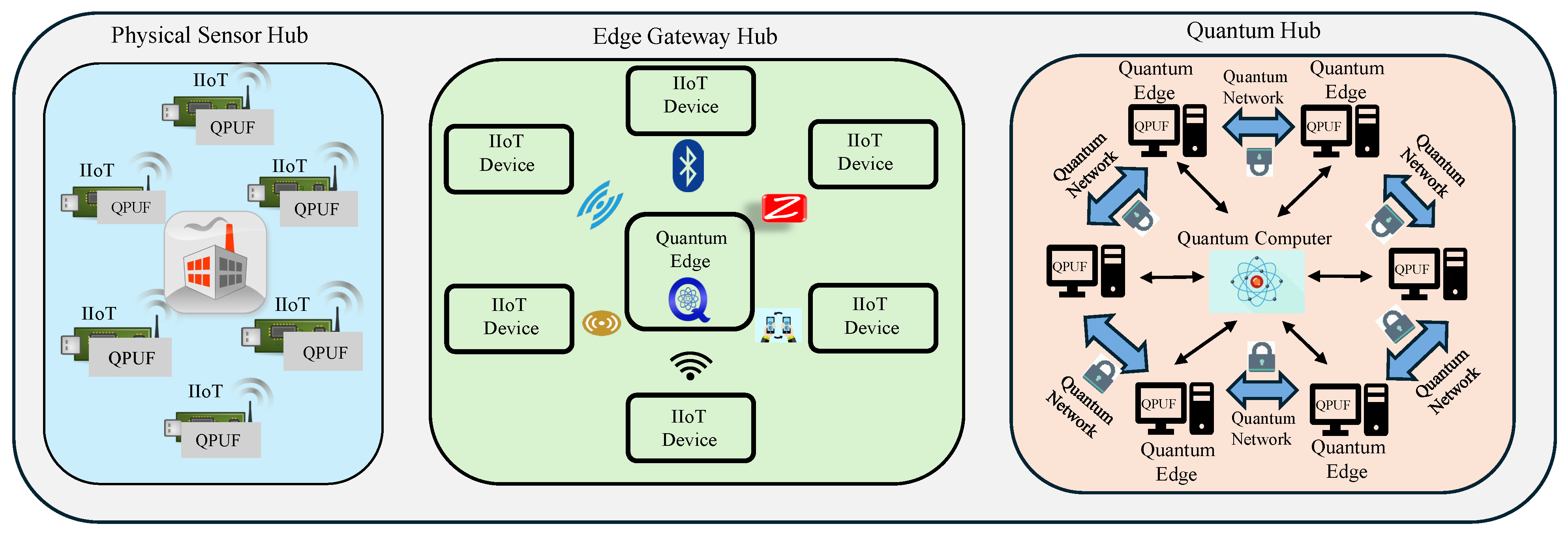
6]. This approach can reduce scalability as the number of IoT devices increases based on the application. The proposed QPUF-driven security approach establishes a robust cloud-based authentication framework among all entities in I-CPS, where a QPUF-generated fingerprint ensures the reliability of both communication and data. Since current quantum computing applications are primarily cloud-based, this approach further enhances scalability in emerging quantum-driven I-CPS environments. A conceptual overview of the proposed QPUF-based secure I-CPS architecture is depicted in
Figure 1.
In I-CPS, all the smart actuators, machines, and smart sensors can be connected to the edge cloud environment for uploading sensitive parametric data related to machines, and production metrics [
15]. To ensure the authenticity and integrity of the device, quantum hardware can be accessed through the cloud to generate a unique response driven by quantum mechanics. Clusters of smart actuators and sensors can obtain unique quantum hardware-generated security keys from QPUF at the quantum computer, ensuring secure authentication. The IIoT devices are controlled and monitored by supervisory control and data acquisition systems (SCADA), ensuring intelligent management control, and communication among various entities in I-CPS. SCADA-based management systems include Human–Machine Interface, Remote and Master Terminal Units, and centralized command control for data sensing, communication, and decision-making tasks [
5].
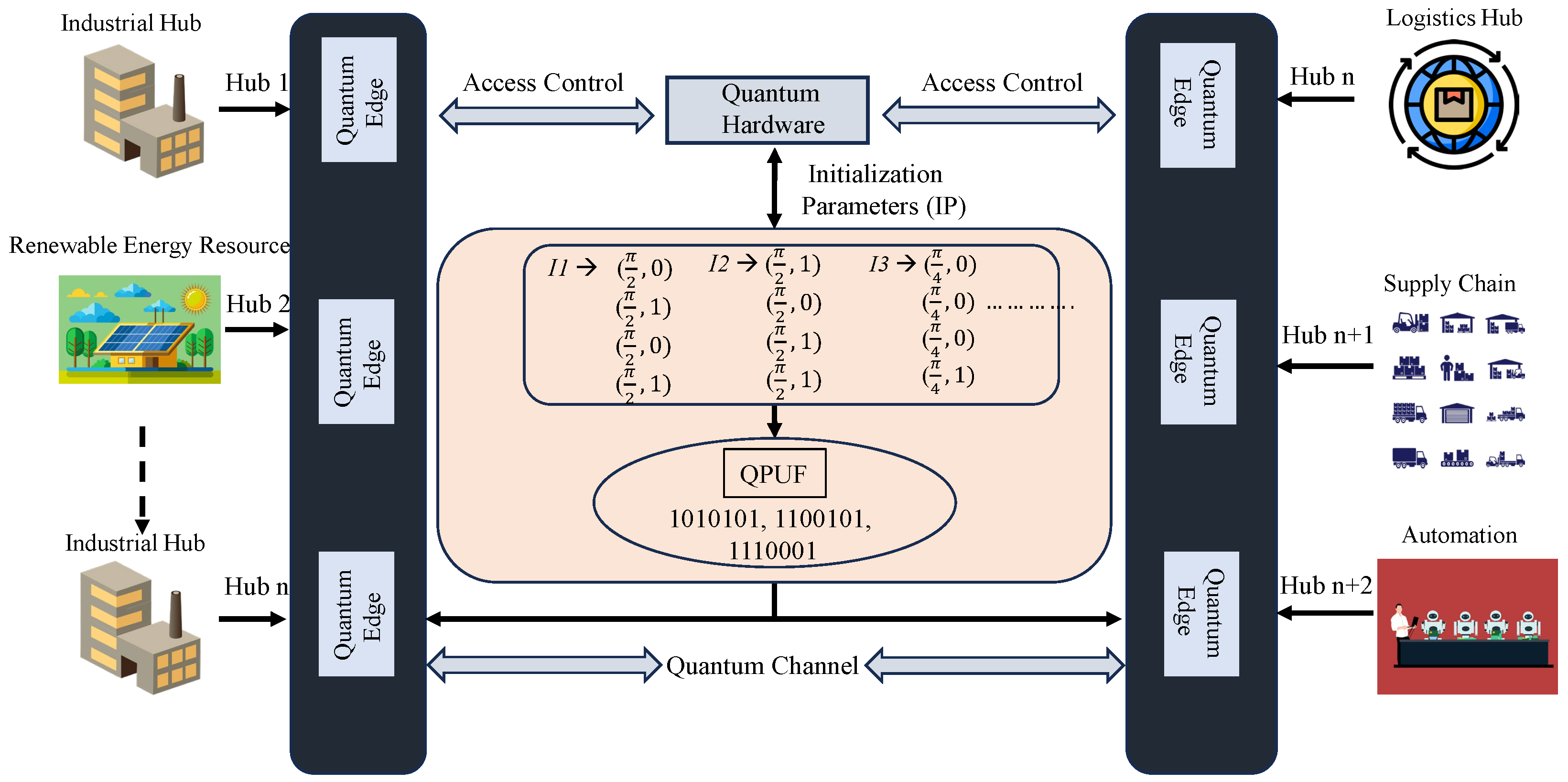
Quantum computing integration can further their capabilities, ensuring efficient data processing, secure quantum channel-driven communication, and quantum-hardware-assisted device attestation in I-CPS. The advantage of including QPUF-based security mechanisms in industrial environments is the easier integration of cloud computing systems in I-CPS in the present age, with the potential for the even more straightforward integration with quantum chips in the future [
4]. An overview of the proposed QSbD primitive for IIoT is presented in
