Mobile User Location Inference Attacks Fusing with Multiple Background Knowledge in Location-Based Social Networks
Abstract
1. Introduction
- (1)
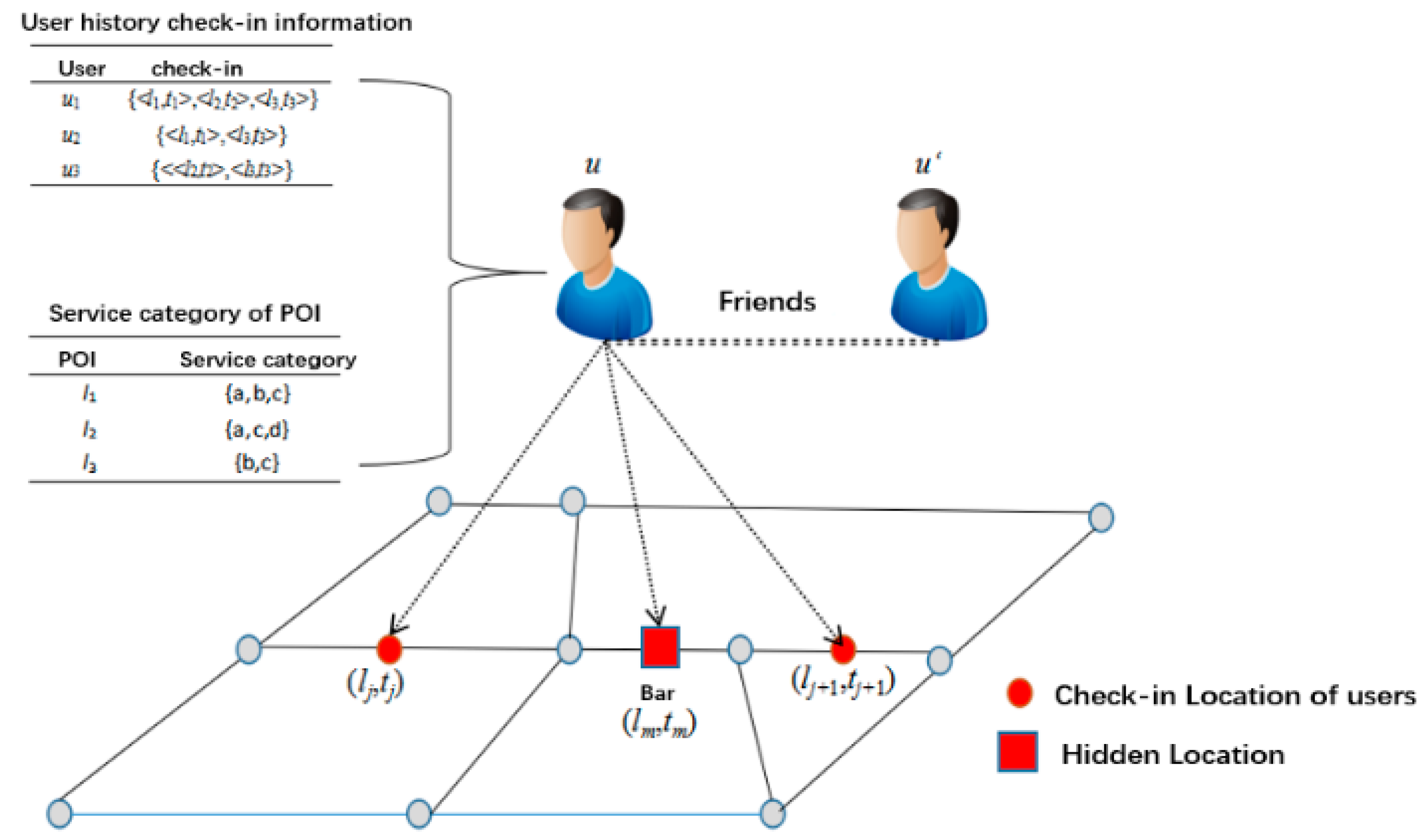
- The historical check-in sequence. The check-in sequence is constituted by the user’s check-in locations sorted by the timestamps. Obviously, the check-in sequences reflect the user’s behavior. For example, from the historical check-in records, the number of check-in sequences including the positions lj and lj+1 both is 10. Then, we find that the user checks-in at lm 3 times between lj and lj+1. Thus, we guess that the user will check-in to the position lm from the location lj to the location lj+1 with the probability 0.3(=3/10) in the future.
