Certificateless Searchable Encryption Scheme in Multi-User Environment
Abstract
:1. Introduction
2. Related Knowledge
2.1. Elliptic Curve
2.2. Mathematically Difficult Problems
3. Scheme Model
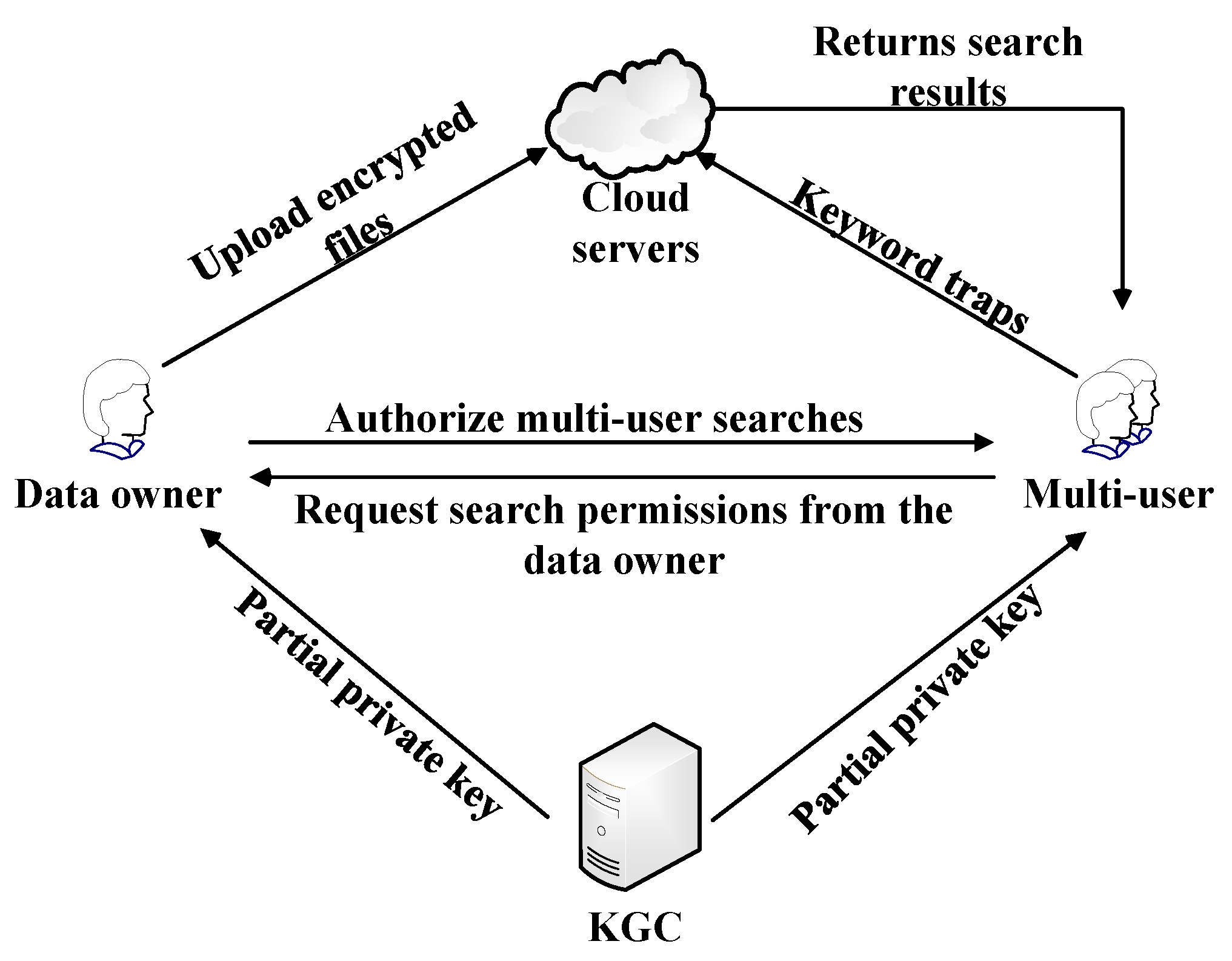
3.1. System Model
3.2. Algorithm Model
3.3. Security Model
4. Specific Construction of the Scheme
4.1. Description of the Scenario
- 1.
- Setup : given a security parameter of as input, the algorithm works as follows.
- (1)
- Generate a cyclic group G of order q on an elliptic curve .
