Lightweight Mutually Authenticated Key Exchange with Physical Unclonable Functions
Abstract
1. Introduction
Contributions
2. Related Work
3. Underlying Primitives
3.1. Physical Unclonable Function (PUF)
- It contains an exponential amount of response-relevant random information tied to an entropy source with a very high information density.
- The read-out speed of PUF responses is limited to low values. Moreover, the limitation is an inherent property of the PUF measurement process and not an arbitrary delay injected into the read-out circuit.
- The CRPs are mutually independent. Furthermore, the pairwise mutual information within any two responses is zero.
3.2. Key-Encryption-Key (KEK)
4. The PUF-MAKE Protocol
4.1. MAKE Enrollment Protocol
- The IA and AS mutually authenticate (MA) using a privacy-preserving PUF-based (P3B) protocol and then generate a session key (SKG), called . An example P3B protocol suitable for PUF-MAKE is described in [26].
- The same MA and SKG process is carried out between Alice and the IA to authenticate and generate a shared session key .
- The IA selects a CRP for Alice from its (constructed during provisioning), extracts , and encrypts it using AES-256. The ciphertext is transmitted to Alice.
- Alice decrypts to obtain . Alice applies the challenges to her hardware HPUF in enrollment mode to generate an authentication key, and helper data . She hashes using a SHA-3 hashing function to produce , and encrypts and with to produce ciphertext .
- Alice transmits ciphertext to IA. On the first iteration of the enrollment process, Alice also stores the tuple [, ] to persistent memory. She will use this challenge and helper data to reproduce during her first in-field authentication, discussed below.
- IA decrypts , fetches the response component of the challenge from its CRP database, and assigns the response to . IS hashes and compares the output with the decrypted received from Alice. If they match then Alice’s is validated. IA then encrypts packet with , containing Alice’s ID, , and AT components, namely , and .
- IA transmits the to AS.
- AS decrypts the and stores , , and in its database. The AT elements in this table will be used by AS for in-field authentication operations carried out on behalf of Alice (and Bob) and to enable Alice and Bob to generate a shared session key.
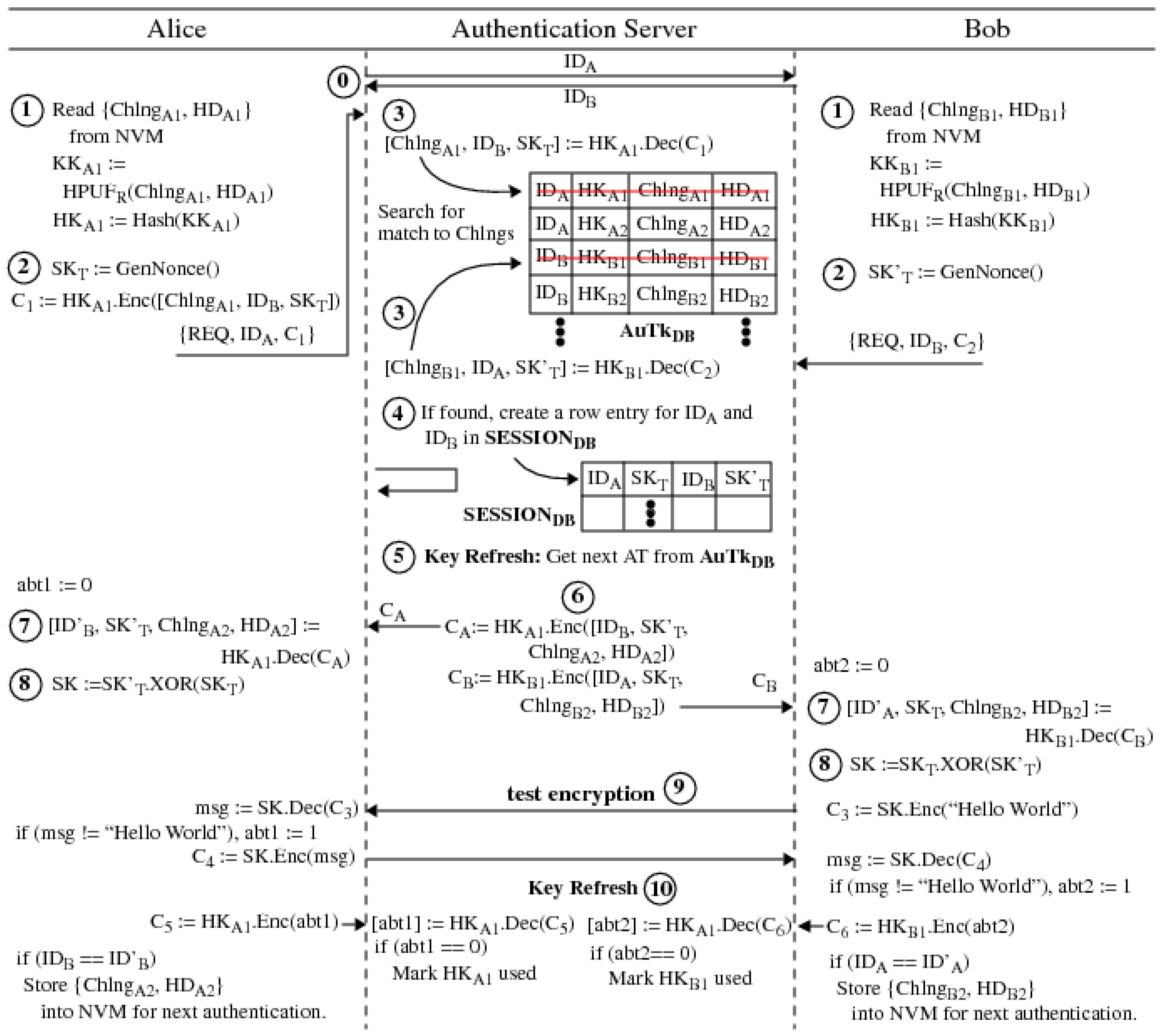
4.2. PUF-MAKE In-Field Interactive Authentication Protocol
