Fair and Secure Multi-Party Computation with Cheater Detection
Abstract
:1. Introduction
Organization
2. Related Work
- Cheater Detection. Detecting cheaters on the Internet has been an important issue, such as astroturfing detection [13,14,15], and a diversity of techniques concerning this matter have been proposed so far. Several studies have been carried out on cheater detection in secret sharing schemes [16,17,18,19]. The results of these techniques are only applicable to secret sharing schemes and thus may not be used to verify the correctness of the new shares computed by secure multi-party computation (SMC) protocol. Several SMC protocols that can detect malicious parties have been proposed so far. Damgård and Orlandi proposed an SMC protocol where every party broadcasts the computed final shares and checks its commitments following the computation of its own final shares [10]. Baum et al. proposed an SMC protocol with an additional audit algorithm [20]. Since the SPDZ protocol was proposed, several SMC protocols have been built on top of the SPDZ protocl to achieve cheater detection and identification [21,22]. Furthermore, there have been efforts to improve the efficiency of SMC protocols with identifiable abort [23]. However, neither of these protocols can prevent malicious parties from learning the final result of computation, whereas honest parties may not. In other words, malicious parties can only be detected following the broadcast of the final shares or the reconstruction of the final output. In such a case, a malicious party can broadcast an incorrect value and obtain all correct final shares of the honest parties as well as its own. The malicious party would then be the only one that can reconstruct the correct output of the computation.
- Fair and Secure Multi-party Computation. It is known that any functionality can be fairly computed in the case of honest majority [24,25,26,27]. However, fairness is impossible to be guaranteed with corrupted majority [28]. Consequently, a number of definitions of security do not consider fairness, even in a Universal Composability (UC) framework, or only consider partial fairness [29,30,31,32]. To overcome this impossibility result, a few approaches to achieve fairness have been proposed. The gradual release approach makes parties take turns releasing their outputs in each round [33,34,35]. However, this approach is still somewhat unfair. Another approach involves employing semi-trusted third parties or physical assumptions [36,37,38]. As part of this approach, a technique using Bitcoin has been proposed [39,40]. It was recently shown that fair, secure, multi-party computation can be achieved by applying a multi-party fair exchange protocol to any SMC protocol [41]. Moreover, several results have been insisted on the possibility of utilizing reputation systems [42], public bulletin boards [43], and trusted hardware [44] to achieve fairness.
- Secure Multi-party Computation in Smart Grid. A number of studies on privacy-preserving aggregation of information for metering or billing have been conducted [45,46,47,48,49,50]. SMC techniques have recently been applied to smart grids to preserve user privacy [7,8]. The protocol proposed in [7] can be applied to smart grids but requires that all participating parties decrypt the final output together in an interactive manner. In [8], Clark and Hopkinson proposed an optimized SMC protocol called transferable multi-party computation (T-MPC) for smart grid networks. To improve efficiency and scalability, T-MPC allows small groups of users to compute the local results of sub-functions. However, it is unable to detect malicious parties and guarantee fairness at the same time.
- Implementations of Secure Multi-party Computation. Implementation and compiler design of SMC is an active area of research. In the early days of research, compilers were developed that convert code written in a high-level language called secure function definition language (SFDL) into a circuit representation (e.g., FairplayMP [3], VIFF [5], SEPIA [6]). Since then, research has been underway for implementations that are more suitable for real-world applications, that is, fast enough to evaluate complex functions and large data sets. For secure two-party computation, most protocols have been designed using circuit garbling [51], such as ABY [52], EzPC [53], and ABY2.0 [54]. For true multi-party computation, a variety of compilers that execute SMC in arbitrary functions have been developed, and representative examples include PICCO [55,56] and MP-SPDZ [57].
Contributions
3. Preliminaries
3.1. Secure Multi-Party Computation
3.1.1. Addition
3.1.2. Multiplication
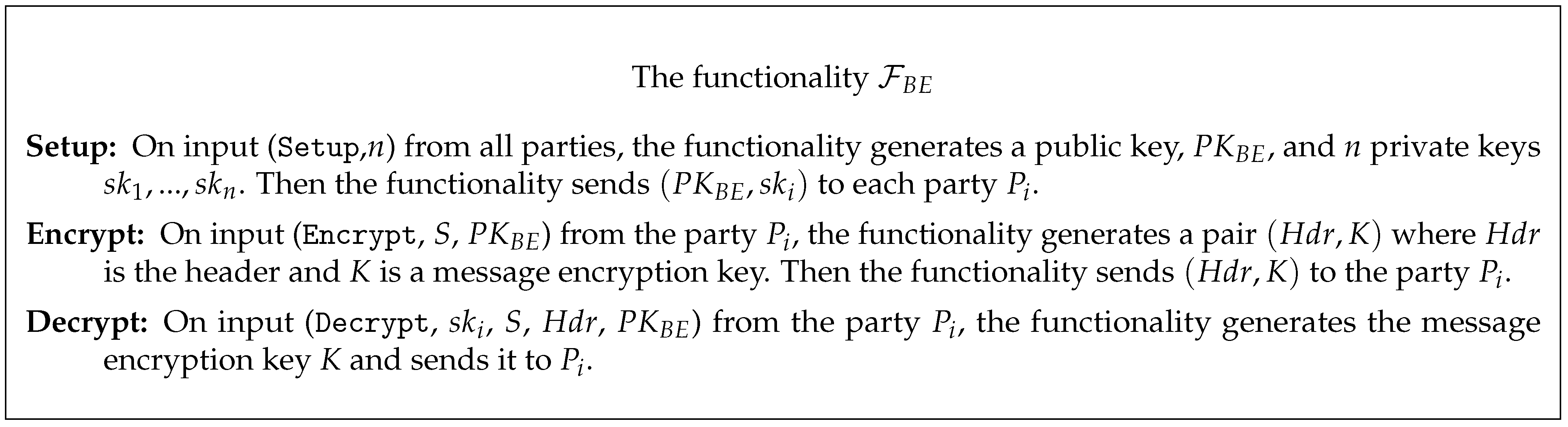
3.2. Public-Key Broadcast Encryption
- Setup (n).