- (2)
- Personalized POIs preferences. In LBSN, each POI is labeled with several service categories. Generally, users’ preferences for the service categories are different. For example, nightclub enthusiasts prefer to visit different bars, while travel enthusiasts like to visit different tourist attractions. Therefore, the personalized preference of the service category can also be used to infer the probability of the user visiting the hidden location lm.
- (3)
- Social networks. Generally, the behaviors of friends are similar. Specifically, users often wander around various streets with their friends and go to a good restaurant or a shopping mall, etc. A user is more likely go to a place recommended by his/her friends. Suppose that a user u’s friend u* always checks-in to the lm. Then, although u does not check-in at lm during the movement from lj to lj+1, the attackers can also infer the likelihood that u visited lm based on the user similarities between u and u*.
- (4)
- Geographical location. In general, the geographical proximity of POIs has a significant impact on the user’s check-in behavior. The probability of accessing li+1 after checking-in at li depends on the distance between the two POIs. For example, users usually go to a mall or a movie theater nearby for convenience. On the other hand, the reachability of a position can be used to prune a sensitive hidden location. Specifically, if a user takes a short traveling time that is less than the minimum time required between the two locations li and lj+1, then the user u certainly cannot visit lm. That is, the location lm is not reachable.
- (5)
- POIs Popularity. If a POI is prevalent, then the POI is more attractive to a user. That means, the visiting probability of the users to this POI will be high. Therefore, we can use the popularity of POIs to infer the accessing probability as well.
2. Literature Review
3. Background
4. Hidden Location Inference Attack Models and Algorithm
4.1. WBI: Weighted Bayesian Hidden Location Inference Model
4.2. Hlpi: Hidden Location Inference Model Based on Multi-Factor Fusion
4.3. Hidden Location Inference Attack Algoriyhm
- (1)
- The sensitive category set SSu which the user u regards to be sensitive is saved in the authorization server. The authorization server is trusted. When the user u wants to use the check-in services, u can send the check-in request with pre-check-in location lj+1 at time tj+1 to the authorization server.
- (2)
- When the authorization server receives users’ check-in requests, Algorithm 1 is utilized. The hidden locations between the user’s previous check-in location lj and pre-check-in location lj+1 are computed. The inferred hidden POIs are sorted by the computed visiting probabilities. The authorization server will send a privacy warning message to u when the categories of the hidden POIs fall into the sensitive category set SSu. The most probable POIs whose category is sensitive are pushed to u in the warning message. The warning message will ask whether the use still wants to check-in at POI lj+1 at time tj+1.
- (3)
- The users can make a choice by themselves. If the user still wants to check-in at location lj, the authorization server will forward the check-in request to the LBS server. Otherwise, the authorization server will drop this check-in request, meaning the check-in service is sacrificed while the user’s privacy is protected.
