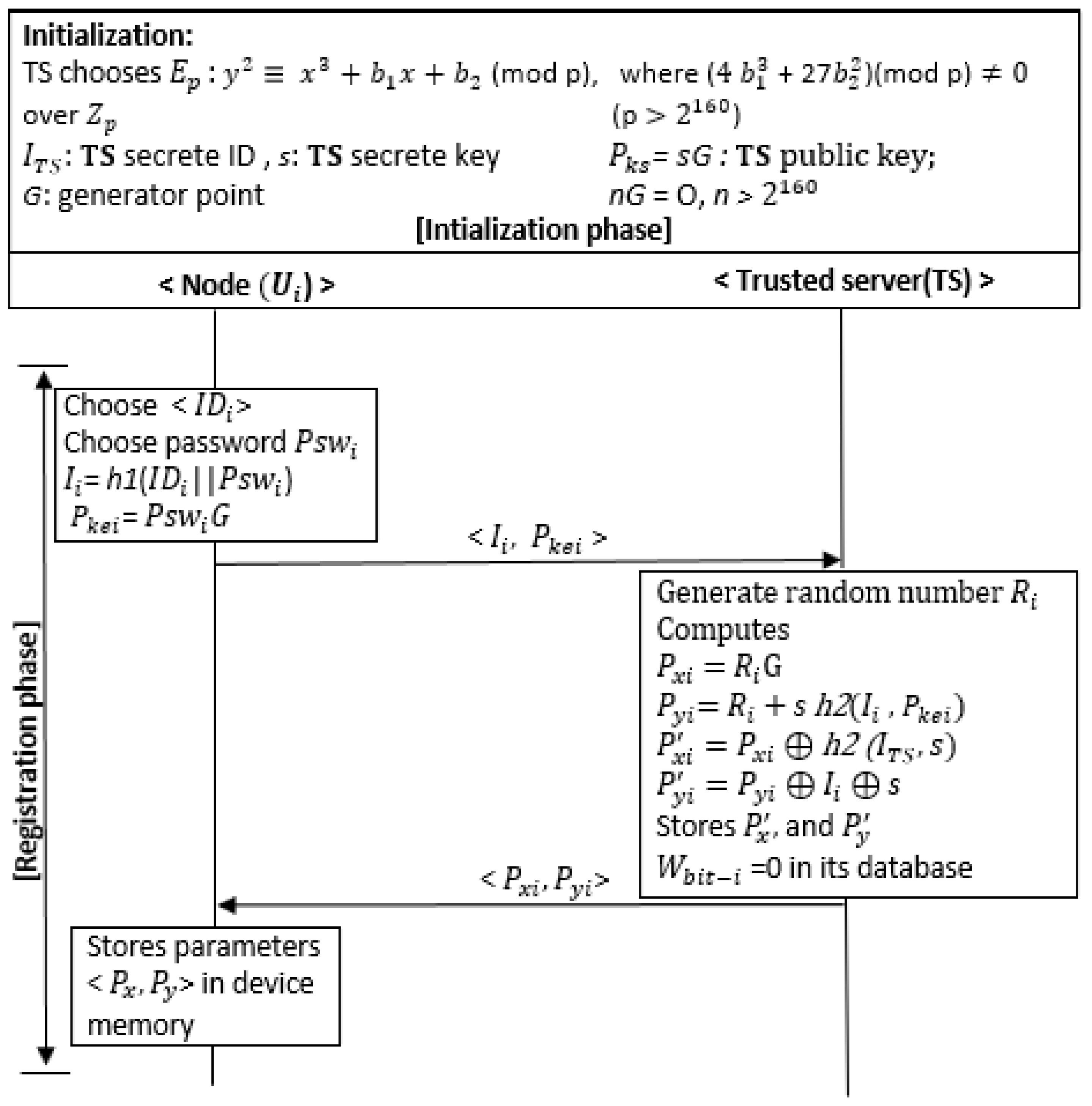
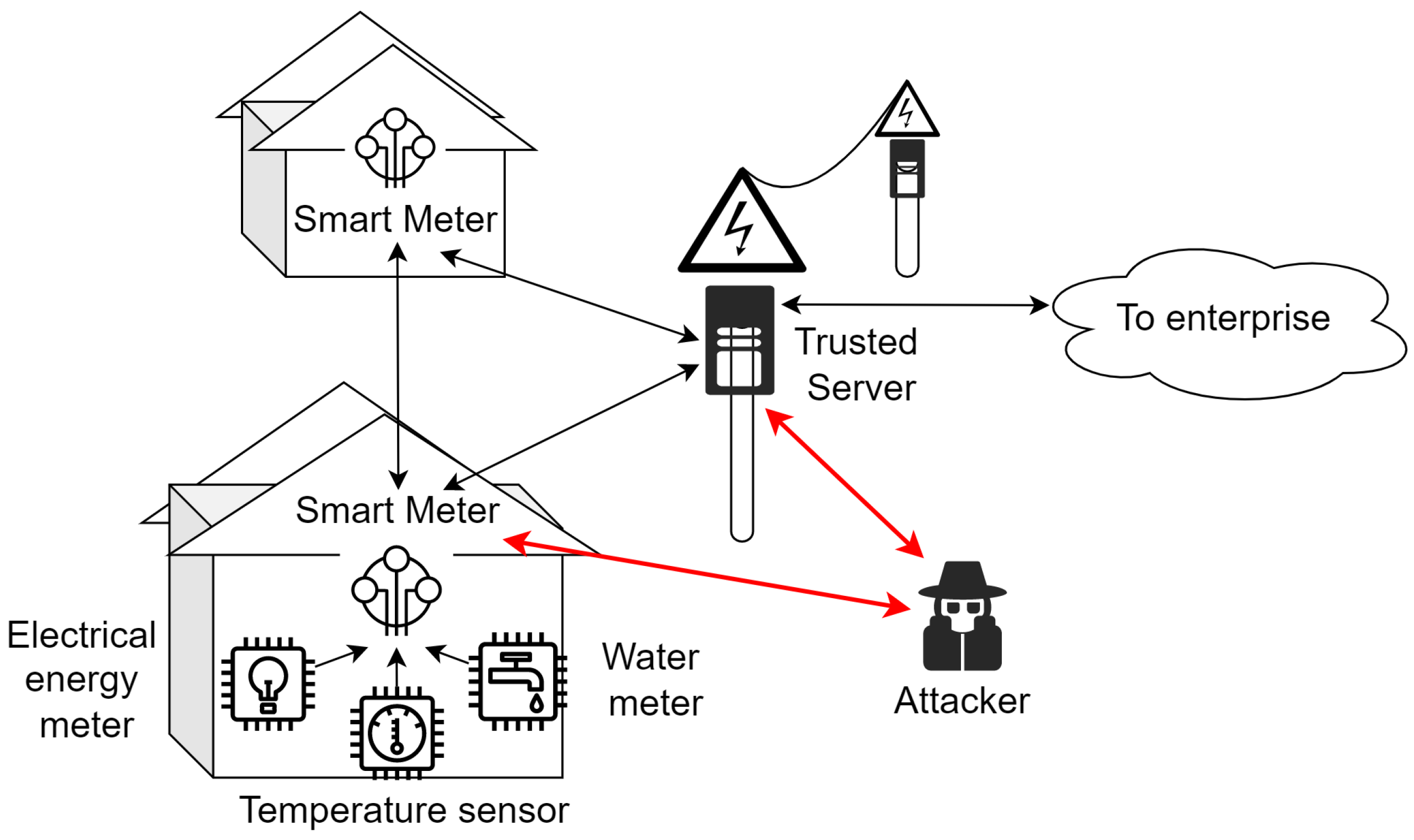
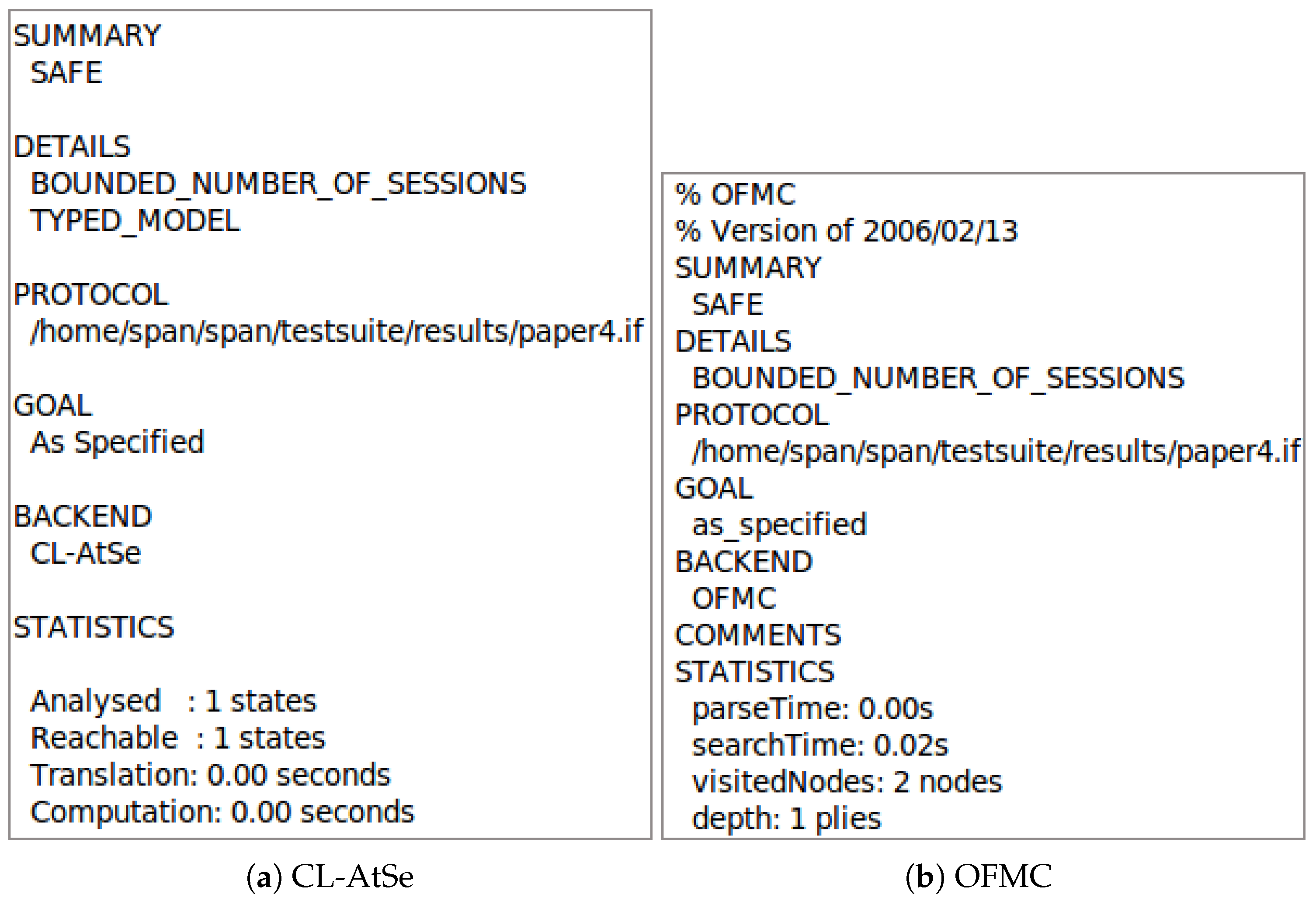
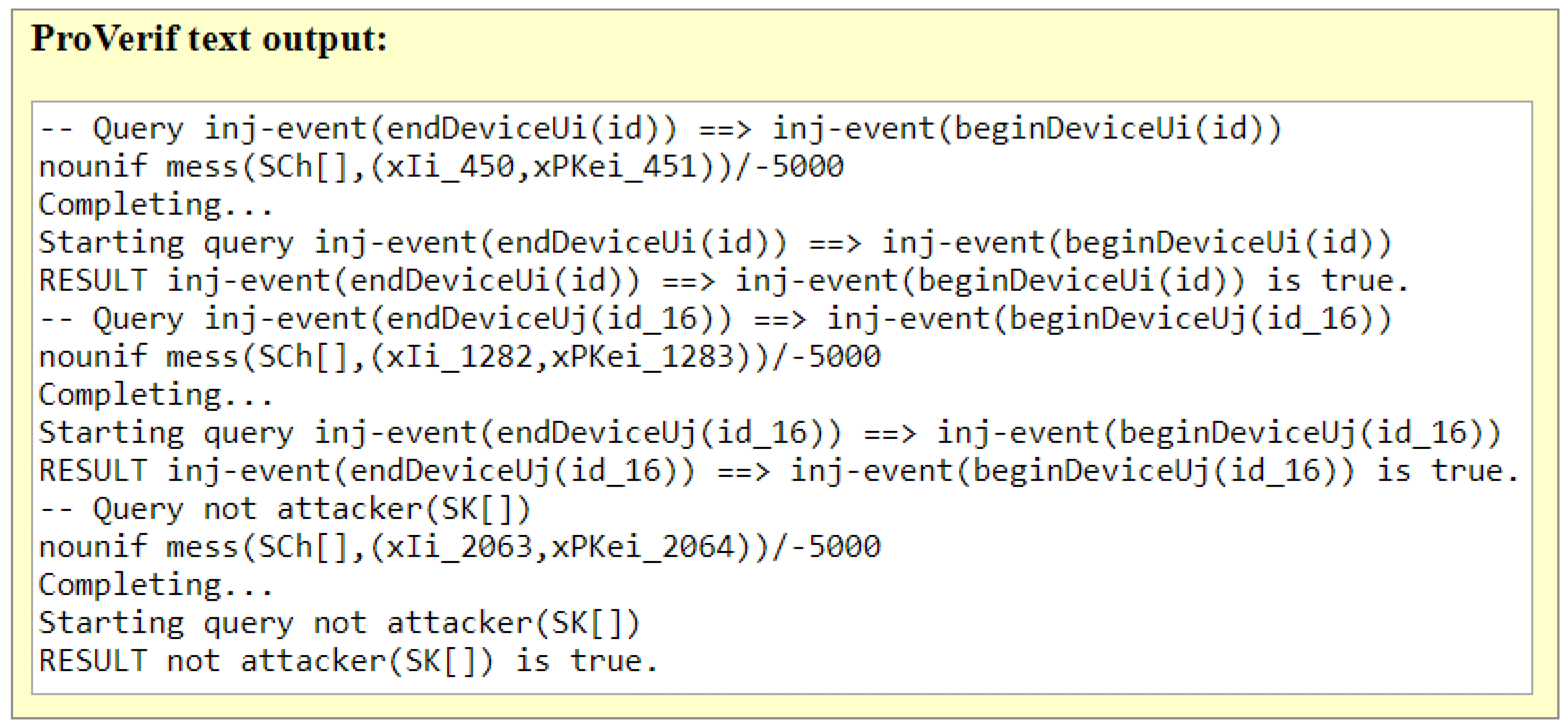
4.1. Formal Security Analysis
To assess
’s effectiveness in attacking LAP-SG and capture its interaction with a node and the ts, we leverage the BPR2000 model [
17,
18].
In BPR2000, queries model the actual adversary capabilities in a real attack. We consider the Send(), Reveal(), Corrupt(), Execute(), and Test() queries defined in [
17]. Furthermore, we consider the following additional queries. Freshness() ensures that the session key is not revealed to
. Thus, to maintain the freshness at instant
t, we must ensure that, at time
t, the Authentication Protocol (AP) computes a session key
. The Reveal() query must not be issued; from the start of the game, at most one Corrupt() query (where the oracle can reveal secret password
and all current instant
of
) has been issued; the common session key
is established if both partners involved at
t are mutually authenticated to each other. Furthermore, impersonation attacks fail only when the TS (or
) agree on a common session key that has not yet been shared with
(or TS).
