The location deployment of the base station as well as the resource allocation between and within user groups affect the overall transmission rate of the system. Therefore, it is important to study how to jointly deploy UAVs for rate optimization of RSMA downlink multi-user group systems under the uncertainty of UAV as a base station location. This section focuses on modeling and analyzing the UAV-assisted downlink RSMA system.
3.1. The Downlink RSMA System’s Modeling
The downlink RSMA system model studied in this paper is shown in
Figure 1. Different groups of users use different communication channels, and users within the same group communicate using the RSMA mechanism, where users need to parse the public messages sent by the base station as well as the private messages sent to themselves.
The rate optimization problem for downlink RSMA systems can be described as Equation (1), where
is the number of users in the group
;
is the downlink transmission rate of user
in group
;
is the location of the UAV base station;
,
,
,
,
and
are UAV position restrictions;
is the rate proportion allocated to user j in the public message of the user group
;
is the public message downlink transmission power of the
-th group;
is the bandwidth allocation for each user group;
is the total bandwidth of the system;
is the power allocation for each user group and user member;
is the power limit of the base station; and
is the downlink rate requirement of the corresponding user.
3.2. Model Solving Optimization
Due to the significant complexity of solving a problem directly (1), this paper decomposes it into three sub-problems: UAV position parameter optimization, user group parameter optimization and RSMA parameter optimization, and designs a ternary cross iterative optimization algorithm to complete the original problem solving. By grouping the UAV position as the UAV parameter, the bandwidth allocation as well as the inter-group power allocation in act as the user group resource parameter. The intra-group power allocation in is grouped into RSMA parameters, and the RSMA parameters of the downlink optimization system can still be solved independently for each user group.
Optimizing UAV parameters such as position, altitude, and power is crucial for enhancing communication performance, especially when UAVs are used as flying base stations in areas with limited infrastructure. This improves coverage, reduces interference, and ensures efficient energy use, making it vital for applications like disaster recovery and remote connectivity. The optimization problem regarding the UAV position parameter can be abstracted into the following form:
where
is the opposite number of the sum of downlink transmission rate.
is the location constraint of the UAV.
is the user’s downlink transmission rate constraint. In this case, the user group parameters as well as the RSMA parameters are treated as constants. In Equation (2), the first constraint determines the deployable region of the UAV, i.e., the search space of the solution, and the second constraint is the rate constraint, which corresponds to the rate demand constraint of Equation (1), which are inequality constraints. The Augmented Lagrange Method (ALM) is used in this paper to transform an inequality constrained optimization problem into an unconstrained optimization problem for further solution. We transform the rate requirement constraints of Equation (1) into the forms of Equation (3), then the left-hand side of the inequality is denoted as
. The objective function of (2) is denoted as
, where
is the coordinates of the UAV. According to reference [
10], the augmented Lagrange function of (2) is calculated as (4), where
is the number of user groups,
is the number of users in group
,
is the Lagrange multiplier, and
is the penalty parameter. The Lagrange multiplier is updated by
, where
represents the value of
when the number of iterations reaches
,
represents the upper limit of
, and
represents the value of solution obtained when the number of iterations reaches
. In this paper, we use dynamic penalty function; the penalty parameter
is updated by
, where
is the number of iterations,
is the range of values of
, and
is the maximum number of iterations. As the number of iterations increases, the penalty parameter
also increases.
