An Overview of DRAM-Based Security Primitives
Abstract
:1. Introduction
- We provide a comprehensive overview of literature relevant to DRAM-based security primitives.
- We then classify this literature using a number of criteria, in order to allow for a clear and thorough view into the current state of the art regarding DRAM-based security primitives.
- We also consider, in our taxonomy, their potential applications of such primitives, as well as their security, in order to provide a brief evaluation of them.
- We additionally compare them to other hardware-based security primitives, noting their advantages and disadvantages, and we also examine their potential for commercial adoption, in order to present an assessment of how practical they are as security mechanisms.
- Finally, we discuss the criteria employed in our classification and their significance in assessing the relevant literature regarding DRAM-based implementations as security mechanisms.
2. Preliminary Concepts
2.1. Dynamic Random Access Memories
2.2. DRAM-Based Security Primitives
2.2.1. Physical Unclonable Functions
2.2.2. Random Number Generators
3. Overview of the Current State of the Art Regarding DRAM-Based Security Primitives
3.1. Brief Literature Taxonomy
3.2. Overview of the Literature Regarding DRAM-Based Security Primitives
3.3. Applications of DRAM-Based Security Primitives
3.4. Security Evaluation of DRAM-Based Security Primitives
3.4.1. Attacks and Defences
3.4.2. Evaluation Metrics
4. Discussion
4.1. A Short Comparison of DRAM-Based Security Primitives to Other Hardware-Based Security Primitives
4.2. The Potential of DRAM-Based Security Primitives for Commercial Adoption
4.3. Classification Criteria
- Year of publication, in order to demonstrate the significance of the topic of DRAM-based security primitives and provide insights into the future development of the relevant scientific field.
- DRAM characteristic being exploited for the implementation of a security primitive, in order to demonstrate the diversity of characteristics being used and highlight the number of works about them.
- Security primitive being implemented, in order to demonstrate that works concerning both PUF and TRNG implementations exist and that both primitive types can be generated, with equally good results, using DRAMs.
- Applications used, in order to demonstrate that all DRAM-based primitives can be employed in a wide range of security applications, serving as the basis for the implementation of relevant cryptographic protocols.
- Security considerations, regarding both attacks against the implemented security primitives and countermeasures against such attacks, as well as an overview of the employed security metrics, in order to provide detailed insights into the security of DRAM-based primitives.
- Implementation setup, in order to discuss whether they can be commercially adopted and how practical are the implementations discussed in the relevant literature.
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| 1T1C | one-Transistor one-Capacitor |
| 2T | two-Transistor |
| 3T | three-Transistor |
| ASIC | Application-Specific Integrated Circuit |
| CMOS | Complementary Metal–Oxide–Semiconductor |
| COTS | Commercial Off-The-Shelf |
| DDR | Double-Data-Rate (type one) |
| DDR2 | Double-Data-Rate type two |
| DDR3 | Double-Data-Rate type three |
| DDR4 | Double-Data-Rate type four |
| DIMM | Dual In-line Memory Module |
| DIP | Dual In-line Package |
| DoS | Denial of Service |
| DRAM | Dynamic Random Access Memory |
| ECC | Error Correction Code |
| eDRAM | embedded Dynamic Random Access Memory |
| eFUSE | electrically programmable fuse |
| FPGA | Field-Programmable Gate Array |
| GB | GigaByte |
| IC | Integrated Circuit |
| IT | Information Technology |
| IoT | Internet of Things |
| KB | KiloByte |
| Kbit | Kilobit |
| LPDDR4 | Low Power Double-Data-Rate type 4 |
| LFSR | Linear-Feedback Shift Register |
| MB | MegaByte |
| MDPI | Multidisciplinary Digital Publishing Institute |
| MitM | Man-in-the-Middle |
| NBTI | Negative-Bias Temperature Instability |
| NIST | National Institute of Standards and Technology (USA) |
| OOB | Out-Of-Band |
| OS | Operating System |
| OTP | One-Time Pad |
| PRNG | Pseudo-Random Number Generator |
| PUF | Physical Unclonable Function |
| QKD | Quantum Key Distribution |
| RAM | Random Access Memory |
| RFID | Radio-Frequency IDentification |
| RICID | Retention-based Intrinsic Chip ID |
| SDRAM | Synchronous Dynamic Random Access Memory |
| SODIMM | Small Outline Dual In-line Memory Module |
| SOI | Silicon-On-Insulator |
| SPICE | Simulation Program with Integrated Circuit Emphasis |
| SRAM | Static Random Access Memory |
| TPM | Trusted Platform Module |
| TRNG | True Random Number Generator |
| USA | United States of America |
| VRT | Variable Retention Time |
| VWL | Wordline Low Voltage |
| WSN | Wireless Sensor Network |
| XOR | eXclusive OR |
References
- Landau, S. Making Sense from Snowden: What’s Significant in the NSA Surveillance Revelations. IEEE Secur. Priv. 2013, 11, 54–63. [Google Scholar] [CrossRef]
- Katzenbeisser, S.; Kocabaş, Ü.; Rožić, V.; Sadeghi, A.R.; Verbauwhede, I.; Wachsmann, C. PUFs: Myth, Fact or Busted? A Security Evaluation of Physically Unclonable Functions (PUFs) Cast in Silicon. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin, Germany, 2012; pp. 283–301. [Google Scholar]
- Tehranipoor, F.; Karimian, N.; Yan, W.; Chandy, J.A. DRAM-Based Intrinsic Physically Unclonable Functions for System-Level Security and Authentication. IEEE Trans. Very Large Scale Integr. Syst. 2017, 25, 1085–1097. [Google Scholar] [CrossRef]
- Xiong, W.; Schaller, A.; Anagnostopoulos, N.A.; Saleem, M.U.; Gabmeyer, S.; Katzenbeisser, S.; Szefer, J. Run-Time Accessible DRAM PUFs in Commodity Devices. In International Conference on Cryptographic Hardware and Embedded Systems; Springer: Berlin, Germany, 2016; pp. 432–453. [Google Scholar]
- Schaller, A.; Xiong, W.; Anagnostopoulos, N.A.; Saleem, M.U.; Gabmeyer, S.; Katzenbeisser, S.; Szefer, J. Intrinsic Rowhammer PUFs: Leveraging the Rowhammer Effect for Improved Security. In Proceedings of the 2017 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, VA, USA, 1–5 May 2017; pp. 1–7. [Google Scholar]
- Prabhu, P.; Akel, A.; Grupp, L.M.; Wing-Kei, S.Y.; Suh, G.E.; Kan, E.; Swanson, S. Extracting Device Fingerprints from Flash Memory by Exploiting Physical Variations. In International Conference on Trust and Trustworthy Computing; Springer: Berlin, Germany, 2011; pp. 188–201. [Google Scholar]
- Tehranipoor, F.; Karimian, N.; Wortman, P.A.; Haque, A.; Fahrny, J.; Chandy, J.A. Exploring Methods of Authentication for the Internet of Things. In Internet of Things: Challenges, Advances, and Applications; Hassan, Q.F., Khan, A.R., Madani, S.A., Eds.; CRC Press: Boca Raton, FL, USA, 2017. [Google Scholar]
- Liu, J.; Jaiyen, B.; Kim, Y.; Wilkerson, C.; Mutlu, O. An Experimental Study of Data Retention Behavior in Modern DRAM Devices: Implications for Retention Time Profiling Mechanisms. In ACM SIGARCH Computer Architecture News; ACM: New York, NY, USA, 2013; Volume 41, pp. 60–71. [Google Scholar]
- Keeth, B.; Baker, R.J.; Johnson, B.; Lin, F. DRAM Circuit Design: Fundamental and High-Speed Topics, 2nd ed.; Wiley-IEEE Press: Piscataway, NJ, USA, 2007. [Google Scholar]
- Chun, K.C.; Jain, P.; Kim, T.H.; Kim, C.H. A 667 MHz Logic-Compatible Embedded DRAM Featuring an Asymmetric 2T Gain Cell for High Speed On-Die Caches. IEEE J. Solid State Circuits 2012, 47, 547–559. [Google Scholar] [CrossRef]
- Tang, Q.; Zhou, C.; Choi, W.; Kang, G.; Park, J.; Parhi, K.K.; Kim, C.H. A DRAM Based Physical Unclonable Function Capable of Generating >1032 Challenge Response Pairs per 1Kbit Array for Secure Chip Authentication. In Proceedings of the 2017 IEEE Custom Integrated Circuits Conference (CICC), Austin, TX, USA, 30 April–3 May 2017. [Google Scholar]
- Tehranipoor, F.; Karimian, N.; Xiao, K.; Chandy, J. DRAM Based Intrinsic Physical Unclonable Functions for System Level Security. In Proceedings of the Great Lakes Symposium on VLSI, Pittsburgh, PA, USA, 20–22 May 2015; pp. 15–20. [Google Scholar]
- Okamura, T.; Minematsu, K.; Tsunoo, Y.; Iida, T.; Kimura, T.; Nakamura, K. DRAM PUF (in Japanese). In Proceedings of the 29th Symposium on Cryptography and Information Security (SCIS 2012); Institute of Electronics, Information and Communication Engineers: Tokyo, Japan, 2012. [Google Scholar]
- Keller, C.; Felber, N.; Gürkaynak, F.; Kaeslin, H.; Junod, P. Physically Unclonable Functions for Secure Hardware (poster); RTD 2010—QCrypt; Swiss National Science Foundation (SNSF): Bern, Switzerland; Nano-Tera.CH: Lausanne, Switzerland, 2012. [Google Scholar]
