Abstract
The Diffie–Hellman protocol, ingenious in its simplicity, is still the major solution in protocols for generating a shared secret in cryptography for e-trading and many other applications after an impressive number of decades. However, lately, the threat from a future quantum computer has prompted successors resilient to quantum computer-based attacks. Here, an algorithm similar to Diffie–Hellman is presented. In contrast to the classic Diffie–Hellman, it involves floating point numbers of arbitrary size in the generation of a shared secret. This can, in turn, be used for encrypted communication based on symmetric cyphers. The validity of the algorithm is verified by proving that a vital part of the algorithm satisfies a one-way property. The decimal part is deployed for the one-way function in a way that makes the protocol a post-quantum key generation procedure. This is concluded from the fact that there is, as of yet, no quantum computer algorithm reverse engineering the one-way function. An example illustrating the use of the protocol in combination with XOR encryption is given.
1. Introduction
More than 40 years ago, Whitfield Diffie and Martin Hellman introduced their paradigm-shifting protocol for encryption key generation [1]. By deployment of public parameters, their suggestion provides a means to secure privacy without the need for transmission of secret parameters. The security depends on the difficulty of solving the Diffie Hellman Problem, i.e., given integers q (the order of a group), g (a generator of that group), (and possibly ), guess the value of . This problem has been proven to be equivalent to the Discrete logarithm Problem, i.e., given integers q, g and , guess the smallest positive integer value a. The Diffie–Hellman protocol was improved by adding authentication (to deal with threats such as the Man-in-the-middle-attack) and refined into descendants, e.g., the Needham–Shroeder and MQV protocols. The development of the Diffie–Hellman protocol by [2] provide a means for including three parties in the session key generation. The concept with a public key protocol for the generation of a shared secret was revolutionary and the achievement is well documented in the literature in the field (see e.g., [3]).
Nevertheless, since 1997, there has been the threat against the Diffie–Hellman protocol from a future more capable version of a quantum computer utilizing Shor’s algorithm for determining the discrete logarithm [4]. Therefore, the desire to develop encryption key algorithms which are resilient to this future threat has been pronounced.
Related Literature
The threat from the quantum computer threat has raised the demands for security assurance of algorithms in that they do not depend on the integer factoring problem or the discrete logarithm problem. One such new candidate for a different core mechanism is the shortest vector problem, in turn, related to the closest vector problem. These are the core guarantees for the security of the lattice-based alternatives among which the NTRU systems (see [5] for an introduction to NTRUEncrypt, [6] for the signature NTRU-SIGN and [7] about the key exchange algorithm NTRU-KE) have gained a leading position. Several properties of security and speed have been thoroughly investigated for this branch of the lattice procedures and the NTRU encryption algorithm is one of the foremost candidates in the NIST competition for the next-level post-quantum public-key encryption method. Still, according to [8], there is a need for improvements of NTRU-KE to make it resilient against man-in-the-middle attacks. Several NTRU descendants for key exchange based on the MaTRU cryptosystem, one of which was introduced by [9] and two other by [10] to mention a few. These protocols satisfy the perfect forward secrecy property and parameters are relatively smaller than the corresponding ones for the NTRU-KE. The other great branch of post-quantum technology is the code-based one. However, few key exchange algorithms have been developed from these systems. A third branch is supersingular isogeny techniques and here, [11] made a quantum computer-resilient Diffie–Hellman variant for ARM processors. Moreover, in [12], two variants of Diffie–Hellman are presented in which a quantum computer was used to synchronize clocks to initiate the process.
Here, a quantum computer-resilient encryption key agreement protocol is considered. It may be defined as indicated by Algorithm 1 in Section 2 below. To verify the validity of the protocol, the key generated by the sender and the key generated by the receiver must coincide. Other aspects such as computation complexity, quantum computer resilience, suggestions about what numbers, public and secret, that contribute to the security are dealt with in Section 3, and possible attacks and countermeasures to prevent them considered in Section 4. Finally an example is given as an illustration in Section 5 and conclusions are summarized in Section 6. Proof is presented in the Appendix A.