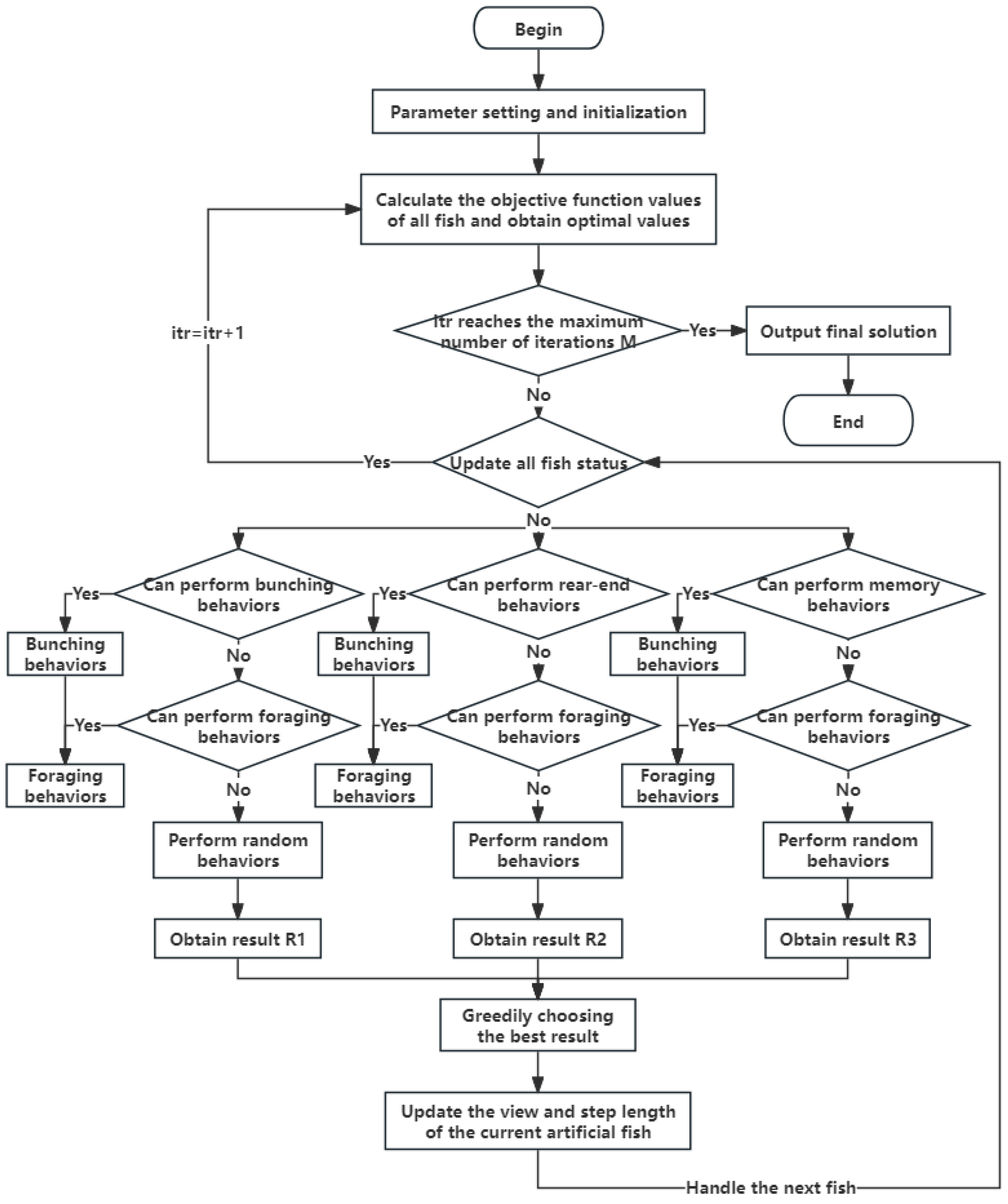
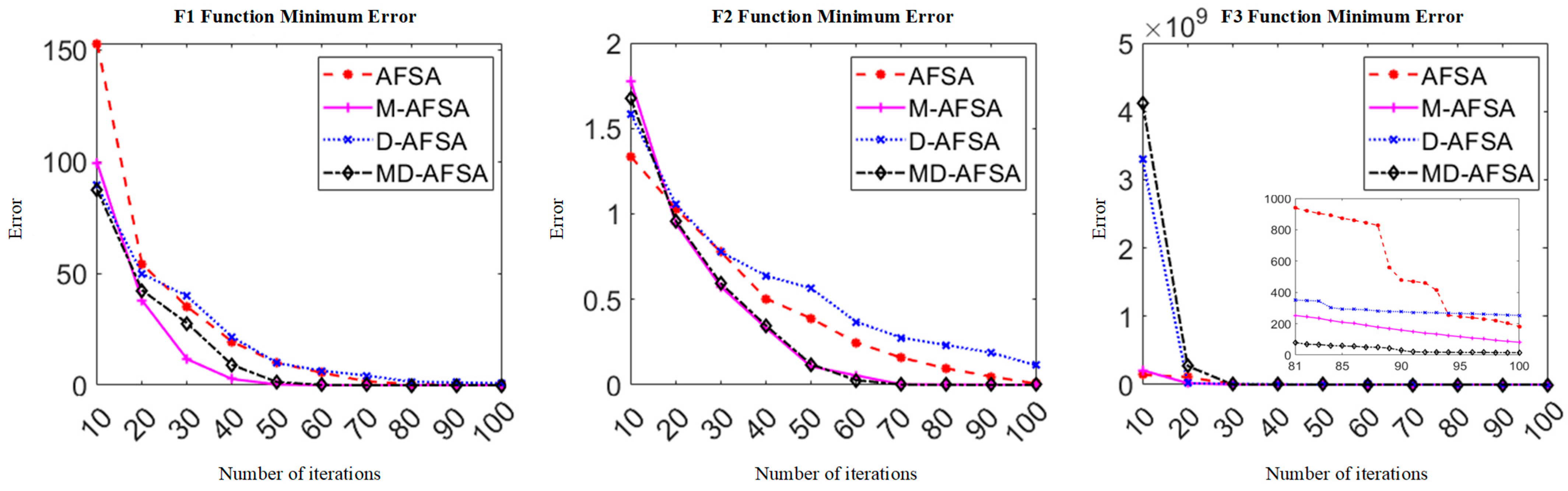
Eventually, the inequality constraint problem (2) is transformed into the unconstrained problem (4), which can be further solved using an unconstrained optimization algorithm. Considering the complexity of the problem and the shortcomings of traditional methods for solving this type of problems [
11], this paper will use a heuristic algorithm to solve the problem and finally designs a dynamic memory fish swarm algorithm, which is described in
Section 3.
Group parameters optimization involves managing resources such as power and bandwidth among multiple users in multicast or broadcast scenarios. It ensures efficient resource utilization, prevents service degradation, and balances power allocation, providing reliable service for all users in dense networks.
Firstly, the problem is abstractly modeled by considering the optimization of the user group parameters of the downlink system, whose optimization parameters include the bandwidth allocation ratio (5) and the power allocation ratio (6) between the groups, and thus the problem can be described as solving for the optimal downlink bandwidth allocation ratio as well as the power allocation ratio
so that the downlink rate and the optimal and satisfy the user’s rate requirements.
where
represents the uplink bandwidth allocated to user group
,
represents the proportion of power shared by the
-th user group.
RSMA optimizes the splitting of user messages, power allocation, and bandwidth distribution to manage interference and enhance network efficiency. It enables better handling of user heterogeneity, improves spectral efficiency, and plays a key role in next-generation networks like 5G and 6G, particularly in UAV-assisted communications.
Consider the optimization of RSMA parameters for the downlink system, which consists of the common message splitting ratio
and the power allocation ratio within the group
. The problem can be described as solving for the optimal
(as in Equation (7)) and
(as in Equation (8)) such that the transmission rate and is maximized while satisfying the user rate requirements.
where
is the number of users in the user group,
represents the rate share of the
-th user in the user group in public messages, and
represents the proportion of power allocated to the
-th message in the group (the total number of messages is the number of users plus one). It can be transformed into a typical linear equation constrained optimization problem with the help of the augmented Lagrange function multiplier method [
23], for which an algorithm is designed in this paper to optimize the solution algorithm of an artificial fish school under the constraints of linear equation, which is realized by adding constraints for each step of the operation of the artificial fish.