- Felber, N. for Gisin, N. Secure High-Speed Communication Based on Quantum Key Distribution (presentation slides); RTD 2010—QCrypt, Annual Plenary Meeting; Swiss National Science Foundation (SNSF): Bern, Switzerland; Nano-Tera.CH: Lausanne, Switzerland, 2012. [Google Scholar]
- Keller, C.; Gürkaynak, F.; Kaeslin, H.; Felber, N. Dynamic Memory-Based Physically Unclonable Function for the Generation of Unique Identifiers and True Random Numbers. In Proceedings of the 2014 IEEE International Symposium on Circuits and Systems (ISCAS), Melbourne, VIC, Australia, 1–5 June 2014; pp. 2740–2743. [Google Scholar]
- Tehranipoor, F.; Yan, W.; Chandy, J.A. Robust Hardware True Random Number Generators using DRAM Remanence Effects. In Proceedings of the 2016 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, VA, USA, 3–5 May 2016; pp. 79–84. [Google Scholar]
- Fainstein, D.; Rosenblatt, S.; Cestero, A.; Robson, N.; Kirihata, T.; Iyer, S.S. Dynamic Intrinsic Chip ID Using 32nm High-K/Metal Gate SOI Embedded DRAM. In Proceedings of the 2012 Symposium on VLSI Circuits (VLSIC), Honolulu, HI, USA, 13–15 June 2012; pp. 146–147. [Google Scholar]
- Sutar, S.; Raha, A.; Kulkarni, D.; Shorey, R.; Tew, J.; Raghunathan, V. D-PUF: An Intrinsically Reconfigurable DRAM PUF for Device Authentication and Random Number Generation. ACM Trans. Embed. Comput. Syst. 2018, 17. [Google Scholar] [CrossRef]
- Hashemian, M.S.; Singh, B.; Wolff, F.; Weyer, D.; Clay, S.; Papachristou, C. A Robust Authentication Methodology Using Physically Unclonable Functions in DRAM Arrays. In Proceedings of the Design, Automation & Test in Europe Conference, Grenoble, France, 9–13 March 2015; pp. 647–652. [Google Scholar]
- Kim, J.S.; Patel, M.; Hassan, H.; Mutlu, O. The DRAM Latency PUF: Quickly Evaluating Physical Unclonable Functions by Exploiting the Latency-Reliability Tradeoff in Modern DRAM Devices. In Proceedings of the 24th International Symposium on High-Performance Computer Architecture (HPCA), Vienna, Austria, 24–28 February 2018. [Google Scholar]
- Bauder, D.W. An Anti-Counterfeiting Concept for Currency Systems; Technical Report PTK-11990; Sandia National Labs: Albuquerque, NM, USA, 1983.
- Simmons, G.J. A System for Verifying User Identity and Authorization at the Point-of Sale or Access. Cryptologia 1984, 8, 1–21. [Google Scholar] [CrossRef]
- Simmons, G.J. Identification of Data, Devices, Documents and Individuals. In Proceedings of the 25th Annual IEEE International Carnahan Conference on Security Technology, Taipei, Taiwan, 1–3 October 1991; pp. 197–218. [Google Scholar]
- Pappu, R.S. Physical One-Way Functions. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 2001. [Google Scholar]
- Pappu, R.; Recht, B.; Taylor, J.; Gershenfeld, N. Physical One-Way Functions. Science 2002, 297, 2026–2030. [Google Scholar] [CrossRef]
- Gassend, B.; Clarke, D.; van Dijk, M.; Devadas, S. Silicon Physical Random Functions. In Proceedings of the 9th ACM Conference on Computer and Communications Security; ACM: New York, NY, USA, 2002; pp. 148–160. [Google Scholar]
- Gassend, B.L.P. Physical Random Functions. Master’s Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 2003. [Google Scholar]
- Guajardo, J.; Kumar, S.S.; Schrijen, G.J.; Tuyls, P. FPGA Intrinsic PUFs and their Use for IP Protection. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin, Germany, 2007; pp. 63–80. [Google Scholar]
- Holcomb, D.E.; Burleson, W.P.; Fu, K. Initial SRAM State as a Fingerprint and Source of True Random Numbers for RFID Tags. In Proceedings of the Conference on RFID Security, Malaga, Spain, 11–13 July 2007. [Google Scholar]
- Yan, W.; Jin, C.; Tehranipoor, F.; Chandy, J.A. Phase Calibrated Ring Oscillator PUF Design and Implementation on FPGAs. In Proceedings of the 27th International Conference on Field Programmable Logic and Applications (FPL 2017), Ghent, East Flanders, Belgium, 4–8 September 2017. [Google Scholar]
- Herder, C.; Yu, M.D.; Koushanfar, F.; Devadas, S. Physical Unclonable Functions and Applications: A Tutorial. Proc. IEEE 2014, 102, 1126–1141. [Google Scholar] [CrossRef]
- Lee, J.W.; Lim, D.; Gassend, B.; Suh, G.E.; van Dijk, M.; Devadas, S. A Technique to Build a Secret Key in Integrated Circuits for Identification and Authentication Applications. In Proceedings of the 2004 Symposium on VLSI Circuits, Digest of Technical Papers, Honolulu, HI, USA, 17–19 June 2004; pp. 176–179. [Google Scholar]
- Majzoobi, M.; Koushanfar, F.; Potkonjak, M. Testing Techniques for Hardware Security. In Proceedings of the 2008 IEEE International Test Conference, Santa Clara, CA, USA, 28–30 October 2008. [Google Scholar]
- Rührmair, U.; Sehnke, F.; Sölter, J.; Dror, G.; Devadas, S.; Schmidhuber, J. Modeling Attacks on Physical Unclonable Functions. In Proceedings of the 17th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 4–8 October 2010; pp. 237–249. [Google Scholar]
- Rührmair, U.; Sölter, J.; Sehnke, F.; Xu, X.; Mahmoud, A.; Stoyanova, V.; Dror, G.; Schmidhuber, J.; Burleson, W.; Devadas, S. PUF Modeling Attacks on Simulated and Silicon Data. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1876–1891. [Google Scholar] [CrossRef] [Green Version]
- Tuyls, P.; Schrijen, G.J.; Škorić, B.; Van Geloven, J.; Verhaegh, N.; Wolters, R. Read-Proof Hardware from Protective Coatings. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin, Germany, 2006; pp. 369–383. [Google Scholar]
- Suh, G.E.; Devadas, S. Physical Unclonable Functions for Device Authentication and Secret Key Generation. In Proceedings of the 44th Annual Design Automation Conference, San Diego, CA, USA, 4–8 June 2007; pp. 9–14. [Google Scholar]
- Su, Y.; Holleman, J.; Otis, B. A 1.6 pJ/bit 96% Stable Chip-ID Generating Circuit Using Process Variations. In Proceedings of the Digest of Technical Papers of the 2007 IEEE International Solid-State Circuits Conference (ISSCC 2007), San Francisco, CA, USA, 11–15 February 2007; pp. 406–611. [Google Scholar]
- Majzoobi, M.; Koushanfar, F.; Potkonjak, M. Lightweight Secure PUFs. In Proceedings of the 2008 IEEE/ACM International Conference on Computer-Aided Design, San Jose, CA, USA, 10–13 November 2008; pp. 670–673. [Google Scholar]
- Kumar, S.S.; Guajardo, J.; Maes, R.; Schrijen, G.J.; Tuyls, P. The Butterfly PUF Protecting IP on Every FPGA. In Proceedings of the 2008 IEEE International Workshop on Hardware-Oriented Security and Trust (HOST 2008), Anaheim, CA, USA, 9 June 2008; pp. 67–70. [Google Scholar]
- Maes, R.; Tuyls, P.; Verbauwhede, I. Intrinsic PUFs from Flip-Flops on Reconfigurable Devices. In Proceedings of the 3rd Benelux Workshop on Information and System Security (WISSec 2008), Eindhoven, The Netherlands, 13–14 November 2008; Volume 17. [Google Scholar]
- Suzuki, D.; Shimizu, K. The Glitch PUF: A New Delay-PUF Architecture Exploiting Glitch Shapes. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin, Germany, 2010; pp. 366–382. [Google Scholar]
- Majzoobi, M.; Ghiaasi, G.; Koushanfar, F.; Nassif, S.R. Ultra-Low Power Current-Based PUF. In Proceedings of the 2011 IEEE International Symposium on Circuits and Systems (ISCAS), Rio de Janeiro Brazil, 15–18 May 2011; pp. 2071–2074. [Google Scholar]
- Chen, Q.; Csaba, G.; Lugli, P.; Schlichtmann, U.; Rührmair, U. The Bistable Ring Puf: A New Architecture for Strong Physical Unclonable Functions. In Proceedings of the 2011 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), San Diego, CA, USA, 5–6 June 2011; pp. 134–141. [Google Scholar]
- Simons, P.; van der Sluis, E.; van der Leest, V. Buskeeper PUFs, a Promising Alternative to D Flip-Flop PUFs. In Proceedings of the 2012 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), San Francisco, CA, USA, 3–4 June 2012; pp. 7–12. [Google Scholar]
- Holcomb, D.E.; Fu, K. Bitline PUF: Building Native Challenge-Response PUF Capability into Any SRAM. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin, Germany, 2014; pp. 510–526. [Google Scholar]
- Bossuet, L.; Ngo, X.T.; Cherif, Z.; Fischer, V. A PUF Based on a Transient Effect Ring Oscillator and Insensitive to Locking Phenomenon. IEEE Trans. Emerg. Top. Comput. 2014, 2, 30–36. [Google Scholar] [CrossRef] [Green Version]
- Willers, O.; Huth, C.; Guajardo, J.; Seidel, H. MEMS Gyroscopes as Physical Unclonable Functions. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 591–602. [Google Scholar]
- Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E.; Leigh, S.; Levenson, M.; Vangel, M.; Banks, D.; Heckert, A.; et al. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; Special Publication 800:22; National Institute of Standards and Technology: Gaithersburg, MD, USA,, 2010.