- (2)
- P is chosen as the generating element of G.
- (3)
- Select uniformly and randomly and compute .
- (4)
- Choose three collision-resistant cryptographic hash functions , : and :. The system parameters are { and master key s = x.
- 2.
- Partial key generation: Given params, master key s and U’s identity , the algorithm stochastic selects and calculates partial public key and partial private key .
- 3.
- User key generation: Given params, user U’s identity , partial and partial private keys , the algorithm randomly selects , generates private key ), and generates public key.
- 4.
- Keyword encryption: Given params, keyword , multiple receiver identities, and receiver’s public key , the algorithm stochastic selects and calculates and uses each recipient i’s identity and public key to compute , and the multi-user keyword ciphertext .
- 5.
- Trapdoor generation: Given params, keyword w, U’s identity and his private key , the algorithm calculates keyword trapdoor .
- 6.
- Test: Given params, a keyword ciphertext and a trapdoor , the algorithm checks whether holds. If it holds, output 1; otherwise, output 0.
4.2. Proof of Correctness
4.3. Proof of Security
5. Efficiency Analysis
5.1. Computation Costs
5.2. Communication Costs
6. Summary
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Sandhu, A.K. Big Data with Cloud Computing: Discussions and Challenges. Big Data Min. Anal. 2022, 5, 32–40. [Google Scholar] [CrossRef]
- Liu, X.; Lu, T.; Yang, X. Authenticizable Keyword Search Scheme with Privacy Protection. J. Electron. Inf. Technol. 2021, 43, 8. [Google Scholar]
- Song, D.X.; Wagner, D.; Perrig, A. Practical Techniques for Searches on Encrypted Data. In Proceedings of the IEEE Symposium on Security & Privacy, Berkeley, CA, USA, 14–17 May 2000. [Google Scholar]
- Boneh, D.; Crescenzo, G.D.; Ostrovsky, R.; Persiano, G. Public Key Encryption with Keyword Search. In Proceedings of the Advances in Cryptology—EUROCRYPT 2004, Interlaken, Switzerland, 2–6 May 2004; Volume 3027. [Google Scholar]
- Baek, J.; Safiavi-Naini, R.; Susilo, W. Public Key Encryption with Keyword Search Revisited. In Proceedings of the Computational Science and Its Applications—ICCSA 2008, Perugia, Italy, 30 June–3 July 2008. [Google Scholar]
- Yong, H.H.; Lee, P.J. Public Key Encryption with Conjunctive Keyword Search and Its Extension to a Multi-user System. In Proceedings of the International Conference on Pairing-Based Cryptography, Tokyo, Japan, 2–4 July 2007. [Google Scholar]
- Byun, J.W.; Rhee, H.S.; Park, H.A.; Lee, D.H. Off-Line Keyword Guessing Attacks on Recent Keyword Search Schemes over Encrypted Data. In Workshop on Secure Data Management; Springer: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless public key cryptography. In Proceedings of the 9th International Conference on the Theory and Application of Cryptology, Taipei, Taiwan, 30 November–4 December 2003. [Google Scholar]
- Peng, Y.; Cui, J.; Peng, C.; Ying, Z. Certificateless Public Key Encryption with Keyword Search. China Commun. 2014, 11, 100–113. [Google Scholar]
- Lu, Y.; Li, J.; Zhang, Y. Privacy-Preserving and Pairing-Free Multirecipient Certificateless Encryption with Keyword Search for Cloud-Assisted IIoT. IEEE Internet Things J. 2020, 7, 2553–2562. [Google Scholar] [CrossRef]
- Wu, L.; Zhang, Y.; Ma, M.; Kumar, N.; He, D. Certificateless searchable public key authenticated encryption with designated tester for cloud-assisted medical Internet of Things. Ann. Telecommun. 2019, 74, 423–434. [Google Scholar] [CrossRef]
- Yang, X.; Chen, G.; Wang, M.; Li, T.; Wang, C. Multi-keyword Certificateless Searchable Public Key Authenticated Encryption Scheme Based on Blockchain. IEEE Access 2020, 8, 158765–158777. [Google Scholar] [CrossRef]
- Ma, M.; He, D.; Kumar, N.; Choo, K.K.R.; Chen, J. Certificateless Searchable Public Key Encryption Scheme for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 759–767. [Google Scholar] [CrossRef]
