The Cybersecurity and the Care Robots: A Viewpoint on the Open Problems and the Perspectives
Abstract
:1. Introduction
- The stability.
- The lower limbs.
- The upper limbs.
- (a)
- To investigate the positioning of CRs in CS studies.
- (b)
- Analyse the problems and peculiarities of the devices that have an impact in this area.
- (c)
- Take stock of the related issues of ethics and regulation.
2. The Position of the Care Robots in the Studies
3. Ethics, Care Robots and Cybersecurity
4. Regulatory Framework, Care Robots and Cybersecurity
4.1. Care Robots and Safety Regulations
4.2. Care Robots and Medical Device Regulation
4.3. Care Robots and Regulations on the Cybersecurity
- The directive on security of network and information systems (also called NIS Directive) that provides measures for boosting the overall CS in the EU [54].
- The General Data Protection Regulation (GDPR) obligating to implement appropriate measures to ensure a level of security appropriate to relevant risks [55].
- The EU Cyber-security Act (Regulation (EU) 2019/881) which establishes an EU-wide cybersecurity certification framework [57].
5. Cyber-Attacks Applicable to Care Robots
5.1. Attacks on the Hardware
5.2. Attacks on the Firmware
5.3. Attacks on Communications
6. Conclusions
6.1. Highlights
- Ethics has an important role and a peculiarity on CRs, such as on the SRs [29]. An in-depth analysis of the ethical issues in this discipline has identified two macro-sectors [30,31]. The first macro-sector is the ethics in a responsible research and innovation [30]. The second macro-sector is the ethics problem encountered while building moral CRs [31]. A strong connection emerges between ethical issues and CS from the examination of the two macro-sectors (also correlated). There is a strong need to rethink a CS connected to ethics issues.
- Targeted surveys with interviews and questionnaires regarding the CS behaviours of insiders with CRs will have to be conducted, as already been carried out, for example, in the health domain generally [28]. This will be useful for building medical knowledge.
- There are shadows in EU MD regulations [53]. First, it focuses a lot on manufacturers and little on recipients/ users. Second, [9] the compliance with CS requirements is challenging, in part due to the potential overlap of different certification schemes with varying geographical or product scope and evolution of external to the MDR regulations. Third, the intended use and certification, often, do not seem aligned.
- There are limits in the application of specific CS certifications. They are voluntary, as in the case of the Cybersecurity ACT [56].
- The CRs would need an ad hoc regulatory framework, in consideration of the peculiarities.
6.2. Reflections
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Giansanti, D. Cybersecurity and the digital-health: The challenge of this millennium. Healthcare 2021, 9, 62. [Google Scholar] [CrossRef]
- Giansanti, D.; Monoscalco, L. The cyber-risk in cardiology: Towards an investigation on the self-perception among the cardiologists. Mhealth 2021, 7, 28. [Google Scholar] [CrossRef]
- Cobo Hurtado, L.; Viñas, P.F.; Zalama, E.; Gómez-GarcíaBermejo, J.; Delgado, J.M.; Vielba García, B. Development and usability validation of a social robot platform for physical and cognitive stimulation in elder care facilities. Healthcare 2021, 9, 1067. [Google Scholar] [CrossRef]
- Sheridan, T.B. A review of recent research in social robotics. Curr. Opin. Psychol. 2020, 36, 7–12. [Google Scholar]
- Mejia, C.; Kajikawa, Y. Bibliometric analysis of social robotics research: Identifying research trends and knowledgebase. Appl. Sci. 2017, 7, 1316. [Google Scholar]
- Social Robots Market—Growth, Trends, COVID-19 Impact, and Forecasts (2021–2026). Available online: https://www.mordorintelligence.com/industry-reports/social-robots-market (accessed on 22 February 2021).
- Dolic, Z.; Castro, R.; Moarcas, A. Robots in Healthcare: A Solution or a Problem? Study for the Committee on Environment, Public Health, and Food Safety. Luxembourg: Policy Department for Economic, Scientific and Quality of Life Policies, European Parliament. 2019. Available online: https://www.europarl.europa.eu/RegData/etudes/IDAN/2019/638391/IPOL_IDA(2019)638391_EN.pdf (accessed on 25 November 2021).