To prove the security of LAP-SG, we introduce the following.
Theorem 1. Consider a PPT making at most q queries, divided in send(), execution(), and hash() queries with length . Furthermore, consider with advantage . Then, for our, it holdswhere is the time required to solve the ECDH problems. Therefore, LAP-SG is semantically secure. Proof. To provide a proof, we exploit game theory. We define five games, denoted as , . denotes the success of the adversary in the ith game, i.e., the adversary successfully guesses bit c after executing the query in game . We define the games as follows.
Game . This game models semantic security attacks on the proposed protocol.
correctly guesses bit
c with probability
. Therefore, the advantage of
in
is
Game . This game models an eavesdropping attack. Via query, can intercept the messages and . also queries the oracle to check whether the received data are the actual session key . To compute the session key, must know the short-term secrets , as well as the long-term secrets and s. Therefore, has no additional advantage in compared to . Therefore, .
Game . This game models an active attack through the use of all oracles queries. However, the selection of random ephemeral secrets
among different sessions is avoided. Also, a collision in the output hash function is avoided. Therefore, game
and
are identical except for the
and
queries in
. Using the birthday paradox, we obtain
where
q is the overall number of queries and
is the length of the query.
Game . This game models an active attack where, without the input of the oracle
query,
is able to identify the hash values
. However, this results in the termination of the protocol authentication. Game
and
are hence indistinguishable if and only if either
or the TS terminate the protocol. Therefore, it follows that
Game . This game considers the Canetti–Krawczyk (CK) adversary model and assumes that either the short-term secrets
or the long-term secrets are revealed during the communication between the involved participant and the TS. In this case, the adversary’s goal is to find the session key by successfully executing the
query. However, to obtain the session key it is required to solve ECDHP and CDHP problems. Therefore, the difference between
and
is negligible as long as the likelihood of solving ECDHP and CDHP is Small. Hence, we have
where
is the time required to solve ECDHP problems, and
is the time required to solve CDHP problems. We introduce the following Lemma 1 to prove the Theorem 1. □
Lemma 1. Difference lemma: Let , be the events of winning games and . Denote an error event by E, such that event occurs if and only if event exists with error E. Then, .
Now, applying difference Lemma 1 on the above games, we have
that can be rewritten as
Theorem 2. Consider a PPT making at most q queries, divided in , , and queries with length , such that the resultant advantage of is . For our, it holdswhere and are the times required to solve ECDH and CDHP problems. Therefore, LAP-SG provides secure mutual authentication. Proof. The proof is based on the games described in the proof of Theorem 1, where proofs from
to
are given. For
, we have
Using Lemma 1 and what is derived for Theorem 1, we can derive the proof of Theorem 2. □
4.2. Secure Protocol Design Analysis
In this subsection, we discuss the trade-off between security and usability of LAP-SG when needs to perform a brute force attack to guess , which may be unfeasible in polynomial time under the capabilities PC-2 and PC-1. For , the number of trials is given by , where represents the size of the device identity space and password space.
We also consider a situation where the adversary tries to exploit security usability parameters. In this case, tries to change the device password, or may run the device. In this case, it is hard for to detect in polynomial time using offline password guessing attacks (SC-FPEE), as the size of the space of is . If attempts to perform the DoS attack (SG-DoSA) to change the password, the maximum time for the password change facility is set to five attempts per day. In this a case, succeeds with probability , which is still higher than a polynomial time. In case of a successful DoS attack (SG-DoSA), the device owner can restore his device by re-registering it. The existing device credentials are then deleted. Due to the tamper-proof nature of the device, our device may have two essential threats, which include DoS attacks and online guessing attacks. However, to launch these attacks successfully on very low-cost IoT devices, needs high-costs instruments with little benefits. Thus, LAP-SG archives security beyond the optimal security limit .
