5. Fault Based Key Recovery Attacks on MORUS
This section describes our fault-based key recovery attacks on MORUS. We propose two different fault-based key recovery attack on MORUS. The first is a permanent fault attack, whereas the second is a transient fault attack.
For MORUS the initialization phase is updated 16 times to mix the key and initialization vector into the 640 bits internal state. However after these 16 operations the key is directly XOR-ed to update the contents of state element
. The state element
may then be used in the computation of the first block of output keystream generated at time
(see Equation (
1)). We discuss a scenario in which these key bits can be revealed. This is the goal of our fault attacks.
MORUS processes the input plaintext after completing the initialization and associated data processing phase. During the associated data processing phase no output keystream is generated. Output keystream bits are generated only during the encryption phase. If the associated data processing phase is skipped (when there is no associated data) then the key bits will be directly XOR-ed in the output keystream function while processing the first plaintext block and faults can be applied to reveal the secret key bits. On the other hand, if the associated data processing phase is performed, then the key bits will get mixed with the contents of other state elements before appearing in the output keystream. In that case, the fault attack will not directly reveal the key bits.
When there is no associated data processing phase, Equation (
2) for the first plaintext block of MORUS can be represented as:
In Equation (
5), if we can remove the effect of
,
,
and
then the first ciphertext block
will just be the XOR of the first plaintext block
and the key
K. In such a scenario an adversary can apply set-to-zero faults in specific state elements to recover the key bits under a known plaintext model. In the following we discuss the effect of removing these state elements by introducing faults in some of the internal states of the cipher.
5.1. Permanent Fault Attack on MORUS-640
To remove the effect of
,
,
and
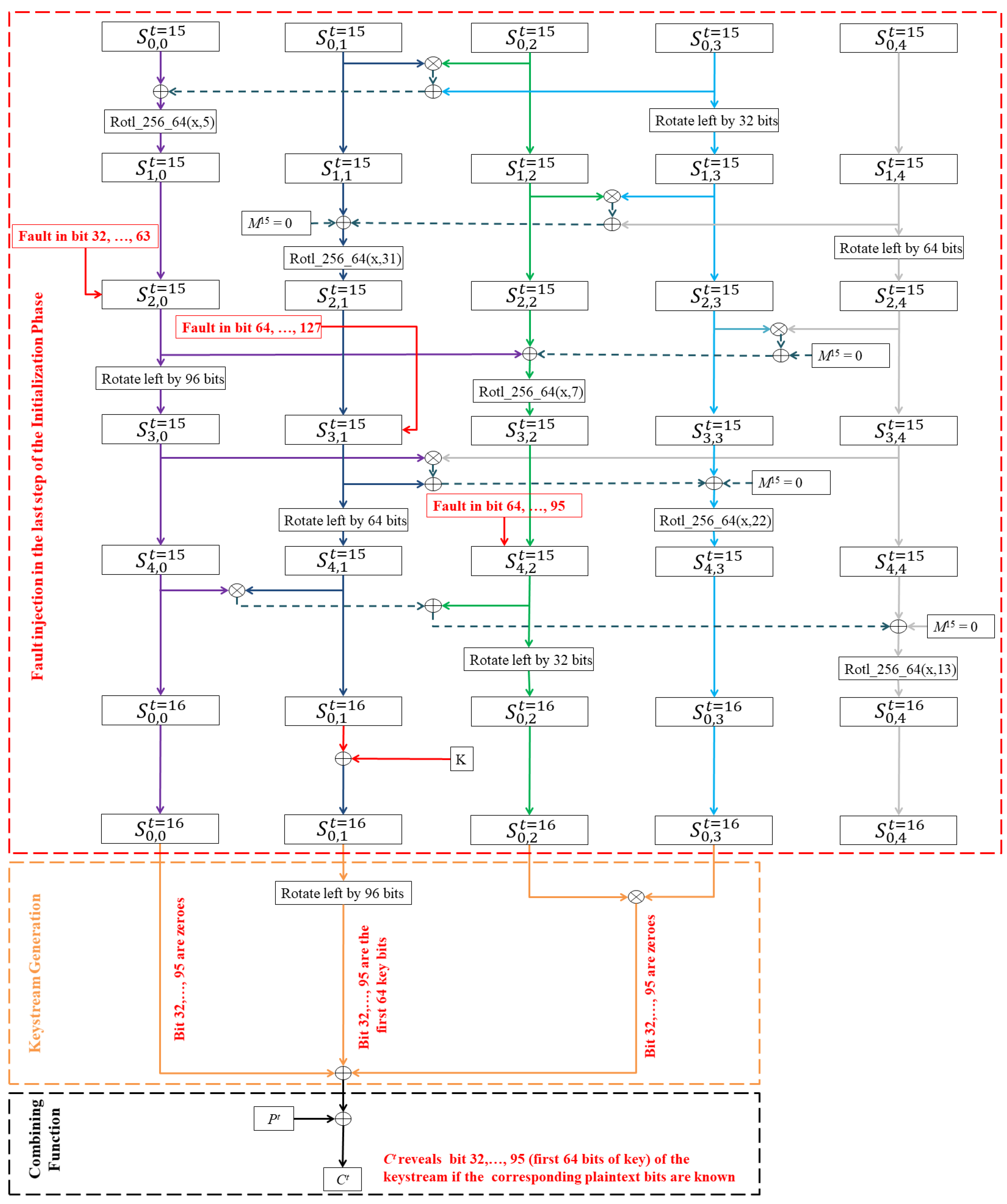
, an adversary can introduce permanent faults to set the contents of some specific registers of MORUS-640 to zero, thereby deleting the register contents. The locations that we target for our fault attack are shown in
Figure 2 and discussed in detail below.