Figure 2.
The rest of this paper is organized as follows. A conceptual idea of SbD and QSbD, along with their strategies and principles, is outlined in
Section 2.
Section 3 illustrates the contemporary related works in IIoT security.
Section 4 discusses the contributions of this research work. The preliminaries and working model of the proposed QPUF architecture are discussed in
Section 5. The QPUF experimental validation results, along with the challenges, are presented in
Section 6. Finally, the conclusion and future work are discussed in
Section 7.
2. Security-by-Design in Quantum Computing
Security-by-Design (SbD) advocates that security practices are introduced in the initial phase of the product development cycle, rather than being implemented during the application phase, to address issues affecting performance and reliability. SbD ensures security is a fundamental feature of the product and can withstand any attack through the intensive testing and evaluation of various possible invasive events and security vulnerabilities [
16]. Privacy-by-design (PbD) is analogous to the SbD approach, focusing more on the development of a product, with privacy protection mechanisms as in-built functionalities capable of ensuring the confidentiality or privacy of data processing as a default working functionality that is completely embedded into the design. SbD/PbD principles define and drive the security ecosystems during the design or product development stage. Examples of SbD include the Windows 11 Operating System, supporting Windows Hello and TPM 2.0 to provide a secure biometric sign-in and hardware-based protection for businesses, along with the boot process, ensuring a secure startup environment that allows for devices to boot-up with manufacturer-trusted software [
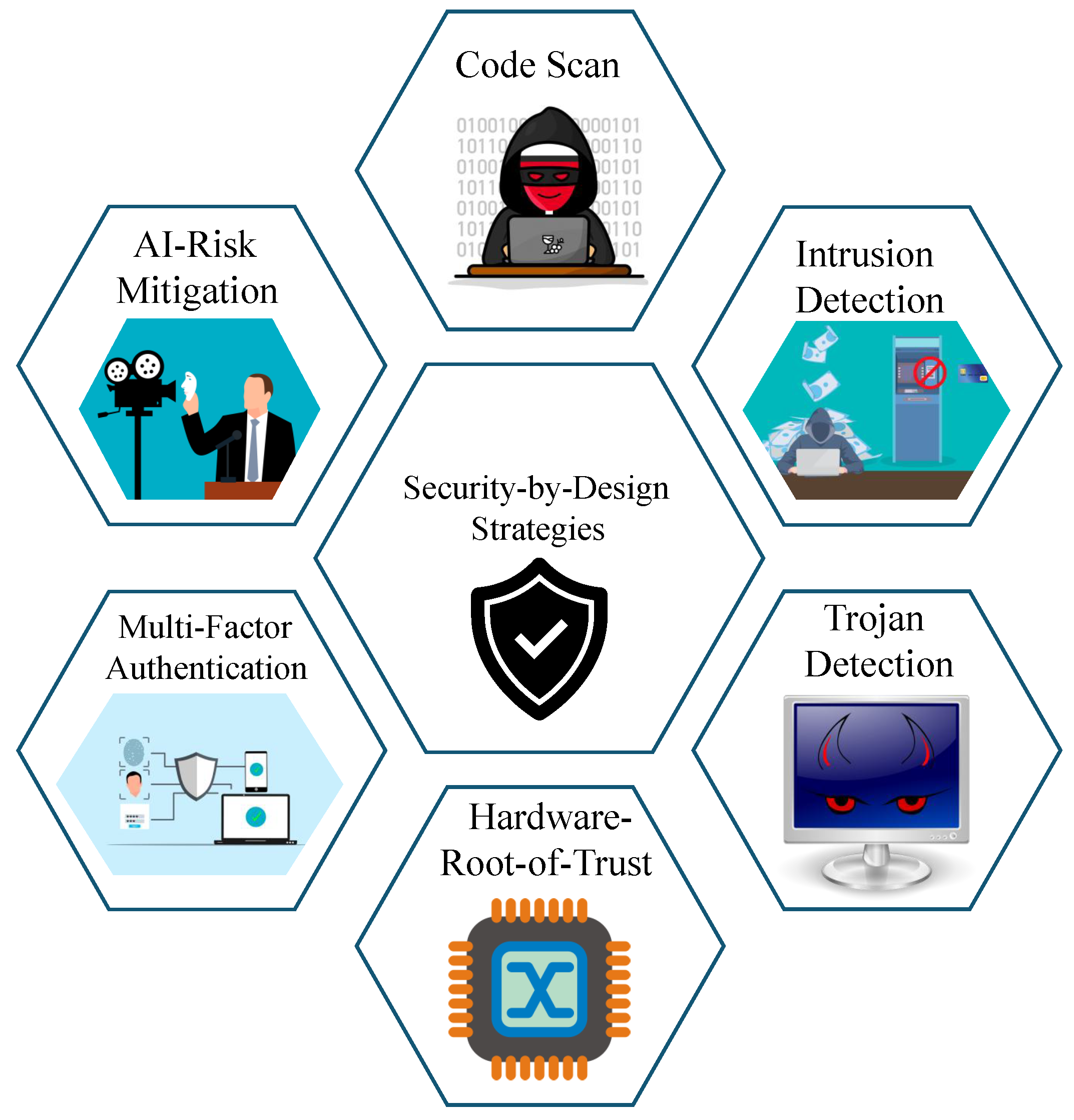
17]. With SbD, the security practices integrated at the design level form a foundation that cannot be tampered with easily without changing the core design or product configuration. A comprehensive overview of Security-by-Design strategies is provided below [
18] and presented in
Figure 3.