- Boldrini, P.; Bonaiuti, D.; Mazzoleni, S.; Posteraro, F. Rehabilitation assisted by robotic and electromechanical devices for people with neurological disabilities: Contributions for the preparation of a national conference in Italy. Eur. J. Phys. Rehabil. Med. 2021, 57, 458–459. [Google Scholar] [CrossRef]
- Fosch-Villaronga, E.; Mahler, T. Safety and robots: Strengthening the link between cybersecurity and safety in the context of care robots. Comput. Law Secur. Rev. 2021, 41, 105528. [Google Scholar]
- European Foresight Monitoring Network, EFMN (2008) Roadmap Robotics for Healthcare. Foresight Brief No. 157. Available online: http://www.foresight-platform.eu/wp-content/uploads/2011/02/EFMN-Brief-No.-157_Robotics-for-Healthcare.pdf (accessed on 22 February 2021).
- European Parliament Resolution of 12 February 2019 on a Comprehensive European Industrial Policy on Artificial Intelligence and Robotics (2018/2088(INI)). Available online: http://www.europarl.europa.eu/doceo/document/TA-8-2019-0081_EN.pdf (accessed on 22 February 2021).
- Specific Research on the Pubmed Database. Available online: https://pubmed.ncbi.nlm.nih.gov/?term=%28cybersecurity%29+AND+%28healthcare%29&sort=date&size=200 (accessed on 25 November 2021).
- Specific Research on the Pubmed Database: (cybersecurity) AND (healthcare) AND (care robots). Available online: https://pubmed.ncbi.nlm.nih.gov/?term=%28cybersecurity%29+AND+%28healthcare%29+AND+%28care+robots%29&sort=date&size=200 (accessed on 25 November 2021).
- Specific Research on the Pubmed Database: (safey[Title/Abstract]) AND (robot). Available online: https://pubmed.ncbi.nlm.nih.gov/?term=%28safey%5BTitle%2FAbstract%5D%29+AND+%28robot%29&sort=date (accessed on 25 November 2021).
- Specific Research on the Pubmed Database: (risk [Title/Abstract]) AND (robot). Available online: https://pubmed.ncbi.nlm.nih.gov/?term=%28risk+%5BTitle%2FAbstract%5D%29+AND+%28robot%29&sort=date&size=200 (accessed on 22 November 2021).
- Murashov, V.; Hearl, F.; Howard, J. Working safely with robot workers: Recommendations for the new workplace. J. Occup. Environ. Hyg. 2016, 13, D61–D71. [Google Scholar] [CrossRef] [Green Version]
- Missala, T. Paradigms and safety requirements for a new generation of workplace equipment. Int. J. Occup. Saf. Ergon. 2014, 20, 249–256. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Bortot, D.; Ding, H.; Antonopolous, A.; Bengler, K. Human motion behavior while interacting with an industrial robot. Work 2012, 41 (Suppl. 1), 1699–1707. [Google Scholar] [CrossRef] [Green Version]
- Guangnan, Z.; Tao, H.; Rahman, M.A.; Yao, L.; Al-Saffar, A.; Meng, Q.; Liu, W.; Yaseen, Z.M. Security and privacy issues related to the workplace-based security robot system. Work 2021, 68, 871–879. [Google Scholar] [CrossRef]
- Zheyuan, C.; Rahman, M.A.; Tao, H.; Liu, Y.; Pengxuan, D.; Yaseen, Z.M. Need for developing a security robot-based risk management for emerging practices in the workplace using the Advanced Human-Robot Co. Work 2021, 68, 1–10. [Google Scholar]
- Yaacoub, J.A.; Noura, H.N.; Salman, O.; Chehab, A. Robotics cyber security: Vulnerabilities, attacks, countermeasures, and recommendations. Int. J. Inf. Secur. 2021, 19, 1–44. [Google Scholar] [CrossRef]
