Abstract
Rivest, Shamir, & Adleman (RSA), bilinear pairing, and elliptic curve are well-known techniques/algorithms for security protocols. These techniques suffer from higher computation and communication costs due to increased sizes of parameters, public keys, and certificates. Hyper-elliptic curve has lower parameter size, public key size, and certificate size. The aim of the proposed work is to reduce the computational cost and communication cost. Furthermore, we validate the security properties of our proposed scheme by using the well-known simulation tool called automated validation of Internet security protocols and applications. Our approach ensures security properties such as resistance against replay attack, confidentiality, authenticity, unforgeability, integrity, non-repudiation, public verifiability, and forward secrecy.
1. Introduction
In the early decades of the Internet, people used particular techniques for secure communication. With its rapid development, security has gradually become more important. Security may be considered in terms of confidentiality, unforgeability, public verifiability, non-repudiation, integrity, authentication, and forward secrecy [1]. Even in the presence of research efforts in the literature, privacy and security measures are still an open challenge [2]. Two elementary cryptographic performances to address the problem of privacy and authenticity in applications were formalized: sign-then-encrypt, encrypt-then-sign, and sign-and-encrypt [3]. Unfortunately, the suggested elementary cryptographic performances require more computational effort. In 1997, Zheng addressed the limitations in elementary performance by introducing a novel technique which he called “signcryption” [3]. Signcryption requires less computational complexity, communication cost, and implementation effort. Moving ahead, Deng and Boa [4] suggested a scheme to reduce computational cost by up to 16% and communication cost by up to 85% when compared to the signature-then-encryption technique. Incongruously, their proposed scheme has more computation and communication costs compared to Zheng’s scheme [3]. Gamage et al. [5] improved the approach mentioned in [4] by using firewalls to secure the message without any close-fitting of message confidentiality and deliver clarifications for authentication. This scheme reduces the computation cost to 40% when compared to the customary approach, and its communication cost is similar to Zheng [3]. Despite this, they are incapable of providing forward secrecy. To improve signcryption, several signcryption schemes have been proposed based on the RSA problem [6,7]. Baeket et al. [8] and then Sharma et al. [9] projected an identity-based signcryption scheme with an extra security service of public verifiability. Furthermore, the new projected scheme in [10] was based on an insubstantial ECC to determine verification and forward secrecy. The scheme needs a limited environment to decrease significant computation and communication costs. Toorani et al. [11] contributed the elliptic curve-based signcryption scheme. They claimed that the proposed signcryption scheme meets a forward secrecy security requirement. Nizamuddin et al. [12] targeted direct public verifiability, while Nizamuddin et al. [13] used one more forward secrecy and public verifiability scheme; however, it essentially needs more assistance with the zero-knowledge protocol. There is work available on the identity-based signcryption schemes in the literature [14,15,16,17,18,19,20,21,22,23], but these approaches suffer from the limitations of the key escrow problem. Furthermore, cryptography schemes called certificate-less signcryption have also been contributed [24,25,26,27,28,29,30,31,32,33]. However, these schemes need a secure channel for the distribution of partial secret keys, which is still a challenge. Most recently, Elkamchouchi et al. [34] proposed a new signcryption based on elliptic curve cryptography. They claimed to provide all security services in their work. However, unfortunately, their scheme suffers from replay attack, computational cost, and communication cost. Moreover, they did not use any simulation tools for validation purposes. In this paper, we propose a provable secured signcryption scheme based on a hyper-elliptic curve which will provide all security features along with low computational and communication cost. In contrast to the standard cryptosystems such as RSA and bilinear pairing, which use 1024 bits, and elliptic curve, which consumes 160 bits, our scheme uses 80 bits for the parameter size while providing the same level of security along with low computational and communication cost. Furthermore, we validate our scheme by using a well-known simulation tool called automated validation of internet security protocols and applications (AVISPA) in Appendix A [35]. Thus, our approach is appropriate to be used in resource-constrained devices such as sensors, pagers, and smart phones.
1.1. Preliminaries
Assume that is the genus of the hyper-elliptic curve over a finite field , where the order of this field is 𝓺. Furthermore, if = 1, then the group order of is . . While if = 2, then the curve will require a field with || , which means that it needs an 80 bit key and parameter size. Suppose is the algebraic closer of a field 𝒻, where 𝒻 is a finite field of the hyper-elliptic curve. Therefore, the hyper-elliptic curve of > 1 over 𝒻 representing the solution set (𝛼,𝛽) ∈𝒻∗𝒻 is shown in the following Equation (1):
where
- 𝗁(α) ∈ [α] is a polynomial and the degree is 𝗁(α) ⩽ g
- 𝘧(α) ∈ 𝒻[α] is the monic polynomial, and the degree is 𝘧(α) ⩽ 2g + 1
- The points on the hyper-elliptic curve do not form a group unlike an elliptic curve
- The hyper-elliptic curve works on divisor which is branded as the formal and finite sum of points on a hyper-elliptic curve that can be further symbolized by Mumford as:
Jacobian group is made by divisor from an abelian group and defining the order of Jacobian group as:
1.2. Hyper-Elliptic Curve Discrete Logarithm (HECDLP)
Suppose there is a divisor of order from the group of Jacobian Also, there is an equation , therefore finding the integer is called hyper-elliptic curve discrete logarithm problem.