| Algorithm 1. Hidden Location Inference Algorithm. |
| Input: lj, lj+1, W, S, C, P, G=<V, E> Output: Pair set of hidden location and the probability <Lm, Pm>
|
5. Results
5.1. Setting
5.2. Results and Analysis
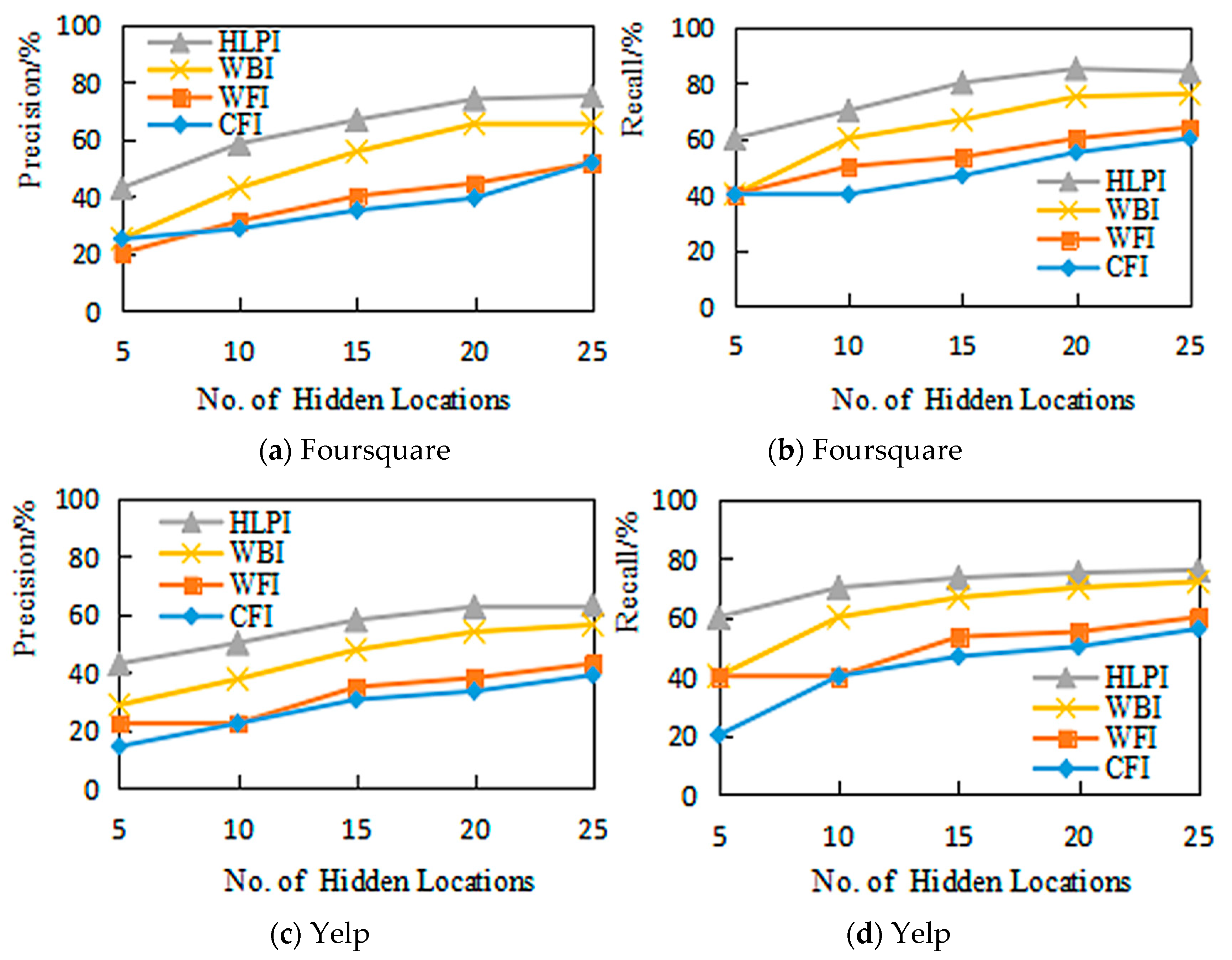
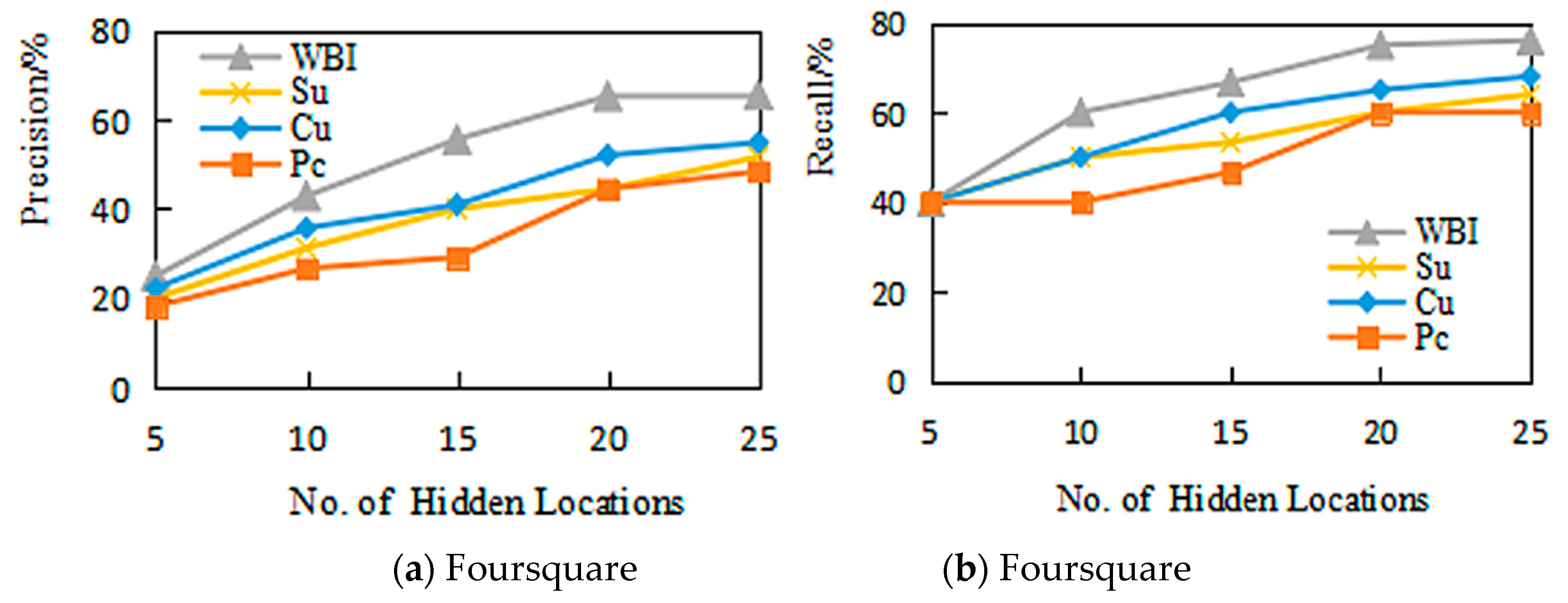
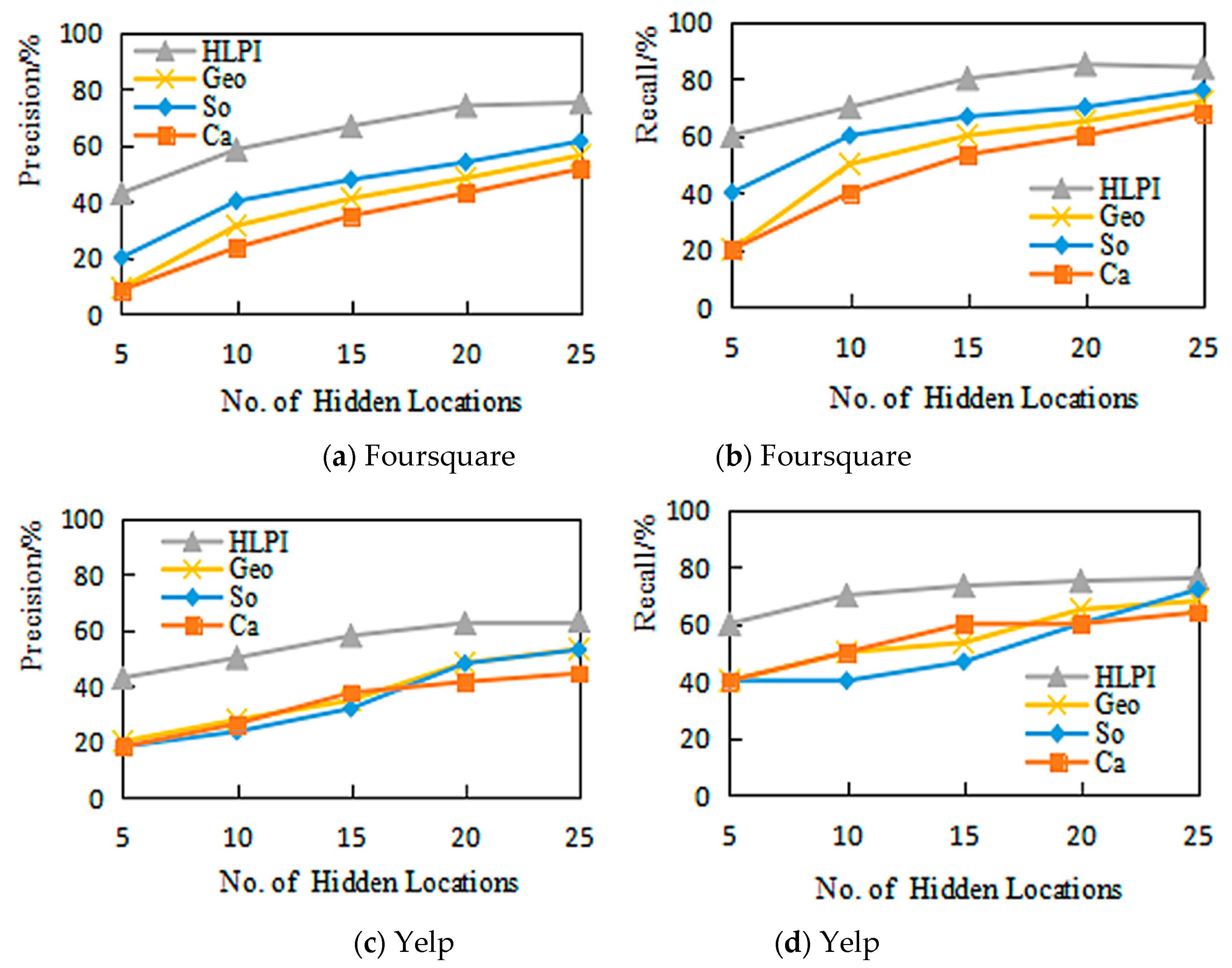
5.2.1. Accuracy
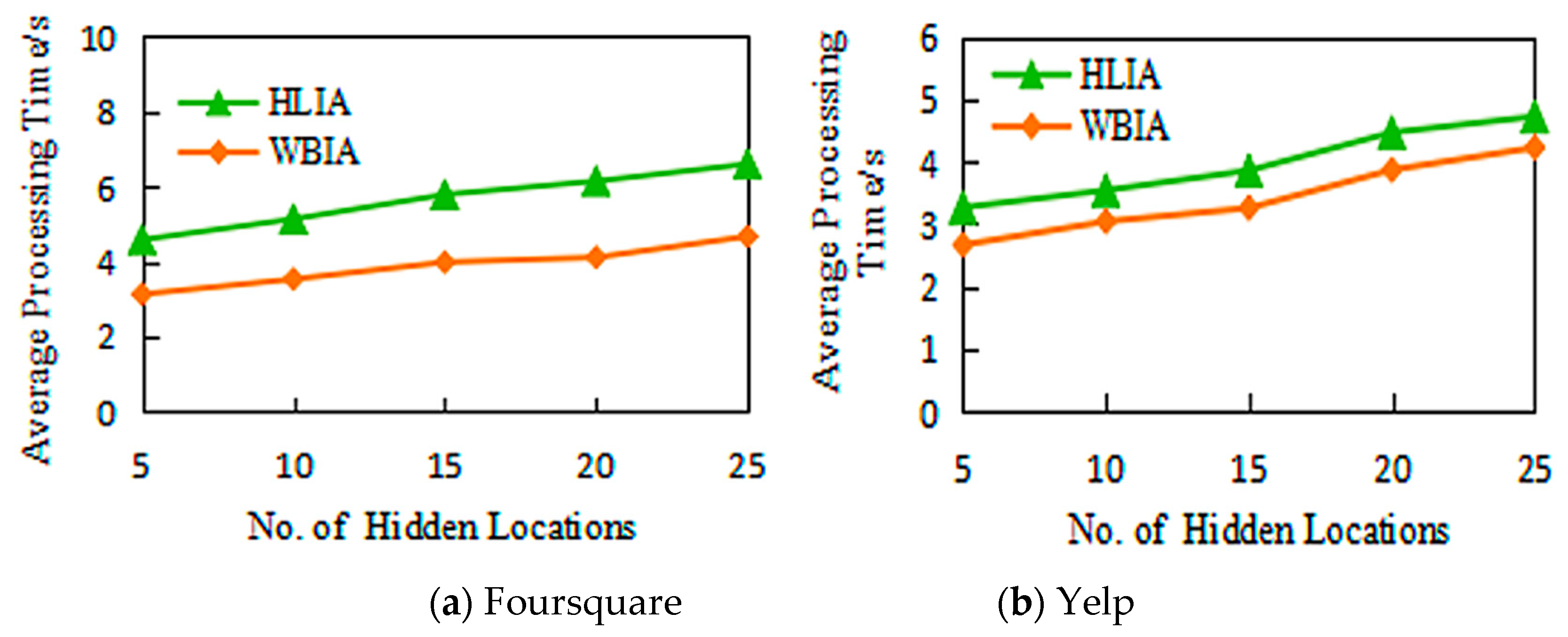
5.2.2. Effectiveness
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Vicente, C.R.; Freni, D.; Bettini, C.; Jensen, C.S. Location-Related Privacy in Geo-Social Networks. IEEE Internet Comput. 2011, 15, 20–27. [Google Scholar] [CrossRef]
- Gao, H.; Liu, H. Data analysis on location-based social networks. In Mobile Social Networking; Springer: New York, NY, USA, 2013; pp. 165–194. [Google Scholar]
- Cao, Y.; Xiao, Y.; Xiong, L.; Bai, L.; Yoshikawa, M. Protecting Spatiotemporal Event Privacy in Continuous Location-Based Services. IEEE Trans. Knowl. Data Eng. 2019. [Google Scholar] [CrossRef]
- Cao, Y.; Xiao, Y.; Xiong, L.; Bai, L. PriSTE: From Location Privacy to Spatiotemporal Event Privacy (short paper). In Proceedings of the 35th IEEE International Conference on Data Engineering (ICDE), Macao, China, 8–11 April 2019. [Google Scholar]
- Shao, Y.; Liu, J.; Shi, S.; Zhang, Y.; Cui, B. Fast De-anonymization of Social Networks with Structural Information. J. Data Sci. Eng. 2019, 4, 76–92. [Google Scholar] [CrossRef]
- Singh, N.; Singh, A.K. Data Privacy Protection Mechanisms in Cloud. J. Data Sci. Eng. 2017, 1, 1–16. [Google Scholar] [CrossRef]
