Abstract
With the rapid development of modern technology, personal privacy has become a critical concern in many applications. Various digitalized applications such as online voting systems and the electronic cash systems need authenticity and anonymity. Blind signature is an advanced technique that provides the authenticity and anonymity of the user by obtaining a valid signature for a message without revealing its content to the signer. The message recovery property minimizes the signature size and allows efficient communication in situations where bandwidth is limited. With the advantage of blind signature and message recovery properties, in this paper, we present a new pairing free blind signature scheme with message recovery in Identity-based settings. The proposed scheme is proven to be secure in the random oracle model under the assumption that the Elliptic Curve Discrete Logarithm Problem (ECDLP) is intractable. The proposed scheme meets the security requirements such as blindness, untracebility, and unforgeability. We compare our scheme with the well-known existing schemes in the literature, and the efficiency analysis shows that our scheme is more efficient in terms of computational and communicational point of view.
1. Introduction
Digital Signature is one of the most important applications of Public Key Cryptography (PKC) and provides authenticity, data integrity, and non-repudiation. In traditional PKC, proposed by Diffie and Hellman [1] in 1976, authentication of public key relies on the certificate issued by Certificate Authority (CA). However, certificate management leads to extra storage, large computation, and communication costs. To surmount the obstacles in traditional PKC, Shamir [2] introduced Identity–based PKC (ID-PKC). In this system, public key of a user is resulting from user’s identity such as email and phone number; and secret key is generated from user’s public key via a trusted third party called Private Key Generator (PKG). To implement the digital signature in the real-world applications, we need to consider different features and properties to make them adequate and proper for different usages. There are many digital signature schemes in the literature with different properties such as Proxy signature, Aggregate signature, Multi signature, Group signature, Ring signature, etc. One of such variant is Blind Signature.
Blind signature is used to protect anonymity of a user in many applications such as electronic payment on e-commerce and anonymous electronic voting systems [3,4,5,6,7,8]. The concept of blind signature was introduced by Chaum [7] in 1982. In contrast to regular digital signature schemes, a blind signature scheme is an interactive two-party protocol between a user and a signer. The user acquires a signature on a message from the signer, however the content of the message and the final blind signature is not known to the signer. With the development of electronic commerce, the preservation of anonymity of the user has been an imperative need. As blind signature allows secure electronic payment and protects customers’ privacy or anonymity in e-cash transactions, it is a very important tool for electronic cash transmission. Similarly, e-voting uses blind signatures to obtain votes without violating the anonymity of the voter.
Message recovery is a concept where some (partial), or all (full), of the message is embedded in the signature itself. A digital signature scheme with this feature allows conserving bandwidth when transmitting a signed message, compared to a signature scheme with appendix. The digital signature scheme with a message recovery was first introduced by Nyberg and Rueppel [9] in 1993. In this signature scheme, the message itself is not required to be transmitted together with the signature. In fact, the message is embedded in the signature and can be recovered during the verification/message recovery process. In this way, the total length of the message and the appended signature can be shortened. It is very much suitable in situations where bandwidth is one of the main concerns. Combination of blind signature technique with message recovery integrates the advantages of both and provides anonymity, untraceability, and unforgeability for low bandwidth devices.
1.1. Related Work
After the introduction of blind signatures by Chaum [7], many blind signature schemes [10,11,12,13,14] were proposed in traditional PKC. Advantages of Identity based cryptosystem attracted the researchers towards it [15]. The first ID-based blind signature scheme was proposed by Zhang et al. [16] in 2002. Later many identity-based blind signature schemes have been proposed in literature along with its applications in e-cash and e-voting systems [17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35]. Most of these schemes are designed using bilinear pairings over elliptic curves [17,18,19,20,21,22,23,25,26,28,31,35]. In 2003, Zhang et al. [17] and in 2005, Huang et al. [18] proposed different efficient ID-based blind signature schemes. In 2006, Zhao et al. [19] proposed a new identity based blind signature scheme from bilinear pairings. In 2008, Kalkan et al. [20] presented a generalized ID-based blind signature from bilinear pairings. In 2010, Rao et al. [21] proposed a blind signature scheme using bilinear pairings over elliptic curves. The proposed scheme is based on the Hess identity-based digital signature scheme [22] and the security is based on the CDH problem. In 2010, Fan et al. [23] proposed a provably secure randomized blind signature scheme based on bilinear pairings. They proved the security for unlinkability, unforgeability in ROM. In the same year, Zhang et al. [24] proposed a novel ID-based blind signature for electronic voting system and Shakerian