- Vulpe, A.; Crăciunescu, R.; Drăgulinescu, A.M.; Kyriazakos, S.; Paikan, A.; Ziafati, P. Enabling security services in socially assistive robot scenarios for healthcare applications. Sensors 2021, 21, 6912. [Google Scholar] [CrossRef]
- Liu, Y.; Yi, Y.; Deng, P.; Zhang, W. Preclinical evaluation of the new EDGE SP 1000 single-port robotic surgical system in gynecology minimal access surgery. Surg. Endosc. 2021, 1–6, (Online ahead of print). [Google Scholar] [CrossRef]
- Li, I.H.; Lin, Y.S.; Lee, L.W.; Lin, W.T. Design, manufacturing, and control of a pneumatic-driven passive robotic gait training system for muscle-weakness in a lower limb. Sensors 2021, 21, 6709. [Google Scholar] [CrossRef]
- Lhotska, L. Application of industry 4.0 concept to health care. Stud. Health Technol. Inform. 2020, 273, 23–37. [Google Scholar] [CrossRef] [PubMed]
- Jarota, M. Artificial intelligence and robotisation in the EU—should we change OHS law? J. Occup. Med. Toxicol. 2021, 16, 18. [Google Scholar] [CrossRef]
- HCI 2020 International 22st International Conference on Human—Computer Interaction. Available online: https://2020.hci.international/files/HCII2020_Final_Program.pdf (accessed on 25 November 2021).
- Coventry, L.; Branley-Bell, D.; Sillence, E.; Magalini, S.; Mari, P.; Magkanaraki, A.; Anastasopoulou, K. Cyber-risk in healthcare: Exploring facilitators and barriers to secure behaviour. In Proceedings of the 22nd International Conference on Human Computer Interaction, Copenhagen, Denmark, 19–24 July 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 105–122. [Google Scholar]
- Specific Research on the Pubmed Database: (social robot) AND (ethics). Available online: https://pubmed.ncbi.nlm.nih.gov/?term=%28social+robot%29+AND+%28ethics%29&sort=date&size=200 (accessed on 25 November 2021).
- Stahl, B.C.; Coeckelbergh, M. Ethics of healthcare robotics: Towards responsible research and innovation. Robot. Auton. Syst. 2016, 86, 152–161. [Google Scholar]
- Gordon, J.S. Building moral robots: Ethical pitfalls and challenges. Sci. Eng. Ethics 2020, 26, 141–157. [Google Scholar] [CrossRef]
- Coeckelbergh, M. Human development or human enhancement? A methodological reflection on capabilities and the evaluation of information technologies. Ethics Inf. Technol. 2011, 13, 81–92. [Google Scholar] [CrossRef] [Green Version]
- Coeckelbergh, M. Are emotional robots deceptive? IEEE Trans. Affect. Comput. 2012, 3, 388–393. [Google Scholar] [CrossRef]
- Coeckelbergh, M. E-care as craftsmanship: Virtuous work, skilled engagement, and information technology in health care. Med. Health Care Philos. 2013, 16, 807–816. [Google Scholar]
- Coeckelbergh, M. Good healthcare is in the ‘‘how’’: The quality of care, the role of machines, and the need for new skills. In Machine Medical Ethics; van Rysewyk, S.P., Pontier, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 33–48. [Google Scholar]
- Decker, M.; Fleischer, T. Contacting the brain—aspects of a technology assessment of neural implants. Biotechnol. J. 2008, 3, 1502–1510. [Google Scholar] [CrossRef]
- Sharkey, A.; Sharkey, N. Granny and the robots: Ethical issues in robot care for the elderly. Ethics Inform. Technol. 2010, 14, 27–40. [Google Scholar]