- Huo, Z.; Meng, X.; Zhang, R. Feel Free to Check-in: Privacy Alert against Hidden Location Inference Attacks in GeoSNs; Springer: Berlin, Germany, 2013; pp. 377–391. [Google Scholar]
- Gruteser, M.; Grunwald, D. Anonymous usage of location-based services through spatial and temporal cloaking. In Proceedings of the International Conference on Mobile Systems, Applications, and Services, San Francisco, CA, USA, 5–8 May 2003; pp. 31–42. [Google Scholar]
- Andrés, M.E.; Bordenabe, N.E.; Chatzikokolakis, K.; Palamidessi, C. Geo-Indistinguishability: Differential privacy for location-based systems. In Proceedings of the ACM Conference on Computer and Communications Security, Berlin, Germany, 4–8 November 2013; pp. 901–914. [Google Scholar]
- Mouratidis, K.; Yiu, M.L. Shortest path computation with no information leakage. arXiv 2012, arXiv:1204.6076. [Google Scholar] [CrossRef]
- Palanisamy, B.; Liu, L. Attack-resilient mix-zones over road networks: Architecture and algorithms. Trans. Mob. Comput 2015, 14, 495–508. [Google Scholar] [CrossRef]
- Yao, L.; Wang, X.; Wang, X.; Hu, H.; Wu, G. Publishing Sensitive Trajectory Data Under Enhanced l-Diversity Model. In Proceedings of the 20th IEEE International Conference on Mobile Data Management, Hong Kong, China, 10–13 June 2019; pp. 160–169. [Google Scholar]
- Ye, Q.; Hu, H.; Meng, X.; Zheng, H. PrivKV: Key-value data collection with local differential privacy. In Proceedings of the IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 19–23 May 2019; pp. 317–331. [Google Scholar]