et al. [25] proposed blind signature scheme from pairings. In 2011, He et al. [26] proposed an efficient identity-based blind signature scheme without bilinear pairings, and their work is motivated by the importance of blind signatures, which guarantees the anonymity of users. Later, Hu et al. [27] presented ID-based blind signature without random oracle model. In 2013, Xu et al. [28] presented an ID-based blind signature scheme from pairings with unlinkability. In the same year, Jain et al. [29] presented an efficient ID-based blind signature scheme in E-voting. Later, Li et al. [30] presented a partially blind signature scheme standard model. In 2014, Pance et al. [31] presented a comparison of ID-based blind signatures from pairings for E-voting. In 2015, Girish et al. [32] proposed a survey paper on Identity based blind signature schemes. In 2016, Islam et al. [33] proposed a provably secure pairing-free identity-based partially blind signature scheme and its application in online e-cash system. The security analysis of the proposed scheme was presented in the random oracle model, which substantiated that it was provably secure. In 2017, Kumar et al. [34] proposed a blind signature for E-voting in ID-based setting. In the same year Sarde et al. [35] presented a blind and proxy blind signature scheme. Most of these schemes are designed using bilinear pairings over elliptic curves. In addition to these, very few ID-based blind signature schemes with message recovery have been proposed in literature [23,36,37,38,39,40]. In 2007, Han et al. [36] proposed a blind signature scheme with message recovery, using pairings over elliptic curves. This paper is based on modified Weil/Tate pairings over elliptic curves, which improves the key size. In 2008, Hassan et al. [37] proposed a new identity-based blind signature scheme with message recovery based on Zhang et al. scheme. Their scheme is more efficient than Han et al. [36] scheme. It requires less bandwidth and is suitable for signing short messages such as pin card numbers and short identifiers. Additionally, in 2013, Diao et al. [38] proposed a new proxy blind signature scheme with message recovery. In 2017, James et al. [39] proposed an identity-based blind signature scheme with message recovery using bilinear pairings over elliptic curves. Recently, in 2018, Verma and Singh [40] proposed an efficient identity-based blind signature scheme with message recovery using bilinear pairings. However, the above-mentioned blind signature schemes are designed using bilinear pairings over elliptic curves. Additionally, these blind signature schemes are designed with message recovery using pairings.
1.2. Motivation
In any PKC, to provide the high security, the length of the key size must be sufficiently large. Larger keys in cryptographic schemes cause less computational efficiency and require more bandwidth. Thus, cryptographic schemes with smaller key size are desirable. To meet this requirement, Koblitz [41] and Miller [42] independently proposed the Elliptic Curve Cryptography (ECC) using elliptic curves. ECC has many advantages over PKC, especially; ECC provides high security with smaller keys in size. For instance, ECC with 512 bit key provides the same level of security as in AES (Advanced Encryption Standard; symmetric algorithm) with 256 bit key and in RSA with 15,360 bit key. Thus, ECC based schemes have shorter key sizes and requires low computational and communicational costs; consequently, time management, storage space, and consumption of bandwidth become very less with these small keys. Though ECC provides much security with short keys, the computational cost of a bilinear pairing over elliptic curve group is a costly operation, and is significantly more expensive than the elliptic curve scalar multiplication operation. In addition, map to point hash function is also very expensive cryptographic operation. Due to the expensive operations such as bilinear pairings and map to point hash functions, most of the cryptographic schemes are having less efficiency while implementing them. In view of this, ECC based schemes without pairing operation under general hash function would be more desirable to achieve high efficiency with the same level of security. Motivated by this, we focus on the design of new identity based blind signature scheme with message recovery in a pairing free environment.
1.3. Our Contribution
In this paper, we present a Pairing Free Identity based Blind Signature scheme with message recovery over elliptic curves. The blindness property provides anonymity and untraceability. This scheme is secure against forgeability and the security proof is presented in the ROM model under the hardness of ECDLP. To the best of our knowledge, this is the first blind signature scheme in identity-based setting addressing about message recovery in a pairing free environment. Our scheme achieves high efficiency and is more comfortable for resource constrained applications. We presented the comparative analysis of our scheme with existing schemes and it shows that the proposed scheme is efficient in terms of computational and communicational point of view.
1.4. Organization
The remaining part of this paper is organized as follows. In Section 2, we presented some preliminaries. The syntax and security model for our PF-IDBS-MR scheme are presented in Section 3. The proposed PF-IDBS-MR scheme is presented in Section 4. Security analysis and efficiency analysis of our PF-IDBS-MR scheme are presented in Section 5. The conclusions of the paper are presented in Section 6.
2. Preliminaries
This section briefly presents the fundamental concepts of ECC and the complexity assumption, on which the proposed scheme is designed and achieves the desired security.