- Sparrow, R.; Sparrow, L. In the hands of machines? The future of aged care. Minds Mach. 2006, 16, 141–161. [Google Scholar]
- Whitby, B. Do you want a robot lover. In Robot Ethics: The Ethical and Social Implications of Robotics; Lin, P., Abney, K., Bekey, G.A., Eds.; MIT Press: Cambridge, MA, USA, 2011; pp. 233–249. [Google Scholar]
- Anderson, S.L.; Anderson, M. Towards a principle-based healthcare agent, In Machine Medical Ethics; van Rysewyk, S.P., Pontier, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 67–78. [Google Scholar]
- Coeckelbergh, M. Artificial agents, good care, and modernity. Theor. Med. Bioeth. 2015, 36, 265–277. [Google Scholar]
- Tonkens, R. Ethics of robotic assisted dying. In Machine Medical Ethics; van Rysewyk, S.P., Pontier, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 207–232. [Google Scholar]
- van Rysewyk, S.P.; Pontier, M. A hybrid bottom-up and top-down approach to machine medical ethics: Theory and data. In Machine Medical Ethics; Van Rysewyk, S.P., Pontier, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 93–110. [Google Scholar]
- Whitby, B. Automating medicine the ethical way. In Machine Medical Ethics; van Rysewyk, S.P., Pontier, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; p. 233. [Google Scholar]
- Moor, J.H. The nature, importance, and difficulty of machine ethics. Res. Gate 2006, 21, 18–21. [Google Scholar]
- Robot ethics: The ethical and social implications of robotics. In Intelligent Robotics and Autonomous Agents; Lin, P.; Abney, K.; Bekey, G.A. (Eds.) MIT Press: Cambridge, MA, USA, 2014. [Google Scholar]
- Wallach, W.; Allen, C. Moral Machines: Teaching Robots Right from Wrong; Oxford University Press: Oxford, UK, 2010. [Google Scholar]
- Anderson, M.; Anderson, S.L. Machine Ethics; Cambridge University Press: Cambridge, MA, USA, 2011. [Google Scholar]
- Gunkel, D.J.; Bryson, J. The machine as moral agent and patient. Philos. Technol. 2014, 27, 5–142. [Google Scholar]
- Anderson, S.L. Machine metaethics. In Machine Ethics; Anderson, M., Anderson, S.L., Eds.; Cambridge University Press: Cambridge, MA, USA, 2011; pp. 21–27. [Google Scholar]
- Finocchiaro, G. Protection of privacy and cyber risk in healthcare. Pharm. Policy Law. 2018, 19, 121–123. [Google Scholar]
- Directive 2001/95/EC of the European Parliament and of the Council of 3 December 2001 on General Product Safety 2001. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=celex%3A52003PC0048 (accessed on 25 November 2021).
- Regulation (EU) 2017/745 of the European Parliament and of the Council of 5 April 2017 on Medical Devices, amending Directive 2001/83/EC, Regulation (EC) No 178/2002 and Regulation (EC) No 1223/2009 and Repealing Council Directives 90/385/EEC and 93/42/EEC.2017. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/HTML/?uri=CELEX:32017R0745&from=IT (accessed on 25 November 2021).
- NIS Directive (The Directive on Security of Network and Information Systems). Available online: https://www.itgovernance.eu/fi-fi/nis-directive-fi (accessed on 25 November 2021).
- Complete Guide to GDPR Compliance. Available online: https://gdpr.eu/ (accessed on 25 November 2021).
- Shaping Europe’s Digital Future. Available online: https://digital-strategy.ec.europa.eu/en/policies/cybersecurity-act (accessed on 25 November 2021).
