Abstract
Elliptic curve cryptography has gained attention due to its strong resilience against current cryptanalysis methods. Inspired by the increasing demand for reliable and secure cryptographic methods, our research investigates the relationship between complex mathematical structures and image encryption. A substitution box (S-box) is the single non-linear component of several well-known security systems. Mordell elliptic curves are used because of their special characteristics and the immense computational capacity of Galois fields. These S-boxes are dynamic, which adds a layer of complexity that raises the encryption process’s security considerably. We suggest an effective technique for creating S-boxes based on a class of elliptic curves over . We demonstrate our approach’s robustness against a range of cryptographic threats through thorough examination, highlighting its practical applicability. The assessment of resistance of the newly generated S-box to common attack methods including linear, differential, and algebraic attacks involves a thorough analysis. This analysis is conducted by quantifying various metrics such as non-linearity, linear approximation, strict avalanche, bit independence, and differential approximation to gauge the S-box’s robustness against these attacks. A recommended method for image encryption involves the use of built-in S-boxes to quickly perform pixel replacement and shuffling. To evaluate the efficiency of the proposed strategy, we employed various tests. The research holds relevance as it can provide alternative guidelines for image encryption, which could have wider consequences for the area of cryptography as a whole. We believe that our findings will contribute to the development of secure communication and data protection, as digital security is becoming increasingly important.
MSC:
94A60; 68P25
1. Introduction
Most individuals frequently want to keep their personal information confidential. There have been several occasions throughout history where it was necessary to keep important information hidden from intruders. In particular, it was still crucial to prevent enemies from intercepting communications between generals or rulers and their troops. In the past, simple strategies were used to obfuscate data. On the other hand, the world became more interconnected as society advanced. Due to the rising demand for electronic services, this resulted in an increasing reliance on electronic systems. It is a generally acknowledged activity to exchange private information online. As a result, the need for advanced techniques of data security has become more and more imperative every day. The basic goal of cryptography is the creation of techniques that guarantee safe communication over the networks. The word “cryptography” is derived from two Greek words: “Kryptos” which refers to something concealed or unrevealed and “graphein” which describes the process of learning or writing. The primary goal of cryptography is often regarded as safeguarding information security. The subjects of computer science, mathematics, communication science, physics, and electrical engineering play a significant role in the development of modern cryptography. Cryptography is useful in many real-world situations like protecting chip-based payment cards, allowing digital currencies, securing computer passwords, and simplifying electronic commerce. An S-box is the nonlinear component of cryptosystems employing block ciphers. These cryptosystems use two kinds of S-boxes, static and dynamic. Static S-boxes are fixed tables with substitution values that do not change during the encryption procedure. Even though they are easy to create and efficient, their fixed nature leaves them open to some kinds of assaults, such as differential cryptanalysis or algebraic attacks. Conversely, dynamic S-boxes provide unpredictability to the substitution procedure. They use functions or algorithms that, depending on certain variables or parameters, dynamically produce the substitution values. By increasing the complexity of the encryption scheme and making it harder for attackers to identify patterns in the substitution process, its security is strengthened.
Strong cryptosystems are also developed using elliptic curves. The most often used strategies for enhancing information security are those based on elliptic curves. We will specifically focus on elliptic curve cryptography (ECC) and the many approaches proposed by many experts in this field. The elliptic curve was initially used as a public key cryptosystem in 1985 by Miller [1]. Additionally, it was shown that the ECC cryptosystem is twenty percent more effective than the Diffie–Hellman algorithm. Koblatiz et al. in [2] presented the concept of a discrete logarithmic issue which is applied to construct a highly secure, quick, and effective security system. An effective method to multiply the elliptic curve points and their resources is provided in [3] and compared with binary and non-adjacent (NAF) forms. It has been found that ECC, which uses a shorter key length than RSA, is more secure overall. In [4], an elliptic curve is used over a prime field to generate elliptic curve points, and then, each point’s x and y coordinates are added. The modulo function is then used to construct various numbers of S-boxes. In [5], a procedure for creating prime field dependent (8 input bits, 8 output bits) S-boxes is described. In this work, the modulo operation is used after the x-coordinate of an elliptic curve to produce the various numbers of S-boxes dependent on the prime field. The authors in [6] presented novel approaches for creating S-boxes utilizing the total order on an elliptic curve (EC) over a prime field. A search method is used to efficiently construct an EC in place of the more traditional group rule, which is computationally expensive. The x-coordinates of the points of the order elliptic curve (OEC) are used in the construction method for the S-boxes. These methods can be used to create various numbers of S-boxes. Although they are independent of the underlying elliptic curve and may or may not generate an S-box for any input value, their result is still unpredictable. A S-box was developed in [7] by using elliptic curves over . Shah et al. in [8] used the Mordell elliptic curves over finite fields with elements 256, 512, 2048. The authors designed three S-boxes with one S-box of nonlinearity 112 and with a very low score of strict avalanche criteria (SAC). The authors concluded that we can obtain good S-boxes over . In this, study, we used the same idea and will show that over , there are extremely good S-boxes as compared to S-boxes produced in [8] in terms of scores of strict avalanche criteria (SAC), bit independence criteria (BIC), linear approximation probability (LAP), and differential approximation probability (DAP) [9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44].
