New Authentication Algorithm Based on Verifiable Encryption with Digital Identity
Abstract
:1. Introduction
2. Digital Identity and Authentication
- appearance information (fingerprints, facial features, biometrics, etc.)
- certificates published by credential service providers
- cards issued by trusted institutions (credit cards, debit cards, driving license cards, etc.)
- personal memories (passwords and secret questions)
- authentication via network
- unlocking local devices
- unlock local devices via network
3. Verifiable Encryption
3.1. Cryptosystem and Authentication Algorithm
- Registration
- Distribute the secret information by public key distribution
- Verification
- Verify the information using an authentication algorithm.
3.2. Verifiable Encryption
4. Cryptosystems Belonging to the VE Class
4.1. Fiat–Shamir’s Algorithm
- Step 1
- Alice chooses random number arbitrarily. Then Alice calculates , and sends x to Bob.
- Step 2
- Bob chooses a random number arbitrarily, and sends e to Alice.
- Step 3
- Alice calculates by using secret information of Alice, and sends y to Bob.
- Step 4
- Bob calculates and checks that is equal to .
4.2. Schnorr’s Algorithm
- Step 1
- Alice chooses random number arbitrarily. Then Alice calculates , and sends a to Bob.
- Step 2
- Bob chooses random number arbitrarily, and sends e to Alice.
- Step 3
- Alice calculates by using secret information of Alice, and sends x to Bob.
- Step 4
- Bob confirms that is equal to mod p.
4.3. One-Time Pad
4.4. Block Cipher Modes of Operation
- Electric code block (ECB) mode divides a plain text into blocks and encrypts in each block.
- Cipher block chaining (CBC) mode calculates the plain text block and preceding ciphered text block by XOR, and then the output is encrypted.
- Output feedback (OFB) mode is used as a pseudorandom number generator that outputs an encrypted initial vector.
- Cipher feedback (CFB) mode calculates the XOR of the modified preceding ciphered text blocks and plain text block.
- generate a key stream z of length n
- (a)
- (b)
- (c)
- calculate
5. New Authentication Algorithm Based on VE
5.1. Authentication via Network
5.2. Unlocking Local Devices
5.3. Unlocking Local Devices via the Network
- The user sends the digital identity to a device.
- The device queries a server via the network, and the server sends back responses.
- The device compares the digital identity with the one from the server.
5.4. Algorithm
- Registration step
- Step 1
- Alice sends to Bob.
- Step 2
- Bob generates k, and calculates .
- Step 3
- Bob sends to the server S.
- Verification step
- Step 1
- Alice sends to Bob.
- Step 2
- Bob generates , and calculates .
- Step 3
- Bob sends to S.
- Step 4
- Server calculates , and sends to Bob.
- Step 5
- Bob calculates , and checks the result.
6. Implementation
6.1. Algorithm
- Registration Step
- Step 1
- A sends A’s digital identity to D.
- Step 2
- D generates the key k that is kept only with D. Then D computes , and sends the encoded digital identity to S.
- Step 3
- S stores in the database.
- Verification Step
- Step 1
- A sends A’s digital identity to D.
- Step 2
- D generates the one-time key for the only one-time authentication. This one-time key is never used after finishing this authentication flow. Then D computes , and sends the encoded digital identity to S.
- Step 3
- S computes the encoded distance between and using map F such thatand sends encoded distance to D.
