Essential Multi-Secret Image Sharing for Sensor Images
Abstract
1. Introduction
2. Related Work and Motivation
3. The Proposed Method
- (1)
- If the amount of shadows from the mth essential shadow set is obtained as less than , then the secret images SIm, SIm+1, …, SIr+1 cannot be restored.
- (2)
- If for each i = 1, 2, …, m, the amount of shadows obtained from the ith essential shadow set is , then the secret images SI1, SI2, …, SIm can be restored.
- (3)
- Obtaining all essential shadows and at least non-essential shadows can restore all secret images.
- For each secret image , an invertible rearranging matrix is used to rearrange all pixel positions, resulting in the rearranged images . Each rearranged image is then segmented into several sectors, each containing t1 pixels.
- For each shadow holder’s parameter x, the corresponding initial image segment T(x)= {} is generated.
- The first essential shadow set is assigned as the first initial shadow subset . XOR operations are performed on all the shadows in the first essential shadow subset , and the result is the first masked shadow. Let j = 1.
- XOR operations are performed between the jth initial shadow set and the jth cover shadow to obtain the (j + 1)th essential shadow set . XOR operations are performed on all the shadows in the (j + 1)th essential shadow set , and the result is the (j + 1)th cover shadow.
- The value of j is added to 1, and step (4) is returned to if j is less than r.
- The XOR operation is performed between the initial shadow set with the rth cover shadow to obtain the non-essential image storage .
- The first shadow set , i.e., the initial shadow set , is used to restore the rearranged secret image, . The XOR operation is performed on all shadows in the initial shadow set to obtain the first cover shadow. Let j = 1.
- The XOR operation is performed on the jth cover shadow with the (j + 1)th essential shadow set to obtain the initial shadow set . Then, the obtained initial shadow set is combined to gain Next, is used to restore the secret images. The XOR operation is performed on the (j + 1)th essential shadow set to obtain the (j + 1)th cover shadows.
- The value of j is added to 1, and if j is less than i, step 2 is repeated.
- The restored rearranged secret images use the inverse of the invertible rearranging matrix during encoding to obtain the distortion-free secret images .
- The first shadow set , i.e., the initial shadow set , is used to restore the rearranged secret image, . The XOR operation is performed on all shadows in the initial shadow set to obtain the first cover shadow. Let j = 1.
- The XOR operation is performed on the jth cover shadow with the (j + 1)th essential shadow set to obtain the initial shadow set . Then, the obtained initial shadow sets are combined. Next, is used to restore the secret images. The XOR operation is performed on the (j + 1)th essential shadow set to obtain the (j + 1)th cover shadows.
- The value of j is added to 1, and if j is less than r, step 2 is repeated.