- Chan, J.J.M.; Sharma, B.; Lv, J.; Thomas, G.; Thulasiram, R.; Thulasiraman, P. True Random Number Generator Using GPUs and Histogram Equalization Techniques. In Proceedings of the 13th IEEE International Conference on High Performance Computing and Communications (HPCC 2011), Banff, AB, Canada, 2–4 September 2011; pp. 161–170. [Google Scholar]
- Tehranipoor, F.; Karimian, N.; Yan, W.; Chandy, J.A. A Study of Power Supply Variation as a Source of Random Noise. In Proceedings of the 30th International Conference on VLSI Design and 16th International Conference on Embedded Systems (VLSID 2017), Hyderabad, India, 7–11 January 2017; pp. 155–160. [Google Scholar]
- Tehranipoor, F.; Wortman, P.; Karimian, N.; Yan, W.; Chandy, J. DVFT: A Lightweight Solution for Power Supply Noise Based TRNG Using a Dynamic Voltage Feedback Tuning System. IEEE Trans. Very Large Scale Integr. Syst. 2018. [Google Scholar] [CrossRef]
- Tehranipoor, F. Design and Architecture of Hardware-Based Random Function Security Primitives. Ph.D. Thesis, University of Connecticut (UConn), Storrs, CT, USA, 2017. [Google Scholar]
- Eckert, C.; Tehranipoor, F.; Chandy, J.A. DRNG: DRAM-Based Random Number Generation Using its Startup Value Behavior. In Proceedings of the 60th IEEE International Midwest Symposium on Circuits and Systems (MWSCAS), Boston, MA, USA, 6–9 August 2017. [Google Scholar]
- Komninos, N.; Philippou, E.; Pitsillides, A. Survey in Smart Grid and Smart Home Security: Issues, Challenges and Countermeasures. IEEE Commun. Surv. Tutor. 2014, 16, 1933–1954. [Google Scholar] [CrossRef]
- Mahmud, R.; Vallakati, R.; Mukherjee, A.; Ranganathan, P.; Nejadpak, A. A Survey on Smart Grid Metering Infrastructures: Threats and Solutions. In Proceedings of the 2015 IEEE International Conference on Electro/Information Technology (EIT), Dekalb, IL, USA, 21–23 May 2015; pp. 386–391. [Google Scholar]
- Karygiannis, A.; Phillips, T.; Tsibertzopoulos, A. RFID Security: A Taxonomy of Risk. In Proceedings of the First International Conference on Communications and Networking in China (ChinaCom 2006), Beijing, China, 25–27 October 2006. [Google Scholar]
- Mitrokotsa, A.; Rieback, M.; Tanenbaum, A. Classification of RFID Attacks. In Proceedings of the 2nd International Workshop on RFID Technology – Concepts Concepts, Applications, Challenges (IWRT 2008), Barcelona, Spain, June 2008; pp. 73–86. [Google Scholar]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A Survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Da Xu, L.; He, W.; Li, S. Internet of Things in Industries: A Survey. IEEE Trans. Ind. Inf. 2014, 10, 2233–2243. [Google Scholar]
- Perera, C.; Zaslavsky, A.; Christen, P.; Georgakopoulos, D. Context Aware Computing for the Internet of Things: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 414–454. [Google Scholar] [CrossRef]
- Chang, C.H.; Zheng, Y.; Zhang, L. A Retrospective and a Look Forward: Fifteen Years of Physical Unclonable Function Advancement. IEEE Circuits Syst. Mag. 2017, 17, 32–62. [Google Scholar] [CrossRef]