2.1. Elliptic Curve Cryptography
Elliptic curve cryptography (ECC) has become more popular and plays a very important role in modern PKC [41,42].
Let be a set of elliptic curve points over the prime field , defined by the non-singular elliptic curve equation: with and . The additive elliptic curve group is defined as and , where the point O is known as “point at infinity”. The order of the elliptic curve over is satisfies the relation . The scalar multiplication on the cyclic group defined as k∙P = P + P+∙∙∙+ P (k times). Here, is the generator of order n.
2.2. Elliptic Curve Discrete Logarithm Problem
- Given a tuple it is computationally hard for any Probabilistic Polynomial Time (PPT) algorithm dv to determine where and
- The probability that any polynomial-time bounded algorithm dv can solve the ECDLP is defined as = Prob
2.3. Notations and Acronyms
The following Table 1 presents the acronyms that are used throughout this paper.

Table 1.
Acronyms and explanation.
The following Table 2 presents the symbols and their descriptions, which have been used throughout this paper.

Table 2.
Notation and Meaning.
3. Syntax and Security Model of the Proposed PF-IDBS-MR Scheme
In this section we present the syntax and security model of the proposed PF-IDBS-MR scheme.
3.1. Syntax of PF-IDBS-MR
A formal model of the proposed scheme consists of the following four algorithms: System Setup, Key Extract, Blind Signature Generation, and Blind Signature Verification. The detailed description of these algorithms is described below.
- System Setup. For a given security parameter the Private Key Generator (PKG) runs this algorithm and generates the system parameters Params and the master key s. Params are made public and s is kept secret. Params are implicit input to all the following algorithms.
- Key Extract. For a given user’s identity ID, the PKG runs this algorithm to generate the public key and private key. PKG sends the private key to the corresponding user over a secure channel.
- Blind Signature Generation. This is an interactive and probabilistic polynomial time protocol, which is operated by the user and the signer. The user first blinds the message and obtains a new version of and then sends it to the signer. The signer uses his/her private key to sign on and obtains and then sends it to the sender/user. The sender un-blinds it to obtain which is a blind signature on the original message
- Blind Signature Verification. For a signer’s identity ID and a blind signature a verifier runs this algorithm to recover the message and check the validity of the blind signature more precisely, the algorithm Verify outputs 1 if accepted, or 0 if rejected.
3.2. Security Requirements of the Proposed PF-IDBS-MR
A secure blind signature scheme must satisfy the following requirements:
- Correctness. If the user and the signer, both comply with the algorithm of blind signature generation, then the blind signature will always be accepted. The correctness of the signature can be checked by anyone using the signer’s public key.
- Blindness. A signature is said to be blind if a given message-signature pair and the signer’s view are statistically independent. While correctly operating one instance of the blind signature scheme, let the output be (i.e., message-signature pair) and the view of the protocol At a later time, the signer is not able to link to Hence, the content of the message is blind to the signer.
- Unforgeability. With this property, the user is not able to forge a valid blind signature. Only the signer can give a valid signature for the associated message.
Now we present the security definitions of blindness and unforgeability for our proposed scheme.
Definition 1.
(Blindness) Letdv be a probabilistic polynomial-time adversary which plays the role of the signer,be two honest users.engage in the blind signature issuing scheme withdv on messages, and output signatures, respectively, whereis a random bit chosen uniformly.are sent todv and thendv outputsFor all suchdv,for any constant, and for sufficiently large
Definition 2.
(Unforgeability) The proposed PF-IDBS-MR is secure against existential forgery under the adaptive chosen message attack (EF-ACMA) and identity attacks if there is no probabilistic polynomial time adversary has a non-negligible advantage in the following game.
Our proposed scheme is existentially unforgeable in the Random Oracle Model (ROM) under an adaptive chosen-message and an adaptive chosen-ID attack. In this model (Game), a forger can choose its messages and its identities adaptively. We give the forger the power to request private keys on identities of its choice. The forger is also given access to the signing oracle for any messages for desired identities. A forger’s advantage is defined as its probability of success in the following game between a challenger and a forger dv. The advantage to win the above game by a PPT-bounded adversary dv with the help of is defined as
.
Game Model.
- Setup. The challenger takes a security parameter k and executes the setup algorithm of the PF-IDBS-MR. returns the system Params to dv and keeps the master secret with itself.
- Queries. The forger dv adaptively makes the following different queries to the challenger
- -
- Hash Queries. When the involved hash functions are modeled by random oracles dv also performs adaptive queries to the hash functions. The Challenger answers these queries of the forger of this oracle, providing it with consistent and totally random values.
- -
- Extract Queries. When dv requests the private key of an identity ID of its choice, the challenger runs the key extraction algorithm on ID and forwards the output to dv.