- Fraiche, A.M.; Matlock, D.D.; Gabriel, W.; Rapley, F.A.; Kramer, D.B. Patient and provider perspectives on remote monitoring of pacemakers and implantable cardioverter-defibrillators. Am. J. Cardiol. 2021, 149, 42–46. [Google Scholar] [CrossRef]
- Tomaiko, E.; Zawaneh, M.S. Cybersecurity threats to cardiac implantable devices:room for improvement. Curr. Opin. Cardiol. 2021, 36, 1–4. [Google Scholar] [CrossRef]
- Saxon, L.A.; Varma, N.; Epstein, L.M.; Ganz, L.I.; Epstein, A.E. Rates of adoption and outcomes after firmware updates for food and drug administration cybersecurity safety advisories. Circ. Arrhythm. Electrophysiol. 2020, 13, e008364. [Google Scholar] [CrossRef]
- Burnside, M.; Crocket, H.; Mayo, M.; Pickering, J.; Tappe, A.; de Bock, M. Do-it-yourself automated insulin delivery: A leading example of the democratization of medicine. J. Diabetes Sci. Technol. 2020, 14, 878–882. [Google Scholar] [CrossRef]
- Woldaregay, A.Z.; Årsand, E.; Walderhaug, S.; Albers, D.; Mamykina, L.; Botsis, T.; Hartvigsen, G. Data-driven modeling and prediction of blood glucose dynamics:Machine learning applications in type 1 diabetes. Artif. Intell. Med. 2019, 98, 109–134. [Google Scholar] [CrossRef]
- DeBoer, M.D.; Breton, M.D.; Wakeman, C.; Schertz, E.M.; Emory, E.G.; Robic, J.L.; Kollar, L.L.; Kovatchev, B.P.; Cherñavvsky, D.R. Performance of an artificial pancreas system for young children with type 1 diabetes. Diabetes Technol. Ther. 2017, 19, 293–298. [Google Scholar] [CrossRef]
- Gaikwad, N.B.; Ugale, H.; Keskar, A.; Shivaprakash, N.C. The internet of battlefield things (IoBT) based enemy localization using soldiers location and gunshot direction. IEEE Internet Things J. 2020, 7, 11725–11734. [Google Scholar]
- Tehranipoor, M.; Koushanfar, F. A survey of hardware Trojan taxonomy and detection. IEEE Des. Test Comput 2010, 27, 10–25. [Google Scholar]
- Wang, X.; Mal-Sarkar, T.; Krishna, A.; Narasimhan, S.; Bhunia, S. Software exploitable hardware Trojans in embedded processor. In 2012 IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems (DFT); IEEE: Piscataway Township, NJ, USA, 2012; pp. 55–58. [Google Scholar]
- Elmiligi, H.; Gebali, F.; El-Kharashi, M.W. Multi-dimensional analysis of embedded systems security. Microprocess. Microsyst. 2016, 41, 29–36. [Google Scholar]
- Clark, G.W.; Doran, M.V.; Andel, T.R. Cybersecurity issues in robotics. In 2017 IEEE Conference on Cognitive and Computational Aspects of Situation Management (CogSIMA); IEEE: Piscataway Township, NJ, USA, 2017; pp. 1–5. [Google Scholar]
- Falliere, N.; Murchu, L.O.; Chien, E. W32. stuxnet dossier.White paper, Symantec Corp. Secur. Response 2011, 5, 29. [Google Scholar]
- Fruhlinger, J. What is Wannacry Ransomware, How does It Infect, and Who Was Responsible. 2017. Available online: https://www.csoonline.com/article/3227906/what-is-wannacry-ransomware-how-does-it-infect-and-who-was-responsible.html (accessed on 25 November 2021).
- Bellovin, S.M.; Merritt, M. Encrypted key exchange: Password based protocols secure against dictionary attacks. In 1992 IEEE Computer Society Symposium on Research in Security and Privacy; IEEE: Piscataway Township, NJ, USA, 1992; pp. 72–84. [Google Scholar]
- Kc, G.S.; Keromytis, A.D.; Prevelakis, V. Countering code injection attacks with instruction-set randomization. In Proceedings of the 10th ACM Conference on Computer and Communications Security, Washington, DC, USA, 27–30 October 2003; pp. 272–280. [Google Scholar]
- Miller, J.; Williams, A.B.; Perouli, D. A case study on the cybersecurity of social robots. In Proceedings of the Companion of the 2018 ACM/IEEE International Conference on Human–Robot Interaction, Chicago, IL, USA, 5–8 March 2018; pp. 195–196. [Google Scholar]
- Shahbaznezhad, H.; Kolini, F.; Rashidirad, M. Employees’ behavior in phishing attacks: What individual, organizational, and technological factors matter? J. Comput. Inf. Syst. 2020, 61, 1–12. [Google Scholar]
- Alabdan, R. Phishing attacks survey: Types, vectors, and technical approaches. Future Internet 2020, 12, 168. [Google Scholar]
- Mo, Y.; Garone, E.; Casavola, A.; Sinopoli, B. False data injection attacks against state estimation in wireless sensor networks. In 2010 49th IEEE Conference on Decision and Control (CDC); IEEE: Piscataway Township, NJ, USA, 2010; pp. 5967–5972. [Google Scholar]
- Senie, D.; Ferguson, P. Network ingress filtering: Defeating denial of service attacks which employ IP source address spoofing. Network 1998. [Google Scholar]
- Navas, R.E.; Le Bouder, H.; Cuppens, N.; Cuppens, F.; Papadopoulos, G.Z. Do not trust your neighbors! A small IoT platform illustrating a man-in-the-middle attack. In Proceedings of the International Conference on Ad-Hoc Networks and Wireless, St. Malo, France, 5–7 September 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 120–125. [Google Scholar]
- Evidence-Based Medicine Guidelines. Available online: https://www.ebm-guidelines.com/dtk/ebmg/home (accessed on 25 November 2021).