- Maes, R. Physically Unclonable Functions: Constructions, Properties and Applications, 1st ed.; Springer: Berlin, Germany, 2013. [Google Scholar]
- Maes, R.; Verbauwhede, I. Physically Unclonable Functions: A Study on the State of the Art and Future Research Directions. In Towards Hardware-Intrinsic Security; Springer: Berlin, Germany, 2010; pp. 3–37. [Google Scholar]
- Rostami, M.; Wendt, J.B.; Potkonjak, M.; Koushanfar, F. Quo Vadis, PUF?: Trends and Challenges of Emerging Physical-Disorder Based Security. In Proceedings of the Conference on Design, Automation & Test in Europe, Dresden, Germany, 24–28 March 2014. [Google Scholar]
- Rührmair, U.; Holcomb, D.E. PUFs at a Glance. In Proceedings of the Conference on Design, Automation & Test in Europe, Dresden, Germany, 24–28 March 2014. [Google Scholar]
- Böhm, C.; Hofer, M. Physical Unclonable Functions in Theory and Practice; Springer Science & Business Media: New York, NY, USA, 2012. [Google Scholar]
- Busch, H.; Sotáková, M.; Katzenbeisser, S.; Sion, R. The PUF Promise. In International Conference on Trust and Trustworthy Computing; Springer: Berlin, Germany, 2010; pp. 290–297. [Google Scholar]
- Eiroa, S.; Baturone, I.; Acosta, A.J.; Dávila, J. Using Physical Unclonable Functions for Hardware Authentication: A Survey. In Proceedings of the XXV Conference on Design of Circuits and Integrated Systems (DCIS), Lanzarote, Las Palmas, Canary Islands, Spain, 12–14 November 2010. [Google Scholar]
- Tehranipoor, M.; Koushanfar, F. A Survey of Hardware Trojan Taxonomy and Detection. IEEE Des. Test Comput. 2010, 27, 10–25. [Google Scholar] [CrossRef]
- Karri, R.; Rajendran, J.; Rosenfeld, K. Trojan Taxonomy. In Introduction to Hardware Security and Trust; Springer: Berlin, Germany, 2012; pp. 325–338. [Google Scholar]
- Karri, R.; Rajendran, J.; Rosenfeld, K.; Tehranipoor, M. Trustworthy Hardware: Identifying and Classifying Hardware Trojans. Computer 2010, 43, 39–46. [Google Scholar] [CrossRef]
- Schaller, A. Lightweight Protocols and Applications for Memory-Based Intrinsic Physically Unclonable Functions Found on Commercial Off-The-Shelf Devices. Ph.D. Thesis, Technische Universität Darmstadt, Darmstadt, Germany, 2017. [Google Scholar]
- Ravishankar, Y. PUFs – An Extensive Survey. Ph.D. Thesis, George Mason University, Fairfax, VA, USA, 2017. [Google Scholar]
- Sahoo, D.P. Design and Analysis of Secure Physically Unclonable Function Compositions. Ph.D. Thesis, Indian Institute of Technology Kharagpur (IIT KGP), Kharagpur, West Bengal, India, 2017. [Google Scholar]
- Bитенко, A. Использование DRAM-PUF для Идентификации Мобильных Устройств под Управлением ОС Android (in Russian). Апробация 2016, 1, 26–29. [Google Scholar]
- Пучков, A.B.; ИванюкА, A.A. Применение Запоминающих Устройств в качестве Криптографических Примитивов для Интегральных Схем Программируемой Логики (in Russian). Proceeding of the 2016 International Conference on Information Technologies and Systems (ITS 2016) – Информационные технологии и системы 2016 (ИТС 2016), Minsk, Belarus, 26 October 2016; pp. 210–211. [Google Scholar]