The confidentiality, integrity, and validity of digital images depend on image encryption techniques, which also secure transmission, solve privacy issues, adhere to legal requirements, stop illegal changes, and safeguard intellectual property rights. Feng et al. in [45] developed a new fractional-order 3D Lorenz chaotic system and a 2D sinusoidally constrained polynomial hyper-chaotic map (2D-SCPM). The multi-image encryption technique outperforms several contemporary image encryption algorithms by utilizing multi-channel fusion, chaotic random substitution, dynamic diffusion, and quick scrambling. The authors in [46] used an image encryption method that employs two keys. The first key is generated by a 2D Logistic Sine map and a Linear Congruential Generator, while the second key is generated from the Tent map, the Bernoulli, and the KAA map. The study in [47] presents a Feistel cipher structure-based simplified picture encryption algorithm (SIEA) for picture security in cloud storage that makes use of the key generation and permutation approaches. For digital image encryption, the study [48] suggests ARHM (AES and Rossler Hyperchaotic Modeling) that combines AES with phantom transformation and the Rossler hyperchaotic system. This model conducts simulations and analyses including key space, key sensitivity, histogram, pixel correlation, entropy, and resistance to differential attacks. It makes use of chaotic system randomness and AES encryption speed. Ali et al. proposed an image encryption algorithm based on S-boxes using the direct product of cyclic groups and Galois fields [49]. The authors in [50] used Mobius transformation on a Galois field to generate robust S-boxes and presented a scheme that can protect medical images in a better way. The use of quantum theory in image encryption has been on the rise lately. The Quantum Chaotic Map and DNA Coding-based Image Encryption Algorithm (QCMDC-IEA) is susceptible to assaults on its DNA domain encryption and has intrinsic security weaknesses such as the presence of an equivalent key resulting from independent chaos-based sequences. A suggested technique of attack takes advantage of these flaws to achieve low complexity and full decipherment. The authors presented recommendations for security enhancements in similar cryptosystems to address the discovered weaknesses [51]. An image encryption algorithm utilizing Quantum Logistic and Lorenz Chaotic Map with DNA Coding, claims enhanced security, but a proposed chosen-plaintext attack exposes vulnerabilities in its permutation and diffusion key. Suggestions for improvement are offered to bolster the algorithm’s security and practicality in cryptographic design [52].
It is evident from the literature that there is a dire need to design robust S-boxes using algebraic structures to enhance the security of cryptosystems. The elliptic curves and Galois fields are used separately in the literature for designing image encryption schemes and S-boxes. The elliptic curves provide greater security due to the short key length, and its usage along with the Galois field can improve the strength of cryptosystems. The following are the motivations for the proposed work:
- The elliptic curves provide great resistance against linear and differential cryptanalysis due to their nonlinear nature.
- Compact S-box designs can be achieved by representing elliptic curves with smaller key sizes than conventional mathematical structures. In terms of efficiency, this can be helpful, particularly in settings with few resources.
- Hardware and software may both effectively implement elliptic curve operations. For real-world applications, such as embedded systems or gadgets with constrained processing power, this efficiency is essential.
- A further degree of protection is provided by the mathematical hardness of elliptic curve problems like the elliptic curve discrete logarithm problem. The cryptographic strength of elliptic curve-based designs is predicated on the difficulty of solving these complex mathematical problems.
- Due to the strong properties of elliptic curves and a highly nonlinear permutation of the Galois field, the proposed strategy for S-boxes and encryption has a greater ability to resist cryptanalysis.
The contributions of the proposed scheme are as follows.
- The generated S-boxes have nonlinearity greater than 105 with four optimal boxes of nonlinearity 112.
- As the degree of irreducible polynomials increases, the number of irreducible polynomials increases quickly, and we can produce millions of S-boxes with the proposed work in a short time.
- The entropy of the proposed cipher image is close to 8, confirming the efficacy of the effectiveness of the method.
2. Preliminaries
In this section, we will present some basic definitions related to the Galois field and elliptic curves.
2.1. Irreducible Polynomial
If is a field, then a polynomial is called irreducible in whenever for , then either or is a constant polynomial.
2.2. Maximal Ideal
Let M be an ideal of R and , then M is called maximal if no proper ideal of R contains M.
2.3. Galois Field
For a prime number p and for an irreducible polynomial of degree m in , the quotient ring is a finite field of order called Galois field and denoted by , where t is a particular root of .