- Zhang, Y.L.; Wen, L.; Wang, H.; Wang, C.F. Searchable symmetric encryption: Improved definitions and efficient constructions. J. Comput. Secur. 2011, 19, 895–934. [Google Scholar]
- Zhang, Y.L.; Wen, L.; Wang, H.; Wang, C.F. Searchable Encryption Scheme without Certificate Authentication in Multi-User Environment. J. Electron. Inf. Technol. 2020, 42, 1094–1101. [Google Scholar]
- Ma, M.; Fan, S.; Feng, D. Multi-user certificateless public key encryption with conjunctive keyword search for cloud-based telemedicine. J. Inf. Secur. Appl. 2020, 55, 102652. [Google Scholar] [CrossRef]
- Qiu, Z.; Meng, X.; Gong, D.; Wei, P.; Huang, Y.; Zhang, P. An Improved elliptic curve group signature scheme. Appl. Math. Prog. 2021, 10, 7. [Google Scholar]
- Miller, V.S. Use of Elliptic Curves in Cryptography. In Proceedings of the Advances in Cryptology—CRYPTO ’85, Santa Barbara, CA, USA, 18–22 August 1985. [Google Scholar]
- Cui, W.; Jia, Z.; Hu, M.; Gong, B.; Wang, L. Signature scheme based on elliptic curve. Comput. Appl. Softw. 2020, 37, 6. [Google Scholar]
- Lin, H.; Gao, F.; Zhang, H.; Jin, Z.; Li, W.; Wen, Q. Public Key Encryption with Equality Test Supporting Flexible Designated Authorization in Cloud Storage. IEEE Syst. J. 2022, 16, 1460–1470. [Google Scholar] [CrossRef]

| Symbol | Interpretation |
|---|---|
| Two large prime numbers | |
| A finite field of order q | |
| An elliptic curve on the finite domain | |
| A group of elliptic curves of order q | |
| P | A generator of G |
| The field of integers modularly q | |
| Secure hash functions | |
| An adversary against CLEKS | |
| An algorithm that solves the CDH problem | |
| System parameters | |
| The master key | |
| The identity of User U | |
| Part of the private key and part of the public key of user U | |
| User U’s private and public keys | |
| The challenger’s private and public keys | |
| Pseudo-public and pseudo-private keys | |
| The identity of the challenger | |
| keywords | |
| The keyword w trap | |
| The keyword w is ciphertext |
| Notation | Description |
|---|---|
| TBP | Time cost for computing a bilinear pairing |
| Th | General hash function runtime |
| TSM | The elapsed time of a scalar multiplication operation |
| TH | The hash function maps to the elapsed time of the points above the group |
| TMM | Calculate the run time of the multiplication |
| Tpa | The elapsed time of the point addition operation on the group |
| TMH | The Hash function maps to the run time of the point |
| |G1| | The size of the element in the G1 |
| |G| | The size of the element in the elliptic curve group G |
| Scheme | Key Generation | Keyword Encryption | Trapdoor Generation | Test |
|---|---|---|---|---|
| [13] | 2TH + 4TSM = 111.276 | 3TH + Th + 4TSM + 3TBP + 3Tpa = 223.2 | TH + Tpa + TSM = 45.1 | 2TH + TSM + Th + 2Tpa + TBP = 101.4 |
| [15] | 2TH + 4TSM = 49.1384 | TH + 3TSM + Tpa = 68.9 | TH + Th + 2TSM + TBP + 2Tpa = 84.2 | 2TSM + 2Th + 4Tpa + 2TBP + TMM = 79.9 |
| Ours | 2TH + 4TSM = 49.243 | 3TSM + TMM = 14.94 | TMM = 19.32 | TSM = 22.1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Feng, T.; Si, J. Certificateless Searchable Encryption Scheme in Multi-User Environment. Cryptography 2022, 6, 61. https://doi.org/10.3390/cryptography6040061
Feng T, Si J. Certificateless Searchable Encryption Scheme in Multi-User Environment. Cryptography. 2022; 6(4):61. https://doi.org/10.3390/cryptography6040061
Chicago/Turabian StyleFeng, Tao, and Jiewen Si. 2022. "Certificateless Searchable Encryption Scheme in Multi-User Environment" Cryptography 6, no. 4: 61. https://doi.org/10.3390/cryptography6040061
APA StyleFeng, T., & Si, J. (2022). Certificateless Searchable Encryption Scheme in Multi-User Environment. Cryptography, 6(4), 61. https://doi.org/10.3390/cryptography6040061