- -
- Sign Queries. When dv requests, adaptively, a signature on a given message with an identity ID, returns a signature
- Output. dv outputs and we say that dv succeeds if:
- (i)
- has never requested to the private key extraction oracle;
- (ii)
- has not been obtained as an answer of the challenger to a sign query ;
- (iii)
- is a valid signature.
4. Proposed PF-IDBS-MR Scheme
The proposed Pairing Free Identity based Blind signature with Message Recovery scheme consists of the following four algorithms:
- System Setup. For a given security parameter the PKG runs this algorithm as follows.
- Choose a cyclic additive group of prime order with the points on an elliptic curve and as the generator of
- Select randomly and compute the system public key
- Choose and as hash functions. are positive integers such that .
- PKG publishes the system parameters as public and keeps the master key as secret.
- Key Extract. Given a user’s identity ID, the PKG runs this algorithm by choosing and computes ; ;This algorithm returns and sends it securely to the corresponding user as his private key.
- Blind signature generation. In order to sign a message blindly by a signer, whose identity is the user and the signer should follow the scenario given below:
- Signer: Chooses a number and computes and sends to the user as a commitment.
- Blinding: The user chooses blinding factors randomly and computesNow the user sends to the signer.
- Signing: The signer computes and sends back to the user.
- Unblinding: The user computes the following.The user outputs and is the blind signature on the messageThe blind signature issuing protocol is shown in Table 3.
 Table 3. The blind signature issuing protocol.
Table 3. The blind signature issuing protocol.
- Blind signature verification. To verify the signature for the message and the identity the verifier computesThe verifier recovers the messageAccept the signature as valid on
5. Analysis of the Proposed PF-IDBS-MR Scheme
This section presents the security analysis and efficiency analysis of the proposed PF-IDBS-MR scheme.
5.1. Security Analysis of the Proposed Scheme
In the following we will analyse the security of our PF-IDBS-MR scheme. We prove the correctness property, blindness property and unforgeability of our PF-IDBS-MR scheme by the following two theorems.
Theorem 1.
(Proof of Correctness) The proposed scheme satisfies the property of correctness.
Proof of Theorem 1.
The following equations give the correctness of the proposed scheme.
□
Theorem 2.
(Blindness) The proposed scheme satisfies the blindness property.
Proof of Theorem 2.
We consider the condition in Definition 1. Let be one of the two signatures given to adversary dv. Let be the data exchanged during one of the signature issuing schemes in the view of dv. It is sufficient to show that there exists two random factors to From the description of the scheme, we know the following equations must hold.
From Equation (3), we get and if replacing in Equation (1), we get that it is obvious that is unique. Then is unique, since Thus, and have exactly the same relation defined by the signature issuing protocol. Such always exist regardless of the values of and Even an infinitely powerful dv outputs a correct value with a probability exactly Thus, the proposed scheme is unconditionally blind. □
Theorem 3.
(Unforgeability) The proposed scheme is existential unforgeable against the adaptive chosen message and identity attacks based on the infeasibility assumption of the ECDLP.
Proof of Theorem 3.
Let be an ECDLP challenger, and it is given a random instance of the ECDL problem in for a randomly chosen . Its goal is to compute . Let dv be an adversary who interacts with , as described in security model of the proposed scheme (Section 3.2). Now, we prove that can solve the ECDLP using dv. During the simulation process, needs to guess the target identity of dv. Without loss of generality, takes as target identity of dv on a message
- Initialization phase. runs the setup algorithm and sets as public key and generates system parameters params and sends params, dv.
- Queries phase. dv can access the following oracle in an adaptive manner and the algorithm responds to these oracles as follows.
- -
- Extraction oracle. maintains an initial-empty which includes the tuples like when dv makes this query on identity looks for in the list and returns the output to dv as follows.
- If aborts.
- IfClearly satisfies the equation Then outputs as secret key of the user and incorporates the tuple to list and returns to dv.
- -
- Queries on oracle When dv asks a query with the input , then replies with previous value , if the tuple is in Otherwise picks a random and returns to dv and adds to the list
- -
- Queries on oracle maintains a list which is initially empty. It contains tuples of the form After receiving the query on , if a tuple exists on returns . Otherwise, picks a random and returns adds to
- -
- Queries on : maintains two separate lists which are initially empty. If the queries are made earlier, then it returns the same answer. Otherwise, picks random numbers from respectively, and returns to adversary. stores these values in lists, respectively.
- -
- Signing oracle. When dv makes this query on first makes queries on oracles and recovers the tuples from lists, respectively. Then, does the following.
