We conduct various security analyses such as informal security, BAN logic, ROR model, and AVISPA simulation tool. Specific details regarding the proof process for each analysis are elaborated in the section below.
7.1. Informal Security Analysis
We perform an informal analysis to demonstrate that our scheme can prevent various attacks, such as insider, OBU captured, privileged insider, offline password guessing, vehicle impersonation, ESL, MitM, forgery, desynchronization, and replay attacks. Additionally, we show that our scheme provides anonymity, conditional privacy, mutual authentication, and perfect forward secrecy.
7.1.1. Insider Attack
If an adversary is a legitimate insider, can authenticate RSUs and the TA. In Sibahee et al.’s scheme, an RSU communicates with the TA using the constant parameter . However, our scheme uses timestamps , and with the parameters to change with each session. This approach protects each session individually and prevents from computing the secret parameter.
7.1.2. OBU Captured Attack
According to
Section 3.1,
can capture an OBU of the legitimate vehicle
and obtain parameters
from the OBU’s memory. However, without knowing the vehicle’s
and
,
cannot calculate the secret parameter
, which is shared between
and the TA. Therefore, our scheme is secure against OBU captured attacks.
7.1.3. Privileged Insider Attack
If is a privileged insider and intercepts the legal vehicle’s registration message , the next goal is that tries to compute a session key . To derive and , needs to know the secret parameter , which is shared with the TA. cannot compute without correctly guessing both and . Consequently, the proposed scheme can defend against privileged insider attacks.
7.1.4. Offline Password Guessing Attack
We assume that can extract stored parameters from . In the proposed scheme, the password is only used in parameters and and is encrypted by a hash function. Since must correctly obtain both and a, cannot guess the .
7.1.5. Identity-Guessing Attack
According to
Section 6.1, the real identity
is only known to
and the TA. After receiving
, the TA derives
, where
and
are the secret parameters that only the TA knows. During the login and authentication phases, the exchanged messages never directly include
. Here,
,
,
,
. For similar explanations in
Section 7.1.4, the proposed scheme has resistance to identity-guessing attacks.
7.1.6. Vehicle Impersonation Attack
Suppose that
attempts to impersonate a legitimate vehicle.
tries to construct the authentication request message
. However,
cannot compute
and
. Based on
Section 7.1.4 and
Section 7.1.5,
cannot derive the parameters
and
x used for authentication, and hence, this attack fails.
7.1.7. ESL Attack
Assume that obtains random nonces , and and tries to compute the session key . In spite of the leakage of all random nonces in a session, the security of is still preserved. This is because the parameter x is derived using either and of , or the master key . Specifically, x is computed as or . Similarly, the computation of requires the parameter , which is only shared between and the TA. Here, . For these reasons, the proposed scheme is secure against ESL attacks.
7.1.8. MitM Attack
can intercept exchanged messages via an open channel. The next goal is to modify the login request message . Although obtains from the message, still needs to compute , which is used to calculate and . The TA can easily detect a tampered because is derived from the parameter related to , which is stored in the secure database of TA. In addition, modifying all messages is impossible because they include random parameters that change with each session. Similarly, it is difficult to modify the message sent from the to the TA, as the parameters are masked with the shared secret key between and the TA. Accordingly, these messages are unavailable to , preventing the implementation of MitM attacks. Therefore, the proposed scheme is resistant to MitM attacks.
7.1.9. Forgery Attack
We assume that
tries to forge authentication messages such as
,
, and
. According to
Section 7.1.8,
cannot obtain the secret keys
to forge these messages. In addition, it is difficult for
to validate using forged messages because all random nonces and secret parameters are required to compute
, and
for validation. These parameters are secure and protected by their hash value. Without correctly guessing all at once, it is impossible to forge the messages. Thus,
cannot forge valid authentication messages.