Threat Modelling is a key SbD component, performing an analysis of the security vulnerabilities of a product from the adversarial perspective. This includes the enabling, proactive identification, analysis, and mitigation of potential threats during the early stages of the product development cycle, identifying critical assets such as firmware and data credentials that require protection and performing an evaluation of external threat factors, including malware and insider threats. This approach helps organizations to evaluate security practices such that they align with industry security standards, such as NIST and ISO 27001. Threat modeling and risk assessment should be adopted using a bottom-up approach during product development and deployment, starting from the physical hardware, network, operating systems, software, database storage, and supply chain. The working flow of threat modeling includes identifying the vulnerabilities at the hardware, firmware, and software levels of the system, identifying critical system assets and data processing flow, evaluating the potential adversarial threats and vulnerabilities, and finally, proposing security countermeasures, such as encryption, authentication, secure boot, hardware-assisted security, and a trusted execution environment (TEE) [
16].
Defense in Depth is an SbD strategy that emphasizes a layered security approach with multiple layers of primitives to protect systems, data, and networks from threats. This strategy helps to address single-point-failure problems and can minimize risks even if the security of one layer is compromised. A layered approach to access control and authorization can minimize adversarial access to the product’s data and resources. This includes employing runtime security agents, firewalls, and intrusion detection systems to protect the systems’ access from adversaries. Additionally, multi-factor, biometric authentication, and least-privilege principles ensure identity and access management. Multi-factor authentication is a layered approach for ensuring the trust and authenticity of systems’ access and control. With MFA-based approaches, Amazon has reported a 99% drop in password-based attacks [
19].
Hardware-Root-of-Trust ensures a trustworthy execution environment for cryptographic operations, authentication, and secure boot. To ensure security from the foundational level of the product, hardware primitives such as PUF and TPM provide various security functionalities, ensuring manufacturer-trusted firmware and software execution during system boot, cryptographic keys storage, and a hardware-secure execution environment to perform computations securely. A secure cloning and hardware-tampering-resistant approach using PUF ensures reliable and efficient security are obtained using inherent silicon variations. Furthermore, hardware-centric fine-grained memory protection through TPM, providing tamper-proof storage, stands as a key SbD strategy [
20].
Secure AI Applications advocate for security and privacy at every stage of AI model development, deployment, and operation using the principles of SbD. The training and quality of sensitive data, which include personal, operational, and financial information, could be compromised, threatening model integrity. Furthermore, extracting medical data from AI-based healthcare models could jeopardize their applications. To address this, security should be seen as an incorporated feature of AI and ML applications, performing adversarial training to make AI models resistant to perturbations and employing secure AI accelerators deployed with security primitives like TPM and PUF. Other possible application scenarios include applying security and privacy-enabled features for the detection and mitigation of deepfakes using secure AI accelerators, preventing the unauthorized use of personalized social media through various approaches, such as hardware-root-trust for watermarking and storage and a lightweight distributed ledger for secure data access and storage.
The key principles of Security-by-Design (SbD) are outlined below [
20]:
Proactive not Reactive: SbD emphasizes adopting systems’ security practices as a proactive approach rather than as an afterthought. This includes adopting threat modeling and code scanning approaches to identify potential vulnerabilities and threats.
User-Centric: The security practices that are adopted should be user-friendly and should not interfere with the systems operations and control, while still ensuring robust inbuilt security systems are in place. This could be achieved through MFA, which facilitates secure user access to systems applications, ensuring systems access for specified users through a robust authentication that works internally while being user-centric through supportive approaches like user-chosen passwords.
Embedded into the Design: SbD ensures security is in place from the very beginning of the product development process and is completely embedded at the system’s architectural level.
Full Functionality—Positive-Sum, Not Zero-Sum, Without Trade-Offs: SbD solutions should not have trade-offs that impact the performance and efficiency of the system; they should be mutually reinforcing without requiring a choice between security and efficiency.
End-to-End Security and Privacy for Lifecycle Protection: Security and privacy measures should be adopted to ensure integrity and reliability throughout the cycle, from system development to application-level deployment.
Visibility and Transparency: Users and organizations should have a clear idea of the security practices and access control mechanisms in place. This includes transparency in the policies that are implemented, and open security standards regarding the use of AI-assisted intelligent automated decision-making systems.