2.4. Elliptic Curve
Consider the field with for some prime p and natural number n, then the elliptic curve over F is defined as
where the point O is called the infinite point. This form is known as the Weierstrass form of an elliptic curve.
If char and , then is known as Edward’s elliptic curve.
If and , then the curve is known as the Montgomery form of an elliptic curve.
2.5. Mordell Elliptic Curve
The elliptic curve with is called a Mordell elliptic curve. If , then there is randomness and distinctness in y-coordinates of points satisfying the elliptic curve.
3. Proposed Algorithm for the Construction of S-boxes
We used the x and y coordinates of points satisfying a Mordell elliptic curve that is interpreted over employing different irreducible polynomials of degree n.
3.1. S-Boxes Using Mordell Elliptic Curve over
An elliptic curve of the form is called a Mordell elliptic curve. The number of points satisfying the curve other than infinity is exactly , so we can use them to construct S-boxes. As there is no repetition in x-coordinates of point , by defining a bijective map, we can obtain an S-box. We call an S-box-m the S-box generated by using an irreducible polynomial with decimal value m. The algorithm is described as follows.
- (1)
- Choose any irreducible polynomial of degree over the binary field.
- (2)
- Choose the Mordell elliptic curve .
- (3)
- Choose x-coordinates of points satisfying the Mordell curve.
- (4)
- Apply the multiplicative inverse of each non-zero element corresponding to a given irreducible polynomial.
- (5)
- For , apply modulo 256 and choose the 1st 256 unique values.
- (6)
- Reshape into matrix.
All 10 S-boxes are presented in Table 1, Table 2, Table 3, Table 4, Table 5, Table 6, Table 7, Table 8, Table 9 and Table 10. The table of comparison shows that S-boxes produced using these polynomials are better than the S-boxes designed in [8] in terms of scores of SAC, BIC SAC, LAP, and DAP.

Table 1.
S-box-283.

Table 2.
S-box-299.

Table 3.
S-box-505.

Table 4.
S-box-313.

Table 5.
S-box-529.

Table 6.
S-box-787.

Table 7.
S-box-1315.

Table 8.
S-box-1789.

Table 9.
S-box-3441.

Table 10.
S-box-7105.
3.2. S-Boxes Using Mordell Elliptic Curves over
Since 512, 2048 , the curve over has exactly points in such a way that there is no repetition in x and y-coordinates with random values in y-coordinates. The proposed algorithm for the S-box is described as follows.
- (1)
- Choose any irreducible polynomial of degree over the binary field.
- (2)
- Choose the Mordell elliptic curve .
- (3)
- Choose y-coordinates of points satisfying the Mordell curve.
- (4)
- Apply modulo 256 on y-coordinates to obtain answers in 0–255.
- (5)
- Select the 1st 256 unique values.
- (6)
- Reshape into a matrix.
4. Security Analysis of S-Boxes
This segment discusses the outcomes of security evaluations conducted on the proposed S-boxes to evaluate their resistance to cryptographic attacks. The S-box was evaluated through five different tests including Nonlinearity, Strict Avalanche Criteria (SAC), Bit Independence Criteria (BIC), Probability of Linear Approximation (LAP), and Probability of Differential Approximation (DAP). The results were compared to some popular S-boxes in Table 11.

Table 11.
Algebraic analysis of proposed and some well-known S-boxes.
4.1. Nonlinearity (NL)
The nonlinearity of a boolean function g is one of the most desirable characteristics of a strong S-box. It is defined as , where represents the Walsh spectrum of the polarity truth table of the boolean function g, and n is the number of input bits. The nonlinearity of a boolean function measures its difference from a set of all affine functions of n variables. We can calculate the Walsh spectrum in the following way; Walsh spectrum = Hadamard matrix of order [polarity truth table of f].
4.2. Strict Avalanche Criteria (SAC)
To assess the cryptographic potency of substitution boxes (S-boxes) used in symmetric key algorithms, one property is known as strict avalanche criteria (SAC). A minor change in the input causes substantial changes in the output when using SAC, which quantifies how much changing a single bit of an S-box’s input impacts the output bits. The output bits of the S-box should change with a probability of 0.5 for each output bit when any one of its input bits is reversed. If all potential input bit changes are averaged, the amount of 0s and 1s in the output bits should be equal. By doing this, it is made sure that no particular output value is preferred by the S-box. Ideally, if k input bits are modified, at least output bits should also change. This characteristic makes sure that a minor change in the input spreads and results in a significant change in the result. A boolean function f satisfies the SAC if for every vector a of hamming weight 1, the function is balanced.
4.3. Bit Independence Criteria (BIC)
Let and be two-bit outputs of an S-box; if is highly nonlinear and satisfies the strict avalanche criteria, then S-box satisfies BIC. The bit independence criteria assesses the correlation between the input bits and the output bits of an S-box. An S-box should exhibit a high degree of bit independence, which means that the output bits should have as little correlation as possible with the input bits.