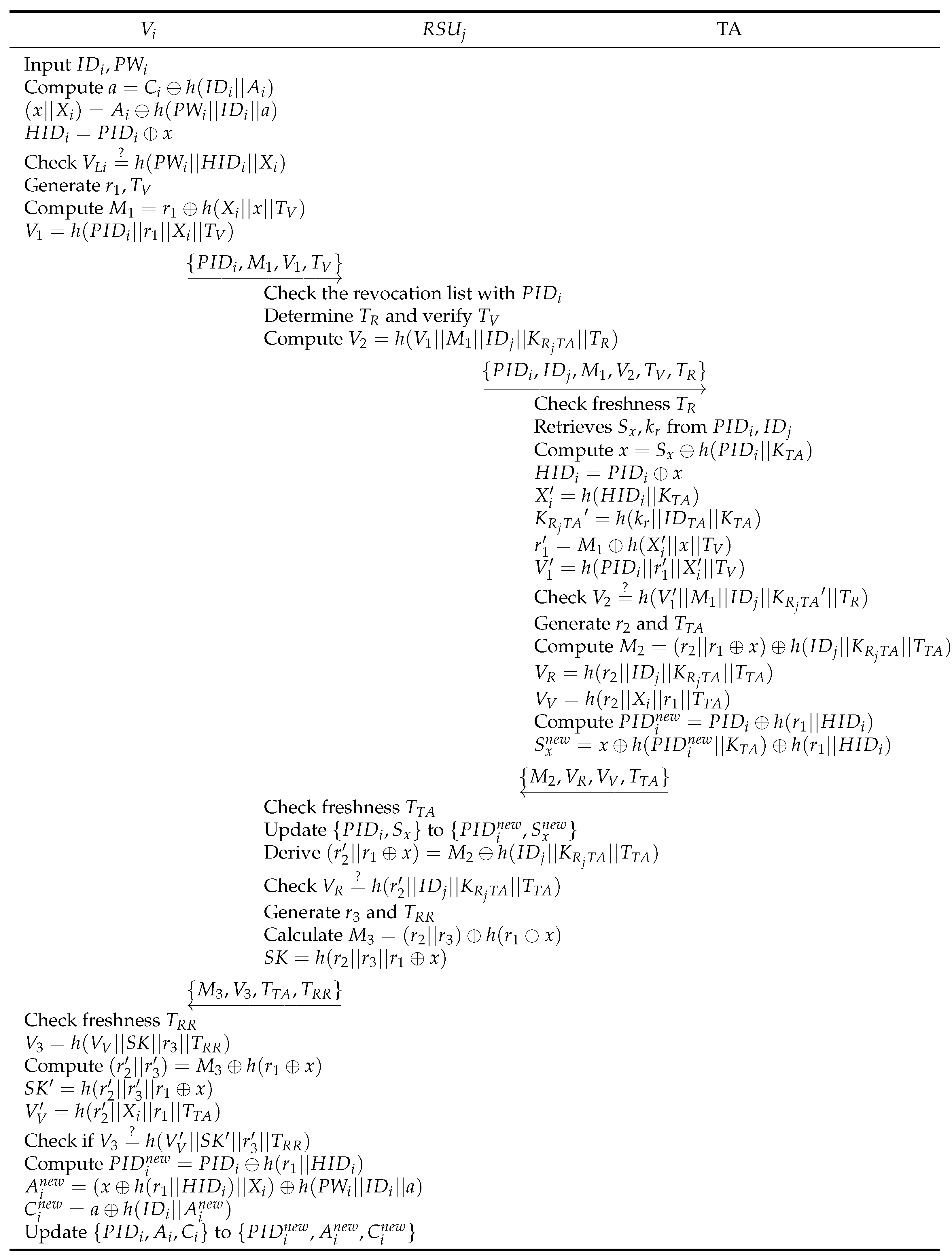
7.1.10. Desynchronization Attack
In each session, the TA and
update
and related parameters,
,
and
. This update is confirmed only after the authentication phase is successfully completed. There is no need to transmit the new parameter
from the TA to
. According to
Section 6.1, the TA derives
and verifies whether the received message is legitimate. After
and
establish the correct session key
, the TA and
update
and other parameters, respectively. If the authentication is terminated, they do not update parameters until the synchronization is successful. In conclusion, the proposed scheme can resist desynchronization issues with pseudo-identity.