We observe that during the 16th step (last update step) of the initialization phase, destroying the last 64 registers (i.e., register 64 to 127) of state element will result in all zero bits in the state element . This is due to the fact that at the fourth round of each step, the contents of are rotated left by 64 bits. The left rotation will bring the zero valued contents of the last 64 bits (faulty bits valued zero) into the first 64 register bits of state element . Since the last 64 registers are permanently set to zero, the rotation will not have any effect on these bits. After the left rotation there are no changes in the state element for that step, i.e., .
The key bits are XOR-ed with the contents of the state element after 16 updates in the initialization phase. As a result, at the end of the initialization phase the first 64 bits of state element will contain the first 64 bits of the key bits. Due to the permanent fault, XOR-ing of the last 64 bits of the key will have no effect on the corresponding bits of this state element. Note that in the encryption phase, the combining function rotates the contents of this state element by 96 bits. Thus the first 64 key bits will actually be XOR-ed at the bit position during the ciphertext computation. To recover the first 64 bits of the corresponding key we must eliminate the effect of bits of state elements , and from the first ciphertext block, using a similar technique to that used for state element .
To eliminate the effect of bits of state element in the keystream computation, one can permanently set bits of state element to zero (i.e., destroy the register bit 32 to 63). At the third round of each step, contents of state element goes through a left rotation of 96 bits. The left rotation will bring the zero valued contents of the bit (faulty bits) into the register bits of state element . The left rotation will not have any effect on the register bits due to the permanent fault. As a result bits of state element will be set to zero, since there are no changes in state element after the third round of each step.
In addition, in Equation (
5) observe that
and
are multiplied bitwise and used in the ciphertext computation. Therefore setting bits
of either of these two state elements to zero will eliminate the effect of both in the keystream computation. To introduce zero valued contents in bits
of state element
, one can permanently set bits
of state element
to zero, i.e., destroy the corresponding registers. At the fifth round of each step, contents of state element
goes through a left rotation of 32 bits. The left rotation will bring the zero valued contents of state bits
(faulty bits) into the register bits
of state element
. The left rotation will not have any effect on the register bits
due to the permanent fault. As a result bits
of state element
will be set to zero, which will eliminate the effect of state
and
in the keystream computation.
