1. Introduction
The Visual Cryptography (VC) had particularly been highlighted in 1987 by Kafri and Keren [
1]. They described a simple technique for encryption of 2D pictures by using random grids. The decryption is obtained by the superposition of two cyphered images. These cyphered images, i.e., encrypted images or key images, are commonly named shares. In 1994, Naor and Shamir [
2] popularized an analogous visual secret sharing technique. These works describe a pixel-based encrypting technique that can directly be decrypted by the human visual system.
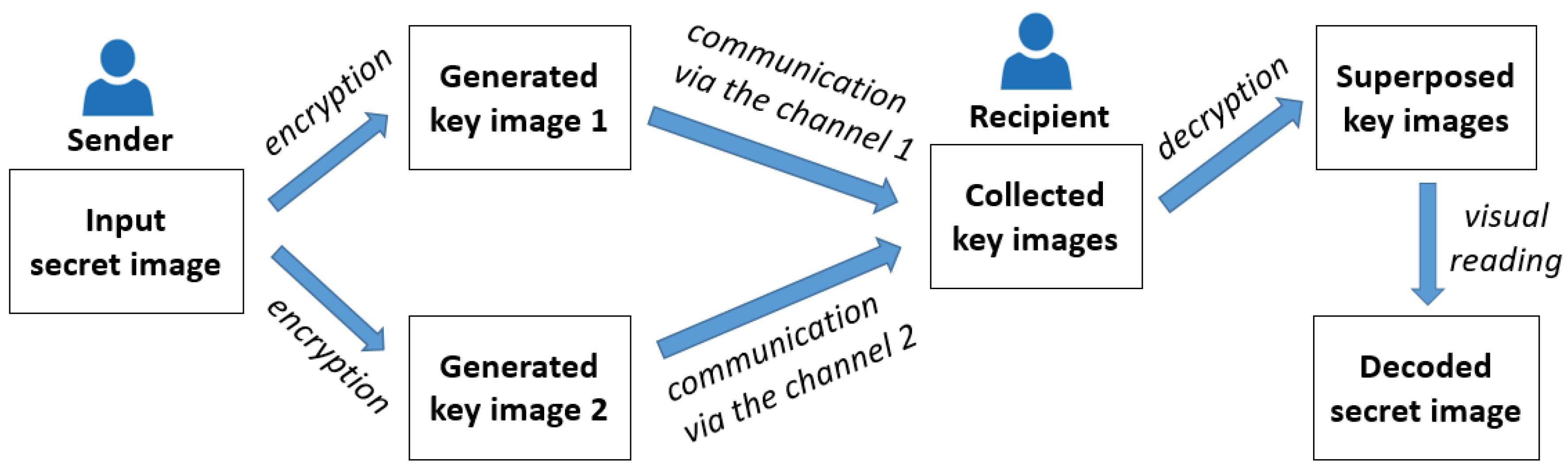
A work-flow diagram of the classical VC is shown in
Figure 1. One single image of interest (content to secretly communicate such as the image of a numeric code) is considered (i.e., input secret image). Then, two key images are generated from this secret image. The generated key images are then sent to a recipient by using two communication channels of different natures for security reasons (e.g., by MMS and by email, respectively). For communication considerations, one can refer for example to [
3,
4,
5]. Once the two key images are collected by the recipient, the content of the secret image can be decrypted by a visual reading of the superposed key images.
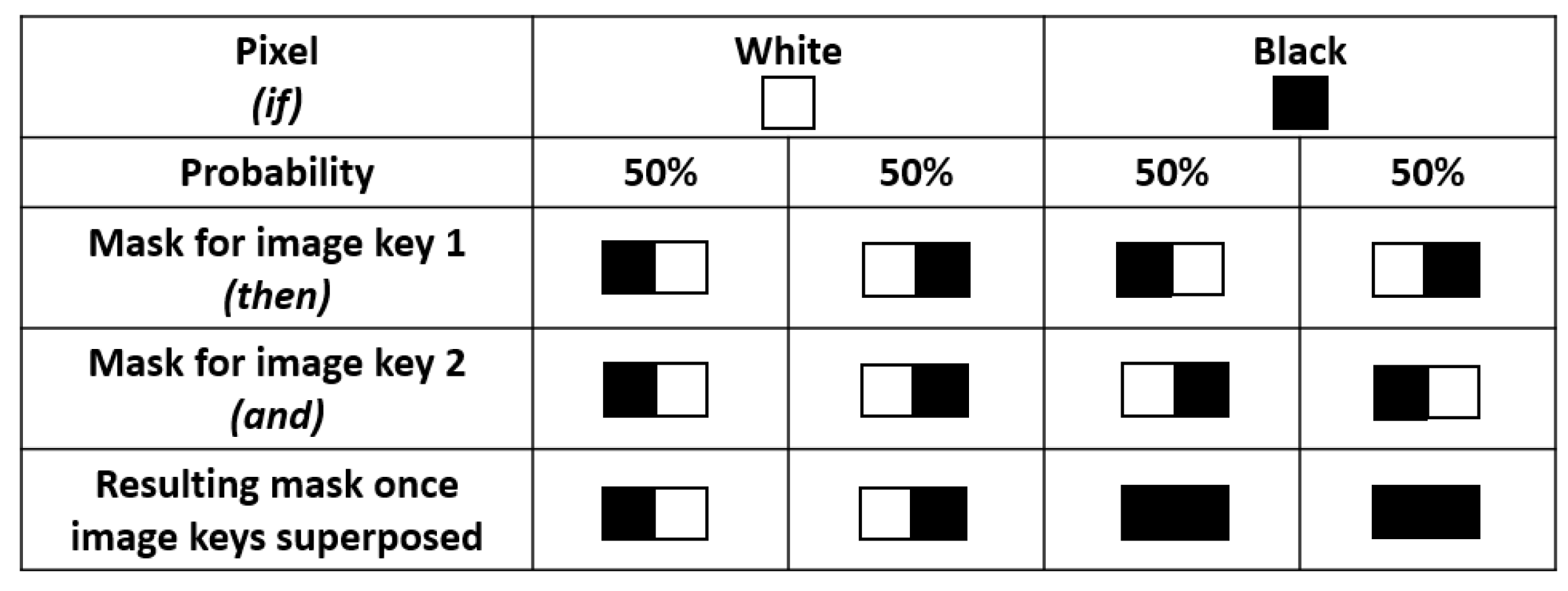
Precisely, an encryption and decryption of a pixel-based VC type is depicted in
Figure 2. Considering a secret image, two key images have to be generated. In the presented case, it is assumed that the secret image contains a numeric code that has been written in white over a black background (i.e., a binary image).