- Rosenblatt, S.; Fainstein, D.; Cestero, A.; Safran, J.; Robson, N.; Kirihata, T.; Iyer, S.S. Field Tolerant Dynamic Intrinsic Chip ID Using 32 nm High-K/Metal Gate SOI Embedded DRAM. IEEE J. Solid-State Circuits 2013, 48, 940–947. [Google Scholar] [CrossRef]
- Rosenblatt, S.; Chellappa, S.; Cestero, A.; Robson, N.; Kirihata, T.; Iyer, S.S. A Self-Authenticating Chip Architecture Using an Intrinsic Fingerprint of Embedded DRAM. IEEE J. Solid-State Circuits 2013, 48, 2934–2943. [Google Scholar] [CrossRef]
- Liu, W.; Zhang, Z.; Li, M.; Liu, Z. A Trustworthy Key Generation Prototype Based on DDR3 PUF for Wireless Sensor Networks. Sensors 2014, 14, 11542–11556. [Google Scholar] [CrossRef] [PubMed]
- Liu, W.; Zhang, Z.; Li, M.; Liu, Z. A Trustworthy Key Generation Prototype Based on DDR3 PUF for Wireless Sensor Networks. In Proceedings of the 2014 International Symposium on Computer, Consumer and Control (IS3C), Taichung, Taiwan, 10–12 June 2014; pp. 706–709. [Google Scholar]
- Zhang, Z. Design and Implementation of DRAM PUF (in Chinese). Master’s Thesis, Huazhong University of Science and Technology, Wuhan, China, 2015. [Google Scholar]
- Rahmati, A.; Hicks, M.; Holcomb, D.E.; Fu, K. Probable Cause: The Deanonymizing Effects of Approximate DRAM. In Proceedings of the 2015 ACM/IEEE 42nd Annual International Symposium on Computer Architecture (ISCA), Portland, Oregon, 13–17 June 2015; pp. 604–615. [Google Scholar]
- Sutar, S.; Raha, A.; Raghunathan, V. D-PUF: An Intrinsically Reconfigurable DRAM PUF for Device Authentication in Embedded Systems. In Proceedings of the 2016 International Conference on Compilers, Architectures, and Sythesis of Embedded Systems (CASES), Pittsburgh, PA, USA, 2–7 October 2016. [Google Scholar]
- Sutar, S.; Raha, A.; Raghunathan, V. Memory-Based Combination PUFs for Device Authentication in Embedded Systems. arXiv, 2017; arXiv:1712.01611. [Google Scholar]
- Tehranipoor, F.; Karimian, N.; Yan, W.; Chandy, J.A. Investigation of DRAM PUFs Reliability Under Device Accelerated Aging Effects. In Proceedings of the 2017 IEEE International Symposium on Circuits and Systems (ISCAS), Baltimore, MD, USA, 28–31 May 2017. [Google Scholar]
- Kumar, R.; Xu, X.; Burleson, W.; Rosenblatt, S.; Kirihata, T. Physically Unclonable Functions: A Window into CMOS Process Variations. In Circuits and Systems for Security and Privacy; Sheikh, F., Sousa, L., Iniewski, K., Eds.; CRC Press: Boca Raton, FL, USA, 2017. [Google Scholar]
- Kirihata, T.; Rosenblatt, S. Dynamic Intrinsic Chip ID for Hardware Security. In VLSI: Circuits for Emerging Applications; Wojcicki, T., Iniewski, K., Eds.; CRC Press: Boca Raton, FL, USA, 2017. [Google Scholar]
- Raha, A.; Jayakumar, H.; Sutar, S.; Raghunathan, V. Quality-Aware Data Allocation in Approximate DRAM. In Proceedings of the 2015 International Conference on Compilers, Architecture and Synthesis for Embedded Systems, Amsterdam, The Netherlands, 4–9 October 2015; pp. 89–98. [Google Scholar]