- Choose
- Set to the list
- Compute
Finally, responds to dv with the signature
Forgery. After forgery, a valid signature on the message under the identity by dv, recovers the corresponding tuples from lists. From the tuples, if halts and fails. Otherwise, if computes the value of as follows. From Forking Lemma (Pointcheval et al. [43]), if we have a replay of with the same random tape but different choices of , , dv will output another signature This signature satisfies the verification equation.
By we now denote discrete logarithms of , respectively, which is
As the signatures , satisfy the verification equations, we get two linearly independent equations as . solves the unknown values from the above two linearly independent equations and outputs as the solution of ECDLP. However, the ECDLP is computationally infeasible by any polynomial-time bounded algorithm. Therefore, based on the intractability assumption of ECDLP, our scheme is provably secure in the ROM against the adaptive chosen message and identity attacks. □
5.2. Efficiency Analysis of the Proposed Scheme
In this section, we analyze the performance of our PF-IDBS-MR scheme. We compare our scheme with the relevant schemes in terms of computational and communicational cost. We consider the experimental results (Ren et al. [44], Cao et al. [45], and Tan et al. [46]), to achieve the comparable security with 1024-bit RSA key, where the bilinear pairing (Tate pairing) is defined over the super singular elliptic curve with embedding degree 2 and the 160-bit Solinas prime number with 512-bit prime number p satisfying The running time is calculated for different cryptographic operations in References [44,45,46] using MIRACL (Shamus software) [47], a standard cryptographic library and implemented on a hardware platform PIV (Pentium-4) 3GHZ processor with 512-MB memory and a windows XP operating system. Furthermore, Chung et al. [48] indicated that the time needed to execute the elliptic curve scalar multiplication is approximately and the time needed to execute the modular exponentiation is approximately It was also mentioned in Reference [45] that the time needed to execute one pairing based scalar multiplication is approximately 6.38 ms, i.e, the time needed to execute one bilinear pairing (Tate pairing) operation is approximately 20.01 ms, i.e., and the time needed to execute one pairing-based exponentiation is approximately , i.e., Now, from the works proposed by Baretto et al. [49] and Tan et al. [46], and We summarize these computational results in Table 4.

Table 4.
Notations and descriptions of various cryptographic operations and their conversions.
5.2.1. Computational Efficiency
The comparison of our proposed PF-IDBS-MR scheme with the existing blind signature schemes, in terms of a computational point of view, is presented in Table 5. The total computational cost of our proposed scheme is which is much more efficient than the well-known existing schemes. While the computational cost of our scheme is equal to Islam et al. scheme [33], our proposed scheme achieves message recovery. Hence, our scheme is considered to be more efficient compared to Islam et al. scheme [33]. From Table 5, it is clear that the computation cost of our PF-IDBS-MR scheme is , which is 76.37% less than Han et al. scheme [36], 67.98% less than Hassan et al. scheme [37], 70.60% less than Fan et al. scheme [23], 69.95% less than Prasad et al. [21], 32.34% less than He et al. scheme [26], 67.01% less than James et al. [39], and 71.01% less than Verma et al. scheme [40]. Hence, our scheme is computationally more efficient when compared to the well-known related schemes [21,23,26,33,36,37,39,40].

Table 5.
Comparison of computational efficiency of our proposed scheme with the related schemes.
5.2.2. Communicational Efficiency
The comparison of our proposed PF-IDBS-MR scheme with the existing blind signature schemes, in terms of communicational point of view, is presented in Table 6. The schemes [21,23,36,37,39,40] are established on bilinear pairings. The remaining related schemes [26,33] and our proposed scheme is established on ECC. To achieve a security level of 80 bits, in bilinear pairing, we consider , where is an additive group that is generated by with the order on the super singular elliptic curve with embedding degree 2. Here, consists of 512 bit prime number and is of 160 bit solinas prime number. To achieve the same 80 bit security level, in ECC, we consider as an additive cyclic group generated by a point on a non-singular elliptic curve and its order is where are prime numbers of 160 bit each and Hence, the size of is 512 bits (i.e., 64 bytes) and the size of is 160 bits (i.e., 20 bytes). Hence, the size of elements in is bits and the size of elements in is bits. Additionally, the size of the elements in is 160 bits.

Table 6.
Comparison of communicational efficiency of our proposed scheme with the related schemes.
Since our proposed scheme is with message recovery, the original message of the signature is not required to be transmitted together with the signature, and hence the signature length of our proposed scheme is and the communication cost is bits = 100 bytes.
From Table 6, it is clear that our PF-IDBS-MR scheme is more efficient compared to the existing blind signature schemes [21,23,26,33,36,37,39,40], in a communicational point of view.