- 0.
- The protocol begins with Alice and Bob sending a request to communicate to each other using an unencrypted packet with identifiers and .
- 1.
- Alice reads from NVM and runs her PUF, , in regeneration mode to regenerate response . She then calculates a hash of using a suitable hash function. Bob performs the same sequence of operations.
- 2.
- Alice and Bob generate session key shards, and , using their PUF-based true-random-number-generators (TRNGs).
- 3.
- Alice assembles packet by concatenating authentication artifacts, , Bob’s device ID, , and the session shard, , which are then AES-encrypted with as the key. Alice sends an authentication request to AS, along with and as metadata. The server matches to the list of known devices in the database populated by the issuing authority (IA) during enrollment. Upon match, the server uses the associated to decrypt and disassembles the , and fields. Authentication is a success if the extracted matches the one stored for in the database; otherwise, this process repeats using each of the remaining elements. If no matches are found, the protocol aborts. Note that both and must be correct for authentication to succeed. If does not match any of those stored in the , the packet will not be decrypted correctly and will be random, causing a mismatch. Alternatively, if is correct and is not, the packet will decrypt correctly but will fail to match. In either case, authentication fails and the server aborts the connection. Bob performs this same set of operations with AS.
- 4.
- If Alice’s authentication succeeds, AS adds and to a database. Similarly, if Bob’s authentication succeeds, AS adds and to the . In both cases, AS first searches for a match to and supplied by Alice and Bob, respectively, to determine if a row already exists, and, if so, adds Alice or Bob’s information to the matching row element instead of creating a new row. Once Alice and Bob’s IDs and are both present, AS proceeds to the next step; otherwise, it stalls the thread waiting for Alice or Bob to complete the transaction. A time-out can also be included that aborts the entire transaction and deletes the element.
- 5.
- The first step of Alice and Bob’s key refresh operation is for AS to fetch new AT elements from the , e.g., it selects rows associated with and elements. The key update mechanism ensures that Alice and Bob are protected against both impersonation and replay attacks.
