1. Introduction
The integration of blockchain technology and artificial intelligence (AI) in the expanding field of cybersecurity represents a significant transformation that effectively tackles the fundamental issues of conventional IT infrastructures. Centralized systems, which are vulnerable to single points of failure, are increasingly inadequate for securely handling the exponential expansion of data. The decentralized and distributed ledger mechanism of blockchain establishes a strong framework for assuring data integrity using cryptographic hashing and consensus procedures, eliminating the necessity for a central authority, therefore reducing vulnerabilities and augmenting trust in the system. This decentralized approach substantially reduces issues like data tampering and illegal access. Moreover, blockchain’s immutable nature provides an additional layer of transparency, which is crucial for auditing and compliance in security-sensitive environments (
Atlam et al. 2020). AI-driven safe computing employs verified data from blockchain to enhance security protocols, hence advancing predictive analytics, anomaly detection, and adaptive security techniques (
Wang et al. 2019). The suggested AI-driven IT infrastructure, supported by blockchain, overcomes the security deficiencies of current systems while improving the scalability, accuracy, and flexibility of risk mitigation measures in a swiftly changing threat environment.
The collaboration between AI and blockchain technology serves as a potent instrument for augmenting cybersecurity resilience. Blockchain offers a transparent, tamper-resistant framework, suitable for securely storing and sharing data in trustless contexts, thereby preserving the integrity and availability of information even during cyberattacks (
Salama and Al-Turjman 2022). Conversely, the function of AI, especially explainable AI (XAI), meets the growing necessity for interpretability in cybersecurity applications, where opaque models have historically created difficulties in regulated sectors like finance and healthcare (
Giudici and Raffinetti 2022). The integration of these technologies enhances cybersecurity measures and guarantees that risk mitigation methods are data-driven and transparent, addressing the requirements of high-stakes sectors that necessitate auditable decision-making processes.
There are important problems and potential that contemporary financial organizations must face as they embrace AI for risk management across various banking sectors. Findings from a study comparing the banking industries in the United States and Nigeria highlight the critical role that AI plays in mitigating a variety of risks, including credit, market, operational, and compliance concerns. Utilizing advanced analytics, machine learning models, and natural language processing, the U.S. banking sector has achieved a mature deployment of AI. This has improved decision-making, fraud detection, and compliance monitoring (
Bussmann et al. 2020). However, there are still certain obstacles that Nigerian banks must overcome before they can fully embrace AI. These include a dearth of trained AI specialists, regulatory hurdles, and outdated IT infrastructure (
Nnaomah et al. 2024). The potential for AI to revolutionize risk management systems is acknowledged in all regions despite these differences; nonetheless, effective integration will depend on appropriate investments and enabling legislation.
The integration of blockchain and IoT technologies is transforming project risk management, providing innovative tools to improve efficiency and transparency throughout project life cycles. The decentralized ledger of blockchain enables secure and immutable data exchange over distributed networks, whereas IoT allows for real-time data collecting, facilitating automated decision-making, and enhancing accuracy in risk assessments (
El Khatib et al. 2023). This integration enables project managers to deploy smart contracts and create peer-to-peer networks that optimize project processes, encompassing planning, execution, risk mitigation, and closure (
El Khatib et al. 2023). Furthermore, utilizing explainable AI techniques like the Shapley–Lorenz decomposition improves interpretability, enabling stakeholders to comprehend and verify AI-generated judgments concerning cyber risk management (
Giudici and Raffinetti 2022). The integration of these technologies improves operational efficiency and ensures transparency, making risk mitigation measures auditable and adaptable to changing project contexts.
Although blockchain and AI technologies have demonstrated potential in various domains, their comprehensive integration for organizational risk management remains underdeveloped. Traditional risk management frameworks often rely on static, siloed processes that lack the adaptability needed to address evolving cyber threats and organizational challenges (
Giudici and Raffinetti 2022). Blockchain’s immutable and decentralized architecture offers a promising foundation for securing organizational operations and mitigating risks, but its application in dynamic and multi-faceted risk management processes has not been fully realized (
Atlam et al. 2020). Similarly, AI’s capabilities in predictive analytics and anomaly detection are underutilized in the context of proactive and explainable risk mitigation strategies (
Wang et al. 2019). Existing solutions also fall short in integrating these technologies into a unified framework that supports scalability, interoperability, and decision-making across diverse organizational functions (
Bussmann et al. 2020). Addressing these challenges requires an innovative infrastructure that leverages blockchain and AI for a holistic, efficient, and adaptive approach to organizational risk management. Based on these gaps, we propose the following research questions:
RQ1: What are the practical applications of blockchain in securing and scaling risk management systems within organizations?
RQ2: How can AI technologies be utilized to enhance the precision of risk predictions and the effectiveness of mitigation actions in real-time organizational scenarios?
RQ3: In what ways does the integration of blockchain and AI reshape the design and execution of risk management frameworks in organizational IT infrastructures?
RQ4: Which innovative approaches can organizations adopt to counter evolving cyber threats while maintaining operational resilience and compliance?
RQ5: How can the proposed riskAIchain framework serve as a robust and scalable infrastructure for comprehensive organizational risk management?
This paper is structured to comprehensively explore the research gaps, research questions, and the proposed solution for organizational IT risk management.
Section 2 provides a background study, establishing the theoretical foundation for integrating blockchain and AI in risk management frameworks.
Section 3 explains the methodology, where the DEMATEL technique is used to identify critical factors and thoughtfully integrate results into the proposed model.
Section 4 examines challenges in traditional IT risk management infrastructures, identifying limitations that necessitate new solutions.
Section 5 outlines emerging cyber threats in the AI world, underscoring the urgency for advanced risk management.
Section 6 explores blockchain and AI in IT risk management, detailing how these technologies enhance security and data integrity.
Section 7 lists the proposed critical factors and use of the DEMATEL technique, prioritizing essential elements for a resilient model.
Section 8 introduces riskAIchain, an AI-driven and blockchain-backed approach, describing the architecture and its ability to address identified challenges. Finally,
Section 9 presents the conclusions and future scope, summarizing key insights and potential areas for expanding this infrastructure’s capabilities.
2. Background
Kuznetsov et al. (
2024) illustrated the disruptive potential of amalgamating AI and blockchain technology to augment the security and transparency of digital systems. Their research highlights that blockchain’s cryptographic features guarantee data immutability and trust independently of centralized authorities, which complements AI’s capacity to examine extensive datasets and discern trends for predictive analytics. This synergy establishes a strong framework for secure data management and proactive threat identification, rendering it especially appropriate for organizational risk management. Nevertheless, the authors emphasize two principal obstacles that arise in such integrations: computational complexity and scalability concerns. The processing requirements of blockchain, particularly in consensus methods, create latency that can impede the real-time decision-making skills of AI systems. As data volume increases, successfully scaling both blockchain and AI while preserving security becomes ever more intricate. These results directly influence the riskAIchain concept, which seeks to utilize both technologies for corporate risk management. It is crucial to address these difficulties within riskAIchain to ensure that the infrastructure can manage large-scale data in real-time while preserving its security benefits.