- Takes as input the number of receivers n and outputs a public key as well as n private keys .
- Encrypt (S, PK).
- Takes a subset and a public key as input, and outputs a pair , where is the header and is a message encryption key. We often refer to as the broadcast ciphertext.Let M be a message to be broadcasted to set S and be the encryption of M under symmetric key K. A sender broadcasts to users in S, where the pair is often called the full header and is often called the broadcast body.
- Decrypt ().
- Takes as input private key for user i, a subset , a header , and the public key . If user i is in S, the algorithm outputs the message encryption key , which is used to decrypt broadcast body and obtain message M.
3.3. Non-Interactive Zero Knowledge
- Prove.
- Takes as input if outputs ⊥. Otherwise, it outputs , where is proof of the statement that .
- Verify.
- Takes as input and outputs 1 to accept the proof. Otherwise, it outputs 0.
3.4. Universally Composable Security
4. Definitions
4.1. Notation
4.2. UC-Secure Fair Multi-Party Computation
- If the inputs are invalid or S sends the message , sends ⊥ to all parties and halts.
- Otherwise, computes . Let be the i-th output. Then, sends to S and to the corresponding honest parties.
5. FSMC Protocol with Cheater Detection
5.1. Setup
5.2. Offline Phase
5.3. Online Phase
6. Security in the Online Phase
7. Application
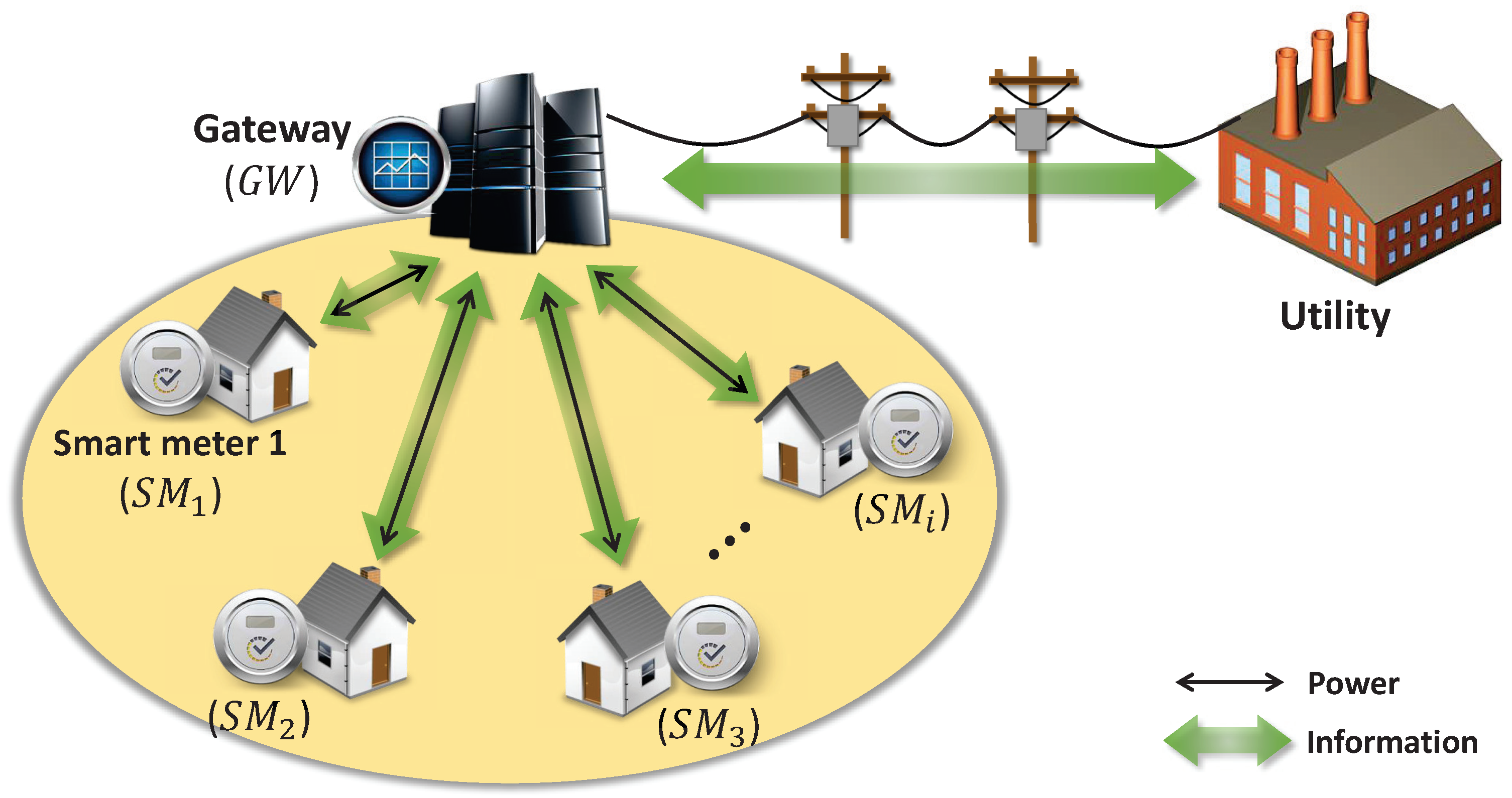
7.1. Applying FSMC Protocol to the Smart Grid
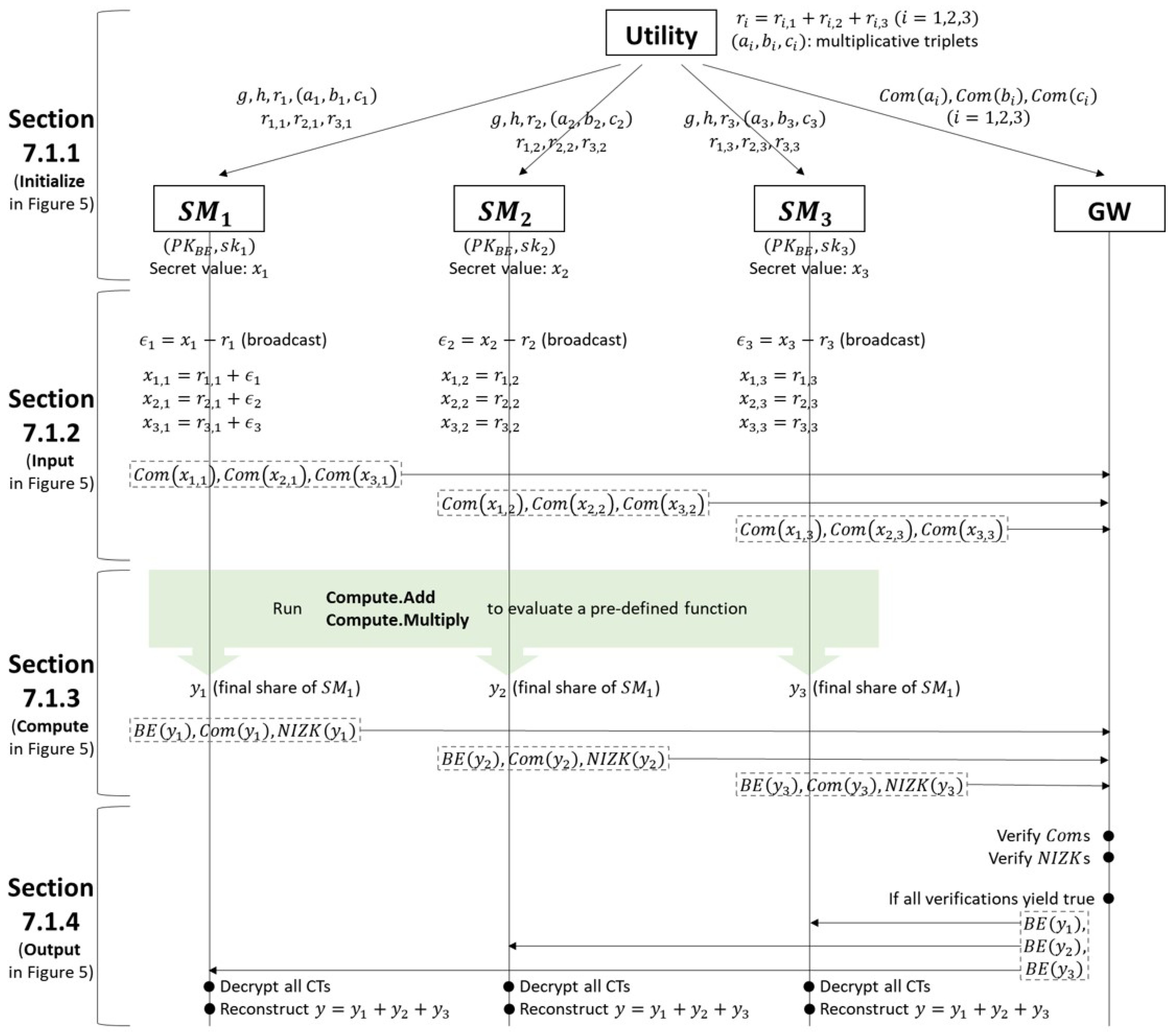
7.1.1. System Setup
- Step 1. Choose and . Set and send to every . These values are used to compute commitment.
- Step 2. Choose uniformly random and send these values to each . These values are used to share the secret input of each .
- Step 3. Choose such that , where and . Send the triple to each . These values are used as multiplication triples.
- Step 4. Create the commitments of the multiplication triples, and send them to . These are used to detect malicious in the Secure Data Retrieval phase. where r is a random value).
7.1.2. User Data Sharing
- Step 1. is privately opened as r to , where .
- Step 2. Broadcast , where is the metering data for each .
- Step 3. Compute locally, where is the share of for each .
- Step 4. Create the commitments of all shares, , and send them to . These commitments are used to detect malicious in the Secure Data Retrieval phase.
7.1.3. Privacy-Preserving Data Aggregation
- Step 1. Run Compute.Add and Compute.Multiply in to compute the final share of the output for computation.
- Step 2. Encrypt the final share using a PKBE scheme under the recipient set, including all , and the in a local area.