In summary, an adversary using this technique must introduce a total of 128 bits of permanent faults in the 640-bit internal state of MORUS-640 to recover the first 64 bits of the key. One can recover the remaining 64 key bits by exhaustive search, which will require a complexity of about . Note that it is not possible to recover the full key of MORUS-640 using only permanent faults, as the faults applied to will result in permanent zero values in 64 bits of , even after the key K has been XOR-ed with this state word. In particular, the attack described above is unable to recover bits 64 to 127 of the key, as these bits of have been permanently set to zero.
However, it is possible to obtain the full key of MORUS-640 by using a combination of permanent and transient faults. With an additional 128 faults (combination of permanent and transient faults) in carefully chosen parts of the state, the entire keystream output for that step will be the key. That is, for registers and now additionally are permanently zero, and for registers and now additionally are permanently zero. For registers are temporarily set to zero. These 64 permanent faults in each of and , together with 128 transient faults in would remove the contribution of the internal state values to the output and allow the full key to be obtained.
5.1.1. Attack Algorithm
The steps involved in recovering 64 bits of the secret key of MORUS-640 using 128 permanent faults are outlined in Algorithm 1. The steps involved in recovering the full 128-bit secret key using 256 faults (combination of permanent and transient faults) are outlined in Algorithm 2.
| Algorithm 1 Algorithm for Partial Key Recovery Attack on MORUS-640 using a Permanent Fault Model. |
- 1:
Load key and initialization vector and continue the initialization phase. - 2:
Insert permanent set to zero faults in registers 32 to 63 of state element . - 3:
Insert permanent set to zero faults in registers 64 to 127 of state element . - 4:
Insert permanent set to zero faults in registers 64 to 95 of state element . - 5:
Complete the initialization phase and construct the first block of the keystream. - 6:
Output bit 32 to 95 of the keystream as the first 64 bits of the secret key.
|
| Algorithm 2 Algorithm for Full Key Recovery Attack on MORUS-640 using a Combination of Permanent and Transient Fault Model. |
- 1:
Load key and initialization vector and continue the initialization phase. - 2:
Insert permanent set to zero faults in registers 32 to 63 and 96 to 127 of state element . - 3:
Insert transient set to zero faults in registers 0 to 127 of state element . - 4:
Insert permanent set to zero faults in registers 64 to 95 and 0 to 31 of state element . - 5:
Complete the initialization phase and construct the first block of the keystream. - 6:
Rotate the keystream to the left by 32 bits and output this as the 128-bit secret key.
|
5.2. Permanent Fault Attack on MORUS-1280
Similar to the technique used for MORUS-640, if the associated data processing phase is skipped, i.e., there is no input associated data, then the key bits will be directly XOR-ed in the output keystream function while processing the first plaintext block. In Equation (
5), an adversary can apply permanent set to zero faults to eliminate the effect of
,
,
and
and recover the secret key of MORUS-1280, under a known plaintext model. The locations that we target for our fault attack are shown in
Figure 3 and discussed in detail below.
During the last step of the initialization phase, destroying the last 128 registers (i.e., register 128 to 255) of state element will result in all zero bits in the state element . There are no changes in the state element for that step, that is . Since the secret key is XOR-ed with the contents of this state element after these 16 steps, the first 128 bits of state element will contain the first 128 bits of the secret key. Due to the permanent fault, XOR-ing of the last 128 bits of the secret key will have no effect on these bits.
Note that in the encryption phase, the combining function rotates the contents of this state element by 192 bits. Following a similar technique to that used for MORUS-640, an adversary can select the relevant bits of state element , and based on the rotation distance of MORUS-1280, and apply permanent set to zero faults in the corresponding bits. By introducing such faults, an adversary can easily recover the first 128 bits of the secret key under a known-plaintext scenario. Recall that this is the entire key when the key size is 128-bit, while it represents the first 128 bits of the key when the key size is 256-bit.