- 6.
- AS constructs a packet for Alice by encrypting Bob’s authentication artifacts , and Alice’s next challenge and with Alice’s AES key. AS constructs a packet for Bob in a similar fashion and transmits the packets to Alice and Bob.
- 7.
- Alice decrypts her with to obtain Bob’s ID , Bob’s and her next authentication challenge. Bob does the same with his packet.
- 8.
- Both Alice and Bob XOR the and shards to obtain a shared session key , which they can use to encrypt communications between them.
- 9.
- Alice and Bob validate their shared key by performing a test encryption operation, where Bob encrypts a test message “Hello World” with and transmits it to Alice. Alice decrypts and validates. If the comparison fails, she sets her flag to 1. She then encrypts with her version of and transmits it to Bob. Bob decrypts and compares it to “Hello World”. If this fails, he sets to 1. Alice also encrypts her flag with and transmits to AS as encrypted packet . Bob carries out the same operation with .
- 10.
- If Alice and Bob succeed in the test encryption comparison operation, they possess a valid shared key and can encrypt communications between them. They notify AS with and , and AS marks the current AT as used. Alice and Bob also update their NVMs with the next Chlng and HD information under the condition that the ID’ values match the original ID values, which indicates they have received valid next challenge information.
5. Security Analysis
5.1. Formal Model
- Σ holds a state , which can be sampled by a physical probe P at measurement points defined by vector .
- Σ enables to be measured from z, where denotes the measurement process.
- 1.
- that represents a measurement made by P of the physical source Σ.
- 2.
- y is sampled in finite, positive, non-zero time t, which is tied to the intrinsic physical characteristics of Σ. The sampling time t is deterministic () based on the design of Σ.
- 3.
- Recovering z from y requires queries to Σ, or expressed formally, the likelihood of guessing by brute-force is:
- 4.
- Similarly, for two distinct physical instantiations, and , the likelihood that a measurement vector z generates an identical response is:
- 5.