- Pan, X.; Zhang, J.; Wang, F.; Philip, S.Y. DistSD: Distance-based social discovery with personalized posterior screening. In Proceedings of the IEEE International Conference on Big Data, Washington, DC, USA, 5–8 December 2016; pp. 1110–1119. [Google Scholar]
- Toch, E.; Cranshaw, J.; Hankes-Drielsma, P.; Springfield, J.; Kelley, P.G.; Cranor, L.; Sadeh, N. Locaccino: A privacy-centric location sharing application. In Proceedings of the 12th ACM International Conference Adjunct Papers on Ubiquitous Computing, Copenhagen, Denmark, 26–29 September 2010; pp. 381–382. [Google Scholar]
- Sadeh, N.; Hong, J.; Cranor, L.; Fette, I.; Kelley, P.; Prabaker, M.; Rao, J. Understanding and capturing people’s privacy policies in a mobile social networking application. Pers. Ubiquitous Comput. 2009, 13, 401–412. [Google Scholar] [CrossRef]
- Kelley, P.G.; Hankes Drielsma, P.; Sadeh, N.; Cranor, L.F. Cranor User-controllable learning of security and privacy policies. In Proceedings of the 1st ACM workshop on Workshop on AISec, Melbourne, Australia, 19–20 August 2008; pp. 11–18. [Google Scholar]
- Freni, D.; Ruiz Vicente, C.; Mascetti, S.; Bettini, C.; Jensen, C.S. Preserving location and absence privacy in geo-social networks. In Proceedings of the ACM International Conference on Information and Knowledge Management, Toronto, ON, Canada, 26–30 October 2010; pp. 309–318. [Google Scholar]