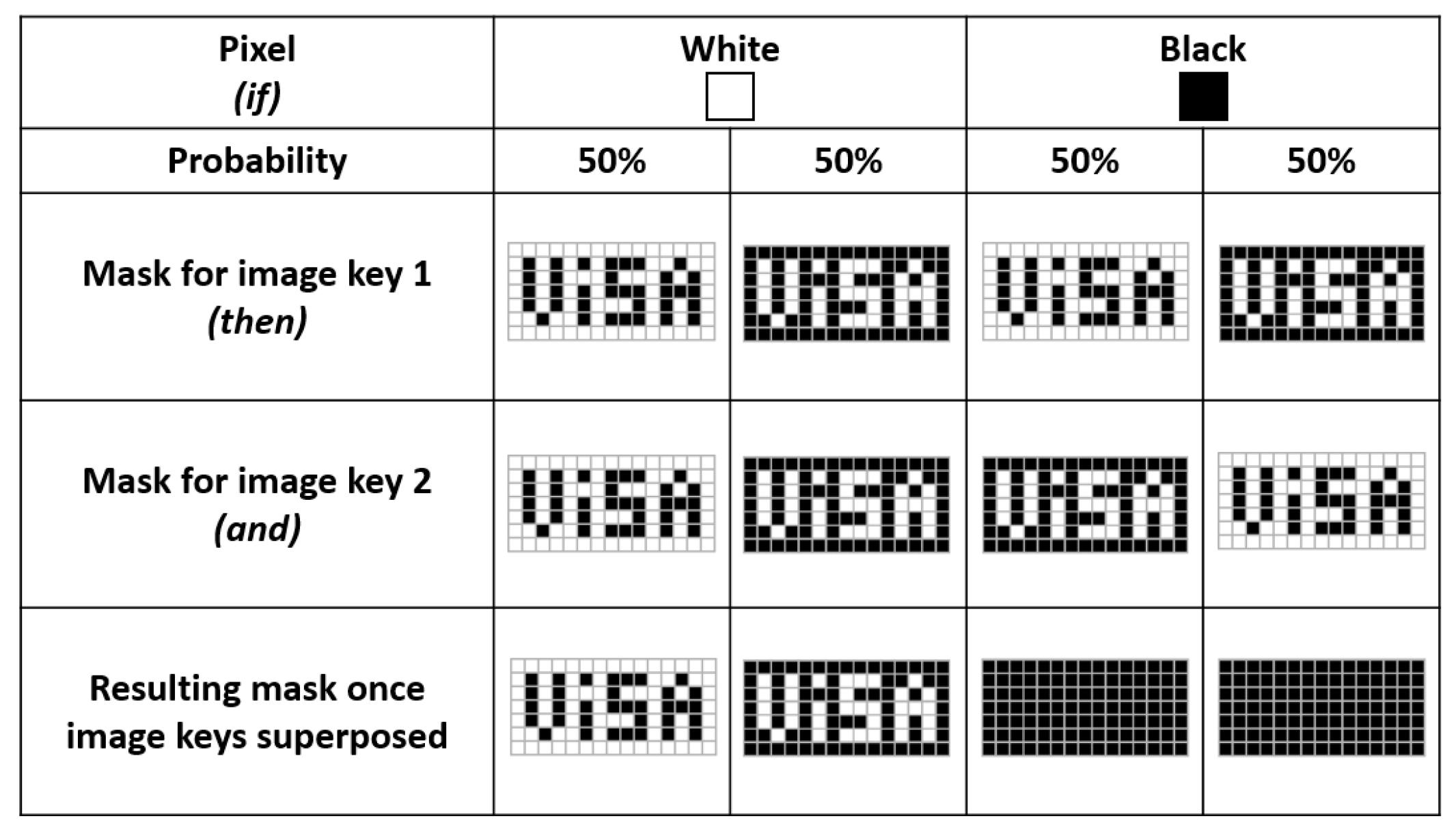
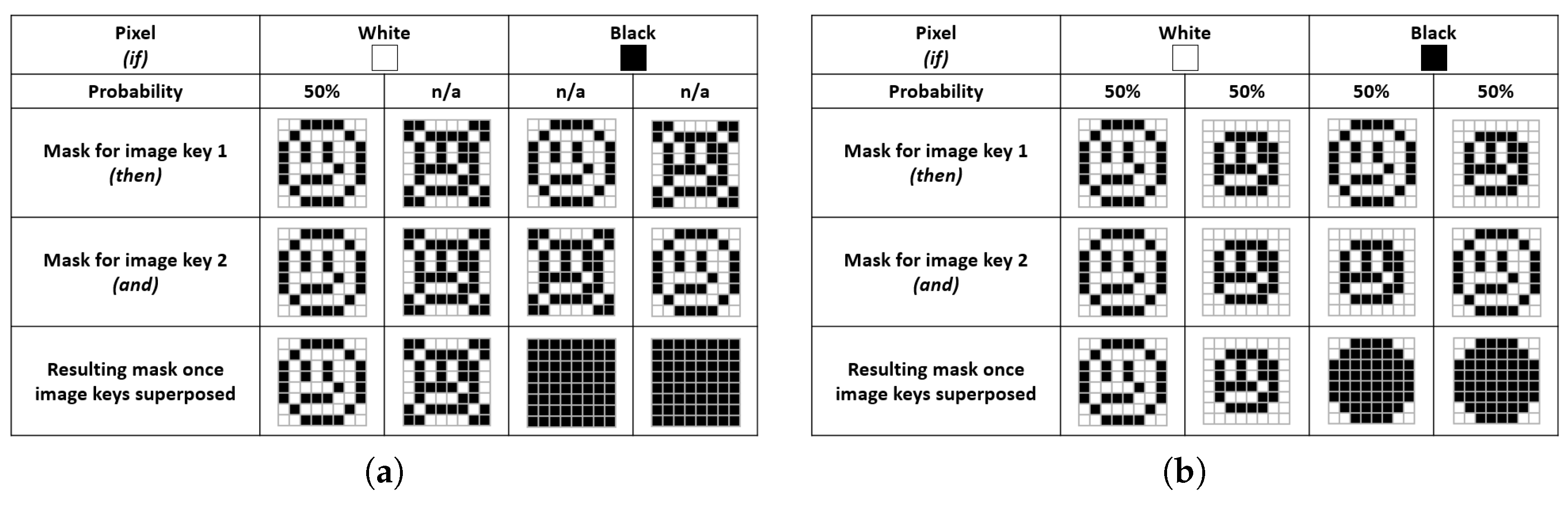
For each pixel of the secret image, a mask composed of two horizontal pixels (one white and the other one black) is generated in the two key images. Consequently, the key images will have a width multiplied by two.
For a white pixel in the secret image (i.e., message element), the same mask of two adjacent pixels will texture both key images. Hence, the superposed masks will show the same mask (invariance) keeping visible the message information.
For a black pixel (i.e., background element), a mask will texture Key Image 1, and its opposite mask will texture Key Image 2. Therefore, their superposition keeps the background element totally black.
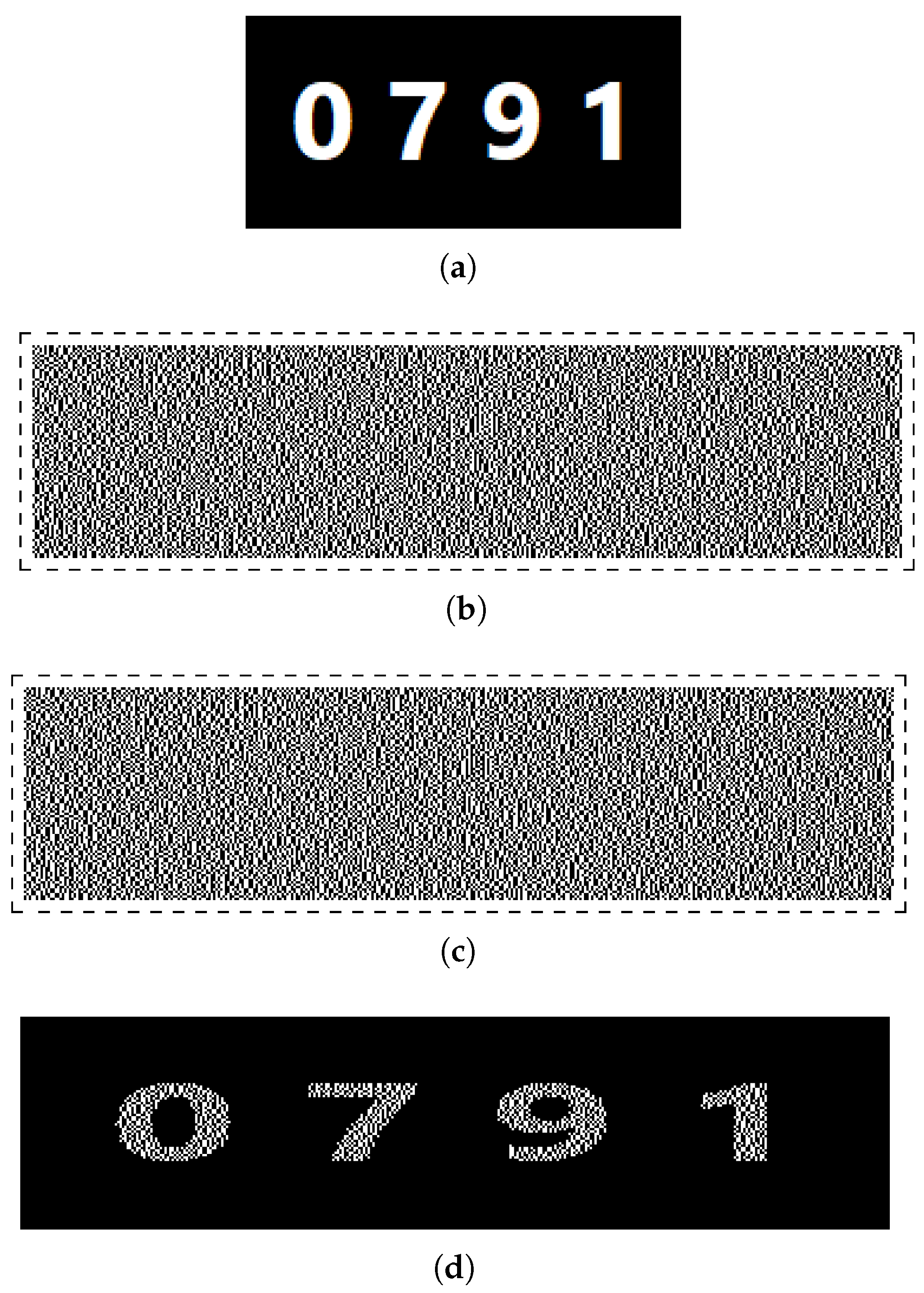
Besides, the masks are randomly and uniformly generated. In this way, the message is not distinguishable from only one key image. An example of a secret image, key images and a decrypted image using the considered pixel-based VC is depicted in
Figure 3.
Similar pixel-based VC techniques are used with halftone imagery [
6] and gray-scale or color images [
7,
8]. Beyond the security aspects, variants of VC aim at concealing an image or a message within another one by steganography (e.g., [