An adversary using this technique must introduce a total 256 bits of permanent fault in the 1280 bits internal state of MORUS-1280. An adversary recovers the whole key when the key size is 128-bit, whereas an adversary recovers the first 128 bits of the key when the key size is 256-bit. An adversary can recover the remaining bits of the key for MORUS-1280-256 by exhaustive search, which will require a complexity of about .
Note that similar to MORUS-640 it is not possible to recover the full key of MORUS-1280-256 using only permanent faults, as the faults applied to will result in permanent zero values in 128 bits of , even after the key K has been XOR-ed with this state word. In particular, the attack described above is unable to recover bits 128 to 255 of the key, as these bits of have been permanently set to zero.
However, it is possible to obtain the full key of MORUS-1280-256 by using a combination of permanent and transient faults. With an additional 256 faults (combination of permanent and transient faults) in carefully chosen parts of the state, the entire keystream output for that step will be the key. That is, for registers and now additionally are permanently zero, and for registers and now additionally are permanently zero. For registers are temporarily set to zero. These 128 permanent faults in each of and , together with 256 transient faults in would remove the contribution of the internal state values to the output and allow the full key of MORUS-1280-256 to be obtained.
5.2.1. Attack Algorithm
The steps involved in recovering 128 bits of the secret key of MORUS-1280 using 256 permanent faults are outlined in Algorithm 3. The steps involved in recovering the full 256-bit secret key of MORUS-1280 using 512 faults (combination of permanent and transient faults) are outlined in Algorithm 4.
| Algorithm 3 Algorithm for Key Full Recovery Attack on MORUS-1280-128/Partial Key Recovery Attack on MORUS-1280-256 using a Permanent Fault Model. |
- 1:
Load key and initialization vector and continue the initialization phase. - 2:
Insert permanent set to zero faults in registers 64 to 127 of state element . - 3:
Insert permanent set to zero faults in registers 128 to 255 of state element . - 4:
Insert permanent set to zero faults in registers 128 to 191 of state element . - 5:
Complete the initialization phase and construct the first block of the keystream. - 6:
Output bit 64 to 191 of the keystream as the first 128 bits of the secret key.
|
| Algorithm 4 Algorithm for Full Key Recovery Attack on MORUS-1280-256 using a Combination of Permanent and Transient Fault Model. |
- 1:
Load key and initialization vector and continue the initialization phase. - 2:
Insert permanent set to zero faults in registers 64 to 127 and 192 to 255 of state element . - 3:
Insert transient set to zero faults in registers 0 to 255 of state element . - 4:
Insert permanent set to zero faults in registers 128 to 191 and 0 to 63 of state element . - 5:
Complete the initialization phase and construct the first block of the keystream. - 6:
Rotate the keystream to the left by 64 bits and output this as the 256-bit secret key.
|
5.3. Reducing the Required Number of Permanent Faults
The attacks presented in
Section 5.1 and
Section 5.2 demonstrate that it is possible to fully recover the key using a combination of permanent and transient faults, but if the number of faults is reduced, then partial key recovery is possible using only a permanent fault model. For example, in MORUS-640 256 faults were required for full key recovery using a combination of permanent and transient faults, whereas 128 permanent faults permitted recovery of 64 bits of the 128-bit key.
Alternatively, we could take a probabilistic approach to key recovery, based on the bias of the AND operation in the combining function. The combining function for the first plaintext block of MORUS described in Equation (
5) has three XOR operations and an AND operation. During the processing of the first input plaintext block, the AND operation in Equation (
5) takes input from the state elements
and
. The output of the AND operation is heavily biased towards zero, so we can remove the output of the AND operation from Equation (
5) with a high probability. Equation (
5) can be rewritten as
For MORUS-640, the output of the first 64 bits of the AND operation is zero with a probability of . In this case, applying a modified version of Algorithm 1 (with step 4 omitted) an adversary needs to introduce 96 permanent faults at the last step of the initialization phase in order to recover the first 64 bits of the key with a probability of . Similarly, applying a modified version of Algorithm 2 (with step 4 omitted) an adversary needs to introduce 192 faults at the last step of the initialization phase in order to recover the entire 128-bit key with a probability of .