- Riboni, D.; Pareschi, L. Bettini Integrating Identity, Location, and Absence Privacy in Context-Aware Retrieval of Points of Interest. In Proceedings of the IEEE International Conference on Mobile Data Management, Lulea, Sweden, 6–9 June 2011; pp. 135–140. [Google Scholar]
- Mascetti, S.; Freni, D.; Bettini, C.; Wang, X.S.; Jajodia, S. Privacy in geo-social networks: Proximity notification with untrusted service providers and curious buddies. VLDB J. 2011, 20, 541–566. [Google Scholar] [CrossRef]
- Sadilek, A.; Kautz, H.; Bigham, J.P. Finding your friends and following them to where you are. In Proceedings of the ACM International Conference on Web Search and Data Mining, Seattle, WA, USA, 8–12 February 2012; pp. 723–732. [Google Scholar]
- Yang, D.; Zhang, D.; Qu, B.; Cudré-Mauroux, P. PrivCheck: Privacy-Preserving Check-in Data Publishing for Personalized Location Based Services. In Proceedings of the Ubicomp, Heidelberg, Germany, 12–16 September 2016; pp. 545–556. [Google Scholar]
- Xue, D.; Wu, L.F.; Li, H.B.; Hong, Z.; Zhou, Z.J. A novel destination prediction attack and corresponding location privacy protection method in geo-social networks. Int. J. Distrib. Sens. Netw. 2017, 13, 1550147716685421. [Google Scholar] [CrossRef]
- Ye, M.; Yin, P.; Lee, W.C.; Lee, D.L. Exploiting geographical influence for collaborative point-of-interest recommendation. In Proceedings of the ACM SIGIR Conference on Research and Development in Information Retrieval, Beijing, China, 25–29 July 2011; pp. 325–334. [Google Scholar]