- Raha, A.; Sutar, S.; Jayakumar, H.; Raghunathan, V. Quality Configurable Approximate DRAM. IEEE Trans. Comput. 2017, 66, 1172–1187. [Google Scholar] [CrossRef]
- Anagnostopoulos, N.A.; Schaller, A.; Fan, Y.; Xiong, W.; Tehranipoor, F.; Arul, T.; Gabmeyer, S.; Szefer, J.; Chandy, J.A.; Katzenbeisser, S. Insights into the Potential Usage of the Initial Values of DRAM Arrays of Commercial Off-The-Shelf Devices for Security Applications. In Proceedings of the 26th Crypto-Day, Nuremberg, Germany, 1–2 June 2017. [Google Scholar]
- Yan, W.; Tehranipoor, F.; Chandy, J.A. PUF-Based Fuzzy Authentication Without Error Correcting Codes. IEEE Trans. Comput.-Aided Design Integr. Circuits Syst. (CAD) 2017, 36, 1445–1457. [Google Scholar] [CrossRef]
- Yan, W.; Tehranipoor, F.; Chandy, J.A. A Novel Way to Authenticate Untrusted Integrated Circuits. In Proceedings of the 2015 IEEE/ACM International Conference on Computer-Aided Design (ICCAD 2015), Austin, TX, USA, 2–6 November 2015; pp. 132–138. [Google Scholar]
- Maes, R.; Tuyls, P.; Verbauwhede, I. A Soft Decision Helper Data Algorithm for SRAM PUFs. In Proceedings of the 2009 IEEE International Symposium on Information Theory (ISIT 2009), Seoul, South Korea, 28 June–3 July 2009; pp. 2101–2105. [Google Scholar]
- Anagnostopoulos, N.A. Optical Fault Injection Attacks in Smart Card Chips and an Evaluation of Countermeasures Against Them. Master’s Thesis, University of Twente, Enschede, The Netherlands, 2014. [Google Scholar]
- Karimian, N.; Wortman, P.A.; Tehranipoor, F. Evolving Authentication Design Considerations for the Internet of Biometric Things (IoBT). In Proceedings of the 2016 International Conference on Hardware/Software Codesign and System Synthesis (CODES+ISSS 2016), Pittsburgh, PA, USA, 2–7 October 2016; pp. 1–10. [Google Scholar]
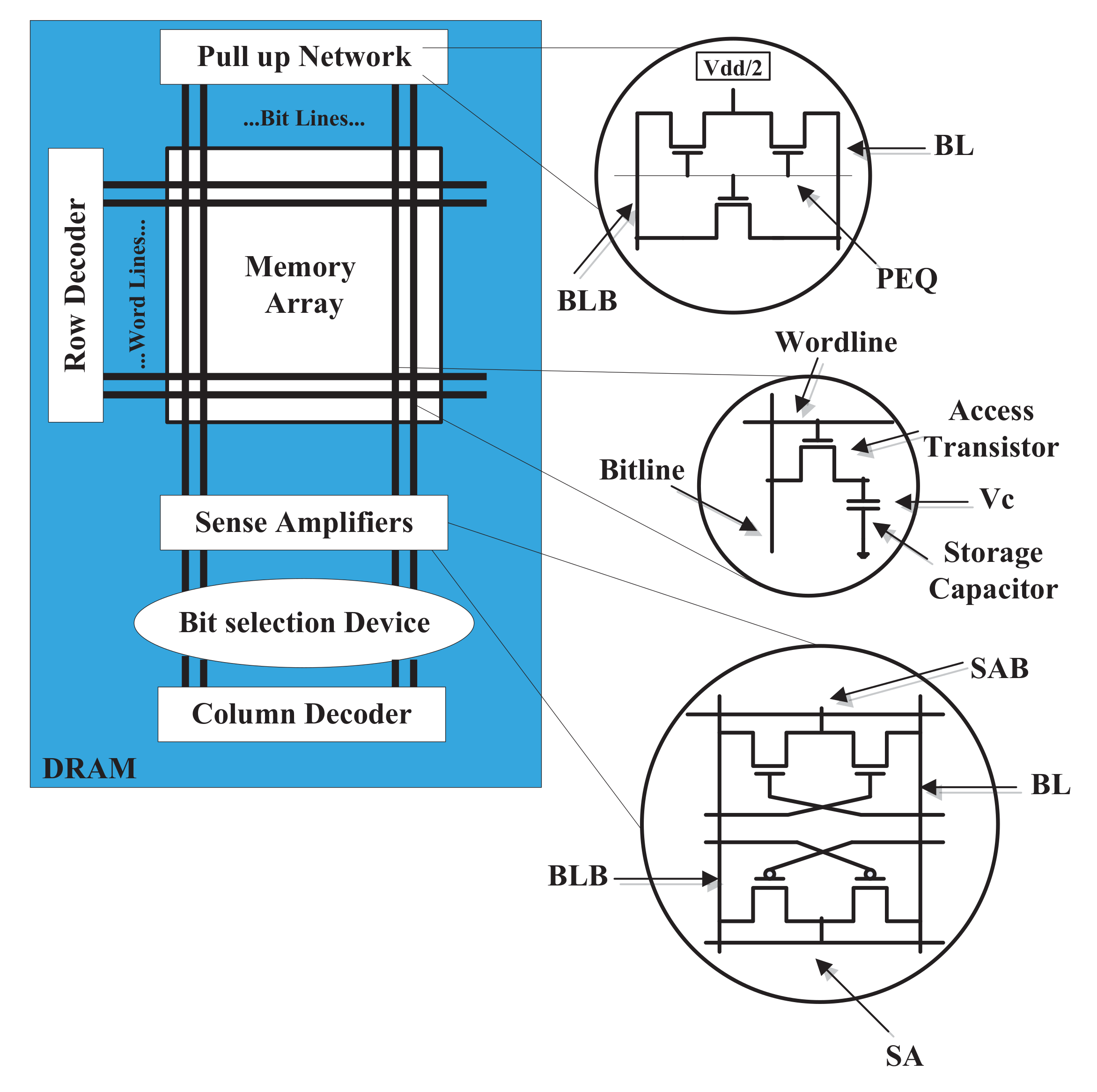
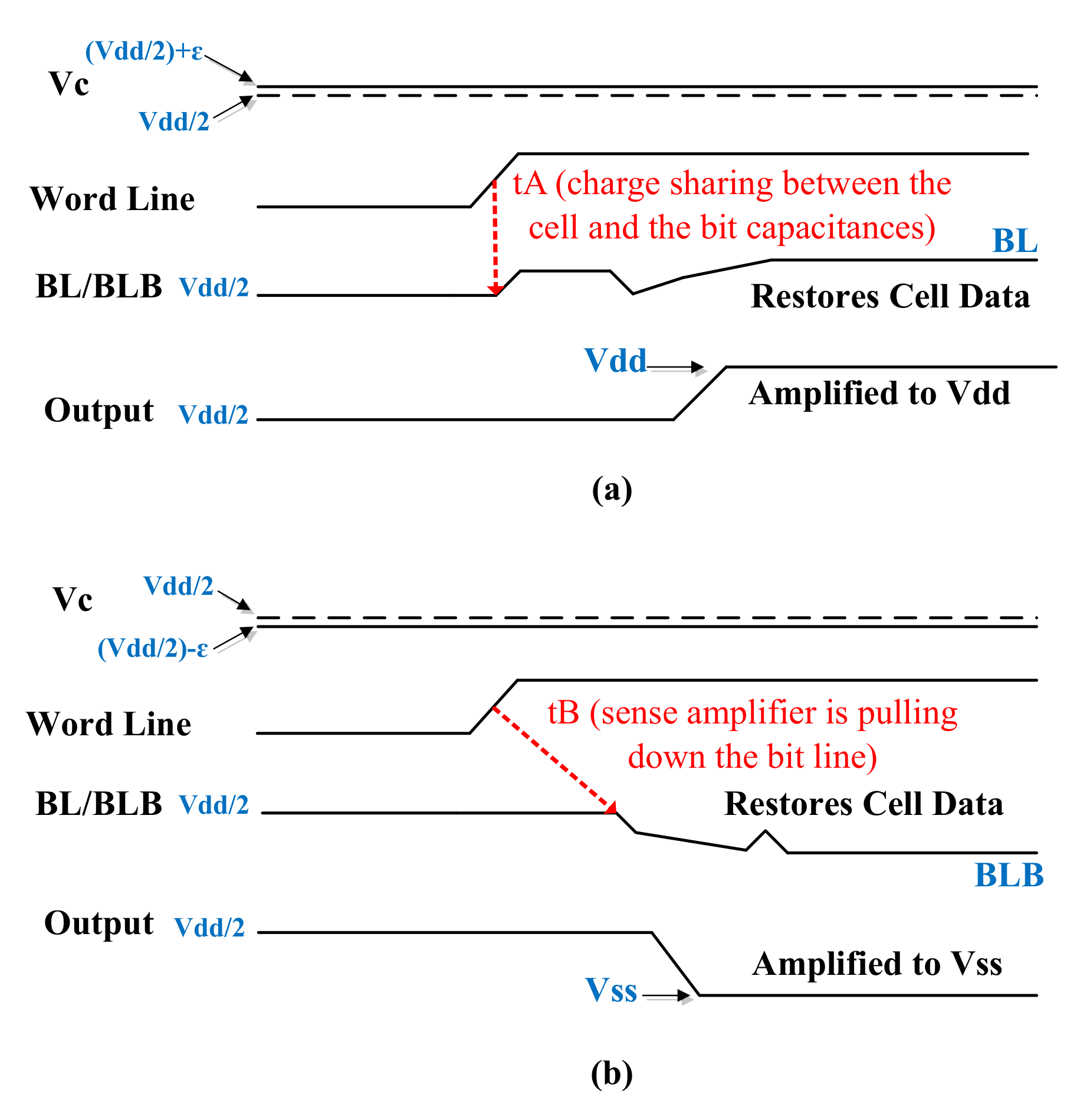
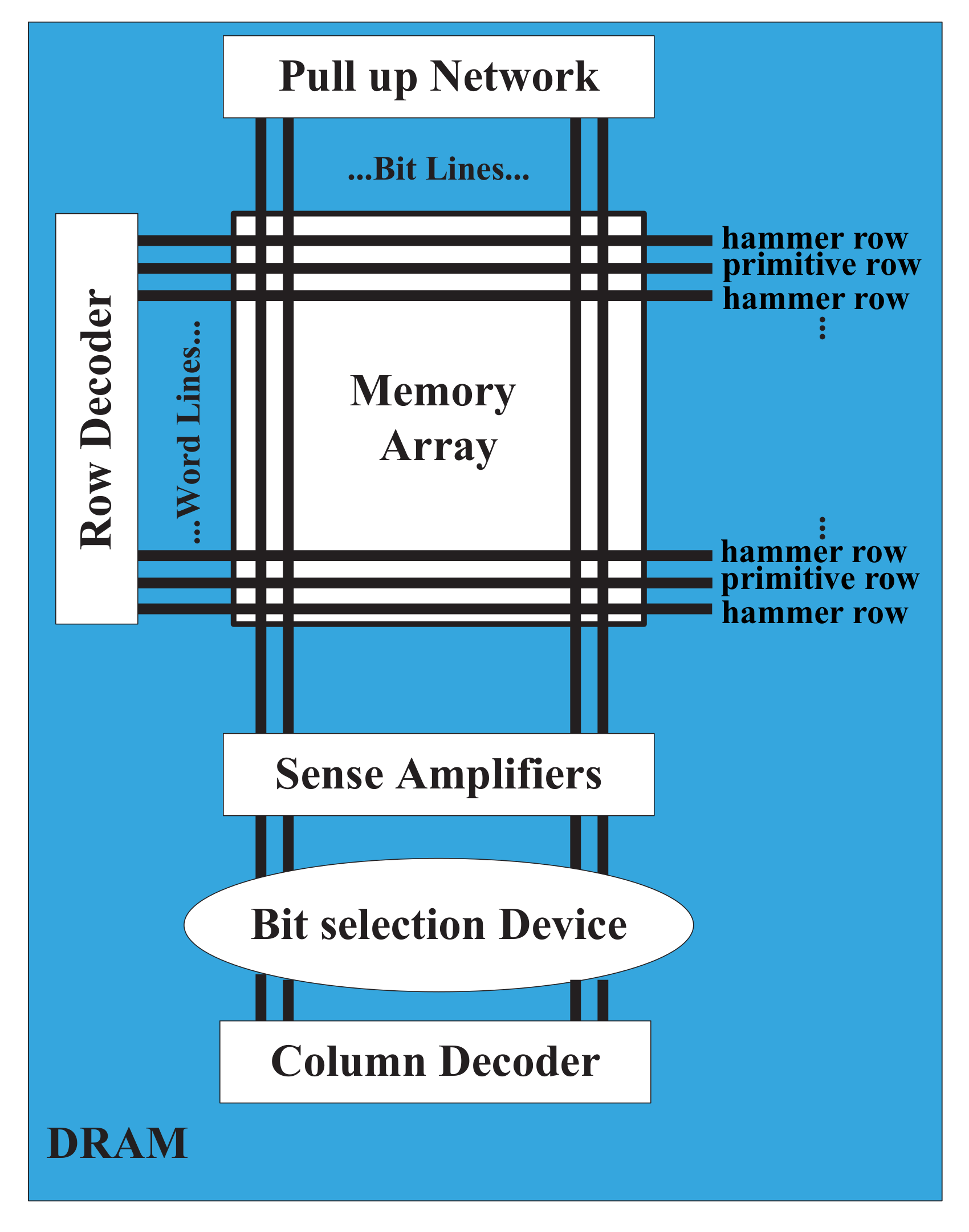
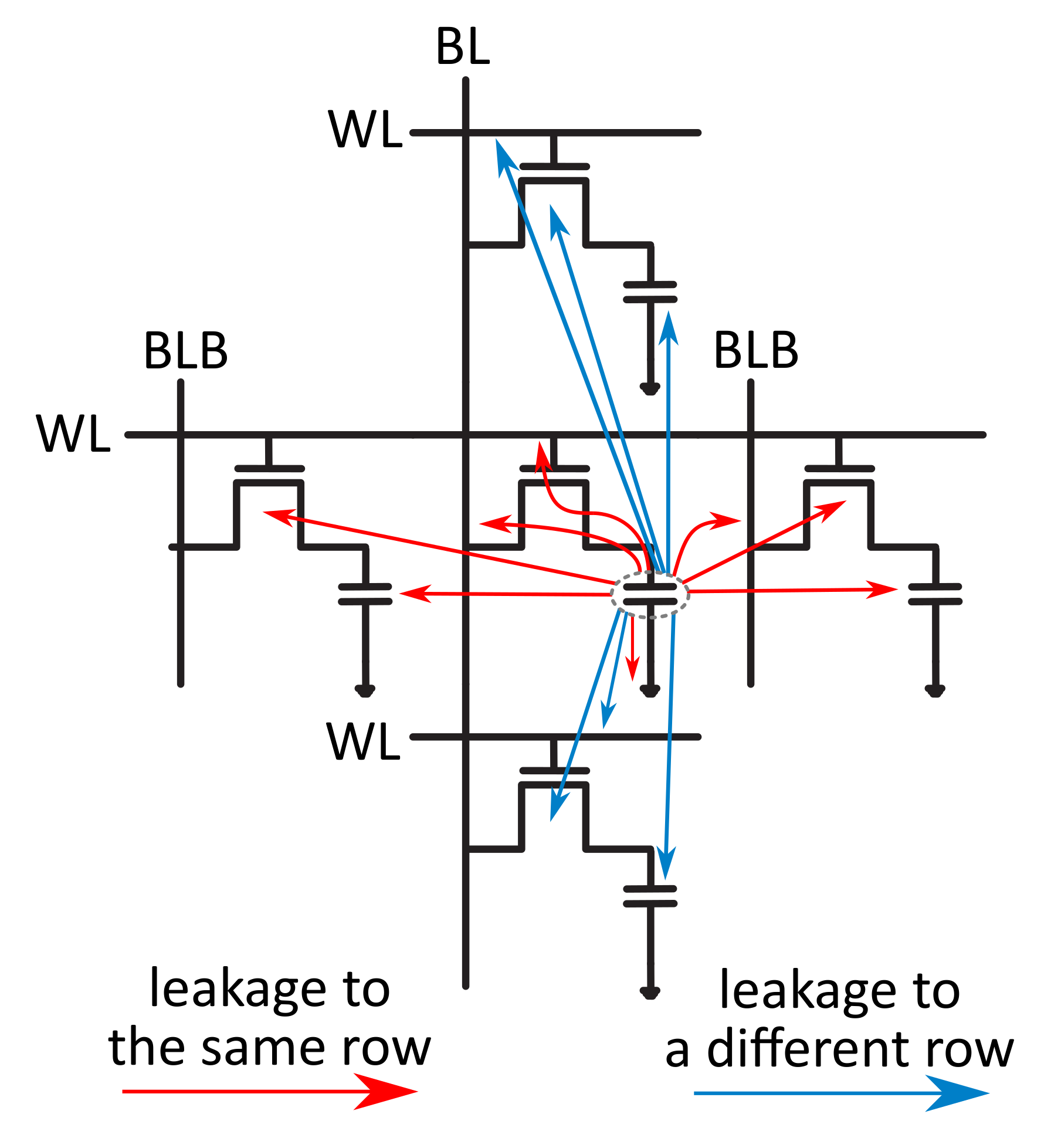
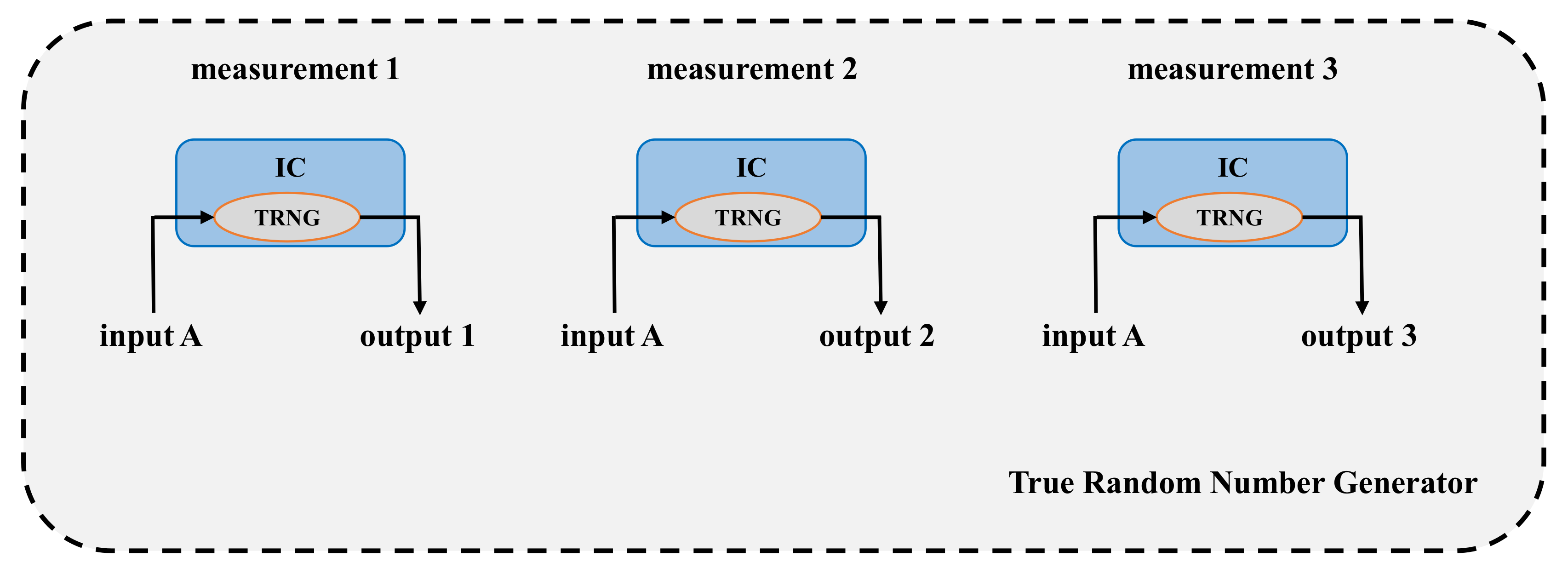
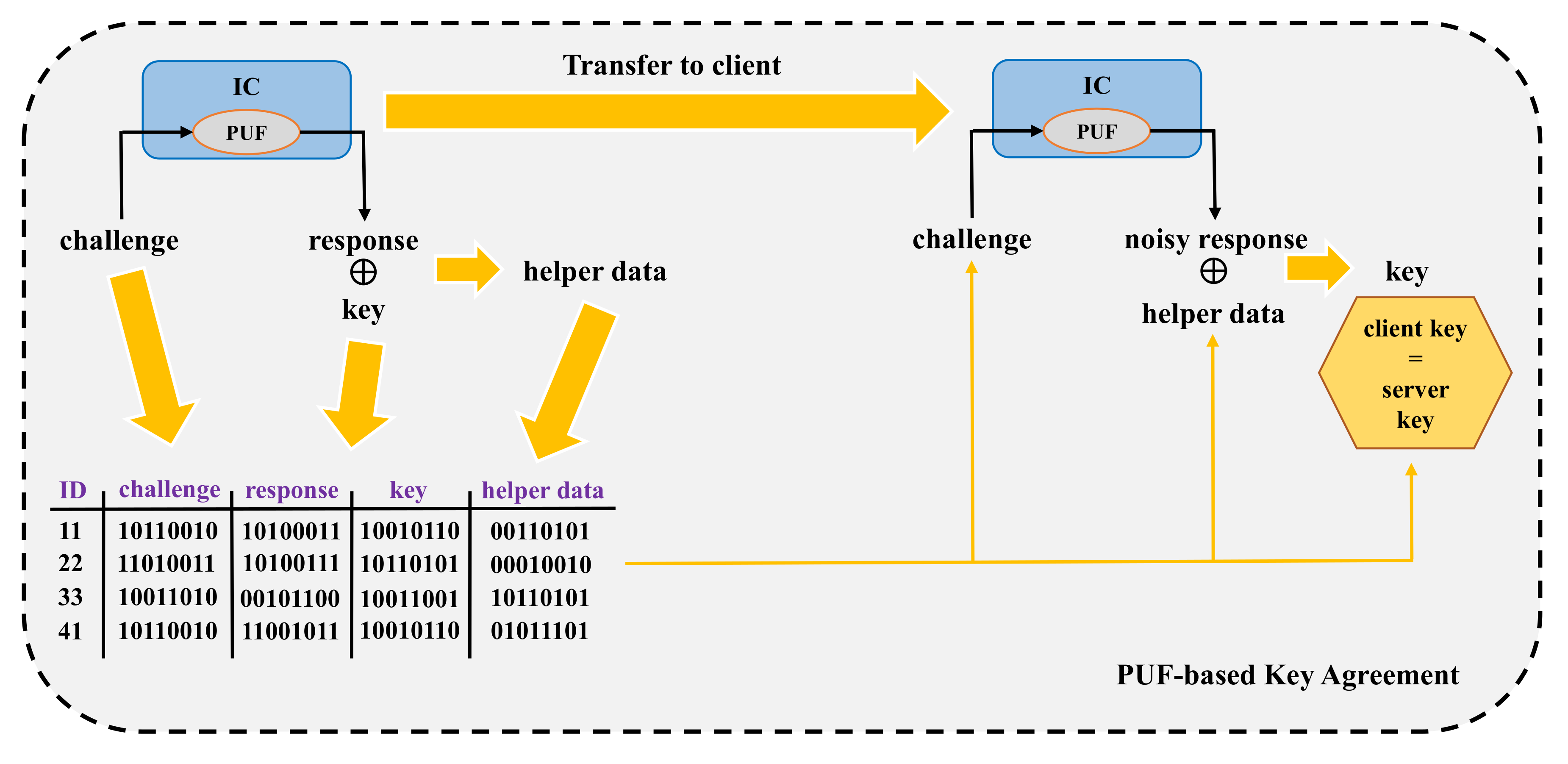
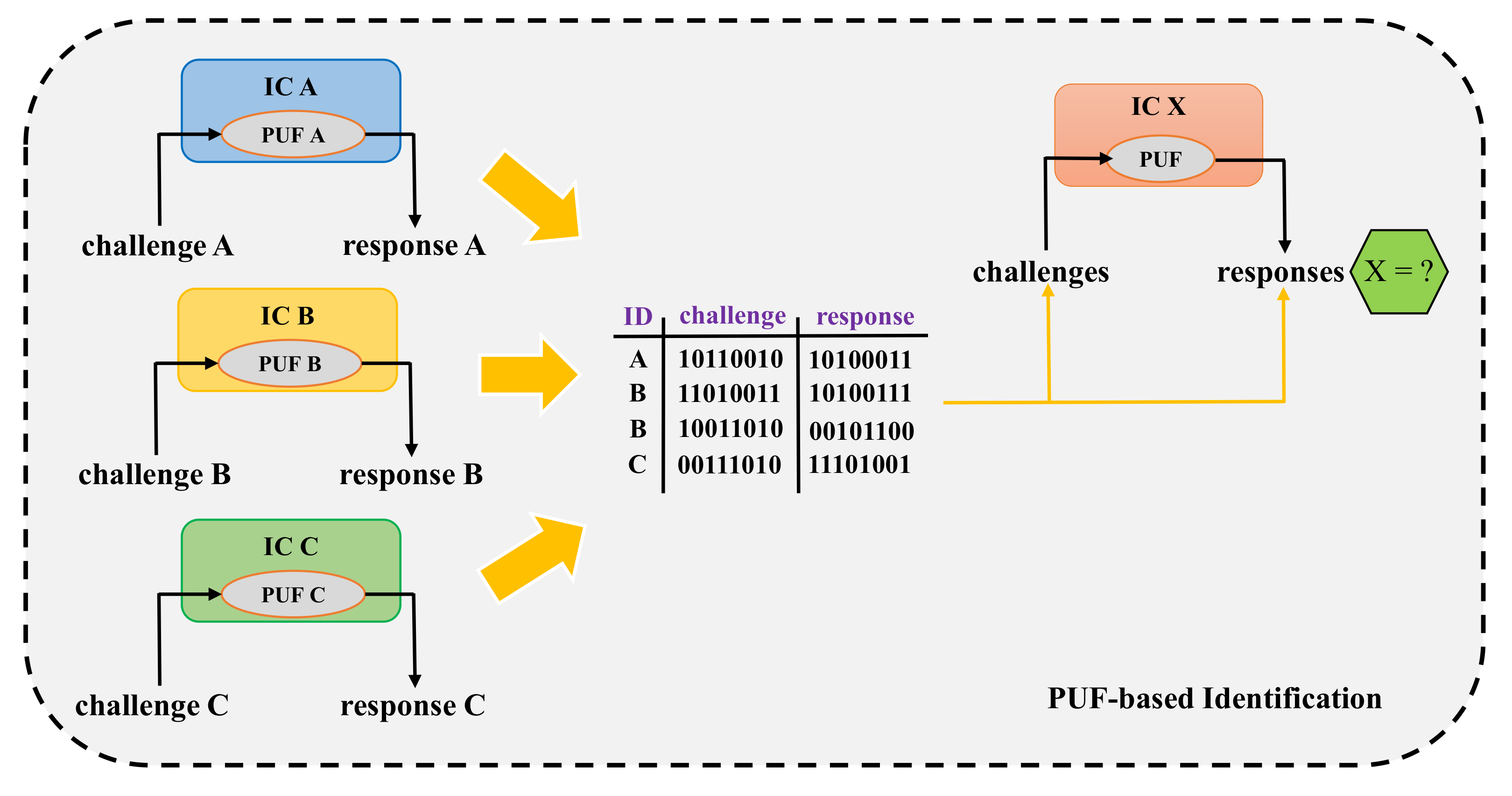
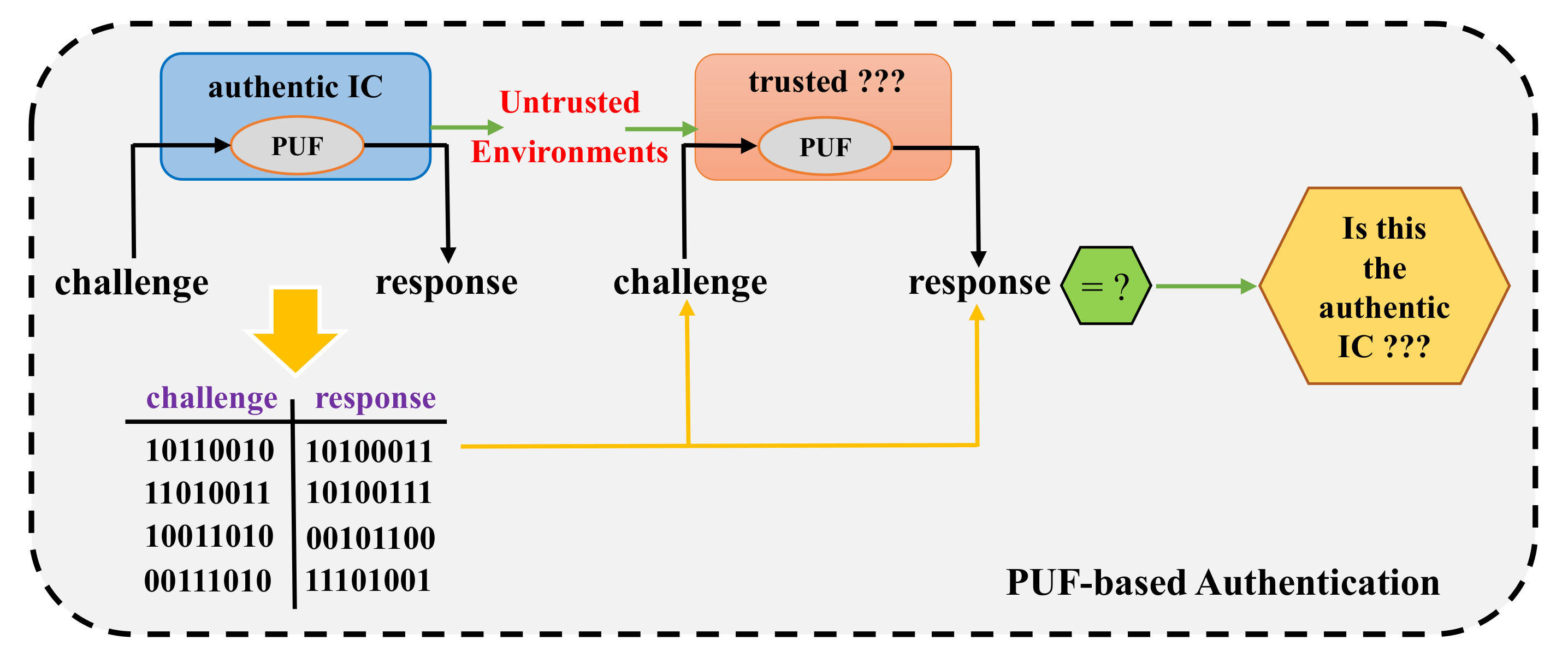
| Year | Publications |
|---|---|
| 2001–2002 | Optical PUF [25,26] |
| 2002–2003 | Arbiter PUF [27,28] |
| 2004 | Feed-Forward Arbiter PUF [33] |
| 2006 | Coating PUF [37] |
| 2007 | SRAM PUF [29,30], Ring Oscillator PUF [38], Latch PUF [39], XOR Arbiter PUF [38] |
| 2008 | Lightweight Arbiter PUF [40], Butterfly PUF [41], Flip-Flop PUF [42] |
| 2010 | Glitch PUF [43] |
| 2011 | Flash PUF [6], Current-based PUF [44], Bistable Ring PUF [45] |
| 2012 | Buskeeper PUF [46], DRAM Decay PUF [13,14,18] |
| 2014 | Bitline PUF [47], Transient Effect Ring Oscillator PUF [48] |
| 2015 | DRAM Startup PUF [12], DRAM Latency PUF [20] |
| 2016 | MEMS PUF [49] |
| 2017 | Row Hammer PUF [5] |
| Memory-based PUFs Delay-based PUFs Other PUFs | |
| Year | Total Amount of Publications | Publications |
|---|---|---|