- Simulating y, given X and P and non-zero , requires operations, where each operation requires duration t to complete.
- 1.
- The PUF function maps a unique unbounded challenge to a unique unbounded response.
- 2.
- The design is collision-resistant: , where and N is the number of response bits in ;
- 3.
- For a distinct physical device, , two non-identical challenges, and , will always generate responses and such that, where is the hamming distance and N is the bit cardinality of and , i.e., 50% of the bits are different between the two responses.
- 4.
- Two distinct physical devices based on the same design ( and ), a unique, identical challenge, , will generate responses and such that .
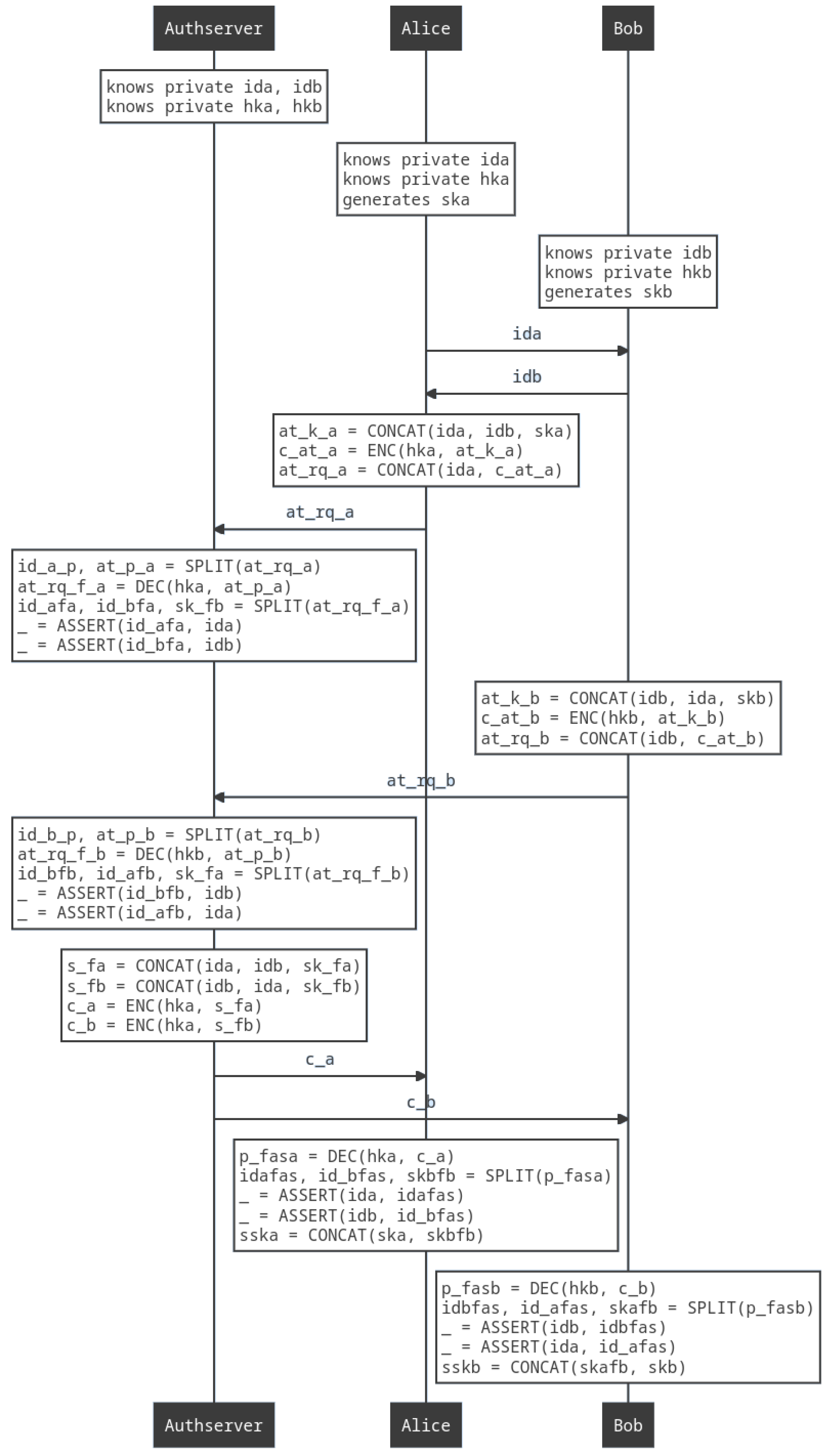
5.2. Protocol Model
| Algorithm 1: Formal description of the protocol |
Common Input: is well-formed
|
| Algorithm 2: Assertions derived from the PUF and protocol properties |
Assertions
|
6. Informal Security Analysis
6.1. Challenge Response Search-Space
6.2. Model-Building
6.3. Unlinkability
6.4. Fault Injection
6.5. Stored Secret Exfiltration
6.6. Bitstream Manipulation
6.7. Cryptographic Primitives
6.8. Enrollment
6.9. Correctness of In-Field Authentication
- Perform all attacks available to a passive attacker
- Control all communications channels specified in the model
- Collect packets over multiple runs of the protocol
- Inject, manipulate, replay, or delete messages at any point with information gathered from previous runs
6.10. Freshness and Replay
6.11. AS Spoofing and Key Exfiltration
7. Experimental Results
- The programmable logic (PL) component of the Zynq 7010 FPGA board is programmed with an instance of a SiRF PUF and KEK key generation algorithm, namely, those described for the SiRF PUF in [29]. A C program running under Linux coordinates communications between network entities and the PUF hardware. A microSD card provides NVM storage.
- The AS is also implemented on a ZYBO Z7-10 board, with the PL component programmed with an instance of the PUF. The C program implementation of AS is a multi-threaded application enabling concurrent communication through sockets with multiple customer devices, and with the IA. The AS utilizes sqlite3 databases to implement the and components of the MAKE protocol.