Polas et al. (
2022) investigated the amalgamation of AI and blockchain in small and medium enterprises (SMEs) in Bangladesh, illustrating how these technologies might transform risk management by improving decision-making precision and mitigating fraud. The authors examined the various advantages of AI’s predictive analytics capabilities and blockchain’s provision of immutable transaction records, which would mitigate organizational risks. Nonetheless, they identified two significant hurdles in this process: insufficient experience and training, as well as resource constraints in SMEs. These obstacles hinder smaller firms from completely embracing and utilizing AI and blockchain technologies for efficient risk management, as these technologies are resource demanding and necessitate a specific level of technical expertise. The riskAIchain model must confront these problems by establishing an infrastructure that is accessible to enterprises with constrained resources and knowledge, thereby facilitating the successful implementation of innovations to improve risk management without burdening smaller entities.
Alabdulatif et al. (
2022) investigated the application of AI and blockchain in intelligent healthcare systems, focusing on data security and cyber risk management. Their research emphasized the capability of employing AI for anomaly detection and blockchain for guaranteeing data integrity, particularly in contexts managing substantial amounts of sensitive information, such as healthcare. The integration of these technologies enhances transparency and security, facilitating real-time monitoring and a secure transfer of patient data among interconnected devices. Nonetheless, the authors recognized two primary challenges: variability in data formats and significant resource utilization. The diverse array of data formats generated by IoT devices in healthcare challenges safe data management and analysis, while blockchain’s resource-intensive operations hinder efficiency in contexts necessitating real-time reactions. These problems are pertinent to the riskAIchain model, which must manage several data sources and guarantee real-time processing capabilities while maintaining security and efficiency.
Elhoseny et al. (
2023) concentrated on the application of AI-driven risk management models to improve security in the bitcoin sector. Their research highlights the significance of employing AI to identify and mitigate risks, especially by evaluating extensive amounts of unstructured data from diverse sources such as social media. Blockchain guarantees data security and immutability; yet a considerable problem emerges in the complexity of precise risk assessment when employing AI models to analyze noisy or extraneous data. Moreover, the computational expense of incessantly monitoring and processing extensive datasets presents an additional challenge, as it may overwhelm system resources. For riskAIchain, these insights indicate that the model must integrate efficient data processing techniques to handle both structured and unstructured data without overburdening system resources, while simultaneously maintaining the precision of AI-driven risk assessments.
Deebak and Al-Turjman (
2021) investigated the application of blockchain and artificial intelligence in privacy-preserving smart contracts, emphasizing cyber risk assessments. Their framework illustrated the capability of integrating AI for fraud detection with blockchain for preserving data privacy and integrity, which is crucial for mitigating corporate risk. Nonetheless, the authors identified two principal challenges: preserving data privacy in decentralized settings and the intricacy of creating secure smart contracts. Decentralized systems exacerbate the safeguarding of sensitive data, as numerous stakeholders may access crucial information, heightening the possibility of unwanted access or manipulation. Moreover, creating safe smart contracts that are impervious to vulnerabilities is exceedingly intricate, as even trivial errors can result in substantial security compromises. These difficulties are pertinent to riskAIchain, which must guarantee that both privacy and contract security are sufficiently resilient to endure future cyber assaults while enabling risk management in decentralized settings. All background study is summarized in
Table 1 with key advantages and key challenges of AI and blockchain.
3. Methodology
In this study, the fuzzy DEMATEL (Decision-Making Trial and Evaluation Laboratory) method was employed to analyze and rank the critical factors influencing the adoption of blockchain technology in IT risk management. The fuzzy DEMATEL approach enables the identification of cause–effect relationships among factors by assessing the interdependencies between them. This process is essential for understanding which factors act as drivers (causal factors) and which are influenced by other factors (effect factors), providing a foundation for designing the riskAIchain framework.
3.1. Data Collection and Expert Panel
Data for this study was collected through a combination of online and offline methods, including email correspondence with IT security experts, startup IT company owners, IS professors, IT service company executives, researchers, and IT major graduate students. A total of 14 valid responses were received, all from experts working in the field of IT infrastructure and blockchain, with a minimum of 5 years of experience in relevant roles. The experts included the following:
Five employees from various IT firms.
Four managers in IT security and governance roles.
Two IT risk management specialists.
Three academics with expertise in IT infrastructure and blockchain methods.
The authors identified a refined list of 10 critical factors through an extensive literature review, addressing key analytical, financial, and technical barriers to blockchain adoption in risk management. Expert input was gathered using the response sheet provided in
Appendix A, where the influence of each critical factor on the remaining nine was meticulously evaluated. This dataset served as the foundation for applying the DEMATEL approach. Using the collected data, we derived the ranking with cause-and-effect factor, the total interrelationship matrix, the total dependency matrix, and the inner dependency matrix of critical factors in tables below, providing comprehensive insights into the interdependencies among the factors.
This study employed a combination of online and offline methods for data collection. Researchers corresponded via email with IT security experts, startup IT company owners, IS professors, IT service company executives, researchers, and IT major graduate students. A total of fourteen valid responses were obtained from experts with a minimum of five years of experience in IT infrastructure and blockchain-related fields. These experts are actively engaged in areas such as IT security, governance, risk management, and academia, offering diverse perspectives to the study. The participants included five employees from various IT firms, four IT security and governance managers, two IT risk management specialists, and three academics with expertise in IT infrastructure and blockchain methodologies.
To ensure the credibility of the data, the selection of experts was guided by their professional background and relevance to the study’s objectives. Participants were selected based on their demonstrated expertise in IT security, blockchain, and risk management, as well as their practical and theoretical contributions to these fields. Each participant was provided with a detailed explanation of the study’s objectives and methodology. This process ensured that they fully understood their role in validating and refining the critical factors identified through the literature review.
To ensure a structured and consistent data collection process, we developed and shared a response sheet with the selected experts. The response sheet was designed to capture the relationships between the identified critical factors using the DEMATEL model. Experts were asked to evaluate these relationships based on a defined scale: 0 indicating no relation, 1 for slight relation, 2 for moderate relation, and 3 for high relation. This structured format allowed respondents to provide their insights on how each factor influenced or was influenced by the others, ensuring a systematic assessment of interdependencies. The collected responses were then consolidated into a matrix representation, as shown in
Appendix A, which served as the foundation for analyzing the causal relationships and prioritizing the critical factors. This process ensured that the data were not only relevant but also methodically aligned with the study’s objectives.
3.2. Fuzzy DEMATEL Procedure
The fuzzy DEMATEL method was applied to evaluate the interrelationships between the critical factors. The steps are as follows:
Constructing the Fuzzy Direct-Relation Matrix
Expert evaluations were gathered using linguistic terms (e.g., no relation, slight, moderate, high), which were then converted into fuzzy numbers: 0 (no relation), 1 (slight), 2 (moderate), and 3 (high). These fuzzy values formed the fuzzy direct-relation matrix, which quantifies the influence of each factor on the others.
Normalizing the Matrix
The fuzzy direct-relation matrix was normalized to ensure consistency and comparability across factors. This step is crucial for maintaining the integrity of the analysis.
Calculating the Total-Relationship Matrix
The total-relationship matrix, which captures both direct and indirect influences among factors, was computed using the equation T = AN(I − AN) − 1 where AN is the normalized matrix, and I is the identity matrix. Excel’s functions like MINVERSE for matrix inversion and MMULT for matrix multiplication are used to derive this total-relation matrix.