| 2012 | 4 | Okamura et al. [13], Fainstein et al. [18], Keller et al. [14] (poster), Felber [15] (presentation slides) |
| 2013 | 2 | Rosenblatt et al. [80], Rosenblatt et al. [81] |
| 2014 | 3 | Liu et al. [82], Liu et al. [83], Keller et al. [16] |
| 2015 | 4 | Tehranipoor et al. [12], Hashemian et al. [20], Zhang [84], Rahmati et al. [85] |
| 2016 | 4 | Tehranipoor et al. [17], Sutar et al. [86], Vitenko [78], Xiong et al. [4] |
| 2017 | 10 | Sutar et al. [87], Tehranipoor et al. [88], Tang et al. [11], Eckert et al. [55], Tehranipoor et al. [3], Schaller [75], Tehranipoor [54], Kumar et al. [89], Kirihata et al. [90], Schaller et al. [5] |
| 2018 (Jan) | 2 | Kim et al. [21], Sutar et al. [19] |
| DRAM natural decay effect DRAM intensified decay effect due to VWL DRAM startup values DRAM data remanence effect DRAM row hammer effect DRAM access latency | ||
| Publication | PUF | TRNG | “Attack” PUF |
|---|---|---|---|
| Okamura et al., 2012 [13] | ✓ | ||
| Fainstein et al., 2012 [18] | ✓ | ||
| Keller et al., 2012 [14] | ✓ | ||
| Felber, 2012 [15] | ✓ | ✓ | |
| Rosenblatt et al., 2013 [80] | ✓ | ||
| Rosenblatt et al., 2013 [81] | ✓ | ||
| Liu et al., 2014 [82] | ✓ | ||
| Liu et al., 2014 [83] | ✓ | ||
| Keller et al., 2014 [16] | ✓ | ✓ | |
| Tehranipoor et al., 2015 [12] | ✓ | ||
| Hashemian et al., 2015 [20] | ✓ | ||
| Zhang, 2015 [84] | ✓ | ||
| Rahmati et al., 2015 [85] | ✓ | ||
| Tehranipoor et al., 2016 [17] | ✓ | ||
| Sutar et al., 2016 [86] | ✓ | ||
| Vitenko, 2016 [78] | ✓ | ||
| Xiong et al., 2016 [4] | ✓ | ||
| Sutar et al., 2017 [87] | ✓ | ||
| Tehranipoor et al., 2017 [88] | ✓ | ||
| Tang et al., 2017 [11] | ✓ | ||
| Eckert et al., 2017 [55] | ✓ | ||
| Tehranipoor et al., 2017 [3] | ✓ | ||
| Schallegreenr, 2017 [75] | ✓ (both) | ||
| Tehranipoor, 2017 [54] | ✓ (only) | ✓ (both) | |
| Kumar et al., 2017 [89] | ✓ | ||
| Kirihata et al., 2017 [90] | ✓ | ||
| Schaller et al., 2017 [5] | ✓ (both) | ||
| Kim et al., 2018 [21] | ✓ (both) | ||
| Sutar et al., 2018 [19] | ✓ | ✓ | |
| DRAM natural decay effect DRAM intensified decay effect due to VWL DRAM startup values DRAM data remanence effect DRAM row hammer effect DRAM access latency | |||
| Publication | Authentication and Anti-Counterfeiting | Identification and De-Anonymisation | Random Number Generation | Key Agreement |
|---|---|---|---|---|
| Okamura et al., 2012 [13] | ✓ | ✓ | ||
| Fainstein et al., 2012 [18] | ✓ | ✓ | ||
| Keller et al., 2012 [14] | ✓ | ✓ | ||
| Felber, 2012 [15] | ✓ | ✓ | ✓ | ✓ |
| Rosenblatt et al., 2013 [80] | ✓ | ✓ | ✓ | |
| Rosenblatt et al., 2013 [81] | ✓ | ✓ | ✓ | |
| Liu et al., 2014 [82] | ✓ | |||
| Liu et al., 2014 [83] | ✓ | |||
| Keller et al., 2014 [16] | ✓ | ✓ | ||
| Tehranipoor et al., 2015 [12] | ✓ | ✓ | ✓ | |
| Hashemian et al., 2015 [20] | ✓ | ✓ | ||
| Zhang, 2015 [84] | ✓ | ✓ | ||
| Rahmati et al., 2015 [85] | ✓ | |||
| Tehranipoor et al., 2016 [17] | ✓ | |||
| Sutar et al., 2016 [86] | ✓ | ✓ | ✓ | |
| Vitenko, 2016 [78] | ✓ | ✓ | ||
| Xiong et al., 2016 [4] | ✓ | ✓ | ✓ | |
| Sutar et al., 2017 [87] | ✓ | |||