2. The Suggested Protocol
An initial transcendental parameter, , is common to both Alice and Bob. The security benefits from distributing x via a secure channel, but this is not necessary. This could be done in the spirit of [12], using a quantum particle state teleported from Alice to Bob or from a TTP to both. This number can, despite being transcendental, have a finite description (such as e or or something). Thereafter, Alice calculates with some specified finite number of digits of accuracy. This she sends to Bob via an open insecure channel using her secret a. Bob uses his secret b to determine , which he sends to Alice. Finally, Alice calculates which coincides with Bob’s according to Theorem A1 in the Appendix A.
The suggested protocol for the generation of a common secret key is summarized in Algorithm 1. The function is typically a pseudo random number generator (where s is the seed). is the set of the integers . For a definition of the operation , see Definition A2 in the Appendix A. Thus, the shared secret, k, is established. The shared secret can subsequently be used for encrypted communication over an insecure channel via symmetric cyphers, such as XOR [13] or AES [14].
| Algorithm 1: The suggested key agreement protocol. |
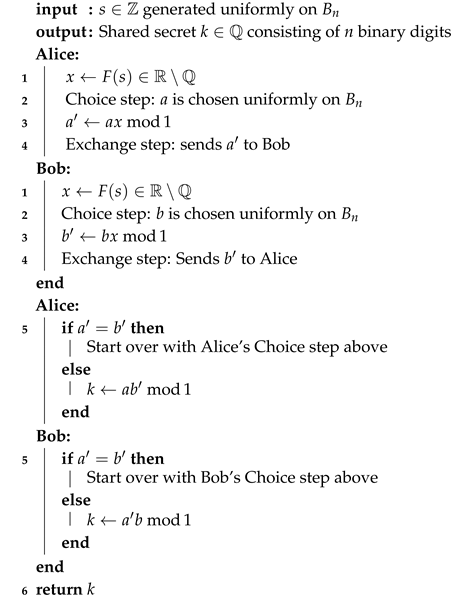 |
Core Function
The protocol depends fundamentally on a core function, , which should possess both a one-way property and a symmetry property. The parameter x belongs to a parameter space, S. Here, .
The former property, the one-way property, means that given a, it should be simple to calculate for any , while for any and given c, it should be difficult to calculate a such that . This very problem, given x and c, both in , the problem of guessing such that is henceforth referred to as the Modulo 1 Factoring Problem, M1FP as defined in Definition A3 in the Appendix A. Assuming that binary arithmetics is used, the maximum number of steps of are achieved in polynomial time (Theorem A2) while solving M1FP is -hard (Theorem A3).
The latter property is the symmetry property that
for all in the parameter space and feasible values . This has to be satisfied for establishment of a key agreement protocol. In this case, that function is the map defined by . The symmetry property of is given by Theorem A1 stated and proven in the Appendix A.
3. Security Aspects
All aspects of robustness and security of a new means for encrypted communication need to be listed and scrutinized step by step. Regarding the proposed protocol, two points of scepticism that may come to mind are
- If the transcendental x is distributed via a secure channel, why not use this number directly as the encryption key?
- In computers, numbers are always finite—transcendental numbers with infinite extent are not possible, but rather floating point numbers with a finite extent are used as an approximation of the exact numbers. In what way does this use of finite floating point non-integers differ from the methods based on large integers?
As for point 1, using the transcendental x as the encryption key would, of course, be a possibility. A problem though is one of robustness; if the secrecy of this number was to be compromised, the encryption would be completely broken if this was the actual key. However, with this protocol, the rest of the procedure would then serve as an additional layer of security. Nevertheless, these treatments also add to the cryptanalytic computation complexity but two extra multiplications and an exchange of numbers are the prices to pay for this enhancement of security.
Regarding point 2, by specifying a transcendental number, there is no indication about how many decimals will be used for the finite key. Using software packages (like the Gnu Multiprecision Library, GMP, see [15]) arbitrarily makes many digits of the floating point approximations of the transcendental numbers possible. However, the length of the numbers and sent from Alice to Bob and vice versa via insecure channels, of course, reveal something about how many digits of accuracy are used in the floating point approximations. Moreover, for the final result (the secret shared between Alice and Bob) consisting of n digits, which are identical for both parties, the number of digits in both and needs to be at least . Then again, the security benefits by having the number of digits in and much larger than that.