- Step 4
- D decodes the encoded distance with the keys k and to obtain the distance , where
6.2. Environment
6.3. Registered Information
6.4. Experiment
- Authentication of same sequences 1 ()
- Authentication of same sequences 2 ()
- Authentication of different sequences ()
- Authentication of different sequences ()
7. Attacks
7.1. Impersonation (Man-in-the-Middle-Attack)
7.2. Plain Text Attack
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Boneh, D.; Di Crescenzo, G.; Ostrovsky, R.; Persiano, G. Public key encryption with keyword search. In Advances in Cryptology—EUROCRYPT 2004, Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Cachin, C., Camenisch, J.L., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; pp. 506–522. [Google Scholar]
- Abdalla, M.; Bellare, M.; Catalano, D.; Kiltz, E.; Kohno, T.; Lange, T.; Malone-Lee, J.; Neven, G.; Paillier, P.; Shi, H. Searchable encryption revisited: Consistency properties, relation to anonymous IBE, and extensions. In Advances in Cryptology—CRYPTO 2005, Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2005; Shoup, V., Ed.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 205–222. [Google Scholar]
- Hu, C.; Liu, P. Decryptable searchable encryption with a designated tester. Procedia Eng. 2011, 15, 1737–1741. [Google Scholar] [CrossRef]
- Li, S.; Li, M.; Xu, H.; Zhou, X. Searchable Encryption Scheme for Personalized Privacy in IoT-Based Big Data. Sensors 2019, 19, 1059. [Google Scholar] [CrossRef] [PubMed]
- Guo, C.; Zhuang, R.; Jie, Y.; Choo, K.K.R.; Tang, X. Secure Range Search over Encrypted Uncertain IoT Outsourced Data. IEEE Internet Things J. 2019, 6, 1520–1529. [Google Scholar] [CrossRef]
- Zhou, R.; Zhang, X.; Wang, X.; Yang, G.; Li, W. Keyword Searchable Encryption with Fine-Grained Forward Secrecy for Internet of Thing Data. In International Conference on Algorithms and Architectures for Parallel Processing ICA3PP; Springer: Cham, Switzerland, 2018; Volume 11337, pp. 288–302. [Google Scholar]
- Rivest, R.L.; Shamir, A.; Adleman, L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Elgamal, T. A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inf. Theory 1985, 31, 469–472. [Google Scholar] [CrossRef]
- Gentry, C. A Fully Homomorphic Encryption Scheme. Ph.D. Dissertation, Stanford University, Stanford, CA, USA, September 2009. [Google Scholar]
- Gentry, C.; Halevi, S. Implementing Gentry’s fully-homomorphic encryption scheme. In Advances in Cryptology—EUROCRYPT 2011, Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Tallinn, Estonia, 15–19 May 2011; Paterson, K.G., Ed.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 129–148. [Google Scholar]
- Yasuda, M.; Shimoyama, T.; Kogure, J.; Yokoyama, K.; Koshiba, T. Packed homomorphic encryption based on ideal lattices and its application to biometrics. In Security Engineering and Intelligence Informatics, Proceedings of the International Conference on Availability, Reliability, and Security, Regensburg, Germany, 2–6 September 2013; Cuzzocrea, A., Kittl, C., Simos, D.E., Weippl, E., Xu, L., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 55–74. [Google Scholar]
- Fiat, A.; Shamir, A. How to prove yourself: Practical solutions to identification and signature problems. In Advances in Cryptology—CRYPTO ’86, Proceedings of the Conference on the Theory and Application of Cryptographic Techniques, Santa Barbara, CA, USA, 11–15 August 1986; Odlyzko, A.M., Ed.; Springer: Berlin/Heidelberg, Germany, 1986; pp. 186–194. [Google Scholar]