- Step 3. Create the commitments and the non-interactive zero-knowledge proof as in Compute.Send of . Send them to .
7.1.4. Secure Data Retrieval
- Step 1. Follow Step 1 of Output in to verify the commitments sent from each .
- Step 2. Verify the non-interactive zero-knowledge proof sent from each .
- Step 3.
- –
- If all verifications yield true, send all ciphertexts sent from each in the Privacy-preserving Data Aggregation phase to all and the in a local area.
- –
- Otherwise, notify each honest of malicious s identities.
- Step 1.
- –
- If there is no malicious , decrypt the ciphertexts from and reconstruct the output using the final shares.
- –
- Otherwise, restart the protocol from the beginning excluding malicious .
7.2. Analysis
7.2.1. Improving Efficiency (in terms of Average)
- Secure Data RetrievalIn order to detect the malicious , executes the following steps:
- –
- Step 1. Follow Step 1 of Output in to verify the commitments sent from each .
- –
- Step 2. Verify the non-interactive zero-knowledge proof sent by each .
- –
- Step 3.
- ∗
- If all verification outputs are true, send all ciphertexts sent by each in the Privacy-preserving Data Aggregation phase to all and the in a local area.
- ∗
- Otherwise, notify each honest of the identities of the malicious s.
If there is no malicious , each decrypts the ciphertexts sent by and reconstructs the average by adding all final shares. If there exists at least one malicious , each honest executes the following steps:(Let be the set of identities of the malicious .)- –
- Step 1. Compute , where is a final share of computed prior to detection and is an initial share that assigned to .
- –
- Step 2. Set the new final share , where .
- –
- Step 3. Create the commitment of its new final share, , and the non-interactive zero-knowledge proof as in Compute.Send of . Send these to .
This phase should be repeated until no malicious party exists. Once detects a malicious , each honest locally executes additional computations to generate the new final share. From the previously computed final share, each honest removes shares , which were provided by the malicious , and adds shares , provided to the malicious . Since the parts related to the malicious are removed through this process, the new final share is correct for all honest .
7.2.2. Efficiency Analysis
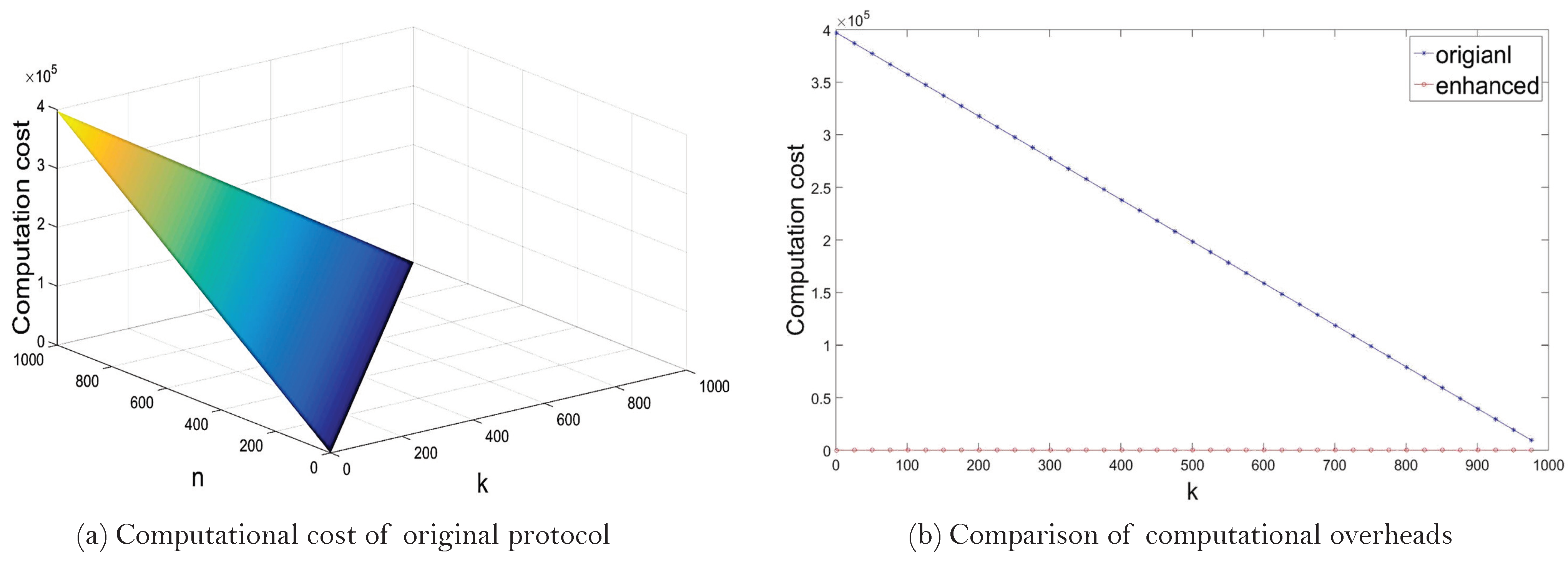
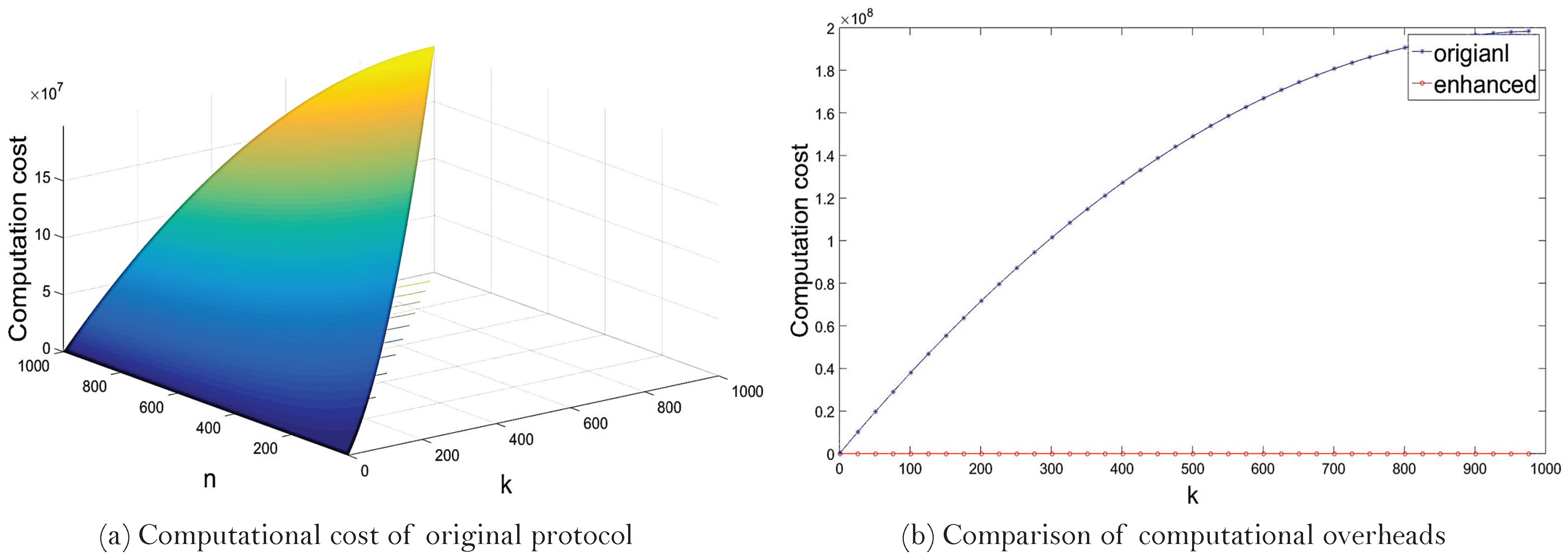
