Symmetry Detection for Quadratic Optimization Using Binary Layered Graphs
Abstract
1. Introduction
2. Formulation Symmetry for Quadratically-Constrained Quadratic Optimization Problems
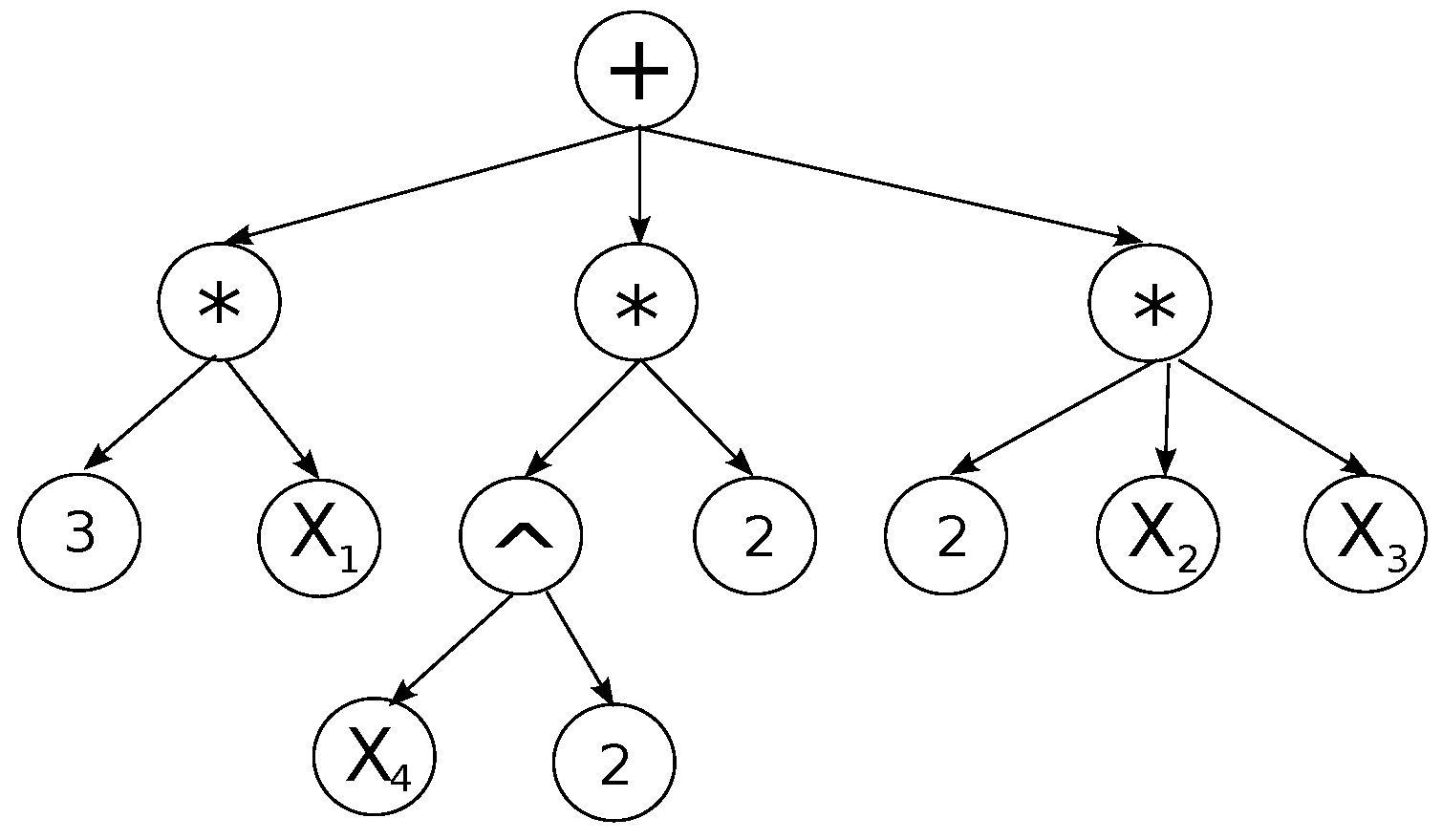
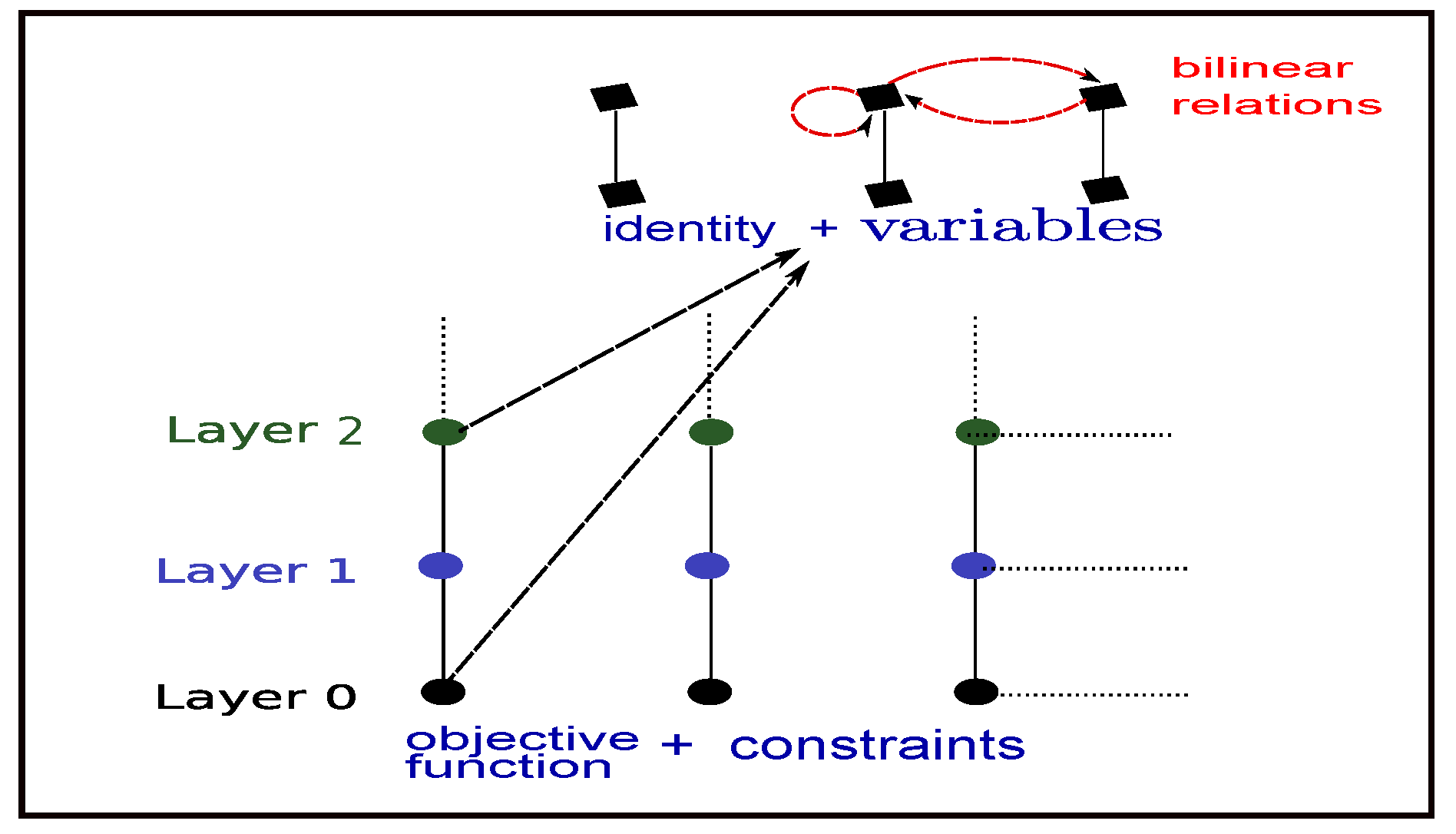
2.1. Symmetry Detection with Expression Graphs
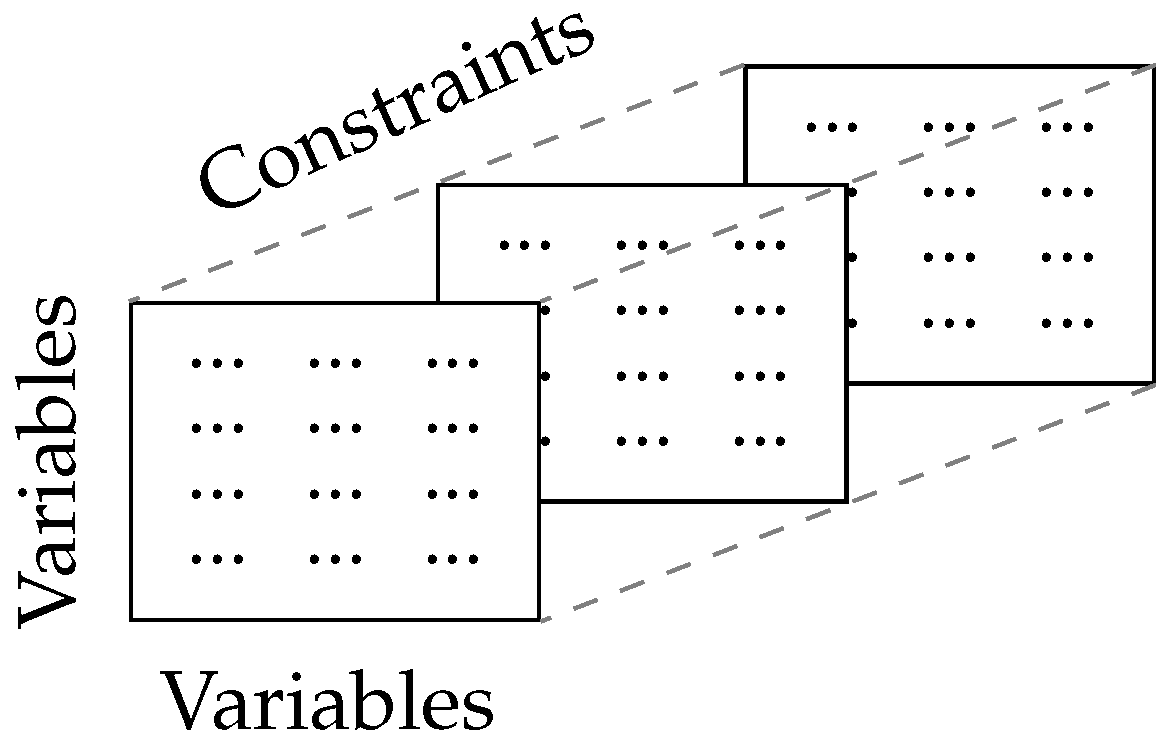
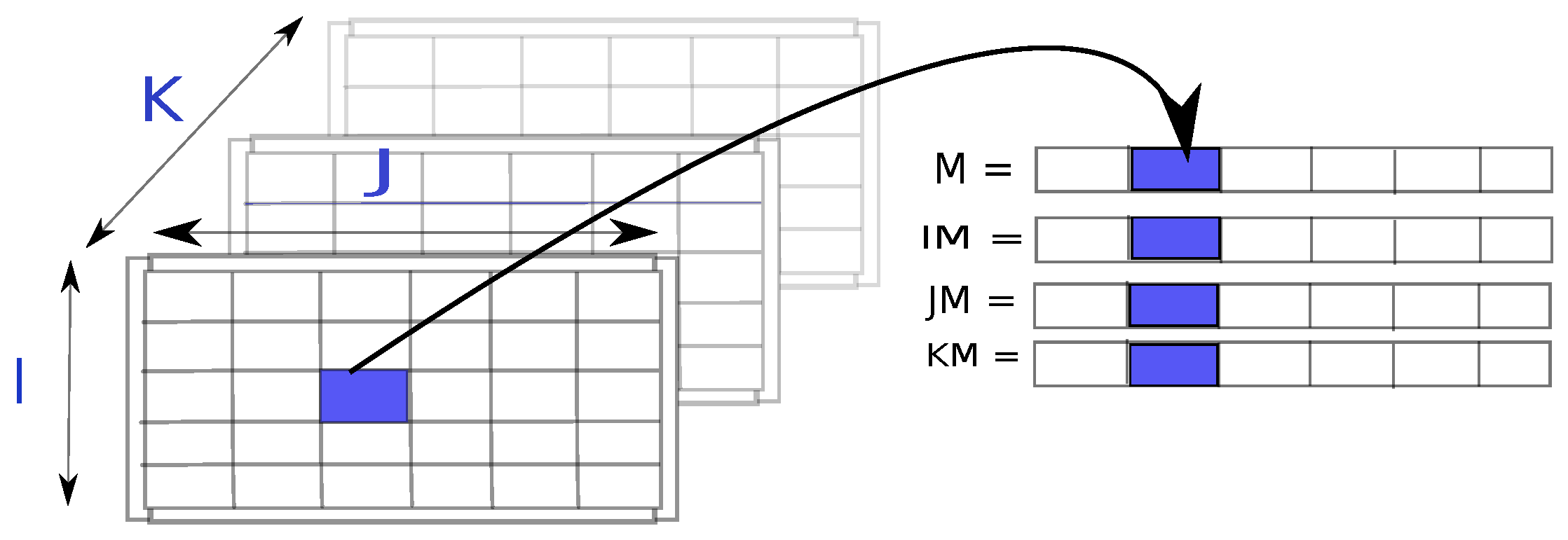