The following bar graphs (Figure 1 and Figure 2) clearly show that our scheme is much more efficient than the existing schemes. Hence, our PF-IDBS-MR scheme is much more efficient than the existing blind signature schemes, both from a computational and communicational cost point of view.
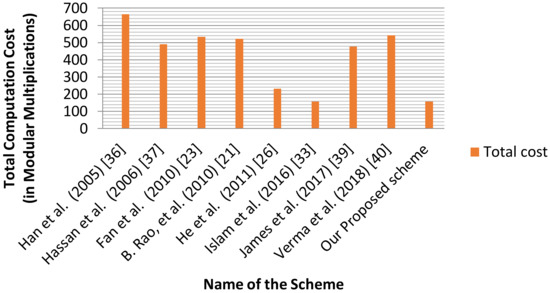
Figure 1.
Graphical representation of Total Computation Cost.
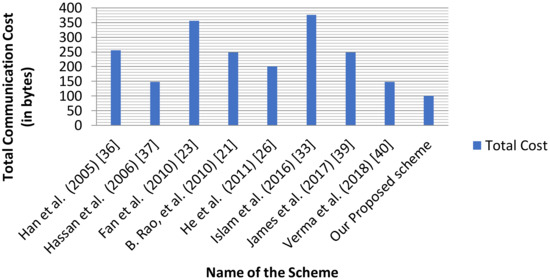
Figure 2.
Graphical representation of Total Communication Cost.
6. Conclusions
In this paper, we have presented a pairing-free Identity-based blind signature scheme with message recovery. This PF-IDBS-MR scheme combines the advantages of blind signature, message recovery property in ID-based setting. Moreover, it is designed in pairing-free environment. The correctness of the proposed scheme has been validated. The proposed scheme is secure and existential unforgeable against the adaptive chosen message and identity attacks under the assumption that ECDLP intractable. The blindness property of the proposed scheme provides the anonymity of the user and the message recovery property of the proposed scheme enhances the bandwidth efficiency. To the best of our knowledge, this is the first blind signature scheme with message recovery in pairing free environment. The comparison of our PF-IDBS-MR scheme with the existing schemes shows that the proposed scheme is efficient in terms of computational and communicational point of view. The proposed scheme is very useful in practical applications such as mobile communications, wireless sensor networks etc., where bandwidth is the main constrain. Due to the blindness and message recovery property, computational, and communicational efficiency, the proposed PF-IDBS-MR scheme can be applied efficiently in the design of e-voting and e-payment applications.
Author Contributions
Conceptualization, S.J.; Investigating, S.J.; Problem Designing, P.V.R.; Formal Analysis and Writing, N.B.G.; Review and Editing, N.B.G.; Supervision, P.V.R.
Funding
This research is received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Diffie, W.; Hellman, M.E. New Directions in Cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Shamir, A. Identity-Based Cryptosystems and Signature Schemes. In Proceedings of the Workshop on the Theory and Application of Cryptographic Techniques, Santa Barbara, CA, USA, 20–24 August 2000; pp. 47–53. [Google Scholar]
- Chang, C.C.; Lee, J.S. An anonymous voting mechanism based on the key exchange protocol. Comput. Secur. 2006, 25, 307–314. [Google Scholar] [CrossRef]
- Fan, C.I.; Sun, W.Z. An efficient multi-receipt mechanism for uncoercible anonymous electronic voting. Math. Comput. Model. 2008, 48, 1611–1627. [Google Scholar] [CrossRef]
- Liaw, H.T. A secure electronic voting protocol for general elections. Comput. Secur. 2004, 23, 107–119. [Google Scholar] [CrossRef]
- Delaune, S.; Kremer, S.; Ryan, M. Coercion-resistance and receipt-freeness in electronic voting. In Proceedings of the 19th IEEE Computer Security Foundations Workshop, Venice, Italy, 5–7 July 2006; pp. 28–42. [Google Scholar]
- Chaum, D. Blind Signatures for Untraceable Payments. Available online: https://link.springer.com/chapter/10.1007%2F978-1-4757-0602-4_18#citeas (accessed on 3 October 2018).