Respect for Users: Security and privacy policies should not overpower users through restricting access rather than ensuring user consent, user-centric systems, and data access control are in place, and regulated ethical AI principles should be deployed, such as privacy-focused data searches.
QSbD focuses on the security of quantum computing applications and emphasizes quantum mechanics as driving principles to ensure the security, privacy, and efficiency of an application from the development stage. This approach, analogous to SbD, focuses on building and deploying quantum-computing algorithms and applications with security and privacy as default primitives, harnessing quantum mechanical principles. Quantum’s no-cloning theorem states that it is impossible to copy or clone the arbitrary unknown quantum state and Heisenberg’s uncertainty principle states the impossibility of absolutely determining the position of a particle [
21]. These principles serve as the driving forces for QSbD, ensuring the hardware is capable of trustworthy, secure, and encrypted communication, as well as enhancing computational processing power compared with classical computing. This validates this technique’s potential use in emerging Quantum IoT applications [
22].
3. Related Research
This section briefly discusses the related prior research on QPUF and security approaches for Industrial IoT systems.
In [
11], it is observed that crosstalk in superconducting transmon qubits impacts the quantum state of a qubit. Based on this observation, the QPUF signature generation process is defined using a Ramsey experiment, which determines the absolute resonant frequency of a qubit. Crosstalk introduces noise, thereby affecting the resonant frequencies of other qubits. A novel QPUF architecture that leverages quantum decoherence and entanglement to generate a unique bitstream of random zeros and ones is proposed in [
21]. The evaluation of the QPUF architecture demonstrated reliable QPUF response generation using quantum Ry, CNOT, Pauli-X, and Hadamard gates.
A novel Quantum tunneling PUF, titled Neo PUF, has been proposed, which operates by storing the PUF signature within an ultra-thin oxide layer, ensuring reliability. This PUF leverages manufacturing variations in oxide thickness to generate unique signatures [
23]. The authors in [
24] proposed Quantum circuit-based PUF designs that rely on tunable rotation angles for the Ry gate. However, their work does not provide an experimental demonstration of the final PUF signature. In contrast, our work experimentally validates the QPUF design implemented using Quantum Logic gates and explicitly defines PUF signatures through approximation. Furthermore, in this protocol, an unverified party cannot intercept communication over the quantum channel between two trusted entities [
25,
26]. In contrast to the previously discussed research on QPUF, the proposed work focuses on achieving enhanced reliability through leveraging quantum entanglement and superposition principles to drive the QPUF circuit. While prior studies have highlighted the need for further improvements in QPUF calibration to attain reliability, they fall short in this regard. This research introduces a novel QPUF topology that generates a scalable Challenge Response with improved randomness, uniqueness, and, notably, reliability.
A novel PUF-based blockchain, named HPCchain, has been proposed in [
27] for security and device authentication in IIoT. This work introduces a consortium Blockchain framework with a PUF-based consensus mechanism. The architecture of HPCchain is structured into four layers: Asset, Blockchain, Data, and Application. The Asset layer comprises PUF-embedded smart sensors, machines, and industrial actuators. The Blockchain layer operates on top of the asset layer, handling the recording and validation of transactions. The Data and Application layers operating above the Blockchain are responsible for analysis, processing, decision-making, and actuation.
A novel approach to sensor data stream integrity verification using PUF in Industrial–Cyber–Physical Systems (I-CPS) is proposed in [
7]. This work introduces a PUF-based method to ensure secure communication between PLC nodes and sensor nodes in industrial environments. By embedding smart sensors with PUF modules, this approach claims to mitigate side-channel attacks. A secure Machine-to-Machine (M2M) communication mechanism leveraging PUF for IIoT has been proposed in [
28]. This work introduces a PUF-based Efficient Authentication and Session Establishment (PEASE) protocol, designed to ensure the confidentiality of a device’s identity with minimal computational power and energy overhead. In [
6], a pseudo-PUF-based IIoT security mechanism, is proposed, utilizing a weak PUF module with limited Challenge–Response Pairs (CRPs), along with a lightweight symmetric encryption module. This approach focuses on reducing energy overhead while enhancing the resiliency of the pseudo-PUF. A simple quantum random generator (QRNG) for security in IIoT applications is proposed in [
4]. This work implements QRNG in both a quantum simulator and in real quantum hardware, providing a quantum virtual private network-based communication framework for IIoT devices and cloud systems. However, it does not provide details of the feasibility of using QRNG in various hardware backends or the impact of noise on system performance. Additionally, a QIoT framework leveraging quantum entanglement for IoT sensor data attestation using Blockchain is proposed in [
29]. This framework is designed for various applications, such as manufacturing monitoring, logistics, and smart grid renewable energy resource management. A comprehensive analysis of the research works on QPUF- and PUF-based security approaches to IIoT systems is presented in
Table 1.
4. Novel Contributions
This section discusses the research problems addressed in the context of an SbD of an IIoT systems, highlights the key contributions of the proposed research, and outlines the proposed methodology.
In IIoT systems, various wireless network communication protocols enable seamless interaction among IIoT entities. However, these entities are susceptible to numerous cyber threats and attacks. Adversarial access to even a single entity can compromise the security and integrity of the entire industrial infrastructure, potentially leading to equipment malfunctions, system outages, or control mechanisms and sensor data being tampered with. The development of quantum chips has amplified interest in their potential across domains such as Artificial Intelligence, IoT, and Blockchain. However, the integration of quantum computing still presents significant challenges, particularly in terms of their interoperability and infrastructure. The proposed research aims to investigate the scope of its application in enhancing security and privacy, guided by the principles of quantum mechanics.
4.1. Research Problems Addressed in the Current Paper
Challenges in achieving the scalable and tamper-proof attestation of IIoT devices in resource-intensive smart industries.
Challenge of ensuring reliable communication among various entities within industrial IoT systems.
Problem of quantum sensor attestation and the need to achieve tamper-proof authentication for IIoT systems.
Problem of generating reliable QPUF responses from inherently noisy quantum computers.