2.2. Symmetry Detection with Tensors
2.2.1. Sparse Tensor Representation
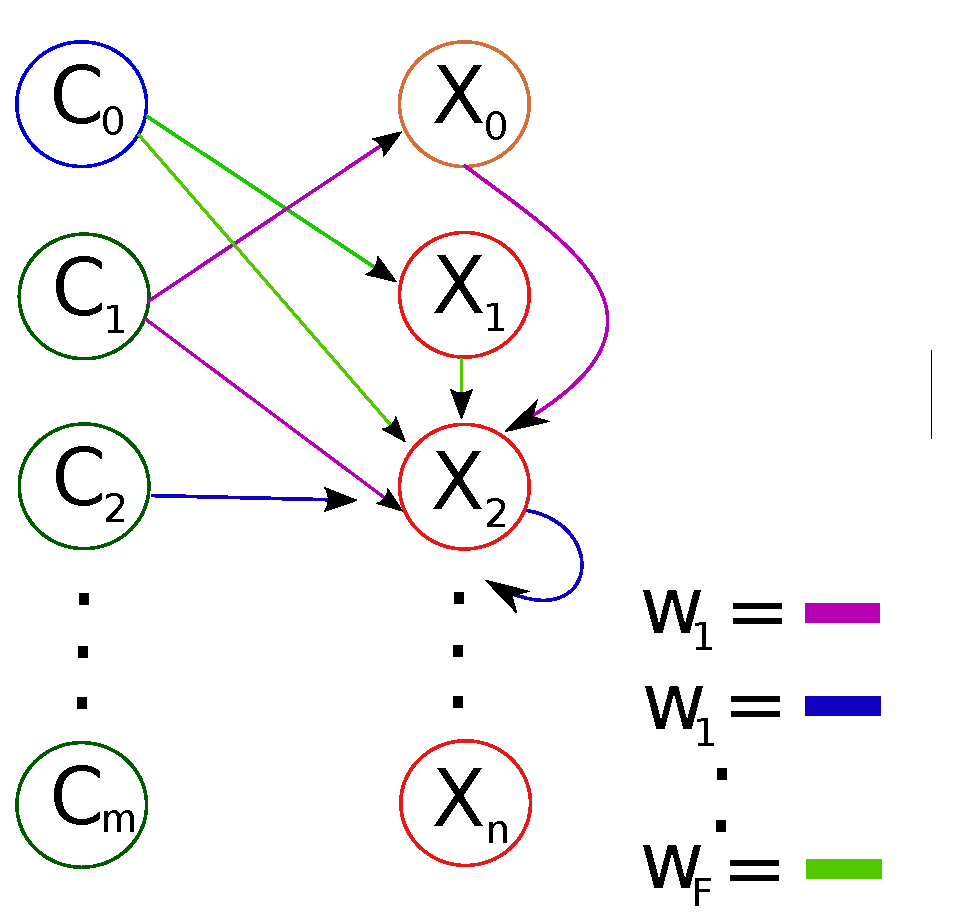
2.2.2. Converting Matrices to Edge-Labeled, Vertex-Colored Graphs
- If , i.e., a quadratic term, then .
- else for bilinear term, , then
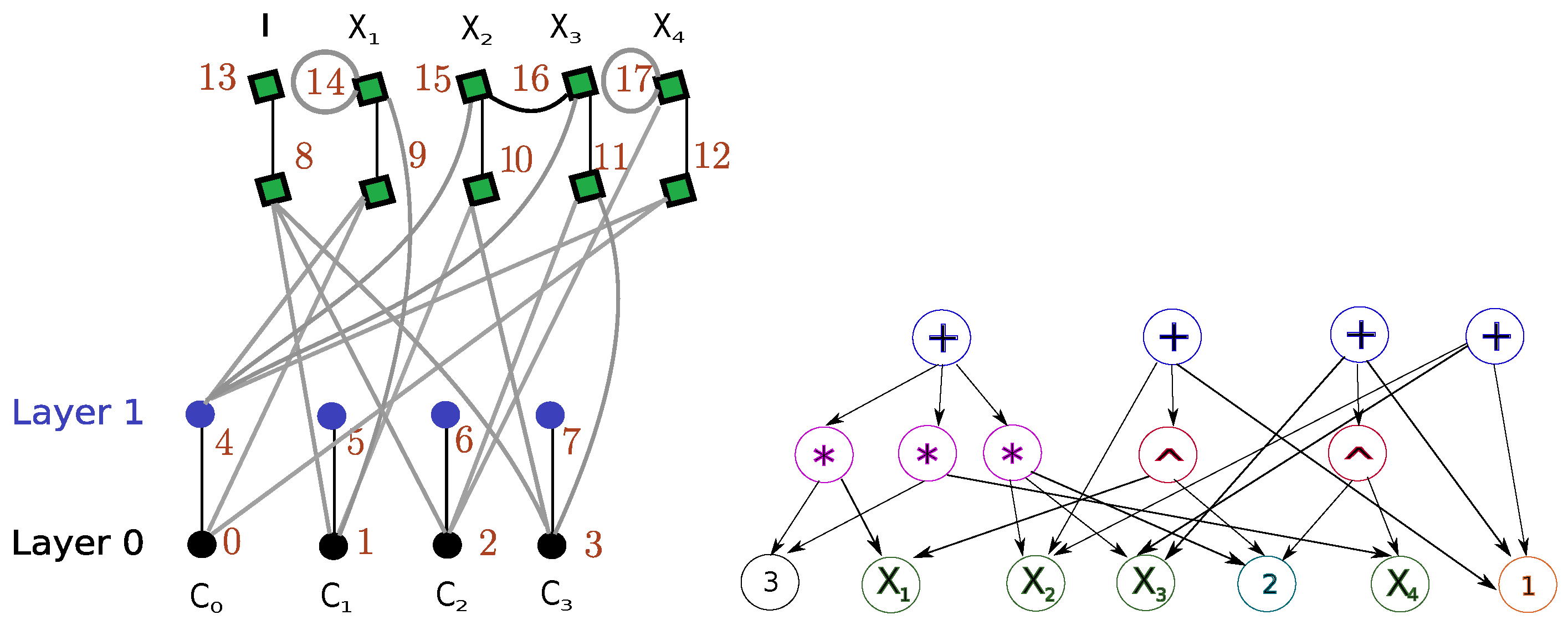
3. Formulation Symmetry Detection via Binary Layered Graphs
| Algorithm 1 Algorithm constructing the vertex set |
|
| Algorithm 2 Algorithm constructing the edge set |
|
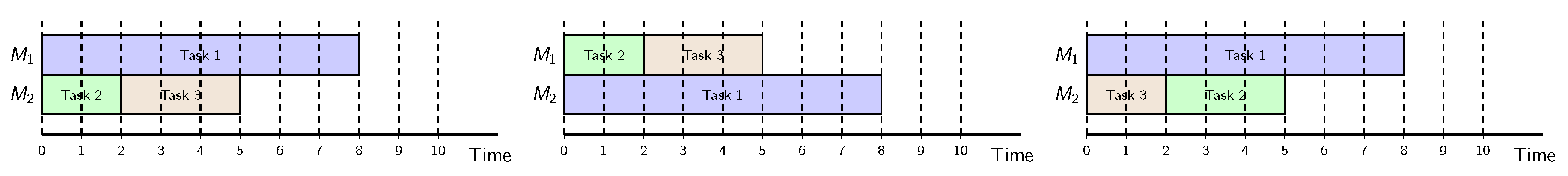
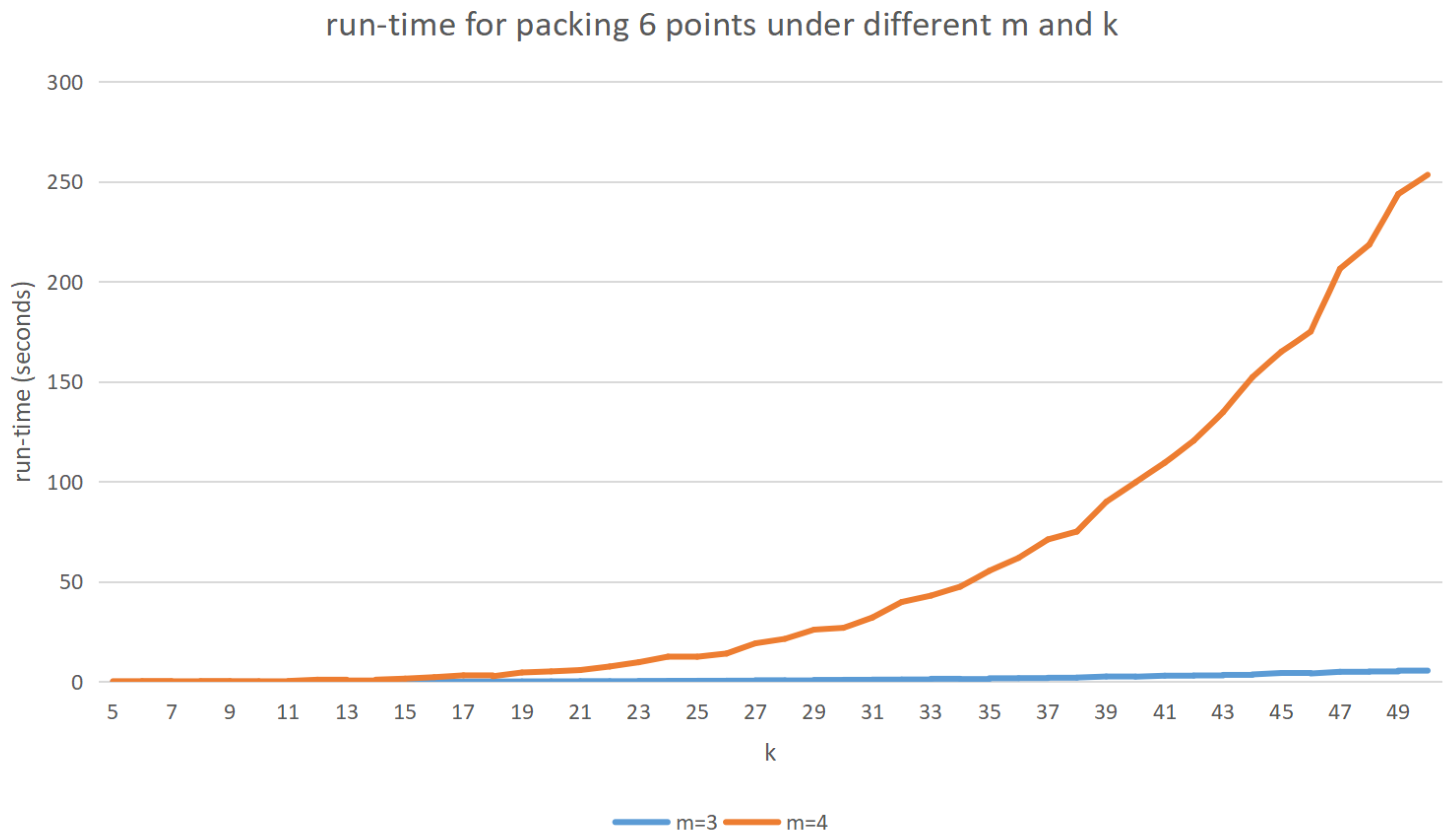
4. Numerical Discussion and Comparison to the State-of-the-Art
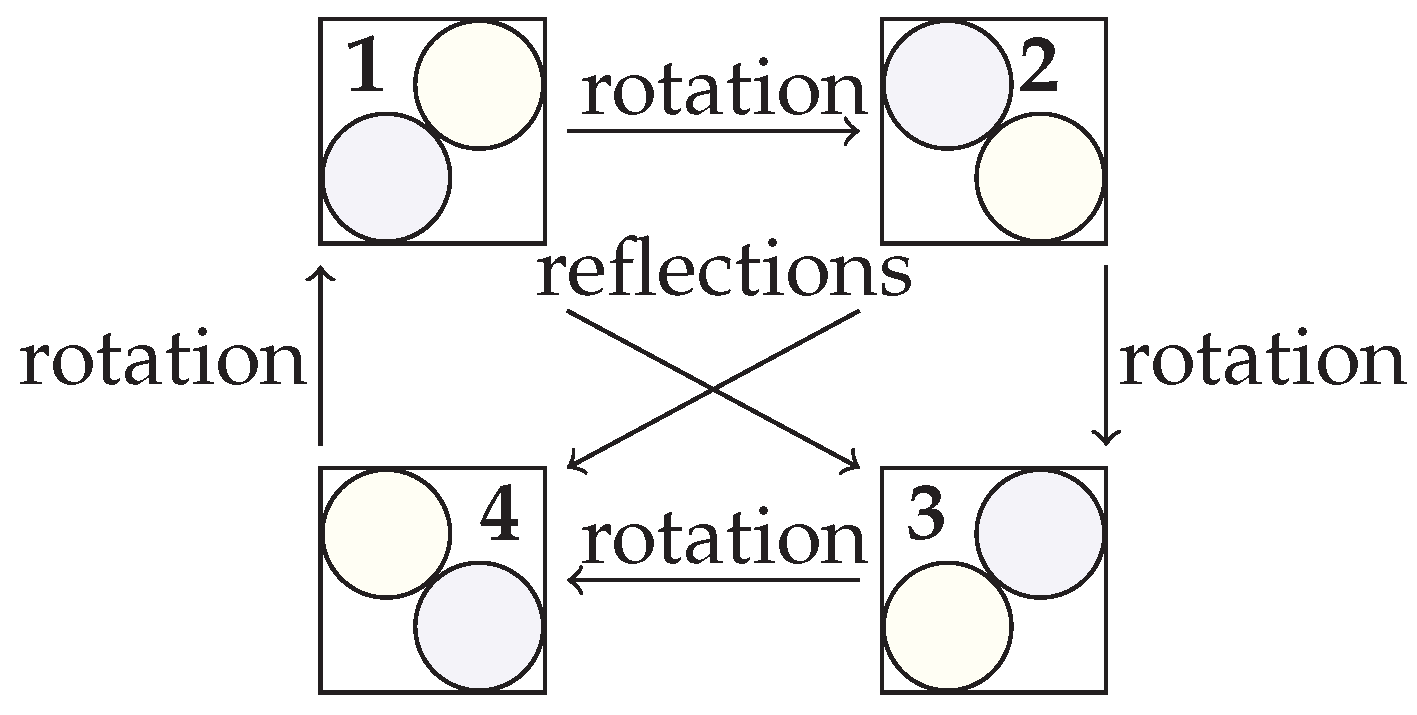
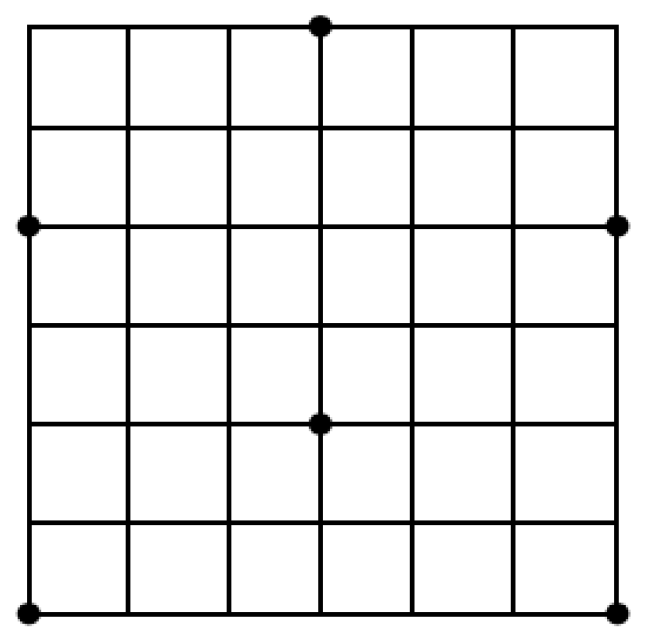
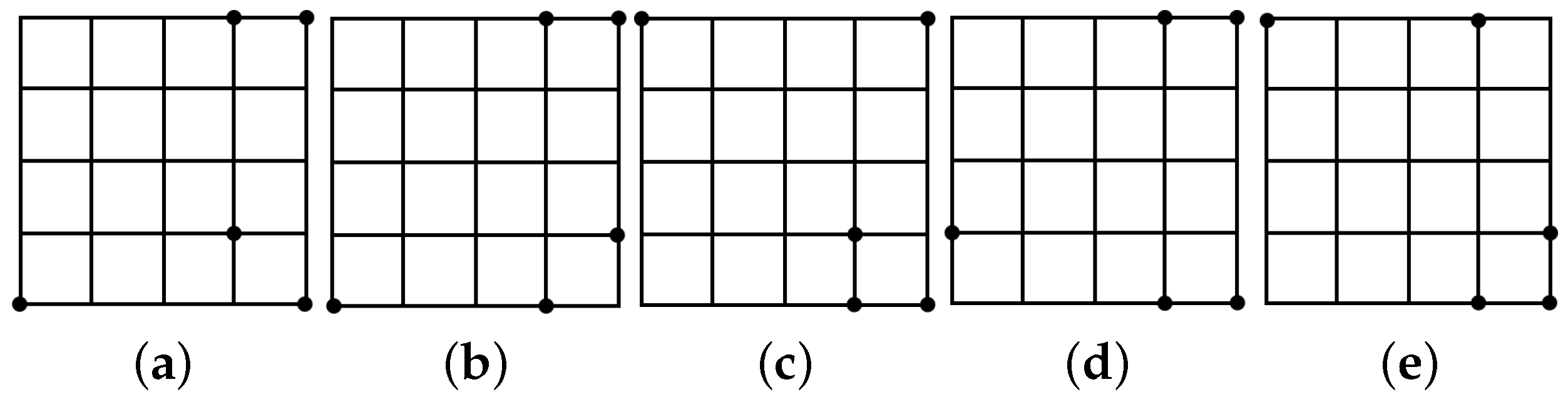
5. Exploiting Symmetry in the Point Packing Problem
Exhaustive Search and 2D Symmetry Removal
| Algorithm 3 Algorithm 1—Exhaustive Search |
| Input: number of points n, number of grids k, number of occupied grids m. Output: The optimal solution
|
| Algorithm 4 Algorithm 2—2D Symmetry Removal |
| Input: number of points n, number of grids k, number of occupied grids m. Output: The optimal solution
|
- One point on , 2 points on and 2 points on . This is from .
- Two points on , 1 point on and 2 points on . This is from .
6. Results and Comparisons
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| MINLP | Mixed-integer nonlinear optimization |
| QCQP | Quadratically-constrained quadratic optimization |
References
- Margot, F. Symmetry in Integer Linear Programming. In 50 Years of Integer Programming 1958–2008: From the Early Years to the State-of-the-Art; Springer: Berlin/Heidelberg, Germany, 2010; pp. 647–686. [Google Scholar]
- Liberti, L. Reformulations in mathematical programming: Automatic symmetry detection and exploitation. Math. Program. 2012, 131, 273–304. [Google Scholar] [CrossRef]
- Costa, A.; Hansen, P.; Liberti, L. On the impact of symmetry-breaking constraints on spatial Branch-and-Bound for circle packing in a square. Discret. Appl. Math. 2013, 161, 96–106. [Google Scholar] [CrossRef]
- Puget, J.F. Automatic Detection of Variable and Value Symmetries. In Proceedings of the 11th International Conference on Principles and Practice of Constraint Programming—CP 2005, Sitges, Spain, 1–5 October 2005; van Beek, P., Ed.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 475–489. [Google Scholar]
- Salvagnin, D. A Dominance Procedure for Integer Programming. Master’s Thesis, University of Padua, Padua, Italy, 2005. [Google Scholar]
- Berthold, T.; Pfetsch, M. Detecting Orbitopal Symmetries. In Proceedings of the Annual International Conference of the German Operations Research Society (GOR), Augsburg, Germany, 3–5 September 2008; Springer: Berlin/Heidelberg, Germany, 2009; pp. 433–438. [Google Scholar]
- Bremner, D.; Dutour Sikirić, M.; Pasechnik, D.V.; Rehn, T.; Schürmann, A. Computing symmetry groups of polyhedra. LMS J. Comput. Math. 2014, 17, 565–581. [Google Scholar] [CrossRef]
- Knueven, B.; Ostrowski, J.; Pokutta, S. Detecting almost symmetries of graphs. Math. Program. Comput. 2018, 10, 143–185. [Google Scholar] [CrossRef]
- Sherali, H.D.; Smith, J.C. Improving Discrete Model Representations via Symmetry Considerations. Manag. Sci. 2001, 47, 1396–1407. [Google Scholar] [CrossRef]
- Liberti, L. Automatic Generation of Symmetry-Breaking Constraints. In Combinatorial Optimization and Applications; Yang, B., Du, D.Z., Wang, C.A., Eds.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 328–338. [Google Scholar]
- Liberti, L.; Ostrowski, J. Stabilizer-based symmetry breaking constraints for mathematical programs. J. Glob. Optim. 2014, 60, 183–194. [Google Scholar] [CrossRef]
- Ghoniem, A.; Sherali, H.D. Defeating symmetry in combinatorial optimization via objective perturbations and hierarchical constraints. IIE Trans. 2011, 43, 575–588. [Google Scholar] [CrossRef]
- Ostrowski, J.; Linderoth, J.; Rossi, F.; Smriglio, S. Constraint Orbital Branching. In Proceedings of the 13th International Conference on Integer Programming and Combinatorial Optimization IPCO, Bertinoro, Italy, 26–28 May 2008; pp. 225–239. [Google Scholar]
- Ostrowski, J.; Linderoth, J.; Rossi, F.; Smiriglio, S. Orbital branching. Math. Program. 2011, 126, 147–178. [Google Scholar] [CrossRef]
- Margot, F. Pruning by isomorphism in branch-and-cut. Math. Program. 2002, 94, 71–90. [Google Scholar] [CrossRef]
- Kaibel, V.; Peinhardt, M.; Pfetsch, M.E. Orbitopal fixing. Discret. Optim. 2011, 8, 595–610. [Google Scholar] [CrossRef]
- Faenza, Y.; Kaibel, V. Extended Formulations for Packing and Partitioning Orbitopes. Math. Oper. Res. 2009, 34, 686–697. [Google Scholar] [CrossRef]
- Pfetsch, M.E.; Rehn, T. A computational comparison of symmetry handling methods for mixed integer programs. Math. Program. Comput. 2019, 11, 37–93. [Google Scholar] [CrossRef]
- Margot, F. Small covering designs by branch-and-cut. Math. Program. 2003, 94, 207–220. [Google Scholar] [CrossRef]
- Costa, A.; Liberti, L.; Hansen, P. Formulation symmetries in circle packing. Electron. Notes Discret. Math. 2010, 36, 1303–1310. [Google Scholar] [CrossRef]
- Ostrowski, J.; Vannelli, A.; Anjos, M.F. Symmetry in Scheduling Problems; Cahier du GERAD G-2010-69; GERAD: Montreal, QC, Canada, 2010. [Google Scholar]
- Ostrowski, J.; Wang, J.; Liu, C. Exploiting Symmetry in Transmission Lines for Transmission Switching. IEEE Trans. Power Syst. 2012, 27, 1708–1709. [Google Scholar] [CrossRef]
- Ostrowski, J.; Wang, J. Network reduction in the Transmission-Constrained Unit Commitment problem. Comput. Ind. Eng. 2012, 63, 702–707. [Google Scholar] [CrossRef]
- Ostrowski, J.; Anjos, M.F.; Vannelli, A. Modified orbital branching for structured symmetry with an application to unit commitment. Math. Program. 2015, 150, 99–129. [Google Scholar] [CrossRef]
- Lima, R.M.; Novais, A.Q. Symmetry breaking in MILP formulations for Unit Commitment problems. Comput. Chem. Eng. 2016, 85, 162–176. [Google Scholar] [CrossRef]
- Knueven, B.; Ostrowski, J.; Wang, J. The Ramping Polytope and Cut Generation for the Unit Commitment Problem. INFORMS J. Comput. 2018, 30, 739–749. [Google Scholar] [CrossRef]
- Kouyialis, G.; Misener, R. Detecting Symmetry in Designing Heat Exchanger Networks. In Proceedings of the International Conference of Foundations of Computer-Aided Process Operations-FOCAPO/CPC, Tucson, AZ, USA, 8–12 January 2017. [Google Scholar]
- Letsios, D.; Kouyialis, G.; Misener, R. Heuristics with performance guarantees for the minimum number of matches problem in heat recovery network design. Comput. Chem. Eng. 2018, 113, 57–85. [Google Scholar] [CrossRef]