Alternatively, for MORUS-1280 the output of the corresponding 128 bits of the AND operation is zero with a probability of . Therefore applying a modified version of Algorithm 3 (with step 4 omitted) an adversary needs to introduce 192 permanent faults at the last step of the initialization phase in order to recover the first 128 bits of the key with a probability of . Similarly, applying a modified version of Algorithm 4 (with step 4 omitted) an adversary needs to introduce 384 faults at the last step of the initialization phase in order to recover the entire 256-bit key with a probability of .
5.4. Transient Fault Attacks on MORUS
The observation from the above sections can be extended in an approach that induces transient faults in the MORUS states to recover the secret key. An adversary can introduce transient set to zero faults at specific times and locations to eliminate the effect of the contents from state elements , and . Following this adversary can observe the corresponding bit in the first keystream block to recover one bit of the secret key.
The contents of state elements and are multiplied bitwise and used in the keystream generation function. Setting any of the bits of these two state elements to zero (inducing transient set to zero fault) will set the output of the bitwise multiplication for the corresponding bits to zero.
In particular, the adversary needs to introduce three bits of faults to recover a single bit of the secret key. To recover the jth bit of the secret key an adversary can introduce a one bit transient fault on the jth register of state element and th register of state elements and , where is the block size of 128-bit or 256-bit for MORUS-640 and MORUS-1280, respectively. The transient fault introduced here is a set to zero fault which temporarily resets the corresponding bits to zero. With the introduction of these three bit faults in state elements , an adversary can recover the jth bit of the secret key. At each time step, an adversary needs only three faults in specific locations, but depending on the key size this process must be repeated 128 or 256 times in order to reveal the whole key.
Consider the scenario where an adversary can induce such faults to different locations of the initial internal states, which are computed from the same key but with different initialization vectors. For MORUS-640, an adversary can select 128 different initial states computed from the same key but different initialization vectors, and for each initial state induce the faults in 3 specific location of state elements . With this the adversary can recover the whole secret key of MORUS-640-128. This will require bits of transient faults.
For MORUS-1280-128, an adversary can select 128 different initial states computed from the same key but different initialization vectors, and for each initial states induce the transient set to zero faults in 3 specific location of state elements . With this the adversary can recover all the secret key of MORUS-1280-128. This will also require bits of transient faults.
Similarly for MORUS-1280-256, an adversary needs to introduce transient set to zero faults in 3 specific location of state elements , and continue this process 256 times with 256 different initial states computed from the same key but with different initialization vectors. This will require bits of transient faults to recover the 256-bit secret key of MORUS-1280-256.
5.4.1. Attack Algorithm
The steps for the transient fault-based key recovery attack are outlined in Algorithm 5.
| Algorithm 5 Algorithm for Transient Fault Based Key Recovery Attack. |
- 1:
Repeat steps 2 to 5 for . - 2:
Load the key and a fresh initialization vector and continue the initialization phase. - 3:
Insert transient set to zero fault in register j of state element . - 4:
Insert transient set to zero faults in register of state elements and . - 5:
Complete the initialization phase and construct the first block of the keystream. - 6:
Output keystream bit as the jth bit of the secret key.
|
5.5. Comparison of Fault Based Key Recovery Attacks
We described two fault-based key recovery attacks on different variants of MORUS. The first attack uses permanent set to zero fault injection into the internal state of MORUS. The second attack uses transient set to zero fault injection into the internal state of MORUS. The results from these fault attacks are presented in
Table 2.
The fault model for these stuck-at fault-based key recovery attacks requires fault injections at a specific time and location. This can be achieved using optical fault injection. The difference between the permanent fault and the transient fault is in the number of faults and the number of key bits recovered.