9]). Other VC variants integrate animation effects using a barrier-grid animation (e.g., kinegram or Scanimation™ [
10]) or animated GIF images (e.g., [
11]).
More related to the representation type of VC, Borchert proposed in [
12] segment-based visual cryptography for the representation of digital images. The principle of the pixel-based VC was extended to masks composed of horizontal and vertical segments for producing a Seven-Segment Display (SSD) (e.g., [
13]). Potential advantages of the segment-based VC by comparison with the classical pixel-based VC are: (i) an easier adjustment of the superposed key images; segment masks can notably facilitate a manual alignment of the encrypted images; (ii) an easier recognition of the symbols by human eyes, particularly in the case of a transparency-on-screen scenario.
To the best of our knowledge, VC methods do not propose techniques to exploit shares as a direct medium of communication in addition to their principal usage (embedding hidden information). Indeed, the majority of shares look like grids of random black and white pixels (i.e., salt and pepper noise) having no direct meaning.
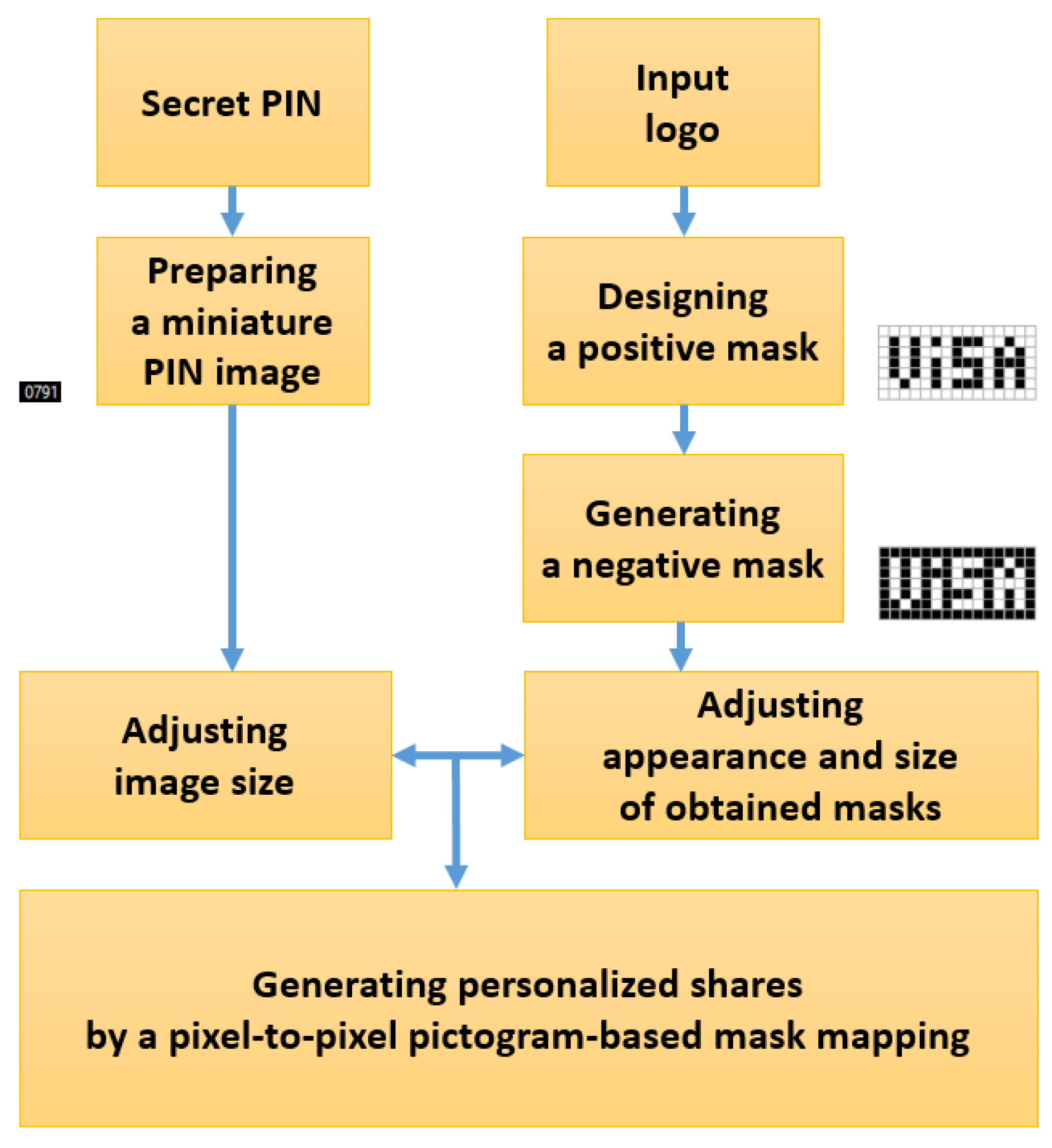