- Luce, B.R.; Drummond, M.; Jönsson, B.; Neumann, P.J.; Schwartz, J.S.; Siebert, U.; Sullivan, S.D. EBM, HTA, and CER: Clearing the confusion. Milbank Q. 2010, 88, 256–276. [Google Scholar] [CrossRef] [Green Version]
- Office of Technology Assessment. 1978. Assessing the Efficacy and Safety of Medical Technologies. September. NTIS order #PB-286929. Available online: http://www.fas.org/ota/reports/7805.pdf (accessed on 25 November 2009).
- INAHTA (International Network of Agencies for Health Technology Assessment). HTA Resources. 2009. Available online: http://www.inahta.org/HTA/ (accessed on 25 November 2009).
- Candiani, G.; Colombo, C.; Daghini, R.; Magrini, N. Come Organizzare una Conferenza di Consenso. Manuale Metodologico, Roma, ISS-SNLG. 2009. Available online: https://www.psy.it/wp-content/uploads/2018/02/Manuale-Metodologico-Consensus.pdf (accessed on 25 November 2021).
- Arcelloni, M.C.; Milani, C. Consensus Conference: Uno Strumento per la Pratica Clinica Riferimenti Storico-Metodologici e Stato Dell’arte dei Lavori Italiani sul Disturbo Primario del Linguaggio e sui Disturbi Specifici dell’Apprendimento. Available online: https://rivistedigitali.erickson.it/il-tnpee/archivio/vol-1-n-1/riferimenti-storico-metodologici-e-stato-dellarte-dei-lavori-italiani-sul-disturbo-primario-del-linguaggio-e-sui-disturbi-specifici-dellapprendimento/ (accessed on 25 November 2021).
- McGlynn, E.A.; Kosecoff, J.; Brook, R.H. Format and conduct of consensus development conferences. Multi-nation comparison. Int. J. Technol. Assess Health Care 1990, 6, 450–469. [Google Scholar] [CrossRef]
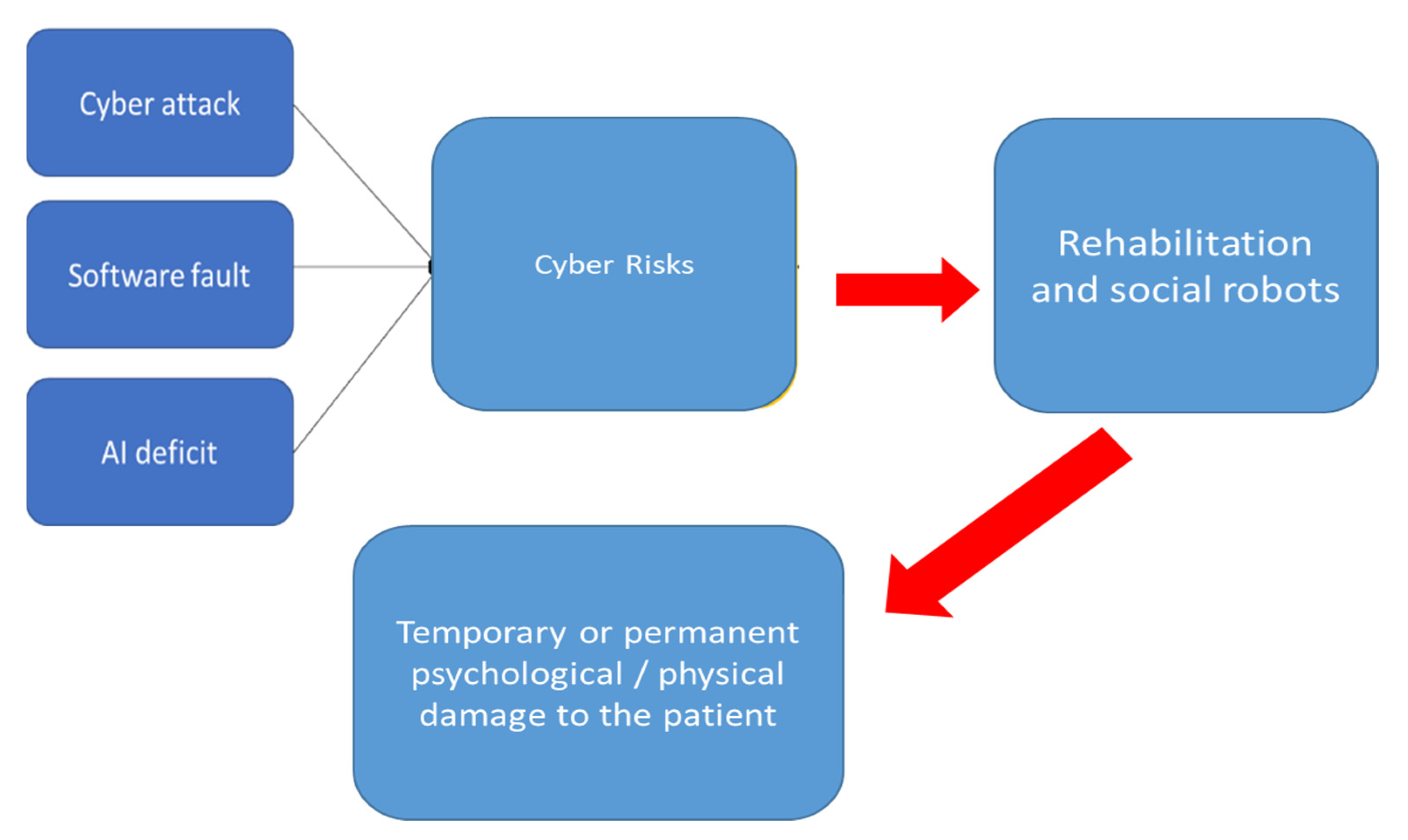
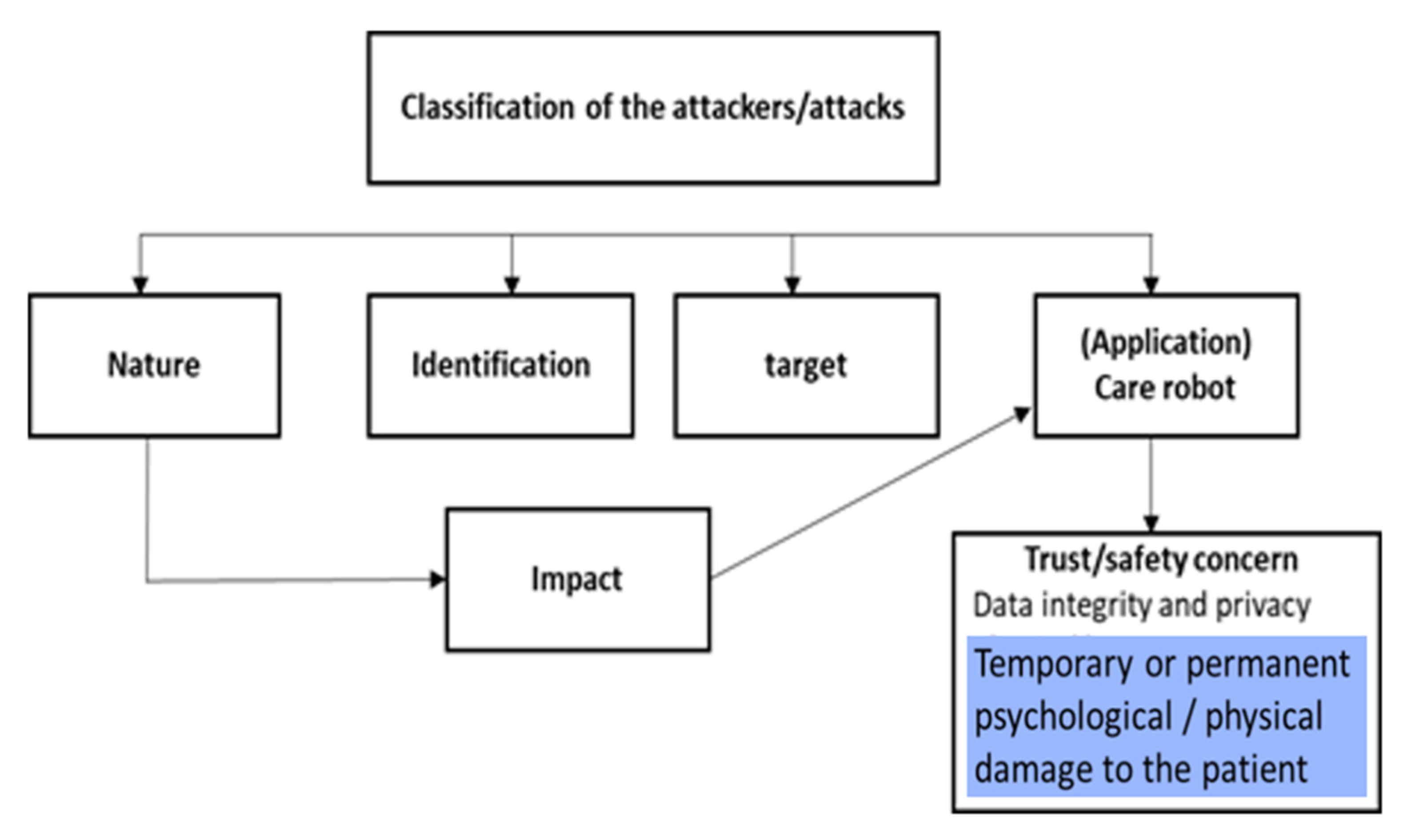


| Application | Description |
|---|---|
| Upper limb rehabilitation | Allowing rehabilitation of the upper limb using exoskeletons or end-effector system |
| Lower limb rehabilitation | Allowing rehabilitation of the lower limb using exoskeletons or end-effector system |
| Stability | Allowing the stability training and recovery using exoskeletons or end-effector system |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Giansanti, D.; Gulino, R.A. The Cybersecurity and the Care Robots: A Viewpoint on the Open Problems and the Perspectives. Healthcare 2021, 9, 1653. https://doi.org/10.3390/healthcare9121653
Giansanti D, Gulino RA. The Cybersecurity and the Care Robots: A Viewpoint on the Open Problems and the Perspectives. Healthcare. 2021; 9(12):1653. https://doi.org/10.3390/healthcare9121653
Chicago/Turabian StyleGiansanti, Daniele, and Rosario Alfio Gulino. 2021. "The Cybersecurity and the Care Robots: A Viewpoint on the Open Problems and the Perspectives" Healthcare 9, no. 12: 1653. https://doi.org/10.3390/healthcare9121653
APA StyleGiansanti, D., & Gulino, R. A. (2021). The Cybersecurity and the Care Robots: A Viewpoint on the Open Problems and the Perspectives. Healthcare, 9(12), 1653. https://doi.org/10.3390/healthcare9121653