Deriving Cause and Effect Values
Once the total-relation matrix is computed, the cause (r) and effect (c) of each factor are calculated by summing the rows and columns of the matrix, respectively. This step is essential in understanding how much each factor influences others (r) and how much it is influenced by others (c). The net effect (r + c) is then computed to determine whether a factor is a causal or effect factor, with positive values indicating driving factors and negative values indicating dependent factors. Additionally, the total effect (r − c) shows the overall prominence of each factor in the system. These values are then used to rank the factors based on their significance. The factors with the highest (r − c) values were considered the most causal drivers, while those with the highest (r + c) values were the factors with the most effect.
Thresholding and Ranking the Factors
The average value of the total-relationship matrix was used as a threshold (α = 0.051) to filter out less significant interrelations, forming the inner dependency matrix. The final ranking of factors, along with their categorization as causal or effect factors, was based on the computed (r − c) and (r + c) values.
3.3. Identification of Critical Factors
This study identified 10 critical factors categorized into analytical, financial, and technical barriers to blockchain adoption. These factors and their relationships and rankings are shown in tables below. The DEMATEL analysis revealed five causal factors (real-time data processing, scalability, risk assessment accuracy, system efficiency, and smart contract security) and five effect factors (computational complexity, data privacy, resource constraints, interoperability of data formats, and technical expertise).
3.4. Methodology for Integrating DEMATEL Results into the riskAIchain Model
The process of incorporating the results from the DEMATEL analysis into the design of the riskAIchain framework followed a structured approach to ensure that the identified critical factors were effectively addressed. The methodology involved several steps aimed at translating the insights from the cause–effect analysis into specific architectural components:
Mapping Causal and Effect Factors to System Requirements
The causal and effect factors derived from the DEMATEL analysis were first mapped to functional and non-functional system requirements. Causal factors, which were identified as driving forces within the system, were prioritized in the design to ensure the proactive mitigation of key challenges. Effect factors, being more dependent on the influence of other factors, were incorporated as considerations for enhancing system robustness and adaptability.
Layered Architectural Design Approach
A layered approach was adopted to structure the framework, where each layer was assigned specific responsibilities based on the identified factors. This approach ensured that each architectural layer directly corresponded to a set of critical factors, enabling targeted mitigation strategies. The layering also facilitated modular development, allowing individual components to be refined or extended based on evolving requirements.
Alignment of System Functions with Critical Factors
Each layer of the riskAIchain framework was designed to address a combination of causal and effect factors by integrating relevant technologies and methodologies. For example, layers responsible for real-time processing and data analytics incorporated advanced AI techniques to address causal factors related to data processing and accuracy, while layers focused on data privacy and interoperability included mechanisms for secure data handling and seamless integration.
Adaptive Feedback Mechanism Incorporation
Based on the analysis of the relationships between the factors, adaptive feedback mechanisms were integrated into the framework. This involved designing components such as feedback loops within the AI-driven analytics layer to continuously refine risk assessments based on real-time data, ensuring the framework’s adaptability to changing risk landscapes.
Use of Security and Compliance Standards
The methodology also involved integrating compliance standards and security best practices to address gaps identified through factors like technical expertise and regulatory requirements. Automated compliance checks and continuous monitoring capabilities were incorporated to ensure that the system remained aligned with industry standards.
Threshold-Based Filtering for Dependency Management
The inner dependency matrix, derived from the DEMATEL results with a threshold value, guided the inclusion of dependencies between components in the architecture. The threshold filtering ensured that only significant dependencies influenced the architectural design, thereby optimizing system efficiency and reducing unnecessary complexity.
Iterative Validation and Refinement
The methodology was iterative, involving validation of the design choices against the DEMATEL results to ensure that the proposed layers effectively addressed the identified barriers. Expert feedback was sought during the design process to refine the architecture, ensuring that the riskAIchain model remained practical and aligned with industry needs.
4. Challenges in Traditional IT Risk Management Infrastructures
IT risk management is crucial for keeping organizations strong in today’s digital world. Growing cybersecurity threats call for frameworks to detect, evaluate, and lower risks while maintaining operations functioning in IT systems. IT risk management supports steady operations, adherence to standards, and security of essential systems. IT risk management infrastructures involve frameworks, processes, and tools. They help find, assess, and reduce IT system risks. These infrastructures ensure IT security, reliability, and compliance. Key parts include methods for assessing risk, strategies to reduce it, and systems for ongoing monitoring. They emphasize the importance of continuous monitoring and improvement, helping organizations adapt to evolving threats and vulnerabilities. By integrating risk management into their operational practices, organizations can enhance their resilience against IT-related risks and ensure compliance with regulatory requirements. Effective communication and collaboration across various stakeholders are essential for building a robust risk management culture (
CompTIA 2022).
IT risk management infrastructures include frameworks, policies, and processes to manage IT risks. They are essential for protecting data, keeping systems secure, and following regulations, especially as technology changes quickly. According to NIST Special Publication 800-30, risk management includes three steps: assessing risks, reducing them, and reviewing actions. It helps IT managers balance the costs of protection with the need to secure systems and data that support their organization’s goals. This approach is not limited to IT; it applies to everyday decisions. For instance, people install home security systems and pay monthly fees to protect their property. They likely consider the costs of security against the value of their belongings and their family’s safety (
National Institute of Standards and Technology 2012).
It is imperative to manage IT risks to preserve the security and stability of an organization. Proven best practices in risk management are promoted through the widespread adoption of standard frameworks. Groups such as the Financial Services Information Sharing and Analysis Center (FS-ISAC) facilitate information exchange and collective threat response, as organizations frequently collaborate and share resources to address cybersecurity and regulatory challenges. Nevertheless, research suggests that these frameworks may be unable to effectively manage intricate, organization-specific IT risks and may not possess the adaptability necessary to confront distinctive obstacles. This problem is especially prevalent in industries that are undergoing rapid change, as new strategies and threats are frequently introduced (
Sayeed et al. 2024).
The NIST Special Publication 800-37 defines seven key components within its risk management framework (RMF) for managing security and privacy risks. It starts with Prepare, which defines goals, responsibilities, and security baselines. Categorize comes next and entails grouping systems according to possible influence on availability, integrity, and confidentiality. Appropriate security measures are found in the Select step and cater to certain hazards. These controls, which guarantee they are recorded and included into current systems are applied in the Implement phase. While Authorize is a formal decision on whether to let system operation depend on remaining risks, Assess analyzes the effectiveness of these safeguards by testing. At last, Monitor guarantees continuous system monitoring that enables changes as hazards develop. This all-encompassing approach produces a dynamic risk management plan that fits corporate objectives and changes with the times (
National Institute of Standards and Technology 2018).
Although methods like ‘AssessITS’ is a useful framework for IT risk assessment by aggregating procedural rules and evaluation criteria catered to organizational objectives, models like it still have great difficulties in the field of conventional IT risk management systems. Their dependence on preset, static structures is one main drawback since it might not be enough to handle fast-developing cyber threats or dangers particular to their company. Many times, lacking real-time adaptability, these conventional systems make it difficult to react quickly to fresh or unanticipated hazards. They might also find it difficult to account for the operational settings and regulatory contexts of various companies or to combine several data sources. More dynamic, flexible risk management methods are therefore especially important since this rigidity can lead to obsolete assessments, missing vulnerabilities, and finally, a weaker defense against cyber threats (
Rahman et al. 2024).