7.1.11. Replay Attack
In our scheme, all exchanged messages include timestamps and random nonces that are changed every session. If obtains messages and on a public channel, may try to process authentication by resending previous messages. However, cannot obtain the messages at the previous session because it fails to check the freshness of random nonces , and , and timestamps , and . Therefore, the proposed scheme is secure against replay attacks.
7.1.12. DoS Attack
To make TA unusable,
can continuously attempt to issue fake request messages. However, according to
Section 7.1.4 and
Section 7.1.5,
has failed login attempts without knowing the vehicle’s real identity and password. If
constructs and sends message
, TA firstly checks the verification of
before performing further computations. According to
Section 3.1,
can register as a legal user and send superfluous request message
. However, RSUs can detect it at the beginning of the authentication phase by checking the revocation list with
. Therefore, the proposed scheme prevents TA from performing cumbrous computation in such situations and reduces the chance of a DoS attack.
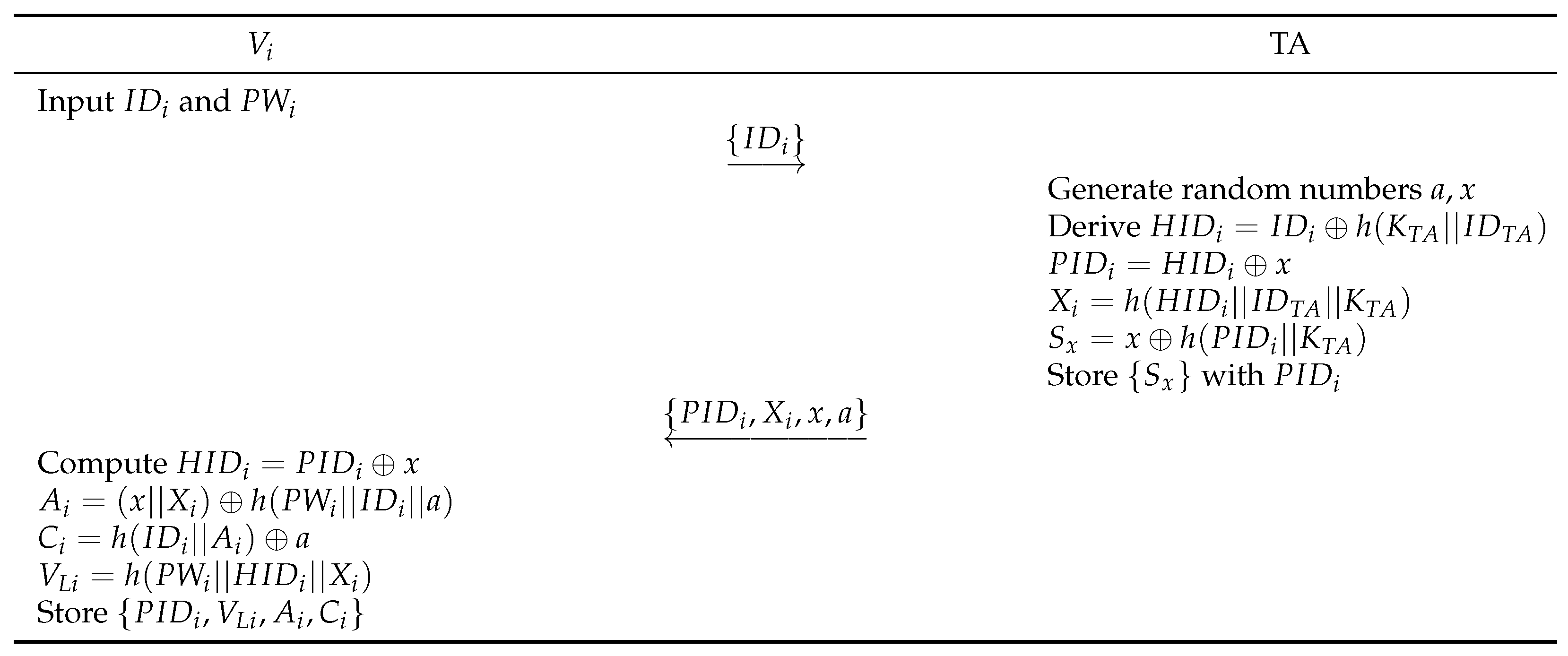
7.1.13. Anonymity
is masked in parameters , , and . In addition, the parameters is masked in parameters , , and . Similarly, pseudo-identity is updated in each session: . Since cannot calculate these parameters, our scheme provides anonymity.