1.3. Basic Notations
In this section, we discuss the basic notations used in our approach:
| Represents a hyper-elliptic curve over the field | |
| : | Is a large prime number and the value of |
| : | Is the divisor of the generalized elliptic curve |
| 𝒽1, 𝒽2, 𝒽3: | Demonstrate the hash functions |
| 𝓒: | Epitomizes the ciphertext |
| m: | Epitomizes the plaintext or message |
| M = 𝓂.: | Represents the message concatenation with divisor |
| : | Represents the private key of the signcrypter |
| : | Represents the public key of the signcrypter |
| : | Represents the private key of the unsigncrypter |
| : | Represents the public key of the unsigncrypter |
| Is a fresh nonce | |
| : | Represent the secret key |
| , : | Representing the subdivided secret key |
| E/D: | Represents the encryption and decryption functions |
| Eyk (Exk(M)): | Represents double encryption |
| Dyk (Dxk(𝓒)): | Represents double decryption |
2. Formal Model of the Proposed Scheme
In Figure 1, we describe the proposed model of our scheme. Our approach contains four entities—data generator, signcrypter, certificate authority, server and verifier/unsigncrypter. Before starting communication the certificate authority first published the entire public parameters e.g., , The data generator verifies the public key of verifier from a certificate authority and then performs the signcryption process with a fresh nonce. After producing the signcryptext, the data generator uploads signcryptext to the server and the server just forwards it to the legitimate receiver/verifier. Later, the verifier first verifies the public key of data generator/signcrypter and then performs the unsigncryption process.
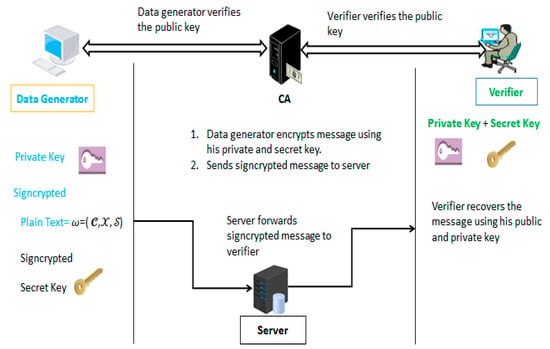
Figure 1.
Flow of Proposed Model.
2.1. Proposed Scheme Construction
The proposed includes key-generation phase, signcryption algorithm, and unsigncryption algorithm.
2.1.1. Key Generation
The Alice/signcrypter picks a number as a private key from and produces their public key = . Also, the Bob or unsigncrypter picks a number from and produces their public key = , where is the divisor on a hyper-elliptic curve.
2.1.2. Signcryption
The Algorithm 1, takes the public key of unsigncrypter, divisor, private key of signcrypter and the message (). After this produces the cipher text and their signature. Sends ω = (𝓒,) to Bob or unsigncrypter.
| Algorithm 1. Algorithm () |
| Randomly select a number γ from {1,…‥‥,q − 1}. |
| Select a nonce |
| Compute where is the divisor on a hyper-elliptic curve. |
| Divide into , |
| Compute |
| Compute |
| Divide into , |
| Compute |
| Compute 𝓒 = |
| Compute 𝓣 = (𝓒) |
| Compute 𝓢 = |
| Send ω = (𝓒, ) to Bob or Unsigncrypter |
2.1.3. Unsigncryption
After receiving the signcrypted text ω = (, ) this algorithm takes ciphertext, signature, the private key of unsigncrypter, divisor and public key of signcrypter (). Therefore, to check the signature authenticity and decrypt the cipher text to plaintext, the unsigncrypter performs unsigncryptions by using the Algorithm 2.
| Algorithm 2. Algorithm () |
| Compute = () |
| Compute (.) |
| Divide into , |
| Divide into , |
| Use the double decryption method |
| Compute |
| Compare if equality holds then there is no change in |
| Verification of signature is done through 𝒵. + . |
3. Correctness
Proof 1.
The unsigncrypter can create the secret session key by using the following calculations.
□
Proof 2.
When any conflict occurs between signcrypter and unsigncrypter, the trusted third party/judge can easily resolve the conflict by performing the following calculation.