- One detection: k malicious usersIn this case, we compare the computational overhead of two protocols when detection occurs only once and k malicious are detected. The number of generating commitments and computing addition operations are listed in Table 1, where n is the number of smart meters. According to the experimental results, a single addition operation in and a single commitment generation cost 0.0004 ms and 397.3102 ms , respectively. Since the User Data Sharing phase is not required during re-computation in the enhanced version of the protocol, only the Privacy-preserving Data Aggregation phase influences the computational cost of the enhanced version.The computational cost of original protocol depends on both k and n. We show the variation in computational overhead in terms of both k and n in Figure 10a. Given that n is fixed, the greater the value of k, the smaller the computational cost of the protocol. On the contrary, computational cost of the enhanced version of the protocol depends only on k. We thus depict the difference in computational overhead between two protocols in terms of k in Figure 10b, given that n = 1000. From the figure, we see that the enhanced version is more efficient until k becomes approximately 999.99. This means that the enhanced version of the protocol is more efficient than the original one, excluding the case where all smart meters are detected as malicious.
- One malicious user: k detectionIn this case, we compare the computation overhead of two protocols when detection occurs k times and one malicious is detected at a time. The number of generating commitments and computing addition operations is listed in Table 2, where n is the number of smart meters. (As above, = 0.0004 ms and = 397.3102 ms.)We show the variation in computational costs of the original protocol in terms of both k and n in Figure 11a, where detection occurs k times and only one malicious is detected at a time. Given that n is fixed, the greater the value of k, the greater the computational cost of the protocol. On the contrary, computational cost of the enhanced version of the protocol depends only on k. We thus depict the difference in computational overhead between two protocols in terms of k in Figure 11b, given that n = 1000. From the figure, we see that the enhanced version of the protocol is more efficient than the original one in all cases.