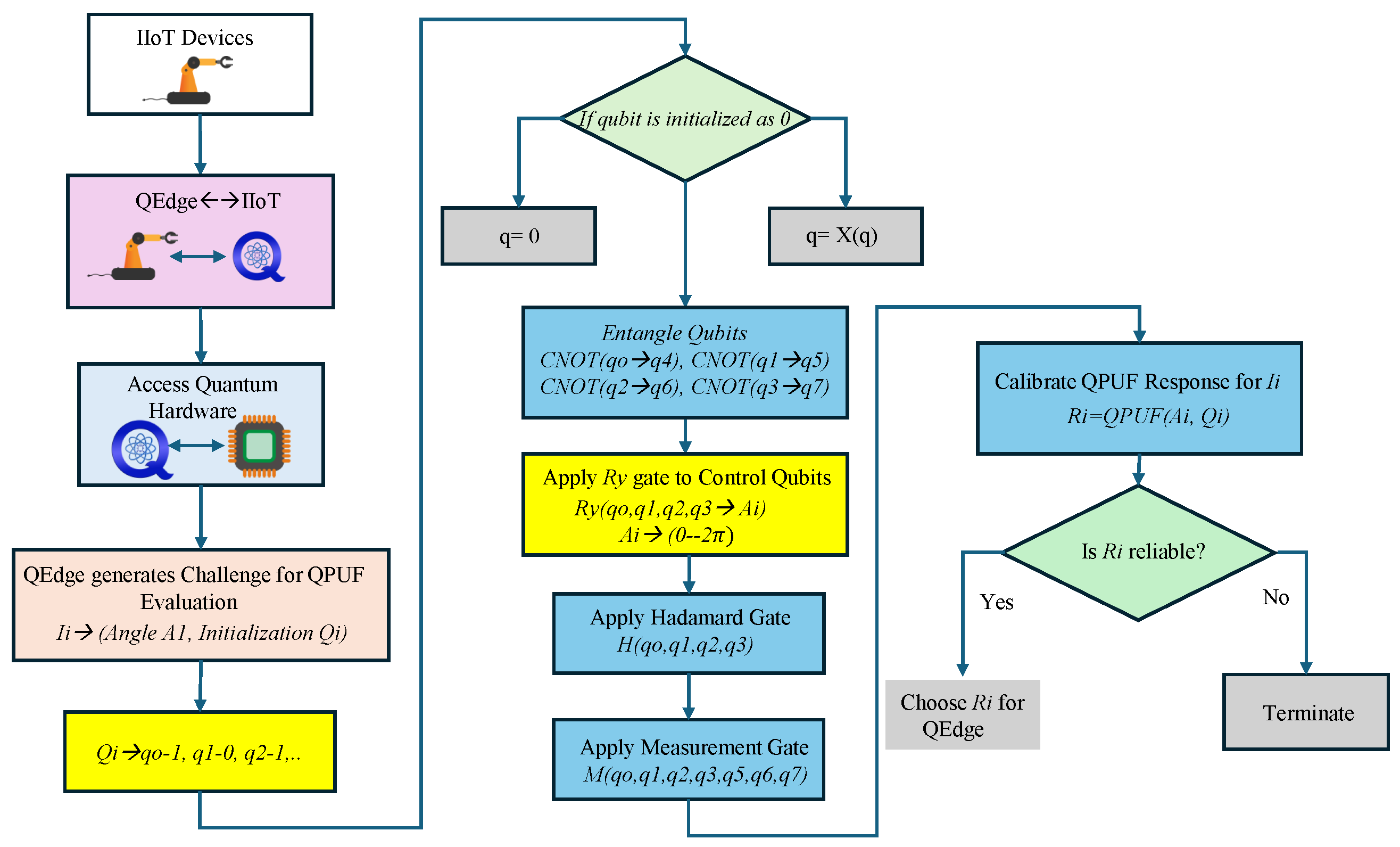
The proposed research introduces a novel QSbD framework to transform IIoT systems through a sustainable, quantum hardware-assisted security framework. Central to this framework is the QPUF, which provides a robust authentication mechanism to ensure the security and integrity of both devices and data. As a unique hardware security primitive, the QPUF holds significant promise for quantum-centric security. This research presents an innovative QPUF topology that leverages quantum mechanics principles. The key contributions and novel features of the proposed research are further detailed below.
4.2. Proposed Solution and Methodology
A QPUF CRP generation method for noisy quantum computers.
QPUF-based secure digital fingerprint for Intelligent Electronic Devices (IED), smart industrial automation systems, and machines in IIoT.
A novel QPUF key generation and identity attestation method for IIoT devices using noisy quantum computers.
A robust quantum-hardware-assisted device attestation framework for SCADA-IIoT systems.
An intelligent device and data security approach enabled by QPUF.
An approach utilizing the quantum principles of entanglement and superposition.
A QPUF architecture implemented using Quantum CNOT, Ry, and H gates, and evaluated on IBM quantum systems.
4.3. Novel Features of the Proposed Solution
A sustainable approach to QPUF response generation with 100% reliability.
A QPUF architecture that demonstrates significant randomness when evaluated on the IBM quantum simulator.
A state-of-the-art solution aimed at enhancing the reliability of quantum computing for Industrial IoT frameworks.
A sustainable method for quantum noise reduction and reliable QPUF response generation.