□
4. Security Analysis
In this section, we discuss the security services of our proposed . Table 1 illustrates the comparisons of the proposed scheme and schemes [10,11,33,34] in terms of security services. Our proposed ensures security services such as resistance against replay attack, confidentiality, authenticity, unforgeability, integrity, non-repudiation, public verifiability, and forward secrecy. We validate our scheme by using a well-known simulation tool called AVISPA [35]. AVISPA is an automatic simulation tool for the purpose of validation, verification, and analysis of Internet security-sensitive modules, applications, and cryptographic techniques. With the verification of AVISPA, it becomes stress-free to ensure that the developed protocol is either SAFE or UNSAFE by considering security parameters. To find the results of the designed protocol, it is essential to put them in the form of the High level protocol specification language (HLPSL) language according to its syntax and rules. Code written on the rules of HLPSL language is then converted into lower-level machine language through the intermediate format (IF). The HLPSL2IF translator performs the translation to an intermediate format (IF). According to Dolev and Yao [36,37], HLPSL2IF translator checks the execution in the wisdom of giving initial knowledge, and every agent can construct the messages he is supposed to. AVISPA tool works with four back ends known as On-the-fly Model-Checker (OFMC), CL-based Attack Searcher (CL-AtSe), SAT-based Model-Checker (SATMC), and Tree-Automata-based Protocol Analyzer (TA4SP) to specify the results. OFMC implements a semi-decision procedure for security of protocols in a bounded number of sessions [38,39]. CL-AtSe represents the set of constraints used to discover if there are attacks on protocols [40]. SATMC [41] is the art of a propositional formula encoding and unrolling of the transition relation to put into a state-of-the-art (SAT) solver to translate back into the attack. The TA4SP [42] illustrates the under-approximation and over-approximation of sessions in protocols by approaching the intruder knowledge with the assistance of regular tree languages. Figure 2 shows the top down flow of AVISPA.

Table 1.
Comparison in term of security requirements.
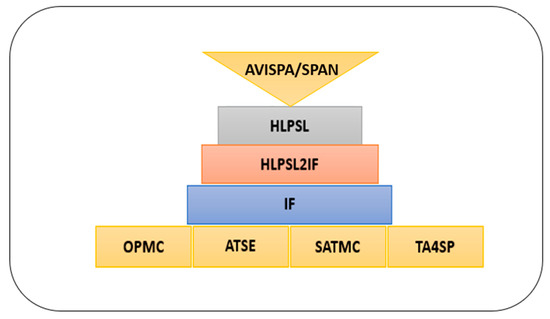
Figure 2.
AVISPA Push-bottom Flow.
4.1. Replay Attack
Our scheme ensures that the attacker cannot perform the reply attack based on old messages. If an attacker wants to resend old messages to the unsigncrypter then it generates the tuple ω = (,) and sends to the unsigncrypter. After receiving a tuple ω = (,) the unsigncrypter checks the nonce Nr, if it is fresh then the unsigncrypter accepts the tuple otherwise rejects it.
4.2. Confidentiality
Our scheme completely satisfies the security requirement of confidentiality. However, before sending the message to the unsigncrypter, the signcrypter uses the secret key to convert the message into ciphertext. Then, an intruder can try to get it from Equation (2). Thus, the intruder must solve Equation (3) and for it must also compute first Equation (4). It is always very challenging to generate the original ciphertext for two hyper-elliptic curve discrete algorithmic problems, so confidentiality of the scheme is maintained.
4.3. Integrity
Our approach calculates the hash value of the message by using the following Equation (5) before delivery. After getting a message the unsigncrypter first checks the freshness of and then computes the hash value from the Equation (6). If freshness checking () results in then integrity of the message is maintained.
4.4. Authenticity
Our scheme ensures the authenticity of signcrypter as the unsigncrypter extract , by computing = , . This is not possible for an intruder to challenge the authenticity of our scheme because they will need the public key of signcrypter and the private key of unsigncrypter to do that. Moreover, unsigncrypter verifies the validity of , after decryption of ciphertext (C) and compares computed , and decrypted , from the cipher text.
4.5. Unforgeability
To produce a forged signature, the forger needs the random private number and the private key of signcrypter , as to whom in the following equation. Furthermore, to find out the private random number and the private key of a sender , the forger must compute Equations (3) and (4). This is not feasible for a forger to makes two time hyper-elliptic discrete algorithmic problems. Therefore, the unforgeability is maintained in our approach.
4.6. Non-Repudiation
Our scheme assures the security service of non-repudiations. In proposing an approach, the sender generates a digital signature on a message like Equation (7). Hence, in this way, if the signcrypter wants to repudiate from there sent messages the trusted third party can easily identify the source by using the public key of signcrypter.
4.7. Forward Secrecy
Our designed meets forward secrecy services of security. In our scheme, even if the private key of a signcrypter is compromised, the attacker cannot decrypt the messages because we use the session secret key for encryption and decryption. Therefore, to generate the secret key from Equation (2), the attacker needs the random number , which is private to the signcrypter. Thus, to generate by using Equation (2) is infeasible and intolerable for attacker to solve the hyper-elliptic curve discrete algorithmic problem. Furthermore, we refresh the secrete key at each session. In this way, our scheme strongly satisfies the forward secrecy property.
4.8. Public Verifiability
Our designed ensures public verifiability; to resolve the conflict, a trusted third party can verify the message is from signcrypter or not, by using the following equations.
- Compute ()
- Compute
- Compare if equality holds, then there is no change in
- Verification of signature is done through 𝒵. + ., if satisfy then the message from signcrypter otherwise not.