The proposed method aims at integrating visible and readable information at the surface of key images while embedding a hidden numerical code. This is done by generating an arrangement of pictorial patterns. In this way, two levels of visual information are used through the same support; one for making visually pleasant shares towards stylization or business promotion, the other one for communicating a secret message.
Section 2 presents this method in detail.
Section 3 exposes experimental results by considering masks of different natures. The robustness of the method to the automatic decoding of a secret message is evaluated through a comparative study.
Section 4 summarizes the contributions and presents the future works.
3. Experimental Results and Evaluation
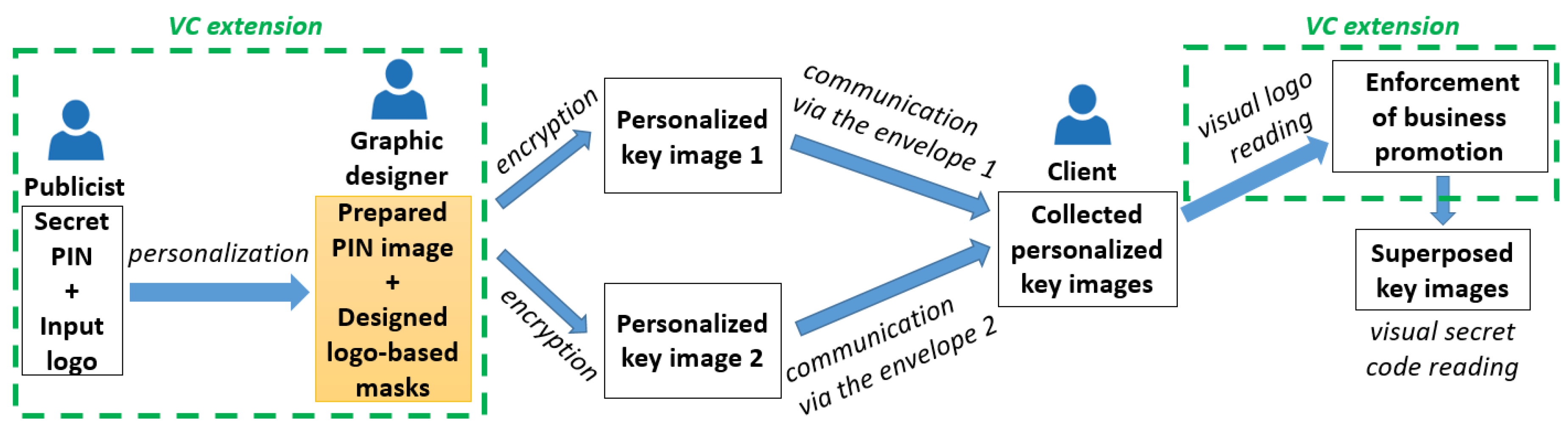
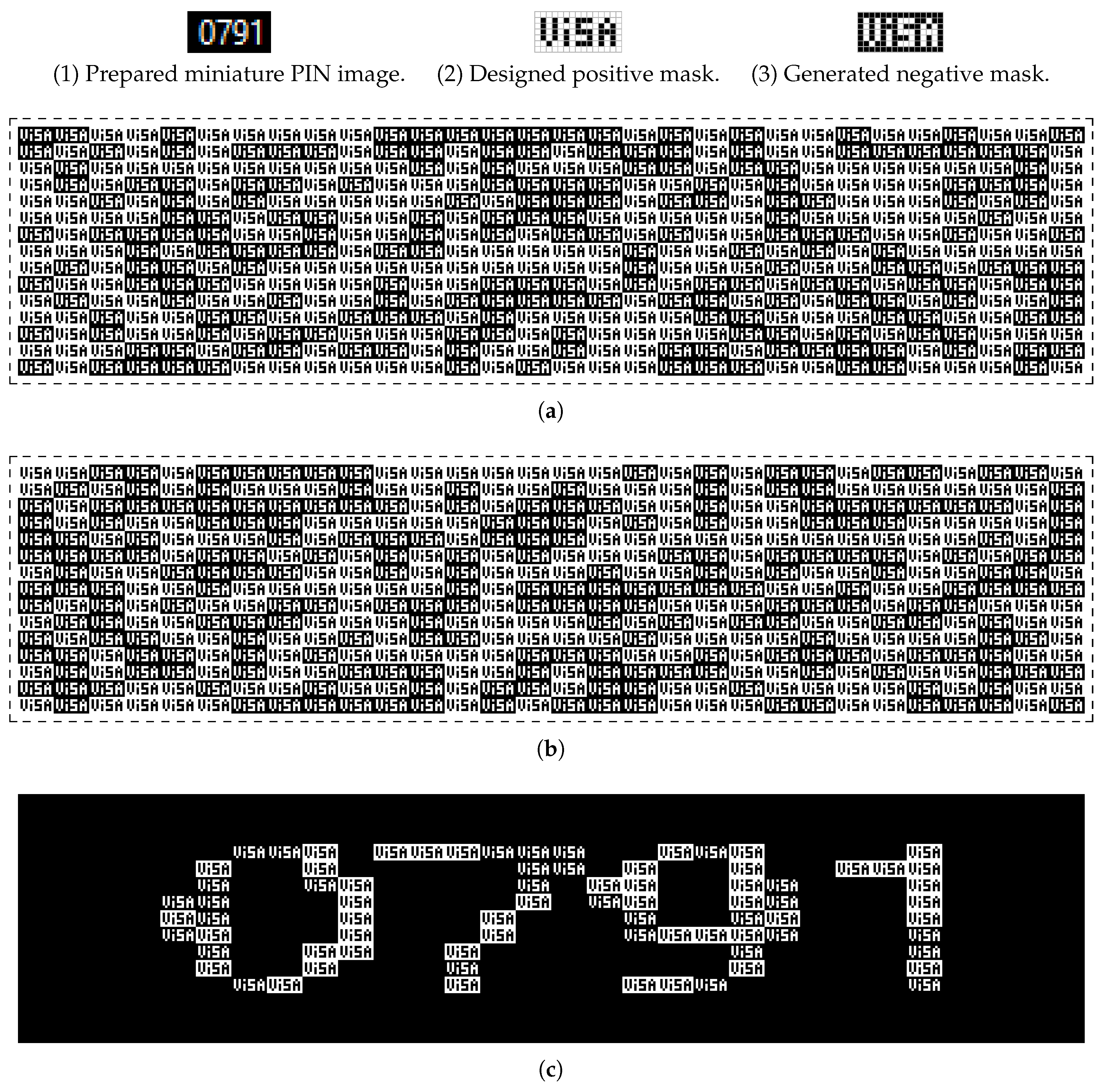
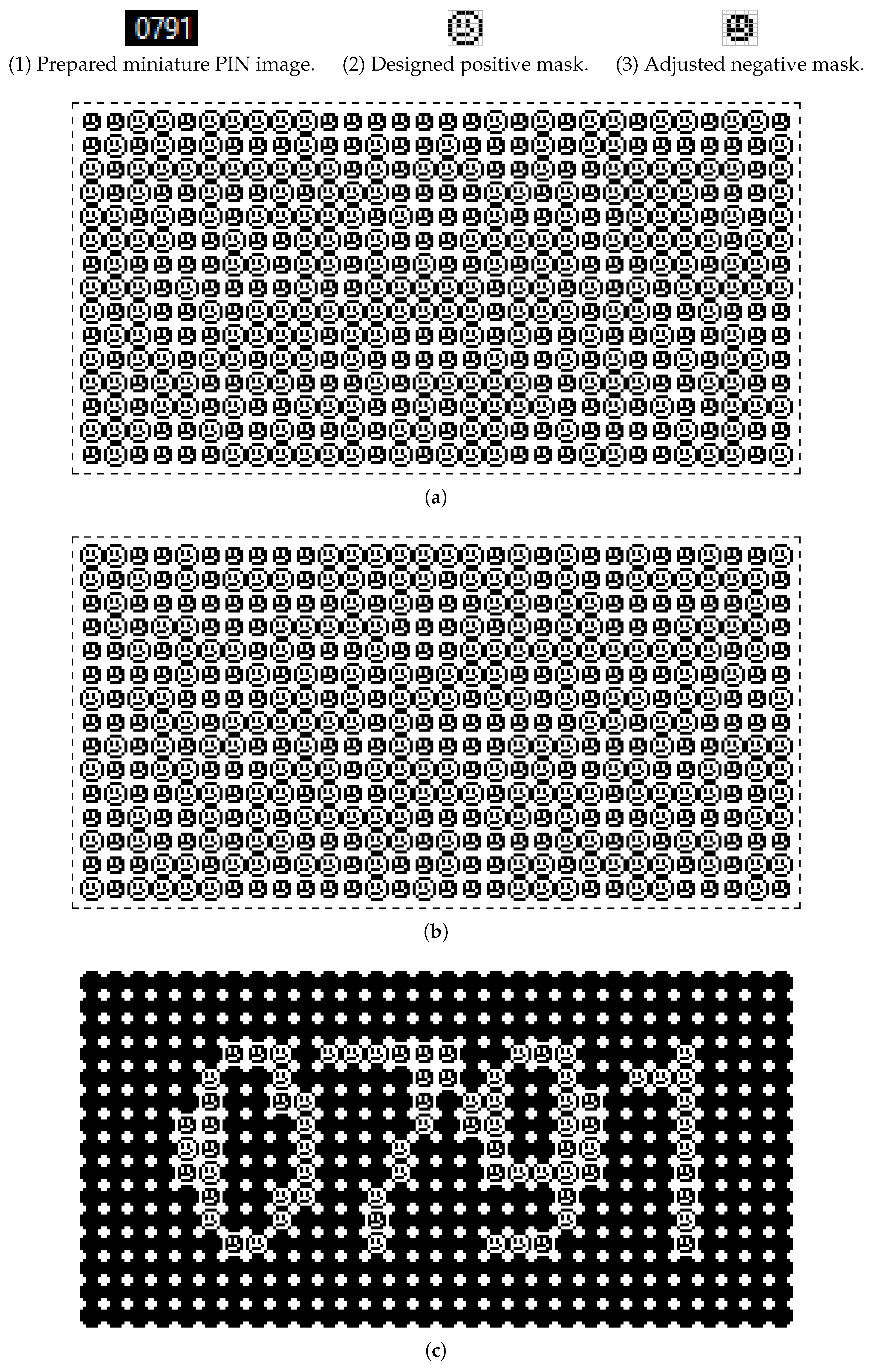
The proposed personalization VC scheme has been applied to a conventional PIN image of size
that is composed of four digits (
Figure 10(1)). Accordingly, pairs of personalized shares have been generated by designing two different pictogram-based masks; namely, from a visa logo for business promotion (