6. Experimental Results
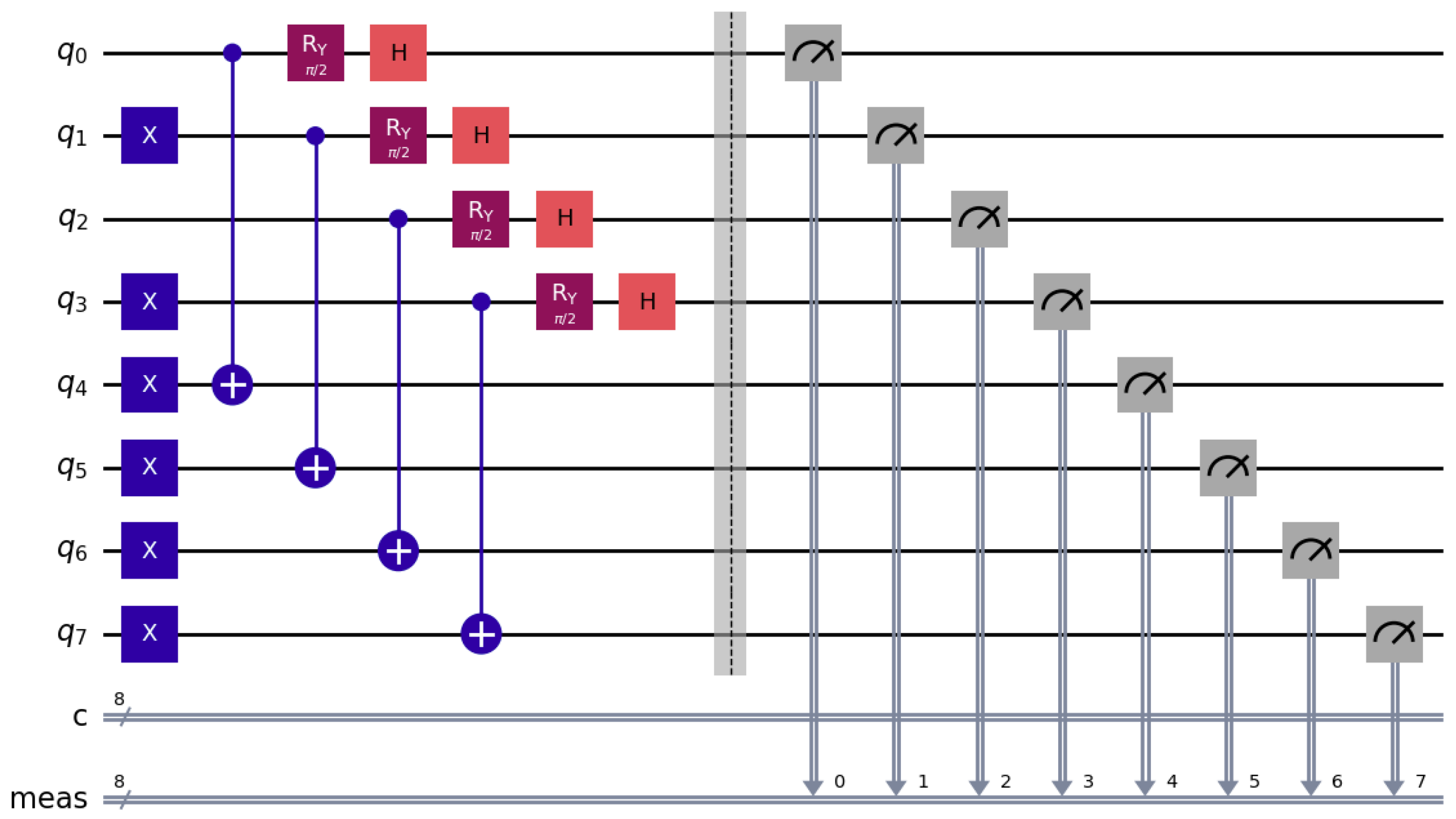
The proposed QPUF architecture was evaluated using IBM quantum systems and simulators. The IBM Qiskit’s “qasm_simulator” was selected for the evaluation, with a total of 100 jobs executed on the simulator across five instances. In each job, all the qubits in the QPUF were randomly initialized using the Pauli X-Gate. For each job, 1024 measurement outcomes or shots were obtained. The most frequently occurring outcome was chosen as the QPUF response key for that job. A total of 100 jobs were executed with 100 unique qubit initializations, utilizing predefined Ry gate angles of [pi/4, pi/2, pi. 3pi/2], applied to entangled control qubits. Five instances of these 100 jobs were conducted on the “qasm_simulator” via the IBM Qiskit Run Time service [
31], which enables users to submit jobs directly to IBM’s quantum systems. For evaluation, the Python programming language was used, and the Quantum PUF metric evaluation was performed on the obtained results. After acquiring an Application Programming Interface (API) token from IBM, the Qiskit Run Time was loaded, and the QPUF circuit was implemented and transpiled. The use of transpilation in the Qiskit Run Time optimized the circuit logic by considering the chosen quantum backend’s qubit connectivity and supported gates, thereby enhancing execution efficiency. Sampler v2 was used to execute quantum circuits in the Qiskit 1.0 version. An evaluation of the QPUF circuit on ibm_brisbane is shown in
Figure 6. Additionally, the proposed QPUF was also evaluated on the Google Cirq simulator [
32], with similar qubit initialization states chosen for evaluation on the qasm_simulator and a tunable rotation angle of 90°. The performance evaluation metrics of the QPUF on Cirq simulator and qasm simulators are presented in
Figure 7.