7.1.14. Conditional Privacy
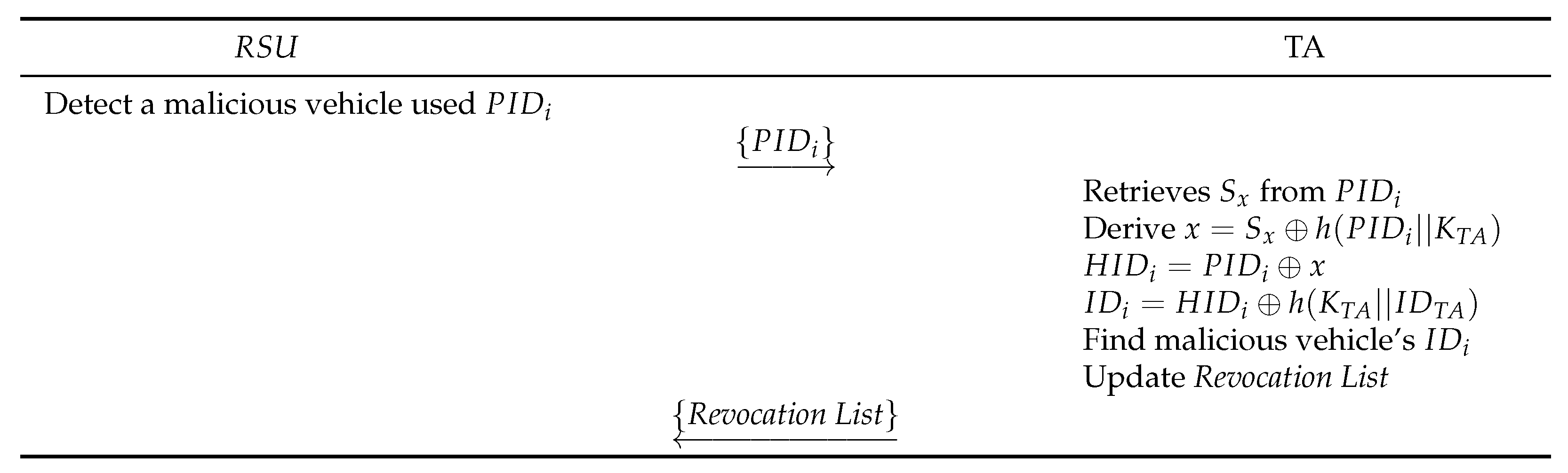
Only the TA can detect real from when vehicles are involved in illegal activities. During the registration phase, the TA stores with secret parameter x. If a malicious vehicle used , the TA retrieves in its secret database. To find the malicious vehicle’s real , the TA computes parameters , , and . Due to the master key , only the TA can calculate these. Finally, the TA reveals the malicious vehicle’s real and updates the revocation list. Thus, our scheme provides conditional privacy.