Figure 10(2,3)) and from an emoticon for a visually pleasant stylization (
Figure 11(2,3)). In both cases, aesthetic and expressive shares have been produced.
More precisely, the designed logo-based positive and negative masks are totally complementary. Once stacked, they produce an entirely black rectangular mask that provides an entirely black background. Designed logo-based masks of size
produce shares of size
(
Figure 10a,b). The readability ratio for the used positive mask (first left column)
permits one to visually decode the message (see the superposed shares in
Figure 10c).
The designed emoticon-based positive and negative masks are partially complementary due to the adjustment of the generated negative mask that has been operated towards obtaining aesthetic shares (without significant boundary effects; see
Figure 11a,b). Once shares are stacked (
Figure 11c), the resulting background looks like a set of adjacent black disks showing white pixels in between (type of repeated noise). Hence, the adjustment of masks can engender a not totally black background. However, it is worth mentioning that the attention is focused on producing personalized shares having the best visual quality while their superpositions keep the message readable. Indeed, the presence of low repeated noise with stacked shares does not affect the message reading through human vision. The designed emoticon-based masks of size
produce shares of size
. The readability ratios for the designed positive mask and the adjusted negative mask respectively are
and
. Such values of the readability ratio permit one to decode the message visually (
Figure 11c). These readability ratios of emoticon-based masks are closer to 0.5 than the ones of the logo-based masks. Accordingly, it can be observed that the most readable message, once shares are superposed, is the emoticon-based one.
In summary, the shares that have been generated from two designed pictogram-based masks of different natures (logo-based in
Figure 10a,b and emoticon-based in
Figure 11a,b) are more aesthetic than the traditional ones (
Figure 3b,c). On the one hand, a visual advertising message is communicated, and on the other hand, a visually pleasant appearance is provided. The proposed personalization of share appearances can exploit a variety of logos, icons or ideograms through paper-based or digital supports. Furthermore, both personalized shares permit one to decode the secret code visually once superposed. Each presented pair of shares can be printed (e.g., on a transparent sheet) and superposed together to observe their embedded secret information.
Besides, we previously emphasized that generating personalized shares can increase the security of their embedded secret message, e.g., in the case of digital communication through computer networks. Indeed, if an automated system intercepts a pair of shares, then the automated recognition of the code via an OCR (Optical Character Recognition) will be difficult since the intercepted shares are noised when superposed (e.g., writings drawn from a mix of positive and negative pictogram-based masks).
Table 1 shows the evaluation of the robustness for superposed shares to the decoding of information by well-known OCR systems. As can be seen, one OCR has successfully recognized the code that is contained in the image of stacked traditional shares. However, none of the tested OCR systems have recognized the code from stacked personalized shares. In this latter case, either erroneous writings are detected or no text is detected. Notably, an OCR system can be duped by the writing of the pictogram-based masks (e.g., detected visa letters from the Google Docs OCR).