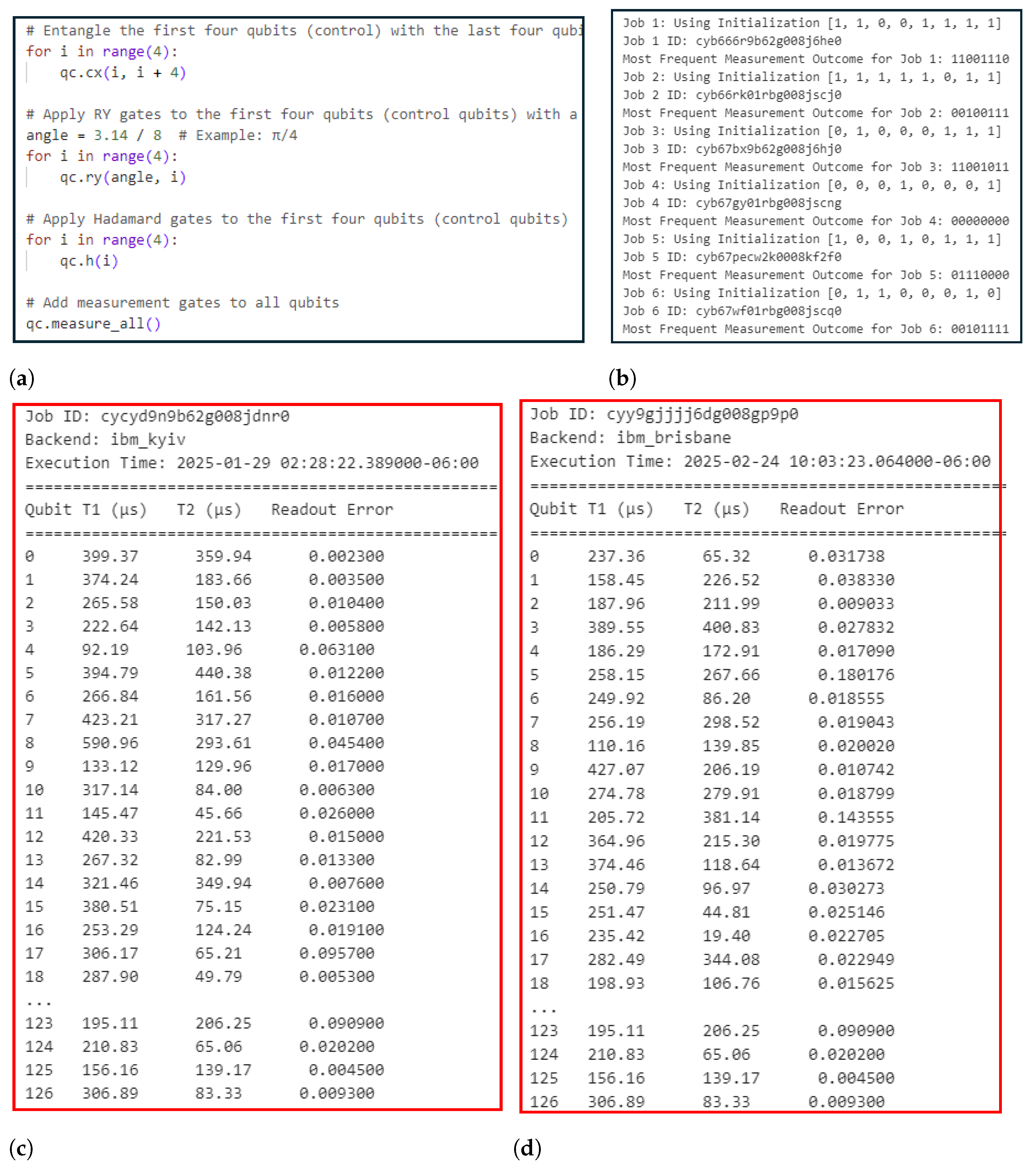
The quantum computing development environment was set up on a personal computer equipped with a 12th Gen Intel Core i7-12700F processor (2.10 GHz), 16 GB RAM, and a 64-bit architecture. The currently deployed versions are Qiskit 1.3.2 and IBM Runtime 0.34.0. With Sampler v2, circuit submission and execution on the backend were more efficient, exhibiting no latency and enabling noise-free quantum circuit execution. For the current evaluation, the IBM quantum platform’s open plan provides access to three Quantum hardware systems as of January 2025: ibm_kyiv, ibm_sherbrooke, and ibm_brisbane. The open plan allows for limited Qiskit runtime usage of 10 min, whereas the current QPUF evaluation time for each job approximately ranges from 2 to 10 s, highlighting the constraints of the execution window. Once a job is submitted to a backend, a unique job address is assigned, and the circuit is executed with the specified initialization parameters.
For hardware evaluation, ibm_kyiv and ibm_brisbane were selected. These are 127-qubit quantum processors that support scalable packaging, enabling a higher qubit density with improved performance. The enhanced performance is attributed to the improved qubit coherence, supported by the advanced Eagle architecture, which increases reliability. Due to the limited circuit evaluation space supported by IBM, only 10 jobs were executed for QPUF evaluation on hardware backends. Each job used a unique qubit initialization sequence, where qubits were initialized using the Pauli-X gate. Following quantum entanglement, a set of tunable Ry gate rotation angles was applied to control the quantum state rotation of entangled qubits. The QPUF reliability evaluation on the IBM quantum systems and simulators is presented in
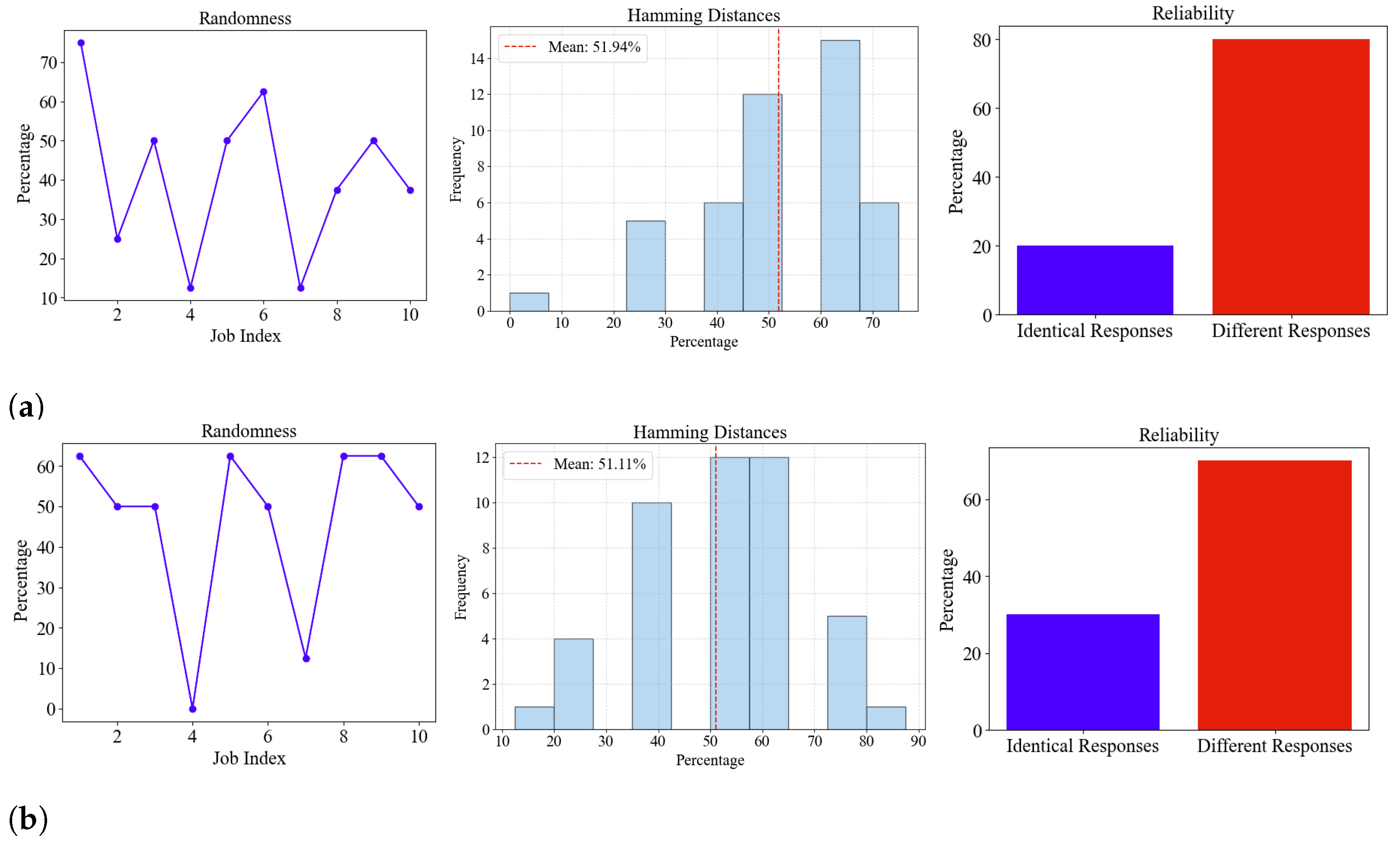
Table 2. The QPUF evaluation of the IBM quantum simulator showed 95% reliability, with almost all the QPUF-generated keys being regenerated across five instances of 100 jobs evaluated at a tunable rotation angle of pi/2. Furthermore, we conducted experimental evaluations of quantum hardware-ibm_sherbrooke, ibm_brisbane, and ibm_kyoto from IBM, and their corresponding performance metrics are presented in
Figure 8. For the hardware evaluation, only 10 evaluations were conducted per instance, with a total of three instances being considered. Additionally, different tunable rotation angles were applied to the first four qubits in the circuit. Our experimental evaluation of the simulators was performed at a fixed tunable rotation angle of 90° and achieved excellent reliability and uniqueness. The corresponding evaluation of hardware at a tunable rotation angle of 90°, although achieving high reliability, did not exhibit the same level of uniqueness.
6.1. Discussion and Analysis