3.1. One or Two Layers of Security
If both the initial number s and the parameters a and b are secret, this provides two layers of security. This version of the algorithm is referred to as Version 1. The use of such a protocol between parties unknown to each other would, of course, be awkward due to the necessity of having to secretly agree on the initial number. Nevertheless, for planned communication between parties prepared in advance, secret initial numbers can be distributed in advance and used later according to some scheme to gain an extra level of security when this is appropriate.
Alternatively, a one-layer security protocol may be implemented by letting the initial number be public. This version of the algorithm is referred to as Version 2. Then, all the security depends on M1FP and the secrecy of a and b. Still, if transcendental x is calculated with very many decimals, then there is an additional element of difficulty for the cryptanalyst provided by not knowing how many digits of accuracy in the transcendental are needed for the actual encryption key. The advantage of a public initial parameter is wanted in the case of initial contact for business communications by insecure channels [1]. In this situation, it is desired for the system for encrypted communication not to require parameters distributed by a secure channel. A protocol that allows the use of a public initial integer s is imperative to the establishment of successful communication and business deals between parties previously unknown to each other.
3.2. Comments about the Initial Transcendental Number
In the implementation of the suggested protocol, it is desired for the number to be entirely different for similar to improve the unpredictability of the numbers involved. This means that if there is another such that but , this should not imply that . More precisely, this property of discontinuity may be defined as
If a pseudo random number generator is used to this end, this discontinuity property should be satisfied to make the procedure less vulnerable.
3.3. Choices of the Secret Integers
As opposed to cryptography based on the integer factorization problem, discrete logarithm problem or elliptic curve versions of these problems, the integer parameters of the suggested protocol need not be prime numbers or satisfy any inter-relational conditions other than that secrets a and b must not be identical to each other.
4. Attacks and Countermeasures
Depending on whether the initial seed s is secret or not, a Naïve attack against the suggested protocol may be launched as indicated by Algorithm 2 below. It is done under the assumption that the function F, rendering the transcendental x from the seed s, is known to the attacker.
The case in which s is secret is referred to as Version 1 and the one when s is public is called Version 2. Having intercepted and , Eve guesses at whether this is a secret. Having made her guess of s, she guesses at and . Then, she calculates comparing to and comparing this value to . Once agreement ( or ) is established, the shared secret is revealed. Based upon the number of digits in and , she can infer how many digits N of accuracy the floating point x can be. The defense against this attack is the computation complexity, see Theorem A3 in the Appendix A.
| Algorithm 2: Schematic description of the Naïve attack. |
 |
If the input is public, Eve only needs to guess at and which obviously reduces the computation complexity. This corresponds to omitting the outer for-loop in the naïve attack Algorithm 2 above.
The most well known threat to the Diffie–Hellman protocol is the man-in-the-middle attack. This may, of course, also be carried out for the suggested protocol. Therefore, modifications corresponding to MQV and Needham–Schroeder protocols resilient to this attack through authentication procedures may be developed to block this opportunity for an eavesdropper.
4.1. Resilience against Quantum Computer
The core function of the suggested key agreement protocol involves arithmetic properties other than those of integer factorization and discrete logarithm. Thus, a capable future quantum computer so far does not impose a threat to the suggested algorithm.
4.2. Computation Complexity
According to Theorem A2 below, the computation complexity of the proposed algorithm is polynomial, while according to Theorem A3, the cryptanalysis by means of the naïve attack is -hard. These figures are on par with the computation efficiency of the Diffie–Hellman method [1].
5. An Example
Assume that Alice wants to send the message "I am Alice" to Bob. To facilitate the reading, the number base 10 is used in this example but for practical use, everything, of course, translates to binary numbers or any other base desired. She transforms the message “I am Alice” to a plaintext sequence of three-digit ASCII numbers . Then, for the key generation, Alice reads the number publically announced or secretly shared by them, uniformly picked on (where n could be 1000 for a decent level of security with today’s capacity) where corresponds for decimal numbers to for binary numbers. This is a seed to be fed to a PRNG, which returns a real number, x, on . Here, with, say, and the seed (for this simple example), Alice gets
She then chooses her secret a uniformly on (where n could be 1000 for decent security). Here, with , she chooses, say, and calculates
of which the first 61 decimals she sends to Bob for a 30-digit accuracy in the final k. Bob, on his end, chooses his secret and calculates
of which the first 61 digits he sends to Alice. Then, after having checked that and differ, the final step of the key generation is realized. Alice generates the shared secret by
as does Bob by
As for the encryption, Alice encrypts her plaintext
e.g., by means of the XOR algorithm with the first 30 decimal digits of k, rendering the cryptotext
(using the decimal sequence of k as an integer and ⊕ as bitwise addition modulo 10), which she sends to Bob. Bob decrypts with the shared secret k consisting of his first 30 decimal digits simply by
(with ⊖ as bitwise subtraction modulo 10) which is readily transformed back to “I am Alice” by ASCII decoding.