The proposed riskAIchain framework offers substantial advancements over existing risk management methodologies by addressing critical challenges that traditional systems fail to overcome. As outlined in
Table 2, conventional IT risk management infrastructures often lack real-time adaptability, rely on static and rigid structures, and struggle with the integration of multiple data sources and compliance requirements. These limitations result in delayed responses, incomplete risk assessments, and reduced resilience against evolving cyber threats. In contrast, riskAIchain introduces a dynamic and comprehensive approach that leverages blockchain’s immutable and decentralized architecture to ensure data integrity and transparency, while AI-driven analytics enable real-time threat detection and predictive risk assessment. The framework also incorporates automated compliance tracking and adaptive mechanisms to address rapid industry changes, ensuring its applicability across diverse organizational contexts. By consolidating advanced features like continuous monitoring, explainable AI (XAI), and smart contracts, riskAIchain bridges the gap between traditional methodologies and the need for scalable, flexible, and proactive risk management. This holistic integration positions the framework as a robust and future-ready solution capable of addressing the complexities of modern IT environments.
5. Emerging Cyber Threats in the AI World
Emerging cyber threats are increasingly sophisticated due to the growing complexity of networked systems. The incorporation of technology such as IoT, smart sensors, and cloud services has broadened the attack surface, rendering vital infrastructures increasingly susceptible. Incidents such as ransomware, Distributed Denial-of-Service (DDoS) attacks, and data breaches are on the rise, frequently aimed at critical sectors including healthcare, transportation, and energy. These threats exploit weaknesses in communication networks, devices, and software, resulting in possible interruptions, data loss, and compromised privacy. Furthermore, fraudsters are utilizing increasingly sophisticated methods, including the exploitation of AI vulnerabilities to modify data or evade detection systems. As the digital world progresses, stringent security measures are needed to mitigate escalating cyber threats, necessitating ongoing adaptation to new attack methodologies and technology (
Demertzi et al. 2023).
Cryptojacking and fileless ransomware pose substantial threats to the financial industry, capitalizing on weaknesses in both conventional and digital infrastructures. Cryptojacking covertly utilizes computing resources for illicit cryptocurrency mining, resulting in hardware deterioration and elevated operational expenses. Fileless ransomware functions covertly by compromising systems without depositing conventional malicious files. It resides in memory and utilizes legitimate software operations, rendering it challenging to identify using conventional security techniques. These advanced assaults can rapidly undermine essential systems, encrypting data or restricting access while circumventing conventional defenses. The covert characteristics and advancing methodologies of fileless ransomware underscore the pressing necessity for sophisticated cybersecurity strategies, including behavior-based detection and proactive threat hunting, to protect financial data and ensure operational resilience (
Kshetri et al. 2024).
The emergence of powerful AI-driven assaults is reshaping the cyber threat environment, as hackers progressively utilize AI methodologies to conduct complex and targeted operations that evade conventional detection systems. These threats exploit vulnerabilities in networked systems, including IoT and cloud settings, utilizing strategies such as automated phishing, adversarial machine learning, and sophisticated malware. With the proliferation of AI-driven assaults, substantial threats to data integrity, privacy, and the security of essential infrastructures emerge, necessitating the urgent implementation of resilient and adaptive cybersecurity measures (
Guembe et al. 2022).
Artificial intelligence improves cybersecurity by utilizing predictive analytics to identify intricate threats via extensive data analysis, pattern recognition, and automation. This method facilitates the detection of advanced attacks, such as novel malware and phishing tactics, by recognizing irregularities in network traffic and user behavior. Machine learning allows systems to adjust to changing threats, consistently enhancing defensive strategies. Nonetheless, the identical technology may be leveraged by adversaries to develop more sophisticated and elusive cyber threats, highlighting the necessity for continuous progress in AI-enhanced security solutions (
Duary et al. 2024).
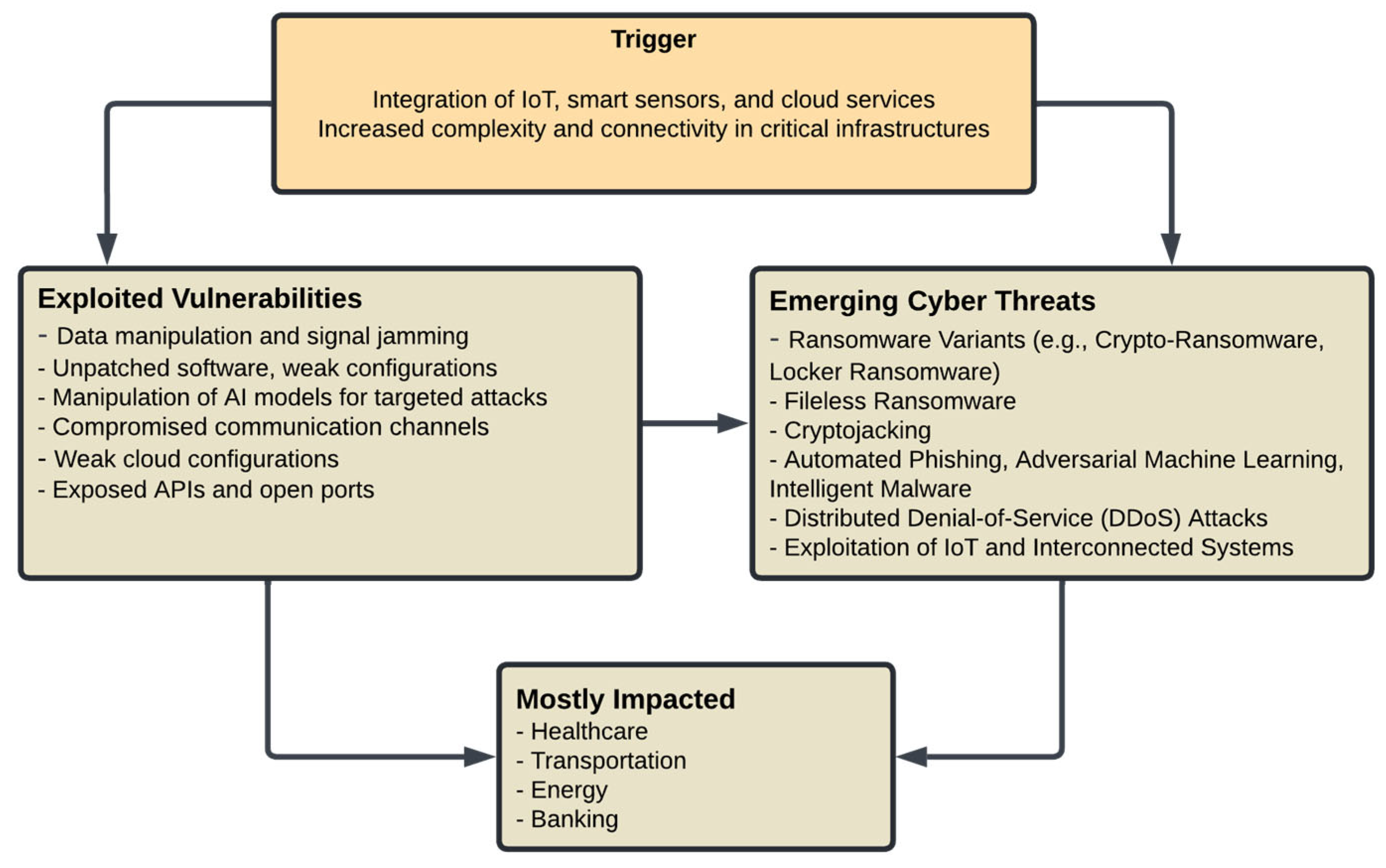
The changing panorama of cyber threats progressively exploits the weaknesses present in interconnected systems, such as UAV-assisted IoT applications. These systems encounter several hazards, such as unauthorized access, data manipulation, and the exploitation of communication protocols. Perpetrators employ advanced strategies, including physical interference, signal jamming, and the insertion of harmful code, to compromise the integrity and operation of these networks. The difficulty of safeguarding these technologies is intensified by the necessity for immediate reactions to evolving threats across various layers, from physical hardware to application protocols as shown in
Figure 1. Mitigating these dangers necessitates comprehensive security measures that incorporate AI, machine learning, and adaptive methods to efficiently identify and counter threats (
Adil et al. 2023).