We have investigated the security services of the designed scheme in terms of a signcryption program. Our designed signcryption scheme accords with the security services for the implementation of both encryption and signatures. We inspected the similarity models of the previous signcryption mechanisms; it is clear that our signcryption scheme offers effective countermeasures in security services, such as schemes [10,33,34], and has been pointed out that the scheme cannot provide resistance against replay attack and not validated through simulation tool; scheme [11] cannot satisfy the services of non-repudiation, and replay attack resistance, and is not validated through simulation tool. By comparison with the previous signcryption mechanisms, the designed method can accomplish all the security services as claimed. Table 1 shows the security requirement comparisons of the proposed scheme and existing schemes [10,11,33,34]. We use the notations for confidentiality, for integrity, for authentication, for unforgeability, for non-repudiation, for forward secrecy, for public verifiability, for reply attack resistance and for security validation by using simulation tools. In addition, we use notation to satisfy the property and not satisfied the property.
5. Computational Cost
It is important to note that the computational cost is necessary for both sender and receiver. Existing security schemes use elliptic curve point multiplication (𝓔𝓒-𝓟𝓜) which is considered to be a costly operation to measure the computational cost [43]. We use hyper-elliptic curve divisor multiplication (𝓗𝓒-𝓓𝓜) that is far cheaper than (𝓔𝓒-𝓟𝓜) in computational cost. Table 2 shows the computational cost comparisons standard security schemes with the proposed scheme.

Table 2.
Comparison of computational cost in terms of major operations.
We observed from [44] the experiments were produced hrough by a PC with the following specifications:
- Intel Core i74510UCPU
- 2.0 GHz processor
- 8 GB of memory
- Windows 7 Home Basic
- Multi-precision Integer and Rational Arithmetic C Library (MIRACL)
Their results concluded that single scalar multiplication practices 0.97 ms for elliptic curve point multiplication (𝓔𝓒-𝓟𝓜). We suppose that, if using the same environment like [44], the hyper-elliptic curve divisors scalar multiplication (𝓗𝓒-𝓓𝓜) will be consumes 0.48 ms because it is the generalized form of elliptic curves and uses the half amount of key,i.e., 80 bits. The following Table 3 shows the computational cost comparisons with respect to time- consuming in milliseconds:

Table 3.
Comparative computational cost in term of milli seconds (ms).
The computational cost is calculated by using the formula [45]. As shown in Table 3, we observed that the schemes [10,11,33] have the same computational cost which is 4.85 ms, scheme [34] is 5.86 ms and proposed scheme is 2.88 milliseconds.
6. Communication Cost
The minimum communication overhead is the essential requirement of a cryptographic technique for wireless networks. In our approach, we assume that for elliptic curve where is a large prime number and for hyper-elliptic curve where 𝓺 is a large prime number Table 4 elaborates the comparisons in terms of cipher text size and additional parameters. The communication cost of schemes [10,11,33] is Also the communication cost of a scheme [34] is and proposed scheme is |.

Table 4.
Shows the communication cost of proposed and existing signcryption.
Generalized Formulas for the Reduction of Communication Cost
Reduction formulas for the communication cost of the proposed scheme in comparison to the schemes of [10,11,33] are computed with the help of the following equation.
Also, the reduction formula for the communication cost of the proposed scheme as compared to a scheme [34] is followed by Equation (3).
Reduction in communication cost depends upon the selection of parameters and the quantity of data. Table 5 shows the comparisons of communication cost of different sizes of ciphertext and parameters of elliptic curves and hyper-elliptic curve of the proposed and existing schemes [10,11,33,34]. It is clear from our analysis that our scheme uses 21.27% to 52.63% less communication cost than [10,11,33], and 11.90% to 35.71% less than the technique presented in [34].

Table 5.
Communication cost comparisons in terms of size of cipher text.
7. Applications
In this phase, we discuss the applications of our design approach in e-payment systems during online shopping [46,47]. Online shopping system includes three main roles—customer, bank, and merchant. Figure 3 shows the deployment of our scheme in e-payment during online shopping. In this system, the customer first selects the item to buy according to his choice. After this, the merchant will send a validated payment order to his customer. Furthermore, the customer generates a signcryptext of validated payment and then sends it to the bank. After receiving the signcryptext the bank approves payment validations by checking their account details. The bank encrypts these charges through secret key, stores it in the temporary memory and sends it back to the customer with following instructions
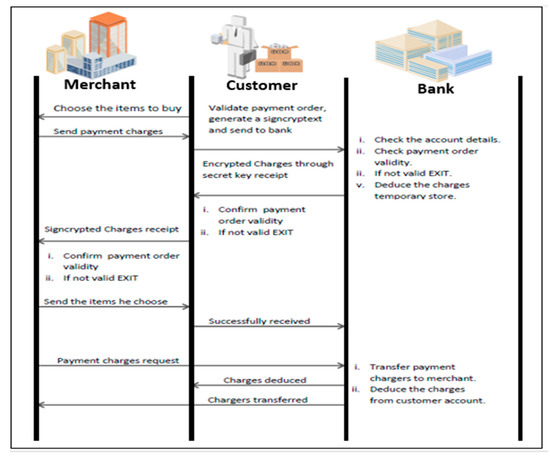
Figure 3.