6. Conclusions
Apart from being resilient to quantum computers, the great achievement of the suggested protocol as opposed to the Diffie–Hellman finite fields methodology is the use of the decimal part of a transcendental number rather than large finite integers. The use of transcendental numbers does not, by nature, restrict the number of digits in the calculation as do integers. In the case with finite fields, the secret numbers are limited by the order of the finite field q. For brute force guessing, one only has to systematically try all numbers less than q. With the proposed method, there is another bound indicated by the number of digits in the transmitted numbers and . However, the cryptanalysis made possible by Shor’s and Grover’s algorithm does not seem to be a threat to this procedure.
Moreover, compared to the Diffie–Hellman method for the generation of a shared secret, the benefits of the suggested protocol are that it requires the transfer of fewer numbers initially and that the key size is unknown. This could, however, possibly be improved by the use of implementation of the algorithm in quantum computers because of their different treatments of transcendental numbers (see [16]). This remains an urgent path for pursuit in future research.
Funding
This research was funded by the Knowledge Foundation of Sweden and Halmstad University, grant number F2019/151. The APC was funded by Halmstad University.
Acknowledgments
The reviewers of the earlier stages of this manuscript are greatly acknowledged for their constructive criticism.
Conflicts of Interest
The author declares no conflict of interest.
Appendix A
In order to define a protocol which deploys transcendental numbers and group arithmetics of mod 1, let us start by defining the integer part of a real number.
Definition A1.
Theinteger partof is
Trivially, whenever . For the integer part of a real number, some arithmetical laws hold.
Lemma A1.
For all and , .
Proof.
According to Definition A1
since as . □
Definition A2.
Thedecimal partof a real number x, , is
For a symmetric encryption key agreement protocol, a one-way function with the symmetry property for all feasible values may be used. To this end, the decimal part as the map turns out to possess precisely that property.
Theorem A1.
For any real number x and integers
Proof.
Given any real number x and integers we have, according to Lemma A1,
Changing the places of a and b above yields which equals to the left side due to the commutativity of the real numbers. □
Next, the encryption is proven to be carried out in polynomial time.
Theorem A2.
Algorithm 1 is in .
Proof.
The calculation generating the transcendental from the seed s is not considered as a part of the algorithm since it can be done in advance. When using x with N bits of accuracy (as a floating point number ) in the algorithm, the calculation of the first step may be done in steps. The same goes for the calculation of . Finally, the generation of the key k is performed by the calculation of and , respectively, thus adding to the steps of the calculation. In total, this means that the calculation of Algorithm 1 is made in polynomial time. □
To make statements about the cryptanalysis complexity, the core problem, M1FP, is formally defined.
Definition A3.
The problem: given x and c, both in , the problem of guessing such that is henceforth referred to as the Modulo 1 Factoring Problem, M1FP.
In addition, a mall result about the expected time required to successfully guess the secret a or b is necessary to support the statement about M1FP and consequently, about the Naïve attack against the proposed method.
Lemma A2.
Let and independently, (where U denotes the discrete uniform distribution). Then, for all .
Proof.
If X and Y are independent random variables, both discrete uniformly distributed over , then and consequently, (see e.g., [17]). Now, let and where X and Y are independent and discrete uniformly distributed over , respectively. Then, in effect, , independently and
since for . □
Finally, the cryptanalysis attack according to the Naïve attack (in Algorithm 2) can be stated to be higher than the exponentialtime, i.e., -hard.
Theorem A3.
M1FP is -hard.
Proof.
Version 1 (when the seed s is secret): Assuming that the secrets s, a and b have been chosen entirely randomly (i.e., uniformly) on , then the expected number of attempts required to guess the right value of is . Correspondingly, to guess or , the expected number of steps is according to Lemma A2 more than . Adding to this the steps for multiplications , we end up with a total complexity of . This makes the naïve attack neither in nor in but rather an -hard problem.