6. Blockchain and AI in It Risk Management
Blockchain technology significantly enhances risk management in contemporary IT infrastructures by offering a decentralized, secure, and transparent framework for transaction and data management. The decentralized ledger of blockchain obviates the necessity for centralized authority, hence diminishing vulnerabilities like single points of failure. This immutable nature guarantees that once data are captured, they cannot be modified, protecting against tampering and providing a dependable audit trail, which is essential for compliance and auditing in risk management. Moreover, consensus mechanisms like proof of work (PoW) and practical byzantine fault tolerance (PBFT) guarantee that transactions are validated by several participants, hence augmenting security, and trust (
Yaqoob et al. 2021). Moreover, the integration of blockchain with IoT enhances security by offering immutable records and enabling secure communication among devices, which is essential for real-time event monitoring and automated reactions via smart contracts (
Alzoubi et al. 2022). The integration of blockchain’s security attributes with automated decision-making enhances resilience and intelligence in risk management, especially within intricate, data-centric contexts.
When it comes to protecting data and transactions over dispersed networks, blockchain’s decentralized and transparent properties provide strong solutions for risk management. Blockchain guarantees that data cannot be changed once recorded without the approval of most participants by applying cryptographic hashing and consensus methods. Because it creates a verifiable and trustworthy audit trail across all system nodes, immutability is an essential component of risk management. In addition, smart contracts and blockchain can work together to automate risk mitigation procedures. When specific risk levels are met, self-executing protocols known as “smart contracts” can initiate predetermined activities, guaranteeing that reactions to possible threats are both fast and consistent (
Meng et al. 2020). The development of lattice-based cryptographic algorithms further demonstrates that blockchain may be applied in contexts that are resistant to quantum computing threats, thus strengthening its role in risk management. Because of these developments, blockchain is now an assistive method of protecting vital company data from potential quantum attacks (
Zheng 2024).
Artificial intelligence (AI) significantly contributes to cybersecurity by offering sophisticated methods for the detection, analysis, and mitigation of cyber threats. AI systems utilize techniques such as machine learning (ML) and deep learning (DL) to analyze extensive datasets, identify concealed patterns, and adjust to emerging attack vectors. AI models are widely employed in supervised and unsupervised learning for tasks such as anomaly detection, intrusion detection, and malware classification. Supervised learning models, including neural networks, have proven effective in identifying spam and filtering malicious content, whereas unsupervised learning facilitates the detection of unknown threats without a dependence on predefined labels (
Saharan 2024). Deep learning models, which autonomously extract features from raw data, have significantly improved intrusion detection systems (IDS), facilitating more accurate identification of cyberattacks, including Distributed Denial of Service (DDoS) (
Tao et al. 2021). The integration of AI and cybersecurity enhances both the speed and precision of threat detection while facilitating more effective real-time risk management. This alignment supports the objective of advancing security frameworks via automated and intelligent responses to emerging risks.
Artificial intelligence (AI) enhances cybersecurity for critical infrastructures through advanced mechanisms for threat detection and risk mitigation. AI-driven models, especially in machine learning and deep learning, are proficient in analyzing large datasets to detect patterns indicative of potential security breaches or vulnerabilities. Utilizing supervised and unsupervised learning, AI systems can identify anomalies in real-time, enhancing the accuracy and efficiency of cybersecurity incident responses. Machine learning algorithms are employed to detect malware and unauthorized access attempts, whereas deep learning models improve the accuracy of these systems by continuously learning from new data inputs (
Belgaum et al. 2021). AI applications in cybersecurity play a crucial role in securing critical infrastructures such as healthcare and smart grids, as the real-time monitoring capabilities of AI can effectively prevent attacks that may cause significant disruptions (
Sakhnini et al. 2020). Integrating AI with existing cybersecurity frameworks enables organizations to develop adaptive and intelligent defense mechanisms, essential for addressing the dynamic nature of cyber threats in contemporary risk management systems.
While AI significantly strengthens the detection and response capabilities of these security systems, integrating blockchain adds further robustness. Blockchain’s decentralized and immutable ledger ensures that event logs from systems like SIEM and IDS are stored securely and cannot be altered, providing an additional layer of trust and integrity. Smart contracts within blockchain can automate security responses in SOAR or XDR platforms, executing predefined actions when AI detects threats. This combination ensures transparency, accountability, and verifiability in AI-driven security decisions. Together, AI and blockchain create a more resilient cybersecurity framework, addressing modern threats while ensuring compliance, governance, and data integrity in critical organizational environments (
Taherdoost 2022).
Artificial intelligence (AI) is increasingly critical to enhancing IT security across various technologies, including firewalls, Security Information and Event Management (SIEM), Security Orchestration, Automation, and Response (SOAR), intrusion detection systems (IDS), Privileged Access Management (PAM), Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), Network Access Control (NAC), and Data Loss Prevention (DLP) systems. AI enables these technologies to perform predictive analytics and real-time anomaly detection, and to automate responses to emerging threats. For example, AI-powered firewalls analyze traffic patterns to block unknown threats, SIEM systems use machine learning to detect suspicious patterns in log data, and SOAR platforms automate threat mitigation based on AI insights. IDS, EDR, and XDR leverage AI to detect and respond to intrusions across networks and endpoints, while PAM systems monitor privileged account activities to detect unusual access behaviors. Additionally, NAC systems control network access, ensuring only authorized devices connect, and DLP systems use AI to prevent data breaches by monitoring unauthorized data transfers as depicted in
Figure 2.
7. Proposed List of Critical Factors and Use of DEMATEL Technique
By following the research gaps mentioned in the paper, we sought to identify the most significant factors that pose challenges for companies or IT infrastructures in adopting blockchain for enhanced risk management. These factors were carefully analyzed, resulting in a list of ten critical factors that could potentially make IT infrastructures vulnerable while adopting blockchain technology. To address this, it was essential to rank these factors based on their vulnerabilities and interdependencies. In this regard, the most compatible quantitative method we found was the DEMATEL (Decision-Making Trial and Evaluation Laboratory) method.
The DEMATEL method is particularly effective in analyzing cause-and-effect relationships among critical factors. It provides a clear visualization of interrelationships, helping us identify not only the most impactful critical factors but also the cascading effects they may have. This method directly supported the development of our model by highlighting which factors to prioritize and how to address their consequences effectively. For organizational risk management, DEMATEL stands out as it systematically disentangles complex interdependencies and allows organizations to focus on causal factors that drive systemic risks. By clarifying which factors influence others and the degree of their impact, it enables a strategic approach to mitigating risks at their roots.