In the next section, we discuss the security of LAP-SG against the most significant known attacks. Due to space constraints, we neglect the attacks that we instead consider in the AVISPA and ProVerif simulations, i.e., MiTM, replay, spoofing, and eavesdropping.
We assess LAP-SG security in comparison with other existing schemes [
3,
7,
13] and show the security capabilities of each solution in
Table 4. The comparison shows that LAP-SG is robust against a larger attack set compared to other existing schemes. Note that results for the state-of-the-art protocols are based on the respective authors’ claims. In addition, existing works, with an exception for Wang et al. [
9], do not explicitly mention security against insider attacks.
4.3. Analysis of Known Attacks
In this section, we discuss the security of LAP-SG against the most significant active and passive attacks.
Replay attack (Active): The attacker impersonates node
by reusing the previously sent challenges. The receiving node
recomputes and checks
via (
1). If true, then
computes another challenge
and forwards it to
. However, the attacker is unable to verify the challenge via (
2) and to compute a valid session key
, as she does not know
. The security parameters
and
are not sent through any messages over public channel nor can be acquired from
and
due to their tamper-proof design. In addition, the security of
(or
) and
(or
) is protected inside
(or
) and
(or
) by ECDHP and CDHP. Hence, LAP-SG is secure against replay attacks.
DoS attack (Active): LAP-SG terminates the communication if the number of incorrect attempts of entering exceeds a limit value. However, the authentication proceeds as long as correct is provided. If the adversary replaces the true challenge by randomly choosing ephemeral secrets and , the receiving node is unable to match the deduction and terminates the protocol with a failure message. The adversary being completely unaware of due to the tamper-proof nature of the device, LAP-SG is robust against DoS attacks.
Password-guessing attack (Passive): In LAP-SG, the original password is stored in using a one-way collision resistant function, and in using of ECDHP. An attacker is unable to guess without knowing and , which are stored in a tamper-proof device and hence not accessible. Hence, LAP-SG is robust against password-guessing attacks.
Node Impersonation attack (Active): Consider the scenario where the adversary impersonates an authenticated node
via parameters
. The adversary randomly chooses parameters
to reply to node
. Then, node
computes (
2), based on the received information. However, since the attacker ignores
,
,
, and
, the computed parameters result wrong, and the session is terminated. Since node
is a tamper-proof device,
and
are secure. Even if the attacker succeeds somehow in tampering the device, it is impossible to compute a valid session key, since the adversary is unaware of the secret parameters
. In addition,
is protected inside
and in session key
by ECDHP and CDHP. Therefore, LAP-SG is resistant towards node impersonation attacks.
Server Impersonation attack (Active): The adversary server randomly chooses parameters
responded to node
. Then, node
computes (
1). However, since the attacker does not know
, the result is wrong and the session is terminated. Since
is a tamper-proof device, the security of
is protected. If an attacker somehow succeeds at tampering the device, then it is impossible for an adversary server to compute a session key as it would need the secret parameters
. In addition, the security of
is protected inside
and in the session key
by ECDHP and CDHP. In addition,
s is protected inside the TS via ECDLP and CDHP
. Hence, LAP-SG is robust against server impersonation attacks.
Sever database theft attack (Passive): The attacker tries to steal information from the server’s database. However, the database is protected by ; therefore, the attacker is unable to compute without knowing s and . It is impossible for an attacker to extract s and from in polynomial time, as it exploits ECDLP and CDHP. If either s or are revealed to an attacker, it is impossible to compute the other parameter from . In addition, even if the encryption key is compromised, then attacker is unable to determine from , as is protected by s and . Therefore, LAP-SG is robust against server database theft attacks.