- Maravelias, C.T.; Grossmann, I.E. A hybrid MILP/CP decomposition approach for the continuous time scheduling of multipurpose batch plants. Comput. Chem. Eng. 2004, 28, 1921–1949. [Google Scholar] [CrossRef]
- Maravelias, C.T. Mixed-Time Representation for State-Task Network Models. Ind. Eng. Chem. Res. 2005, 44, 9129–9145. [Google Scholar] [CrossRef]
- Mistry, M.; Callia D’Iddio, A.; Huth, M.; Misener, R. Satisfiability modulo theories for process systems engineering. Comput. Chem. Eng. 2018, 113, 98–114. [Google Scholar] [CrossRef]
- Smith, E.M.B.; Pantelides, C.C. A symbolic reformulation/spatial branch-and-bound algorithm for the global optimisation of nonconvex MINLPs. Comput. Chem. Eng. 1999, 23, 457–478. [Google Scholar] [CrossRef]
- Tawarmalani, M.; Sahinidis, N.V. A polyhedral branch-and-cut approach to global optimization. Math. Program. 2005, 103, 225–249. [Google Scholar] [CrossRef]
- Belotti, P.; Lee, J.; Liberti, L.; Margot, F.; Wachter, A. Branching and Bounds Tightening techniques for Non-convex MINLP. Optim. Methods Softw. 2009, 24, 597–634. [Google Scholar] [CrossRef]
- Youdong, L.; Linus, S. The global solver in the LINDO API. Optim. Methods Softw. 2009, 24, 657–668. [Google Scholar]
- Misener, R.; Floudas, C.A. ANTIGONE: Algorithms for coNTinuous/Integer Global Optimization of Nonlinear Equations. J. Glob. Optim. 2014, 59, 503–526. [Google Scholar] [CrossRef]
- Vigerske, S. Decomposition in Multistage Stochastic Programming and a Constraint Integer Programming Approach to Mixed-Integer Nonlinear Programming. Ph.D. Thesis, Humboldt-Universität zu Berlin, Berlin, Germany, 2013. [Google Scholar]
- Mahajan, A.; Leyffer, S.; Linderoth, J.; Luedtke, J.; Munson, T. Minotaur: A mixed-integer nonlinear optimization toolkit. Optim. Online 2017, 6275. [Google Scholar]
- Boukouvala, F.; Misener, R.; Floudas, C.A. Global optimization advances in Mixed-Integer Nonlinear Programming, MINLP, and Constrained Derivative-Free Optimization, CDFO. Eur. J. Oper. Res. 2016, 252, 701–727. [Google Scholar] [CrossRef]
- Fourer, R.; Maheshwari, C.; Neumaier, A.; Orban, D.; Schichl, H. Convexity and concavity detection in computational graphs: Tree walks for convexity assessment. INFORMS J. Comput. 2010, 22, 26–43. [Google Scholar] [CrossRef]
- Hart, W.E.; Laird, C.; Watson, J.; Woodruff, D.L. Pyomo: Modeling and solving mathematical programs in python. Math. Program. Comput. 2011, 3, 219–260. [Google Scholar] [CrossRef]
- Ceccon, F.; Siirola, J.D.; Misener, R. SUSPECT: MINLP special structure detector for Pyomo. Optim. Lett. 2019. [Google Scholar] [CrossRef]
- McKay, B.D.; Piperno, A. Practical graph isomorphism, II. J. Symb. Comput. 2014, 60, 94–112. [Google Scholar] [CrossRef]
- Ramani, A.; Aloul, F.; Markov, I.; Sakallah, K.A. Breaking instance-independent symmetries in exact graph coloring. J. Artif. Intell. Res. 2006, 1, 324–329. [Google Scholar] [CrossRef]
- Ramani, A.; Markov, I.L. Automatically Exploiting Symmetries in Constraint Programming. In Recent Advances in Constraints; Faltings, B.V., Petcu, A., Fages, F., Rossi, F., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 98–112. [Google Scholar]
- Anstreicher, K.M. Semidefinite programming versus the reformulationlinearization technique for nonconvex quadratically constrained quadratic programming. J. Glob. Optim. 2009, 43, 471–484. [Google Scholar] [CrossRef]
- Misener, R.; Floudas, C.A. Global optimization of mixed-integer quadratically-constrained quadratic programs (MIQCQP) through piecewise-linear and edge-concave relaxations. Math. Program. 2012, 136, 155–182. [Google Scholar] [CrossRef]
- Misener, R.; Floudas, C.A. GloMIQO: Global mixed-integer quadratic optimizer. J. Glob. Optim. 2013, 57, 3–50. [Google Scholar] [CrossRef]
- Furini, F.; Traversi, E.; Belotti, P.; Frangioni, A.; Gleixner, A.; Gould, N.; Liberti, L.; Lodi, A.; Misener, R.; Mittelmann, H. QPLIB: A library of quadratic programming instances. Math. Program. Comput. 2019, 11, 237–265. [Google Scholar] [CrossRef]
- Jones, D.R. A fully general, exact algorithm for nesting irregular shapes. J. Glob. Optim. 2014, 59, 367–404. [Google Scholar] [CrossRef]
- Misener, R.; Smadbeck, J.B.; Floudas, C.A. Dynamically generated cutting planes for mixed-integer quadratically constrained quadratic programs and their incorporation into GloMIQO 2. Optim. Methods Softw. 2015, 30, 215–249. [Google Scholar] [CrossRef]
- Wang, A.; Hanselman, C.L.; Gounaris, C.E. A customized branch-and-bound approach for irregular shape nesting. J. Glob. Optim. 2018, 71, 935–955. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kouyialis, G.; Wang, X.; Misener, R. Symmetry Detection for Quadratic Optimization Using Binary Layered Graphs. Processes 2019, 7, 838. https://doi.org/10.3390/pr7110838
Kouyialis G, Wang X, Misener R. Symmetry Detection for Quadratic Optimization Using Binary Layered Graphs. Processes. 2019; 7(11):838. https://doi.org/10.3390/pr7110838
Chicago/Turabian StyleKouyialis, Georgia, Xiaoyu Wang, and Ruth Misener. 2019. "Symmetry Detection for Quadratic Optimization Using Binary Layered Graphs" Processes 7, no. 11: 838. https://doi.org/10.3390/pr7110838
APA StyleKouyialis, G., Wang, X., & Misener, R. (2019). Symmetry Detection for Quadratic Optimization Using Binary Layered Graphs. Processes, 7(11), 838. https://doi.org/10.3390/pr7110838