- The IA is implemented as a multi-threaded application with socket communication channels to customer devices and to AS. It also utilizes a sqlite3 database to implement the component.
- An openSSL implementation of the AES encryption algorithm is used for all protocol encryption and decryption operations. AES is configured to use a 256-bit key and CBC mode.
- An openSSL implementation of the SHA-3 256-bit hashing algorithm is used for all protocol hashing operations.
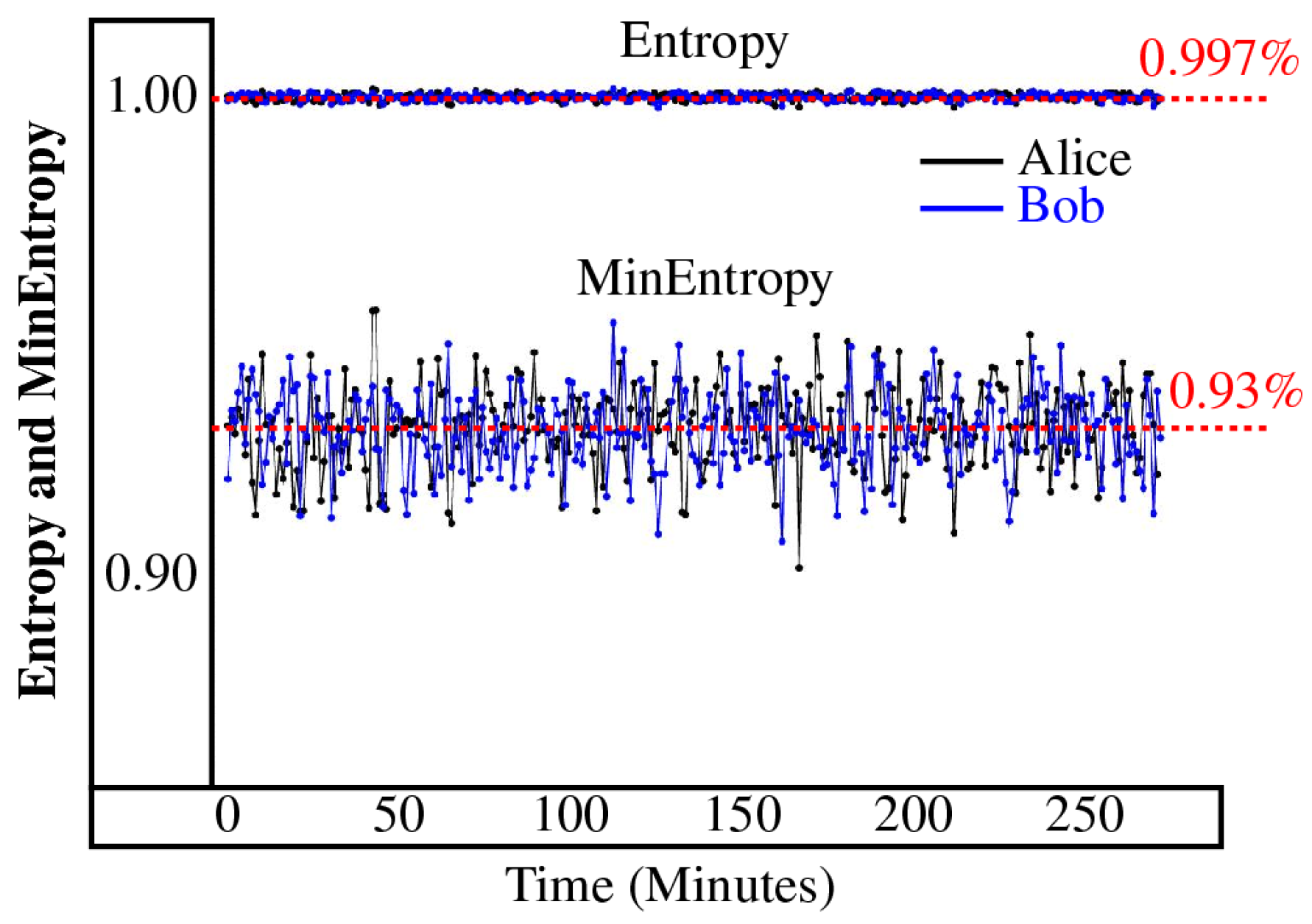
7.1. KEK Bitstring Statistical Analysis
7.2. Communication Complexity
7.3. Resource Utilization
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Guin, U.; Singh, A.; Alam, M.; Cañedo, J.; Skjellum, A. A Secure Low-Cost Edge Device Authentication Scheme for the Internet of Things. In Proceedings of the 2018 31st International Conference on VLSI Design and 2018 17th International Conference on Embedded Systems (VLSID), Pune, India, 6–10 January 2018; pp. 85–90. [Google Scholar] [CrossRef]
- Canetti, R. Universally composable security: A new paradigm for cryptographic protocols. In Proceedings of the 42nd IEEE Symposium on Foundations of Computer Science, Las Vegas, NV, USA, 14–17 October 2001; pp. 136–145. [Google Scholar] [CrossRef]
- Diffie, W.; Van Oorschot, P.C.; Wiener, M.J. Authentication and authenticated key exchanges. Des. Codes Cryptogr. 1992, 2, 107–125. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P. Entity Authentication and Key Distribution. In Advances in Cryptology—CRYPTO’ 93; Springer: Berlin/Heidelberg, Germany, 1993; pp. 232–249. [Google Scholar]
- Bellare, M.; Rogaway, P. Provably Secure Session Key Distribution: The Three Party Case. In Proceedings of the STOC ’95—Twenty-Seventh Annual ACM Symposium on Theory of Computing. Association for Computing Machinery, Las Vegas, NV, USA, 29 May–1 June 1995; pp. 57–66. [Google Scholar]
- Bellare, M.; Pointcheval, D.; Rogaway, P. Authenticated Key Exchange Secure against Dictionary Attacks. In Advances in Cryptology—EUROCRYPT 2000; Springer: Berlin/Heidelberg, Germany, 2000; pp. 232–249. [Google Scholar]