4.4. Linear Approximation Probability (LAP)
The probability of linear approximation for an S-box is the likelihood that its inputs will approach its outputs linearly given a certain number of input–output pairs. A weaker S-box would have a higher linear approximation probability because it would be more susceptible to linear attacks. On the other side, a smaller linear approximation probability indicates a stronger S-box. Due to this, the S-box exhibits greater resilience against linear attacks. The following formula can be used to calculate the linear approximation probability
considering to be the input and output masks, respectively.
4.5. Differential Approximation Probability (DP)
The differential approximation probability for an S-box quantifies the probability that a particular input difference will result in a particular output difference, taking into account a specified number of rounds. It quantifies the probability of a particular differential characteristic occurring within the S-box. To calculate the differential approximation probability, one typically performs an exhaustive search over all possible input and output differences for a given number of rounds, counting the occurrences of each difference and calculating the probability as the ratio of the occurrences of the desired difference to the total number of input/output pairs tested. The lower the differential approximation probability, the more resistant the S-box is against differential cryptanalysis. A lower probability indicates that the S-box does not exhibit any strong differentials, making it more difficult for an attacker to exploit differential characteristics and break the cipher.
where is the input, and is the output differential.
4.6. Discussion
- Large nonlinearity is required for the S-box to fend off linear attacks. Table 11 shows that there are four S-boxes with optimal nonlinearity, while the remaining also have considerable scores.
- The strict avalanche criterion is deemed to be met rather effectively by the SAC score that is close to the optimal value of 0.50. Table 11 shows that, in comparison to most recently created S-boxes with the avalanche effect, our best SAC score of is quite near to the ideal value. As a result, the suggested S-box successfully satisfies the strict avalanche criteria.
- Under the bits independence requirement, the pair-wise disjoint boolean functions have demonstrated strong performance for both SAC and nonlinearity scores. Each of our proposed S-boxes has a sound score of nonlinearity and SAC.
- A lower DU score is indicative of a secure S-box. Among all generated S-boxes, none of the S-boxes has a score of DU greater than 10.
- The resistance of the S-box against linear cryptanalysis is likewise correlated with the likelihood of linear approximation. It is claimed that an S-box with a lower LAP score is more resistant to linear cryptanalysis. The LP values of our S-boxes are lower than many of the proposed S-boxes as shown in Table 11.
5. Image Encryption
In this section, we will examine an innovative approach for protecting digital images that makes use of a specially designed S-box. Our analysis included several distinct tests designed to assess the durability and effectiveness of our picture encryption approach while also testing its resistance to prospective attacks. After a thorough evaluation and analysis of our process, we compared the outcomes to those attained using well-known encryption methods. The results of our study showed that the suggested method for encrypting digital images performed the best overall. All the codings were completed in MATLAB R2023a using the CBC mode of AES with a random key of 256 bits. Figure 1a–k represents the plain and cipher image of a baboon, while Table 12 is the comparison of image encryption schemes.
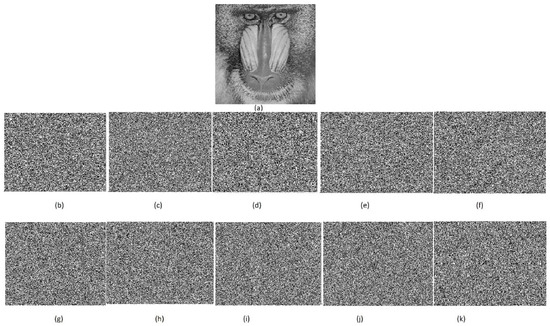
Figure 1.
Plain image and cipher images using proposed S-boxes.

Table 12.
Results of majority logic criteria and differential analysis of image encryption scheme.
5.1. Entropy
Entropy is a metric that quantifies the degree of unpredictability or disorganization in the pixel values of an image. By utilizing Shannon’s entropy formula, which factors in the probability distribution of diverse pixel values present in the image, one can determine the entropy of an image. If all 256-pixel values within an 8-bit grayscale image occur with equal probability, then the image’s entropy value reaches its maximum possible value of 8. Scrambled illustrations with an entropy value that is near 8 have pixel values that are spread out as uniformly as possible. Therefore, it becomes difficult to predict the original image from the scrambled image.
where represents the probability of a pixel.
A strong image encryption scheme must have an entropy score close to 8.