Explanation of application.
- Confirm payment order validity
- If not valid then EXIT
For the further process of order, the customer signcrypts these details and sends to the merchant. After confirming the payment order validity, the merchant delivers the particular goods to the customer. After receiving the goods, the customer forwards this acknowledgment to the bank to deduct the charges from his account. To end the whole communication securely, the bank sends payment deduction to the sender as well as to the merchant.
8. Conclusions
This paper presents a new provable secured signcryption scheme () based on hyper-elliptic curve. The proposed scheme, reduced in communication cost about 21.27% to 52.63% from [10,11,33], and from [34] is about 11.90% to 35.71%, and reduced in computational cost about 40.61% from [10,11,33], and about 50.85% from [34]. Furthermore, the proposed scheme ensures security properties such as resistance against replay attack confidentiality, authenticity, unforgeability, integrity, non-repudiation, public verifiability, and forward secrecy. Furthermore, we have validated the security properties of our proposed scheme by using well-known simulation tools such as AVISPA.
Author Contributions
Conceptualization, I.U. and N.U.A.; methodology, I.U.; software, H.K., J.K., and M.R.; validation, I.U., J.K., M.R., N.U.A., and M.N.; formal analysis, I.U.; investigation, S.J.K.; writing—original draft preparation, I.U.; writing—review and editing, H.A.; supervision, N.U.A.; project administration, N.U.A.
Funding
This study received no external funding.
Acknowledgments
The authors thanks to anonymous reviewers.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
This section we validate our scheme by using a well-known simulation tool called AVISPA [35]. We generate HLPSL code for our proposed scheme which is shown in Table A1 and tests the result over two protocols OFMC and CL-based Attack Searcher (ATSE). Figure A1 and Figure A2 represent the simulation results of the proposed scheme over OFMC and ATSE, respectively. We cannot use the same notations of our algorithm in HLPSL code due to the classified syntax of the AVISPA tool. The notations used afore to arrow are termed in algorithm and notations procedure after the arrow are used in HLPSL code.
- → H, HH, HHH: hash functions
- M: Is plain text or message
- → M’: Is the cipher text
- → Ju: public key of unsigncrypter
- → inv (Js): private key of signcrypter
- → inv (Ju): private key of unsigncrypter
- → Js: public key of signcrypter
- →(Signcrypter.{H1(M’.Xz’.Nr)}_inv(Js).{H2(Alpa’.H1(M’.Xz’.Nr).inv(Js)).Ju}_Eyk’.{M’.Nr.Exk’}_Eyk’): encryption
- → (Signcrypter.{H1(M’.Xz’.Nr)}_inv(Js).{H2(Alpa’.H1(M’.Xz’.Nr).inv(Js) ).Ju}_Eyk’.{M’.Nr.Exk’}_Eyk’): decryption.
- → Eyk, Exk: Symmetric key
- → Alpa’: random number
- , → Xz,Yz: Dividing
- Ki → intruder public key
- inv (ki) → intruder private key
- → {M’.Nr.Exk’}_Eyk’)
- → {H1(M’.Xz’.Nr)}_inv(Js)
- → {H2(Alpa’.H1(M’.Xz’.Nr).inv(Js) ).Ju}_Eyk’
In algorithm represents the signature, represents double encryption and represents double decryption which cannot be signified directly in the code. In HLPSL code Ns: represents nonce for signcrypter, Nr: nonce for unsigncrypter, K: symmetric key, Ki: intruder public key, inv (ki): intruder private key, ki: symmetric key of an intruder.

Table A1.
HLPSL CODE.
Table A1.
HLPSL CODE.