- Chaum, D.; Fiat, A.; Naor, M. Untraceable electronic cash. Adv. Cryptol. 1990, 403, 319–327. [Google Scholar]
- Nyberg, K.; Rueppel, R.A. A New Signature Scheme Based on the DSA Giving Message Recovery. In Proceedings of the 1st ACM Conference on Communication and Computer Security, Fairfax, VA, USA, 3–5 November 1993. [Google Scholar]
- Jeng, F.G.; Chen, T.L.; Chen, T.S. An ECC-based blind signature scheme. J. Netw. 2010, 5, 921–928. [Google Scholar] [CrossRef]
- Shen, V.R.L.; Chung, Y.F.; Chen, T.S.; Lin, Y.A. A Blind Signature Based on Discrete Logarithm Problem. Int. J. Innov. Comput. Inf. Control 2011, 7, 5403–5416. [Google Scholar]
- Garcia, L.L.; Perez, L.J.D.; Henriquez, F.R. A pairing-based blind signature e-voting scheme. Comput. J. 2014, 57, 1460–1471. [Google Scholar] [CrossRef]
- Verma, G.K.; Singh, B.B. New ID based fair blind signatures. Int. J. Current Eng. Sci. Res. 2016, 3, 41–47. [Google Scholar]
- Darwish, A.; Gendy, M.M.E. A New Cryptographic Voting Verifiable Scheme for E-Voting System Based on Bit Commitment and Blind Signature. Int. J. Swarm Intel. Evol. Comput. 2017, 6, 2. [Google Scholar] [CrossRef]
- Sahu, R.A.; Padhye, S. ID-based signature scheme from bilinear pairings: A survey. Front. Electr. Electron. Eng. 2011, 6, 487–500. [Google Scholar] [CrossRef]
- Zhang, F.; Kim, K. ID-based blind signature and ring signature from pairings. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Queenstown, New Zealand, 1–5 December 2002. [Google Scholar]
- Zhang, F.; Kim, K. Efficient ID-based blind signature and proxy signature. In Proceedings of the Australasian Conference on Information Security and Privacy, Sydney, NSW, Australia, 9–11 July 2003. [Google Scholar]
- Huang, Z.; Chen, K.; Wang, Y. Efficient identity-based signatures and blind signatures. In Proceedings of the International Conference on Cryptology and Network Security, Xiamen, China, 14–16 December 2005. [Google Scholar]
- Zhao, Z.; Zhao, Z.; Tang, X.; Liu, Y. A New ID-Based Blind Signature from Bilinear Pairings. In Proceedings of the 2006 IET International Conference on Wireless, Mobile and Multimedia Networks, Hangzhou, China, 6–9 November 2006. [Google Scholar]
- Kalkan, S.; Kaya, K.; Selcuk, A.A. Generalized ID-Based Blind Signatures from Bilinear Pairings. In Proceedings of the 23rd International Symposium on Computer and Information Sciences, Istanbul, Turkey, 27–29 October 2008. [Google Scholar]
- Rao, B.U.; Ajmath, K.A.; Reddy, P.V.; Gowri, T. An ID-Based Blind Signature Scheme from Bilinear Pairings. Int. J. Comput. Sci. Secur. 2010, 4, 98–106. [Google Scholar]
- Hess, F. Efficient identity-based signature schemes based on pairings. In Proceedings of the International Workshop on Selected Areas in Cryptography, St. John’s, NF, Canada, 15–16 August 2002. [Google Scholar]
- Fan, C.I.; Sun, W.Z.; Huang, V.S.M. Provably secure randomized blind signature scheme based on bilinear pairing. Comput. Math. Appl. 2010, 60, 285–293. [Google Scholar] [CrossRef]
- Zhang, L.; Hu, Y.; Tian, X.; Yang, Y. Novel identity-based blind signature for electronic voting system. In Proceedings of the 2010 Second International Workshop on Education Technology and Computer Science, Wuhan, China, 6–7 March 2010; pp. 122–125. [Google Scholar]
- Shakerian, R.; Pour, T.M.; Kamali, S.H. An identity based public key cryptography blind signature scheme from bilinear pairings. In Proceedings of the 2010 3rd International Conference on Computer Science and Information Technology, Chengdu, China, 9–11 July 2010; pp. 28–32. [Google Scholar]
- He, D.; Chen, J.; Zhang, R. An efficient identity-based blind signature scheme without bilinear pairings. Comput. Electr. Eng. 2011, 37, 444–450. [Google Scholar] [CrossRef]
- Hu, X.; Wang, J.; Yang, Y. Secure ID-based blind signature scheme without random oracle. In Proceedings of the 2011 International Conference on Network Computing and Information Security, Guilin, China, 14–15 May 2011; pp. 245–249. [Google Scholar]
- Xu, G.; Xu, G. An ID-based Blind Signature from Bilinear Pairing with Unlinkability. In Proceedings of the 3rd International Conference on Consumer Electronics, Communications and Networks, Xianning, China, 20–22 November 2013. [Google Scholar]
- Jain, R.T.; Patel, A.A. Computationally Efficient ID-Based Blind Signature Scheme in E-Voting. Int. J. Sci. Res. Dev. 2013, 1. Available online: https://s3.amazonaws.com/academia.edu.documents/33502839/IJSRDV1I3034.pdf?AWSAccessKeyId=AKIAIWOWYYGZ2Y53UL3A&Expires=1539744028&Signature=o5N7XWZ%2BVlfugIaaf%2FESsqJzfCc%3D&response-content-disposition=inline%3B%20filename%3DComputationally_Efficient_ID-Based_Blind.pdf (accessed on 26 September 2018).