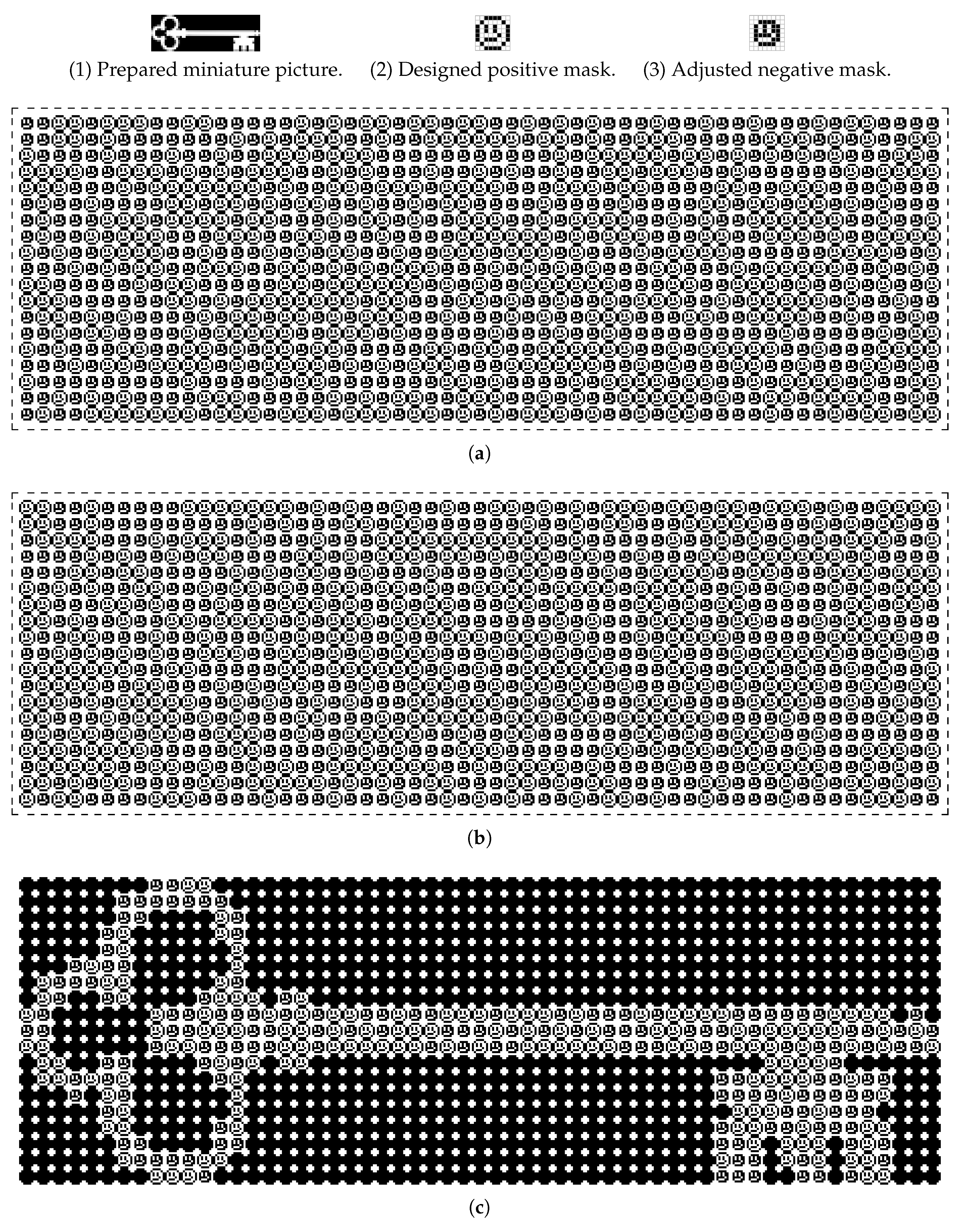
As a last experiment, the designed emoticon-based masks of size
have been matched with the image of a secret picture (from OCAL (Open Clip Art Library)) of size
(see
Figure 12(1)). Personalized shares have been produced with a size of
and with visually pleasant stylized appearances (
Figure 12a,b). The secret picture is easily recognizable once shares are stacked, as can be seen in
Figure 12c. Hence, the proposed pictogram-based personalization of share appearances can also be exploited for the creation of varied applications related to the visual communication of secret pictures (e.g., for visual effects or games).
4. Conclusions and Future Works
A technique has been presented for extending the traditional VC scheme towards the personalization of shares. This personalization technique has been primarily designed for applications related to the communication of secret numeric codes. In contrast with the existing techniques, the proposed method permits the incorporation of visible and readable information at share surfaces while embedding a secret numerical code. A category of dual-use VC shares is thus highlighted. Performances of the proposed method have been presented through a potential application of VC for the communication of a PIN number. Experimental results show effective share personalization and its potential use as a new medium of communication for business promotion and for the creation of visually pleasant appearances. It has been shown that the personalization of shares can also be effective in the communication of secret pictures. Moreover, personalized shares can make the decoding of a secret code more secure than with traditional shares. Indeed, stacked personalized shares show the secret part textured with pictograms and possibly even a noised background, which make the reading of the secret code difficult for Optical Character Recognition systems.
Future works may investigate the personalization of VC shares by exploiting a mix of varied pictograms. For instance, positive and negative masks can be created for each letter of an alphabet. Then, shares can be mapped by letter masks with respect to letters of a selected text. In this way, secret information such as a numeric code can be hidden in texts (i.e., shares mapped with letter-based pictograms). Moreover, works may tackle the development of a colorization method for the proposed pictogram-based VC technique. Furthermore, a case study could be undertaken for evaluating the potential use of personalized shares towards the generation of a new type of CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart).