Abstract
In the context of new threats to Public Key Cryptography arising from a growing computational power both in classic and in quantum worlds, we present a new group law defined on a subset of the projective plane over an arbitrary field , which lends itself to applications in Public Key Cryptography and turns out to be more efficient in terms of computational resources. In particular, we give explicitly the number of base field operations needed to perform the mentioned group law. Based on it, we present a Diffie-Hellman-like key agreement protocol. We analyze the computational difficulty of solving the mathematical problem underlying the proposed Abelian group law and we prove that the security of our proposal is equivalent to the discrete logarithm problem in the multiplicative group of the cubic extension of the finite field considered. We present an experimental setup in order to show real computation times along a comparison with the group operation in the group of points of an elliptic curve. Based on current state-of-the-art algorithms, we provide parameter ranges suitable for real world applications. Finally, we present a promising variant of the proposed group law, by moving from the base field to the ring , and we explain how the security becomes enhanced, though at the cost of a longer key length.
Keywords:
abelian group law; discrete logarithm problem; norm of an extension; projective cubic curve MSC:
Primary 20K01; Secondary 12F05; 14H50; 15A04; 68Q25; 94A60
1. Introduction and Related Work
Neal Koblitz [1] and Victor Miller [2] presented independently but simultaneously proposals that made use of the multiplicative group of a finite field in order to implement certain asymmetric cryptosystems. Koblitz presented an implementation of Diffie-Hellman key-agreement protocol [3] based on the use of elliptic curves. On his part, Miller offered a proposal more on the theoretical side, avoiding comparisons with existing implementations. In all those cases, the security is based on the infeasibility of the discrete logarithm problem over elliptic curves (ECDLP), which is to this day considered as difficult as the integer factorization problem (IFP), upon which RSA [4] cryptosystem is based, or the discrete logarithm problem (DLP) employed in ElGamal cryptosystem [5].
Diffie-Hellman key-agreement protocol for elliptic curves (ECDH) consists essentially in mapping the operations customarily carried out in the multiplicative group to the set of points of an elliptic curve, endowed with an additive group operation. However, this protocol painfully succumbs in the face of a plain man-in-the-middle attack and, for this reason, Menezes, Qu, and Vanstone proposed [6] an authenticated variant, known as Elliptic Curve Menezes-Qu-Vanstone key agreement protocol (ECMQV). In general, the outcome of these key-agreement protocols is that the users eventually share a value—the key or a seed to derive the key—which was initially unknown for any of them, and cannot be inferred (more precisely: It is computationally infeasible to infer it) from the information exchanged between the parties.
Along with these key-agreement protocols, several elliptic-curve-based asymmetric cryptosystems have seen the light in these last years. The first proposals of the so-called elliptic-curve cryptosystems (ECC) were revisions adapted from existing systems, such as ElGamal’s [5], or Massey-Omura’s [7]. They were publicized by Koblitz in [1].
The problem with the elliptic-curve version of ElGamal’s and Massey-Omura’s cryptosystems is that the user needs to map each possible message to a point of the curve. This fact is an important drawback since, on the one hand, the cardinal of the curve points is finite, so the user is limited to a finite number of possible messages; and, on the other hand, the user needs some kind of “equivalence table” between messages and points in order to cipher and decipher. Therefore, these cryptosystems are limited in practice to those settings in which the set of possible messages is fixed in advance.
In order to overcome these limitations, Menezes and Vanstone proposed in [8] the Elliptic Curve Menezes-Vanstone cryptosystem (ECMV) for elliptic curves over finite fields . In ECMV, each message is represented by elements of the Cartesian product , not necessarily points of the elliptic curve. The protocol includes a systematic procedure to divide any message into blocks and to codify each block as an element of the Cartesian product. The downside is that ciphertext length depends entirely on plaintext length.
In spite of the efforts, ECC has abandoned the battlefield of cryptosystems in favor of key-agreement protocols as a building block for hybrid cryptosystems. In the latter, ECC permits the users to share a session (ephemeral) key, whence a symmetric key is derived to be used together with a symmetric cryptosystem, such as AES.
In this setting, Mihir Bellare and Philip Rogaway [9] published in 1997 the Discrete Logarithm Augmented Encryption Scheme (DLAES). Along with Michel Abdalla, the system was improved in 1998 by the same authors, and renamed as DHAES (Diffie-Hellman Augmented Encryption Scheme) [10]. Eventually renamed to DHIES (Diffie-Hellman Integrated Encryption Scheme) [11,12], it is an improved extension of ElGamal’s cryptosystem [5]. DHIES is really a complex protocol, much more involved than ElGamal or Koblitz’s proposal in [1], which includes public key operations, symmetric ciphering, authentication and hash function computation. While ElGamal and Koblitz directly ciphered a message, without any further use of other necessary elements for a proper integrated scheme, DHIES provides security against chosen ciphertext attacks at no extra cost in terms of number of operations or key lengths [11]. Together with other proposals, DHIES was employed in the preparation of standards [13,14].
Finally, it is worth mentioning the so-called ECIES (Elliptic Curve Integrated Encryption Scheme), which embraces several integrated ciphering schemes using DHIES-based elliptic curves and it is described in the relevant security standards, such as [13,14,15] (a comparison among different ECIES implementations may be found in [16]). Remark that, whenever ECIES is recommended (even with minor differences regarding implementations), it is to be used in a hybrid setting, where a (DH-type) session key agreement protocol is a must.
Setting aside the already mentioned cryptosystems and key-agreement protocols, it is probably in digital signature schemes that elliptic curve cryptography is mostly demanded. The ElGamal-based Elliptic Curve Digital Signature Algorithm (ECDSA) is analogous to the Digital Signature Algorithm (DSA) [17], using additive rather than multiplicative notation. ECDSA has consolidated into an internationally accepted standard [13,18].
When dealing with ECC, one of the most important aspects to keep in mind is the processes of curve generation and selection. Several standards tackle such methods and show examples of curve selection as part of the public-key generation process. Among them, it is worth mentioning X9.63 [13], IEEE 1363 [19], and FIPS 186-4 [20], issued by the National Institute of Standards and Technology (NIST) of the USA. However, in practice, such standards lack precision and clarity when it comes to selecting seeds for random generation, or prime numbers, thus limiting the ability of serving really practical purposes.
For these reasons, several initiatives have ripened, such as Brainpool [21], considered to be the first international proposal to provide clear and transparent procedures in order to generate the parameters of elliptic curves for cryptographic purposes. Under the Brainpool initiative, several elliptic curves, presented in reduced Weierstrass format, have been considered safe beyond any doubt by many experts.
Later on, researchers Daniel Bernstein and Tania Lange [22] reviewed the elliptic curve generation procedures, including those in Brainpool. In particular, they scrutinized 20 curves from several sources under a number of security requirements that they considered a must. The result was that just only Edwards and Montgomery curves [23] satisfied those requirements. In view of this outcome, the experts decided to propose a new set of curves, known as SafeCurves that really met the set of safety requirements [22]. Moreover, Baignères [24] proposed a new Edwards elliptic curve (the so-called million dollar curve) by means of a new technique that insists in the randomness of the input parameters to the generation process.
In spite of those efforts, the currently most deployed elliptic curves, both in hardware and software implementations, are those presented in the reduced Weierstrass format, whereas Edwards or Montgomery curves are seldom used, maybe because the additional security provided by them is not worth their lower computation efficiency (multiplications with scalars). A performance comparison among the three types of curves cited above can be found in [25]. In the latter, the authors resorted to the examples provided by the initiative SafeCurves, together with a Java implementation developed by them.
Koyama et al. proposed in [26] the use of elliptic curves over the ring , where n is an odd composite square-free integer. In particular, n is the product of two large primes, as in the RSA cryptosystem. The security of the cryptosystem of Koyama et al.’s is based upon IFP, though the authors did not prove whether solving the IFP was equivalent to breaking their cryptosystem. Later on, Meyer and Müller proved in [27] that breaking a modified version of Koyama’s cryptosystem was indeed equivalent to factorizing n. In addition, they proposed a digital signature scheme based on elliptic curves defined over .
Another interesting question is the ever growing necessity of implementing elliptic curve cryptography on ubiquitous portable devices (smartphones, smart cards, pen-drives, and the like), which gives rise to new challenges. Actually, these devices normally present severe limitations regarding storage capacity or processing power, as compared with ordinary desktop computers. Elliptic curve cryptography is amenable to these devices since key sizes are much smaller than in other cryptosystems (for example, RSA) for similar security levels.
It is very common nowadays to find elliptic curve cryptography on such devices, and hence implementations of multiplication operations. These operations, in turn, are threatened by the ever more powerful side channel and fault injection attacks. For example, Reference [28] documents recent developments on those side channel attacks to ECC implementations. It is completely necessary to implement the multiplication algorithms in such a way that they do not leak any information to possible attackers. Reference [29] describes some options to avoid such attacks when implementing scalar multiplications for elliptic curves.
It is also very well known that the advent of a universal quantum computer with sufficient computation power could break the most commonly used asymmetric cryptosystems. In fact, Shor’s algorithm [30], proposed in 1997, is known to solve IFP and DLP (or ECDLP) in polynomial time if such quantum computer does exist; however, there is no agreement as to how many qubits would be required to execute Shor’s or other quantum algorithms, but some estimations point to a number of qubits several orders of magnitude larger than the number of qubits available in currently existing quantum computers [31]. Should such number of qubits be available, IFP or DLP could be solved in a bunch of hours. For example, a personal computer needs, roughly speaking, bit operations to factor a number n, whereas a quantum computer executing Shor’s algorithm could perform such factorization with only bit operations and using bit storage.
Though it seems that a quantum computer with the required computation power will not be available any time soon, the new source of attacks coming from quantum world and the need to ensure that the information protected by current asymmetric systems continues to be accessible forced the NIST to launch an international call [32] for new cryptographic algorithms resilient to the power leveraged by quantum computation: the so-called quantum-resistant algorithms. These are expected to cover at least proposals for new asymmetric encryption schemes, digital signature schemes, and key encapsulation mechanisms (KEM). The main quantum-resistant proposals include difficult problems stemming from coding theory, lattices, hash functions, and isogenies over elliptic curves, to mention just a few. In January 2019, the NIST published the list of submitted algorithms that have passed on to the second round of the call [33]. Among them, there stands the proposal SIKE as a key encapsulation mechanism that is based on isogenies over elliptic curves.
The previous paragraphs summarize the current state of affairs regarding classic and quantum cryptography and make it clear that there is much to be done in both classic and quantum worlds. Taking that current context into account, this work presents a new group law defined on a subset of the projective plane over an arbitrary field , which lends itself to applications in public key cryptography. Apart from the mathematical novelty implied, this new group law presents several features worth public key cryptosystems, such as:
- a Diffie-Hellman-like key agreement, since such protocol remains a basic piece for any hybrid cryptosystem, as commented above.
- an extension to the ring providing enhanced security, following the same vein as the one followed by [26,27].
- no side channel attacks known to date, given the recentness of this proposal and due to the particular group law defined.
- gives rise to new research lines, such as defining isogenies over the group structure, thus opening the path to a possibly new quantum-resistant problem.
In a nutshell, the main contribution of this paper is to propose a new group law, defined on the complement of a projective cubic plane curve, prove its properties, and consider the possibility of using it as a building block for cryptographic applications in the field of Public Key Cryptography (PKC).
The paper is organized as follows: Section 2 presents the group law and its main characteristics and properties. In particular, we define the mathematical problem associated with the considered group law, and we give the explicit formulas to compute the group operation of any two elements of the group. These formulas, which involve coefficients from the base field, are applicable to any pair of elements of the group with no exception whatsoever, which is advantageous in view of possible cryptographic applications, since this feature helps, for example, to withstand side channel attacks.
As an application of the defined group law to PKC, a cryptographic protocol, in particular, a Diffie-Hellman-like key agreement protocol, is defined in Section 3. We also analyze the computational difficulty of solving the mathematical problem underlying the defined group law, and we prove that the hardness of our problem is equivalent to that of the discrete logarithm problem on the multiplicative group of the cubic extension of the finite field considered.
In Section 4, we consider an entirely analogous system, but shifting the general base field to the ring . We make it clear that this last proposal enhances the security of the system, since it now depends not only on DLP but also on the factorization problem, though at the price of doubling the key length.
The last section is devoted to the conclusions.
2. The Group Law Defined
Our purpose in this section is to search for a particular (finite) group endowed with an internal operation that makes it cyclic provided that certain conditions hold. In the latter case, we define yet another (discrete) logarithm operation, which, if found to be difficult to carry out, may give rise to cryptographic applications.
We will work with three-dimensional vector spaces and their associated two-dimensional projective spaces, defined over finite fields. We will consider certain cubic curve defined over this ambient projective space, so that the set over which we will define our new group operation is precisely the set of points of the projective space that do not belong to that cubic curve.
We will show the conditions under which the cubic curve has no points in the projective space, which means that the group embraces the the full projective space. We will provide the explicit formulas to compute the group law in the base field and the good piece of news is that these formulas are the same for any of the elements in the group, a feature much cherished in cryptographic settings.
Let be a field and let us consider a linear endomorphism of the vector space . We define the polynomial , where . The polynomial Q is homogeneous of degree 3, and does not depend on A, but only on the characteristic polynomial of A.
A new group law is proposed . Let the multiplicative group act on V by the diagonal action, i.e., , and let denote the projective plane, namely . Then, the proposed group law induces an Abelian group law on .
If the characteristic polynomial is irreducible in , then , and therefore the group law extends to the whole projective plane ; moreover, if the base field is a finite field , with characteristic different from 2 or 3, then the group is proved to be cyclic.
The latter property permits us to apply the notion of discrete logarithm to the group . If we fix a generator , then any element h of the group is the addition of g with itself a finite number of times, say n, so that . The number n is the logarithm of h to the base g.
Given any element , and a generator g of the group, the discrete logarithm problem (DLP) consists of finding the smallest integer n, such that . In this work, we prove that the DLP over with a proper choice of the generator is equivalent to the DLP over the multiplicative group .
Popular current cryptosystems are based on the discrete logarithm problem over different groups, such as the group of invertible elements in a finite field, or the group of points of an elliptic curve with the addition of points as group operation. Our proposal could fit perfectly well in the same niche.
As is the case for analogous public key protocols, the users of the present proposal agree to a single base field and an (irreducible) polynomial:
The public system parameters include the base field , coefficients , and a generator g.
Next, we prove that the polynomial Q does not depend on A, but only on the characteristic polynomial of A.
Lemma 1.
Let be a field and let V be the vector space . If is a linear map such that the endomorphisms are linearly independent, then the homogeneous cubic polynomial does not depend on the matrix A but only on the coefficients of its characteristic polynomial .
Proof.
Let be the algebraic closure of . As the endomorphisms are linearly independent, the annihilator polynomial of A coincides with by virtue of the Cayley-Hamilton theorem. Hence, there exists a basis of such that the matrix of A in this basis equals one of the following three matrices:
and, from a simple calculation, we obtain
for every . □
Theorem 1.
Every linear map such that the endomorphisms are linearly independent, induces a law of composition
by the following formula:
where , , .
Moreover, the set of elements such that for some element in coincides with the set , and ⊕ induces a group law
If C denotes the projective cubic curve defined by , then the group law ⊕ also induces a group law
Proof.
In matrix notation, these formulas can equivalently be written as
and as a simple computation shows, the determinant of the linear system above is equal to , where Q is defined by the formula (2). Hence, , for some in , if and only if .
The commutativity of ⊕ is a direct consequence of the invariance of the formula (4) under the substitutions , , .
Moreover, formula (3) can also be written as follows:
From the associativity of the composition law of endomorphisms, we deduce
Hence, , .
From Equation (4), it follows that the unit element is the point , which does not belong to since .
By taking determinants in Equation (3), we obtain
Therefore, the opposite element of exists and it is given by the following formulas:
Finally, if , are replaced by , , respectively, with , then transforms into , thus proving that the group law projects onto . □
Remark 1.
Note that the Equations (4), allowing one to compute the ⊕ group operation in terms of the coefficients in the ground field, are applicable to any element of the group, with no exception at all.
Remark 2.
If , , , then, from Equation (2), we obtain , . Hence, and belong to if and only if , i.e., when A is invertible.
2.1. The Basic Cubic
Proposition 1.
Let be the polynomial introduced in Lemma 1 and let . If is the norm of the extension of , then a point belongs to the cubic curve C defined in Theorem 1 if and only if . In particular, if χ is irreducible in , then C has no point in .
Proof.
Every induces an -linear endomorphism given by , , and, from the very definition of the norm, we have . As a computation shows, we obtain , thus proving the first part of the statement.
Moreover, is irreducible if and only if is a field, and then the only element with norm 0 is in fact . To see this, assume on the contrary that , with and . Since the norm is a group homomorphism, we can write
which is a contradiction. Consequently, the curve C has no point in . □
Corollary 1.
The polynomial χ is irreducible in if and only if the cubic C is irreducible.
Proof.
Actually, if factors in , say , with , then we have
Conversely, if is irreducible in , then, according to the second part of Proposition 1, the only solution to the cubic equation is . Hence, Q must be irreducible, as a reducible cubic admits non-trivial solutions in the ground field. □
Corollary 2.
If the characteristic polynomial χ of A is irreducible in , then there is no linear transformation reducing the polynomial Q defined in (2) to Weierstrass form.
Proof.
Replacing by , , in (2), we obtain a cubic , which is in Weierstrass form (see [34] [§2.1]) if and only if the coefficients a, b, and c of the terms , , and , respectively, vanish. As a computation shows, we have , and we can conclude by applying Proposition 1. □
2.2. Cyclicity
Theorem 2.
If is a finite field of characteristic different from 2 or 3 and the polynomial introduced in Lemma 1 is irreducible in , then the group is cyclic.
Proof.
Since , the polynomial is separable and in its splitting field we have , the roots , , being pairwise distinct, and in a certain basis of the matrix of A is given by the formula (1). As the Galois group acts transitively on the roots of , there exist two automorphisms such that and . If , , , is an element in , then, for every positive integer n, we have
Consequently, if is a generator of the multiplicative group , then the vector generates the group and its corresponding projective point generates the group , with . □
Remark 3.
It is important to keep in mind that the implication in Theorem 2 works only in the way in which it is worded. If one selects a generator of the group , it will in general be a generator of only a subgroup of the whole group. Consequently, when choosing a generator for , it is convenient to pick it from the set of generators in and, after that, project it onto .
Remark 4.
As the order of the group is , the statement of Theorem 2 means that there exists an element of order . According to the proof of Theorem 2, this is equivalent to saying that the matrix A in (1) is of order in the linear group . A classical result (see [35] [Theorem, p. 379]) states that such a collineation always exists, but we need a direct proof of this fact to be able to apply it below in Section 3.1; see also [36] [Proposition 2.1].
Remark 5.
When the polynomial χ is reducible, experimental tests carried out in the prime field show that the projective cubic curve C defined as has a number of points from the set only.
Since the projective space has a total of points, the group is left, respectively, with points.
If the number of points of C is either or , then the group is still cyclic, and has the expected number of generators, namely, either or , respectively, where φ is Euler’s totient function.
However, none of the other two possibilities give rise to a cyclic group. Rather, for the case where C has points, there appears a number of cyclic groups, whose cardinalities are the divisors of ; it is important to remark that the total number of points left for the group is precisely . Thus, the group can be decomposed as a direct sum of a number of cyclic groups such that the product of their cardinalities is .
As for the case when C has points, the group is not cyclic either and can be decomposed as a direct sum of 2 cyclic groups with p points each. Remark that now the total number of points left for the group is , so again the numbers of points of the cyclic groups of this case match the divisors of p.
Remark 6.
Hasse’s theorem states [37] [Theorem 4.1] that the number of points in an elliptic curve verifies that , i.e., . However, the projective space in our proposal has points, thus rendering brute-force and known-message attacks much more difficult.
3. A Cryptographic Protocol
We have presented the group and the conditions under which it is cyclic. In this section, we will show how this group can be profited as a basic building block for cryptographic applications, and we will assess its cryptographic security level.
We resort to current state-of-the-art algorithms deployed to attack the discrete logarithm problem. Among them, index-calculus algorithm stands out since it displays a subexponential expected running time.
Equipped with these tools, we will show how this group permits us to set up a basic, à la Diffie-Hellman, key-exchange protocol, and what cryptographic security is to be expected from it. Actually, we will present the range in which the protocol setup parameters should lie in order to achieve a certain security level.
We also provide an experimental setup that we have carried out in order to obtain computation times for the new group operation on a real setting, along with a comparison with computation times required to sum points on elliptic curves.
First of all, we establish the computational security of the mathematical problem defined over the cyclic group considered. Later on, as an example of cryptographic protocol, we present a Diffie-Hellman-like key agreement protocol.
3.1. Equivalence of DLP in and
Proposition 2.
Let be a finite field of characteristic or 3. Assume the polynomial in Lemma 1 is irreducible in , and let be a root of χ.
If is a generator of the group and belongs to this group, then is a solution to the equation
if and only if n is a solution to the equation in the multiplicative group , where , and .
Therefore, the DLP in the group is equivalent to the DLP in .
Proof.
Letting , the statement follows from the matrix formula in the proof of Theorem 2 taking the very definition of the group law ⊕ by formula (3) into account. □
In the present case, Proposition 2 states the “equivalence” because the reduction of problems (see, for example, [38] [p. 5], [39] [Ch. 8]) works both ways, namely, DLP in the group reduces to the DLP in and the other way around. Hence, Proposition 2 proves that the use of the group is safe for standard implementations in PKC (e.g., see [34] [§1.6]), since the security it provides is equivalent to that of DLP in , as long as the caveat stated in Remark 3 is taken into account.
In terms of cryptanalysis, logarithms in can be computed using “generic” algorithms, i.e., those that assume no particular structure in (or extra knowledge of) the group. The most popular ones are Pohlig-Hellman (which reduces the computation in the whole group to the computation of the logarithm in all subgroups of prime order of ), Shank’s Baby Step/Giant Step, and Pollard’s Rho algorithm. All of them need an exponential computation time.
However, there exists the so-called index-calculus algorithm, which is much faster as it is able to compute discrete logarithms in the multiplicative group of a finite field in subexponential time (see, e.g., [40]). Since the operations in the proposed group can be efficiently transferred to those in , it follows that index-calculus algorithm can be applied to the multiplicative group of the latter. This fact does not render the group operation automatically useless in the face of possible cryptographic applications, as long as proper key lengths are utilized.
For general finite fields, such as the proposed one, with a multiplicative group of size N, current state-of-the-art algorithms (including index-calculus) report computation times of
where and c are parameters in the ranges and (sometimes c is omitted and we default to ). Actually, drives the transition from an exponential-time algorithm (when approaches 1) to a pure polynomial-time algorithm (as tends to 0).
The first subexponential algorithms had complexity and applied only to prime fields. Soon was achieved for any finite field, with values for c ranging from for fields with high characteristic to for medium characteristic. When dealing with small characteristic fields, recent research brought down the complexity to [41] and even to quasi-polynomial time [42,43]. If the group size is , and we write , then the characteristic is considered “small”, “medium-sized” or “large” depending on whether , , or , respectively.
In any case, the previous results have been applied in practice and several cryptanalysis have been successfully carried out (see [44,45]), so it seems sensible to avoid using small characteristics and also extensions of moderate characteristic included in the range threatened by recent cryptanalytic techniques [42,43,46]. However, these algorithms are heuristic and are proved to work only for certain particular cases, not difficult to circumvent: for example, if one has , it suffices to choose both p and n to be prime in order to thwart both [42,43]. For a detailed account of history and current status, see [47] (in particular §4.2), and [48].
Our proposal is to use a group of prime order , over a ground field . Using formula (5), we can compute how many elements in provide a given security level. Since the number of elements is roughly the square of the value of q, it follows that q can be represented with only one half of the bits needed for n. This has a direct impact on the computation time of the ⊕ operation in , since it is performed in (see Equation (4) and cost analysis in Section 3.4).
3.2. System Setup and System Parameters for a Key Agreement Protocol
The group lends readily itself as a building block for standard cryptographic applications to be constructed upon it. One of such applications is a Diffie-Hellman-like key agreement protocol, which will be described in the following sections.
In the sequel, we provide the necessary steps to set up the system. Moreover, the users also need to fix some system parameters.
System Setup
To set up the system, the following steps are in order:
- Choose a ground field with characteristic different from 2 or 3, such that is prime.
- Select elements such that the polynomialis irreducible in .
- Consider . Select such that it is a generator of .
- Compute the coordinates of seen as a vector over , which will be denoted as .
- Consider a projection , such that , and .Observe that (see proof of Proposition 1). If we compute , where , we have that . Therefore, the projection consists simply in computing , for .Defining the projection in this way is convenient, since it automatically gives rise to a generator in with a unitary norm, which means that all the elements generated by it will enjoy also a unitary norm.Remark en passant that the previous device works only if 3 is invertible in . Fortunately, this is always the case since otherwise the following implications hold: and the latter equation would contradict the fact that we chose ℓ as a prime.
Remark 7.
In order to save space, we can always find an irreducible χ such that . Obviously, cannot be 0, but we may wonder whether we could in addition take . However, this is not possible according to [49] (Lemma 7). The latter reference studies the number of irreducible binomials , with , and concludes that the number of such irreducible binomials is
The largest square-free number that divides is denoted by and
For our case, , hence . However, then , since we chose to be a prime, thus implying .
Accordingly, we conclude that and cannot be simultaneously taken as 0.
System Parameters
The system parameters are defined by the set , following the notation and conditions explained above.
3.3. The Key Agreement Protocol
The key agreement follows the well-known Diffie-Hellman paradigm. Any two users , willing to agree on a common value, which remains secret, set up a system and agree on its parameters, as stated previously.
The protocol runs as follows:
- User A selects uniformly at random, with , computesand sends it to user B.
- User B selects uniformly at random, computesand sends it to user A.
- User A computes .
- User B computes .
According to the definitions, the following equalities clearly hold:
Hence, the properties of the operation ⊕ in ensure that actually , which is the common value expected as the output of the protocol.
3.4. Cost of the ⊕ Operation in
Let S and P be the number of field operations in order to perform an addition and a multiplication respectively in . From the formula (4), it follows that the total number of operations for computing is equal to , once the precomputations of , , and are assumed.
3.5. A Toy Example
We provide hereafter an example of computing a discrete logarithm by brute-force search. In general, this algorithm is, of course, infeasible, but we choose very small parameters in order to illustrate the operation of the group .
Let us take the prime field , with , for which is also a prime. Accordingly, the group is cyclic. We set the parameters , , , since the polynomial is irreducible in .
We select the element as a generator in . As explained above, it is convenient to project it onto a unitary norm point of . To achieve this goal, we perform the following steps:
Observe that indeed . We choose a target point and performing a similar computation we get . The problem is to find the discrete logarithm of Y to the base X, i.e., find the integer n such that . Iterating the operation, we carry out an exhaustive search:
Eventually, we come up with the target point. Since the operation has been iterated ten times, we conclude for this particular pair, so that . Remark that, to perform each step, it suffices to follow the formula (4).
3.6. Experimental Results
We have conducted several experiments in order to assess the computation time of the ⊕ operation in . The basic setup consists of selecting prime fields, , over which the ⊕ operation will be tested. Observe that, according to formula (4), performing the operation boils down to a number of additions and multiplications over the base field; hence, the expected computation time will depend on the size of its elements; informally, size (also known as bit length) means the number of bits in the binary representation of such elements. The selected prime fields, , will have increasing values for the size of p, i.e., increasing bit lengths in the representation of their elements.
Taking the previous considerations into account the experiment is conducted as follows: we take increasing values of p and, for each value, we perform all the required computations to add two random points in , following formula (4). We repeat the experiment a large number of times for distinct points and record the mean computation time for each value of p.
In order to compare computation times, we repeated the same experiment for the point addition in elliptic curves over , using the same range of bit lengths. As before, the idea is selecting random points and adding them using, in particular, projective coordinates according to the formulas given in [50] [§13.2.1.b]. Repeating the computation a large number of times, we record the mean computation time for each value of p. Choosing the point addition operation in elliptic curves as the term of comparison with the ⊕ operation seems sensible since both operations share a relatively large number of basic operations (namely, additions, multiplications, and inversions) in the ground field.
We implemented the experiments using Java SE Runtime Environment version 1.8.0_171-b11 and the execution was carried out on an Intel Core i7-4790 platform (Santa Clara, CA, USA) running at GHz. We performed the experiment in the range 32–512 bits in steps of 32 bits.
The experiments yielded the results shown in Table 1. In each line, the first column represents the number of bits of the binary representation of the elements in , the ground field. The second and third columns represent the mean computation time needed to perform the addition of two points in the group via the operation ⊕, and in an elliptic curve over , respectively. All the computation times are measured in microseconds.

Table 1.
Computation time for one single operation in each setting.
Having a visual idea of the results reported in Table 1 is best achieved by depicting them in a combined graph. To this end, we show in Figure 1 the graphical representation of the computation times for both operations, as reported in Table 1. Both graphs are conveniently labeled so that one of them depicts the computation time for the ⊕ operation in , and the other one depicts the computation time for the point addition in elliptic curves over . The x-axis represents the bit length of p common for both operations.
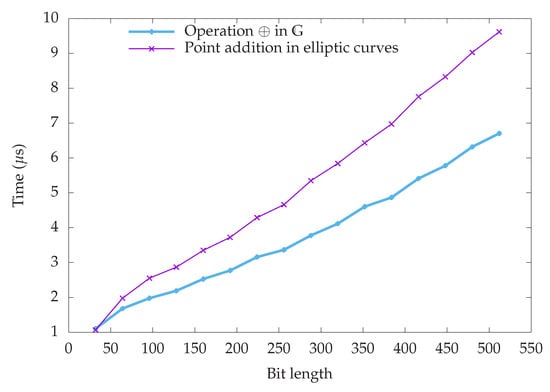
Figure 1.
Comparison of average computation times for both settings.
The graph pushes to the foreground some interesting remarks:
- The computation times shown in Figure 1 for both settings show a essentially linear growth, which is convenient in view of practical applications.
- Though the point addition in elliptic curves is slightly slower than the ⊕ operation in for the same bit length over the ground field, they keep a rather constant ratio between them, which is roughly equal to .
3.7. Real World Parameters
In order to assess the size for real world parameters, we resort to the recommendations issued by NIST [51]. These recommendations are based on the knowledge of the execution time of the best algorithms solving any particular problem. We will reproduce here an excerpt of Table 2 in that reference, which summarizes the bit sizes for the relevant parameters applicable to our proposal.

Table 2.
Comparable cryptographic strengths.
We explain hereafter the meaning of the columns. To begin with, Security strength represents the binary logarithm of the estimated time taken by the best known algorithm for solving the problem (which is proportional to the number of cryptographic operations), thus breaking the cryptosystem. The center column, labeled as Group order, is related to the group where the cryptosystem is defined; in our case, it is the projective space where is the base field. In particular, each line in this column represents the binary logarithm of the number of elements in the projective space needed to achieve the security strength indicated in the leftmost column.
Since we propose that the number of points in the projective space is , the base field size (namely, the binary logarithm of q) is half the size of n, as represented in the rightmost column. Remark that this is a nice feature, since the multiplication cost in the base field is intimately related to the size of the latter.
Finally, the public key consists of one projective point. Since we chose unitary norm for such point, it can be represented with just two elements of the base field. Therefore, public key size is twice as much as the base field size (it needs twice as many bits).
4. A More Robust System
The security of the cryptosystem proposed in the previous sections can be increased by extending the theory developed for a field to the case of a unitary commutative ring R.
Essentially, we will stick to the ring , where is an integer, the product of two primes of similar size, p and q. We will strain ourselves in order to apply all the concepts developed in the previous sections to this new setting in an attempt to improve the security and efficiency of the proposed scheme.
We will manage to obtain the definition of a group law acting over the direct product of two projective spaces, . In this new setting, the security is reinforced since an attacker is forced to sequentially solve an instance of the integer factorization problem and an instance (actually two instances, but they can be parallelized) of the discrete logarithm problem.
In fact, let M be a free R-module of finite rank and let be an R-linear map with characteristic polynomial , X being an indeterminate, I the identity matrix of order , and the matrix of A in an arbitrary basis for M. According to [52] [III, §8, 11.Proposition 20], the Cayley-Hamilton Theorem holds in this setting, namely .
Hence, if and , , then .
As above, we can define a degree-3 homogeneous polynomial in by setting . As a computation shows, we have
thus proving that Lemma 1 still holds in this case; i.e., Q depends on only, but not on the matrix .
The projective plane over R is then defined as follows: , where denotes the multiplicative group of invertible elements in R and acts on by
Proceeding as in the previous sections, a composition law , , , , , can be defined by the formula
and similarly we deduce
The determinant of the matrix of (6) is equal to . Hence, ⊕ induces a composition law . If C denotes the set of classes modulo of points such that , then ⊕ also induces a composition law , where , as if is invertible and , then is also invertible.
The same proof given in the case of a field shows that the composition law ⊕ is associative, commutative, and admits an identity element, which is the vector .
If with prime integers, then from Chinese Remainder Theorem there is a ring isomorphism between and the product ring . Hence, each vector can be assigned a pair in and the group acts on in the same way as acts on and does on .
Consequently, if and only if at least one of its two components is distinct from , so that
Therefore, .
Moreover, letting , as a computation shows, one obtains and , and is invertible if and only if and both are invertible in and , respectively. If corresponds to in , then , where , , and , . Hence,
We set
If both and are irreducible polynomials in and , respectively, then, according to Proposition 1, the points of the associated curves and reduce to the origin; i.e., , , where and denote the origin in and , respectively.
From (7), taking (8) into account, it follows: . Consequently, we conclude that , where and are the subgroups given by
and, from Theorem 2, we thus obtain
Proposition 3.
If the polynomials and are irreducible in and , respectively, then the group is isomorphic to the direct product of the cyclic groups and . Hence, is cyclic if and only if and are coprimes; i.e., .
Remark 8.
If , then , , with . The cyclic subgroup S in spanned by is of order . As and , , it follows: , which indicates that in general the group S is large enough, even if a and b are not coprimes.
Remark 9.
It is clear that the group is also amenable as a building block for a key-agreement protocol by choosing , with m composite. Observe that its security is enhanced with respect to its counterpart , q a prime power, since the algorithms known to be efficient to compute discrete logarithms only work in the multiplicative group of a field. This means that one is forced to factorize m in order to apply such algorithms to the present case, thus increasing the time complexity and the security of the system, though at the price of doubling the key length.
5. Conclusions
In this work, we have defined a group law, ⊕, over the set , and considered the discrete logarithm problem associated with them. We have analyzed their properties and stated the security of the problem considered. Moreover, based on it, we have defined a cryptographic key agreement protocol as one possible application of this problem to public key cryptography. Finally, we shift the system to the group over the ring , which turns out to be completely analogous to the previous one and offers an enhanced security, though at the cost of some extra key length.
As future work, we think that it is possible to extend this discrete logarithm problem in order to define new cryptographic protocols for encryption/decryption and digital signatures, among others, in a similar way as ElGamal or elliptic curve cryptosystems were defined from the Diffie-Hellman key agreement protocol.
Author Contributions
Conceptualization, R.D.D., L.H.E. and J.M.M.; Funding acquisition, L.H.E.; Investigation, R.D.D., L.H.E. and J.M.M.; Methodology, R.D.D., L.H.E. and J.M.M.; Writing—original draft, R.D.D., L.H.E. and J.M.M.; Writing—review & editing, R.D.D., L.H.E. and J.M.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research has been partially supported by Ministerio de Economía, Industria y Competitividad (MINECO), Agencia Estatal de Investigación (AEI), and European Regional Development Fund (ERDF, EU), through project COPCIS, Grant No. TIN2017-84844-C2-1-R, and by Comunidad de Madrid (Spain) through project CYNAMON, Grant No. P2018/TCS-4566-CM, co-funded along with ERDF.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| DLP | Discrete Logarithm Problem |
| PKC | Public Key Cryptography |
References
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Miller, V.S. Use of elliptic curves in cryptography. Lect. Notes Comput. Sci. 1986, 218, 417–426. [Google Scholar] [CrossRef]
- Diffie, W.; Hellman, M.E. New directions in cryptography. IEEE Trans. Inform. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Rivest, R.; Shamir, A.; Adleman, L.M. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- ElGamal, T. A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inform. Theory 1985, 31, 469–472. [Google Scholar] [CrossRef]
- Menezes, A.J.; Qu, M.; Vanstone, S.A. Some new key agreement protocols providing implicit authentication. In Proceedings of the 2nd Workshop on Selected Areas in Cryptography (SAC ’95), Carleton University, Ottawa, ON, Canada, 18–19 May 1995; pp. 22–32. [Google Scholar]
- Massey, J.L.; Omura, J.K. Method and Apparatus for Maintaining the Privacy of Digital Messages Conveyed by Public Transmission. 1986. Available online: www.google.com/patents/US4567600 (accessed on 1 March 2020).
- Menezes, A.; Vanstone, S. Elliptic curve cryptosystems and their implementation. J. Cryptol. 1993, 6, 209–224. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P. Minimizing the use of random oracles in authenticated encryption schemes. Lect. Notes Comput. Sci. 1997, 1334, 1–16. [Google Scholar] [CrossRef]
- Abdalla, M.; Bellare, M.; Rogaway, P. DHAES: An Encryption Scheme Based on the Diffie-Hellman Problem. Available online: http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.28.2910 (accessed on 1 March 2020).
- Abdalla, M.; Bellare, M.; Rogaway, P. DHIES: An Encryption Scheme Based on the Diffie-Hellman Problem. 2001. Available online: http://web.cs.ucdavis.edu/~rogaway/papers/dhies.pdf (accessed on 1 March 2020).
- Abdalla, M.; Bellare, M.; Rogaway, P. The oracle Diffie-Hellman assumptions and an analysis of DHIES. Lect. Notes Comput. Sci. 2001, 2020, 143–158. [Google Scholar] [CrossRef]
- ANSI. Public Key Cryptography for the Financial Services Industry: Key Agreement and key Transport Using Elliptic Curve Cryptography; American National Standards Institute: New York, NY, USA, 2001. [Google Scholar]
- IEEE. Standard Specifications for Public Key Cryptography-Amendment 1: Additional Techniques; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2004. [Google Scholar]
- ISO/IEC. Information Technology-Security Techniques-Encryption Algorithms-Part 2: Asymmetric Ciphers; International Organization for Standardization/International Electrotechnical Commission: Geneva, Switzerland, 2006. [Google Scholar]
- Gayoso Martínez, V.; Hernández Álvarez, F.; Hernández Encinas, L.; Sánchez Ávila, C. Analysis of ECIES and other cryptosystems based on elliptic curves. J. Inf. Assur. Secur. 2011, 6, 285–293. [Google Scholar]
- NIST. Digital Signature Standard (DSS); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2000.
- ANSI. Public Key Cryptography for the Financial Services Industry: The Elliptic Curve Digital Signature Algorithm (ECDSA); American National Standards Institute: New York, NY, USA, 2005. [Google Scholar]
- IEEE. Standard Specifications for Public Key Cryptography; Institute of Electrical and Electronics Engineers: Piscataway, NJ, USA, 2000. [Google Scholar]
- National Institute of Standard and Technology. Digital Signature Standard (DSS); NIST FIPS 186-4; National Institute of Standard and Technology: Gaithersburg, MD, USA, 2009.
- Lochter, M.; Merkle, J. Elliptic Curve Cryptography (ECC) Brainpool Standard Curves and Curve Generation. Request for comments (RFC 5639), Internet Engineering Task Force. 2010. Available online: https://datatracker.ietf.org/doc/rfc5639/ (accessed on 1 March 2020).
- Bernstein, D.J.; Lange, T. SafeCurves, 2014. Available online: http://safecurves.cr.yp.to/ (accessed on 1 March 2020).
- Edwards, H. A normal form for elliptic curves. Bull. Am. Math. Soc. 2007, 44, 393–422. [Google Scholar] [CrossRef]
- Baignères, T.; Delerablée, C.; Finiasz, M.; Goubin, L.; Lepoint, T.; Rivain, M. Trap Me If You Can. Million Dollar Curve. Cryptology ePrint Archive: Report 2015/1249. 2016. Available online: https://eprint.iacr.org/2015/1249 (accessed on 1 March 2020).
- Gayoso Martínez, V.; Hernández Encinas, L.; Martín Muñoz, A.; Durán Díaz, R. Secure elliptic curves and their performance. Log. J. IGPL 2019, 27, 277. [Google Scholar] [CrossRef]
- Koyama, K.; Maurer, U.M.; Okamoto, T.; Vanstone, S.A. New Public-Key Schemes Based on Elliptic Curves over the Ring . Lect. Notes Comput. Sci. 1992, 576, 252–266. [Google Scholar] [CrossRef]
- Meyer, B.; Müller, V. A Public Key Cryptosystem Based on Elliptic Curves over Equivalent to Factoring. Lect. Notes Comput. Sci. 1996, 1070, 49–59. [Google Scholar] [CrossRef]
- Papachristodoulou, L.; Batina, L.; Mentens, N. Recent Developments in Side-Channel Analysis on Elliptic Curve Cryptography Implementations. In Hardware Security and Trust: Design and Deployment of Integrated Circuits in a Threatened Environment; Sklavos, N., Chaves, R., Di Natale, G., Regazzoni, F., Eds.; Springer International Publishing: Berlin, Germany, 2017; pp. 49–76. [Google Scholar] [CrossRef]
- Gayoso Martínez, V.; Hernández Encinas, L.; Martín Muñoz, A. Implementation of Cryptographic Algorithms for Elliptic Curves. In Geometry, Algebra and Applications: From Mechanics to Cryptography; Springer: Cham, Switzerland, 2016; Chapter 11; pp. 121–133. [Google Scholar] [CrossRef]
- Shor, P. Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer. SIAM J. Comput. 1997, 26, 1484–1509. [Google Scholar] [CrossRef]
- Gidney, C.; Ekeå, M. How to Factor 2048 bit RSA Integers in 8 Hours Using 20 Million Noisy Qubits. arXiv 2009, arXiv:1905.09749. [Google Scholar]
- NIST. Post-Quantum Cryptography. On-Line Publication, 2017. Available online: https://csrc.nist.gov/Projects/Post-Quantum-Cryptography (accessed on 1 March 2020).
- NIST. Post-Quantum Cryptography, 2nd round. On-line publication: 2019. Available online: https://csrc.nist.gov/projects/post-quantum-cryptography/round-2-submissions (accessed on 1 March 2020).
- Menezes, A.J. Elliptic Curve Public Key Cryptosystems; The Kluwer International Series in Engineering and Computer Science. Communications and Information Theory; Kluwer Academic Publishers: Boston, MA, USA, 1993; Volume 234. [Google Scholar] [CrossRef]
- Singer, J. A theorem in finite projective geometry and some applications to number theory. Trans. Am. Math. Soc. 1938, 43, 377–385. [Google Scholar] [CrossRef]
- Ghorpade, S.R.; Hasan, S.U.; Kumari, M. Primitive polynomials, Singer cycles and word-oriented linear feedback shift registers. Des. Codes Cryptogr. 2011, 58, 123–134. [Google Scholar] [CrossRef]
- Silverman, J.H.; Tate, J.T. Rational Points on Elliptic Curves; Undergraduate Texts in Mathematics, Springer International Publishing: Cham, Switzerland, 2015. [Google Scholar] [CrossRef]
- Koblitz, N.; Menezes, A.J. Another look at “Provable Security”. J. Cryptol. 2007, 20, 3–37. [Google Scholar] [CrossRef]
- Papadimitriou, C.H. Computational Complexity; Addison-Wesley Publishing Company: Reading, MA, USA, 1994. [Google Scholar] [CrossRef]
- Odlyzko, A.M. Handbook of Finite Fields; CRC Press: Boca Raton, FL, USA, 2013; pp. 393–401. [Google Scholar]
- Joux, A. A New Index Calculus Algorithm with Complexity L(1/4 + o(1)) in Small Characteristic. In International Conference on Selected Areas in Cryptography; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8282, pp. 355–379. [Google Scholar] [CrossRef]
- Barbulescu, R.; Gaudry, P.; Joux, A.; Thomé, E. A heuristic quasi-polynomial algorithm for discrete logarithm in finite fields of small characteristic. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2014. [Google Scholar] [CrossRef]
- Granger, R.; Kleinjung, T.; Zumbrägel, J. On the discrete logarithm problem in finite fields of fixed characteristic. Trans. Am. Math. Soc. 2018, 370, 3129–3145. [Google Scholar] [CrossRef]
- Adj, G.; Menezes, A.; Oliveira, T.; Rodríguez-Henríquez, F. Computing discrete logarithms using Joux’s algorithm. ACM Comm. Computer Algebra 2015, 49, 60.v. [Google Scholar] [CrossRef]
- Kleinjung, T.; Diem, C.; Lenstra, A.K.; Priplata, C.; Stahlke, C. Computation of a 768-Bit Prime Field Discrete Logarithm. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Cham, Switzerland, 2017; Volume 10210, pp. 185–201. [Google Scholar] [CrossRef]
- Hayasaka, K.; Aoki, K.; Kobayashi, T.; Takagi, T. A construction of three-dimensional lattice sieve for number field sieve over GF(pn). Cryptology ePrint Archive, 2015/1179, 2015. Available online: https://eprint.iacr.org/2015/1179.pdf (accessed on 1 March 2020).
- Joux, A.; Odlyzko, A.; Pierrot, C. Open problems in Mathematics and Computational Science; Springer International Publishing: Cham, Switzerland, 2014; pp. 5–36. [Google Scholar] [CrossRef]
- Granger, R.; Kleinjung, T.; Zumbrägel, J. Indiscreet logarithms in finite fields of small characteristic. Adv. Math. Commun. 2018, 12, 263–286. [Google Scholar] [CrossRef]
- Heyman, R.; Shparlinski, I.E. Counting irreducible binomials over finite fields. Finite Fields Their Appl. 2016, 38, 1–12. [Google Scholar] [CrossRef]
- Cohen, H.; Frey, G.; Avanzi, R.; Doche, C.; Lange, T.; Nguyen, K.; Vercauteren, F. Handbook of Elliptic and Hyperelliptic Curve Cryptography; Chapman and Hall/CRC, Taylor & Francis Group: New York, NY, USA, 2005. [Google Scholar] [CrossRef]
- Barker, E. Recommendation for Key Management, Part 1: General; NIST: Gaithersburg, MD, USA, 2016. Available online: https://csrc.nist.gov/publications/detail/sp/800-57-part-1/rev-4/final (accessed on 1 March 2020).
- Bourbaki, N. Éléments de Mathématique. Algèbre. Chapitres 1 à 3; Herman: Paris, France, 1970. [Google Scholar] [CrossRef]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).