8. Conclusions and Future Research Directions
Author Contributions
Funding
Conflicts of Interest
References
- Naor, M.; Pinkas, B.; Sumner, R. Privacy Preserving Auctions and Mechanism Design. In Proceedings of the 1st ACM Conference on Electronic Commerce, Denver, CO, USA, 3–5 November 1999; EC’99. pp. 129–139. [Google Scholar]
- Bogetoft, P.; Christensen, D.; Damgård, I.; Geisler, M.; Jakobsen, T.; Krøigaard, M.; Nielsen, J.; Nielsen, J.; Nielsen, K.; Pagter, J.; et al. Secure Multiparty Computation Goes Live. In Financial Cryptography and Data Security; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5628, pp. 325–343. [Google Scholar]
- Ben-David, A.; Nisan, N.; Pinkas, B. FairplayMP: A system for secure multi-party computation. In Proceedings of the 15th ACM Conference on Computer and Communications Security, New York, NY, USA, 27–31 October 2008; pp. 257–266. [Google Scholar]
- Bogdanov, D.; Laur, S.; Willemson, J. Sharemind: A framework for fast privacy-preserving computations. In European Symposium on Research in Computer Security; Springer: Berlin/Heidelberg, Germany, 2008; pp. 192–206. [Google Scholar]
- Damgård, I.; Geisler, M.; Krøigaard, M.; Nielsen, J.B. Asynchronous multiparty computation: Theory and implementation. In International Workshop on Public Key Cryptography; Springer: Berlin/Heidelberg, Germany, 2009; pp. 160–179. [Google Scholar]
- Burkhart, M.; Strasser, M.; Many, D.; Dimitropoulos, X. SEPIA: Privacy-preserving aggregation of multi-domain network events and statistics. Network 2010, 1, 15–32. [Google Scholar]
- Peter, A.; Tews, E.; Katzenbeisser, S. Efficiently Outsourcing Multiparty Computation Under Multiple Keys. IEEE Trans. Inf. Forensics Secur. 2013, 8, 2046–2058. [Google Scholar] [CrossRef] [Green Version]
- Clark, M.; Hopkinson, K. Transferable Multiparty Computation With Applications to the Smart Grid. IEEE Trans. Inf. Forensics Secur. 2014, 9, 1356–1366. [Google Scholar] [CrossRef]
- Kerschbaum, F. Adapting Privacy-Preserving Computation to the Service Provider Model. In Proceedings of the CSE’09, International Conference on Computational Science and Engineering, Vancouver, BC, Canada, 29–31 August 2009; Volume 3, pp. 34–41. [Google Scholar]
- Damgård, I.; Orlandi, C. Multiparty Computation for Dishonest Majority: From Passive to Active Security at Low Cost. In Advances in Cryptology-CRYPTO 2010; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6223, pp. 558–576. [Google Scholar]
- Hirt, M.; Tschudi, D. Efficient General-Adversary Multi-Party Computation. In Advances in Cryptology-ASIACRYPT 2013; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2013; Volume 8270, pp. 181–200. [Google Scholar]
- Damgård, I.; Pastro, V.; Smart, N.; Zakarias, S. Multiparty Computation from Somewhat Homomorphic Encryption. In Advances in Cryptology-CRYPTO 2012; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7417, pp. 643–662. [Google Scholar]
- Peng, J.; Choo, R.K.K.; Ashman, H. Astroturfing detection in social media: Using binary n-gram analysis for authorship attribution. In Proceedings of the 2016 IEEE Trustcom/BigDataSE/ISPA, Tianjin, China, 23–26 August 2016; pp. 121–128. [Google Scholar]
- Mahbub, S.; Pardede, E.; Kayes, A.; Rahayu, W. Controlling astroturfing on the internet: A survey on detection techniques and research challenges. Int. J. Web Grid Serv. 2019, 15, 139–158. [Google Scholar] [CrossRef]
- Mahbub, S.; Pardede, E.; Kayes, A. Detection of Harassment Type of Cyberbullying: A Dictionary of Approach Words and Its Impact. Secur. Commun. Netw. 2021, 2021. [Google Scholar] [CrossRef]
- Cabello, S.; Padro, C.; Saez, G. Secret Sharing Schemes with Detection of Cheaters for a General Access Structure. Des. Codes Cryptogr. 2002, 25, 175–188. [Google Scholar] [CrossRef]
- Araki, T. Efficient (k,n) Threshold Secret Sharing Schemes Secure Against Cheating from n–1 Cheaters. In Information Security and Privacy; Lecture Notes in Computer Science; Pieprzyk, J., Ghodosi, H., Dawson, E., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4586, pp. 133–142. [Google Scholar]
- Harn, L.; Lin, C. Detection and identification of cheaters in (t, n) secret sharing scheme. Des. Codes Cryptogr. 2009, 52, 15–24. [Google Scholar] [CrossRef]
- Obana, S. Almost Optimum t-Cheater Identifiable Secret Sharing Schemes. In Advances in Cryptology-EUROCRYPT 2011; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6632, pp. 284–302. [Google Scholar]
- Baum, C.; Damgård, I.; Orlandi, C. Publicly Auditable Secure Multi-Party Computation. In Security and Cryptography for Networks; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2014; Volume 8642, pp. 175–196. [Google Scholar]
- Spini, G.; Fehr, S. Cheater detection in SPDZ multiparty computation. In International Conference on Information Theoretic Security; Springer: Berlin/Heidelberg, Germany, 2016; pp. 151–176. [Google Scholar]
- Cunningham, R.; Fuller, B.; Yakoubov, S. Catching MPC cheaters: Identification and openability. In International Conference on Information Theoretic Security; Springer: Berlin/Heidelberg, Germany, 2017; pp. 110–134. [Google Scholar]
- Baum, C.; Orsini, E.; Scholl, P.; Soria-Vazquez, E. Efficient constant-round MPC with identifiable abort and public verifiability. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2020; pp. 562–592. [Google Scholar]