5.2. Correlation
One method for evaluating the similarity between a filter and the corresponding pixels in an image is called correlation, which involves convolving the filter over the image using a mathematical operation. A way to assess the robustness of the confidentiality protocol is to examine the correlation between the original image and the scrambled image. A desirable property of an image encryption system is that the correlation statistic value amidst the original and scrambled images should be as close to 0 as possible. In practical image encryption scenarios, a correlation coefficient value approaching zero is considered ideal. A correlation coefficient value below 0.1 is generally considered a strong indicator of a high-quality encryption scheme. However, if the correlation coefficient value exceeds 0.1, it implies the existence of a weak encryption scheme with a risk of unveiling the original image from the scrambled image.
where and represent the means of their respective variables.
5.3. Contrast
The difference in brightness or intensity between various areas of an encrypted image is referred to as contrast in a cipher image. It specifies how distinct the dark and bright parts appear in the cipher image. Contrast is important for picture encryption because it influences the visual appeal and readability of the encrypted image. A stronger contrast indicates that there is a notable difference in brightness or intensity between various areas of the encrypted image. A high-contrast cipher image offers several advantages in an encryption scheme:
- (1)
- Enhanced Security: Higher contrast can make it more challenging for attackers to analyze or extract meaningful information from the cipher image. Well-defined edges and distinct intensity variations can make it harder to detect patterns or identify specific features within the image.
- (2)
- Robustness Against Attacks: A cipher image with higher contrast can exhibit greater resilience against common attacks, such as statistical analysis, pixel correlation, or known-plaintext attacks. The increased variability in intensity levels can make it more difficult to exploit statistical regularities and effectively break the encryption.
- (3)
- Improved Visual Quality: Although the primary goal of image encryption is security, maintaining a visually appealing and interpretable cipher image is also desirable. Higher contrast often leads to a more visually striking encrypted image, which may enhance the user experience and the overall acceptance of the encryption scheme.
5.4. Homogeneity
The degree of uniformity or unpredictability of the cipher image created during the encryption process is referred to as homogeneity. In a homogeneous cipher image, each pixel value would be distinct from its surrounding pixels and the initial image’s general structure, exhibiting a high degree of randomness. On a scale from 0 to 1, the measure of homogeneity ranges from high heterogeneity or variety to high homogeneity or uniformity.
where M is the number of gray levels in the image, and represents the position of a pixel in the GLCM.
5.5. Energy
Energy quantifies the overall contrast or level of activity in an image, and it is computed by summing the squared elements in the Gray-Level Co-occurrence Matrix (GLCM). A higher energy value indicates that the image contains more texture and contrast, while a lower energy value signifies a more homogeneous or uniform appearance.
5.6. Number of Pixel Change Rate (NPCR)
The percentage of pixels between two dissimilar images is measured using this metric. NPCR examines the impact of a single-pixel alteration on the entire image encrypted using the suggested approach. It counts how many pixels in an encrypted image change every time a pixel in the original image changes. Consider two encrypted images C1 and C2 with dimensions M and N, corresponding to two plain images that have a one-pixel change. We can measure NPCR as
where .
5.7. Unified Average Changing Intensity (UACI)
The average intensity of the variations between the encrypted image and the original image is measured by the Unified Average Changing Intensity (UACI). We can measure UACI with the formula
whereas are defined in NPCR.
5.8. Noise Attack Analysis
Even with noise from salt and pepper, the encryption approach should guarantee that the image’s actual content is kept private. Significant information about the underlying image content should not be revealed by the noise. The encryption plan might be made to adjust to different noise levels. Because of its versatility, the scheme can withstand variations in noise levels or types without losing its effectiveness. We used salt and pepper noise with different intensity levels to check the effectiveness of the proposed image encryption scheme. We can observe that the PSNR values are still greater than 30 after adding noise in the image (see Table 13). Figure 2 shows the results of the noise attack with an intensity of , respectively.

Table 13.
Noise attack analysis.
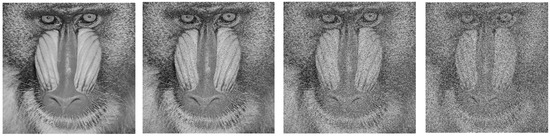
Figure 2.
Salt and pepper noise attack on baboon with intensity of 0.1, 0.3, 0.5.
6. Conclusions and Future Study
Robust cryptographic solutions are extremely important as the digital landscape continues to change. Our study explores the complex field of image encryption, utilizing the strong characteristics of elliptic curve cryptography to improve security protocols. This paper utilizes the intricate configuration of elliptic curves within the binary Galois field extension to establish an effective approach for constructing S-boxes. There are a lot of existing schemes for designing S-boxes using the prime field, but we used . We compared our results with existing schemes on prime fields and . We concluded that for , the produced S-boxes are relatively weak as compared to the usage of . Our conclusion contradicts the conclusion of [8] by producing a large number of S-boxes using and . Our thorough analysis, which included measures, such as bit independence, strict avalanche, non-linearity, linear approximation, and differential approximation, highlighted the robustness of our suggested approach. Furthermore, we have employed S-boxes in the substitution process, yielding significantly superior results compared to various alternative methods. We demonstrated the effectiveness and efficiency of our method through extensive testing, providing a viable substitute for strengthening digital security protocols. Our research has the potential to advance data security and secure communication paradigms and advance the field of cryptography as a whole. Going ahead, our study offers insightful advice and suggestions for creating robust encryption systems, which are essential for protecting sensitive data in a world getting more digitally connected. In the future, we are interested in using some more elliptic and hyperelliptic curves over to design robust S-boxes.