Node spoofing attack (Active): The attacker masquerades as a legitimate node to retrieve its secret credentials. As mentioned in the password guessing attack and replay attack, it is impossible for an attacker to extract and guess password from and thanks to ECDLP and CDHP. Furthermore, the security parameters and are ephemeral and expire after every session. In addition, security parameters are stored in tamper-proof nodes. Hence, LAP-SG is secure against node spoofing attacks.
Many logged-in users attack (Active): LAP-SG maintains a working bit for every communication. After a successful verification step, the involved nodes set their communication bit towards the communicating node to one. If node receives an authentication request from another node which uses the credentials of , then checks whether the status bit is equal to one. If the status is one, then node rejects these requests. Therefore, LAP-SG is robust against many logged-in users attacks.
Forward secrecy (Active): In LAP-SG the session key security depends not only on the private key , but also on the ephemeral secret which expires after every session termination. For an attacker, it is computationally impossible to extract the security parameters or from due to the complexity of the ECDLP and CDHP. Hence, LAP-SG is secure towards forward secrecy attacks.
Insider attack (Active): In LAP-SG, the password is sent to the TS or to other nodes via . In addition, it is impossible to extract the password from and from due to ECDLP and CDHP. Therefore, privileged insider attacks fail to impersonate the secret information of a legitimate node . Hence, LAP-SG is robust against insider attacks.
Known session-specific temporary information attack (Active): The session key computation is performed after successful mutual authentication between node and . If an adversary somehow succeeds in discovering the ephemeral secrets , still it would not be able to compute a session key as the password is protected via a one-way collision-resistant hash function , ECDLP and CDHP. In addition, if either one of the parameters is revealed to the attacker, it is computationally infeasible to determine either or from . This is due to the difficulties in solving the CDHP and ECDLP for pairs in using a polynomial-time algorithm. Consequently, LAP-SG withstands a known session-specific temporary information attack.
Attacks on node anonymity (Passive): Device anonymity ensures that the attacker cannot find the actual device identity of node . This identity is well-protected with their password by concealing it inside a one-way collision-resistant hash function, whose output is given by . Both and are never sent through any message. In addition, for every new communication, the device is able to change its periodically. In our scheme, we took the combination equation to present its identity to other nodes in network. However, even after knowing the combination equation value, the attacker cannot correctly guess the identity and password, which results in them failing to compute the next authentication equations and challenges. In addition, the security of the device is well protected because of the tamper-proof nature. Therefore, LAP-SG ensures the safety of the device’s identity and password over the CC.
Stolen-verifier attack (Active): During the registration phase, the TS stores
and
in its database. Even though the attacker may access this information, it would be unable to access the actual security parameters
and
, which are protected using the secret server key
s and
.
and
are stored in the tamper-proof device
, encrypted with secret key
. In addition, even if the attacker makes a large number of login request with another node
, it fails to verify the challenge (
1) and to compute
. This is due to the attacker being unaware of
, which is hard to extract from parameters
and
due to the one-way collision-resistant function, ECDHP, and the device’s tamper-proof nature. Consequently, LAP-SG can resist stolen-verifier attacks.
Man-in-the-middle attack (Active): The successful mutual authentication ensures the safety of an authentication scheme from man-in-the-middle attacks. LAP-SG prevents MiTM attacks and supports successful mutual authentication, which will be shown from the result of the ProVerif tool in
Section 4.5.
Eavesdropping attack (Passive): To perform a successful eavesdropping attack, the attacker needs to extract the security parameters , and from an open transmission channel. Even if the attacker succeeds in obtaining these security parameters, they cannot determine password . In addition, it is very hard to determine the ephemeral secret due to the complexity of ECDHP and ECDLP, as detailed in node impersonation attacks. Therefore, LAP-SG is resistant towards eavesdropping attacks.
We assess LAP-SG security in comparison with other existing schemes [
3,
7,
13] and show the security capabilities of each solution in
Table 4. The comparison shows that LAP-SG is robust against a larger attack set compared to other existing schemes. Note that the results for the state-of-the-art protocols are based on the respective authors’ claims. In addition, existing works, with the exception of that of Wang et al. [
9], do not explicitly mention security against insider attacks.