- Goldreich, O.; Micali, S.; Wigderson, A. How to Play ANY Mental Game. In Proceedings of the Nineteenth Annual ACM Symposium on Theory of Computing, New York, NY, USA, 25–27 May 1987; STOC’87. pp. 218–229. [Google Scholar]
- Ben-Or, M.; Goldwasser, S.; Wigderson, A. Completeness Theorems for Non-cryptographic Fault-tolerant Distributed Computation. In Proceedings of the Twentieth Annual ACM Symposium on Theory of Computing, Chicago, IL, USA, 2–4 May 1988; STOC’88. pp. 1–10. [Google Scholar]
- Chaum, D.; Crépeau, C.; Damgard, I. Multiparty Unconditionally Secure Protocols. In Proceedings of the Twentieth Annual ACM Symposium on Theory of Computing, Chicago, IL, USA, 2–4 May 1988; STOC’88. pp. 11–19. [Google Scholar]
- Rabin, T.; Ben-Or, M. Verifiable Secret Sharing and Multiparty Protocols with Honest Majority. In Proceedings of the Twenty-First Annual ACM Symposium on Theory of Computing, Seattle, WA, USA, 14–17 May 1989; STOC’89. pp. 73–85. [Google Scholar]
- Cleve, R. Limits on the Security of Coin Flips when Half the Processors Are Faulty. In Proceedings of the Eighteenth Annual ACM Symposium on Theory of Computing, Berkeley, CA, USA, 28–30 May 1986; STOC’86. pp. 364–369. [Google Scholar]
- Beaver, D.; Goldwasser, S. Multiparty Computation with Faulty Majority. In Advances in Cryptology-CRYPTO 1989; Lecture Notes in Computer Science; Springer: New York, NY, USA, 1990; Volume 435, pp. 589–590. [Google Scholar]
- Goldwasser, S.; Levin, L. Fair Computation of General Functions in Presence of Immoral Majority. In Advances in Cryptology-CRYPTO 1990; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1991; Volume 537, pp. 77–93. [Google Scholar]
- Fitzi, M.; Gottesman, D.; Hirt, M.; Holenstein, T.; Smith, A. Detectable Byzantine Agreement Secure Against Faulty Majorities. In Proceedings of the Twenty-First Annual Symposium on Principles of Distributed Computing, Monterey, CA, USA, 21–24 July 2002; PODC’02. pp. 118–126. [Google Scholar]
- Goldwasser, S.; Lindell, Y. Secure Computation without Agreement. In Distributed Computing; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2002; Volume 2508, pp. 17–32. [Google Scholar]
- Even, S.; Goldreich, O.; Lempel, A. A Randomized Protocol for Signing Contracts. Commun. ACM 1985, 28, 637–647. [Google Scholar] [CrossRef]
- Boneh, D.; Naor, M. Timed Commitments. In Advances in Cryptology-CRYPTO 2000; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2000; Volume 1880, pp. 236–254. [Google Scholar]
- Garay, J.; MacKenzie, P.; Prabhakaran, M.; Yang, K. Resource Fairness and Composability of Cryptographic Protocols. In Theory of Cryptography; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2006; Volume 3876, pp. 404–428. [Google Scholar]
- Asokan, N.; Shoup, V.; Waidner, M. Optimistic fair exchange of digital signatures. In Advances in Cryptology-EUROCRYPT’98; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1998; Volume 1403, pp. 591–606. [Google Scholar]
- Cachin, C.; Camenisch, J. Optimistic Fair Secure Computation. In Advances in Cryptology-CRYPTO 2000; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2000; Volume 1880, pp. 93–111. [Google Scholar]
- Lepinski, M.; Micali, S.; Peikert, C.; Shelat, A. Completely Fair SFE and Coalition-safe Cheap Talk. In Proceedings of the Twenty-third Annual ACM Symposium on Principles of Distributed Computing, St. John’s, NL, Canada, 25–28 July 2004; PODC’04. pp. 1–10. [Google Scholar]
- Andrychowicz, M.; Dziembowski, S.; Malinowski, D.; Mazurek, L. Secure Multiparty Computations on Bitcoin. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 18–21 May 2014; SP ’14. pp. 443–458. [Google Scholar]
- Bentov, I.; Kumaresan, R. How to Use Bitcoin to Design Fair Protocols. In Advances in Cryptology-CRYPTO 2014; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8617, pp. 421–439. [Google Scholar]
- Kılınç, H.; Küpçü, A. Optimally Efficient Multi-Party Fair Exchange and Fair Secure Multi-Party Computation. In Topics in Cryptology-CT-RSA 2015; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2015; Volume 9048, pp. 330–349. [Google Scholar]
- Asharov, G.; Lindell, Y.; Zarosim, H. Fair and Efficient Secure Multiparty Computation with Reputation Systems. In Advances in Cryptology-ASIACRYPT 2013; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2013; Volume 8270, pp. 201–220. [Google Scholar]
- Choudhuri, A.R.; Green, M.; Jain, A.; Kaptchuk, G.; Miers, I. Fairness in an unfair world: Fair multiparty computation from public bulletin boards. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 719–728. [Google Scholar]
- Paul, S.; Shrivastava, A. Efficient fair multiparty protocols using Blockchain and trusted hardware. In International Conference on Cryptology and Information Security in Latin America; Springer: Berlin/Heidelberg, Germany, 2019; pp. 301–320. [Google Scholar]
- Li, F.; Luo, B.; Liu, P. Secure Information Aggregation for Smart Grids Using Homomorphic Encryption. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications (SmartGridComm), Gaithersburg, MD, USA, 4–6 October 2010; pp. 327–332. [Google Scholar]
- Kursawe, K.; Danezis, G.; Kohlweiss, M. Privacy-Friendly Aggregation for the Smart-Grid. In Privacy Enhancing Technologies; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6794, pp. 175–191. [Google Scholar]