- The XOR operation is performed on the rth cover shadow with any the non-essential shadow set to obtain the corresponding subset in the initial shadow set . Then, this is combined with the previously obtained initial shadow set . Next, is used to restore the secret images .
- The restored rearranged secret images use the inverse of the invertible rearranging matrix during encoding to obtain the distortion-free secret images .
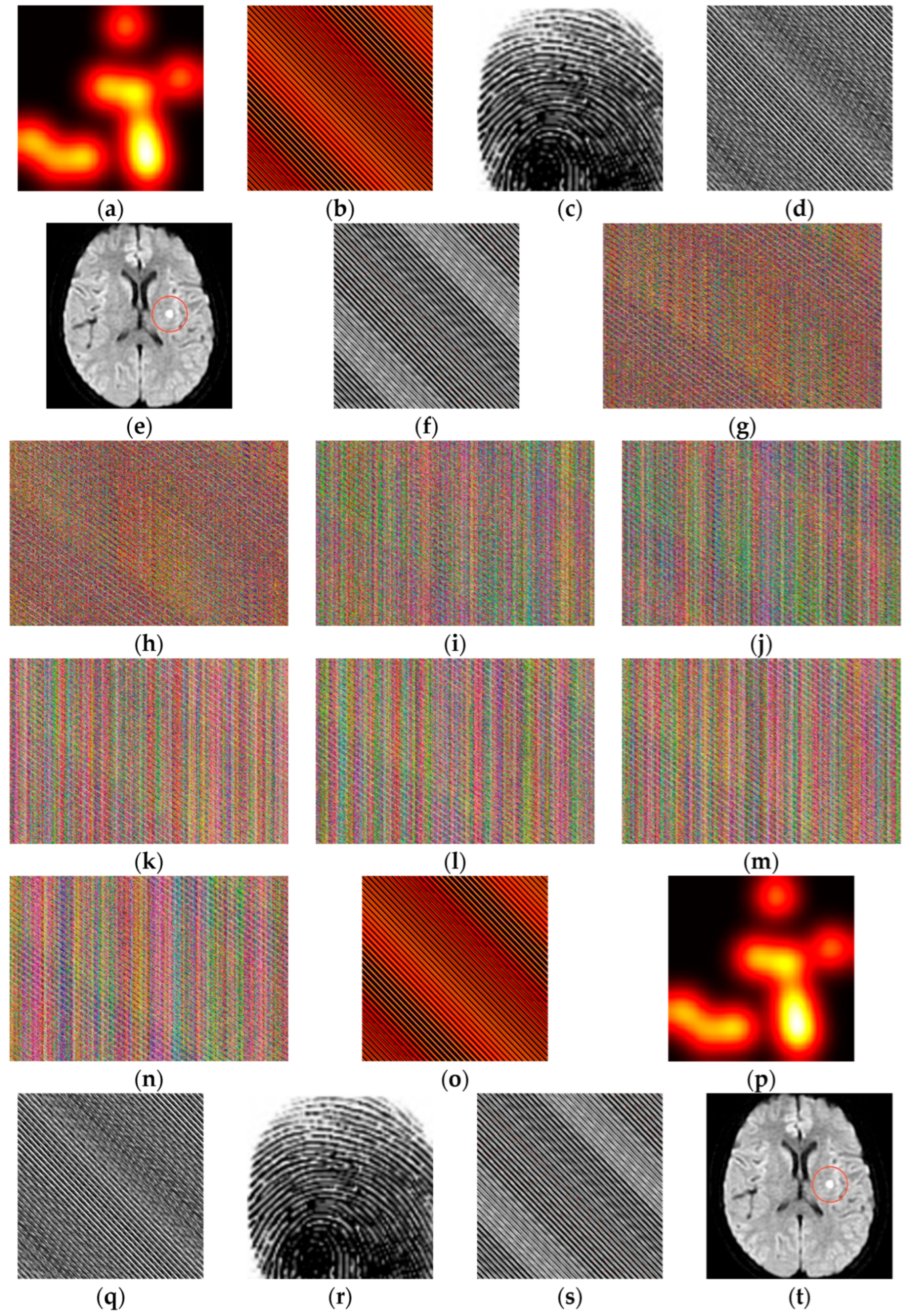
4. Experimental Results
5. Security Analysis
- (1)
- Shadow interception
- (2)
- Collusion attacks
- (3)
- Rearrangement obfuscation
- (4)
- Unauthorized reconstruction
6. Performance Consideration and Comparative Analysis
- (1)
- Computational complexity:
- (2)
- Scalability:
- (3)
- Storage and transmission overhead:
7. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Naor, M.; Shamir, A. Visual Cryptography; Advances in Cryptology–Eurocrypt 94; Springer: Berlin, Germany, 1995; pp. 1–12. [Google Scholar]
- Ibrahim, D.R.; Teh, J.S.; Abdullah, R. An overview of visual cryptography techniques. Multimed. Tools Appl. 2021, 80, 31927–31952. [Google Scholar] [CrossRef]
- Wang, B.; Wang, W.; Zhao, P. A zero-watermark algorithm for multiple images based on visual cryptography and image fusion. J. Vis. Commun. Image Represent. 2022, 87, 103569. [Google Scholar] [CrossRef]
- Chang, C.C.; Hwang, R.J. Sharing secret images using shadow codebooks. Inf. Sci. 1998, 111, 335–345. [Google Scholar] [CrossRef]
- Thien, C.C.; Lin, J.C. Secret image sharing. Comput. Graph. 2002, 26, 765–770. [Google Scholar] [CrossRef]
- Chen, S.K.; Lin, J.C. Fault-tolerant and progressive transmission of images. Pattern Recognit. 2005, 38, 2466–2471. [Google Scholar] [CrossRef]
- Hung, K.H.; Chang, Y.J.; Lin, J.C. Progressive sharing of an image. Opt. Eng. 2008, 47, 047006. [Google Scholar] [CrossRef]
- Wang, X.L.; Xie, D.; Chen, F.L.; Wu, B.; Zen, Y.Y. Progressive and multi-level sharing scheme with hierarchical shadows. Multimed. Tools Appl. 2022, 81, 31039–31059. [Google Scholar] [CrossRef]
- Wu, Y.S.; Thien, C.C.; Lin, J.C. Sharing and hiding secret images with size constraint. Pattern Recognit. 2004, 37, 1377–1385. [Google Scholar] [CrossRef]
- Thien, C.C.; Lin, J.C. An Image-Sharing Method with User-Friendly Shadow Images. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 1161–1169. [Google Scholar] [CrossRef]
- Cheng, J.; Liu, L.; Chen, F.; Jiang, Y. Meaningful Secret Image Sharing with Uniform Image Quality. Mathematics 2022, 10, 3241. [Google Scholar] [CrossRef]
- Wang, R.Z.; Shyu, S.J. Scalable secret image sharing. Signal Process. Image Commun. 2007, 22, 363–373. [Google Scholar] [CrossRef]
- Yang, C.N.; Huang, S.M. Constructions and properties of k out of n scalable secret image sharing. Opt. Commun. 2010, 283, 1750–1762. [Google Scholar] [CrossRef]
- Yang, C.N.; Chu, Y.Y. A general (k, n) scalable secret image sharing scheme with the smooth scalability. J. Syst. Softw. 2011, 84, 1726–1733. [Google Scholar] [CrossRef]
- Liu, Y.X.; Yang, C.N.; Yeh, P.H. Reducing shadow size in smooth scalable secret image sharing. Secur. Commun. Netw. 2014, 7, 2237–2244. [Google Scholar] [CrossRef]