| Tehranipoor et al., 2017 [88] | ✓ | ✓ | ||
| Tang et al., 2017 [11] | ✓ | ✓ | ||
| Eckert et al., 2017 [55] | ✓ | |||
| Tehranipoor et al., 2017 [3] | ✓ | ✓ | ✓ | |
| Schaller, 2017 [75] | ✓ (both) | ✓ (both) | ✓ (both) | ✓ (both) |
| Tehranipoor, 2017 [54] | ✓ (both) | ✓ (only) | ✓ (both) | ✓ (both) |
| Kumar et al., 2017 [89] | ✓ | ✓ | ✓ | |
| Kirihata et al., 2017 [90] | ✓ | ✓ | ✓ | |
| Schaller et al., 2017 [5] | ✓ (both) | ✓ (both) | ✓ (both) | |
| Kim et al., 2018 [21] | ✓ (both) | |||
| Sutar et al., 2018 [19] | ✓ | ✓ | ✓ | ✓ |
| DRAM natural decay effect DRAM intensified decay effect due to VWL DRAM startup values DRAM data remanence effect DRAM row hammer effect DRAM access latency | ||||
| Implementation Setup | Publications |
|---|---|
| Monte Carlo simulation | Fainstein et al., 2012 [18], Rosenblatt et al., 2013 [80], Rosenblatt et al., 2013 [81], Kumar et al., 2017 [89], Kirihata et al., 2017 [90] |
| SPICE-based simulation | Hashemian et al., 2015 [20] |
| novel eDRAM ASIC | Fainstein et al., 2012 [18], Rosenblatt et al., 2013 [80], Rosenblatt et al., 2013 [81], Tang et al., 2017 [11], Kumar et al., 2017 [89], Kirihata et al., 2017 [90] |
| FPGA and external DIP DRAM | Tehranipoor et al., 2015 [12], Tehranipoor et al., 2017 [88], Tehranipoor et al., 2017 [3], Tehranipoor, 2017 [54] (only) |
| FPGA and removable DIMM DRAM | Liu et al., 2014 [82], Liu et al., 2014 [83], Keller et al., 2014 [16], Zhang, 2015 [84], Rahmati et al., 2015 [85], Sutar et al., 2016 [86], Sutar et al., 2017 [87], Sutar et al., 2018 [19] |
| FPGA and on-board DRAM | Okamura et al., 2012 [13], Tehranipoor et al., 2016 [17], Eckert et al., 2017 [55], Tehranipoor, 2017 [54] |
| evaluation board and external DIP DRAM | Rahmati et al., 2015 [85] |
| evaluation board and removable DIMM DRAM | Kim et al., 2018 [21] |
| evaluation board and on-board DRAM | Xiong et al., 2016 [4], Schaller, 2017 [75],Schaller et al., 2017 [5] |
| conventional commercial hardware | Vitenko, 2016 [78] (on-board DRAM) |
| DRAM natural decay effect DRAM intensified decay effect due to VWL DRAM startup values DRAM data remanence effect DRAM row hammer effect DRAM access latency | |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Anagnostopoulos, N.A.; Katzenbeisser, S.; Chandy, J.; Tehranipoor, F. An Overview of DRAM-Based Security Primitives. Cryptography 2018, 2, 7. https://doi.org/10.3390/cryptography2020007
Anagnostopoulos NA, Katzenbeisser S, Chandy J, Tehranipoor F. An Overview of DRAM-Based Security Primitives. Cryptography. 2018; 2(2):7. https://doi.org/10.3390/cryptography2020007
Chicago/Turabian StyleAnagnostopoulos, Nikolaos Athanasios, Stefan Katzenbeisser, John Chandy, and Fatemeh Tehranipoor. 2018. "An Overview of DRAM-Based Security Primitives" Cryptography 2, no. 2: 7. https://doi.org/10.3390/cryptography2020007
APA StyleAnagnostopoulos, N. A., Katzenbeisser, S., Chandy, J., & Tehranipoor, F. (2018). An Overview of DRAM-Based Security Primitives. Cryptography, 2(2), 7. https://doi.org/10.3390/cryptography2020007