- Okamoto, T. Authenticated Key Exchange and Key Encapsulation in the Standard Model. In Advances in Cryptology—ASIACRYPT 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 474–484. [Google Scholar]
- Law, L.; Menezes, A.; Qu, M.; Solinas, J.; Vanstone, S. An Efficient Protocol for Authenticated Key Agreement. Des. Codes Cryptogr. 1995, 28, 119–134. [Google Scholar] [CrossRef]
- Krawczyk, H. HMQV: A High Performance Secure Diffie-Hellman Protocol. In Advances in Cryptology—CRYPTO 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 546–566. [Google Scholar]
- LaMacchia, B.; Lauter, K.; Mityagin, A. Stronger Security of Authenticated Key Exchange. In Proceedings of the International Conference on Provable Security, Wollongong, Australia, 1–2 November 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 1–16. [Google Scholar]
- Delvaux, J.; Peeters, R.; Gu, D.; Verbauwhede, I. A Survey on Lightweight Entity Authentication with Strong PUFs. ACM Comput. Surv. 2015, 48, 1–42. [Google Scholar] [CrossRef]
- Idriss, T.; Bayoumi, M. Lightweight highly secure PUF protocol for mutual authentication and secret message exchange. In Proceedings of the 2017 IEEE International Conference on RFID Technology & Application (RFID-TA), Warsaw, Poland, 20–22 September 2017; pp. 214–219. [Google Scholar] [CrossRef]
- Mahalat, M.H.; Saha, S.; Mondal, A.; Sen, B. A PUF based Light Weight Protocol for Secure WiFi Authentication of IoT devices. In Proceedings of the 2018 8th International Symposium on Embedded Computing and System Design (ISED), Cochin, India, 13–15 December 2018; pp. 183–187. [Google Scholar] [CrossRef]
- Mahalat, M.H.; Karmakar, D.; Mondal, A.; Sen, B. PUF Based Secure and Lightweight Authentication and Key-Sharing Scheme for Wireless Sensor Network. J. Emerg. Technol. Comput. Syst. 2021, 18, 1–23. [Google Scholar] [CrossRef]
- Che, W.; Martin, M.; Pocklassery, G.; Kajuluri, V.K.; Saqib, F.; Plusquellic, J. A Privacy-Preserving, Mutual PUF-Based Authentication Protocol. Cryptography 2017, 1, 3. [Google Scholar] [CrossRef]
- Chatterjee, U.; Govindan, V.; Sadhukhan, R.; Mukhopadhyay, D.; Chakraborty, R.S.; Mahata, D.; Prabhu, M.M. Building PUF Based Authentication and Key Exchange Protocol for IoT Without Explicit CRPs in Verifier Database. IEEE Trans. Dependable Secur. Comput. 2019, 16, 424–437. [Google Scholar] [CrossRef]