With permanent faults, the adversary is able to recover at least half the secret key. If the entire key is not recovered, then the remaining key bits may be obtained through exhaustive search. Alternatively, a larger number of faults (combination of permanent and transient faults) may reveal the entire key. The key recovery using permanent fault model or a combination of permanent and transient fault model requires fewer faults than that for transient fault model. For the transient fault, an adversary can recover the entire key; however, this requires up to three times as many faults compared to the permanent fault attacks.
The adversary needs to have access to the physical implementation of the algorithm to apply these fault attacks. Also note that both of these transient and permanent fault attacks described in this paper are based on the assumption that there is no associated data. These attacks are not feasible otherwise.
The fault model described here requires an adversary to use faults which set specific bits of the registers to zero, i.e., set to zero fault. These results are theoretical, and we did not perform any experiments since the results are straightforward given that the faults can be applied in the implementation of the algorithm. However, we note that the fault models for our proposed key recovery attacks have been shown to work in hardware [
12], and also adopted in several other research papers [
11,
14].
6. Fault Based Forgery Attack on MORUS
This section discusses a fault-based forgery attack on MORUS. The goal of the attack is to modify the input message by flipping specific message bit(s) and have this modified message accepted as legitimate at the receiver side. The modification can be either in the associated data or in the plaintext. In order to achieve this, we require the production of the appropriate tag value for the modified message.
Fault based forgery attacks on the authenticated encryption ciphers CLOC and SILC were introduced by Roy et al. [
15]. Later, in the CAESAR Google discussion forum it was pointed out by Iwata et al. [
16] that any authenticated encryption scheme can be forged using faulty encryption queries. This requires an adversary to inject faults in the inputs submitted to the encryption oracle and then use the output of the encryption oracle with the faulty inputs to continue with the forgery. We describe here a similar fault injected forgery, however; we propose the injection of faults into the internal state instead of the inputs, and apply this fault injection based forgery to MORUS.