| HLPSL Code () |
| role |
| %%start of the protocol by Signcrypter already knows the Unsigncrypter’s |
| role_Signcrypter(Signcrypter:agent,Unsigncrypter:agent,Ju:public_key,Js:public_key,Nr:text,Ns:text,SND,RCV:channel(dy)) |
| played_by Signcrypter |
| def= |
| local |
| %%start of the protocol by Signcrypter already knowing the %%Unsigncrypter’s public key |
| State:nat,Alpa:text,H1:hash_func,Xz:text,H2:hash_func,Eyk:symmetric_key,M:text,Exk:symmetric_key |
| init |
| State:= 0 |
| transition |
| %% signcrypter receives challenge from Unsigncrypter by using his public %%key and nonce, sends message to unsigncrypter in response |
| 1. State=0/\ RCV(Unsigncrypter.{Ns}_Js) =|> State’:=1/\ Eyk’:=new()/\ Exk’:=new()/\ M’:=new()/\ Xz’:=new()/\ Alpa’:=new()/\ SND(Signcrypter.{H1(M’.Xz’.Nr)}_inv(Js).{H2(Alpa’.H1(M’.Xz’.Nr).inv(Js)).Ju}_Eyk’.{M’.Nr.Exk’}_Eyk’)/\ SND(Signcrypter.{H2(Alpa’.H1(M’.Xz’.Nr).inv(Js)).Ju}_Eyk’)/\ SND(Signcrypter.{M’.Nr.Exk’}_Eyk’) |
| end role |
| role |
| %%defining the role played by signcrypter by using its keys… |
| role_Unsigncrypter(Signcrypter:agent,Unsigncrypter:agent,Ju:public_key,Js:public_key,Nr:text,Ns:text,SND,RCV:channel(dy)) |
| played_by Unsigncrypter |
| def= |
| local |
| State:nat,Alpa:text,H1:hash_func,Xz:text,H2:hash_func,Eyk:symmetric_key,M:text,Exk:symmetric_key |
| init |
| State:= 0 |
| transition |
| 1. State=0/\ RCV(start) =|> State’:=1/\ SND(Unsigncrypter.{Ns}_Js) |
| 2. State=1/\ RCV(Signcrypter.{H1(M’.Xz’.Nr)}_inv(Js).{H2(Alpa’.H1(M’.Xz’.Nr).inv(Js)).Ju}_Eyk’.{M’.Nr.Exk’}_Eyk’) =|> State’:=2 |
| 3. State=2/\ RCV(Signcrypter.{H2(Alpa.H1(M.Xz.Nr).inv(Js)).Ju}_Eyk) =|> State’:=3 |
| 4. State=3/\ RCV(Signcrypter.{M.Nr.Exk}_Eyk) =|> State’:=4 |
| end role |
| role |
| %%session1 between agents signcrypter and unsigncrypter |
| session1(Signcrypter:agent,Unsigncrypter:agent,Ju:public_key,Js:public_key,Nr:text,Ns:text) |
| def= |
| local |
| SND2,RCV2,SND1,RCV1:channel(dy) |
| composition |
| role_Unsigncrypter(Signcrypter,Unsigncrypter,Ju,Js,Nr,Ns,SND2,RCV2)/\ role_Signcrypter(Signcrypter,Unsigncrypter,Ju,Js,Nr,Ns,SND1,RCV1) |
| end role |
| role |
| %%session2 between agents signcrypter and unsigncrypter |
| session2(Signcrypter:agent,Unsigncrypter:agent,Ju:public_key,Js:public_key,Nr:text,Ns:text) |
| def= |
| local |
| SND1,RCV1:channel(dy) |
| composition |
| role_Signcrypter(Signcrypter,Unsigncrypter,Ju,Js,Nr,Ns,SND1,RCV1) |
| end role |
| role environment() |
| def= |
| const |
| hash_0:hash_func,nr:text,ju:public_key,alice:agent,bob:agent,js:public_key,ns:text,const_1: agent,const_2:public_key,const_3:public_key,const_4:text,const_5:text,auth_1:protocol_id, sec_2:protocol_id |
| intruder_knowledge = {alice,bob} |
| composition |
| session2(i,const_1,const_2,const_3,const_4,const_5)/\ session1(alice,bob,ju,js,nr,ns) |
| end role |
| goal |
| %% defining the goals as an aim of protocol |
| authentication_on auth_1 |
| secrecy_of sec_2 |
| end goal |
| environment() |
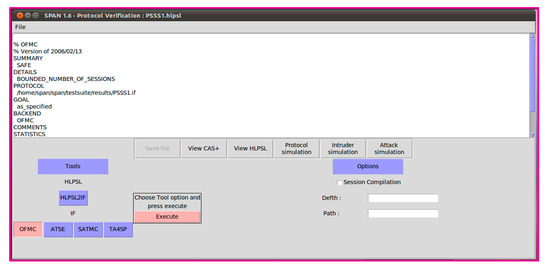
Figure A1.
OFMC simulation results.
Figure A2.
ATSE simulation results.