DEMATEL is effective for risk management because it provides clear insights by ranking factors based on their influence (drivers) and impact (dependencies). This is particularly valuable in addressing challenges in blockchain adoption, such as scalability, interoperability, and privacy concerns. DEMATEL excels in capturing the interrelationships among these factors, helping organizations focus on root causes and cascading effects. For instance, studies have shown that DEMATEL can effectively classify and prioritize security challenges in blockchain-based systems, such as authentication, intrusion detection, and availability, making it highly relevant for blockchain-driven network security (
Kamalov et al. 2023). Unlike static models such as Structural Equation Modelling (SEM), which are less effective for dynamic systems, DEMATEL is well suited for evolving scenarios. Bayesian networks, while powerful for probabilistic analysis, are computationally intensive and less practical for real-time applications. DEMATEL has been applied in risk management frameworks to overcome such limitations by identifying causal relationships among IT-GRC factors and optimizing security measures through iterative evaluations (
Ramalingam et al. 2018). Similarly, Fuzzy Cognitive Maps (FCM) rely heavily on subjective judgments, and System Dynamics (SD) demands significant expertise and computational resources, making them less feasible for broader adoption. Analytic Network Process (ANP), though capable of analyzing interdependencies, becomes overly complex for large-scale systems. DEMATEL’s simplicity and adaptability make it a preferred choice, particularly in blockchain contexts where it clarifies the causal relationships between critical factors and supports strategic decision-making. Its ability to integrate with blockchain, a decentralized and immutable technology for secure and transparent data processing, further strengthens its applicability in addressing modern cybersecurity challenges (
Gheisari et al. 2023).
In the context of IT infrastructure, DEMATEL helped us pinpoint how factors such as scalability and real-time data processing act as drivers for other challenges like resource constraints and data privacy concerns. This insight informed the design of our proposed risk management framework, enabling targeted interventions to mitigate risks. By applying DEMATEL, we were able to build a robust and adaptable model that not only identifies critical risk factors but also maps out their interdependencies, making it an indispensable tool for addressing the complexities of modern risk management scenarios.
The proposed critical factors (CF) outlined in this section are derived from an extensive review of the relevant literature. These factors highlight key challenges and advantages of integrating AI and blockchain technologies in the context of organizational risk management. The ten critical factors serve as the foundation for our analysis (
Table 3). Using the DEMATEL (Decision-Making Trial and Evaluation Laboratory) method, we will perform a regression analysis to evaluate how these factors interrelate and influence one another. This analysis is essential to ensure that the proposed riskAIchain model effectively addresses these challenges before the model is formally introduced.
By conducting this analysis prior to proposing the model, we aim to identify key causal relationships and dependencies between the factors. The results will provide insights into the most influential factors, which will help guide the development of the riskAIchain model. This ensures that our proposed infrastructure is designed with a clear understanding of the critical factors impacting the performance, scalability, and security of AI and blockchain systems within organizational risk management frameworks.
7.1. Steps of DEMATEL Procedure
The steps involved in DEMATEL were adopted from
Sinha et al. (
2019) and are as follows:
7.1.1. Direct-Relation Matrix
Inputs from the experts were taken for
Dn ×
n by comparing criteria in pairs. Elements of the
Dn ×
n were indicated by
pij where n number of factors
pij influence levels of factor i on factor j. The averaged matrices D for all the experts was calculated by averaged scores of the H experts as given in Equation (1).
where
—importance weight of kth expert.
7.1.2. Normalizing Direct-Relation Matrix
Equations (2) and (3) are applied to obtain the normalized direct-relation matrix.
7.1.3. Total-Relationship Matrix
With the help of Equation (4) can be computed. Where ‘I’ is an identity matrix as shown in Equation (4)
7.1.4. Causal Relationship Diagram
R and C which are the sum of the row and column are computed by using Equations (5)–(7).
7.1.5. Findings from the DEMATEL Analysis
The findings from the DEMATEL analysis is shown in tables below as
Table 4 (ranking with cause-and-effect factor),
Table 5 (total interrelationship matrix),
Table 6 (total dependency matrix), and
Table 7 (inner dependency matrix).
7.2. Explanation of DEMATEL Analysis Results
The DEMATEL methodology was used to make a cause–effect relationship between the critical factors in this research. According to this method, the cause factors were determined if the (r − c) values > 0 and the effect factors were determined if the (r − c) values < 0. From the results, it showed that out of ten critical factors, five were identified as ‘causal’ factors, whereas five were identified as ‘effect’ factors. The cause–effect categories are identified in
Table 5. Critical factors are real-time data processing, scalability, risk assessment accuracy, system efficiency, and smart contract security. Similarly, results showed that the effect factors are computational complexity, data privacy, resource constraints, interoperability of data formats, and technical expertise.
Technical barriers/factors such as “scalability”, “real-time data processing”, “risk assessment accuracy”, “smart contract security”, and “system efficiency” were classified as causal factors. It notifies the significance of technical barriers in all aspects of the adoption of blockchain for risk assessment in IT infrastructure. Analytical and financial barriers such as “scalability”, “real-time data processing”, “smart contract security”, and “system efficiency” were identified as causal factors. This indicates that IT firms face difficulties in financing an IT infrastructure alongside analytical issues that create barriers for the adoption of blockchain technology.
Table 5 also shows the top five significant factors. These factors are “real-time data processing”, “scalability”, “computational complexity”, “data privacy”, and “resource constraints.” “Real-time data processing” is the most critical factor with a maximum (r − c) value of 0.02. And “smart contract security” is the least critical factor with a minimum (r + c) value of 1.36. The results of the DEMATEL method have been validated by comparison to the shortlisted literature studies.
Real-time data processing was identified as the most prominent factor as it had influence over the other nine factors. It shows that the capability to analyze and process data in real-time is not compatible without compromising efficiency or accuracy in the existing system for IT firms. Scalability is also an important prominent factor as it has prominence over the six other factors in the table. It signifies that the IT infrastructure faces problems in risk management with handling increasing volumes of data and transactions while maintaining performance and security. The third most prominent factor is computational complexity. It indicates that the existing system faces a problem of interoperability with latency and affects decision-making speed for the resource-intensive nature of AI and blockchain. As a result, any IT company who does not take precautions faces problems in interoperability for the adoption of blockchain in IT-infrastructure. The fourth prominent factor is data privacy. In the existing system, firms cannot ensure the privacy of sensitive information in decentralized systems, especially when multiple stakeholders are involved. The fifth prominent factor that was found out in the result was resource constraints. It signifies the barriers of using AI and the adoption of blockchain technology in terms of computational power, storage, and financial investment.
7.3. Use of Results to Build the Proposed riskAIchain Framework
The proposed riskAIchain framework is strategically designed to address the critical factors identified through the DEMATEL analysis, optimizing risk management in IT infrastructures by leveraging blockchain and AI. The architecture’s layers and components are purposefully incorporated to tackle the cause-and-effect relationships among the factors, ensuring a comprehensive approach to mitigating risks.