Version 2 (when the seed s is public): The argument is similar to Version 1 except that the initial guessing at s is omitted. This boils down to a total complexity of , still making the attack an -hard. □
References
- Diffie, W.; Hellman, M. New Directions in Cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–655. [Google Scholar] [CrossRef]
- Gupta, D.; Biswas, G. On Securing Bi- and Tri-partite Session Key Agreement Protocol Using IBE Framework. Wirel. Pers. Commun. 2017, 96, 4505–4524. [Google Scholar] [CrossRef]
- Goldwasser, S. New Directions in Cryptography: Twenty Some Years Later. In Proceedings of the 38th Annual Symposium on Foundations of Computer Science, Miami Beach, FL, USA, 20–22 October 1997; pp. 314–324. [Google Scholar]
- Shor, P. Polynomial-time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer. SIAM J. Comput. 1997, 25, 1484–1509. [Google Scholar] [CrossRef]
- Hoffstein, J.; Pipher, J.; Silverman, J. NTRU: A Ring-based Public Key Cryptosystem. In Algorithmic Number Theory, Third International Symposium ANTS-III; Springer: Berlin/Heidelberg, Germany, 1998; pp. 267–288. [Google Scholar]
- Hoffstein, J.; Pipher, J.; Silverman, J. NSS: An NTRU Lattice-based Signature Scheme. In Advance in Cryptology—EUROCRYPT 2001, International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2001; pp. 211–228. [Google Scholar]
- Lei, X.; Liao, X. NTRU-KE: A Lattice-based Public Key Exchange Protocol. IACR Cryptol. ePrint Arch. 2013, 2013, 718. [Google Scholar]
- Gupta, D.; Biswas, G.; Nandan, R. Security Weakness of a Lattice-based Key Exchange Protocol. In Proceedings of the 2018 4th International Conference on Recent Advances in Information Technology, Dhanbad, India, 15–17 March 2018; pp. 1–5. [Google Scholar]
- Singh, S.; Padhye, S. MaTRU-KE: A Key Exchange Protocol Based on MaTRU cryptosystem. Int. J. Commun. Syst. 2019, 32, e3886. [Google Scholar] [CrossRef]
- Akleylek, S.; Kaya, N. New Quantum Secure Key Exchange Protocols Based on MaTRU. In Proceedings of the 2018 6th International Symposium on Digital Forensic and Security, Antalya, Turkey, 22–25 March 2018; pp. 260–264. [Google Scholar]
- Jalali, A.; Azarderakhsh, R.; Kermani, M.; Jao, D. Supersingular Isogeny Diffie-Hellman Key Exchange on 64-Bit RAM. IEEE Trans. Dependable Secur. Comput. 2019, 16, 902–912. [Google Scholar] [CrossRef]
- Li, X.; Leung, L.; Kwan, A.; Zhang, X.; Kahanda, D.; Anshel, M. Post-Quantum Diffie-Hellman and Symmetric Key Exchange Protocols. In Proceedings of the 2006 IEEE Information Assurance Workshop, West Point, NY, USA, 21–23 June 2006; p. 382. [Google Scholar]
- Miller, F. Telegraphic Code to Insure Privacy and Secrecy in the Transmission of Telegrams; CM Cornwell: New York, NY, USA, 1882. [Google Scholar]
- Dworkin, M.; Barker, E.; Nechvatal, J.; Foti, J.; Bassham, L.; Roback, E.; Dray, J., Jr. Advanced Encryption Standard (AES); Technical Report, Federal Inf. Process. Stds. (NIST FIPS)-197; NIST: Gaithersburg, MD, USA, 2001. [Google Scholar]
- Granlund, T. GNU MP—The GNU Multiple Precision Arithmetic Library, 6.1.2 ed.; Free Sofware Foundation Inc.: Boston, MA, USA, 2016. [Google Scholar]
- Wiebe, N.; Kluchnikov, V. Floating Point Representations in Quantum Circuit Synthesis. arXiv 2013, arXiv:1305.5528v3. [Google Scholar] [CrossRef]
- Feller, W. An Introduction to Probability Theory and Its Applications, 2nd ed.; John Wiley and Sons: Hoboken, NJ, USA, 1950. [Google Scholar]
© 2020 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).