- Chatterjee, U.; Chakraborty, R.S.; Mukhopadhyay, D. A PUF-based secure communication protocol for IoT. ACM Trans. Embed. Comput. Syst. (TECS) 2017, 16, 1–25. [Google Scholar] [CrossRef]
- Wallrabenstein, J.R. Practical and Secure IoT Device Authentication Using Physical Unclonable Functions. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud, Vienna, Austria, 22–24 August 2016; pp. 99–106. [Google Scholar] [CrossRef]
- Yu, M.D.; Hiller, M.; Delvaux, J.; Sowell, R.; Devadas, S.; Verbauwhede, I. A Lockdown Technique to Prevent Machine Learning on PUFs for Lightweight Authentication. IEEE Trans.-Multi-Scale Comput. Syst. 2016, 2, 146–159. [Google Scholar] [CrossRef]
- Zhang, J.; Qu, G. Physical Unclonable Function-Based Key Sharing via Machine Learning for IoT Security. IEEE Trans. Ind. Electron. 2020, 67, 7025–7033. [Google Scholar] [CrossRef]
- Zheng, Y.; Liu, W.; Gu, C.; Chang, C.H. PUF-Based Mutual Authentication and Key Exchange Protocol for Peer-to-Peer IoT Applications. IEEE Trans. Dependable Secur. Comput. 2023, 20, 3299–3316. [Google Scholar] [CrossRef]
- Van Herrewege, A.; Katzenbeisser, S.; Maes, R.; Peeters, R.; Sadeghi, A.R.; Verbauwhede, I.; Wachsmann, C. Reverse Fuzzy Extractors: Enabling Lightweight Mutual Authentication for PUF-Enabled RFIDs. In Proceedings of the Financial Cryptography and Data Security, Kralendijk, Bonaire, 27 Februray–2 March 2012; Springer: Berlin/Heidelberg Germany, 2012; pp. 374–389. [Google Scholar]
- Zerrouki, F.; Ouchani, S.; Bouarfa, H. T2S-MAKEP and T2T-MAKEP: A PUF-based Mutual Authentication and Key Exchange Protocol for IoT devices. Internet Things 2023, 24, 100953. [Google Scholar] [CrossRef]
- Tun, N.W.; Mambo, M. Secure PUF-Based Authentication Systems. Sensors 2024, 24, 5295. [Google Scholar] [CrossRef] [PubMed]
- Rührmair, U.; Sölter, J.; Sehnke, F. On the Foundations of Physical Unclonable Functions. Cryptology ePrint Archive, Paper 2009/277. 2009. Available online: https://eprint.iacr.org/2009/277 (accessed on 8 August 2024).