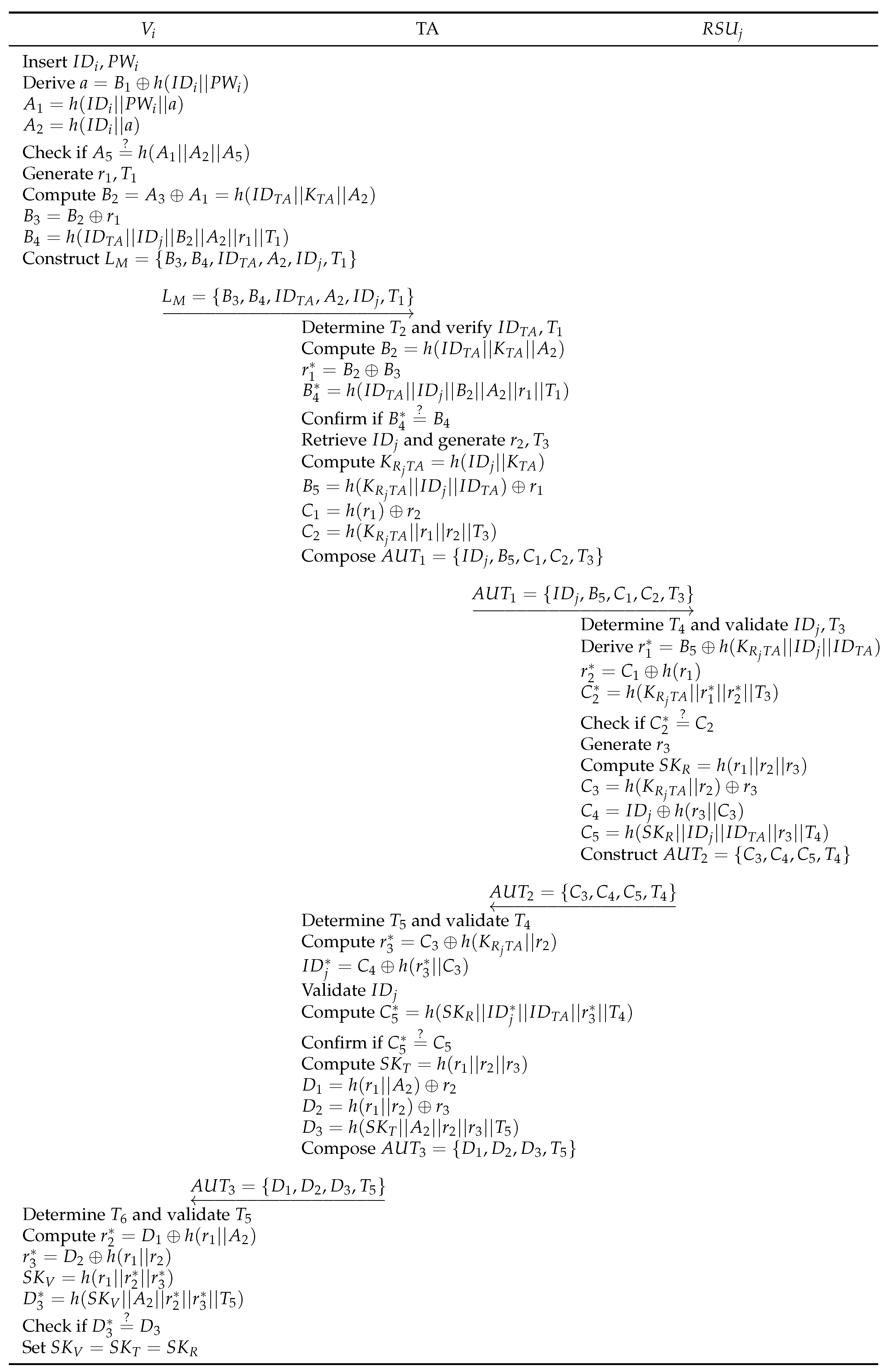
7.1.15. Mutual Authentication
To establish the authentication, our scheme performs a verification process. After inputs and into the OBU, the vehicle checks the equality of and . If it is not equal, the login phase is terminated. The login request over the RSU is validated at the TA by checking if . On the other hand, the RSU verifies and the vehicle checks . In every verification process, the session is terminated immediately if a validation fails.