Author Contributions
The material is the result of joint efforts of A.S.A., R.A., M.K.J., J.A. and G. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The findings of this study are not supported by any data.
Acknowledgments
The authors extend their appreciation to Princess Nourah Bint Abdulrahman University for funding this research under Researchers Supporting Project number (PNURSP2024R231), Princess Nourah Bint Abdulrahman University, Riyadh, Saudi Arabia.
Conflicts of Interest
There are no perceived biases due to personal affiliations among the authors.
References
- Miller, V.S. Use of elliptic curves in cryptography. In Proceedings of the Conference on the Theory and Application of Cryptographic Techniques, Santa Barbara, CA, USA, 18–22 August 1985; pp. 417–426. [Google Scholar]
- Koblitz, N.; Menezes, A.; Vanstone, S. The state of elliptic curve cryptography. Des. Codes Cryptogr. 2000, 19, 173–193. [Google Scholar] [CrossRef]
- Kodali, R.K.; Patel, K.H.; Sarma, N. Energy efficient elliptic curve point multiplication for WSN applications. In Proceedings of the 2013 National Conference on Communications (NCC), New Delhi, India, 15–17 February 2013; pp. 1–5. [Google Scholar]
- Khalid, I.; Jamal, S.S.; Shah, T.; Shah, D.; Hazzazi, M.M. A novel scheme of image encryption based on elliptic curves isomorphism and substitution boxes. IEEE Access 2021, 9, 77798–77810. [Google Scholar] [CrossRef]
- Hayat, U.; Azam, N.A.; Asif, M. A method of generating 8 × 8 substitution boxes based on elliptic curves. Wirel. Pers. Commun. 2018, 101, 439–451. [Google Scholar] [CrossRef]
- Hayat, U.; Azam, N.A. A novel image encryption scheme based on an elliptic curve. Signal Process. 2019, 155, 391–402. [Google Scholar] [CrossRef]
- Farwa, S.; Sohail, A.; Muhammad, N. A novel application of elliptic curves in the dynamical components of block ciphers. Wirel. Pers. Commun. 2020, 115, 1309–1316. [Google Scholar] [CrossRef]
- Shah, T.; Aljaedi, A.; Hazzazi, M.M.; Alharbi, A.R. Design of Nonlinear Components Over a Mordell Elliptic Curve on Galois Fields. Comput. Mater. Contin. 2022, 71, 1313–1329. [Google Scholar]
- Razaq, A.; Yousaf, A.; Shuaib, U.; Siddiqui, N.; Ullah, A.; Waheed, A. A novel construction of substitution box involving coset diagram and a bijective map. Secur. Commun. Netw. 2017, 2017, 5101934. [Google Scholar] [CrossRef]
- Cheon, J.H.; Chee, S.; Park, C. S-boxes with controllable nonlinearity. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, EUROCRYPT ’99, Prague, Czech Republiic, 2–6 May 1999; pp. 286–294. [Google Scholar]
- Asghari, P.; Javadi, S.H.H.S. Lightweight Key-Dependent Dynamic S-Boxes based on Hyperelliptic Curve for IoT Devices. arXiv 2021, arXiv:2102.13340. [Google Scholar]
- Massey, J.; Lai, X. International Data Encryption Algorithm; Eidgenossische Technique Hoehschule (ETH): Zurich, Switzerland, 1991. [Google Scholar]
- Joan, D.; Vincent, R. The Design of Rijndael: AES—The Advanced Encryption Standard; Springer: Berlin/Heidelberg, Germany, 2002. [Google Scholar]
- Shannon, C.E. Communication theory of secrecy systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Gan, Z.; Chai, X.; Yuan, K.; Lu, Y. A novel image encryption algorithm based on LFT based S-boxes and chaos. Multimed. Tools Appl. 2018, 77, 8759–8783. [Google Scholar] [CrossRef]
- Hussain, I.; Shah, T.; Gondal, M.A.; Khan, W.A.; Mahmood, H. A group theoretic approach to construct cryptographically strong substitution boxes. Neural Comput. Appl. 2013, 23, 97–104. [Google Scholar] [CrossRef]
- Hussain, I.; Shah, T.; Gondal, M.A.; Khan, M.; Khan, W.A. Construction of new S-box using a linear fractional transformation. World Appl. Sci. J. 2011, 14, 1779–1785. [Google Scholar]