In the associated data processing and encryption phases of MORUS, the input associated data and the plaintext are loaded into the internal state of the cipher. Therefore, any changes in the input associated data or the plaintext will affect the internal state. An adversary can apply a forgery attack by injecting faults into the internal state of MORUS to reflect the changes made in either the associated data or in the plaintext. For the following discussion we use the term M to represent either the associated data or the plaintext.
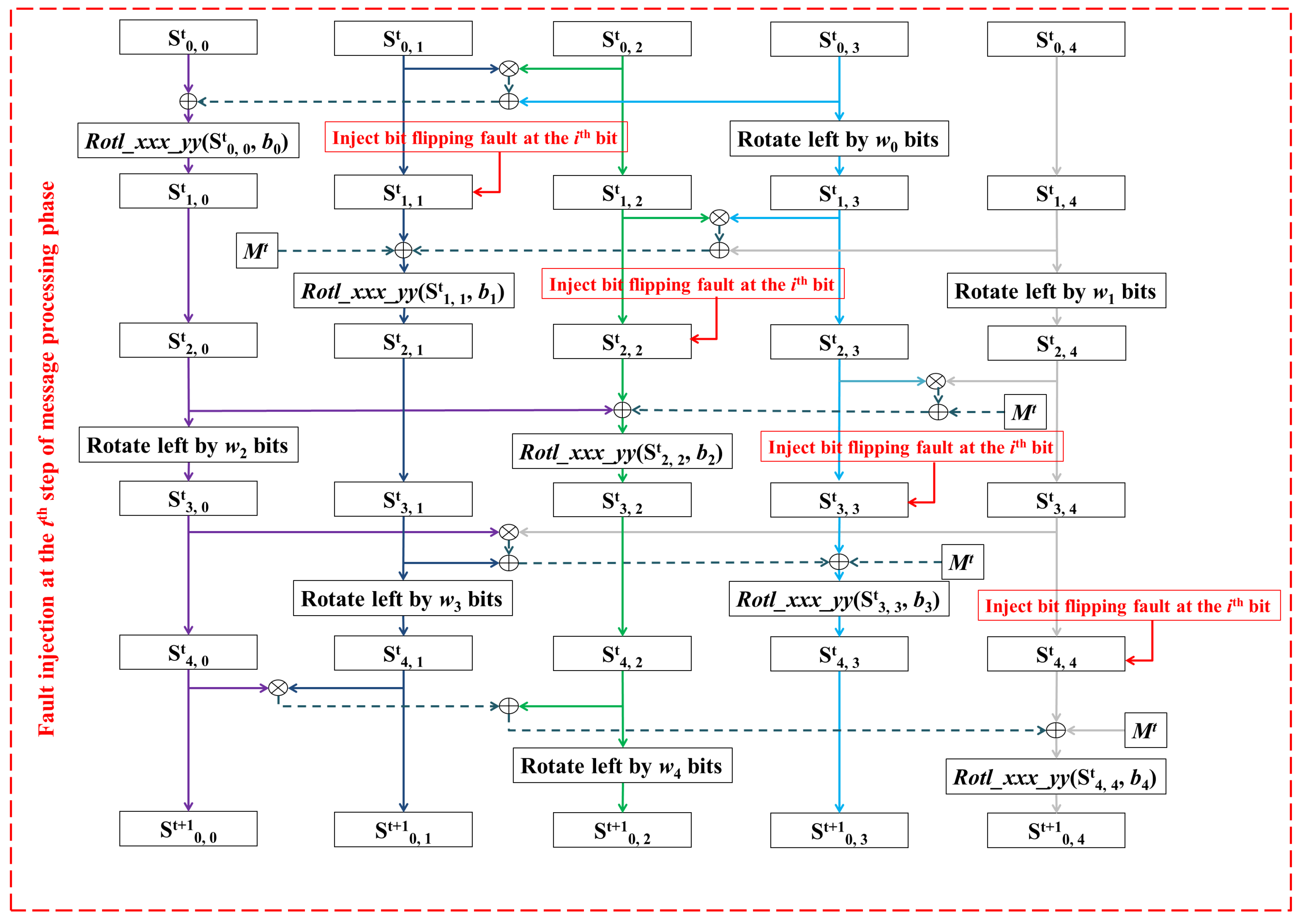
Suppose the adversary wants to modify the ith bit of the message block as received by the receiver. Let denote the modified message block, where the modification is a bit flip in the ith bit of the original message block . We observe that the input message block is XOR-ed with the contents of state element , , and . Thus XOR-ing with the contents of the state element , , and will flip the ith bit of the respective state element.
To perform a forgery attack on the message
, the adversary can apply bit flipping faults to the
ith bit of the state elements
,
,
and
. This is equivalent to modifying the input message block from
to
at the sender’s device, where the modification is a complementation of the
ith bit of the original input message block
.
Figure 4 illustrates the locations of the fault injections to achieve the fault-based forgery attack on MORUS.
Let denote the tag generated for the fault induced version of the state. The adversary can use this faulty tag to perform the forgery attack. Note that the fault was introduced in the internal state bits after the computation of the ciphertext block , and so the fault does not affect the transmitted ciphertext. Therefore, an adversary needs to also modify the ith bit of the corresponding ciphertext block (by flipping the ith bit) in the case where is a plaintext block. Similarly an adversary needs to modify the ith bit of the corresponding associated data block in the case where is an associated data block. The adversary can simply intercept and change the transmitted message block to , and send it with the faulty tag as the output. The adversary does not need to apply any faults at the receiver’s side.
In the decryption and tag verification phase, the receiver will XOR the recovered message block with the state element , , and of MORUS. The modified ciphertext block , or the modified associated data block ensures that the recovered message will be the same as . The recovered message is then XOR-ed with the state elements , , and , which complements the ith bit of the respective state elements. So the internal state contents in the receiver’s device are now the same as those after applying the bit-flipping faults at the sender’s device.