- Zhang, J.D.; Chow, C.Y. GeoSoCa: Exploiting Geographical, Social and Categorical Correlations for Point-of-Interest Recommendations. In Proceedings of the ACM SIGIR Conference on Research and Development in Information Retrieval, Santiago, Chile, 9–13 August 2015; pp. 443–452. [Google Scholar]
- Zhang, J.D.; Chow, C.Y. CoRe: Exploiting the personalized influence of two-dimensional geographic coordinates for location recommendations. Inf. Sci. 2015, 293, 163–181. [Google Scholar] [CrossRef]
- Bao, J.; Zheng, Y.; Mokbel, M.F. Location-based and preference-aware recommendation using sparse geo-social networking data. In Proceedings of the SIGSPATIAL 2012 International Conference on Advances in Geographic Information Systems, Redondo Beach, CA, USA, 6–9 November 2012; pp. 199–208. [Google Scholar]
- Hu, L.; Sun, A.; Liu, Y. Your neighbors affect your ratings: On geographical neighborhood influence to rating prediction. In Proceedings of the ACM SIGIR Conference on Research and Development in Information Retrieval, Melbourne, Australia, 6–11 July 2014; pp. 345–354. [Google Scholar]
- Yin, H.; Cui, B.; Sun, Y.; Hu, Z.; Chen, L. LCARS: A spatial item recommender system. ACM Trans. Inf. Syst. 2014, 32, 1–37. [Google Scholar] [CrossRef]
- Yin, H.; Sun, Y.; Cui, B.; Hu, Z.; Chen, L. LCARS: A location-content-aware recommender system. In Proceedings of the ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Chicago, IL, USA, 11–14 August 2013; pp. 221–229. [Google Scholar]
- Ying, J.J.C.; Kuo, W.N.; Tseng, V.S.; Lu, E.H.C. Mining User Check-In Behavior with a Random Walk for Urban Point-of-Interest Recommendations. ACM Trans Intell. Syst. Technol. 2014, 5, 1–26. [Google Scholar] [CrossRef]