- Plusquellic, J.; Tsiropoulou, E.E.; Minwalla, C. Privacy-Preserving Authentication Protocols for IoT Devices Using the SiRF PUF. IEEE Trans. Emerg. Top. Comput. 2023, 11, 918–933. [Google Scholar] [CrossRef]
- Rührmair, U.; Busch, H.; Katzenbeisser, S. Strong PUFs: Models, Constructions, and Security Proofs. In Towards Hardware-Intrinsic Security: Foundations and Practice; Springer: Berlin/Heidelberg, Germany, 2010; pp. 79–96. [Google Scholar] [CrossRef]
- van Dijk, M.; Rührmair, U. Physical Unclonable Functions in Cryptographic Protocols: Security Proofs and Impossibility Results. Cryptology ePrint Archive, Report 2012/228 2012. Available online: https://ia.cr/2012/228 (accessed on 10 August 2024).
- Plusquellic, J. Shift Register, Reconvergent-Fanout (SiRF) PUF Implementation on an FPGA. Cryptography 2022, 6, 59. [Google Scholar] [CrossRef]
- Rührmair, U.; Sehnke, F.; Sölter, J.; Dror, G.; Devadas, S.; Schmidhuber, J. Modeling Attacks on Physical Unclonable Functions. In Proceedings of the 17th ACM Conference on Computer and Communications Security, Chicago IL, USA, 4–8 October 2010; pp. 237–249. [Google Scholar] [CrossRef]
- Rührmair, U.; Xu, X.; Sölter, J.; Mahmoud, A.; Majzoobi, M.; Koushanfar, F.; Burleson, W. Efficient Power and Timing Side Channels for Physical Unclonable Functions. In Proceedings of the Cryptographic Hardware and Embedded Systems, Busan, Republic of Korea, 23–26 September 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 476–492. [Google Scholar]
- Delvaux, J. Machine-Learning Attacks on PolyPUFs, OB-PUFs, RPUFs, LHS-PUFs, and PUF-FSMs. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2043–2058. [Google Scholar] [CrossRef]
- Ramsay, C.; Lohuis, J. TEMPEST Attacks against AES; Fox-IT: Fremont, CA, USA, 2017. [Google Scholar]
- Das, D.; Sen, S. Electromagnetic and Power Side-Channel Analysis: Advanced Attacks and Low-Overhead Generic Countermeasures through White-Box Approach. Cryptography 2020, 4, 30. [Google Scholar] [CrossRef]
- Kobeissi, N.; Nicolas, G.; Tiwari, M. Verifpal: Cryptographic Protocol Analysis for the Real World. In Proceedings of the CCSW’20—2020 ACM SIGSAC Conference on Cloud Computing Security Workshop, New York, NY, USA, 9 November 2020; p. 159. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Digilent Corporation. ZYBO-Z7 Reference Manual; Digilent Corporation: Pullman, WA, USA, 2021. [Google Scholar]
- Bean, B.; Minwalla, C.; Tsiropoulou, E.E.; Plusquellic, J. PUF-based Digital Money with Propagation-of-Provenance and Offline Transfers between Two Parties. J. Emerg. Technol. Comput. Syst. 2024, 20, 1–26. [Google Scholar] [CrossRef]




| Scheme | Single Node | Server |
|---|---|---|
| SOTA [21] | ||
| This work |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Minwalla, C.; Plusquellic, J.; Tsiropoulou, E.E. Lightweight Mutually Authenticated Key Exchange with Physical Unclonable Functions. Cryptography 2024, 8, 46. https://doi.org/10.3390/cryptography8040046
Minwalla C, Plusquellic J, Tsiropoulou EE. Lightweight Mutually Authenticated Key Exchange with Physical Unclonable Functions. Cryptography. 2024; 8(4):46. https://doi.org/10.3390/cryptography8040046
Chicago/Turabian StyleMinwalla, Cyrus, Jim Plusquellic, and Eirini Eleni Tsiropoulou. 2024. "Lightweight Mutually Authenticated Key Exchange with Physical Unclonable Functions" Cryptography 8, no. 4: 46. https://doi.org/10.3390/cryptography8040046
APA StyleMinwalla, C., Plusquellic, J., & Tsiropoulou, E. E. (2024). Lightweight Mutually Authenticated Key Exchange with Physical Unclonable Functions. Cryptography, 8(4), 46. https://doi.org/10.3390/cryptography8040046