- Schnorr, C.P. Efficient identification and signatures for smart cards. In Advances in Cryptology—CRYPTO ’89, Proceedings of the Conference on the Theory and Application of Cryptology, Santa Barbara, CA, USA, 20–24 August 1989; Brassard, G., Ed.; Springer: New York, NY, USA, 1989; pp. 239–252. [Google Scholar]
- Feige, U.; Fiat, A.; Shamir, A. Zero-knowledge proofs of identity. J. Cryptol. 1988, 1, 77–94. [Google Scholar] [CrossRef]
- Goldwasser, S.; Micali, S.; Rackoff, C. The knowledge complexity of interactive proof systems. SIAM J. Comput. 1989, 18, 186–208. [Google Scholar] [CrossRef]
- Goldreich, O. Foundations of Cryptography: Volume 1—Basic Tools; Cambridge University Press: Cambridge, UK, 2001. [Google Scholar]
- Daemen, J.; Rijmen, V. The Design of Rijndael: AES—The Advanced Encryption Standard; Springer Science and Business Media: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Murakami, T. Japan’s National IT Strategy and the Ubiquitous Network; NRI Paper 97; Nomura Research Institute: Tokyo, Japan, 2005. [Google Scholar]
- Abundo, M.; Accardi, L.; Auricchio, A. Hyperbolic automorphisms of tori and pseudo-random sequences. Calcolo 1992, 29, 213–240. [Google Scholar] [CrossRef]
- Accardi, L.; Regoli, M.; Ohya, M. The QP-DYN algorithms. In QP–PQ Quantum Probability and White Noise Analysis, Volume 28; Accardi, L., Freudenberg, W., Ohya, M., Eds.; World Scientific: Singapore, 2010; pp. 1–16. [Google Scholar]



| Type | Examples | |
|---|---|---|
| 1 | authentication via network | electronic commerce transaction private information transmission |
| 2 | unlocking local devices | unlocking smartphones biometric authentication |
| 3 | unlocking local devices via network | entering workplace, concert hall, checkout-free shopping store |
| Aspect | Specification |
|---|---|
| OS | Mac OS High Sierra 10.13.5 |
| CPU | Intel Core i7 1.7 GHz |
| Memory | 8 GB |
| Language | Python |
| Type of Information | Variable | Value |
|---|---|---|
| plain text | 1001100000011101100101000001100000011100111 1110001110111100010001101111110110100001001 010000010010000001110100101000111101101010 | |
| key | 1001100110111111111111011001011101010100001 1000010111001110100011011111000110101111011 010001111000001110110000011010100100000101 | |
| cipher text | 1101000100110100110001111010010001100110 0110011100101100101100001100000011100100 00001101010001111000100110010011001101111 |
| Type of Information | Variable | Value |
|---|---|---|
| plain text | 1001100000011101100101000001100000011100111 1110001110111100010001101111110110100001001 010000010010000001110100101000111101101010 | |
| key | 1100010100010110010111101011110011010010110 1010011101100000110110011000010011111010010 000011001010001110000101010101010001111010 | |
| cipher text | 101110100001011110010101010010011001110001 010001001101110010011111011110010101101101 1010011011000001111110001111101101100010000 | |
| encrypted result | 101110010101001101000110010101110000110111 001000101010111001010100011101010101010100 1010010110010000000110101001111110101111111 | |
| result | 0 |
| Type of Information | Variable | Value |
|---|---|---|
| plain text | 1001100000011101100101000001100000011100111 1110001110111100010001101111110110100001001 010000010010000001110100101000111101101010 | |