The DEMATEL results identified real-time data processing as the most significant causal factor. This layer directly addresses the challenge by integrating a predictive analytics engine and an anomaly detection module, enabling real-time data processing and the swift detection of potential risks. Additionally, explainable AI (XAI) enhances decision-making transparency, addressing issues of computational complexity by making analytical processes more interpretable. The inclusion of a feedback loop ensures the continuous improvement of risk assessment accuracy, thus enhancing the system’s ability to adapt and learn from evolving data patterns.
With data privacy recognized as an effect factor, this layer incorporates Zero Trust Architecture and data encryption to safeguard sensitive information in decentralized environments, which is a significant concern identified in the analysis. The inclusion of access control mechanisms ensures robust protection of critical data, further strengthening privacy measures. The smart contracts and immutable audit trails within the decentralized blockchain layer contribute to data integrity, making the system resilient against resource constraints and security breaches.
This analysis highlighted challenges related to scalability and interoperability of data formats. The blockchain’s distributed ledger and consensus mechanism offer a scalable solution to manage growing data volumes while maintaining security. Moreover, smart contracts enable seamless integration across diverse systems, addressing latency and interoperability issues associated with computational complexity. The immutable audit trail feature ensures that compliance and traceability requirements are met, reducing risks associated with smart contract security.
To address the technical expertise gap identified in the DEMATEL results, this layer facilitates regulatory compliance and continuous monitoring, thus reducing dependency on manual interventions. Automated compliance reporting and monitoring help organizations meet regulatory requirements, while the Risk and Compliance Report feature supports proactive decision-making, ensuring alignment with industry standards.
The prominence of the interoperability of data formats as a challenge necessitated the inclusion of an API gateway and blockchain–AI data interface in this layer. These components facilitate seamless data exchange between different systems and technologies, overcoming the integration and latency challenges associated with diverse IT environments.
Incorporating a real-time dashboard, threat intelligence, and incident response automation addresses the need for enhanced real-time data processing. This layer centralizes risk monitoring, providing a comprehensive view of the threat landscape and enabling timely responses. Automated incident response processes also improve system efficiency, reducing resource consumption while ensuring rapid reaction to security incidents.
8. AI-Driven and Blockchain-Backed Approach: riskAIchain
riskAIchain is a groundbreaking framework designed to address the complexities of modern IT risk management by integrating blockchain technology and AI-driven analytics. It offers significant advancements over existing methodologies by improving security, scalability, and decision-making in a dynamic cyber environment. This section presents the operational details of the framework, substantiates its practical value, and highlights its tangible benefits through theoretical application scenarios.
8.1. riskAIchain Framework
The riskAIchain framework is depicted in
Figure 3 with six layers, each addressing specific challenges in risk management:
Data Privacy and Integrity Layer: Ensures data confidentiality and security using Zero-Trust Architecture, encryption, and access controls.
Decentralized Blockchain Layer: Provides a distributed, immutable ledger with smart contracts and consensus mechanisms for secure and transparent data management.
AI-Driven Analytics Layer: Enhances predictive capabilities, anomaly detection, and decision-making through continuous learning and explainable AI (XAI).
Interoperability Layer: Facilitates seamless communication between blockchain and AI systems via APIs and interfaces for efficient data exchange.
Security and Compliance Layer: Maintains adherence to regulatory requirements and generates compliance reports for proactive risk governance.
Risk Monitoring and Management Layer: Features a real-time dashboard, threat intelligence tools, and automated incident response capabilities for comprehensive risk oversight.
8.1.1. Decentralized Blockchain Layer
At the core of riskAIchain is a decentralized blockchain infrastructure, which ensures the integrity and transparency of all transactions and data records. Blockchain’s distributed ledger system offers an immutable audit trail, ensuring data cannot be altered once it is recorded. This layer incorporates smart contracts, which are self-executing protocols that automate risk management processes based on predefined conditions. The consensus mechanism embedded within this layer guarantees that all participants agree on the state of the blockchain, minimizing risks of fraud or tampering. By utilizing blockchain’s decentralized nature, riskAIchain eliminates the need for a centralized authority, reducing the potential single points of failure and enhancing the resilience of the risk management system.
8.1.2. AI-Driven Analytics Layer
Above the blockchain layer is the AI-driven analytics module, which powers predictive analytics, anomaly detection, and decision-making in real time. This layer leverages artificial intelligence (AI) to detect emerging threats, identify patterns, and anticipate risks before they materialize. Using machine learning algorithms, the system continuously improves its ability to recognize anomalies in data and predict possible cyberattacks or system vulnerabilities. Explainable AI (XAI) is a crucial component here, providing transparency in AI-driven decisions and enabling stakeholders to understand the reasoning behind critical security actions. The continuous feedback loop in this layer ensures that as the AI learns from new data, verified through the blockchain, it refines its risk assessment models for enhanced accuracy.
8.1.3. Interoperability Layer
Connecting the blockchain and AI layers is the interoperability layer, which facilitates seamless communication between these technologies. This layer houses the blockchain–AI data interface, allowing secure data exchanges between the blockchain’s ledger and the AI-driven analytics engine. Through an API gateway, riskAIchain enables smooth data flow across layers, ensuring that the AI can access verified data for analysis and feedback its findings into the blockchain. This interoperability is critical to the system’s performance, as it ensures that data integrity is maintained throughout the risk management process, while AI enhances the speed and intelligence of decision-making.
8.1.4. Risk Monitoring and Management Layer
At the user interface level, riskAIchain incorporates a real-time risk monitoring and management system. This layer offers a dashboard that allows users to visualize risk assessments, monitor system vulnerabilities, and track potential threats as they evolve. The dashboard is designed for real-time updates, providing continuous insight into the organization’s risk posture. Integrated into this layer is an automated incident response module, which can take predefined actions based on real-time alerts generated by the AI. The system is also connected to a threat intelligence database, ensuring it is up to date on the latest vulnerabilities and attack vectors, further enhancing its proactive risk management capabilities.
8.1.5. Data Privacy and Integrity Layer
In conjunction with the blockchain, the data privacy and integrity layer is responsible for securing sensitive information. It ensures that all data ingested by the system is encrypted, while access control mechanisms prevent unauthorized users from retrieving or altering critical information. Additionally, riskAIchain adheres to a Zero Trust Architecture, which assumes that every access request—both internal and external—must be thoroughly verified before granting entry. This focus on data integrity and privacy fortifies the system, safeguarding it from breaches and ensuring compliance with data protection regulations.
8.1.6. Security and Compliance Layer
Alongside the risk management system is a dedicated security and compliance layer that ensures the platform meets industry standards and regulatory requirements. This layer includes tools for generating detailed risk and compliance reports, which auditors and regulators can use to assess the system’s adherence to security standards. Continuous monitoring capabilities further ensure that riskAIchain stays compliant with evolving regulations. By keeping the system in line with legal and industry standards, this layer reduces the risks associated with regulatory penalties and non-compliance.
8.1.7. Data Flow and Synergy Across Layers
The architecture of riskAIchain operates as a cohesive unit, where data flows seamlessly between layers. Data ingested by the AI-driven analytics layer is verified and stored in the blockchain, ensuring transparency and integrity. Smart contracts, stored on the blockchain, execute actions based on AI insights, automating responses to potential risks. The feedback loop continuously improves the AI by feeding it accurate, verified data from the blockchain, which enhances the system’s ability to make informed predictions. Users interact with the system via the real-time dashboard, accessing insights and reports generated by AI, while the blockchain ensures the reliability of all underlying data.