Once the message is processed, the finalization process at the receiver side generates the tag . Clearly, both of the tags are generated from the same state contents; thus, the tag generated at the receiver is the same as the tag sent by the sender. Therefore using the faulty tag the modified message will be accepted as legitimate at the receiver.
Let denote the number of bits flipped in an input message block . Then the total number of faults required for the forgery attack is equal to . This is because a single bit flip in the input affects four bits in the state of MORUS.
6.1. Attack Algorithm for Fault Based Forgery
The steps involved in the fault-based forgery attack on MORUS are outlined in Algorithm 6.
| Algorithm 6 Algorithm for Fault Based Forgery Attack on MORUS. |
- 1:
Insert bit flipping faults at the ith bit of state element , , and of the sender device. - 2:
Continue the finalization process at the sender and observe the faulty tag . - 3:
Modify the bit of the associated data block to , if the goal is associated data modification. Alternatively, modify the ith bit of the ciphertext block to . - 4:
Send the modified associated data or the modified ciphertext , with the faulty tag .
|
6.2. Feasibility of Fault Based Forgery Attack on MORUS
The fault-based forgery attack applied in this paper requires precise application of bit-flipping faults. This model imposes a restrictive criteria on the adversary’s capability since it requires the injection of the bit-flipping faults in a precise location. Note that bit-flipping faults have been applied in practice [
13]; however, the fault may affect more than a single bit. Therefore, our fault model does not prohibit the adversary from applying the bit-flipping faults, but application of these faults in precise location may not be achieved yet in practice. This paper demonstrates a vulnerability in the integrity component of MORUS if such a fault model can be applied in practice.
7. Conclusions
This paper examines the applicability of fault attacks on the authenticated encryption cipher MORUS. In particular, we described fault attacks with two different goals: one to breach the confidentiality component of MORUS and the other to breach the integrity component. This is a first attempt at analysing the security of MORUS with respect to fault attacks, and although these attacks are relatively direct applications of the fault models, it may be possible to augment this for more effective attacks. This is planned as future work.
We introduced a fault-based key recovery attack on MORUS-640-128 which can recover 64 bits of the secret key by introducing 128 bit permanent faults in the 640-bit internal state. Similarly, we introduced a fault attack for MORUS-1280, which can recover 128 bits of the secret key with 256 bits of permanent faults. This is the entire key for MORUS-1280, if the key size is 128-bit. We demonstrated that permanent faults can be also combined with transient faults to recover the entire secret key for all the variants of MORUS.
We analysed the injection of transient faults into the internal state of MORUS. Our analysis shows that the secret keys of MORUS-640-128 and MORUS-1280-256 can be recovered, with 384 and 768 bits of transient faults, respectively. Note that all of these fault-based key recovery attacks apply only when there is no associated data. These attacks are not feasible when there is associated data input.
We also introduced a fault-based forgery attack on MORUS. This is a simple and trivial attack which works by flipping specific bits of the message during transmission and introducing bit flipping faults in the corresponding bit(s) of state elements at the sender’s device. The adversary can use the faulty tag to have the modified message accepted as legitimate. This attack works because the message is directly XOR-ed into the state. This attack requires the introduction of four bits of faults in the MORUS state elements, for a single bit flip in the input message.
We demonstrated that physical attacks such as fault injections can be powerful against all variants of MORUS. The fault-based key recovery attack on MORUS works because the secret key of MORUS is XOR-ed with a particular component of the internal state after performing the last round of the initialization phase. This operation is performed to prevent a key recovery attack when the initial internal state is recovered. To provide security against the fault-based key recovery of MORUS, an additional state update step can be introduced after this operation and before generating keystream.
The fault attacks proposed in this paper do not require nonce-reuse. Thus, the designer restrictions on nonce-reuse do not prohibit these attacks. However, these are attacks on the implementation rather than the algorithm itself. Therefore, it is important to have appropriate physical protection for cryptographic devices to prevent these type of fault attacks.