| key | 1100001100110100001000110000010000001000111 0111110101101100011101101010101000111000111 110011011101000010001110001100010111011001 | |
| cipher text | 1011011001010011011011100011100000101000001 001111011010000001100000101011110011001110 100011001111000011111010100100101010110011 | |
| encrypted result | 1011010100010111101111010010011010111001101 111100010100010111110110101101110010111100 100010100101001100111110010110110011011100 | |
| result | 0 |
| Type of Information | Variable | Value |
|---|---|---|
| plain text | 1101100110010101011011010011101101011000101 1010110111000101011111000010010001110011010 101101011001111011110000111100011100011000 | |
| key | 1001101000011010111011010110110101110000110 1101010001001111011011100011011100110100101 011011011011111001000111010100111001011100 | |
| cipher text | 1000011100011111000000001010110001010000110 111100110001010000100100001001101000111111 110110000010000010110111101000100101000100 | |
| encrypted result | 1000010001011011110100111011001011000001010 001111111111000110110010001111101001001101 110111101000001101110011011010111100101011 | |
| result | 1000001100010001111100100100011010001000100 100111001111001001110101101100111010010011 111101001011111010000100010100100001110010 |
| Type of Information | Variable | Value |
|---|---|---|
| plain text | 0 | |
| key | 1001001000100111000101111100010100001011101 0101100100100000000010111010000110001001000 111101011011001010101101110001111100010101 | |
| cipher text | 1001001000100111000101111100010100001011101 0101100100100000000010111010000110001001000 111101011011001010101101110001111100010101 | |
| encrypted result | 1001001110000101011111100100101001000011011 0011111101010010110000001010110110000111010 111100110001000101101001000011100101111010 | |
| result | 1001100000011101100101000001100000011100111 1110001110111100010001101111110110100001001 010000010010000001110100101000111101101010 | |
| Hamming distance | h | 59 |
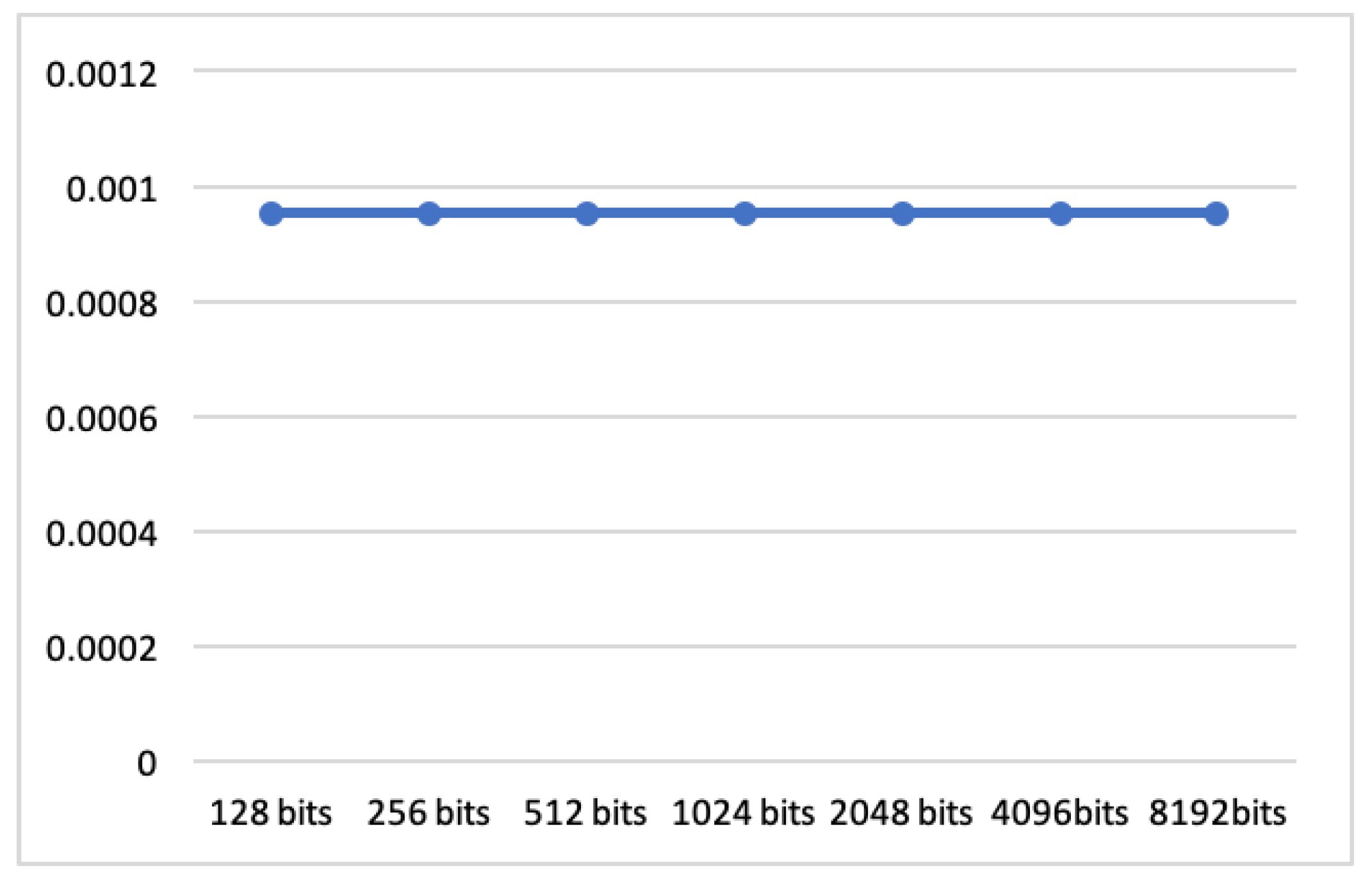
| Length of Plaintext | Encryption | Verification | Decryption |
|---|---|---|---|
| 128 bits | 0.00095367 ms | 0.00095367 ms | 0.00095367 ms |
| 256 bits | 0.00095367 ms | 0.00095367 ms | 0.00095367 ms |
| 512 bits | 0.00095367 ms | 0.00095367 ms | 0.00095367 ms |
| 1024 bits | 0.00095367 ms | 0.00095367 ms | 0.00095367 ms |
| 2048 bits | 0.00095367 ms | 0.00095367 ms | 0.00095367 ms |
| 4096 bits | 0.00095367 ms | 0.00095367 ms | 0.00095367 ms |
| 8192 bits | 0.00095367 ms | 0.00095367 ms | 0.00095367 ms |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kihara, M.; Iriyama, S. New Authentication Algorithm Based on Verifiable Encryption with Digital Identity. Cryptography 2019, 3, 19. https://doi.org/10.3390/cryptography3030019
Kihara M, Iriyama S. New Authentication Algorithm Based on Verifiable Encryption with Digital Identity. Cryptography. 2019; 3(3):19. https://doi.org/10.3390/cryptography3030019
Chicago/Turabian StyleKihara, Maki, and Satoshi Iriyama. 2019. "New Authentication Algorithm Based on Verifiable Encryption with Digital Identity" Cryptography 3, no. 3: 19. https://doi.org/10.3390/cryptography3030019
APA StyleKihara, M., & Iriyama, S. (2019). New Authentication Algorithm Based on Verifiable Encryption with Digital Identity. Cryptography, 3(3), 19. https://doi.org/10.3390/cryptography3030019