The QPUF evaluation of IBM’s qasm_simulator achieved 100% reliability. Compared to the published research, this is the first QPUF design to attain 100% reliability across five instances of jobs, each evaluated with varying qubit initializations. The evaluation demonstrated an average intra-hamming distance and randomness of 50%. For QPUF response extraction from ibm_kyiv, a total of six job instances were executed, with each job producing 1024 measurement outcomes. All job strings from the six instances were analyzed to determine the most frequently observed measurement outcome. Due to noise and decoherence, occasional bit flips are expected, which could potentially alter the response. However, by evaluating occurrences across multiple instances, the most widely observed job string was selected as the reliable response for the respective backend and initialization parameters. The evaluation confirms that the QPUF circuit achieves 100% reliability, but its outcomes depend on the backends’ unique unclonable parameters at a specific time. Since backend calibration data are updated every 2–4 h, variations in these parameters can affect quantum state assessments.
During QPUF response computation, parameters were calibrated from the selected hardware. IBM performs a periodic calibration of the TI and T2 times, as well as readout errors, every few hours. In this research study, the experimental evaluation demonstrated reliable QPUF response generation without bit flips or noise when the QPUF circuit was executed on hardware within a specified time, provided that the parameters remained stable within the 2–4 h calibration window. However, fluctuations in qubits’ parameter values due to calibration introduce noise, leading to instability and potential bit flips in QPUF responses. As shown in
Table 2, the execution of QPUF on ibm_kyiv, and ibm_brisbane successfully regenerated a few QPUF responses without bit flips.
The calibration data, as presented previously in
Figure 6, includes a job ID and its backend configuration parameters, recorded during QPUF circuit evaluation. Additionally, they show the QPUF responses that were consistently regenerated across all five job instances executed under similar backend configuration parameters at the specified time. Our observations indicate that QPUF evaluations conducted with similar parameters exhibit consistent reliability among hardware. However, variations in these parameters across different evaluations lead to fluctuations in QPUF responses and reliability.
The comparative performance analysis of the proposed QPUF is an extension of the earlier architecture introduced in [
13], demonstrating improved reliability, uniqueness, and randomness by introducing quantum entanglement using a quantum C-NOT gate. Additionally, a comprehensive performance analysis of QPUF with state-of-the-art research is presented in
Table 3.
6.2. Challenges in the Evaluation
The accessibility of quantum computers remains a significant issue. However, as research on noise-free quantum computing and advanced quantum chips progresses, quantum computers are expected to become more accessible for a wider range of applications, making the execution of hundreds or even thousands of jobs much easier. The noisy quantum systems may sometimes produce identical responses across different types of quantum hardware, potentially affecting the outcomes and uniqueness of the circuit. This could be attributed to the very closely resonant driving frequencies, which fluctuate over time and qubit crosstalk. A potential solution is to assign a unique set of qubits for each quantum job when executing QPUF. By leveraging the quantum systems with a higher number of qubits, stable driving resonant frequencies, and improved coherence times, QPUF instantiation can be further optimized.