References
- Mehmood, A.; Ullah, I.; Noor-Ul-Amin; Umar, A.I. Public Verifiable Generalized Authenticated Encryption (ℙ℣₢Ǣ) based on Hyper Elliptic Curve. J. Appl. Environ. Biol. Sci. 2017, 7, 194–200. [Google Scholar]
- Sadat, A.; Ahmad, R.; Ullah, I.; Khattak, H.; Ullah, S. Multi Receiver Signcryption Based On Hyper Elliptic Curve Cryptosystem. J. Appl. Environ. Biol. Sci. 2017, 7, 194–200. [Google Scholar]
- Zheng, Y. Digital signcryption or how to achieve cost (signature & encryption) ≪ cost (signature) + cost(encryption). Lect. Notes Comput. Sci. 1997, 165–179. [Google Scholar] [CrossRef]
- Bao, F.; Deng, R.H. A signcryption scheme with signature directly verifiable by public key. Lect. Notes Comput. Sci. 1998, 55–59. [Google Scholar] [CrossRef]
- Zheng, Y. Identification, signature and signcryption using high order residues modulo an RSA composite. In Public Key Cryptography; Springer: Berlin/Heidelberg, Germany, 2001; pp. 48–63. [Google Scholar]
- Malone-Lee, J.; Mao, W. Two Birds One Stone: Signcryption Using RSA. Lect. Notes Comput. Sci. 2003, 211–226. [Google Scholar] [CrossRef]
- Baek, J.; Steinfeld, R.; Zheng, Y. Formal proofs for the security of signcryption. In Public Key Cryptography; Springer: Berlin/Heidelberg, Germany, 2002; pp. 80–98. [Google Scholar]
- Sharma, G.; Bala, S.; Verma, A.K. An identity-based ring signcryption scheme. In IT Convergence and Security; Springer: Dordrecht, The Netherlands, 2013; pp. 151–157. [Google Scholar] [CrossRef]
- Zheng, Y.; Imai, H. How to construct efficient signcryption schemes on elliptic curves. Inf. Process. Lett. 1998, 68, 227–233. [Google Scholar] [CrossRef]
- Hwang, R.-J.; Lai, C.-H.; Su, F.-F. An efficient signcryption scheme with forward secrecy based on elliptic curve. Appl. Math. Comput. 2005, 167, 870–881. [Google Scholar] [CrossRef]
- Toorani, M.; Beheshti, A.A. An elliptic curve-based signcryption scheme with forward secrecy. arXiv 2010, arXiv:1005.1856. [Google Scholar] [CrossRef]
- Nizamuddin; Chudry, S.A.; Amin, N. Signcryption schemes withforward secrecybased on hyperelliptic curve cryptosystem. In Proceedings of the High Capacity Optical Networks and Enabling Technologies, (HONET), Riyadh, Saudi Arabia, 19–21 December 2011; pp. 244–247. [Google Scholar]
- Nizamuddin; Chudry, S.A.; Nasar, W.; Javaid, Q. Efficient signcryption schemes based on hyper elliptic curve cryptosystem. In Proceedings of the 7th International Conference on Emerging Technologies (ICET), Islamabad, Pakistan, 5–6 September 2011; pp. 1–4. [Google Scholar]
- Malone-Lee, J. Identity Based Signcryption. Cryptology ePrint Archive, Report 2002/098. 2002. Available online: https://eprint.iacr.org/2002/098.pdf (accessed on 26 May 2019).
- Libert, B.; Quisquater, J.J. A new identity based signcryption scheme from pairings. In Proceedings of the IEEE Information Theory Workshop (Cat. No.03EX674), Paris, France, 31 March–4 April 2003. [Google Scholar] [CrossRef]
- Chow, S.S.M.; Yiu, S.M.; Hui, L.C.K.; Chow, K.P. Efficient Forward and Provably Secure ID-Based Signcryption Scheme with Public Verifiability and Public Ciphertext Authenticity. Lect. Notes Comput. Sci. 2004, 352–369. [Google Scholar] [CrossRef]
- Boyen, X. Multipurpose Identity-Based Signcryption. Lect. Notes Comput. Sci. 2003, 383–399. [Google Scholar] [CrossRef]
- Chen, L.; Malone-Lee, J. Improved identity-based signcryption. In Proceedings of the Public Key Cryptography-PKC’05, LNCS 3386, Les Diablerets, Switzerland, 23–26 January 2005; pp. 362–379. [Google Scholar]
- Barreto, P.S.L.M.; Libert, B.; McCullagh, N.; Quisquater, J.-J. Efficient and Provably-Secure Identity-Based Signatures and Signcryption from Bilinear Maps. In Advances in Cryptology—ASIACRYPT 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 515–532. [Google Scholar]
- Selvi, S.S.D.; Vivek, S.S.; Rangan, C.P. Identity based public verifiable signcryption scheme. In Proceedings of the ProvSec’10, LNCS 6402, Malacca, Malaysia, 13–15 October 2010; pp. 244–260. [Google Scholar]
- Yu, Y.; Yang, B.; Sun, Y.; Zhu, S. Identity based signcryption scheme without random oracles. Comput. Stand. Interfaces 2009, 31, 56–62. [Google Scholar] [CrossRef]
- Jin, Z.; Wen, Q.; Du, H. An improved semantically-secure identity-based signcryption scheme in the standard model. Comput. Electr. Eng. 2010, 36, 545–552. [Google Scholar] [CrossRef]
- Li, F.; Muhaya, F.B.; Zhang, M.; Takagi, T. Efficient Identity-Based Signcryption in the Standard Model. Lect. Notes Comput. Sci. 2011, 120–137. [Google Scholar] [CrossRef]
- Liu, Z.; Hu, Y.; Zhang, X.; Ma, H. Certificateless signcryption scheme in the standard model. Inf. Sci. 2010, 180, 452–464. [Google Scholar] [CrossRef]
- Miao, S.; Zhang, F.; Li, S.; Mu, Y. On security of a certificateless signcryption scheme. Inf. Sci. 2013, 232, 475–481. [Google Scholar] [CrossRef]
- Weng, J.; Yao, G.; Deng, R.; Chen, M.; Li, X. Cryptanalysis of a certificateless signcryption scheme in the standard model. Inf. Sci. 2011, 181, 661–667. [Google Scholar] [CrossRef]
- Zhu, H.; Li, H.; Wang, Y. Certificateless signcryption scheme without pairing. J. Comput. Res. Dev. 2010, 47, 1587–1594. [Google Scholar]
- Huang, Y.; Zhang, J.; Chen, H. On the Security of a Certificateless Signcryption Scheme. In Proceedings of the IWECA 2014, Ottawa, ON, Canada, 8–9 May 2014; pp. 664–667. [Google Scholar]
- Shi, W.; Kumar, N.; Gong, P.; Zhang, Z. Cryptanalysis and improvement of a certificateless signcryption scheme without bilinear pairing. Front. Comput. Sci. 2014, 8, 656–666. [Google Scholar] [CrossRef]
- Cheng, L.; Wen, Q. An improved certificateless signcryption in the standard model. Int. J. Netw. Secur. 2015, 17, 597–606. [Google Scholar]
- Islam, S.; Li, F. Leakage-free and provably secure certificateless signcryption scheme using bilinear pairings. Comput. J. 2015, 58, 2636–2648. [Google Scholar] [CrossRef]
- Li, L.; Shirase, M.; Takagib, T. Certificateless hybrid signcryption. Math. Comput. Mod. 2013, 57, 324–343. [Google Scholar] [CrossRef]
- Mohapatra, R.K. Signcryption Schemes with forward Secrecy Based on Elliptic Curve Cryptography. Ph.D. Thesis, 2010. Available online: http://ethesis.nitrkl.ac.in/2009/ (accessed on 26 May 2019).