7.1.16. Perfect Forward Secrecy
If obtains , attempts to compute of a legitimate . However, is only used in the parameter . Moreover, and are not utilized indirectly, such as , and . Even if is leaked, cannot obtain without the shared secret parameters or . Thus, the proposed scheme can achieve perfect forward secrecy.
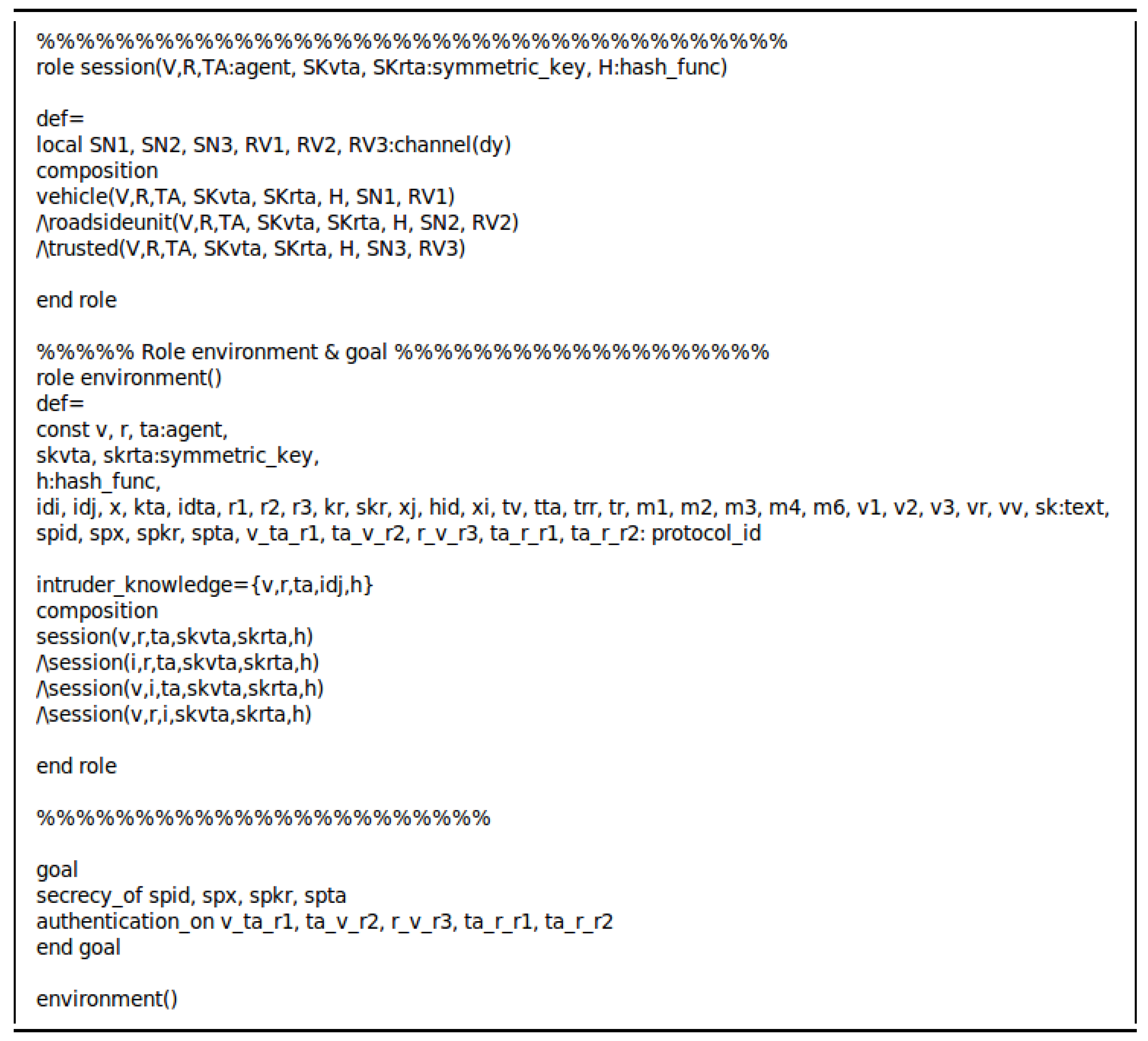
7.3. ROR Model
We utilize the ROR model [
19] to analyze the semantic security of the proposed scheme. In this model, we denote
as the
instances of participants. There are three participants in the proposed scheme, which are vehicle
, RSU
, and TA
. The ROR model assumes that an adversary
can perform various attacks to disclose the session key by executing queries, such as
Execute, CorruptOBU, Send, and
Test. Moreover, all participants, including
, can access a collision-resistant cryptographic one-way hash function
, which is said as
[
38]. The detailed description of queries is as below.
Execute(, , ): can eavesdrop the transmitted messages between , , and via public channel. This query represents the eavesdropping attack by .
CorruptOBU(): performs this query to extract the stored data from the OBU of .
Send(, Msg): Using this query, can send a message to the participant and receive a reply.
Test(): uses this query to verify the semantic security of the session key. By executing this query, can obtain a coin flip test, where represents the tail of a coin and represents the head of a coin. Based on the result, receives a random string when and the session key when from . Otherwise, receives a value. If cannot distinguish the result between a random string and the session key, the session key is secure.
Theorem 1. Suppose that attempts to distinguish the session key and a random number. We denote as the advantage of in the model. Then, and denote the number of and queries executed by , and is the range of the . and are the distributed identity and password dictionaries, and and are the size of each dictionary. Proof. can perform the attack procedures through four games . denotes the probability that guesses the correct result c in . The proof processes of and are described as follows:
: This game represents that
attempts the actual attack on the proposed authentication schemes. Then,
can guess a random bit
c at the beginning of the game and hence the outcome is the following Equation (
2).
:
performs
query to attempt the eavesdropping attack. After that,
verifies whether the obtained session key
and a random number are real by executing
query. However,
cannot obtain meaningful parameters using an eavesdropping attack to calculate the session key
. This means
cannot obtain any advantage from winning
. Therefore,
and
are indistinguishable, and we obtain the following:
: In this game,
performs
and
queries to obtain the session key.
can attempt to modify transmitted messages. However, deriving secret parameters from the intercepted messages is a computationally infeasible task. It’s because all exchanged messages in our scheme are encrypted with one-way hash function
, which has collision-resistant properties. According to [
39], the birthday paradox represents the probability of hash collision as
, where
is the length of a hash result. Thus, we can obtain the advantage of
in
as below.
:
can try to obtain
with
.
can obtain the information
. However,
needs
which is masked with
and
. Therefore,
can try to guess the values from identity and password dictionaries. Basically, the length of identity is 160 bits. As the length of a password increases, the probability that
correctly guesses both identity and password decreases exponentially. The whole combinations of dictionaries
are roughly
, where
is the length of the password. Then, we can obtain the following:
As all the games are executed,
must guess the exact bit
c. However,
has no advantage to guess
c; then, we can obtain the below equation.
Using Equations (
2), (
3), and (
6), we can obtain the result as below:
We obtain the following result by applying the triangular inequality to Equation (
7):
Finally, we obtain the required result by multiplying both sides of Equation (
8) by 2.
Therefore, we prove Theorem 1.
□