- Kosmides, P.; Demestichas, K.; Adamopoulou, E.; Remoundou, C.; Loumiotis, I.; Theologou, M.; Anagnostou, M. Providing recommendations on location-based social networks. J. Ambient Intell. Humaniz. Comput. 2016, 7, 567–578. [Google Scholar] [CrossRef]

| Dataset | Foursquare | Yelp |
|---|---|---|
| Number of users | 717,382 | 70,817 |
| Number of point of interests (POIs) | 49,027 | 15,579 |
| Number of POI Category | 602 | 591 |
| Number of check-in | 206,416 | 335,022 |
| Number of friend pairs | 2,767,235 | 303,032 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pan, X.; Chen, W.; Wu, L. Mobile User Location Inference Attacks Fusing with Multiple Background Knowledge in Location-Based Social Networks. Mathematics 2020, 8, 262. https://doi.org/10.3390/math8020262
Pan X, Chen W, Wu L. Mobile User Location Inference Attacks Fusing with Multiple Background Knowledge in Location-Based Social Networks. Mathematics. 2020; 8(2):262. https://doi.org/10.3390/math8020262
Chicago/Turabian StylePan, Xiao, Weizhang Chen, and Lei Wu. 2020. "Mobile User Location Inference Attacks Fusing with Multiple Background Knowledge in Location-Based Social Networks" Mathematics 8, no. 2: 262. https://doi.org/10.3390/math8020262
APA StylePan, X., Chen, W., & Wu, L. (2020). Mobile User Location Inference Attacks Fusing with Multiple Background Knowledge in Location-Based Social Networks. Mathematics, 8(2), 262. https://doi.org/10.3390/math8020262