- Li, P.; Yang, C.N.; Wu, C.C.; Kong, Q.; Ma, Y. Essential secret image sharing scheme with different importance of shadows. J. Vis. Commun. Image Represent. 2013, 24, 1106–1114. [Google Scholar] [CrossRef]
- Yang, C.N.; Li, P.; Wu, C.C.; Cai, S.R. Reducing shadow size in essential secret image sharing by conjunctive hierarchical approach. Signal Process. Image Commun. 2015, 31, 1–9. [Google Scholar] [CrossRef]
- Chen, C.C.; Tsai, Y.H. An expandable essential secret image sharing structure. J. Inf. Hiding Multimed. Signal Process. 2016, 7, 135–144. [Google Scholar]
- Chen, S.K. Essential secret image sharing with increasable shadows. Opt. Eng. 2016, 55, 013103. [Google Scholar] [CrossRef]
- Chen, C.C.; Chen, S.C. Two-layered structure for optimally essential secret image sharing scheme. J. Vis. Commun. Image Represent. 2016, 38, 595–601. [Google Scholar] [CrossRef]
- Li, P.; Yang, C.N.; Zhou, Z. Essential secret image sharing scheme with the same size of shadows. Digit. Signal Process. 2016, 50, 51–60. [Google Scholar] [CrossRef]
- Chen, C.C. Essential Secret Image Sharing Scheme with Equal-sized Shadows Generation. J. Vis. Commun. Image Represent. 2018, 52, 143–150. [Google Scholar] [CrossRef]
- Yadav, M.; Singh, R. Essential secret image sharing approach with same size of meaningful shares. Multimed. Tools Appl. 2022, 81, 22677–22694. [Google Scholar] [CrossRef]
- Li, P.; Liu, Z.; Yang, C.N. A construction method of (t, k, n)-essential secret image sharing scheme. Signal Process. Image Commun. 2018, 65, 210–220. [Google Scholar] [CrossRef]
- Dehkordi, M.H.; Farahi, S.T.; Mashhadi, S. LWE-Based Verifiable Essential Secret Image Sharing Scheme ((t, s, k, n)-VESIS). IET Image Process. 2024, 18, 1053–1072. [Google Scholar] [CrossRef]
- Chattopadhyay, A.K.; Saha, S.; Nag, A.; Singh, J.P. A verifiable multi-secret image sharing scheme based on DNA encryption. Multimed. Tools Appl. 2025, 84, 1967–1983. [Google Scholar] [CrossRef]
| Feature/Method | Proposed EMSIS Scheme | (t, s, k, n)-ESS [25] | DNA-Multi-SIS [26] |
|---|---|---|---|
| Recovery type | Lossless | Lossless | Lossless |
| Hierarchical recovery | Yes | No | No |
| Fault tolerance (non-essential shadows) | Yes | Limited | No |
| Shadow size uniformity | Adjustable | Fixed | Fixed |
| Context-aware reconstruction (e.g., sensor data) | Yes | No | No |
| Resistance to partial shadow attack | High | Moderate | Low |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, S.-K. Essential Multi-Secret Image Sharing for Sensor Images. J. Imaging 2025, 11, 228. https://doi.org/10.3390/jimaging11070228
Chen S-K. Essential Multi-Secret Image Sharing for Sensor Images. Journal of Imaging. 2025; 11(7):228. https://doi.org/10.3390/jimaging11070228
Chicago/Turabian StyleChen, Shang-Kuan. 2025. "Essential Multi-Secret Image Sharing for Sensor Images" Journal of Imaging 11, no. 7: 228. https://doi.org/10.3390/jimaging11070228
APA StyleChen, S.-K. (2025). Essential Multi-Secret Image Sharing for Sensor Images. Journal of Imaging, 11(7), 228. https://doi.org/10.3390/jimaging11070228





