Information Technology and Medical Technology Personnel´s Perception Regarding Segmentation of Medical Devices: A Focus Group Study
Abstract
1. Introduction
- Medical devices can cause substantial harm.
- The user of medical devices must understand how to achieve a high level of security.
- Hackers might be able to reprogram medical devices to send harmful commands.
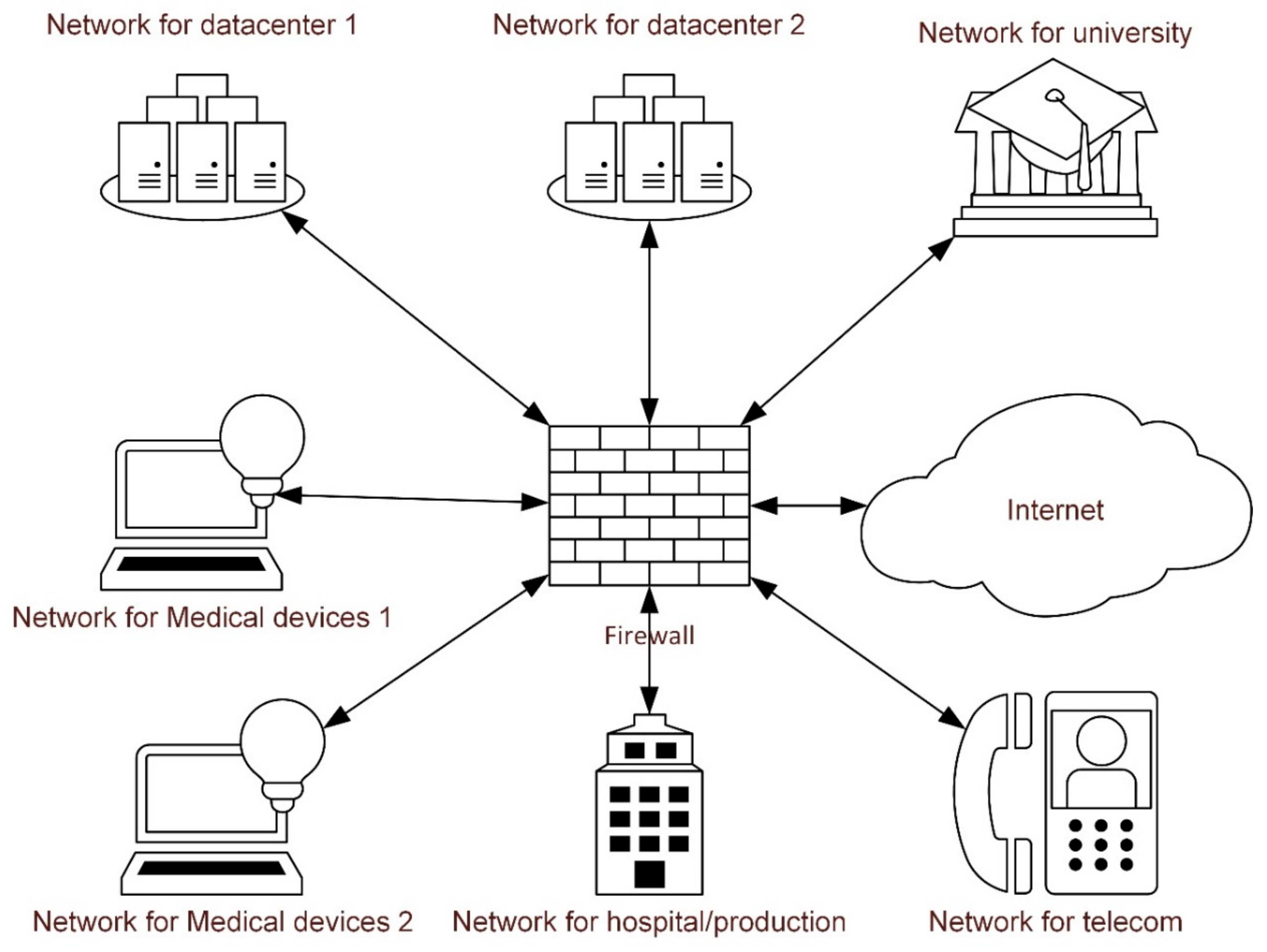
- One way to reduce the risk of hackers and prevent intrusion is network segmentation.
- MT and IT personnel must be positive to the increase in cybersecurity.
2. Material and Methods
2.1. Design and Setting
2.2. Informants
2.3. Ethics
2.4. Data Collection
2.5. Data Analysis
3. Results
3.1. Information Security
3.1.1. Outsider Threats
3.1.2. Insider Threats
3.2. Implementation of Segmentation in Healthcare
3.2.1. Predictions of an Increase in Costs and Administration
3.2.2. Predictions of Required Knowledge Improvement for the Healthcare Organization
3.2.3. Possibilities and Pitfalls Concerning Segmentation
3.2.4. Increased Demands on Medical Device Manufacturers
4. Discussion
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- European Commission. Council Directive 93/42/EEC Concerning Medical Devices. Available online: https://eur-lex.europa.eu/eli/dir/1993/42/2007-10-11 (accessed on 20 January 2020).
- Abernethy, A.P.; Wheeler, J.L.; Bull, J. Development of a health information technology-based data system in community-based hospice and palliative care. Am. J. Prev. Med. 2011, 40, S217–S224. [Google Scholar] [CrossRef] [PubMed]
- Mc Caffery, F.; Burton, J.; Richardson, I. Risk management capability model for the development of medical device software. Softw. Qual. J. 2010, 18, 81–107. [Google Scholar] [CrossRef]
- Tulasidas, S.; Mackay, R.; Craw, P.; Hudson, C.; Gkatzidou, V.; Balachandran, W. Process of designing robust, dependable, safe and secure software for medical devices: Point of care testing device as a case study. J. Softw. Eng. Appl. 2013, 6, 1–13. [Google Scholar] [CrossRef]
- Arney, D.; Venkatasubramanian, K.; Sokolsky, O.; Lee, I.; Venkatasubramanian, K.K. Biomedical devices and systems security. Eng. Med. Biol. Soc. 2011, 11, 2376–2379. [Google Scholar]
- Jha, A.K.; Prasopa-Plaizier, N.; Larizgoitia, I.; Bates, D.W. Patient safety research: An overview of the global evidence. Qual. Saf. Health Care 2010, 19, 42–47. [Google Scholar] [CrossRef] [PubMed]
- Ivarsson, B.; Wiinberg, S.; Svensson, M. Information and/or medical technology staff experience with regulations for medical information systems and medical devices. Health Policy Technol. 2016, 5, 383–388. [Google Scholar] [CrossRef][Green Version]
- Nurse, J.R.; Buckley, O.; Legg, P.A.; Goldsmith, M.; Creese, S.; Wright, G.R.; Whitty, M. Understanding Insider Threat: A Framework for Characterising Attacks. In Proceedings of the 2014 IEEE Security and Privacy Workshops (SPW), San Jose, CA, USA, 17–18 May 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 214–228. [Google Scholar]
- De Bruijn, H.; Janssen, M. Building cybersecurity awareness. The need for evidence-based framing strategies. Gov. Inf. Q. 2017, 34, 1–7. [Google Scholar] [CrossRef]
- Fischbacher-Smith, D.; Fischbacher-Smith, M. The vulnerability of public spaces: Challenges for UK hospitals under the ‘new’ terrorist threat. Public Manag. Rev. 2013, 15, 330–343. [Google Scholar] [CrossRef]
- Coventry, L.; Branley, D. Cybersecurity in healthcare. A narrative review of trends, threats and ways forward. Maturitas 2018, 113, 48–52. [Google Scholar] [CrossRef]
- Leavitt, N. Researchers fight to keep implanted medical devices safe from hackers. Computer 2010, 43, 11–14. [Google Scholar] [CrossRef]
- Martin, G.; Martin, P.; Hankin, C.; Darzi, A.; Kinross, J. Cybersecurity and healthcare: How safe are we? BMJ 2017, 358, j3179. [Google Scholar] [CrossRef]
- Mahler, T.; Nissim, N.; Shalom, E. Know your enemy: Characteristics of cyber-attacks on medical imaging devices. arXiv 2018, arXiv:1801.05583. [Google Scholar]
- Schwartz, S.; Ross, A.; Carmody, S. The evolving state of medical device cybersecurity. Biomed. Instrum. Technol. 2018, 52, 103–111. [Google Scholar] [CrossRef] [PubMed][Green Version]
- Reichenberg, N.; Improving Security via Proper Network Segmentation. Security Week 2014, 20. Available online: https://www.securityweek.com/improving-security-proper-network-segmentation (accessed on 20 January 2020).
- Hagland, M. Cybersecurity—A New Era in Network Segmentation? Available online: https://www.hcinnovationgroup.com/cybersecurity/article/13029865/a-new-era-in-network-segmentation (accessed on 20 January 2020).