- Younas, I.; Khan, M. A new efficient digital image encryption based on inverse left almost semi group and Lorenz chaotic system. Entropy 2018, 20, 913. [Google Scholar] [CrossRef]
- Razaq, A.; Al-Olayan, H.A.; Ullah, A.; Riaz, A.; Waheed, A. A Novel Technique for the Construction of Safe Substitution Boxes Based on Cyclic and Symmetric Groups. Secur. Commun. Netw. 2018, 2018, 4987021. [Google Scholar] [CrossRef]
- Hussain, I.; Shah, T.; Gondal, M.A.; Mahmood, H. An efficient approach for the construction of LFT S-boxes using chaotic logistic map. Nonlinear Dyn. 2013, 71, 133–140. [Google Scholar] [CrossRef]
- Siddiqui, N.; Afsar, U.; Shah, T.; Qureshi, A. A Novel Construction of S16 AES S-boxes. Int. J. Comput. Sci. Inf. Secur. (IJCSIS) 2016, 14, 810–818. [Google Scholar]
- Mahmood, S.; Farwa, S.; Rafiq, M.; Riaz, S.M.J.; Shah, T.; Jamal, S.S. To study the effect of the generating polynomial on the quality of nonlinear components in block ciphers. Secur. Commun. Netw. 2018, 2018, 5823230. [Google Scholar] [CrossRef]
- Attaullah; Jamal, S.S.; Shah, T. A Novel Algebraic Technique for the Construction of Strong Substitution Box. Wirel. Pers. Commun. 2018, 99, 213–226. [Google Scholar] [CrossRef]
- Naseer, Y.; Shah, T.; Shah, D.; Hussain, S. A novel algorithm of constructing highly nonlinear Sp-boxes. Cryptography 2019, 3, 6. [Google Scholar] [CrossRef]
- Zhang, T.; Chen, C.P.; Chen, L.; Xu, X.; Hu, B. Design of highly nonlinear substitution boxes based on I-Ching operators. IEEE Trans. Cybern. 2018, 48, 3349–3358. [Google Scholar] [CrossRef]
- Zahid, A.H.; Arshad, M.J.; Ahmad, M. A novel construction of efficient substitution-boxes using cubic fractional transformation. Entropy 2019, 21, 245. [Google Scholar] [CrossRef]
- Bin Faheem, Z.; Ali, A.; Khan, M.A.; Ul-Haq, M.E.; Ahmad, W. Highly dispersive substitution box (S-box) design using chaos. ETRI J. 2020, 42, 619–632. [Google Scholar] [CrossRef]
- Shahzad, I.; Mushtaq, Q.; Razaq, A. Construction of new S-box using action of quotient of the modular group for multimedia security. Secur. Commun. Netw. 2019, 2019, 2847801. [Google Scholar] [CrossRef]
- Tian, Y.; Lu, Z. Chaotic S-box: Intertwining logistic map and bacterial foraging optimization. Math. Probl. Eng. 2017, 2017, 6969312. [Google Scholar] [CrossRef]
- Biham, E.; Shamir, A. Differential cryptanalysis of DES-like cryptosystems. J. Cryptol. 1991, 4, 3–72. [Google Scholar] [CrossRef]
- Yucel, M.; Vergili, I. Avalanche and Bit Independence Properties for the Ensembles of Randomly Chosen nxn S-boxes. Turk. J. Electr. Eng. Comput. Sci. 2001, 9, 3. [Google Scholar]
- Seberry, J.; Zhang, X.M.; Zheng, Y. Systematic generation of cryptographically robust S-boxes. In Proceedings of the 1st ACM Conference on Computer and Communications Security, Fairfax, VA, USA, 3–5 August 1993; pp. 171–182. [Google Scholar]
- Cipher, D. Linear Cryptanalysis Method for. In Proceedings of the Advances in Cryptology–EUROCRYPT’93: Workshop on the Theory and Application of Cryptographic Techniques, Lofthus, Norway, 23–27 May 1993; Springer: Berlin/Heidelberg, Germany, 2003; Volume 765, p. 386. [Google Scholar]
- Pieprzyk, J.; Finkelstein, G. Towards effective nonlinear cryptosystem design. IEE Proc.-Comput. Digit. Tech. 1988, 135, 325–335. [Google Scholar] [CrossRef]
- Webster, A.F.; Tavares, S.E. On the design of S-boxes. In Proceedings of the Conference on the Theory and Application of Cryptographic Techniques, CRYPTO’85, Santa Barbara, CA, USA, 18–22 August 1985; pp. 523–534. [Google Scholar]
- Lu, Q.; Zhu, C.; Deng, X. An efficient image encryption scheme based on the LSS chaotic map and single S-box. IEEE Access 2020, 8, 25664–25678. [Google Scholar] [CrossRef]
- Alzaidi, A.A.; Ahmad, M.; Doja, M.N.; Al Solami, E.; Beg, M.S. A new 1D chaotic map and β-hill climbing for generating substitution-boxes. IEEE Access 2018, 6, 55405–55418. [Google Scholar] [CrossRef]