- Li, F.; Zhang, M.; Takagi, T. Identity-based partially blind signature in the standard model for electronic cash. Math. Comput. Model. 2013, 58, 196–203. [Google Scholar] [CrossRef]
- Pance, R.; Ljupcho, A. Comparison of ID-Based Blind Signatures from Pairings for E-Voting Protocols. In Proceedings of the 37th International Convention on Information and Communication Technology, Electronics and Microelectronics, Opatija, Croatia, 26–30 May 2014; pp. 26–30. [Google Scholar]
- Girish; Krupa, K.T.; Phaneendra, H.D. Survey on Identity Based Blind Signature. Int. J. Comput. Sci. Inf. Technol. 2015, 6, 2678–2681. [Google Scholar]
- Islam, S.H.; Amin, R.; Biswas, G.P.; Obaidat, M.S.; Khan, M.K. Provably Secure Pairing-Free Identity-Based Partially Blind Signature Scheme and Its Application in Online E-Cash System. Arab. J. Sci. Eng. 2016, 41, 3163–3176. [Google Scholar] [CrossRef]
- Kumar, M.; Katti, C.P.; Saxena, P.C. An Identity-Based Blind Signature Approach for E-Voting System. Int. J. Modern Educ. Comput. Sci. 2017, 10, 47–54. [Google Scholar] [CrossRef]
- Sarde, P.; Banerjee, A. A Secure ID-Based Blind and Proxy Blind Signature Scheme from Bilinear Pairings. J. Appl. Secur. Res. 2017, 12, 2. [Google Scholar] [CrossRef]
- Han, S.; Chang, E. A Pairing-Based Blind Signature Scheme with Message Recovery. Int. J. Inf. Technol. 2007, 1, 2602–2607. [Google Scholar]
- Hassan, E.; Yasmine, A. A New Blind Identity-Based Signature Scheme with Message Recovery. Online J. Electron. Electr. Eng. 2008, 2, 2. [Google Scholar]
- Diao, L.; Gu, J.; Yen, I.L. A New Proxy Blind Signature Scheme with Message Recovery. Inf. Technol. J. 2013, 12, 6159–6163. [Google Scholar]
- James, S.; Gowri, T.; Babu, G.R.; Reddy, P.V. Identity-Based Blind Signature Scheme with Message Recovery. Int. J. Electr. Comput. Eng. 2017, 7, 2674–2682. [Google Scholar]
- Verma, G.K.; Singh, B.B. Efficient identity-based blind message recovery signature scheme from pairings. Inst. Eng. Technol. J. 2018, 12, 150–156. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic curve cryptosystem. J. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Miller, V.S. Use of elliptic curves in cryptography. Proc. Adv. Cryptol. 1985, 218, 417–426. [Google Scholar]
- Pointcheval, D.; Stern, J. Security arguments for digital signatures and blind signatures. J. Cryptol. 2000, 13, 361–396. [Google Scholar] [CrossRef]
- Ren, K.; Lou, W.; Zeng, K.; Moran, P.J. On broadcast authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2007, 6, 4136–4144. [Google Scholar] [CrossRef]
- Cao, X.; Kou, W.; Du, X. A pairing-free identity-based authenticated key agreement protocol with minimal message exchanges. Inf. Sci. 2010, 180, 2895–2903. [Google Scholar] [CrossRef]
- Tan, S.Y.; Heng, S.H.; Goi, B.M. Java Implementation for Pairing-Based Cryptosystems. Proc. Int. Conf. Comput. Sci. Appl. 2010, 6019, 188–198. [Google Scholar]
- Shamus Software Ltd. Miracl Library. Available online: https://www.miracl.com (accessed on 3 October 2018).
- Chung, Y.F.; Huang, K.H.; Lai, F.; Chen, T.S. ID-based digital signature scheme on the elliptic curve cryptosystem. Comput. Stand. Interfaces 2007, 29, 601–604. [Google Scholar] [CrossRef]
- Barreto, P.S.L.M.; Libert, B.; McCullagh, N.; Quisquater, J.J. Efficient and provably secure identity-based signatures and signcryption from bilinear maps. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Chennai, India, 4–8 December 2005; Volume 3788, pp. 515–532. [Google Scholar]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).