- Hiemstra, H. Influence of Building Structure and Building Content on Residential Fires. Master’s Thesis, Lund University, Lund, Sweden, 2016. [Google Scholar]
- Genge, B.; Graur, F.; Haller, P. Experimental assessment of network design approaches for protecting industrial control systems. Int. J. Crit. Infrastruct. Prot. 2015, 11, 24–38. [Google Scholar] [CrossRef]
- Sittig, D.F.; Singh, H. A socio-technical approach to preventing, mitigating, and recovering from ransomware attacks. Appl. Clin. Inform. 2016, 7, 624–632. [Google Scholar]
- Todinov, M. Reducing risk through segmentation, permutations, time and space exposure, inverse states, and separation. Int. J. Risk Conting. Manag. 2015, 4, 1–21. [Google Scholar] [CrossRef]
- Länsisalmi, H.; Kivimäki, M.; Aalto, P.; Ruoranen, R. Innovation in healthcare: A systematic review of recent research. Nurs. Sci. Q. 2006, 19, 66–72. [Google Scholar] [CrossRef]
- Anell, A.; Glenngard, A.H.; Merkur, S. Sweden health system review. Health Syst. Transit. 2012, 14, 1–159. [Google Scholar]
- Fridlund, B. Qualitative methods in healthcare research: Some issues related to utilisation and scrutiny. Care Crit. Ill 1998, 14, 212–214. [Google Scholar]
- Bowling, A. Research Methods in Health: Investigating Health and Health Services; McGraw-Hill Education: Berkshire, UK, 2014. [Google Scholar]
- Graneheim, U.H.; Lundman, B. Qualitative content analysis in nursing research: Concepts, procedures and measures to achieve trustworthiness. Nurse Educ. Today 2004, 24, 105–112. [Google Scholar] [CrossRef]
- Burnard, P. Teaching the analysis of textual data: An experiential approach. Nurse Educ. Today 1996, 16, 278–281. [Google Scholar] [CrossRef]
- Kruse, C.S.; Frederick, B.; Jacobson, T.; Monticone, D.K. Cybersecurity in healthcare: A systematic review of modern threats and trends. Technol. Health Care 2017, 25, 1–10. [Google Scholar] [CrossRef] [PubMed]
- Webb, T.; Dayal, S. Building the wall: Addressing cybersecurity risks in medical devices in the USA and Australia. Comput. Law Secur. Rev. 2017, 33, 559–563. [Google Scholar] [CrossRef]
- Regan, G.; McCaffery, F.; Mc Daid, K.; Flood, D. Medical device standards’ requirements for traceability during the software development lifecycle and implementation of a traceability assessment model. Comput. Stand. Interfaces 2013, 36, 3–9. [Google Scholar] [CrossRef]
- Jalali, M.S.; Razak, S.; Gordon, W. Health care and cybersecurity, bibliometric analysis of the literature. J. Med. Internet Res. 2019, 21, e12644. [Google Scholar] [CrossRef]
| Gender | |
|---|---|
| Women | 3 |
| Men | 15 |
| Age | |
| Mean Standard deviation | 52 ± 10 |
| Median (range) | 51 (33–67) |
| Time in professions (years) | |
| Mean SD | 18 ± 12 |
| Median (range) | 17 (2–40) |
| Highest level of education | |
| High school (n) | 3 |
| University (n) | 15 |
| Meaning Unit | Condensed | Code | Subcategory | Category |
|---|---|---|---|---|
| …So theoretically, if somebody would have a bad intent, it’s very easy today. Considering that today the risk is greater internally than externally. And it doesn’t have to be malicious, it may be that you make a mistake because you have access to things that you should not have access to. And then that’s really a good thing then, to segment, we clearly get what’s stealing from and we can follow it up in a new way… (Participant 2) | “…it doesn’t have to be malicious, of course, you might make a mistake just because you have access to things that you shouldn’t have” (Participant 2). | Improving patient security | Insider threats | Information Security |
| “I think it will require a great deal of resources to get it implemented. I see it as very resource-intensive to implement… longer lead times and complicated administration. There is, as we stated, not enough resources to handle requests in firewall changes…” (Participant 17) | “I see it [implementation] as very resource-intensive to implement … longer lead times and complicated administration” (Participant 17) | Resource-intensive project | Predictions of an increase in costs and administration | Implementation of segmentation in healthcare |
| Categories | Sub-Categories |
|---|---|
| Information Security | Outsider threats |
| Implementation of segmentation in healthcare | Insider threats |
| Predictions of an increase in costs and administration | |
| Predictions of required knowledge improvement for the healthcare organization | |
| Possibilities and pitfalls concerning segmentation |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Johansson, D.; Jönsson, P.; Ivarsson, B.; Christiansson, M. Information Technology and Medical Technology Personnel´s Perception Regarding Segmentation of Medical Devices: A Focus Group Study. Healthcare 2020, 8, 23. https://doi.org/10.3390/healthcare8010023
Johansson D, Jönsson P, Ivarsson B, Christiansson M. Information Technology and Medical Technology Personnel´s Perception Regarding Segmentation of Medical Devices: A Focus Group Study. Healthcare. 2020; 8(1):23. https://doi.org/10.3390/healthcare8010023
Chicago/Turabian StyleJohansson, David, Patrik Jönsson, Bodil Ivarsson, and Maria Christiansson. 2020. "Information Technology and Medical Technology Personnel´s Perception Regarding Segmentation of Medical Devices: A Focus Group Study" Healthcare 8, no. 1: 23. https://doi.org/10.3390/healthcare8010023
APA StyleJohansson, D., Jönsson, P., Ivarsson, B., & Christiansson, M. (2020). Information Technology and Medical Technology Personnel´s Perception Regarding Segmentation of Medical Devices: A Focus Group Study. Healthcare, 8(1), 23. https://doi.org/10.3390/healthcare8010023