- Lu, R.; Liang, X.; Li, X.; Lin, X.; Shen, X. EPPA: An Efficient and Privacy-Preserving Aggregation Scheme for Secure Smart Grid Communications. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1621–1631. [Google Scholar]
- Yang, L.; Xue, H.; Li, F. Privacy-preserving data sharing in Smart Grid systems. In Proceedings of the 2014 IEEE International Conference on Smart Grid Communications (SmartGridComm), Venice, Italy, 3–6 November 2014; pp. 878–883. [Google Scholar]
- Mustafa, M.A.; Cleemput, S.; Aly, A.; Abidin, A. An MPC-based protocol for secure and privacy-preserving smart metering. In Proceedings of the 2017 IEEE PES Innovative Smart Grid Technologies Conference Europe (ISGT-Europe), Turin, Italy, 26–29 September 2017; pp. 1–6. [Google Scholar]
- Mustafa, M.A.; Cleemput, S.; Aly, A.; Abidin, A. A secure and privacy-preserving protocol for smart metering operational data collection. IEEE Trans. Smart Grid 2019, 10, 6481–6490. [Google Scholar] [CrossRef] [Green Version]
- Yao, A.C.C. How to generate and exchange secrets. In Proceedings of the 27th Annual Symposium on Foundations of Computer Science (sfcs 1986), Toronto, ON, Canada, 27–29 October 1986; pp. 162–167. [Google Scholar]
- Demmler, D.; Schneider, T.; Zohner, M. ABY-A Framework for Efficient Mixed-Protocol Secure Two-Party Computation; NDSS: San Diego, CA, USA, 11 February 2015. [Google Scholar]
- Chandran, N.; Gupta, D.; Rastogi, A.; Sharma, R.; Tripathi, S. EzPC: Programmable and efficient secure two-party computation for machine learning. In Proceedings of the 2019 IEEE European Symposium on Security and Privacy (EuroS&P), Stockholm, Sweden, 17–19 June 2019; pp. 496–511. [Google Scholar]
- Patra, A.; Schneider, T.; Suresh, A.; Yalame, H. ABY2. 0: Improved mixed-protocol secure two-party computation. In Proceedings of the 30th {USENIX} Security Symposium ({USENIX} Security 21), Virtual Event, 11–13 August 2021. [Google Scholar]
- Zhang, Y.; Steele, A.; Blanton, M. PICCO: A general-purpose compiler for private distributed computation. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 813–826. [Google Scholar]
- Zhang, Y.; Blanton, M.; Almashaqbeh, G. Implementing support for pointers to private data in a general-purpose secure multi-party compiler. ACM Trans. Priv. Secur. (TOPS) 2017, 21, 1–34. [Google Scholar] [CrossRef]
- Keller, M. MP-SPDZ: A versatile framework for multi-party computation. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Virtual Event, 9–13 November 2020; pp. 1575–1590. [Google Scholar]
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Goldreich, O.; Micali, S.; Wigderson, A. How to play any mental game, or a completeness theorem for protocols with honest majority. In Providing Sound Foundations for Cryptography: On the Work of Shafi Goldwasser and Silvio Micali; Association for Computing Machinery: New York, NY, USA, 2019; pp. 307–328. [Google Scholar]
- Beaver, D. Efficient multiparty protocols using circuit randomization. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1991; pp. 420–432. [Google Scholar]
- Naor, D.; Naor, M.; Lotspiech, J. Revocation and tracing schemes for stateless receivers. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2001; pp. 41–62. [Google Scholar]
- Dodis, Y.; Fazio, N. Public key broadcast encryption for stateless receivers. In ACM Workshop on Digital Rights Management; Springer: Berlin/Heidelberg, Germany, 2002; pp. 61–80. [Google Scholar]
- Groth, J.; Ostrovsky, R.; Sahai, A. Perfect Non-interactive Zero Knowledge for NP. In Advances in Cryptology-EUROCRYPT 2006; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2006; Volume 4004, pp. 339–358. [Google Scholar]
- Canetti, R. Universally composable security: A new paradigm for cryptographic protocols. In Proceedings of the 42nd IEEE Symposium on Foundations of Computer Science, Washington, DC, USA, 14–17 October 2001; pp. 136–145. [Google Scholar]
- Pedersen, T. Non-Interactive and Information-Theoretic Secure Verifiable Secret Sharing. In Advances in Cryptology-CRYPTO 1991; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1992; Volume 576, pp. 129–140. [Google Scholar]
- pbc Library. 2012. Available online: https://crypto.stanford.edu/pbc/ (accessed on 15 March 2021).
- gmp Library. 2014. Available online: https://gmplib.org (accessed on 15 March 2021).






| Original Protocol | Enhanced Version | |
|---|---|---|
| Input | - | |
| (commitment) | ||
| Compute | ||
| (addition) |
| Original Protocol | Enhanced Version | |
|---|---|---|
| Input | - | |
| (commitment) | ||
| Compute | ||
| (addition) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Seo, M. Fair and Secure Multi-Party Computation with Cheater Detection. Cryptography 2021, 5, 19. https://doi.org/10.3390/cryptography5030019
Seo M. Fair and Secure Multi-Party Computation with Cheater Detection. Cryptography. 2021; 5(3):19. https://doi.org/10.3390/cryptography5030019
Chicago/Turabian StyleSeo, Minhye. 2021. "Fair and Secure Multi-Party Computation with Cheater Detection" Cryptography 5, no. 3: 19. https://doi.org/10.3390/cryptography5030019
APA StyleSeo, M. (2021). Fair and Secure Multi-Party Computation with Cheater Detection. Cryptography, 5(3), 19. https://doi.org/10.3390/cryptography5030019