- Yong, W.; Peng, L. An improved method to obtaining S-box based on chaos and genetic algorithm. HKIE Trans. 2012, 19, 53–58. [Google Scholar] [CrossRef]
- Lambić, D. A novel method of S-box design based on chaotic map and composition method. Chaos Solitons Fractals 2014, 58, 16–21. [Google Scholar] [CrossRef]
- Nizam Chew, L.C.; Ismail, E.S. S-box construction based on linear fractional transformation and permutation function. Symmetry 2020, 12, 826. [Google Scholar] [CrossRef]
- Arshad, B.; Siddiqui, N. Construction of highly nonlinear substitution boxes (S-boxes) based on connected regular graphs. Int. J. Comput. Sci. Inf. Secur. (IJCSIS) 2020, 18, 105–122. [Google Scholar]
- Siddiqui, N.; Yousaf, F.; Murtaza, F.; Ehatisham-ul Haq, M.; Ashraf, M.U.; Alghamdi, A.M.; Alfakeeh, A.S. A highly nonlinear substitution-box (S-box) design using action of modular group on a projective line over a finite field. PLoS ONE 2020, 15, e0241890. [Google Scholar] [CrossRef] [PubMed]
- Pali, I.A.; Soomro, M.A.; Memon, M.; Maitlo, A.A.; Dehraj, S.; Umrani, N.A. Construction of an s-box using suppersingular elliptic curve over finite field. J. Hunan Univ. Nat. Sci. 2023, 50. [Google Scholar] [CrossRef]
- Razaq, A.; Ahmad, M.; El-Latif, A.A.A. A novel algebraic construction of strong S-boxes over double GF (27) structures and image protection. Comput. Appl. Math. 2023, 42, 90. [Google Scholar] [CrossRef]
- Feng, W.; Wang, Q.; Liu, H.; Ren, Y.; Zhang, J.; Zhang, S.; Qian, K.; Wen, H. Exploiting newly designed fractional-order 3D Lorenz chaotic system and 2D discrete polynomial hyper-chaotic map for high-performance multi-image encryption. Fractal Fract. 2023, 7, 887. [Google Scholar] [CrossRef]
- Alexan, W.; Elkandoz, M.; Mashaly, M.; Azab, E.; Aboshousha, A. Color image encryption through chaos and kaa map. IEEE Access 2023, 11, 11541–11554. [Google Scholar] [CrossRef]
- Lavanya, M.; Sundar, K.; Saravanan, S. Simplified Image Encryption Algorithm (SIEA) to enhance image security in cloud storage. Multimed. Tools Appl. 2024, 1–33. [Google Scholar] [CrossRef]
- Yi, G.; Cao, Z. An Algorithm of Image Encryption based on AES & Rossler Hyperchaotic Modeling. Mob. Netw. Appl. 2023, 1–9. [Google Scholar] [CrossRef]
- Ali, R.; Jamil, M.K.; Alali, A.S.; Ali, J.; Afzal, G. A robust S box design using cyclic groups and image encryption. IEEE Access 2023, 11, 135880–135890. [Google Scholar] [CrossRef]
- Ali, J.; Jamil, M.K.; Alali, A.S.; Ali, R.; Guiraiz. A medical image encryption scheme based on Mobius transformation and Galois field. Heliyon 2024, 10, e23652. [Google Scholar] [CrossRef] [PubMed]
- Wen, H.; Lin, Y. Cryptanalysis of an image encryption algorithm using quantum chaotic map and DNA coding. Expert Syst. Appl. 2024, 237, 121514. [Google Scholar] [CrossRef]
- Chen, X.; Yu, S.; Wang, Q.; Guyeux, C.; Wang, M. On the cryptanalysis of an image encryption algorithm with quantum chaotic map and DNA coding. Multimed. Tools Appl. 2023, 82, 42717–42737. [Google Scholar] [CrossRef]
- Hussain, I.; Shah, T.; Mahmood, H.; Gondal, M.A. A projective general linear group based algorithm for the construction of substitution box for block ciphers. Neural Comput. Appl. 2013, 22, 1085–1093. [Google Scholar] [CrossRef]
- Murtaza, G.; Azam, N.A.; Hayat, U. Designing an efficient and highly dynamic substitution-box generator for block ciphers based on finite elliptic curves. Secur. Commun. Netw. 2021, 2021, 3367521. [Google Scholar] [CrossRef]
- Khan, M.; Shah, T.; Mahmood, H.; Gondal, M.A.; Hussain, I. A novel technique for the construction of strong S-boxes based on chaotic Lorenz systems. Nonlinear Dyn. 2012, 70, 2303–2311. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).