8.2. Advancements over Existing Frameworks
The integration of blockchain and AI provides unique capabilities to enhance existing risk management methodologies. Blockchain ensures the immutability and traceability of data, eliminating vulnerabilities such as tampering or unauthorized access. AI adds advanced predictive capabilities, allowing for real-time identification of emerging threats, dynamic risk assessments, and automated incident responses. By combining these technologies, riskAIchain resolves key limitations of centralized systems, such as single points of failure and latency in decision-making processes (
Pal et al. 2021).
The decentralized nature of the blockchain layer strengthens data integrity and trust among stakeholders, critical for industries like finance and healthcare. For example, smart contracts enable the automated execution of predefined risk mitigation actions, significantly reducing human error and reaction time during security incidents. Meanwhile, the AI-driven analytics layer delivers actionable insights by processing verified data from the blockchain, ensuring high accuracy in threat detection and response (
Goodfellow et al. 2017;
Ribeiro et al. 2016).
8.3. Practical Implementation and Validation
Although this paper does not yet include a full real-world application, it outlines a theoretical application scenario that demonstrates the framework’s feasibility, potential, and practical value. The integration of AI and blockchain in riskAIchain presents a significant advancement over traditional risk management methodologies, providing enhanced security, transparency, and efficiency. These application scenarios illustrate how riskAIchain can address critical challenges in various sectors, aligning with existing research, which emphasizes the potential of technology-driven frameworks in mitigating risks and improving decision-making processes.
Scenario: Financial Sector Risk Management: In the banking environment, riskAIchain can process transactional data using its AI-driven analytics layer to detect anomalies indicative of fraudulent activities. Verified transactional records from the blockchain ensure accurate anomaly detection, while smart contracts trigger predefined actions, such as freezing suspicious accounts or notifying relevant authorities. A real-time dashboard enables security teams to monitor ongoing incidents and make informed decisions rapidly (
Yuhertiana and Hadi Amin 2024).
Scenario: Healthcare Data Security: In a decentralized healthcare network, riskAIchain ensures the secure exchange of patient records among hospitals and insurers. The blockchain layer prevents unauthorized access, while the AI layer identifies potential data breaches or irregularities in access patterns, mitigating risks effectively (
Velmovitsky et al. 2021;
Bhumichai et al. 2024).
Just as
Giudici et al. (
2022) showed how technology could reduce volatility risks in financial markets, riskAIchain enhances operational outcomes by improving fraud detection, reducing compliance costs, and enabling faster incident responses.
8.4. riskAIchain Implications and Contributions
This framework contributes to the field by proposing a comprehensive and scalable framework that addresses gaps in traditional risk management systems. By integrating blockchain and AI, riskAIchain achieves the following:
Enhanced data security and transparency through an immutable ledger and Zero Trust principles.
Improved decision-making speed and accuracy with real-time analytics and explainable AI.
Automation of risk responses, minimizing reliance on manual intervention.
This proposed approach sets the stage for future studies exploring real-world deployments, such as validating the framework in different organizational contexts or refining its layers for sector-specific application. Potential domains include financial services, supply chain logistics, and critical infrastructure systems, where real-time risk management is paramount. Comprehensive case studies and performance benchmarks will further establish the framework’s scientific rigor and practical feasibility.
8.5. Novelty and Scientific Contribution
The proposed riskAIchain framework offers a significant advancement in organizational risk management by integrating blockchain technology and AI into a unified and comprehensive infrastructure. Traditional risk management systems often rely on static methodologies that fail to adapt to the evolving cyber threat landscape or effectively leverage emerging technologies. This study addresses these limitations by proposing a multi-layered approach that enhances critical processes such as threat detection, response automation, regulatory compliance, and data security. A key feature of riskAIchain is its ability to proactively detect and address risks using AI-driven analytics. The framework leverages predictive analytics and anomaly detection to anticipate potential threats, offering organizations the capability to mitigate risks before they escalate. This represents a departure from conventional reactive approaches and establishes a more dynamic, forward-looking model. Additionally, the integration of smart contracts within the blockchain layer automates predefined risk mitigation actions, reducing reliance on manual intervention and ensuring swift responses to incidents. This automation significantly enhances operational efficiency and minimizes the likelihood of human error during critical risk scenarios.
This framework also strengthens regulatory compliance and data governance. The blockchain’s immutable ledger ensures that the integrity and traceability of data, which is crucial for industries such as finance and healthcare where transparency and accountability are paramount. By incorporating explainable AI (XAI), the framework addresses a major barrier to AI adoption in regulated environments: the lack of interpretability in decision-making processes. XAI not only makes AI-driven decisions more transparent but also provides stakeholders with the confidence to rely on these decisions in high-stakes scenarios. From a practical perspective, riskAIchain demonstrates broad applicability across various sectors. In banking, for instance, the framework ensures secure transactional processing while automating fraud detection and response. Healthcare organizations can utilize the system to secure patient data exchanges and detect unauthorized access patterns, ensuring compliance with strict privacy regulations. In critical infrastructure environments, the framework prevents disruptions by securing communication between IoT devices and identifying vulnerabilities in real time. These applications showcase how riskAIchain moves beyond theoretical advancements to provide actionable solutions for real-world challenges.
Moreover, the framework’s novelty lies in its ability to seamlessly integrate blockchain and AI in a way that addresses long-standing challenges in risk management, including static structures, a lack of scalability, and limited adaptability to evolving threats. Unlike fragmented solutions that address the isolated aspects of risk management, riskAIchain connects its multiple layers such as predictive analytics, smart contracts, interoperability interfaces, and compliance reporting to function as a cohesive system. This holistic integration ensures real-time feedback, enabling AI to refine predictive models with verified blockchain data, while maintaining security, transparency, and adaptability across industries. By offering a scalable and interoperable architecture, the framework not only addresses current organizational needs but also paves the way for future advancements in risk management practices. With its ability to automate risk responses, enhance decision-making transparency, and dynamically adapt to emerging threats, riskAIchain establishes a robust foundation for both practical applications and academic exploration, demonstrating its transformative potential across industries.
9. Conclusions and Future Scope
As specified, traditional IT infrastructures are increasingly inadequate for meeting the demands of modern risk management and addressing the swiftly evolving landscape of cyber threats. In response, we proposed the riskAIchain framework, an innovative AI-driven and blockchain-backed IT infrastructure designed with multiple layers to enhance risk management processes. By integrating AI and blockchain technologies, the framework leverages features such as immutable records, real-time event monitoring, and secure communication through consensus mechanisms like proof of work (PoW) and practical Byzantine fault tolerance (PBFT). Supported by ten critical factors identified through extensive research and validated using regression analysis, the framework significantly enhances the reliability, speed, and accuracy of risk management, empowering organizations to proactively address emerging cyber threats in an AI-dominated era.
Looking ahead, the framework offers immense potential for future advancements. Incorporating emerging technologies such as Augmented Reality (AR), Virtual Reality (VR), the metaverse, and advanced blockchain applications, along with the further integration of AI, machine learning (ML), and deep learning (DL), can expand its capabilities. Additionally, refining the framework to address sophisticated threats like zero-day attacks can further bolster its effectiveness. As state actors and malicious entities continue to exploit vulnerabilities in existing cybersecurity models, the riskAIchain model stands as a forward-thinking solution to enhance resilience and pave the way for robust risk management strategies in the face of future challenges.