- Elkamchouchi, H.M.; El-Atiky, M.H.; Abouelkheir, E. A Public Verifiability Signcryption Scheme without Pairings. Int. J. Comput. Appl. 2017, 157, 35–40. [Google Scholar]
- Vigano, L. Automated security protocol analysis with the AVISPA tool. Electron. Notes Theor. Comput. Sci. 2006, 155, 61–86. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the Security of Public-Key Protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Basin, D.; Modersheim, S.; Vigan, L. An On-The-Fly Model-Checker for Security Protocol Analysis. In Proceedings of the ESORICS’03; Springer-Verlag: Berlin/Heidelberg, Germany, 2003; LNCS 2808; pp. 253–270. [Google Scholar]
- Clark, J.; Jacob, J. A Survey of Authentication Protocol Literature: Version 1.0. 17 November 1997. Available online: www.cs.york.ac.uk/~jac/papers/drareview.ps.gz (accessed on 26 May 2019).
- Donovan, B.; Norris, P.; Lowe, G. Analyzing a Library of Security Protocols using Casper and FDR. In Proceedings of the FLOC’99 Workshop on Formal Methods and Security Protocols (FMSP’99); 1999. Available online: http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.21.7256 (accessed on 26 May 2019).
- Chevalier, Y.; Vigneron, L. Automated Unbounded Verification of Security Protocols. In Proc. CAV’02, LNCS 2404; Springer: Berlin/Heidelberg, Germany, 2002; Available online: https://link.springer.com/chapter/10.1007/3-540-45657-0_24 (accessed on 26 May 2019).
- Armando, A.; Compagna, L. SATMC: A SAT-based Model Checker for Security Protocols. In Proc. JELIA’04, LNAI 3229; Springer: Berlin/Heidelberg, Germany, 2004; Available online: https://link.springer.com/chapter/10.1007/978-3-540-30227-8_68 (accessed on 26 May 2019 ).
- Boichut, Y.; Heam, P.-C.; Kouchnarenko, O.; Oehl, F. Improvements on the Genet And Klay Technique to Automatically Verify Security Protocols. In Proc. AVIS’04, ENTCS. Available online: https://www.researchgate.net/publication/246435265_Improvements_on_the_Genet_and_Klay_technique_to_automatically_verify_security_protocols (accessed on 26 May 2019).
- Ullah, S.; Junaid, M.; Habib, F.; Sana; Insafullah; Hizbullah. A novel proxy blind signcryption scheme based on hyper elliptic curve. In Proceedings of the 12th International Conference on Natural Computation, Fuzzy Systems and Knowledge Discovery (ICNC-FSKD), Changsha, China, 13–15 August 2016. [Google Scholar] [CrossRef]
- Zhou, C.; Zhao, Z.; Zhou, W.; Mei, Y. Certificateless Key-Insulated Generalized Signcryption Scheme without Bilinear Pairings. Secur. Commun. Netw. 2017, 2017, 8405879. [Google Scholar] [CrossRef]
- Ch, S.A.; Nizamuddin; Sher, M. Public Verifiable Signcryption Schemes with Forward Secrecy Based on Hyperelliptic Curve Cryptosystem. Commun. Comput. Inf. Sci. 2012, 135–142. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Farash, M.S.; Naqvi, H.; Sher, M. A secure and efficient authenticated encryption for electronic payment systems using elliptic curve cryptography. Electron. Commer. Res. 2015, 16, 113–139. [Google Scholar] [CrossRef]
- Yang, J.H.; Chang, Y.F.; Chen, Y.H. An efficient authenticated encryption scheme based on ECC and its application for electronic payment. Inf. Technol. Control 2013, 42, 315–324. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).